4ed0e5ebad81c6af7c6a3b30f9879f9d.ppt
- Количество слайдов: 32
 Introduction to Novell Nsure Identity Manager 2 (formerly Dir. XML) Deven Macdonald Product Manager dmacdonald@novell. com
Introduction to Novell Nsure Identity Manager 2 (formerly Dir. XML) Deven Macdonald Product Manager dmacdonald@novell. com
 Contents Dir. XML Today New Features in Nsure Identity Manager 2 Upgrading to Identity Manager 2 2 © 3/17/2018 Novell Inc,
Contents Dir. XML Today New Features in Nsure Identity Manager 2 Upgrading to Identity Manager 2 2 © 3/17/2018 Novell Inc,
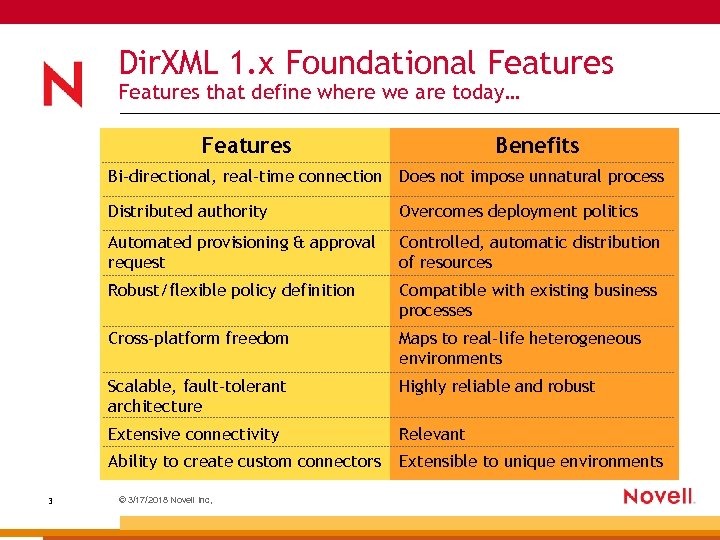 Dir. XML 1. x Foundational Features that define where we are today… Features Benefits Bi-directional, real-time connection Does not impose unnatural process Distributed authority Automated provisioning & approval request Controlled, automatic distribution of resources Robust/flexible policy definition Compatible with existing business processes Cross-platform freedom Maps to real-life heterogeneous environments Scalable, fault-tolerant architecture Highly reliable and robust Extensive connectivity Relevant Ability to create custom connectors 3 Overcomes deployment politics Extensible to unique environments © 3/17/2018 Novell Inc,
Dir. XML 1. x Foundational Features that define where we are today… Features Benefits Bi-directional, real-time connection Does not impose unnatural process Distributed authority Automated provisioning & approval request Controlled, automatic distribution of resources Robust/flexible policy definition Compatible with existing business processes Cross-platform freedom Maps to real-life heterogeneous environments Scalable, fault-tolerant architecture Highly reliable and robust Extensive connectivity Relevant Ability to create custom connectors 3 Overcomes deployment politics Extensible to unique environments © 3/17/2018 Novell Inc,
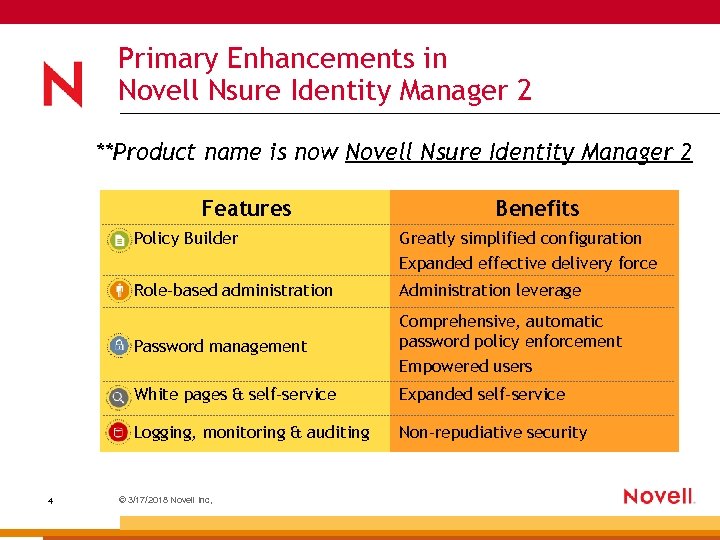 Primary Enhancements in Novell Nsure Identity Manager 2 **Product name is now Novell Nsure Identity Manager 2 Features Benefits Policy Builder Role-based administration Administration leverage Password management Comprehensive, automatic password policy enforcement Empowered users White pages & self-service Expanded self-service Logging, monitoring & auditing 4 Greatly simplified configuration Expanded effective delivery force Non-repudiative security © 3/17/2018 Novell Inc,
Primary Enhancements in Novell Nsure Identity Manager 2 **Product name is now Novell Nsure Identity Manager 2 Features Benefits Policy Builder Role-based administration Administration leverage Password management Comprehensive, automatic password policy enforcement Empowered users White pages & self-service Expanded self-service Logging, monitoring & auditing 4 Greatly simplified configuration Expanded effective delivery force Non-repudiative security © 3/17/2018 Novell Inc,
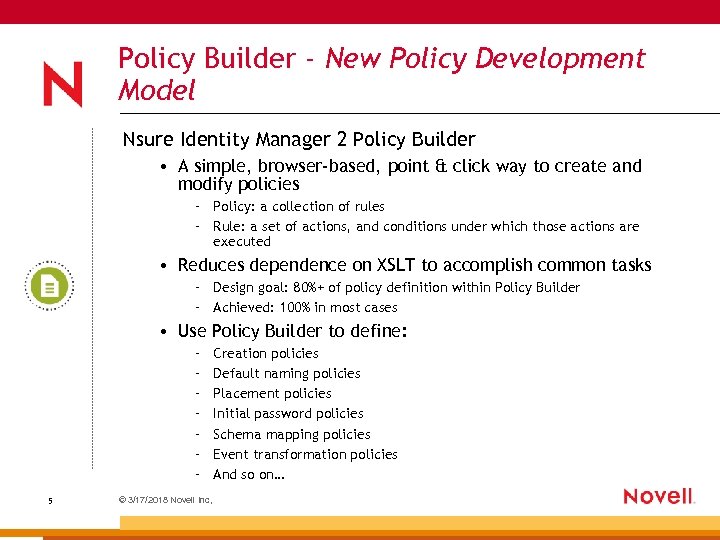 Policy Builder - New Policy Development Model Nsure Identity Manager 2 Policy Builder • A simple, browser-based, point & click way to create and modify policies – Policy: a collection of rules – Rule: a set of actions, and conditions under which those actions are executed • Reduces dependence on XSLT to accomplish common tasks – Design goal: 80%+ of policy definition within Policy Builder – Achieved: 100% in most cases • Use Policy Builder to define: – – – – 5 © 3/17/2018 Novell Inc, Creation policies Default naming policies Placement policies Initial password policies Schema mapping policies Event transformation policies And so on…
Policy Builder - New Policy Development Model Nsure Identity Manager 2 Policy Builder • A simple, browser-based, point & click way to create and modify policies – Policy: a collection of rules – Rule: a set of actions, and conditions under which those actions are executed • Reduces dependence on XSLT to accomplish common tasks – Design goal: 80%+ of policy definition within Policy Builder – Achieved: 100% in most cases • Use Policy Builder to define: – – – – 5 © 3/17/2018 Novell Inc, Creation policies Default naming policies Placement policies Initial password policies Schema mapping policies Event transformation policies And so on…
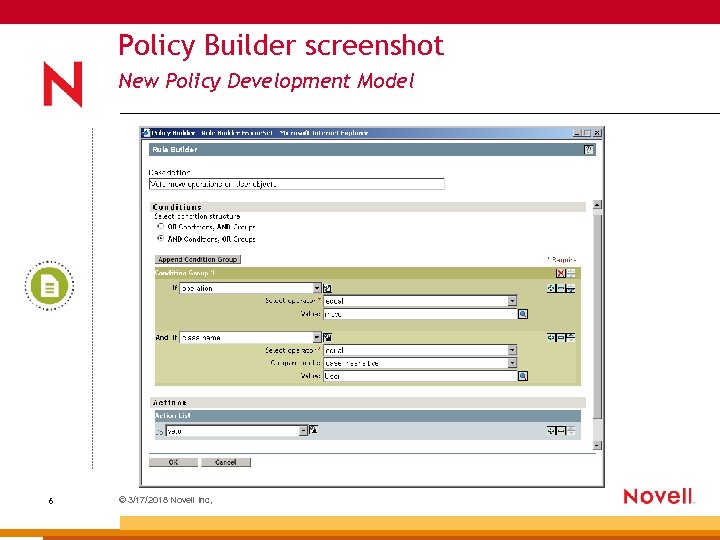 Policy Builder screenshot New Policy Development Model 6 © 3/17/2018 Novell Inc,
Policy Builder screenshot New Policy Development Model 6 © 3/17/2018 Novell Inc,
 New Policy Development Model Bottom Line, What’s Changed? Rules and Policies definitions In Dir. XML 1. 1 a, the policies used in a driver configuration were called rules, objects and Stylesheet objects. In Identity Manager 2, each part of the driver configuration is called a Policy object, and these policies contain individual rules. The Policy Builder helps you set up twenty-five of the most common rules using the new IDM Script, with NO XSLT. 7 © 3/17/2018 Novell Inc,
New Policy Development Model Bottom Line, What’s Changed? Rules and Policies definitions In Dir. XML 1. 1 a, the policies used in a driver configuration were called rules, objects and Stylesheet objects. In Identity Manager 2, each part of the driver configuration is called a Policy object, and these policies contain individual rules. The Policy Builder helps you set up twenty-five of the most common rules using the new IDM Script, with NO XSLT. 7 © 3/17/2018 Novell Inc,
 New Policy Development Model The Details What are Rules, What are Policies? In Dir. XML 1. x, the term rule described a set of rules, the individual rules in this set, and the conditions and actions within the individual rules, depending on the context. This overlap caused confusion. In Identity Manager 2, policy replaces the previous usage of rule, when describing the high level transformation that is occurring. You define a set of policies, consisting of one or more policies, where each policy contains one or more rules. The term rule describes only an individual set of conditions and actions. 8 © 3/17/2018 Novell Inc,
New Policy Development Model The Details What are Rules, What are Policies? In Dir. XML 1. x, the term rule described a set of rules, the individual rules in this set, and the conditions and actions within the individual rules, depending on the context. This overlap caused confusion. In Identity Manager 2, policy replaces the previous usage of rule, when describing the high level transformation that is occurring. You define a set of policies, consisting of one or more policies, where each policy contains one or more rules. The term rule describes only an individual set of conditions and actions. 8 © 3/17/2018 Novell Inc,
 New Policy Development Model Policies are now created in one of two ways: 1 New Way: Using the Policy Builder to generate Dir. XML Script. (Existing, non-XSLT rules are converted to Dir. XML Script automatically upon import. ) 2 Old Way: Using XSLT stylesheets. 9 © 3/17/2018 Novell Inc,
New Policy Development Model Policies are now created in one of two ways: 1 New Way: Using the Policy Builder to generate Dir. XML Script. (Existing, non-XSLT rules are converted to Dir. XML Script automatically upon import. ) 2 Old Way: Using XSLT stylesheets. 9 © 3/17/2018 Novell Inc,
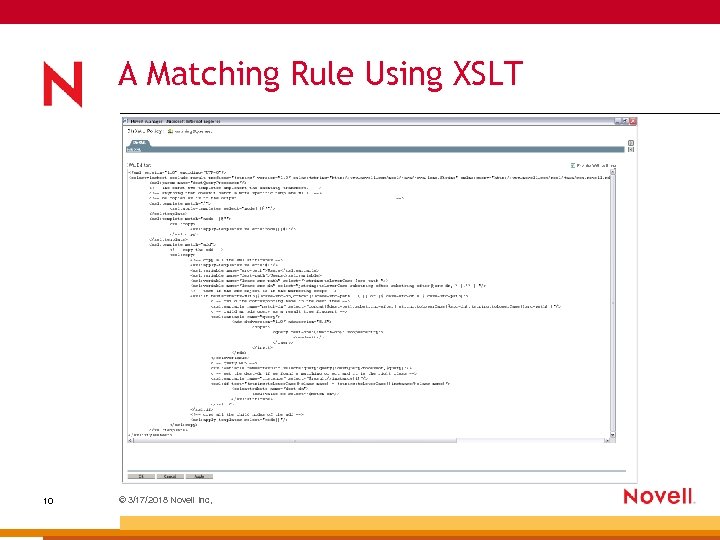 A Matching Rule Using XSLT 10 © 3/17/2018 Novell Inc,
A Matching Rule Using XSLT 10 © 3/17/2018 Novell Inc,
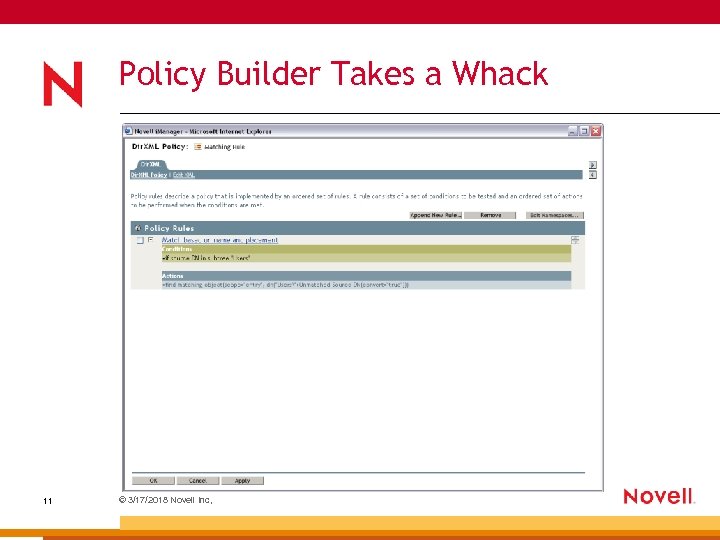 Policy Builder Takes a Whack 11 © 3/17/2018 Novell Inc,
Policy Builder Takes a Whack 11 © 3/17/2018 Novell Inc,
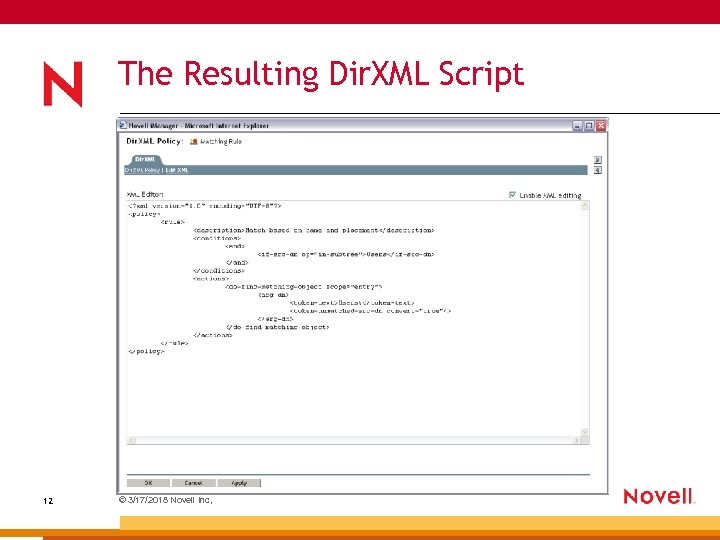 The Resulting Dir. XML Script 12 © 3/17/2018 Novell Inc,
The Resulting Dir. XML Script 12 © 3/17/2018 Novell Inc,
 Role-based Entitlements Provides resource entitlements to users based on their memberships in a role. • Role membership is determined dynamically or statically – Dynamic memberships can be defined by combinations of attributes – Uses inclusion and/or exclusion to define membership • Sample entitlements: – Accounts on connected systems – Inclusion in a NOS group – Inclusion in an email distribution list • Entitlements are re-calculated and provisioned when users are added or changed 13 © 3/17/2018 Novell Inc,
Role-based Entitlements Provides resource entitlements to users based on their memberships in a role. • Role membership is determined dynamically or statically – Dynamic memberships can be defined by combinations of attributes – Uses inclusion and/or exclusion to define membership • Sample entitlements: – Accounts on connected systems – Inclusion in a NOS group – Inclusion in an email distribution list • Entitlements are re-calculated and provisioned when users are added or changed 13 © 3/17/2018 Novell Inc,
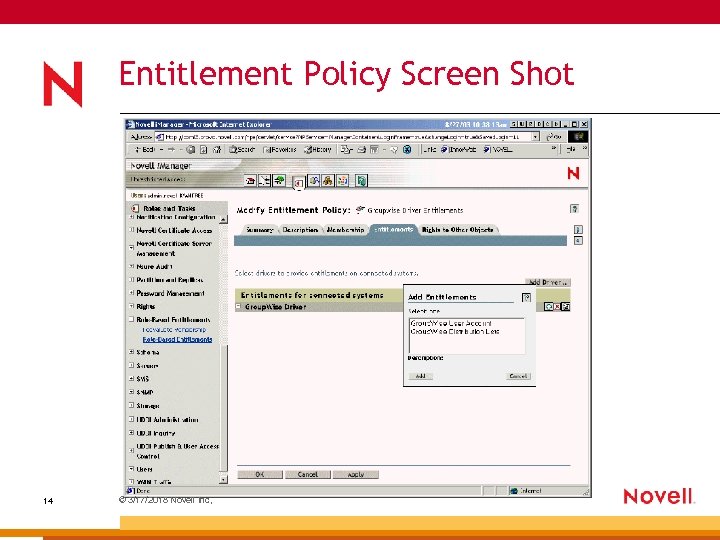 Entitlement Policy Screen Shot 14 © 3/17/2018 Novell Inc,
Entitlement Policy Screen Shot 14 © 3/17/2018 Novell Inc,
 Role-based Entitlements on connected systems are defined by the Identity Manager (IDM) developer who creates the driver configuration. They can be anything that the driver supports. The driver configurations that ship with IDM 2 can be used out-of-the-box with connected systems, but they show only a sample of what a IDM developer could do when defining entitlements. Because Role-Based Entitlements functionality is based on IDM, you must have IDM drivers installed and configured properly in order to be able to administer connected systems. 15 © 3/17/2018 Novell Inc,
Role-based Entitlements on connected systems are defined by the Identity Manager (IDM) developer who creates the driver configuration. They can be anything that the driver supports. The driver configurations that ship with IDM 2 can be used out-of-the-box with connected systems, but they show only a sample of what a IDM developer could do when defining entitlements. Because Role-Based Entitlements functionality is based on IDM, you must have IDM drivers installed and configured properly in order to be able to administer connected systems. 15 © 3/17/2018 Novell Inc,
 Which Drivers Support RBE? The driver configurations included with Identity Manager 2 support Role-Based Entitlements for the following connected systems: • Active Directory • Exchange • Group. Wise • LDAP • Notes • NIS • NT Domain 16 © 3/17/2018 Novell Inc,
Which Drivers Support RBE? The driver configurations included with Identity Manager 2 support Role-Based Entitlements for the following connected systems: • Active Directory • Exchange • Group. Wise • LDAP • Notes • NIS • NT Domain 16 © 3/17/2018 Novell Inc,
 Who Should Use Role Based Entitlements Role-Based Entitlements is an alternative way to administer Identity Manager. Consider the following: 1. Choose RBE if you prefer a more centralized model of IDM administration. 2. The Role-Based Entitlement model fits an environment where one or a few administrators have authority to control which entitlements are given to groups of users. 3. RBE is a good fit for a small or mid-sized business that can centralize authority for administering business policies. It gives you a big-picture view. 4. However--You should decide between using custom IDM policies and using Role-Based Entitlements. You should not use both methods for provisioning user entitlements on the same connected system. 17 © 3/17/2018 Novell Inc,
Who Should Use Role Based Entitlements Role-Based Entitlements is an alternative way to administer Identity Manager. Consider the following: 1. Choose RBE if you prefer a more centralized model of IDM administration. 2. The Role-Based Entitlement model fits an environment where one or a few administrators have authority to control which entitlements are given to groups of users. 3. RBE is a good fit for a small or mid-sized business that can centralize authority for administering business policies. It gives you a big-picture view. 4. However--You should decide between using custom IDM policies and using Role-Based Entitlements. You should not use both methods for provisioning user entitlements on the same connected system. 17 © 3/17/2018 Novell Inc,
 Password Management A suite of password-related security functions: • System-wide password policy – Establish password policy that will be used for and enforced on connected systems • Password self-service – Empower users to help themselves with forgotten passwords, password resets, changing passwords • Password distribution – Specify connected systems that will receive the organization’s common password, as defined in password policy • Bi-directional password synchronization – Manage the native password management activities in connected systems, ensuring consistency 18 © 3/17/2018 Novell Inc,
Password Management A suite of password-related security functions: • System-wide password policy – Establish password policy that will be used for and enforced on connected systems • Password self-service – Empower users to help themselves with forgotten passwords, password resets, changing passwords • Password distribution – Specify connected systems that will receive the organization’s common password, as defined in password policy • Bi-directional password synchronization – Manage the native password management activities in connected systems, ensuring consistency 18 © 3/17/2018 Novell Inc,
 Password Management Password Policy • Administrators specify required properties of an acceptable password for systems throughout the enterprise • Examples of password policy controls: – – – Minimum/maximum number of characters Minimum number of upper case characters Minimum number of numerals Password re-use forbidden Password exclusion lists And so on… • Conformance is checked before allowing password to be set in the Nsure Identity Manager 2 identity vault 19 © 3/17/2018 Novell Inc,
Password Management Password Policy • Administrators specify required properties of an acceptable password for systems throughout the enterprise • Examples of password policy controls: – – – Minimum/maximum number of characters Minimum number of upper case characters Minimum number of numerals Password re-use forbidden Password exclusion lists And so on… • Conformance is checked before allowing password to be set in the Nsure Identity Manager 2 identity vault 19 © 3/17/2018 Novell Inc,
 Password Management Password Self-Service • Administrators configure self-service policies – Challenge/Response options – Challenge/Response success actions (for example: ) – – Email hint Reset to last good password Display hint on the page Allow users to change their password • Users configure their own hints and/or answers to challenge questions – Hint is not allowed to contain the password 20 © 3/17/2018 Novell Inc,
Password Management Password Self-Service • Administrators configure self-service policies – Challenge/Response options – Challenge/Response success actions (for example: ) – – Email hint Reset to last good password Display hint on the page Allow users to change their password • Users configure their own hints and/or answers to challenge questions – Hint is not allowed to contain the password 20 © 3/17/2018 Novell Inc,
 Password Management Password Distribution • User sets a new common password using the self-service password interface • New password is checked against password policy • New password is set on user object within the Nsure Identity Manager 2 identity vault • Password is distributed to associated user objects on connected systems 21 © 3/17/2018 Novell Inc, Connected Systems • • • e. Directory Legacy NDS Active Directory/Exchange 2000 Windows NT Domains Network Information Service (NIS) • Linux • Solaris • other UNIX Group. Wise Lotus Notes Sun. One SAP User Management Relational databases • Oracle • DB 2 • Sybase
Password Management Password Distribution • User sets a new common password using the self-service password interface • New password is checked against password policy • New password is set on user object within the Nsure Identity Manager 2 identity vault • Password is distributed to associated user objects on connected systems 21 © 3/17/2018 Novell Inc, Connected Systems • • • e. Directory Legacy NDS Active Directory/Exchange 2000 Windows NT Domains Network Information Service (NIS) • Linux • Solaris • other UNIX Group. Wise Lotus Notes Sun. One SAP User Management Relational databases • Oracle • DB 2 • Sybase
 Password Management Bi-directional Password Synchronization • Users can perform password management functions through native password interfaces – – – Windows NT (NT Domains) Windows 2000 (Active Directory) Windows 2003 (remotely, Active Directory) e. Directory (all platforms) NIS (Unix, Linux) • Nsure Identity Manager 2 detects the change and checks against policy • If successful, password is distributed throughout the connected system • If unsuccessful – Failure Notice sent via email – Password is reset to last good password 22 © 3/17/2018 Novell Inc,
Password Management Bi-directional Password Synchronization • Users can perform password management functions through native password interfaces – – – Windows NT (NT Domains) Windows 2000 (Active Directory) Windows 2003 (remotely, Active Directory) e. Directory (all platforms) NIS (Unix, Linux) • Nsure Identity Manager 2 detects the change and checks against policy • If successful, password is distributed throughout the connected system • If unsuccessful – Failure Notice sent via email – Password is reset to last good password 22 © 3/17/2018 Novell Inc,
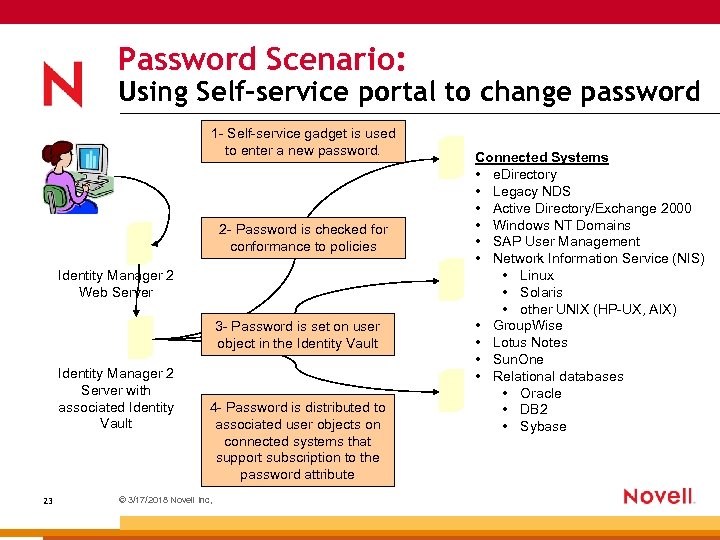 Password Scenario: Using Self-service portal to change password 1 - Self-service gadget is used to enter a new password. 2 - Password is checked for conformance to policies Identity Manager 2 Web Server 3 - Password is set on user object in the Identity Vault Identity Manager 2 Server with associated Identity Vault 23 4 - Password is distributed to associated user objects on connected systems that support subscription to the password attribute © 3/17/2018 Novell Inc, Connected Systems • e. Directory • Legacy NDS • Active Directory/Exchange 2000 • Windows NT Domains • SAP User Management • Network Information Service (NIS) • Linux • Solaris • other UNIX (HP-UX, AIX) • Group. Wise • Lotus Notes • Sun. One • Relational databases • Oracle • DB 2 • Sybase
Password Scenario: Using Self-service portal to change password 1 - Self-service gadget is used to enter a new password. 2 - Password is checked for conformance to policies Identity Manager 2 Web Server 3 - Password is set on user object in the Identity Vault Identity Manager 2 Server with associated Identity Vault 23 4 - Password is distributed to associated user objects on connected systems that support subscription to the password attribute © 3/17/2018 Novell Inc, Connected Systems • e. Directory • Legacy NDS • Active Directory/Exchange 2000 • Windows NT Domains • SAP User Management • Network Information Service (NIS) • Linux • Solaris • other UNIX (HP-UX, AIX) • Group. Wise • Lotus Notes • Sun. One • Relational databases • Oracle • DB 2 • Sybase
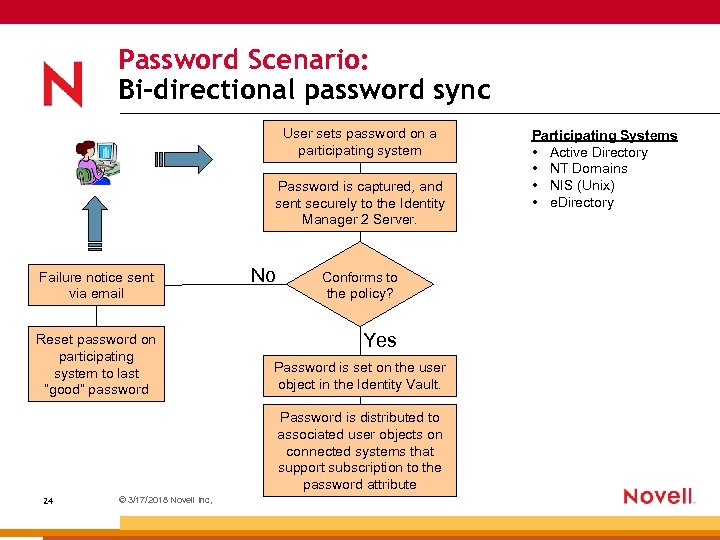 Password Scenario: Bi-directional password sync User sets password on a participating system Password is captured, and sent securely to the Identity Manager 2 Server. Failure notice sent via email Reset password on participating system to last “good” password No Conforms toto Conforms thethepolicy? the policy? Yes Password is set on the user object in the Identity Vault. Password is distributed to associated user objects on connected systems that support subscription to the password attribute 24 © 3/17/2018 Novell Inc, Participating Systems • Active Directory • NT Domains • NIS (Unix) • e. Directory
Password Scenario: Bi-directional password sync User sets password on a participating system Password is captured, and sent securely to the Identity Manager 2 Server. Failure notice sent via email Reset password on participating system to last “good” password No Conforms toto Conforms thethepolicy? the policy? Yes Password is set on the user object in the Identity Vault. Password is distributed to associated user objects on connected systems that support subscription to the password attribute 24 © 3/17/2018 Novell Inc, Participating Systems • Active Directory • NT Domains • NIS (Unix) • e. Directory
 Primary Enhancement: White Pages & Self-Service e. Guide • Look up information on objects in e. Directory and/or other LDAP repositories • Anonymous mode or Authenticated mode • Allows user to maintain their own information • Integrated Organizational Chart view • Supports digital photos, etc. 25 © 3/17/2018 Novell Inc,
Primary Enhancement: White Pages & Self-Service e. Guide • Look up information on objects in e. Directory and/or other LDAP repositories • Anonymous mode or Authenticated mode • Allows user to maintain their own information • Integrated Organizational Chart view • Supports digital photos, etc. 25 © 3/17/2018 Novell Inc,
 Primary Enhancement: Nsure Audit Integration Novell’s official logging & auditing framework • Centralized log for all systems throughout the enterprise – SQL, flat file or SYSLOG – Standard for all Novell applications – Open to 3 rd party integration • Nsure Identity Manager 2 logs all identity management activity • Includes reporting and notification capabilities • Optional upgrades – Non-repudiative log – Real-time monitor 26 © 3/17/2018 Novell Inc,
Primary Enhancement: Nsure Audit Integration Novell’s official logging & auditing framework • Centralized log for all systems throughout the enterprise – SQL, flat file or SYSLOG – Standard for all Novell applications – Open to 3 rd party integration • Nsure Identity Manager 2 logs all identity management activity • Includes reporting and notification capabilities • Optional upgrades – Non-repudiative log – Real-time monitor 26 © 3/17/2018 Novell Inc,
 Upgrading to Nsure Identity Manager 2 Upgrade Overview • New version is backward compatible – Drivers can be mix of old/new – XSLT Configuration does not change • Automatic conversion of XML rules and filters to new format • Drivers updated separately from the engine – Continue administration of previous versions with existing i. Manager 27 © 3/17/2018 Novell Inc,
Upgrading to Nsure Identity Manager 2 Upgrade Overview • New version is backward compatible – Drivers can be mix of old/new – XSLT Configuration does not change • Automatic conversion of XML rules and filters to new format • Drivers updated separately from the engine – Continue administration of previous versions with existing i. Manager 27 © 3/17/2018 Novell Inc,
 Upgrading to Nsure Identity Manager 2 Upgrade Consists of… Laying down new Code: • • • e. Directory (optional) Dir. XML engine i. Manager plugins Drivers Converting into new format: • XML rules (now all policy gates can be done via XML, not just convert, placement, matching) • Filters (all one object, filter for notify vs. sync, merge authority) 28 © 3/17/2018 Novell Inc,
Upgrading to Nsure Identity Manager 2 Upgrade Consists of… Laying down new Code: • • • e. Directory (optional) Dir. XML engine i. Manager plugins Drivers Converting into new format: • XML rules (now all policy gates can be done via XML, not just convert, placement, matching) • Filters (all one object, filter for notify vs. sync, merge authority) 28 © 3/17/2018 Novell Inc,
 Upgrading to Nsure Identity Manager 2 Upgrade Process Install on top of existing e. Dir/Dir. XML • Following the process will automatically shut down e. Dir, install the new Dir. XML engine, and restart e. Dir. • If existing drivers are set for automatic startup, they will start up as well Install new i. Manager, new plug-ins Open up driver configuration in i. Manager • This will automatically convert XML-based policies (create, placement, matching), and will convert filters to the new format 29 © 3/17/2018 Novell Inc,
Upgrading to Nsure Identity Manager 2 Upgrade Process Install on top of existing e. Dir/Dir. XML • Following the process will automatically shut down e. Dir, install the new Dir. XML engine, and restart e. Dir. • If existing drivers are set for automatic startup, they will start up as well Install new i. Manager, new plug-ins Open up driver configuration in i. Manager • This will automatically convert XML-based policies (create, placement, matching), and will convert filters to the new format 29 © 3/17/2018 Novell Inc,
 More Information For more information about Nsure Identity Manager please visit: https: //innerweb. novell. com/identitymanager We will be continually adding information to this site for your use so please check it regularly 30 © 3/17/2018 Novell Inc,
More Information For more information about Nsure Identity Manager please visit: https: //innerweb. novell. com/identitymanager We will be continually adding information to this site for your use so please check it regularly 30 © 3/17/2018 Novell Inc,
 31 © 3/17/2018 Novell Inc,
31 © 3/17/2018 Novell Inc,
 Unpublished Work of Novell, Inc. All Rights Reserved. This work is an unpublished work and contains confidential, proprietary, and trade secret information of Novell, Inc. Access to this work is restricted to Novell employees who have a need to know to perform tasks within the scope of their assignments. No part of this work may be practiced, performed, copied, distributed, revised, modified, translated, abridged, condensed, expanded, collected, or adapted without the prior written consent of Novell, Inc. Any use or exploitation of this work without authorization could subject the perpetrator to criminal and civil liability. General Disclaimer This document is not to be construed as a promise by any participating company to develop, deliver, or market a product. Novell, Inc. , makes no representations or warranties with respect to the contents of this document, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. , reserves the right to revise this document and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. 32 © 3/17/2018 Novell Inc,
Unpublished Work of Novell, Inc. All Rights Reserved. This work is an unpublished work and contains confidential, proprietary, and trade secret information of Novell, Inc. Access to this work is restricted to Novell employees who have a need to know to perform tasks within the scope of their assignments. No part of this work may be practiced, performed, copied, distributed, revised, modified, translated, abridged, condensed, expanded, collected, or adapted without the prior written consent of Novell, Inc. Any use or exploitation of this work without authorization could subject the perpetrator to criminal and civil liability. General Disclaimer This document is not to be construed as a promise by any participating company to develop, deliver, or market a product. Novell, Inc. , makes no representations or warranties with respect to the contents of this document, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. , reserves the right to revise this document and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. 32 © 3/17/2018 Novell Inc,


