58b96c40127af236f376674f2aaa0894.ppt
- Количество слайдов: 119
 Introduction to IPv 6 Protocols Australian Telecommunications CRC Next Generation Internet Program @ Centre for Telecommunications and Information Engineering Monash University http: //ctieware. eng. monash. edu. au/twiki/bin/view/Applprog © 2003 -2005 Monash CTIE
Introduction to IPv 6 Protocols Australian Telecommunications CRC Next Generation Internet Program @ Centre for Telecommunications and Information Engineering Monash University http: //ctieware. eng. monash. edu. au/twiki/bin/view/Applprog © 2003 -2005 Monash CTIE
 Hello, who are we? Centre for Telecommunications and Information Engineering (CTIE): Research centre within Monash University Part of ATcrc Next Generation Internet Program Have an IPv 6 testbed running Developers of IPv 6 Multimedia applications Implementers of IPv 6 Mobility protocols Contributors to IETF Working Groups and standards on Mobile. IP and IPv 6 Diverse Research and Commercial Experience. © 2003 -2005 Monash CTIE Slide 2
Hello, who are we? Centre for Telecommunications and Information Engineering (CTIE): Research centre within Monash University Part of ATcrc Next Generation Internet Program Have an IPv 6 testbed running Developers of IPv 6 Multimedia applications Implementers of IPv 6 Mobility protocols Contributors to IETF Working Groups and standards on Mobile. IP and IPv 6 Diverse Research and Commercial Experience. © 2003 -2005 Monash CTIE Slide 2
 What we will present : Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 3
What we will present : Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 3
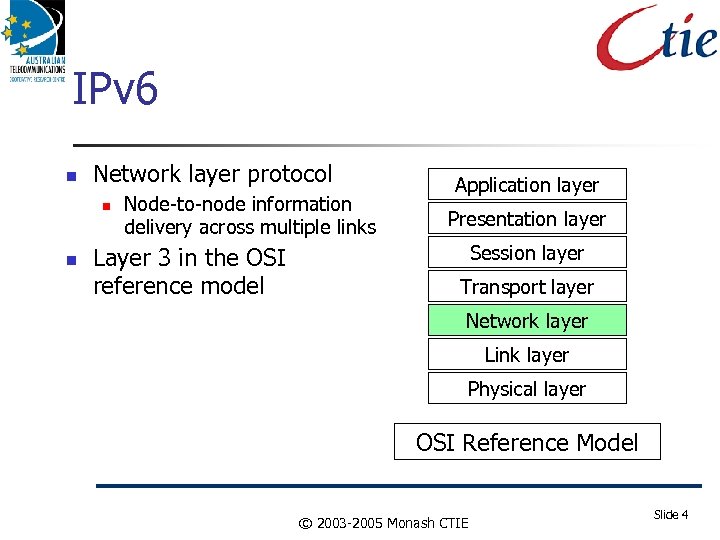 IPv 6 Network layer protocol Node-to-node information delivery across multiple links Layer 3 in the OSI reference model Application layer Presentation layer Session layer Transport layer Network layer Link layer Physical layer OSI Reference Model © 2003 -2005 Monash CTIE Slide 4
IPv 6 Network layer protocol Node-to-node information delivery across multiple links Layer 3 in the OSI reference model Application layer Presentation layer Session layer Transport layer Network layer Link layer Physical layer OSI Reference Model © 2003 -2005 Monash CTIE Slide 4
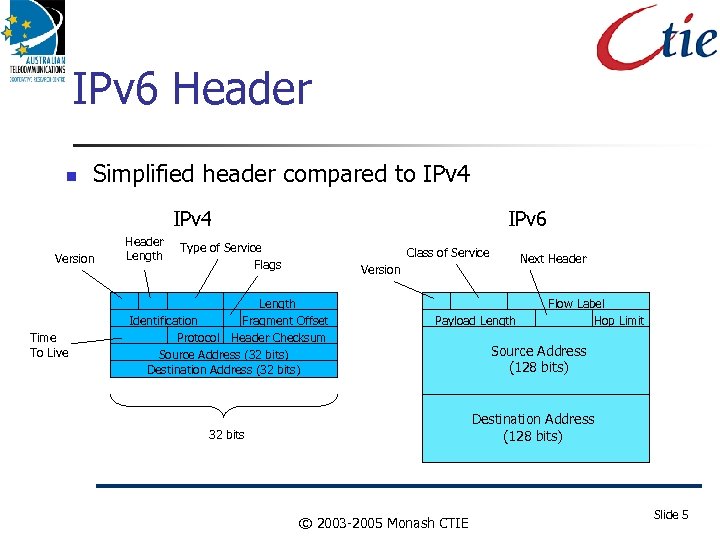 IPv 6 Header Simplified header compared to IPv 4 Version Time To Live Header Length IPv 6 Type of Service Flags Class of Service Next Header Version Length Identification Fragment Offset Protocol Header Checksum Source Address (32 bits) Destination Address (32 bits) Payload Length Flow Label Hop Limit Source Address (128 bits) Destination Address (128 bits) 32 bits © 2003 -2005 Monash CTIE Slide 5
IPv 6 Header Simplified header compared to IPv 4 Version Time To Live Header Length IPv 6 Type of Service Flags Class of Service Next Header Version Length Identification Fragment Offset Protocol Header Checksum Source Address (32 bits) Destination Address (32 bits) Payload Length Flow Label Hop Limit Source Address (128 bits) Destination Address (128 bits) 32 bits © 2003 -2005 Monash CTIE Slide 5
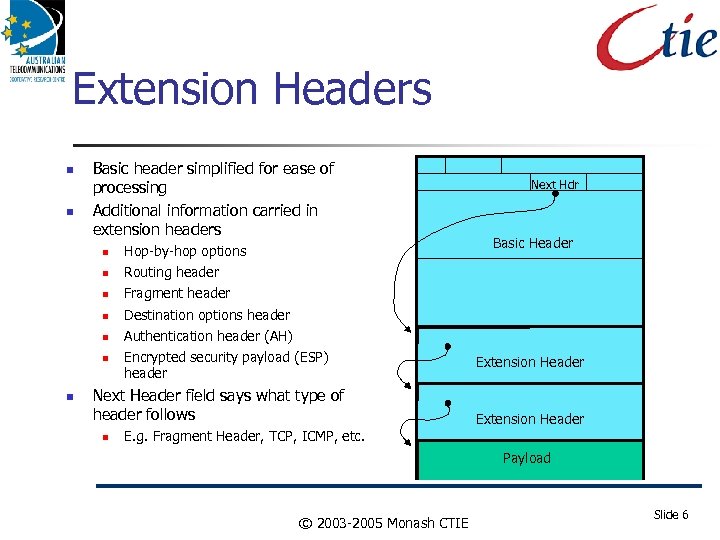 Extension Headers Basic header simplified for ease of processing Additional information carried in extension headers Hop-by-hop options Fragment header Destination options header Authentication header (AH) Basic Header Routing header Next Hdr Encrypted security payload (ESP) header Next Header field says what type of header follows Extension Header E. g. Fragment Header, TCP, ICMP, etc. Payload © 2003 -2005 Monash CTIE Slide 6
Extension Headers Basic header simplified for ease of processing Additional information carried in extension headers Hop-by-hop options Fragment header Destination options header Authentication header (AH) Basic Header Routing header Next Hdr Encrypted security payload (ESP) header Next Header field says what type of header follows Extension Header E. g. Fragment Header, TCP, ICMP, etc. Payload © 2003 -2005 Monash CTIE Slide 6
 ICMPv 6 Same basic concept as ICMP (for IPv 4) Error messages – e. g. : Destination unreachable Packet too big Time exceeded Parameter problem Information messages – e. g. : Echo request/reply Router solicitation/advertisement Multicast Listener Discovery (like IGMP for IPv 4) © 2003 -2005 Monash CTIE Slide 7
ICMPv 6 Same basic concept as ICMP (for IPv 4) Error messages – e. g. : Destination unreachable Packet too big Time exceeded Parameter problem Information messages – e. g. : Echo request/reply Router solicitation/advertisement Multicast Listener Discovery (like IGMP for IPv 4) © 2003 -2005 Monash CTIE Slide 7
 Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 8
Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 8
 Address space 128 bit addresses Massive address space to last for the foreseeable future Default allocation is for all sites to receive 216=65536 subnets Ensures that it is possible to allocate a globally unique address to every host so that end-to-end applications are possible © 2003 -2005 Monash CTIE Slide 9
Address space 128 bit addresses Massive address space to last for the foreseeable future Default allocation is for all sites to receive 216=65536 subnets Ensures that it is possible to allocate a globally unique address to every host so that end-to-end applications are possible © 2003 -2005 Monash CTIE Slide 9
 Address types Unicast Anycast Multicast No more broadcast! © 2003 -2005 Monash CTIE Slide 10
Address types Unicast Anycast Multicast No more broadcast! © 2003 -2005 Monash CTIE Slide 10
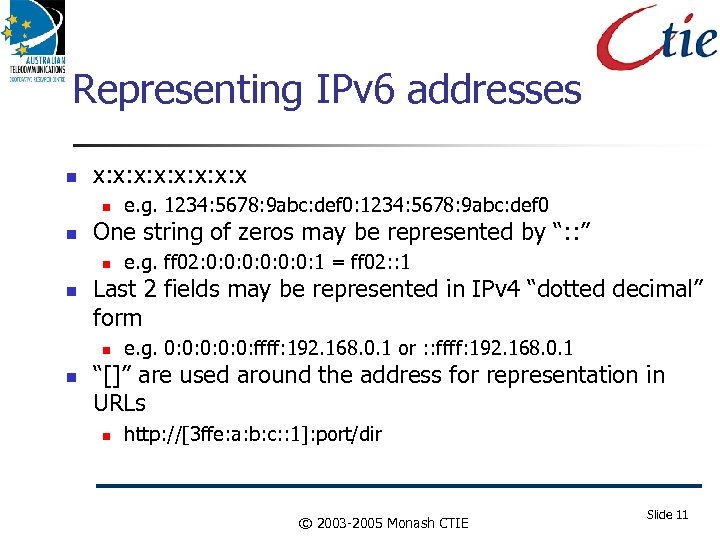 Representing IPv 6 addresses x: x: x One string of zeros may be represented by “: : ” e. g. ff 02: 0: 0: 0: 1 = ff 02: : 1 Last 2 fields may be represented in IPv 4 “dotted decimal” form e. g. 1234: 5678: 9 abc: def 0: 1234: 5678: 9 abc: def 0 e. g. 0: 0: 0: ffff: 192. 168. 0. 1 or : : ffff: 192. 168. 0. 1 “[]” are used around the address for representation in URLs http: //[3 ffe: a: b: c: : 1]: port/dir © 2003 -2005 Monash CTIE Slide 11
Representing IPv 6 addresses x: x: x One string of zeros may be represented by “: : ” e. g. ff 02: 0: 0: 0: 1 = ff 02: : 1 Last 2 fields may be represented in IPv 4 “dotted decimal” form e. g. 1234: 5678: 9 abc: def 0: 1234: 5678: 9 abc: def 0 e. g. 0: 0: 0: ffff: 192. 168. 0. 1 or : : ffff: 192. 168. 0. 1 “[]” are used around the address for representation in URLs http: //[3 ffe: a: b: c: : 1]: port/dir © 2003 -2005 Monash CTIE Slide 11
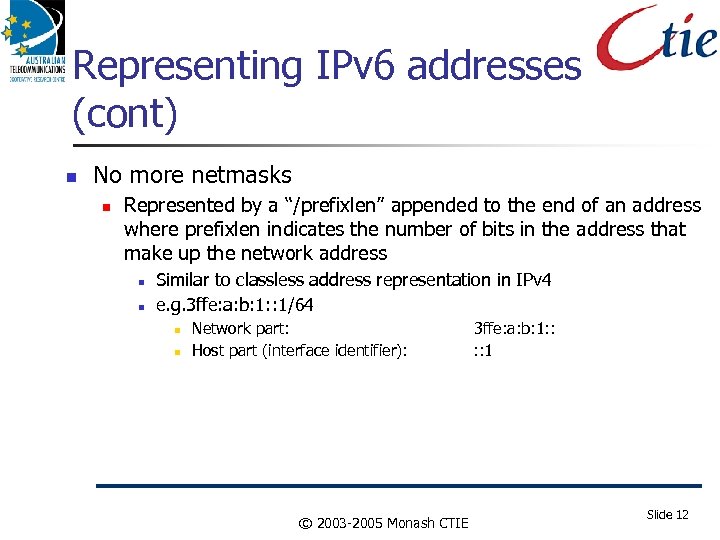 Representing IPv 6 addresses (cont) No more netmasks Represented by a “/prefixlen” appended to the end of an address where prefixlen indicates the number of bits in the address that make up the network address Similar to classless address representation in IPv 4 e. g. 3 ffe: a: b: 1: : 1/64 Network part: Host part (interface identifier): © 2003 -2005 Monash CTIE 3 ffe: a: b: 1: : 1 Slide 12
Representing IPv 6 addresses (cont) No more netmasks Represented by a “/prefixlen” appended to the end of an address where prefixlen indicates the number of bits in the address that make up the network address Similar to classless address representation in IPv 4 e. g. 3 ffe: a: b: 1: : 1/64 Network part: Host part (interface identifier): © 2003 -2005 Monash CTIE 3 ffe: a: b: 1: : 1 Slide 12
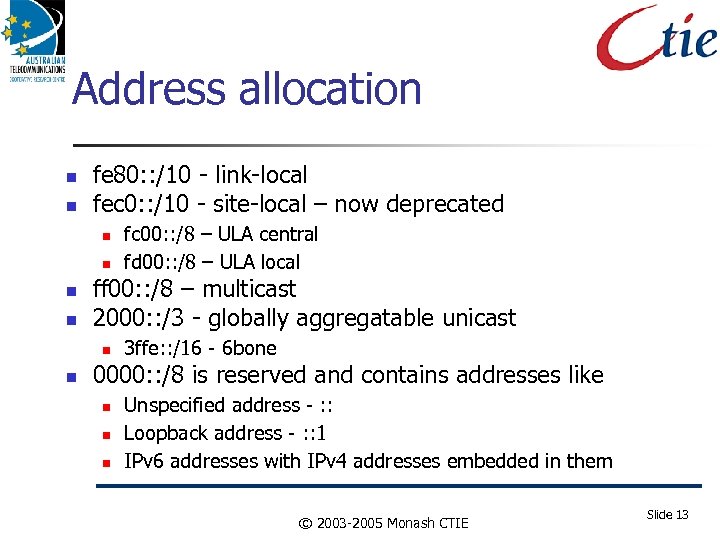 Address allocation fe 80: : /10 - link-local fec 0: : /10 - site-local – now deprecated ff 00: : /8 – multicast 2000: : /3 - globally aggregatable unicast fc 00: : /8 – ULA central fd 00: : /8 – ULA local 3 ffe: : /16 - 6 bone 0000: : /8 is reserved and contains addresses like Unspecified address - : : Loopback address - : : 1 IPv 6 addresses with IPv 4 addresses embedded in them © 2003 -2005 Monash CTIE Slide 13
Address allocation fe 80: : /10 - link-local fec 0: : /10 - site-local – now deprecated ff 00: : /8 – multicast 2000: : /3 - globally aggregatable unicast fc 00: : /8 – ULA central fd 00: : /8 – ULA local 3 ffe: : /16 - 6 bone 0000: : /8 is reserved and contains addresses like Unspecified address - : : Loopback address - : : 1 IPv 6 addresses with IPv 4 addresses embedded in them © 2003 -2005 Monash CTIE Slide 13
 Unicast addressing Associated with an interface rather than a node Several types of unicast addresses Limited scope – link-local, ULA Globally aggregatable Transition – IPv 4 compatible, IPv 4 mapped © 2003 -2005 Monash CTIE Slide 14
Unicast addressing Associated with an interface rather than a node Several types of unicast addresses Limited scope – link-local, ULA Globally aggregatable Transition – IPv 4 compatible, IPv 4 mapped © 2003 -2005 Monash CTIE Slide 14
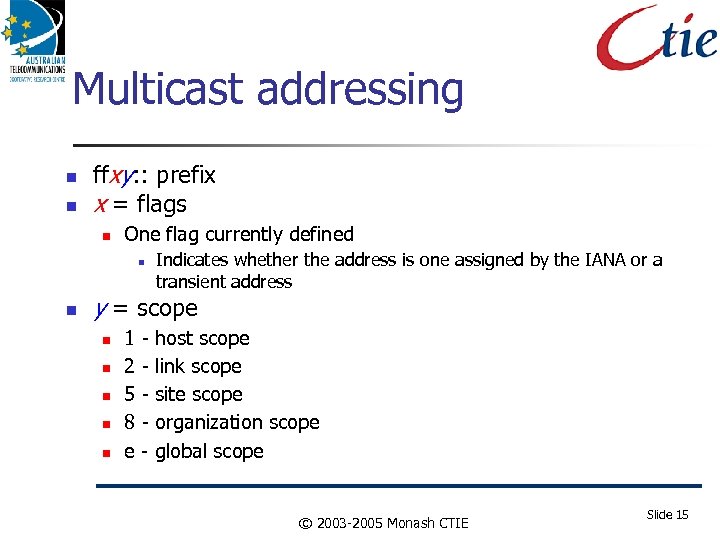 Multicast addressing ffxy: : prefix x = flags One flag currently defined Indicates whether the address is one assigned by the IANA or a transient address y = scope 1 - host scope 2 - link scope 5 - site scope 8 - organization scope e - global scope © 2003 -2005 Monash CTIE Slide 15
Multicast addressing ffxy: : prefix x = flags One flag currently defined Indicates whether the address is one assigned by the IANA or a transient address y = scope 1 - host scope 2 - link scope 5 - site scope 8 - organization scope e - global scope © 2003 -2005 Monash CTIE Slide 15
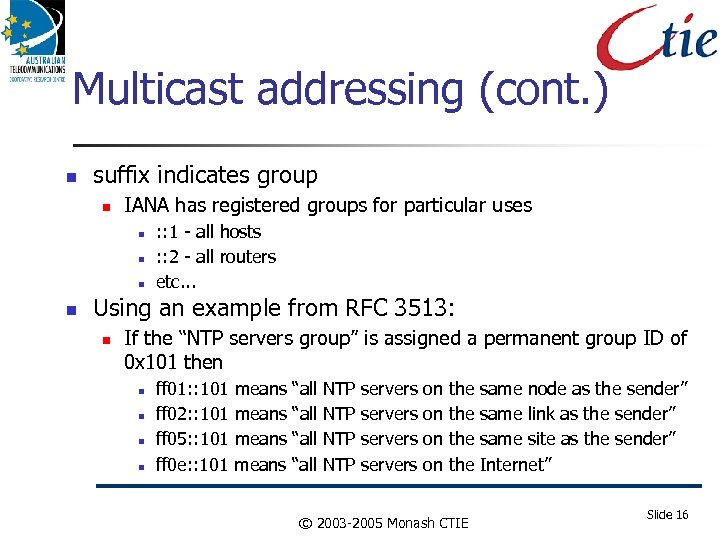 Multicast addressing (cont. ) suffix indicates group IANA has registered groups for particular uses : : 1 - all hosts : : 2 - all routers etc. . . Using an example from RFC 3513: If the “NTP servers group” is assigned a permanent group ID of 0 x 101 then ff 01: : 101 means “all NTP servers on the same node as the sender” ff 02: : 101 means “all NTP servers on the same link as the sender” ff 05: : 101 means “all NTP servers on the same site as the sender” ff 0 e: : 101 means “all NTP servers on the Internet” © 2003 -2005 Monash CTIE Slide 16
Multicast addressing (cont. ) suffix indicates group IANA has registered groups for particular uses : : 1 - all hosts : : 2 - all routers etc. . . Using an example from RFC 3513: If the “NTP servers group” is assigned a permanent group ID of 0 x 101 then ff 01: : 101 means “all NTP servers on the same node as the sender” ff 02: : 101 means “all NTP servers on the same link as the sender” ff 05: : 101 means “all NTP servers on the same site as the sender” ff 0 e: : 101 means “all NTP servers on the Internet” © 2003 -2005 Monash CTIE Slide 16
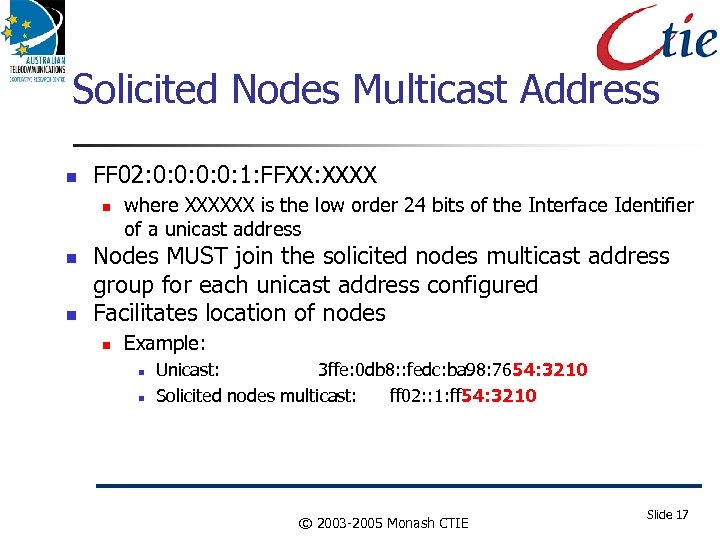 Solicited Nodes Multicast Address FF 02: 0: 0: 1: FFXX: XXXX where XXXXXX is the low order 24 bits of the Interface Identifier of a unicast address Nodes MUST join the solicited nodes multicast address group for each unicast address configured Facilitates location of nodes Example: Unicast: 3 ffe: 0 db 8: : fedc: ba 98: 7654: 3210 Solicited nodes multicast: ff 02: : 1: ff 54: 3210 © 2003 -2005 Monash CTIE Slide 17
Solicited Nodes Multicast Address FF 02: 0: 0: 1: FFXX: XXXX where XXXXXX is the low order 24 bits of the Interface Identifier of a unicast address Nodes MUST join the solicited nodes multicast address group for each unicast address configured Facilitates location of nodes Example: Unicast: 3 ffe: 0 db 8: : fedc: ba 98: 7654: 3210 Solicited nodes multicast: ff 02: : 1: ff 54: 3210 © 2003 -2005 Monash CTIE Slide 17
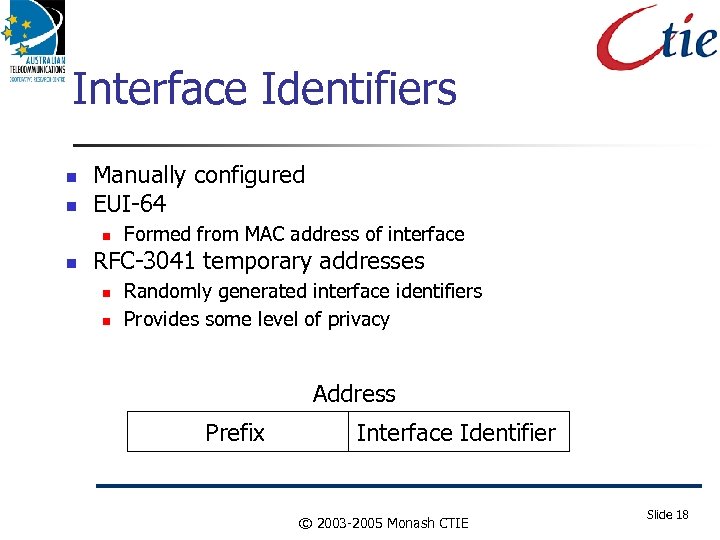 Interface Identifiers Manually configured EUI-64 Formed from MAC address of interface RFC-3041 temporary addresses Randomly generated interface identifiers Provides some level of privacy Address Prefix Interface Identifier © 2003 -2005 Monash CTIE Slide 18
Interface Identifiers Manually configured EUI-64 Formed from MAC address of interface RFC-3041 temporary addresses Randomly generated interface identifiers Provides some level of privacy Address Prefix Interface Identifier © 2003 -2005 Monash CTIE Slide 18
 Address configuration Stateful DHCPv 6 - RFC 3315 Clients use scoped multicast to reach servers and relays May provide information in addition to addresses – e. g. DNS address Stateless Routers send periodic advertisements May also be solicited Hosts use information in advertisements to create valid addresses © 2003 -2005 Monash CTIE Slide 19
Address configuration Stateful DHCPv 6 - RFC 3315 Clients use scoped multicast to reach servers and relays May provide information in addition to addresses – e. g. DNS address Stateless Routers send periodic advertisements May also be solicited Hosts use information in advertisements to create valid addresses © 2003 -2005 Monash CTIE Slide 19
 Router Advertisement RAs are sent periodically and in response to Router Solicitations Contains link prefix, lifetime, MTU, etc. Hosts construct addresses by appending their interface identifier to the prefix advertised by the router This address then needs to be tested to ensure uniqueness © 2003 -2005 Monash CTIE Slide 20
Router Advertisement RAs are sent periodically and in response to Router Solicitations Contains link prefix, lifetime, MTU, etc. Hosts construct addresses by appending their interface identifier to the prefix advertised by the router This address then needs to be tested to ensure uniqueness © 2003 -2005 Monash CTIE Slide 20
 Duplicate Address Detection Multicast is used to assist in detection of conflicting addresses Packets are sent to the solicited nodes multicast address The packet essentially asks if anyone is already using this address If another node responds, the interface either shuts down or tries another address The nature of the multicast address ensures that a host that is using the tested address must be listening, but most other hosts won't be. © 2003 -2005 Monash CTIE Slide 21
Duplicate Address Detection Multicast is used to assist in detection of conflicting addresses Packets are sent to the solicited nodes multicast address The packet essentially asks if anyone is already using this address If another node responds, the interface either shuts down or tries another address The nature of the multicast address ensures that a host that is using the tested address must be listening, but most other hosts won't be. © 2003 -2005 Monash CTIE Slide 21
 Duplicate Address Detection © 2003 -2005 Monash CTIE Slide 22
Duplicate Address Detection © 2003 -2005 Monash CTIE Slide 22
 Link Address Resolution Uses the same packet types as DAD Equivalent of ARP in IPv 4 Neighbour Solicitation message is sent to the solicited nodes multicast address (rather than broadcast as in IPv 4). Host with the destination IP address responds with a Neighbour Advertisement that includes its link layer address. © 2003 -2005 Monash CTIE Slide 23
Link Address Resolution Uses the same packet types as DAD Equivalent of ARP in IPv 4 Neighbour Solicitation message is sent to the solicited nodes multicast address (rather than broadcast as in IPv 4). Host with the destination IP address responds with a Neighbour Advertisement that includes its link layer address. © 2003 -2005 Monash CTIE Slide 23
 Link Address Resolution © 2003 -2005 Monash CTIE Slide 24
Link Address Resolution © 2003 -2005 Monash CTIE Slide 24
 Neighbour Unreachability Detection Hosts maintain a cache of devices they have communicated with recently. The table indicates the reachability state of each host. Neighbour solicitation/advertisement messages are used to probe devices to confirm reachability Not done when it can be confirmed by other information such as TCP three-way handshake Also not initiated just because a device hasn't been heard for some time. Old entries removed © 2003 -2005 Monash CTIE Slide 25
Neighbour Unreachability Detection Hosts maintain a cache of devices they have communicated with recently. The table indicates the reachability state of each host. Neighbour solicitation/advertisement messages are used to probe devices to confirm reachability Not done when it can be confirmed by other information such as TCP three-way handshake Also not initiated just because a device hasn't been heard for some time. Old entries removed © 2003 -2005 Monash CTIE Slide 25
 IPv 6 MTU & PATH MTU Discovery Maximum Transmission Unit (MTU) IPv 6 MTU minimum 1280 bytes (vs. IPv 4 68 bytes) IPv 6 fragmentation end-to-end Routers don’t fragment IPv 6 packets - end nodes do it. Path MTU discovery not mandatory Routers may reply with ICMPv 6 ‘Packet too big’ and drop if packet exceeds router/link MTU. © 2003 -2005 Monash CTIE Slide 26
IPv 6 MTU & PATH MTU Discovery Maximum Transmission Unit (MTU) IPv 6 MTU minimum 1280 bytes (vs. IPv 4 68 bytes) IPv 6 fragmentation end-to-end Routers don’t fragment IPv 6 packets - end nodes do it. Path MTU discovery not mandatory Routers may reply with ICMPv 6 ‘Packet too big’ and drop if packet exceeds router/link MTU. © 2003 -2005 Monash CTIE Slide 26
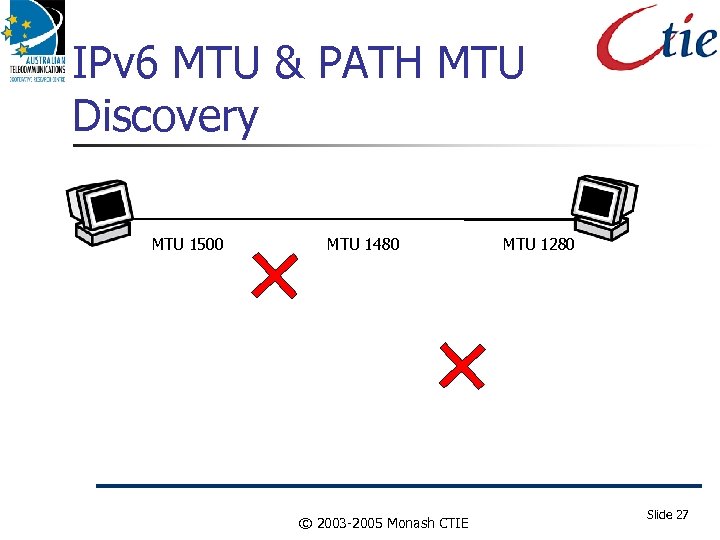 IPv 6 MTU & PATH MTU Discovery MTU 1500 MTU 1480 © 2003 -2005 Monash CTIE MTU 1280 Slide 27
IPv 6 MTU & PATH MTU Discovery MTU 1500 MTU 1480 © 2003 -2005 Monash CTIE MTU 1280 Slide 27
 Summary Huge address space Hosts can autoconfigure their own addresses Scoping allows for some clever use of multicast Neighbour Discovery replaces ARP for address resolution Also introduces new functionality of Stateless address autoconfiguration, DAD, NUD, PMTU discovery © 2003 -2005 Monash CTIE Slide 28
Summary Huge address space Hosts can autoconfigure their own addresses Scoping allows for some clever use of multicast Neighbour Discovery replaces ARP for address resolution Also introduces new functionality of Stateless address autoconfiguration, DAD, NUD, PMTU discovery © 2003 -2005 Monash CTIE Slide 28
 Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 29
Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 29
 Packet switched networks Internet is a packet switched network Each packet contains full addressing information Simple headers for IPv 6 Routing is the process of working out how to send a packet to its destination © 2003 -2005 Monash CTIE Slide 30
Packet switched networks Internet is a packet switched network Each packet contains full addressing information Simple headers for IPv 6 Routing is the process of working out how to send a packet to its destination © 2003 -2005 Monash CTIE Slide 30
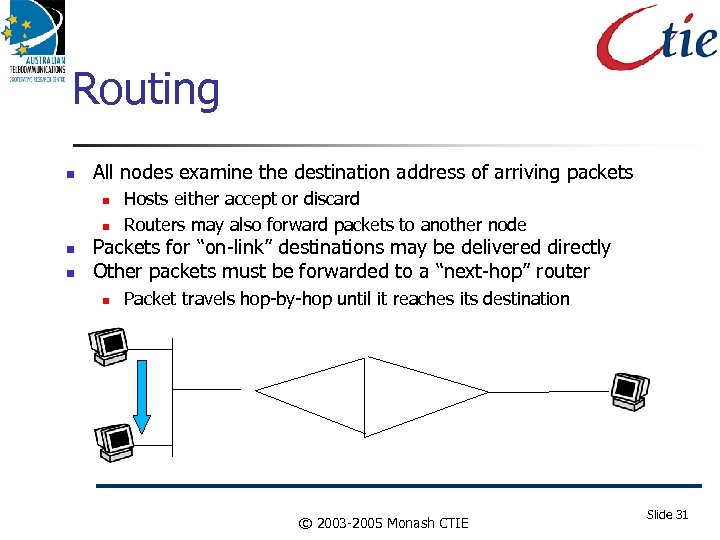 Routing All nodes examine the destination address of arriving packets Hosts either accept or discard Routers may also forward packets to another node Packets for “on-link” destinations may be delivered directly Other packets must be forwarded to a “next-hop” router Packet travels hop-by-hop until it reaches its destination © 2003 -2005 Monash CTIE Slide 31
Routing All nodes examine the destination address of arriving packets Hosts either accept or discard Routers may also forward packets to another node Packets for “on-link” destinations may be delivered directly Other packets must be forwarded to a “next-hop” router Packet travels hop-by-hop until it reaches its destination © 2003 -2005 Monash CTIE Slide 31
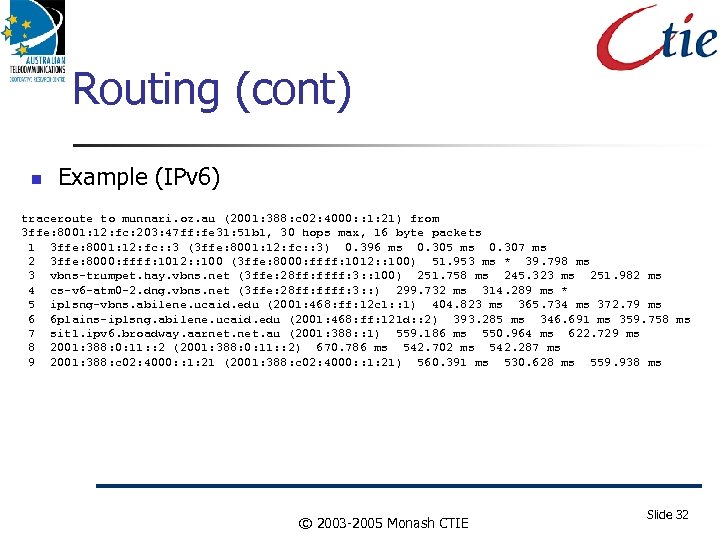 Routing (cont) Example (IPv 6) traceroute to munnari. oz. au (2001: 388: c 02: 4000: : 1: 21) from 3 ffe: 8001: 12: fc: 203: 47 ff: fe 31: 51 b 1, 30 hops max, 16 byte packets 1 3 ffe: 8001: 12: fc: : 3 (3 ffe: 8001: 12: fc: : 3) 0. 396 ms 0. 305 ms 0. 307 ms 2 3 ffe: 8000: ffff: 1012: : 100 (3 ffe: 8000: ffff: 1012: : 100) 51. 953 ms * 39. 798 ms 3 vbns-trumpet. hay. vbns. net (3 ffe: 28 ff: ffff: 3: : 100) 251. 758 ms 245. 323 ms 251. 982 ms 4 cs-v 6 -atm 0 -2. dng. vbns. net (3 ffe: 28 ff: ffff: 3: : ) 299. 732 ms 314. 289 ms * 5 iplsng-vbns. abilene. ucaid. edu (2001: 468: ff: 12 c 1: : 1) 404. 823 ms 365. 734 ms 372. 79 ms 6 6 plains-iplsng. abilene. ucaid. edu (2001: 468: ff: 121 d: : 2) 393. 285 ms 346. 691 ms 359. 758 ms 7 sit 1. ipv 6. broadway. aarnet. au (2001: 388: : 1) 559. 186 ms 550. 964 ms 622. 729 ms 8 2001: 388: 0: 11: : 2 (2001: 388: 0: 11: : 2) 670. 786 ms 542. 702 ms 542. 287 ms 9 2001: 388: c 02: 4000: : 1: 21 (2001: 388: c 02: 4000: : 1: 21) 560. 391 ms 530. 628 ms 559. 938 ms © 2003 -2005 Monash CTIE Slide 32
Routing (cont) Example (IPv 6) traceroute to munnari. oz. au (2001: 388: c 02: 4000: : 1: 21) from 3 ffe: 8001: 12: fc: 203: 47 ff: fe 31: 51 b 1, 30 hops max, 16 byte packets 1 3 ffe: 8001: 12: fc: : 3 (3 ffe: 8001: 12: fc: : 3) 0. 396 ms 0. 305 ms 0. 307 ms 2 3 ffe: 8000: ffff: 1012: : 100 (3 ffe: 8000: ffff: 1012: : 100) 51. 953 ms * 39. 798 ms 3 vbns-trumpet. hay. vbns. net (3 ffe: 28 ff: ffff: 3: : 100) 251. 758 ms 245. 323 ms 251. 982 ms 4 cs-v 6 -atm 0 -2. dng. vbns. net (3 ffe: 28 ff: ffff: 3: : ) 299. 732 ms 314. 289 ms * 5 iplsng-vbns. abilene. ucaid. edu (2001: 468: ff: 12 c 1: : 1) 404. 823 ms 365. 734 ms 372. 79 ms 6 6 plains-iplsng. abilene. ucaid. edu (2001: 468: ff: 121 d: : 2) 393. 285 ms 346. 691 ms 359. 758 ms 7 sit 1. ipv 6. broadway. aarnet. au (2001: 388: : 1) 559. 186 ms 550. 964 ms 622. 729 ms 8 2001: 388: 0: 11: : 2 (2001: 388: 0: 11: : 2) 670. 786 ms 542. 702 ms 542. 287 ms 9 2001: 388: c 02: 4000: : 1: 21 (2001: 388: c 02: 4000: : 1: 21) 560. 391 ms 530. 628 ms 559. 938 ms © 2003 -2005 Monash CTIE Slide 32
 Routing (cont) A router may have many interfaces and/or neighbours How does the router know where to send a packet? Routing table © 2003 -2005 Monash CTIE Slide 33
Routing (cont) A router may have many interfaces and/or neighbours How does the router know where to send a packet? Routing table © 2003 -2005 Monash CTIE Slide 33
 Routing tables Contains information about how to get a packet “closer” to its destination Destination prefix Next hop router Outgoing interface Metric Routing table is consulted for longest matching prefix Packet is forwarded using the information in the routing table entry with the longest matching prefix © 2003 -2005 Monash CTIE Slide 34
Routing tables Contains information about how to get a packet “closer” to its destination Destination prefix Next hop router Outgoing interface Metric Routing table is consulted for longest matching prefix Packet is forwarded using the information in the routing table entry with the longest matching prefix © 2003 -2005 Monash CTIE Slide 34
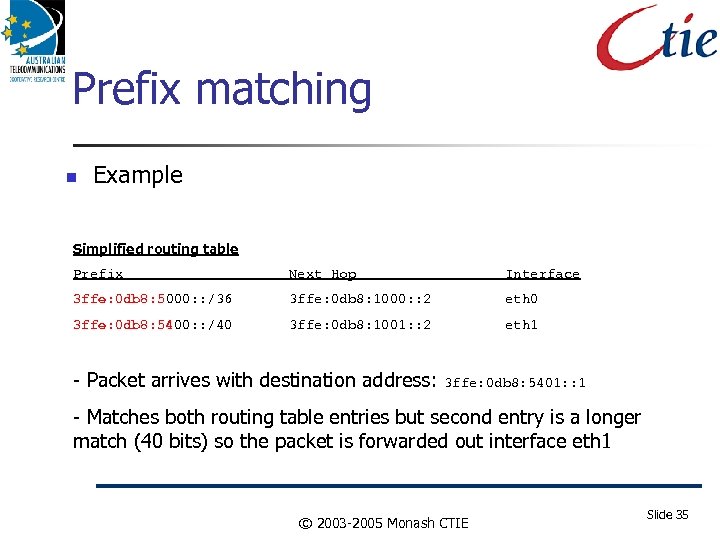 Prefix matching Example Simplified routing table Prefix Next Hop Interface 3 ffe: 0 db 8: 5000: : /36 3 ffe: 0 db 8: 1000: : 2 eth 0 3 ffe: 0 db 8: 5400: : /40 3 ffe: 0 db 8: 1001: : 2 eth 1 - Packet arrives with destination address: 3 ffe: 0 db 8: 5401: : 1 - Matches both routing table entries but second entry is a longer match (40 bits) so the packet is forwarded out interface eth 1 © 2003 -2005 Monash CTIE Slide 35
Prefix matching Example Simplified routing table Prefix Next Hop Interface 3 ffe: 0 db 8: 5000: : /36 3 ffe: 0 db 8: 1000: : 2 eth 0 3 ffe: 0 db 8: 5400: : /40 3 ffe: 0 db 8: 1001: : 2 eth 1 - Packet arrives with destination address: 3 ffe: 0 db 8: 5401: : 1 - Matches both routing table entries but second entry is a longer match (40 bits) so the packet is forwarded out interface eth 1 © 2003 -2005 Monash CTIE Slide 35
 Static vs. Dynamic How is the routing table constructed? Routing table entries may be made by hand Static routes Not scalable Most routing table entries calculated automatically Dynamic routes Routers exchange information with one another Routing protocols © 2003 -2005 Monash CTIE Slide 36
Static vs. Dynamic How is the routing table constructed? Routing table entries may be made by hand Static routes Not scalable Most routing table entries calculated automatically Dynamic routes Routers exchange information with one another Routing protocols © 2003 -2005 Monash CTIE Slide 36
 The Internet “Network of networks” Not practical for every host (or even router) to have a routing table entry for every other host/router in the Internet To make routing tables practical, we need entries that refer to multiple hosts E. g. Default route: 0: : /0 3 ffe: 0 db 8: 1000: : 2 eth 0 “ 0: : /0” will always match and will always be the shortest match This single entry covers every host that we don’t already have another entry for © 2003 -2005 Monash CTIE Slide 37
The Internet “Network of networks” Not practical for every host (or even router) to have a routing table entry for every other host/router in the Internet To make routing tables practical, we need entries that refer to multiple hosts E. g. Default route: 0: : /0 3 ffe: 0 db 8: 1000: : 2 eth 0 “ 0: : /0” will always match and will always be the shortest match This single entry covers every host that we don’t already have another entry for © 2003 -2005 Monash CTIE Slide 37
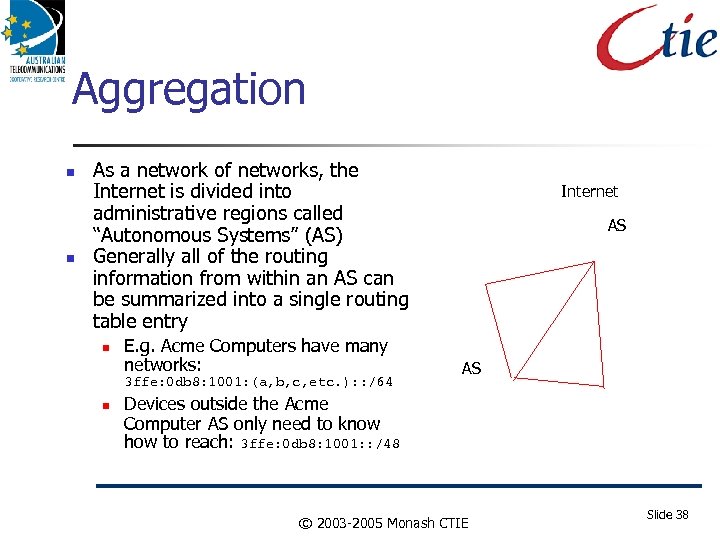 Aggregation As a network of networks, the Internet is divided into administrative regions called “Autonomous Systems” (AS) Generally all of the routing information from within an AS can be summarized into a single routing table entry E. g. Acme Computers have many networks: 3 ffe: 0 db 8: 1001: (a, b, c, etc. ): : /64 Internet AS AS Devices outside the Acme Computer AS only need to know how to reach: 3 ffe: 0 db 8: 1001: : /48 © 2003 -2005 Monash CTIE Slide 38
Aggregation As a network of networks, the Internet is divided into administrative regions called “Autonomous Systems” (AS) Generally all of the routing information from within an AS can be summarized into a single routing table entry E. g. Acme Computers have many networks: 3 ffe: 0 db 8: 1001: (a, b, c, etc. ): : /64 Internet AS AS Devices outside the Acme Computer AS only need to know how to reach: 3 ffe: 0 db 8: 1001: : /48 © 2003 -2005 Monash CTIE Slide 38
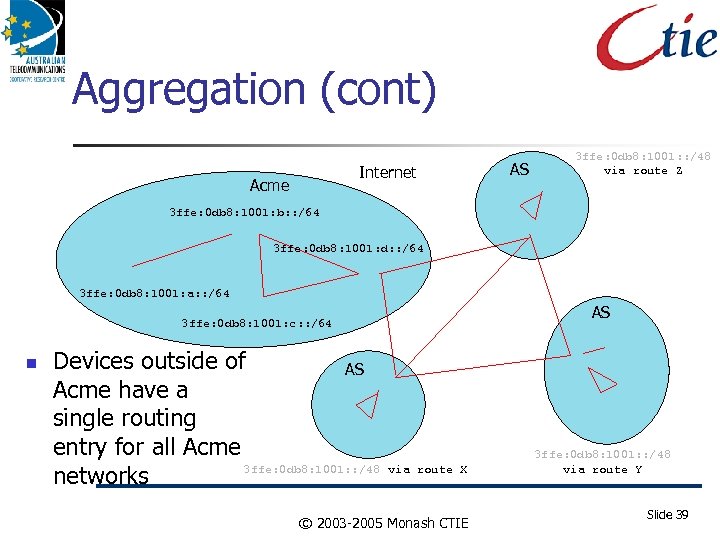 Aggregation (cont) Internet Acme AS 3 ffe: 0 db 8: 1001: : /48 via route Z 3 ffe: 0 db 8: 1001: b: : /64 3 ffe: 0 db 8: 1001: d: : /64 3 ffe: 0 db 8: 1001: a: : /64 AS 3 ffe: 0 db 8: 1001: c: : /64 Devices outside of AS Acme have a single routing entry for all Acme 3 ffe: 0 db 8: 1001: : /48 networks via route X © 2003 -2005 Monash CTIE 3 ffe: 0 db 8: 1001: : /48 via route Y Slide 39
Aggregation (cont) Internet Acme AS 3 ffe: 0 db 8: 1001: : /48 via route Z 3 ffe: 0 db 8: 1001: b: : /64 3 ffe: 0 db 8: 1001: d: : /64 3 ffe: 0 db 8: 1001: a: : /64 AS 3 ffe: 0 db 8: 1001: c: : /64 Devices outside of AS Acme have a single routing entry for all Acme 3 ffe: 0 db 8: 1001: : /48 networks via route X © 2003 -2005 Monash CTIE 3 ffe: 0 db 8: 1001: : /48 via route Y Slide 39
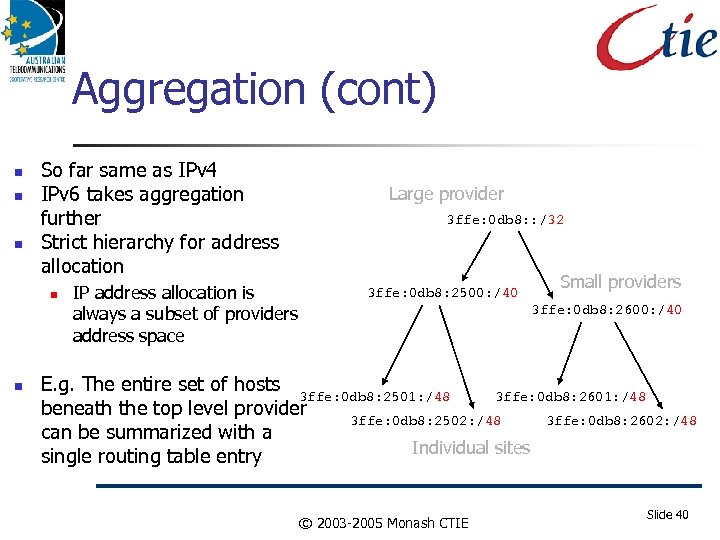 Aggregation (cont) So far same as IPv 4 IPv 6 takes aggregation further Strict hierarchy for address allocation IP address allocation is always a subset of providers address space Large provider 3 ffe: 0 db 8: : /32 3 ffe: 0 db 8: 2500: /40 Small providers 3 ffe: 0 db 8: 2600: /40 E. g. The entire set of hosts 3 ffe: 0 db 8: 2501: /48 3 ffe: 0 db 8: 2601: /48 beneath the top level provider 3 ffe: 0 db 8: 2502: /48 3 ffe: 0 db 8: 2602: /48 can be summarized with a Individual sites single routing table entry © 2003 -2005 Monash CTIE Slide 40
Aggregation (cont) So far same as IPv 4 IPv 6 takes aggregation further Strict hierarchy for address allocation IP address allocation is always a subset of providers address space Large provider 3 ffe: 0 db 8: : /32 3 ffe: 0 db 8: 2500: /40 Small providers 3 ffe: 0 db 8: 2600: /40 E. g. The entire set of hosts 3 ffe: 0 db 8: 2501: /48 3 ffe: 0 db 8: 2601: /48 beneath the top level provider 3 ffe: 0 db 8: 2502: /48 3 ffe: 0 db 8: 2602: /48 can be summarized with a Individual sites single routing table entry © 2003 -2005 Monash CTIE Slide 40
 Threats to Aggregation Provider independent addressing Multihoming Connecting to the Internet through multiple providers Not yet standardized One of the big hurdles in the way of IPv 6 deployment © 2003 -2005 Monash CTIE Slide 41
Threats to Aggregation Provider independent addressing Multihoming Connecting to the Internet through multiple providers Not yet standardized One of the big hurdles in the way of IPv 6 deployment © 2003 -2005 Monash CTIE Slide 41
 Routing Protocols Two types of routing protocols Exterior routing protocols are used to exchange information between ASs Interior, Exterior BGP-4+ Interior routing protocols exchange information with other routers under the same administrative control RIPng, OSPFv 3 © 2003 -2005 Monash CTIE Slide 42
Routing Protocols Two types of routing protocols Exterior routing protocols are used to exchange information between ASs Interior, Exterior BGP-4+ Interior routing protocols exchange information with other routers under the same administrative control RIPng, OSPFv 3 © 2003 -2005 Monash CTIE Slide 42
 Exterior Protocols Communicate with other systems Control routing table sizes Manage policy Use bandwidth efficiently © 2003 -2005 Monash CTIE Slide 43
Exterior Protocols Communicate with other systems Control routing table sizes Manage policy Use bandwidth efficiently © 2003 -2005 Monash CTIE Slide 43
 Interior Protocols Independent of protocols used in other ASs Convey complete routing information with an AS Some protocols allow summarization within an AS OSPF areas Propagate change rapidly © 2003 -2005 Monash CTIE Slide 44
Interior Protocols Independent of protocols used in other ASs Convey complete routing information with an AS Some protocols allow summarization within an AS OSPF areas Propagate change rapidly © 2003 -2005 Monash CTIE Slide 44
 Routing Information Protocol – Next Generation (RIPng) Interior gateway protocol Based on RIP (IPv 4) Distance vector algorithm Limited to networks with no more than 15 hops Routing decisions take into account fixed metrics (usually 1) © 2003 -2005 Monash CTIE Slide 45
Routing Information Protocol – Next Generation (RIPng) Interior gateway protocol Based on RIP (IPv 4) Distance vector algorithm Limited to networks with no more than 15 hops Routing decisions take into account fixed metrics (usually 1) © 2003 -2005 Monash CTIE Slide 45
 Route table Each router maintains a route table Each entry in the table contains: prefix of destination metric equal to sum of metrics along each hop to the destination network IPv 6 address of next hop a flag to indicate recent changes have taken place various timers associated with route © 2003 -2005 Monash CTIE Slide 46
Route table Each router maintains a route table Each entry in the table contains: prefix of destination metric equal to sum of metrics along each hop to the destination network IPv 6 address of next hop a flag to indicate recent changes have taken place various timers associated with route © 2003 -2005 Monash CTIE Slide 46
 Request/response packets UDP used to carry messages Packet format route tag used to separate RIPng routes for network being managed, from those of an external RIPng process that have been imported into the network Responses may be in response to a request packet or may be sent periodically without solicitation Responses contain lists of route table entries for the sender May contain complete or partial tables © 2003 -2005 Monash CTIE Slide 47
Request/response packets UDP used to carry messages Packet format route tag used to separate RIPng routes for network being managed, from those of an external RIPng process that have been imported into the network Responses may be in response to a request packet or may be sent periodically without solicitation Responses contain lists of route table entries for the sender May contain complete or partial tables © 2003 -2005 Monash CTIE Slide 47
 Split horizon Don't advertise routes learned from an interface out that interface Poisoned-reverse Do advertise routes learned from an interface out that interface, but set metric to infinity so that they appear to be unreachable © 2003 -2005 Monash CTIE Slide 48
Split horizon Don't advertise routes learned from an interface out that interface Poisoned-reverse Do advertise routes learned from an interface out that interface, but set metric to infinity so that they appear to be unreachable © 2003 -2005 Monash CTIE Slide 48
 Major Differences from RIP includes a "next hop" entry in each routing table entry (RTE) Due to the length of IPv 6 addresses, RIPng defines a special RTE that contains a next-hop address that applies to all following RTEs until another next-hop RTE is included © 2003 -2005 Monash CTIE Slide 49
Major Differences from RIP includes a "next hop" entry in each routing table entry (RTE) Due to the length of IPv 6 addresses, RIPng defines a special RTE that contains a next-hop address that applies to all following RTEs until another next-hop RTE is included © 2003 -2005 Monash CTIE Slide 49
 Open Shortest Path First (OSPF) Another interior gateway protocol Link state algorithm Version 3 supports IPv 6 © 2003 -2005 Monash CTIE Slide 50
Open Shortest Path First (OSPF) Another interior gateway protocol Link state algorithm Version 3 supports IPv 6 © 2003 -2005 Monash CTIE Slide 50
 Areas Large ASs may be broken up into “Areas” Helps control the amount of traffic used to propagate information © 2003 -2005 Monash CTIE Slide 51
Areas Large ASs may be broken up into “Areas” Helps control the amount of traffic used to propagate information © 2003 -2005 Monash CTIE Slide 51
 Designated routers Uses an election process to pick one router on each link to be “in charge” © 2003 -2005 Monash CTIE Slide 52
Designated routers Uses an election process to pick one router on each link to be “in charge” © 2003 -2005 Monash CTIE Slide 52
 Flooding Link state information is propagated by flooding the entire network Contrast with RIP where information about entire network is passed only to neighbours Link State Advertisements (LSAs) are stored by routers in a “link-state database” Dijkstra’s algorithm used on this database to calculate the shortest path tree and populate the routing table © 2003 -2005 Monash CTIE Slide 53
Flooding Link state information is propagated by flooding the entire network Contrast with RIP where information about entire network is passed only to neighbours Link State Advertisements (LSAs) are stored by routers in a “link-state database” Dijkstra’s algorithm used on this database to calculate the shortest path tree and populate the routing table © 2003 -2005 Monash CTIE Slide 53
 Differences from OSPFv 2 (IPv 4) Protocol processing done per-link rather than per-subnet IP addresses are no longer used in OSPF packets Single links may have multiple IPv 6 subnets and devices on the same link that don't share a subnet may still communicate directly packets carry topology information in the form of router IDs (which are 32 -bit values like IPv 4 addresses and are sometimes represented that way) Flooding scope added to LSAs Link, Area and AS scope © 2003 -2005 Monash CTIE Slide 54
Differences from OSPFv 2 (IPv 4) Protocol processing done per-link rather than per-subnet IP addresses are no longer used in OSPF packets Single links may have multiple IPv 6 subnets and devices on the same link that don't share a subnet may still communicate directly packets carry topology information in the form of router IDs (which are 32 -bit values like IPv 4 addresses and are sometimes represented that way) Flooding scope added to LSAs Link, Area and AS scope © 2003 -2005 Monash CTIE Slide 54
 Differences from OSPFv 2 (IPv 4) (cont) Support for multiple instances of OSPF per link Link-local addresses used for communication between routers where possible Special multicast addresses All. SPFRouters: ff 02: : 5 All. DRouters: ff 02: : 6 Authentication removed from protocol specification OSPF now relies on the IP Authentication Header and IP Encapsulating Security Payload features of IPv 6 to secure the integrity of routing exchanges © 2003 -2005 Monash CTIE Slide 55
Differences from OSPFv 2 (IPv 4) (cont) Support for multiple instances of OSPF per link Link-local addresses used for communication between routers where possible Special multicast addresses All. SPFRouters: ff 02: : 5 All. DRouters: ff 02: : 6 Authentication removed from protocol specification OSPF now relies on the IP Authentication Header and IP Encapsulating Security Payload features of IPv 6 to secure the integrity of routing exchanges © 2003 -2005 Monash CTIE Slide 55
 Border Gateway Protocol (BGP) Exterior gateway protocol that allows routing information to be exchanged between autonomous systems (ASs) sufficient to determine reachability and eliminate routing loops. © 2003 -2005 Monash CTIE Slide 56
Border Gateway Protocol (BGP) Exterior gateway protocol that allows routing information to be exchanged between autonomous systems (ASs) sufficient to determine reachability and eliminate routing loops. © 2003 -2005 Monash CTIE Slide 56
 BGP Peers Information is exchanged between pairs of routers called BGP peers Information carried using TCP Small “keep alive” packets keep the TCP session from timing out. © 2003 -2005 Monash CTIE Slide 57
BGP Peers Information is exchanged between pairs of routers called BGP peers Information carried using TCP Small “keep alive” packets keep the TCP session from timing out. © 2003 -2005 Monash CTIE Slide 57
 BGP routes Contains “Network Layer Reachability Information” (NLRI) plus “path attributes” Next Hop AS path Routing decisions may be based on the attributes Policies are used to determine which routes are sent to a peer and which routes will be accepted © 2003 -2005 Monash CTIE Slide 58
BGP routes Contains “Network Layer Reachability Information” (NLRI) plus “path attributes” Next Hop AS path Routing decisions may be based on the attributes Policies are used to determine which routes are sent to a peer and which routes will be accepted © 2003 -2005 Monash CTIE Slide 58
 Updates Entire routing table exchanged when peering first established Because TCP is used, only changes need to be transmitted after that Efficient use of bandwidth (compared to IGPs) Routes may added, deleted or modified Routing loops are avoided by examining the AS path © 2003 -2005 Monash CTIE Slide 59
Updates Entire routing table exchanged when peering first established Because TCP is used, only changes need to be transmitted after that Efficient use of bandwidth (compared to IGPs) Routes may added, deleted or modified Routing loops are avoided by examining the AS path © 2003 -2005 Monash CTIE Slide 59
 Supporting IPv 6 BGP-4+ contains extensions for supporting network protocols other than IPv 4 BGP Identifier is still an IPv 4 address Very little required in order to support IPv 6 -only routers still need an IPv 4 address to run BGP New attribute defined that carries both the IPv 6 NLRI as well as the next hop Next hop attribute is not used (v 4 only) © 2003 -2005 Monash CTIE Slide 60
Supporting IPv 6 BGP-4+ contains extensions for supporting network protocols other than IPv 4 BGP Identifier is still an IPv 4 address Very little required in order to support IPv 6 -only routers still need an IPv 4 address to run BGP New attribute defined that carries both the IPv 6 NLRI as well as the next hop Next hop attribute is not used (v 4 only) © 2003 -2005 Monash CTIE Slide 60
 Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 61
Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 61
 DNS - Domain Name System DNS translates “fully qualified domain names” like: Into IP addresses like: www. ctie. monash. edu. au 130. 194. 137. 141 or 2001: 388: 608 c: fc: 205: 5 dff: fe 00: 9 e 3 a DNS servers hold records associating names to IP numbers Applications use DNS Client (resolver) to access the records Each DNS entry contains multiple record types (RR) and information No modification required to support IPv 6 addresses in the DNS system Newer DNS software supports both IPv 4 and IPv 6 access © 2003 -2005 Monash CTIE Slide 62
DNS - Domain Name System DNS translates “fully qualified domain names” like: Into IP addresses like: www. ctie. monash. edu. au 130. 194. 137. 141 or 2001: 388: 608 c: fc: 205: 5 dff: fe 00: 9 e 3 a DNS servers hold records associating names to IP numbers Applications use DNS Client (resolver) to access the records Each DNS entry contains multiple record types (RR) and information No modification required to support IPv 6 addresses in the DNS system Newer DNS software supports both IPv 4 and IPv 6 access © 2003 -2005 Monash CTIE Slide 62
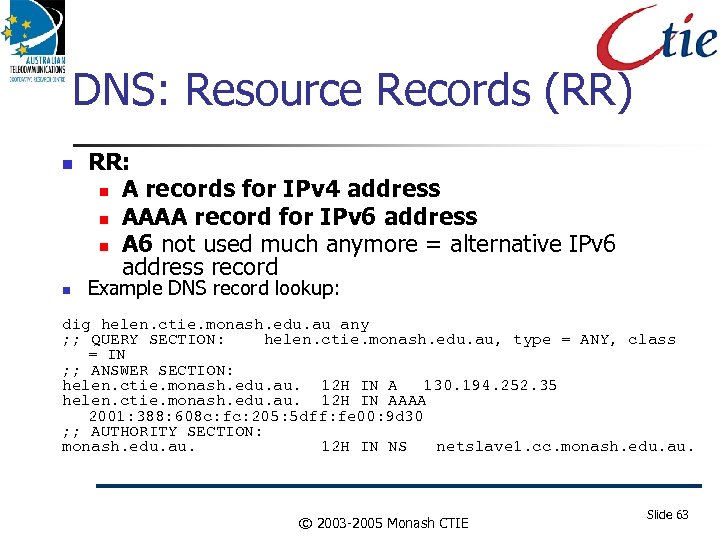 DNS: Resource Records (RR) RR: A records for IPv 4 address AAAA record for IPv 6 address A 6 not used much anymore = alternative IPv 6 address record Example DNS record lookup: dig helen. ctie. monash. edu. au any ; ; QUERY SECTION: helen. ctie. monash. edu. au, type = ANY, class = IN ; ; ANSWER SECTION: helen. ctie. monash. edu. au. 12 H IN A 130. 194. 252. 35 helen. ctie. monash. edu. au. 12 H IN AAAA 2001: 388: 608 c: fc: 205: 5 dff: fe 00: 9 d 30 ; ; AUTHORITY SECTION: monash. edu. au. 12 H IN NS netslave 1. cc. monash. edu. au. © 2003 -2005 Monash CTIE Slide 63
DNS: Resource Records (RR) RR: A records for IPv 4 address AAAA record for IPv 6 address A 6 not used much anymore = alternative IPv 6 address record Example DNS record lookup: dig helen. ctie. monash. edu. au any ; ; QUERY SECTION: helen. ctie. monash. edu. au, type = ANY, class = IN ; ; ANSWER SECTION: helen. ctie. monash. edu. au. 12 H IN A 130. 194. 252. 35 helen. ctie. monash. edu. au. 12 H IN AAAA 2001: 388: 608 c: fc: 205: 5 dff: fe 00: 9 d 30 ; ; AUTHORITY SECTION: monash. edu. au. 12 H IN NS netslave 1. cc. monash. edu. au. © 2003 -2005 Monash CTIE Slide 63
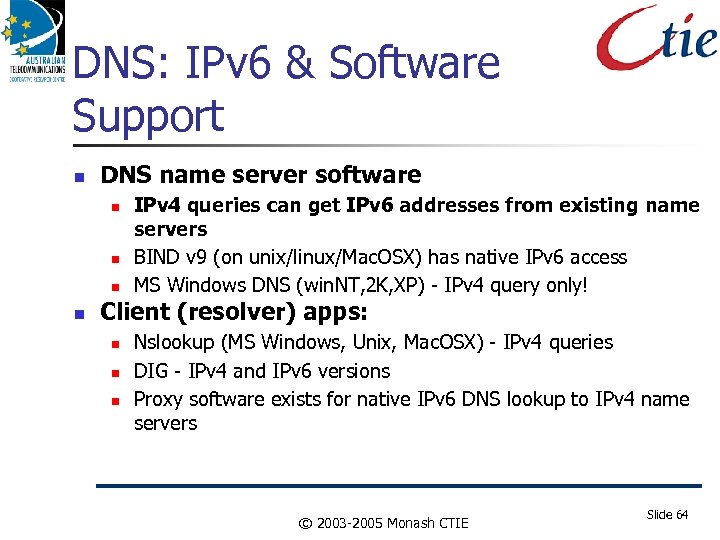 DNS: IPv 6 & Software Support DNS name server software IPv 4 queries can get IPv 6 addresses from existing name servers BIND v 9 (on unix/linux/Mac. OSX) has native IPv 6 access MS Windows DNS (win. NT, 2 K, XP) - IPv 4 query only! Client (resolver) apps: Nslookup (MS Windows, Unix, Mac. OSX) - IPv 4 queries DIG - IPv 4 and IPv 6 versions Proxy software exists for native IPv 6 DNS lookup to IPv 4 name servers © 2003 -2005 Monash CTIE Slide 64
DNS: IPv 6 & Software Support DNS name server software IPv 4 queries can get IPv 6 addresses from existing name servers BIND v 9 (on unix/linux/Mac. OSX) has native IPv 6 access MS Windows DNS (win. NT, 2 K, XP) - IPv 4 query only! Client (resolver) apps: Nslookup (MS Windows, Unix, Mac. OSX) - IPv 4 queries DIG - IPv 4 and IPv 6 versions Proxy software exists for native IPv 6 DNS lookup to IPv 4 name servers © 2003 -2005 Monash CTIE Slide 64
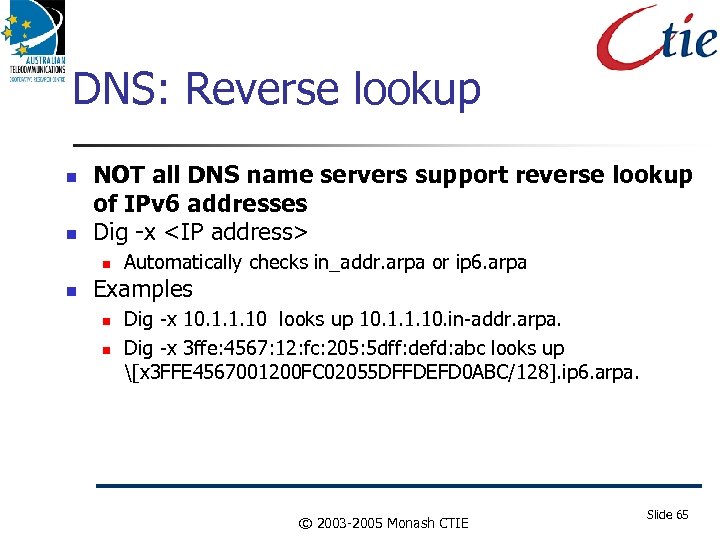 DNS: Reverse lookup NOT all DNS name servers support reverse lookup of IPv 6 addresses Dig -x
DNS: Reverse lookup NOT all DNS name servers support reverse lookup of IPv 6 addresses Dig -x
 Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 66
Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 66
 IPv 4 to IPv 6 Transition Strategies and mechanisms: The problem: IPv 4 to IPv 6 transition is gradual IPv 6 devices need to communicate to IPv 4 IPv 6 needs to communicate over IPv 4 links The solutions: Dual Stack (IPv 4, IPv 6) Routers and workstations Tunnels Protocol Translations and Application specific gateways RFC 2893 Transition Mechanisms for IPv 6 Hosts and Routers © 2003 -2005 Monash CTIE Slide 67
IPv 4 to IPv 6 Transition Strategies and mechanisms: The problem: IPv 4 to IPv 6 transition is gradual IPv 6 devices need to communicate to IPv 4 IPv 6 needs to communicate over IPv 4 links The solutions: Dual Stack (IPv 4, IPv 6) Routers and workstations Tunnels Protocol Translations and Application specific gateways RFC 2893 Transition Mechanisms for IPv 6 Hosts and Routers © 2003 -2005 Monash CTIE Slide 67
 Dual Stack Dual Stack (IPv 4, IPv 6) Routers and workstations Application doesn’t really need to know what the transport is. Can communicate to both IPv 4 and IPv 6 © 2003 -2005 Monash CTIE Slide 68
Dual Stack Dual Stack (IPv 4, IPv 6) Routers and workstations Application doesn’t really need to know what the transport is. Can communicate to both IPv 4 and IPv 6 © 2003 -2005 Monash CTIE Slide 68
 Dual Stack (cont) Applications on dual stack hosts: For applications that only support IPv 4 - use IPv 4 only For applications that support IPv 6: If DNS lookup of destination resolves address to IPv 4 destination, use IPv 4 If DNS resolves address to IPv 6 destination use IPv 6 Routers – send traffic based on IP type, and routing rules © 2003 -2005 Monash CTIE Slide 69
Dual Stack (cont) Applications on dual stack hosts: For applications that only support IPv 4 - use IPv 4 only For applications that support IPv 6: If DNS lookup of destination resolves address to IPv 4 destination, use IPv 4 If DNS resolves address to IPv 6 destination use IPv 6 Routers – send traffic based on IP type, and routing rules © 2003 -2005 Monash CTIE Slide 69
 IPv 4 -mapped addresses IPv 4 Mapped addresses --> IPv 6 node to IPv 4 node Used by IPv 6 applications for internal representation of IPv 4 addresses IPv 6 node communicates directly (via dual stack) to IPv 4 address 80 bits 0, 16 bits 1, 32 bits of IPv 4 address on the end 0: 0: 0: FFFF: 192. 17. 1. 42 : : FFFF: c 0 a 7: abcd © 2003 -2005 Monash CTIE Slide 70
IPv 4 -mapped addresses IPv 4 Mapped addresses --> IPv 6 node to IPv 4 node Used by IPv 6 applications for internal representation of IPv 4 addresses IPv 6 node communicates directly (via dual stack) to IPv 4 address 80 bits 0, 16 bits 1, 32 bits of IPv 4 address on the end 0: 0: 0: FFFF: 192. 17. 1. 42 : : FFFF: c 0 a 7: abcd © 2003 -2005 Monash CTIE Slide 70
 IPv 4 compatible addresses IPv 4 compatible addresses represent an IPv 6 node without having a real IPv 6 address IPv 6 node communicates directly (via dual stack) to IPv 4 addresses 96 bits 0, 32 bits of IPv 4 address on the end 0: 0: 0: 192. 17. 1. 42 : : c 0 a 7: abcd Used by tunneling protocols like 6 to 4 Can’t use IPv 6 stateless address autoconfiguration – requires preconfigured IPv 4 address for node. © 2003 -2005 Monash CTIE Slide 71
IPv 4 compatible addresses IPv 4 compatible addresses represent an IPv 6 node without having a real IPv 6 address IPv 6 node communicates directly (via dual stack) to IPv 4 addresses 96 bits 0, 32 bits of IPv 4 address on the end 0: 0: 0: 192. 17. 1. 42 : : c 0 a 7: abcd Used by tunneling protocols like 6 to 4 Can’t use IPv 6 stateless address autoconfiguration – requires preconfigured IPv 4 address for node. © 2003 -2005 Monash CTIE Slide 71
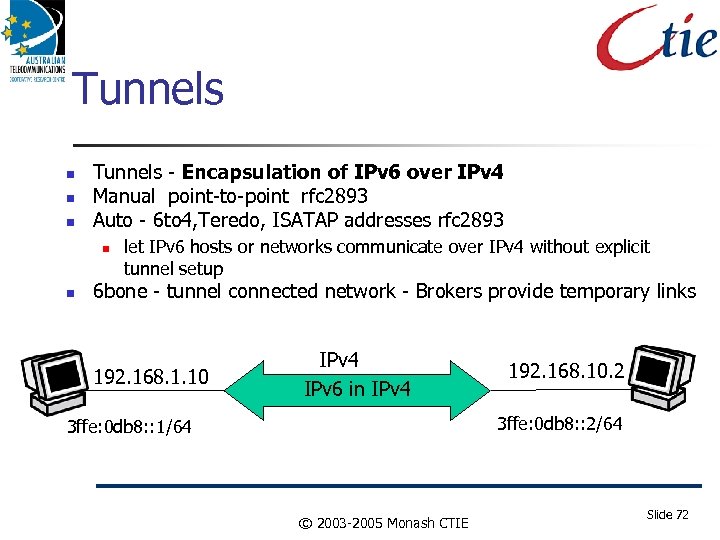 Tunnels - Encapsulation of IPv 6 over IPv 4 Manual point-to-point rfc 2893 Auto - 6 to 4, Teredo, ISATAP addresses rfc 2893 let IPv 6 hosts or networks communicate over IPv 4 without explicit tunnel setup 6 bone - tunnel connected network - Brokers provide temporary links 192. 168. 1. 10 IPv 4 IPv 6 in IPv 4 192. 168. 10. 2 3 ffe: 0 db 8: : 2/64 3 ffe: 0 db 8: : 1/64 © 2003 -2005 Monash CTIE Slide 72
Tunnels - Encapsulation of IPv 6 over IPv 4 Manual point-to-point rfc 2893 Auto - 6 to 4, Teredo, ISATAP addresses rfc 2893 let IPv 6 hosts or networks communicate over IPv 4 without explicit tunnel setup 6 bone - tunnel connected network - Brokers provide temporary links 192. 168. 1. 10 IPv 4 IPv 6 in IPv 4 192. 168. 10. 2 3 ffe: 0 db 8: : 2/64 3 ffe: 0 db 8: : 1/64 © 2003 -2005 Monash CTIE Slide 72
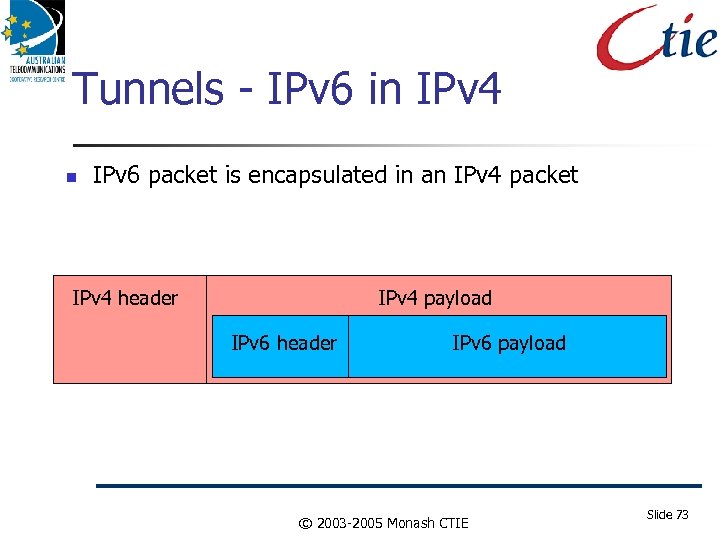 Tunnels - IPv 6 in IPv 4 IPv 6 packet is encapsulated in an IPv 4 packet IPv 4 header IPv 4 payload IPv 6 header IPv 6 payload © 2003 -2005 Monash CTIE Slide 73
Tunnels - IPv 6 in IPv 4 IPv 6 packet is encapsulated in an IPv 4 packet IPv 4 header IPv 4 payload IPv 6 header IPv 6 payload © 2003 -2005 Monash CTIE Slide 73
 Tunnels - IPv 6 in IPv 4 tunnel appears as a single hop to the IPv 6 nodes The MTU decreases by the IPv 4 header size (20 bytes) Tunnel types: Router-Router Node-Node Node-Router Tunnel configuration - manual (mainly for point to point), automatic, tunnel broker (as per 6 bone - for occasional use) © 2003 -2005 Monash CTIE Slide 74
Tunnels - IPv 6 in IPv 4 tunnel appears as a single hop to the IPv 6 nodes The MTU decreases by the IPv 4 header size (20 bytes) Tunnel types: Router-Router Node-Node Node-Router Tunnel configuration - manual (mainly for point to point), automatic, tunnel broker (as per 6 bone - for occasional use) © 2003 -2005 Monash CTIE Slide 74
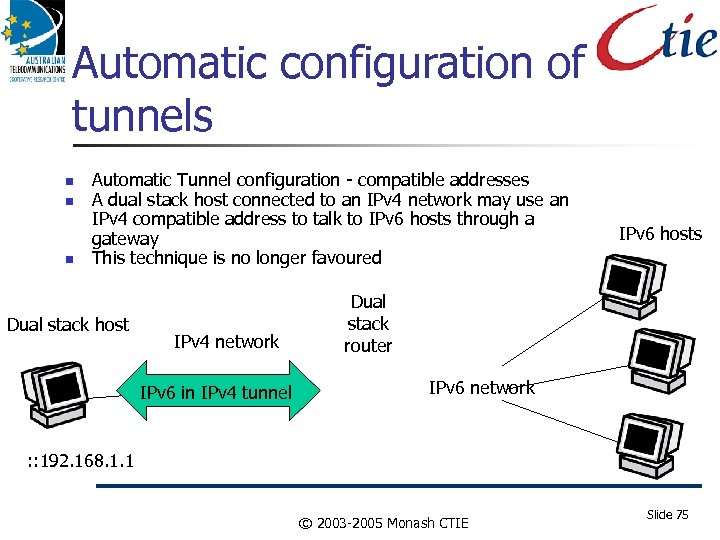 Automatic configuration of tunnels Automatic Tunnel configuration - compatible addresses A dual stack host connected to an IPv 4 network may use an IPv 4 compatible address to talk to IPv 6 hosts through a gateway This technique is no longer favoured Dual stack host IPv 4 network IPv 6 in IPv 4 tunnel IPv 6 hosts Dual stack router IPv 6 network : : 192. 168. 1. 1 © 2003 -2005 Monash CTIE Slide 75
Automatic configuration of tunnels Automatic Tunnel configuration - compatible addresses A dual stack host connected to an IPv 4 network may use an IPv 4 compatible address to talk to IPv 6 hosts through a gateway This technique is no longer favoured Dual stack host IPv 4 network IPv 6 in IPv 4 tunnel IPv 6 hosts Dual stack router IPv 6 network : : 192. 168. 1. 1 © 2003 -2005 Monash CTIE Slide 75
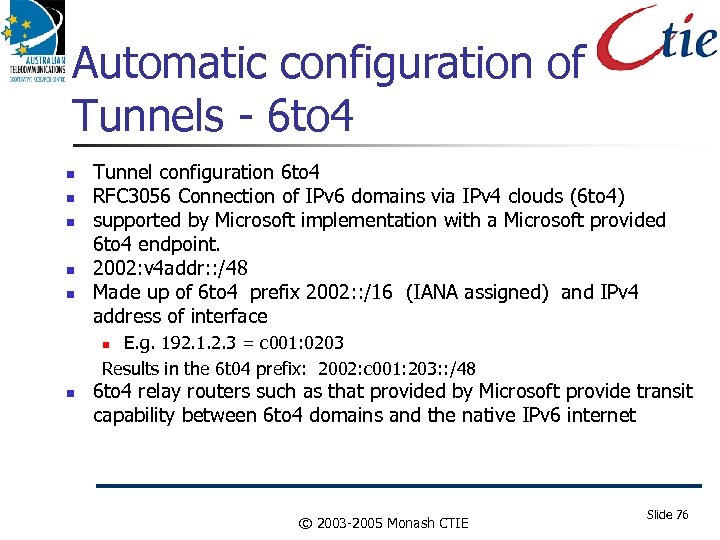 Automatic configuration of Tunnels - 6 to 4 Tunnel configuration 6 to 4 RFC 3056 Connection of IPv 6 domains via IPv 4 clouds (6 to 4) supported by Microsoft implementation with a Microsoft provided 6 to 4 endpoint. 2002: v 4 addr: : /48 Made up of 6 to 4 prefix 2002: : /16 (IANA assigned) and IPv 4 address of interface E. g. 192. 1. 2. 3 = c 001: 0203 Results in the 6 t 04 prefix: 2002: c 001: 203: : /48 6 to 4 relay routers such as that provided by Microsoft provide transit capability between 6 to 4 domains and the native IPv 6 internet © 2003 -2005 Monash CTIE Slide 76
Automatic configuration of Tunnels - 6 to 4 Tunnel configuration 6 to 4 RFC 3056 Connection of IPv 6 domains via IPv 4 clouds (6 to 4) supported by Microsoft implementation with a Microsoft provided 6 to 4 endpoint. 2002: v 4 addr: : /48 Made up of 6 to 4 prefix 2002: : /16 (IANA assigned) and IPv 4 address of interface E. g. 192. 1. 2. 3 = c 001: 0203 Results in the 6 t 04 prefix: 2002: c 001: 203: : /48 6 to 4 relay routers such as that provided by Microsoft provide transit capability between 6 to 4 domains and the native IPv 6 internet © 2003 -2005 Monash CTIE Slide 76
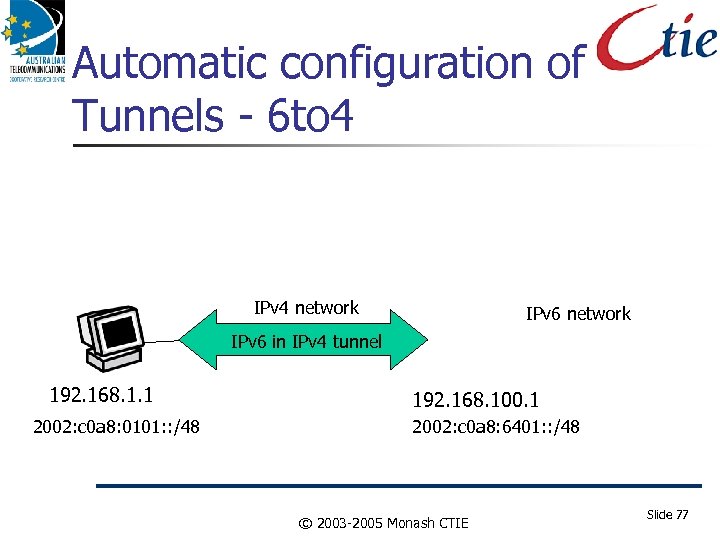 Automatic configuration of Tunnels - 6 to 4 IPv 4 network IPv 6 in IPv 4 tunnel 192. 168. 1. 1 2002: c 0 a 8: 0101: : /48 192. 168. 100. 1 2002: c 0 a 8: 6401: : /48 © 2003 -2005 Monash CTIE Slide 77
Automatic configuration of Tunnels - 6 to 4 IPv 4 network IPv 6 in IPv 4 tunnel 192. 168. 1. 1 2002: c 0 a 8: 0101: : /48 192. 168. 100. 1 2002: c 0 a 8: 6401: : /48 © 2003 -2005 Monash CTIE Slide 77
 IPv 4 to IPv 6 Transition. Protocol Translation NAT updated for IPv 6 NAT-PT Protocol Translation additions for IPv 6 variations Header field changes, meaning of fields change. Application specific gateways SIIT DNS FTP protocol has addresses embedded in the messages - need translation at the gateway device [NAT-PT specifies this]. © 2003 -2005 Monash CTIE Slide 78
IPv 4 to IPv 6 Transition. Protocol Translation NAT updated for IPv 6 NAT-PT Protocol Translation additions for IPv 6 variations Header field changes, meaning of fields change. Application specific gateways SIIT DNS FTP protocol has addresses embedded in the messages - need translation at the gateway device [NAT-PT specifies this]. © 2003 -2005 Monash CTIE Slide 78
 NAT-PT and ALG’s NAT-PT and NAPT-PT. Network Address Translation updated for IPv 6 NAT-PT, NAPT-PT translate protocols (e. g. : ICMP) as well as addresses They define Application Layer Gateways as well (nat-pt specifies FTP, DNS ALG’s as well as protocol translations) E. g. : NAT-PT translates ICMPv 6 ‘path too big’ message into IPv 4 ICMP equivalent Introduces single point of failure device in the network. May not be possible for all ICMPv 6 packets © 2003 -2005 Monash CTIE Slide 79
NAT-PT and ALG’s NAT-PT and NAPT-PT. Network Address Translation updated for IPv 6 NAT-PT, NAPT-PT translate protocols (e. g. : ICMP) as well as addresses They define Application Layer Gateways as well (nat-pt specifies FTP, DNS ALG’s as well as protocol translations) E. g. : NAT-PT translates ICMPv 6 ‘path too big’ message into IPv 4 ICMP equivalent Introduces single point of failure device in the network. May not be possible for all ICMPv 6 packets © 2003 -2005 Monash CTIE Slide 79
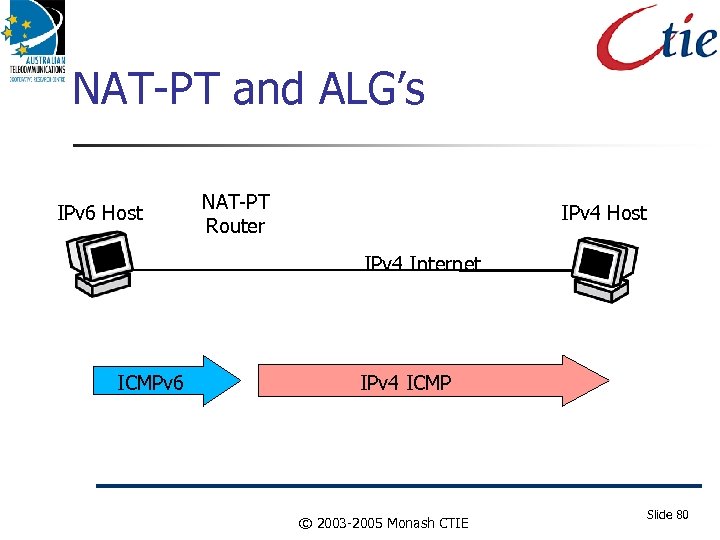 NAT-PT and ALG’s IPv 6 Host NAT-PT Router IPv 4 Host IPv 4 Internet ICMPv 6 IPv 4 ICMP © 2003 -2005 Monash CTIE Slide 80
NAT-PT and ALG’s IPv 6 Host NAT-PT Router IPv 4 Host IPv 4 Internet ICMPv 6 IPv 4 ICMP © 2003 -2005 Monash CTIE Slide 80
 NAT-PT and NAPT-PT NAT-PT Network Address Translation – Protocol Translation NAPT-PT Network Address Port Translation-protocol translation NAT-PT uses a pool of IPv 4 addresses – allocates one per IPv 6 address. NAPT translates ports as well as addresses. This allows single IPv 4 address to represent multiple IPv 6 addresses Stateful address/header translations as per SIIT © 2003 -2005 Monash CTIE Slide 81
NAT-PT and NAPT-PT NAT-PT Network Address Translation – Protocol Translation NAPT-PT Network Address Port Translation-protocol translation NAT-PT uses a pool of IPv 4 addresses – allocates one per IPv 6 address. NAPT translates ports as well as addresses. This allows single IPv 4 address to represent multiple IPv 6 addresses Stateful address/header translations as per SIIT © 2003 -2005 Monash CTIE Slide 81
 SIIT RFC: 2765 Stateless IP/ICMP Translation Algorithm (SIIT) Allows IPv 6 only nodes to communicate to IPv 4 nodes Uses boxes on network to do stateless translation of IP/ICMP Translates packet headers from IPv 4 to IPv 6 mapped or translated addresses Must generate appropriate header entries (e. g. : checksums) for protocol Rewrites ICMP error message as they contain IP addresses embedded Requires IPv 4 allocation mechanism for the IPv 6 node and also tunnel/routing configuration © 2003 -2005 Monash CTIE Slide 82
SIIT RFC: 2765 Stateless IP/ICMP Translation Algorithm (SIIT) Allows IPv 6 only nodes to communicate to IPv 4 nodes Uses boxes on network to do stateless translation of IP/ICMP Translates packet headers from IPv 4 to IPv 6 mapped or translated addresses Must generate appropriate header entries (e. g. : checksums) for protocol Rewrites ICMP error message as they contain IP addresses embedded Requires IPv 4 allocation mechanism for the IPv 6 node and also tunnel/routing configuration © 2003 -2005 Monash CTIE Slide 82
 Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 83
Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 83
 Contents IPv 4 and IPv 6 Security Attacks against Internetworks IPv 6 Security Issues. IPv 6 Security features. © 2003 -2005 Monash CTIE Slide 84
Contents IPv 4 and IPv 6 Security Attacks against Internetworks IPv 6 Security Issues. IPv 6 Security features. © 2003 -2005 Monash CTIE Slide 84
 IPv 4 and IPv 6 Security Weaknesses of IPv 4 security IPv 6 Security Inherits from IPv 4 Trust of received packet information (spoofing) Host-to-host security not widely available Packet service, can insert packets Ingress filtering will be incomplete Many of the IPv 4 applications will be in IPv 6 (email, web) IPv 6 Built with security in mind IPv 6 aims to be 'no worse than IPv 4' IP Security Protocols (All hosts support IPSec) New Internet applications specified with security in mind © 2003 -2005 Monash CTIE Slide 85
IPv 4 and IPv 6 Security Weaknesses of IPv 4 security IPv 6 Security Inherits from IPv 4 Trust of received packet information (spoofing) Host-to-host security not widely available Packet service, can insert packets Ingress filtering will be incomplete Many of the IPv 4 applications will be in IPv 6 (email, web) IPv 6 Built with security in mind IPv 6 aims to be 'no worse than IPv 4' IP Security Protocols (All hosts support IPSec) New Internet applications specified with security in mind © 2003 -2005 Monash CTIE Slide 85
 Attacks against Internetworks Do. S attacks Hijack Attacks Packet forgery Man In the Middle Theft of service/Qo. S. Impersonation Attacks against resources (Server, Link, Qo. S) Snooping Data Insertion/Deletion Host Intrusion Worms and Viruses (Application Issue!) This may not get better under IPv 6. © 2003 -2005 Monash CTIE Slide 86
Attacks against Internetworks Do. S attacks Hijack Attacks Packet forgery Man In the Middle Theft of service/Qo. S. Impersonation Attacks against resources (Server, Link, Qo. S) Snooping Data Insertion/Deletion Host Intrusion Worms and Viruses (Application Issue!) This may not get better under IPv 6. © 2003 -2005 Monash CTIE Slide 86
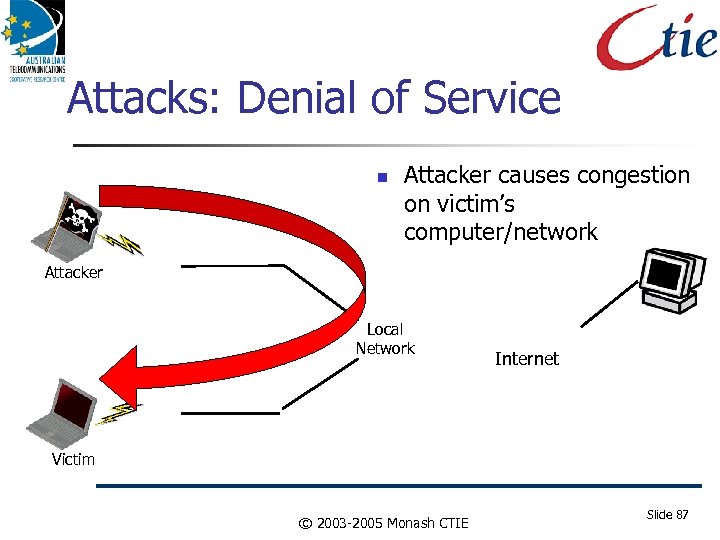 Attacks: Denial of Service Attacker causes congestion on victim’s computer/network Attacker Local Network Internet Victim © 2003 -2005 Monash CTIE Slide 87
Attacks: Denial of Service Attacker causes congestion on victim’s computer/network Attacker Local Network Internet Victim © 2003 -2005 Monash CTIE Slide 87
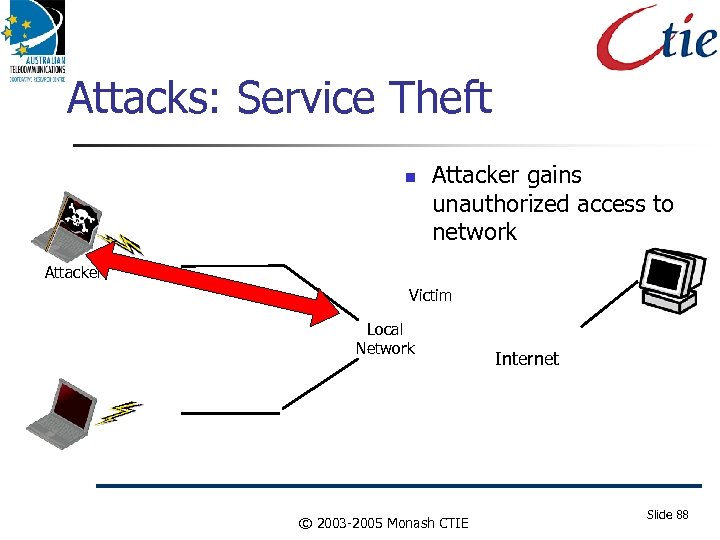 Attacks: Service Theft Attacker gains unauthorized access to network Attacker Victim Local Network © 2003 -2005 Monash CTIE Internet Slide 88
Attacks: Service Theft Attacker gains unauthorized access to network Attacker Victim Local Network © 2003 -2005 Monash CTIE Internet Slide 88
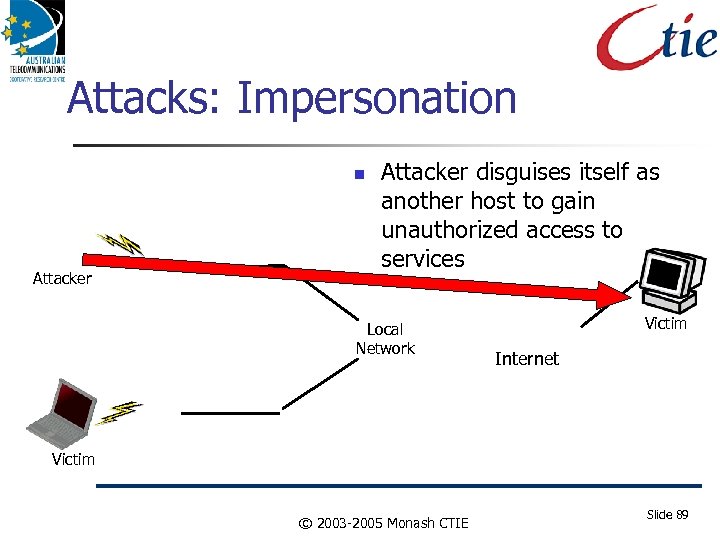 Attacks: Impersonation Attacker disguises itself as another host to gain unauthorized access to services Local Network Victim Internet Victim © 2003 -2005 Monash CTIE Slide 89
Attacks: Impersonation Attacker disguises itself as another host to gain unauthorized access to services Local Network Victim Internet Victim © 2003 -2005 Monash CTIE Slide 89
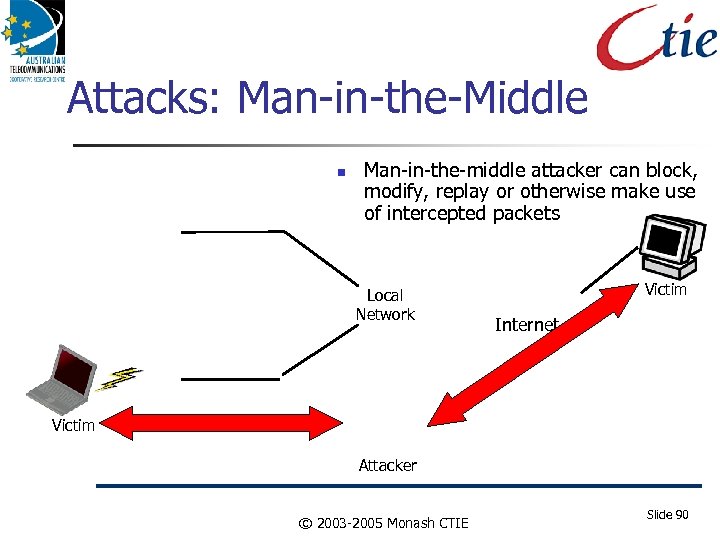 Attacks: Man-in-the-Middle Man-in-the-middle attacker can block, modify, replay or otherwise make use of intercepted packets Local Network Victim Internet Victim Attacker © 2003 -2005 Monash CTIE Slide 90
Attacks: Man-in-the-Middle Man-in-the-middle attacker can block, modify, replay or otherwise make use of intercepted packets Local Network Victim Internet Victim Attacker © 2003 -2005 Monash CTIE Slide 90
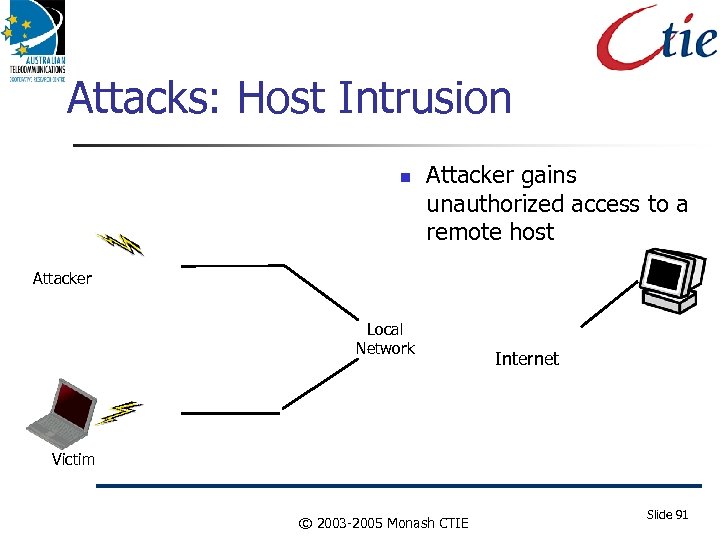 Attacks: Host Intrusion Attacker gains unauthorized access to a remote host Attacker Local Network Internet Victim © 2003 -2005 Monash CTIE Slide 91
Attacks: Host Intrusion Attacker gains unauthorized access to a remote host Attacker Local Network Internet Victim © 2003 -2005 Monash CTIE Slide 91
 IPv 6 Security Issues IPv 6 Security issues. Data Confidentiality/Integrity Neighbour Discovery/ Autoconfiguration Network Access Control Mobile IPv 6 Key Distribution Transition Mechanisms © 2003 -2005 Monash CTIE Slide 92
IPv 6 Security Issues IPv 6 Security issues. Data Confidentiality/Integrity Neighbour Discovery/ Autoconfiguration Network Access Control Mobile IPv 6 Key Distribution Transition Mechanisms © 2003 -2005 Monash CTIE Slide 92
 IPv 6 Security Features IPv 6 Security features. IPSec SEND (SEcuring Neighbour Discovery) AAAv 6 Mobile IPv 6 Return Routability © 2003 -2005 Monash CTIE Slide 93
IPv 6 Security Features IPv 6 Security features. IPSec SEND (SEcuring Neighbour Discovery) AAAv 6 Mobile IPv 6 Return Routability © 2003 -2005 Monash CTIE Slide 93
 Security Features: IPSec(v 6) IPSec End-to-End Security Authentication Encryption Available in some IPv 4 nodes, required in ALL IPv 6 nodes. © 2003 -2005 Monash CTIE Slide 94
Security Features: IPSec(v 6) IPSec End-to-End Security Authentication Encryption Available in some IPv 4 nodes, required in ALL IPv 6 nodes. © 2003 -2005 Monash CTIE Slide 94
 Security Features: SEND SEcuring Neighbor Discovery: Provides a method for applying IPSec to Neighbor Discovery Works in situations where IPSec typically wouldn't (Chicken and Egg) Protects autoconfiguration messages from attackers on the same link. Proves address ownership locally (Using CGA, ABK). In early stages of development Key Technology © 2003 -2005 Monash CTIE Slide 95
Security Features: SEND SEcuring Neighbor Discovery: Provides a method for applying IPSec to Neighbor Discovery Works in situations where IPSec typically wouldn't (Chicken and Egg) Protects autoconfiguration messages from attackers on the same link. Proves address ownership locally (Using CGA, ABK). In early stages of development Key Technology © 2003 -2005 Monash CTIE Slide 95
 Security Features: AAAv 6 AAAv 6 Protocols: Provide Authentication, Authorization and Accounting Used on access networks Works with NAS, Wireless LAN (EAP), PANA, PPP, Mobile IPv 6 DIAMETER protocol (supercedes RADIUS) Can specify Authorization policy through Attribute-Value-Pairs. © 2003 -2005 Monash CTIE Slide 96
Security Features: AAAv 6 AAAv 6 Protocols: Provide Authentication, Authorization and Accounting Used on access networks Works with NAS, Wireless LAN (EAP), PANA, PPP, Mobile IPv 6 DIAMETER protocol (supercedes RADIUS) Can specify Authorization policy through Attribute-Value-Pairs. © 2003 -2005 Monash CTIE Slide 96
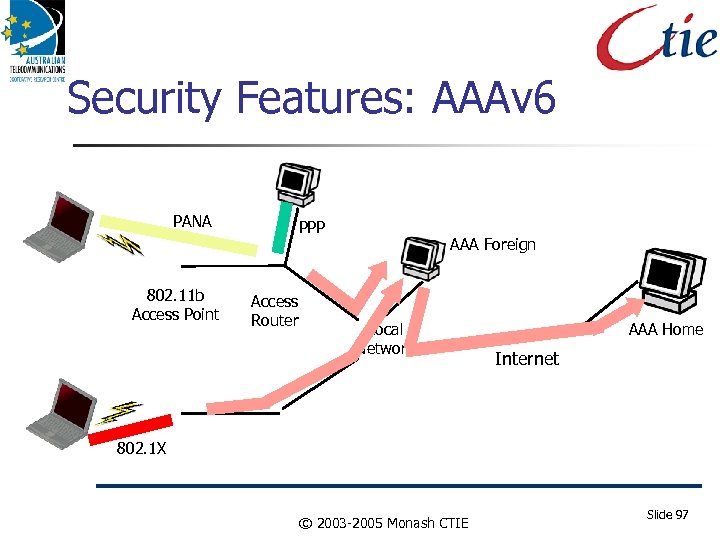 Security Features: AAAv 6 PANA 802. 11 b Access Point PPP Access Router AAA Foreign Local Network AAA Home Internet 802. 1 X © 2003 -2005 Monash CTIE Slide 97
Security Features: AAAv 6 PANA 802. 11 b Access Point PPP Access Router AAA Foreign Local Network AAA Home Internet 802. 1 X © 2003 -2005 Monash CTIE Slide 97
 Security Issues: Key Distribution The Public Key Infrastructure (PKI) has been around for a long time. Not many nodes have public keys (poor adoption). Many Key Exchange systems rely upon Public Key availability. Shared keys don't work for generic peer-to-peer communication. SEND relies upon Delegation Chains which establish trust between peers using digital signatures. Cryptographically generated addresses take pessimistic approach (no widely adopted PKI) If Keys are distributed, still need to replace/update securely. © 2003 -2005 Monash CTIE Slide 98
Security Issues: Key Distribution The Public Key Infrastructure (PKI) has been around for a long time. Not many nodes have public keys (poor adoption). Many Key Exchange systems rely upon Public Key availability. Shared keys don't work for generic peer-to-peer communication. SEND relies upon Delegation Chains which establish trust between peers using digital signatures. Cryptographically generated addresses take pessimistic approach (no widely adopted PKI) If Keys are distributed, still need to replace/update securely. © 2003 -2005 Monash CTIE Slide 98
 Security Issues: Transition Mechanisms Most IPv 6 hosts will be 'dual stack' IPv 4 systems will not have same security feature set as IPv 6 Double Handling of security policy (Mistakes easier). Small chance of attacks through protocol translation systems (IPSec may not work well, though). © 2003 -2005 Monash CTIE Slide 99
Security Issues: Transition Mechanisms Most IPv 6 hosts will be 'dual stack' IPv 4 systems will not have same security feature set as IPv 6 Double Handling of security policy (Mistakes easier). Small chance of attacks through protocol translation systems (IPSec may not work well, though). © 2003 -2005 Monash CTIE Slide 99
 Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 100
Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 100
 Advocacy and Forums More info: http: //www. ipv 6 -taskforce. org/ ) International Task Forces (in the EC, Korea, India, North America, Taiwan) have been set up to run summits and seminars promoting adoption and understanding of IPv 6 The IETF (Internet Engineering Task Force) is finalizing standards for IPv 6 extensions such as Mobility and Secure Neighbour Discovery. The IPv 6 Forum has released the "IPv 6 Ready" logo, which can be used to indicate a product's compliance with IPv 6 standards. © 2003 -2005 Monash CTIE Slide 101
Advocacy and Forums More info: http: //www. ipv 6 -taskforce. org/ ) International Task Forces (in the EC, Korea, India, North America, Taiwan) have been set up to run summits and seminars promoting adoption and understanding of IPv 6 The IETF (Internet Engineering Task Force) is finalizing standards for IPv 6 extensions such as Mobility and Secure Neighbour Discovery. The IPv 6 Forum has released the "IPv 6 Ready" logo, which can be used to indicate a product's compliance with IPv 6 standards. © 2003 -2005 Monash CTIE Slide 101
 World-wide connectivity Advocacy won't help if the packets don't get through! Academic Networks: Internet 2 (US), Grange. Net (AU), 6 NET (EU), CERNET 2 (China), etc. Commercial Networks: NTT in Japan and elsewhere Telia and NTT have commercial offerings in Europe. Uptake in USA is slow but gaining momentum. Sprint, MCI, etc. © 2003 -2005 Monash CTIE Slide 102
World-wide connectivity Advocacy won't help if the packets don't get through! Academic Networks: Internet 2 (US), Grange. Net (AU), 6 NET (EU), CERNET 2 (China), etc. Commercial Networks: NTT in Japan and elsewhere Telia and NTT have commercial offerings in Europe. Uptake in USA is slow but gaining momentum. Sprint, MCI, etc. © 2003 -2005 Monash CTIE Slide 102
 IPv 6 Implementations (more info: http: //www. ipv 6. org/impl/ ) Looking at three Classes of implementations: Host Implementations Mobile. IPv 6 Router Implementations © 2003 -2005 Monash CTIE Slide 103
IPv 6 Implementations (more info: http: //www. ipv 6. org/impl/ ) Looking at three Classes of implementations: Host Implementations Mobile. IPv 6 Router Implementations © 2003 -2005 Monash CTIE Slide 103
 Host Implementations Most vendor Unix: Solaris 8 +, AIX 4. 3 +, etc. Linux - kernels 2. 2 + include IPv 6 (2. 5+ full IPSecv 6) Free. BSD - includes KAME from 4. 0 Open. BSD - includes KAME from 2. 7 MS Windows - supported from XP onwards (some API issues) Mac OS X (10. 2 Jaguar onwards, some API issues) Embedded Implementations from Wind River, Elmic, etc. © 2003 -2005 Monash CTIE Slide 104
Host Implementations Most vendor Unix: Solaris 8 +, AIX 4. 3 +, etc. Linux - kernels 2. 2 + include IPv 6 (2. 5+ full IPSecv 6) Free. BSD - includes KAME from 4. 0 Open. BSD - includes KAME from 2. 7 MS Windows - supported from XP onwards (some API issues) Mac OS X (10. 2 Jaguar onwards, some API issues) Embedded Implementations from Wind River, Elmic, etc. © 2003 -2005 Monash CTIE Slide 104
 Router Implementations Available from major vendors including: Cisco IOS 12. 2 T + Juniper JUNOS 5. 1 + Nortel © 2003 -2005 Monash CTIE Slide 105
Router Implementations Available from major vendors including: Cisco IOS 12. 2 T + Juniper JUNOS 5. 1 + Nortel © 2003 -2005 Monash CTIE Slide 105
 Network Applications Server Applications Apache web server supports IPv 6 Many other services do too, due to 'dual stack' approach. Desktop Applications Microsoft Internet Explorer Secure Shell (ssh) FTP, Telnet © 2003 -2005 Monash CTIE Slide 106
Network Applications Server Applications Apache web server supports IPv 6 Many other services do too, due to 'dual stack' approach. Desktop Applications Microsoft Internet Explorer Secure Shell (ssh) FTP, Telnet © 2003 -2005 Monash CTIE Slide 106
 Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 107
Progress: Basics Addressing Routing Domain Name System IPv 4 to IPv 6 transition Security State of the Art Mobile IPv 6 © 2003 -2005 Monash CTIE Slide 107
 Contents IP Mobility Mobile IPv 4 Problem Statement Simple solutions Limitations Mobile IPv 6 Motivation Mobile IPv 6 Handovers © 2003 -2005 Monash CTIE Slide 108
Contents IP Mobility Mobile IPv 4 Problem Statement Simple solutions Limitations Mobile IPv 6 Motivation Mobile IPv 6 Handovers © 2003 -2005 Monash CTIE Slide 108
 Mobile Packets the Future? Trends towards packetisation of everything Easier to incorporate different data streams User control of usage models We don't know what the applications will be (but we can take some guesses). Once we have IP connectivity, anything goes. . . © 2003 -2005 Monash CTIE Slide 109
Mobile Packets the Future? Trends towards packetisation of everything Easier to incorporate different data streams User control of usage models We don't know what the applications will be (but we can take some guesses). Once we have IP connectivity, anything goes. . . © 2003 -2005 Monash CTIE Slide 109
 The Internet Mobility Challenge IP address is not only a unique address, but tied to Network Topology Movement of an IP device between networks relies on Layer 2 or Layer 3 context transfer. When Layer 3 transfer occurs, IP address changes. Higher layer protocols cannot handle IP address changes (e. g. TCP) IP Mobility must hide or prevent IP address changes for higher protocol layers © 2003 -2005 Monash CTIE Slide 110
The Internet Mobility Challenge IP address is not only a unique address, but tied to Network Topology Movement of an IP device between networks relies on Layer 2 or Layer 3 context transfer. When Layer 3 transfer occurs, IP address changes. Higher layer protocols cannot handle IP address changes (e. g. TCP) IP Mobility must hide or prevent IP address changes for higher protocol layers © 2003 -2005 Monash CTIE Slide 110
 Layer 2 mobility limitations Single Layer 3 broadcast domain All broadcasts go over wireless medium Handovers between networks problematic Service Provider to Enterprise/Service Provider Heterogeneous handovers Need to re-implement mobility for every Layer 2 © 2003 -2005 Monash CTIE Slide 111
Layer 2 mobility limitations Single Layer 3 broadcast domain All broadcasts go over wireless medium Handovers between networks problematic Service Provider to Enterprise/Service Provider Heterogeneous handovers Need to re-implement mobility for every Layer 2 © 2003 -2005 Monash CTIE Slide 111
 Using DHCP for roaming Dynamic Host Configuration Protocol Allows devices to get an address when visiting a network. Available for IPv 4 and IPv 6. Existing sessions do not survive movement across link boundaries Address management not required in IPv 6 (Stateless Address Autoconfiguration) Provides additional information (DNS &etc) © 2003 -2005 Monash CTIE Slide 112
Using DHCP for roaming Dynamic Host Configuration Protocol Allows devices to get an address when visiting a network. Available for IPv 4 and IPv 6. Existing sessions do not survive movement across link boundaries Address management not required in IPv 6 (Stateless Address Autoconfiguration) Provides additional information (DNS &etc) © 2003 -2005 Monash CTIE Slide 112
 Mobile IP No geographic limitations No physical connection No modifications to other hosts or routers No modifications to IP addressing Secure Transparent to transport layer Assumptions <1 change per second routing based only on destination address © 2003 -2005 Monash CTIE Slide 113
Mobile IP No geographic limitations No physical connection No modifications to other hosts or routers No modifications to IP addressing Secure Transparent to transport layer Assumptions <1 change per second routing based only on destination address © 2003 -2005 Monash CTIE Slide 113
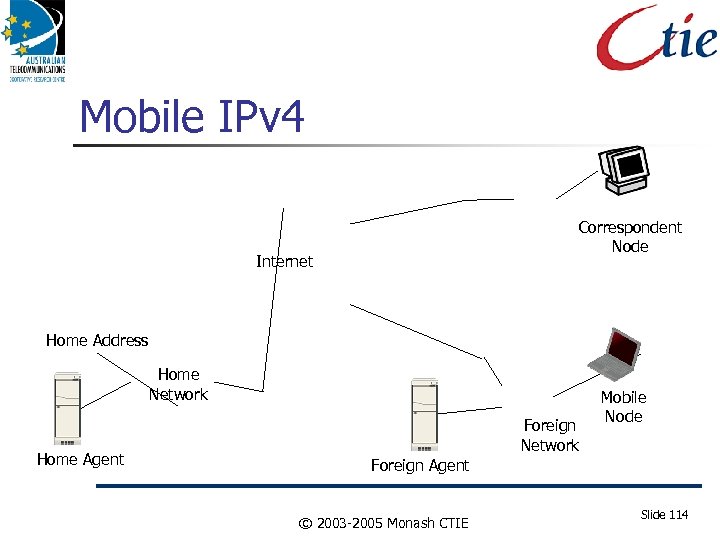 Mobile IPv 4 Correspondent Node Internet Home Address Home Network Home Agent Foreign Network Mobile Node Foreign Agent © 2003 -2005 Monash CTIE Slide 114
Mobile IPv 4 Correspondent Node Internet Home Address Home Network Home Agent Foreign Network Mobile Node Foreign Agent © 2003 -2005 Monash CTIE Slide 114
 Mobile IPv 6 Address Autoconfiguration Optional Headers Routing Header - replaces tunneling Home Address – overcomes ingress filtering Binding update and request Host Binding Caches No Foreign Agents Route optimisation IPSec Separate Security Specification Supports privacy © 2003 -2005 Monash CTIE Slide 115
Mobile IPv 6 Address Autoconfiguration Optional Headers Routing Header - replaces tunneling Home Address – overcomes ingress filtering Binding update and request Host Binding Caches No Foreign Agents Route optimisation IPSec Separate Security Specification Supports privacy © 2003 -2005 Monash CTIE Slide 115
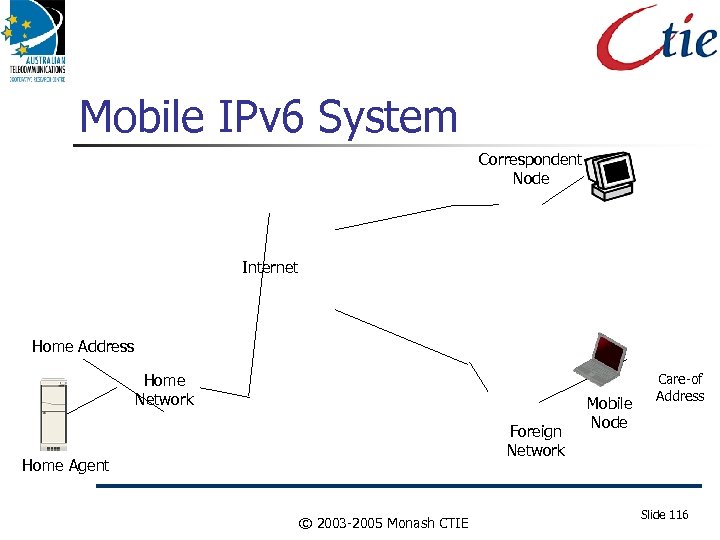 Mobile IPv 6 System Correspondent Node Internet Home Address Home Network Foreign Network Home Agent © 2003 -2005 Monash CTIE Mobile Node Care-of Address Slide 116
Mobile IPv 6 System Correspondent Node Internet Home Address Home Network Foreign Network Home Agent © 2003 -2005 Monash CTIE Mobile Node Care-of Address Slide 116
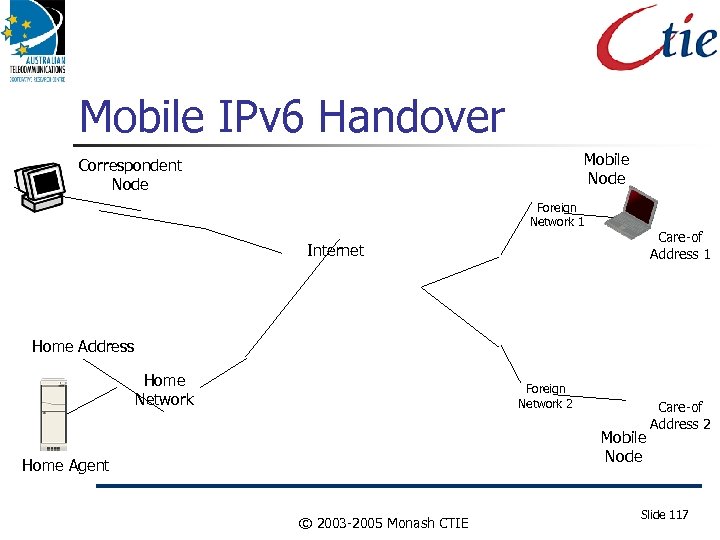 Mobile IPv 6 Handover Mobile Node Correspondent Node Foreign Network 1 Care-of Address 1 Internet Home Address Home Network Foreign Network 2 Mobile Node Home Agent © 2003 -2005 Monash CTIE Care-of Address 2 Slide 117
Mobile IPv 6 Handover Mobile Node Correspondent Node Foreign Network 1 Care-of Address 1 Internet Home Address Home Network Foreign Network 2 Mobile Node Home Agent © 2003 -2005 Monash CTIE Care-of Address 2 Slide 117
 Mobile IPv 6 Benefits: 1. Uses IPv 6 Router Discovery to detect movement 2. Uses IPv 6 Address Autoconfiguration 3. Route Optimisation 4. Limited support required in Access Network. Complexities: 1. Movement detection granularity is low 2. Dead time related to distance from HA 3. Security for CN/HA bindings 4. Duplicate Address Detection slow © 2003 -2005 Monash CTIE Slide 118
Mobile IPv 6 Benefits: 1. Uses IPv 6 Router Discovery to detect movement 2. Uses IPv 6 Address Autoconfiguration 3. Route Optimisation 4. Limited support required in Access Network. Complexities: 1. Movement detection granularity is low 2. Dead time related to distance from HA 3. Security for CN/HA bindings 4. Duplicate Address Detection slow © 2003 -2005 Monash CTIE Slide 118
 Thank you © 2003 -2005 Monash CTIE
Thank you © 2003 -2005 Monash CTIE


