76c29923a239a4c509be416e27e67645.ppt
- Количество слайдов: 31

Introduction to Mobility Do van Thanh Forelesning på NTNU 19. September 2001
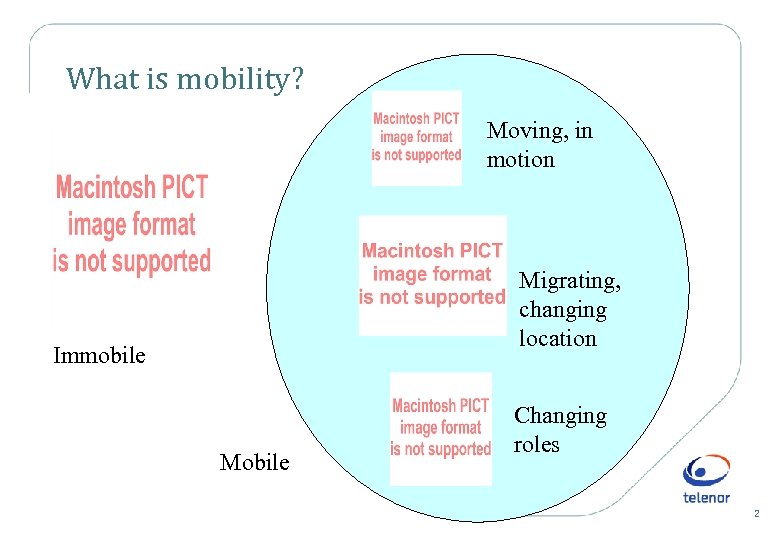
What is mobility? Moving, in motion Migrating, changing location Immobile Mobile Changing roles 2

What is mobility? In the Merriam-Webster's Collegiate Dictionary: Main Entry: 1 mo·bile Pronunciation: 'm. O-b&l, -"b. Il also -"b. El Function: adjective Etymology: Middle English mobyll, from Middle French mobile, from Latin mobilis, from mov. Ere to move Date: 15 th century 1 : capable of moving or being moved : MOVABLE <a mobile missile launcher> 2 a : changeable in appearance, mood, or purpose <mobile face> b : ADAPTABLE, VERSATILE 3 : moving habitually or occasionally from one region or climate to another <the study of migratory birds> MIGRATORY 4 a : characterized by the mixing of social groups b : having the opportunity for or undergoing a shift in status within the hierarchical social levels of a society <socially mobile workers> 5 : marked by the use of vehicles for transportation <mobile warfare> 6 : of or relating to a mobile - mo·bil·i·ty /m. O-'bi-l&-t. E/ noun 3
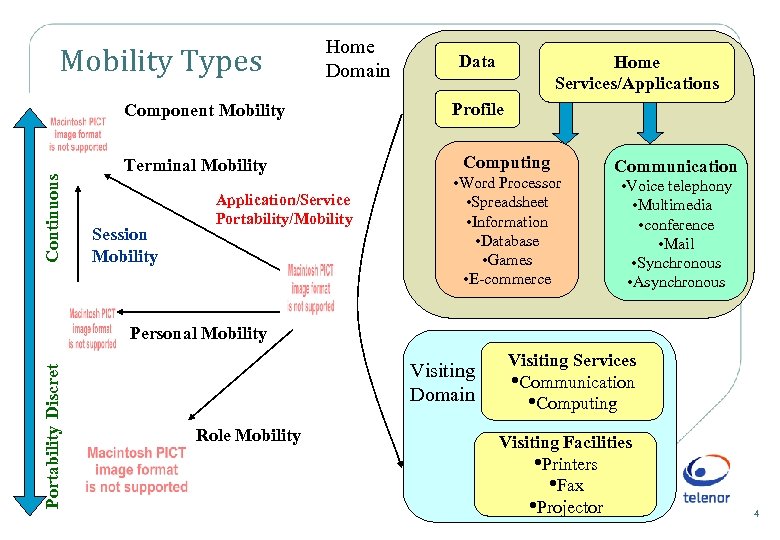
Mobility Types Home Domain Continuous Component Mobility Terminal Mobility Session Mobility Application/Service Portability/Mobility Data Home Services/Applications Profile Computing • Word Processor • Spreadsheet • Information • Database • Games • E-commerce Communication • Voice telephony • Multimedia • conference • Mail • Synchronous • Asynchronous Portability Discret Personal Mobility Visiting Domain Role Mobility Visiting Services • Communication • Computing Visiting Facilities • Printers • Fax • Projector 4
Mobility Types • Terminal mobility allows the terminal to change location while maintaining all services. • Component mobility allows components e. g. earphone, microphone, etc. of a terminal to change location while maintaining all services. The components form a PAN (Personal Area Network) • Personal mobility allows the user to access all services independently of terminals and networks. • Role mobility allows the user to change roles and get access to distinct preferences, rights and limitations. 5
Mobility Types • Session mobility ensures that active sessions are not disrupted while users change terminals. • Application/service portability or mobility allows software entities (codes, objects, processes) to be relocated from one machine to another or even moved between machines while processing. Ex: Applets (code) – Mobile Agents (object) 6
Mobility Types • Continuous Mobility enables continuous availability of services while the user moves. – Ex: Cellular systems • Discrete Mobility enables the availability of services within certain areas and for certain access points, e. g. Home an Office, but not while moving from one area to another – Ex: DECT, Wireless LAN • Portability is an example of discrete terminal mobility, where it is allowed to move a terminal from one plug to another. 7

What is mobility? • Mobility is confined to any particular networks. – Mobile does not mean necessarily wireless since wireline networks can also offer mobility – Wireless does not mean mobile since devices like parkometer, soft drink automate may communicate wireless and remain immobile. • Mobility is not a service because mobility as such has no value for a user if not supplemented with other services. Mobility enhances the availability of other services. • Mobility is a capability that can be added to any network system 8
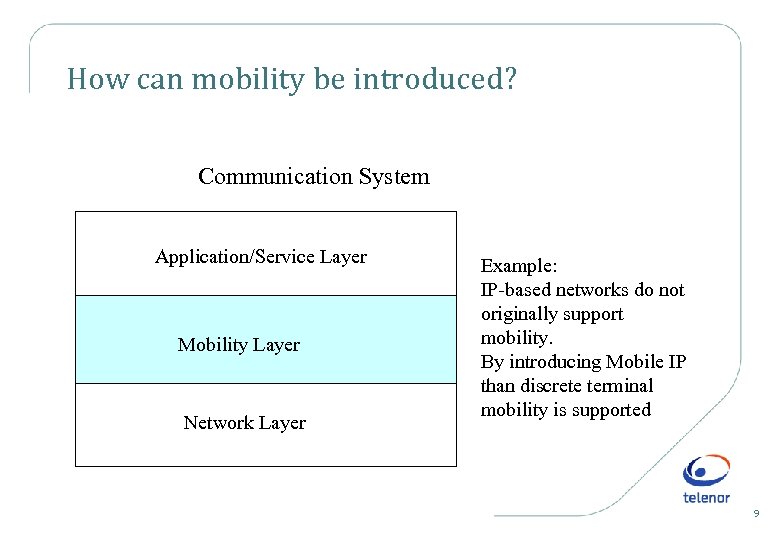
How can mobility be introduced? Communication System Application/Service Layer Mobility Layer Network Layer Example: IP-based networks do not originally support mobility. By introducing Mobile IP than discrete terminal mobility is supported 9
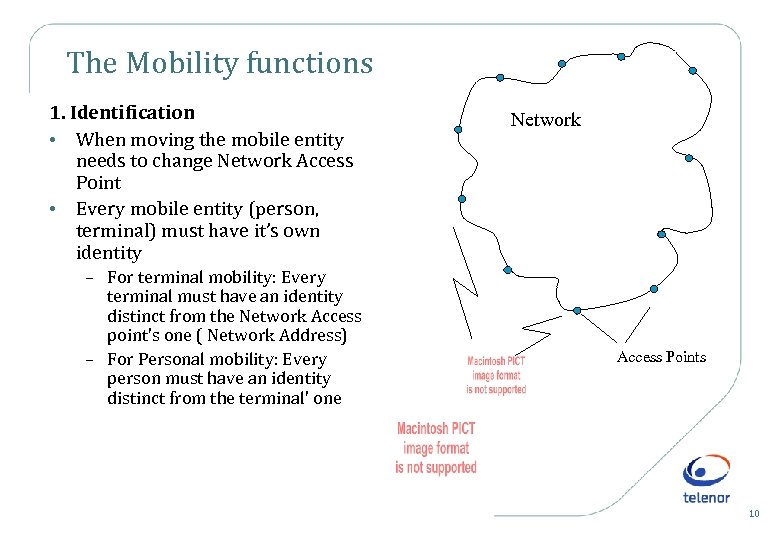
The Mobility functions 1. Identification • When moving the mobile entity needs to change Network Access Point • Every mobile entity (person, terminal) must have it’s own identity – For terminal mobility: Every terminal must have an identity distinct from the Network Access point's one ( Network Address) – For Personal mobility: Every person must have an identity distinct from the terminal' one Network Access Points 10
The Mobility functions 1. Identification • Every entity has only one identity, but may have several identifiers • An identifier is assigned uniquely to one mobile entity • An identifier may be permanent or temporarily allocated according to time, location, context, etc. • A human user may have several identifiers, one public such as email or personal such as login name Example: In GSM Each terminal has a IMEI (International Mobile Equipment Identity) Each mobile subscriber has two identifiers: IMSI (International Mobile Subscriber Identity) TMSI (Temporary Mobile Subscriber Identity) 11
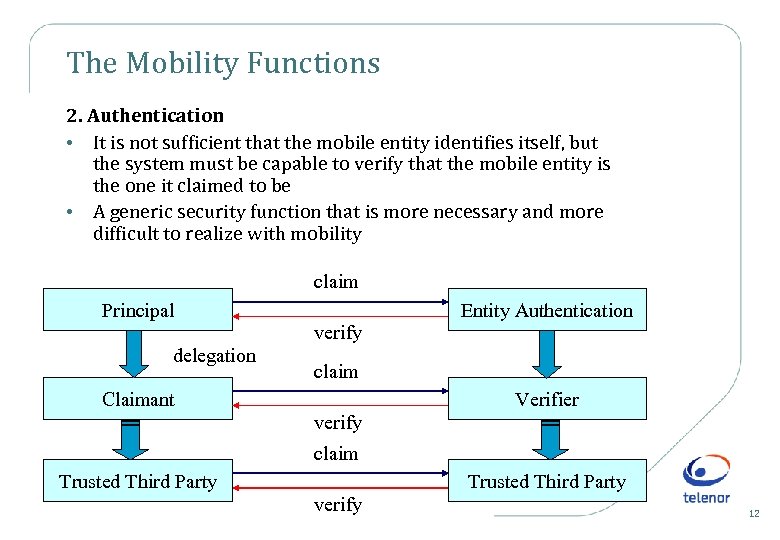
The Mobility Functions 2. Authentication • It is not sufficient that the mobile entity identifies itself, but the system must be capable to verify that the mobile entity is the one it claimed to be • A generic security function that is more necessary and more difficult to realize with mobility claim Principal Entity Authentication verify delegation claim Claimant Verifier verify claim Trusted Third Party verify 12
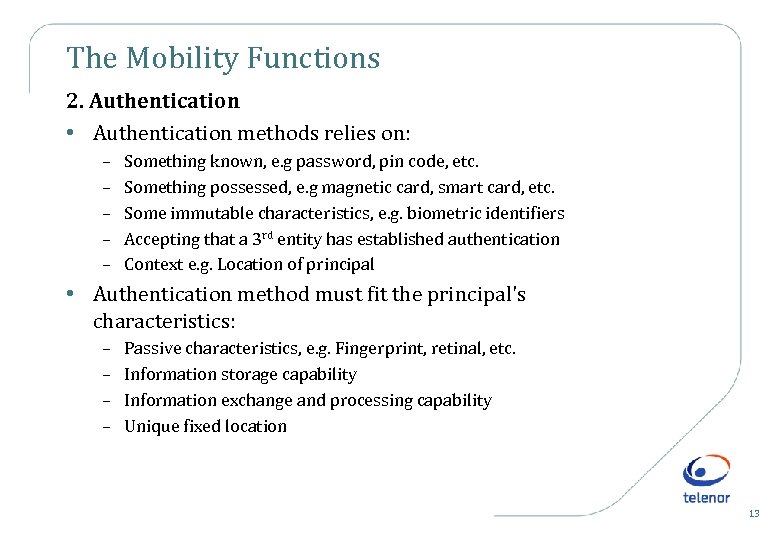
The Mobility Functions 2. Authentication • Authentication methods relies on: – – – Something known, e. g password, pin code, etc. Something possessed, e. g magnetic card, smart card, etc. Some immutable characteristics, e. g. biometric identifiers Accepting that a 3 rd entity has established authentication Context e. g. Location of principal • Authentication method must fit the principal's characteristics: – – Passive characteristics, e. g. Fingerprint, retinal, etc. Information storage capability Information exchange and processing capability Unique fixed location 13
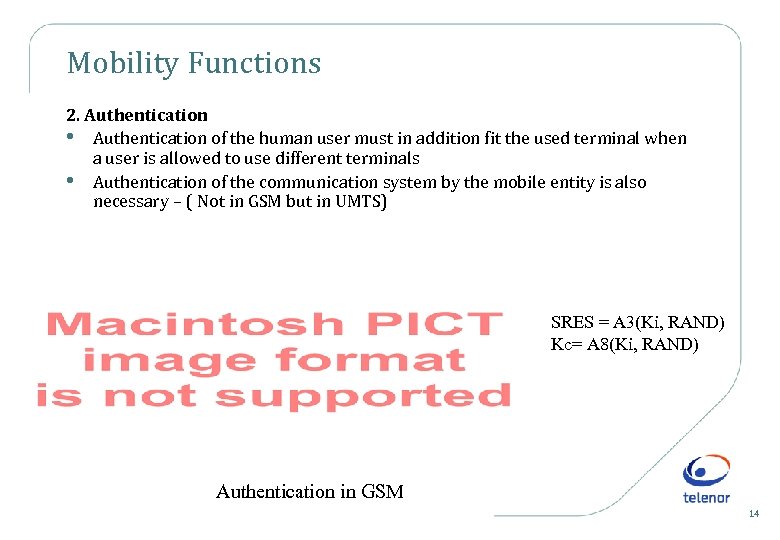
Mobility Functions 2. Authentication • Authentication of the human user must in addition fit the used terminal when a user is allowed to use different terminals • Authentication of the communication system by the mobile entity is also necessary – ( Not in GSM but in UMTS) SRES = A 3(Ki, RAND) Kc= A 8(Ki, RAND) Authentication in GSM 14

Mobility Functions 3. Access Control (or Authorisation) • Even though a mobile entity is authenticated it is not necessarily authorised to access services. • Access control' s goal is to counter the threat of unauthorized access. • The access rights of the mobile entity is limited by: – Roaming restriction – Time restriction – Credit limit 15
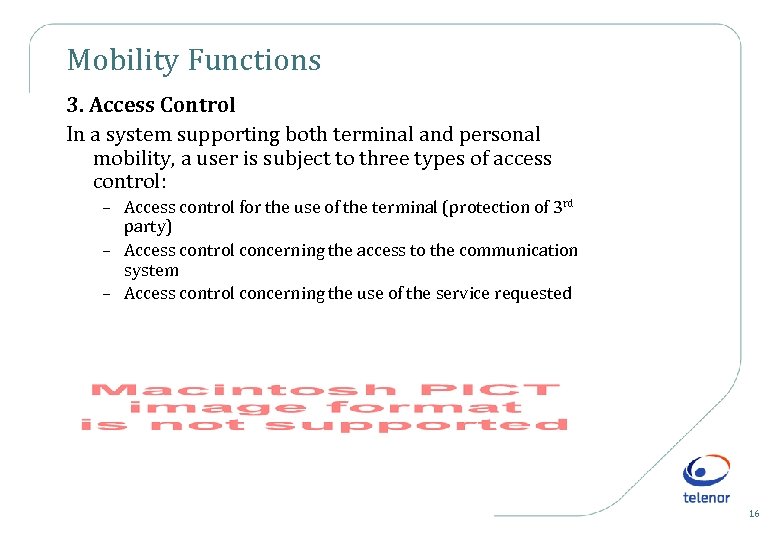
Mobility Functions 3. Access Control In a system supporting both terminal and personal mobility, a user is subject to three types of access control: – Access control for the use of the terminal (protection of 3 rd party) – Access control concerning the access to the communication system – Access control concerning the use of the service requested 16
Mobility Functions 4. Registration/Deregistration • When a terminal moves and uses different access points • Or when a user is using different terminals The system must know about it. A registration is necessary. • Registration is the procedure that associates a mobile entity with a location directly or indirectly. Network Access Points 17

Mobility Functions 4. Registration/Deregistration 18
Mobility Functions 4. Registration/Deregistration • Initiated by communication system – – • • On-the-fly or Lazy Predetermination: • Periodic • Based on changes Initiated by mobile entity Example of GSM: combination of both On-the-fly & Predetermination 19
Mobility Functions 4. Registration/Deregistration • User registration • – – Default registration Local registration Remote registration Registration through profiles User Deregistration – Local deregistration – Remote deregistration – Forced deregistration 20
Mobility Functions 5. User Profile Management • Every user has specific preferences concerning services and their presentation, look and feel, etc. • The setup data is saved in the user profile • The profile can be extended to comprise a address book, a list of favorite links, etc. 21
Mobility Functions 5. User Profile Management • Requirements on the user profile: • – The user should be able to modify his profile from any terminal anywhere and anytime – The applications must be configured according to the profile – Must be saved in a secured manner When the user is using different terminals and different access points, the usage of the profile must be in concordance with the terminal capabilities and the access point physical characteristics. 22

Mobility Functions 5. User Profile Management • With the demand for more customisation of applications combined with the plurality of terminals and devices, the User Profile will play a crucial role in the future • However, not much has been done yet. • The challenge is: "Who is doing the User Profile Management? " 23
Mobility Functions 6. Initiation of services/applications • Distinction between service and application: An application when being executed will offer a service to a user through a session. • Ex: The application "MS Word" when running will offer a word processing service to the user. • The user must have the possibility to initiate or start the same services independently of the access point and the terminal. • Application initiated by the user is called outgoing application (”pull”) Two cases according to the location of the applications: • Application located in the mobile terminal: no problem Ø Ex: Laptop or PDA with all applications 24
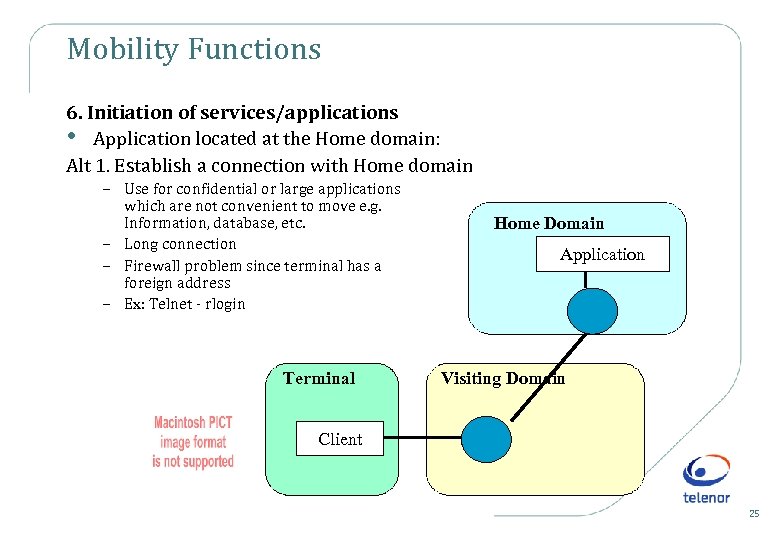
Mobility Functions 6. Initiation of services/applications • Application located at the Home domain: Alt 1. Establish a connection with Home domain – Use for confidential or large applications which are not convenient to move e. g. Information, database, etc. – Long connection – Firewall problem since terminal has a foreign address – Ex: Telnet - rlogin Terminal Home Domain Application Visiting Domain Client 25
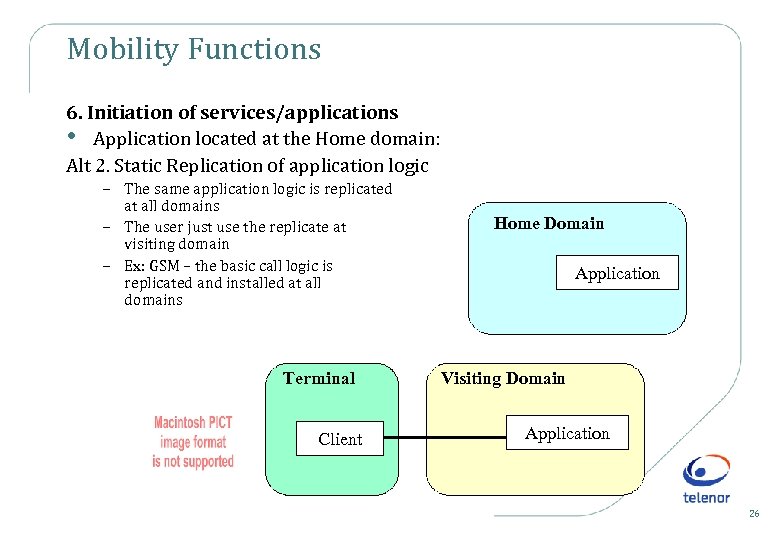
Mobility Functions 6. Initiation of services/applications • Application located at the Home domain: Alt 2. Static Replication of application logic – The same application logic is replicated at all domains – The user just use the replicate at visiting domain – Ex: GSM – the basic call logic is replicated and installed at all domains Terminal Client Home Domain Application Visiting Domain Application 26
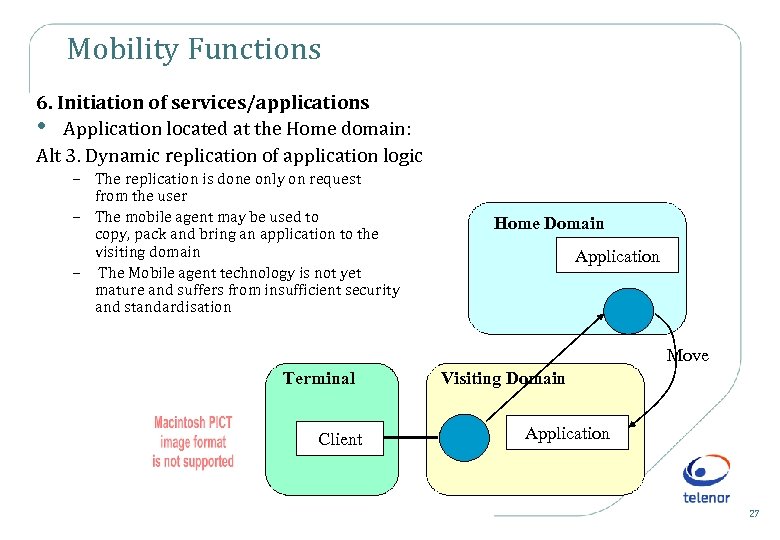
Mobility Functions 6. Initiation of services/applications • Application located at the Home domain: Alt 3. Dynamic replication of application logic – The replication is done only on request from the user – The mobile agent may be used to copy, pack and bring an application to the visiting domain – The Mobile agent technology is not yet mature and suffers from insufficient security and standardisation Home Domain Application Move Terminal Client Visiting Domain Application 27
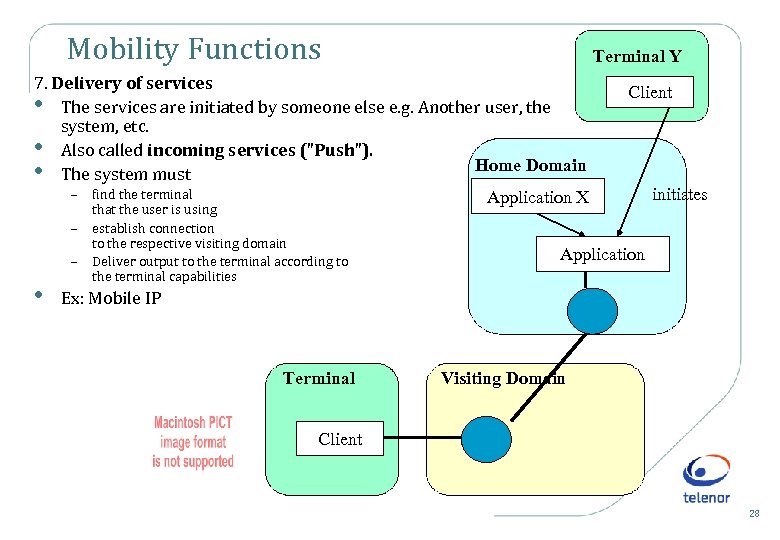
Mobility Functions Terminal Y 7. Delivery of services • The services are initiated by someone else e. g. Another user, the system, etc. • Also called incoming services (”Push”). Home Domain • The system must – find the terminal Application X – – • that the user is using establish connection to the respective visiting domain Deliver output to the terminal according to the terminal capabilities Client initiates Application Ex: Mobile IP Terminal Visiting Domain Client 28
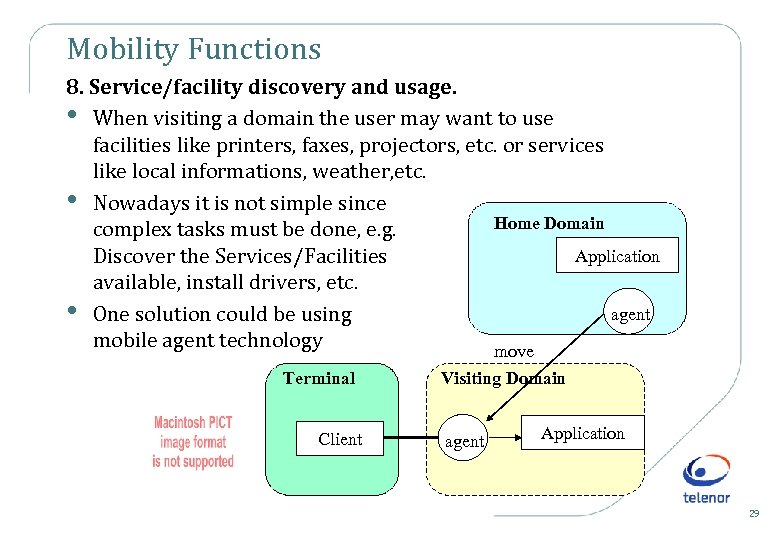
Mobility Functions 8. Service/facility discovery and usage. • When visiting a domain the user may want to use facilities like printers, faxes, projectors, etc. or services like local informations, weather, etc. • Nowadays it is not simple since Home Domain complex tasks must be done, e. g. Application Discover the Services/Facilities available, install drivers, etc. agent • One solution could be using mobile agent technology move Terminal Client Visiting Domain agent Application 29
Mobility Functions 9. Support of mobility-based applications • Mobility-based applications are born with mobility. They are meaningless without mobility. • Examples are taxi dispatch, fleet management, public safety, etc. • Such application needs location information that the mobility layer has. • Provides a mobility interface to mobility-based applications • – Ex: Get. Address (in Terminal. ID, out Address, Out Status) Get. Terminal (in User. ID, out Terminal. ID, Out Status) For UMTS, OSA (Open Service Architecture) /Parlay has specified such a mobility interface 30
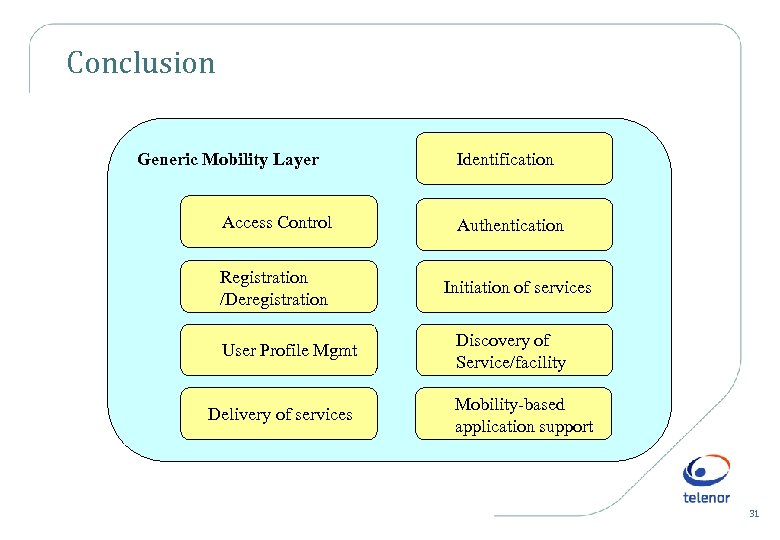
Conclusion Generic Mobility Layer Access Control Registration /Deregistration User Profile Mgmt Delivery of services Identification Authentication Initiation of services Discovery of Service/facility Mobility-based application support 31
76c29923a239a4c509be416e27e67645.ppt