87b85115d6672723922a181c64a66fc3.ppt
- Количество слайдов: 109
 Introduction to Information Security Mark Stamp Department of Computer Science San Jose State University stamp@cs. sjsu. edu Intro to Information Security 1
Introduction to Information Security Mark Stamp Department of Computer Science San Jose State University stamp@cs. sjsu. edu Intro to Information Security 1
 The Cast of Characters q Alice and Bob are the good guys q Trudy is the bad guy q Trudy is our generic “intruder” Intro to Information Security 2
The Cast of Characters q Alice and Bob are the good guys q Trudy is the bad guy q Trudy is our generic “intruder” Intro to Information Security 2
 Alice’s Online Bank q Alice opens Alice’s Online Bank (AOB) q What are Alice’s security concerns? q If Bob is a customer of AOB, what are his security concerns? q How are Alice and Bob concerns similar? How are they different? q How does Trudy view the situation? Intro to Information Security 3
Alice’s Online Bank q Alice opens Alice’s Online Bank (AOB) q What are Alice’s security concerns? q If Bob is a customer of AOB, what are his security concerns? q How are Alice and Bob concerns similar? How are they different? q How does Trudy view the situation? Intro to Information Security 3
 CIA q Confidentiality, Integrity and Availability q AOB must prevent Trudy from learning Bob’s account balance q Confidentiality: prevent unauthorized reading of information Intro to Information Security 4
CIA q Confidentiality, Integrity and Availability q AOB must prevent Trudy from learning Bob’s account balance q Confidentiality: prevent unauthorized reading of information Intro to Information Security 4
 CIA q Trudy must not be able to change Bob’s account balance q Bob must not be able to improperly change his own account balance q Integrity: prevent unauthorized writing of information Intro to Information Security 5
CIA q Trudy must not be able to change Bob’s account balance q Bob must not be able to improperly change his own account balance q Integrity: prevent unauthorized writing of information Intro to Information Security 5
 CIA AOB’s information must be available when needed q Alice must be able to make transaction q o If not, she’ll take her business elsewhere Availability: Data is available in a timely manner when needed q Availability is a “new” security concern q o In response to denial of service (Do. S) Intro to Information Security 6
CIA AOB’s information must be available when needed q Alice must be able to make transaction q o If not, she’ll take her business elsewhere Availability: Data is available in a timely manner when needed q Availability is a “new” security concern q o In response to denial of service (Do. S) Intro to Information Security 6
 Beyond CIA q How does Bob’s computer know that “Bob” is really Bob and not Trudy? q Bob’s password must be verified o This requires some clever cryptography q What are security concerns of pwds? q Are there alternatives to passwords? Intro to Information Security 7
Beyond CIA q How does Bob’s computer know that “Bob” is really Bob and not Trudy? q Bob’s password must be verified o This requires some clever cryptography q What are security concerns of pwds? q Are there alternatives to passwords? Intro to Information Security 7
 Beyond CIA When Bob logs into AOB, how does AOB know that “Bob” is really Bob? q As before, Bob’s password is verified q Unlike standalone computer case, network security issues arise q What are network security concerns? q Protocols are critically important q Crypto also important in protocols q Intro to Information Security 8
Beyond CIA When Bob logs into AOB, how does AOB know that “Bob” is really Bob? q As before, Bob’s password is verified q Unlike standalone computer case, network security issues arise q What are network security concerns? q Protocols are critically important q Crypto also important in protocols q Intro to Information Security 8
 Beyond CIA q Once Bob is authenticated by AOB, then AOB must restrict actions of Bob o Bob can’t view Charlie’s account info o Bob can’t install new software, etc. Enforcing these restrictions is known as authorization q Access control includes both authentication and authorization q Intro to Information Security 9
Beyond CIA q Once Bob is authenticated by AOB, then AOB must restrict actions of Bob o Bob can’t view Charlie’s account info o Bob can’t install new software, etc. Enforcing these restrictions is known as authorization q Access control includes both authentication and authorization q Intro to Information Security 9
 Beyond CIA q Cryptography, protocols and access control are implemented in software q What are security issues of software? o Most software is complex and buggy o Software flaws lead to security flaws o How to reduce flaws in software development? Intro to Information Security 10
Beyond CIA q Cryptography, protocols and access control are implemented in software q What are security issues of software? o Most software is complex and buggy o Software flaws lead to security flaws o How to reduce flaws in software development? Intro to Information Security 10
 Beyond CIA q Some software is intentionally evil o Malware: computer viruses, worms, etc. q What can Alice and Bob do to protect themselves from malware? q What can Trudy do to make malware more “effective”? Intro to Information Security 11
Beyond CIA q Some software is intentionally evil o Malware: computer viruses, worms, etc. q What can Alice and Bob do to protect themselves from malware? q What can Trudy do to make malware more “effective”? Intro to Information Security 11
 Beyond CIA q Operating systems enforce security o For example, authorization q OS: large and complex software o Win XP has 40, 000 lines of code! o Subject to bugs and flaws like any other software o Many security issues specific to OSs o Can you trust an OS? Intro to Information Security 12
Beyond CIA q Operating systems enforce security o For example, authorization q OS: large and complex software o Win XP has 40, 000 lines of code! o Subject to bugs and flaws like any other software o Many security issues specific to OSs o Can you trust an OS? Intro to Information Security 12
 My Book q The o o text consists of four major parts Cryptography Access control Protocols Software Intro to Information Security 13
My Book q The o o text consists of four major parts Cryptography Access control Protocols Software Intro to Information Security 13
 Cryptography q “Secret codes” q The book covers o o o Classic cryptography Symmetric ciphers Public key cryptography Hash functions Advanced cryptanalysis Intro to Information Security 14
Cryptography q “Secret codes” q The book covers o o o Classic cryptography Symmetric ciphers Public key cryptography Hash functions Advanced cryptanalysis Intro to Information Security 14
 Access Control q Authentication o Passwords o Biometrics and other q Authorization o Access Control Lists (ACLs) and Capabilities o Multilevel security (MLS), security modeling, covert channel, inference control o Firewalls and Intrusion Detection Systems Intro to Information Security 15
Access Control q Authentication o Passwords o Biometrics and other q Authorization o Access Control Lists (ACLs) and Capabilities o Multilevel security (MLS), security modeling, covert channel, inference control o Firewalls and Intrusion Detection Systems Intro to Information Security 15
 Protocols q Simple authentication protocols o “Butterfly effect” --- small change can have drastic effect on security o Cryptography used in protocols q Real-world security protocols o SSL, IPSec, Kerberos o GSM security Intro to Information Security 16
Protocols q Simple authentication protocols o “Butterfly effect” --- small change can have drastic effect on security o Cryptography used in protocols q Real-world security protocols o SSL, IPSec, Kerberos o GSM security Intro to Information Security 16
 Software q Software security-critical flaws o Buffer overflow o Other common flaws q Malware o Specific viruses and worms o Prevention and detection o The future of malware Intro to Information Security 17
Software q Software security-critical flaws o Buffer overflow o Other common flaws q Malware o Specific viruses and worms o Prevention and detection o The future of malware Intro to Information Security 17
 Software q Software reverse engineering (SRE) o How hackers “dissect” software q Digital rights management q Limits of testing o Shows difficulty of security in software o Also raises OS security issues o Open source vs closed source Intro to Information Security 18
Software q Software reverse engineering (SRE) o How hackers “dissect” software q Digital rights management q Limits of testing o Shows difficulty of security in software o Also raises OS security issues o Open source vs closed source Intro to Information Security 18
 Software q Operating systems o Basic OS security issues o “Trusted” OS requirements o NGSCB: Microsoft’s trusted OS for PC q Software is a big security topic o Lots of material to cover o Lots of security problems to consider Intro to Information Security 19
Software q Operating systems o Basic OS security issues o “Trusted” OS requirements o NGSCB: Microsoft’s trusted OS for PC q Software is a big security topic o Lots of material to cover o Lots of security problems to consider Intro to Information Security 19
 Think Like Trudy q In the past, no respectable sources talked about “hacking” in detail q It was argued that such info would help hackers q Very recently, this has changed o Books on network hacking, how to write evil software, how to hack software, etc. Intro to Information Security 20
Think Like Trudy q In the past, no respectable sources talked about “hacking” in detail q It was argued that such info would help hackers q Very recently, this has changed o Books on network hacking, how to write evil software, how to hack software, etc. Intro to Information Security 20
 Think Like Trudy q Good guys must think like bad guys! q A police detective o Must study and understand criminals q In information security o We want to understand Trudy’s motives o We must know Trudy’s methods o We’ll often pretend to be Trudy Intro to Information Security 21
Think Like Trudy q Good guys must think like bad guys! q A police detective o Must study and understand criminals q In information security o We want to understand Trudy’s motives o We must know Trudy’s methods o We’ll often pretend to be Trudy Intro to Information Security 21
 Think Like Trudy q Is all of this security information a good idea? q “It’s about time somebody wrote a book to teach the good guys what the bad guys already know. ” --- Bruce Schneier Intro to Information Security 22
Think Like Trudy q Is all of this security information a good idea? q “It’s about time somebody wrote a book to teach the good guys what the bad guys already know. ” --- Bruce Schneier Intro to Information Security 22
 Think Like Trudy q We must try to think like Trudy q We must study Trudy’s methods q We can admire Trudy’s cleverness q Often, we can’t help but laugh at Alice and Bob’s stupidity q But, we cannot act like Trudy Intro to Information Security 23
Think Like Trudy q We must try to think like Trudy q We must study Trudy’s methods q We can admire Trudy’s cleverness q Often, we can’t help but laugh at Alice and Bob’s stupidity q But, we cannot act like Trudy Intro to Information Security 23
 Security Books Intro to Information Security 24
Security Books Intro to Information Security 24
 Security Books q q Security Engineering: A Guide to Building Dependable Distributed Systems, Anderson, John Wiley & Sons, Inc. , 2001 Plusses o Highly readable/entertaining o Case studies o Emphasis on human factors q Minuses o Glosses over technical issue o Not a textbook Intro to Information Security 25
Security Books q q Security Engineering: A Guide to Building Dependable Distributed Systems, Anderson, John Wiley & Sons, Inc. , 2001 Plusses o Highly readable/entertaining o Case studies o Emphasis on human factors q Minuses o Glosses over technical issue o Not a textbook Intro to Information Security 25
 Security Books q q Network Security: Private Communication in a Public World, second edition, Kaufman, Perlman, and Speciner, Prentice Hall, 2002 Plusses o Solid on protocols o Brief but good on crypto q Minuses o No software, access control o Too much RFC detail Intro to Information Security 26
Security Books q q Network Security: Private Communication in a Public World, second edition, Kaufman, Perlman, and Speciner, Prentice Hall, 2002 Plusses o Solid on protocols o Brief but good on crypto q Minuses o No software, access control o Too much RFC detail Intro to Information Security 26
 Security Books Security in Computing, third edition, Pfleeger and Pfleeger, Prentice Hall, 2003 q Plusses q o Good on OS topics o OK on software topics q Minuses o Dated o Boring Intro to Information Security 27
Security Books Security in Computing, third edition, Pfleeger and Pfleeger, Prentice Hall, 2003 q Plusses q o Good on OS topics o OK on software topics q Minuses o Dated o Boring Intro to Information Security 27
 Security Books q q Applied Cryptography: Protocols, Algorithms and Source Code in C, Second Edition, Schneier, John Wiley & Sons, Inc. , 1995 (2 nd edition) Plusses o Encyclopedic o Widely used q Minuses o Crypto only o Sloppy in places Intro to Information Security 28
Security Books q q Applied Cryptography: Protocols, Algorithms and Source Code in C, Second Edition, Schneier, John Wiley & Sons, Inc. , 1995 (2 nd edition) Plusses o Encyclopedic o Widely used q Minuses o Crypto only o Sloppy in places Intro to Information Security 28
 Security Books q q Computer Security, Gollmann, John Wiley & Sons, Inc. , 1999 Plusses o Chapter 8: How things go wrong o Good on security modeling q Minuses o Mostly theoretical o No software/limited topics Intro to Information Security 29
Security Books q q Computer Security, Gollmann, John Wiley & Sons, Inc. , 1999 Plusses o Chapter 8: How things go wrong o Good on security modeling q Minuses o Mostly theoretical o No software/limited topics Intro to Information Security 29
 Security Books q q Computer Security: Art and Science, Bishop, Addison Wesley, 2003 Plusses o Security modeling o Theory q Minuses o Theory, theory, and more theory o As much fun to read as a calculus textbook Intro to Information Security 30
Security Books q q Computer Security: Art and Science, Bishop, Addison Wesley, 2003 Plusses o Security modeling o Theory q Minuses o Theory, theory, and more theory o As much fun to read as a calculus textbook Intro to Information Security 30
 Security Books q q Fundamentals of Secure Computer Systems, Tjaden, Franklin, Beedle, and Associates, 2003 Plusses o Intrusion detection systems o Good general approach q Minuses o Weak crypto, software, protocols o Good approach, not well executed Intro to Information Security 31
Security Books q q Fundamentals of Secure Computer Systems, Tjaden, Franklin, Beedle, and Associates, 2003 Plusses o Intrusion detection systems o Good general approach q Minuses o Weak crypto, software, protocols o Good approach, not well executed Intro to Information Security 31
 Security Books q q Cryptography and Network Security: Principles and Practice, 3 rd edition, Stallings, Prentice Hall, 2002 Plusses o Some OK protocols material q Minuses o Lots of pointless facts o Not coherent Intro to Information Security 32
Security Books q q Cryptography and Network Security: Principles and Practice, 3 rd edition, Stallings, Prentice Hall, 2002 Plusses o Some OK protocols material q Minuses o Lots of pointless facts o Not coherent Intro to Information Security 32
 “Hacker” Books q Counter Hack: A Step-by-Step Guide to Computer Attacks and Effective Defenses, Skoudis, Prentice Hall, 2001 q Shellcoder’s Handbook: Discovering and Exploiting Security Holes, Koziol et al, Wiley, 2004 q Hacker Disassembling Uncovered, Kaspersky, A-List, 2003 q Reversing: Secrets of Reverse Engineering, Eilam, Wiley, 2005 Intro to Information Security 33
“Hacker” Books q Counter Hack: A Step-by-Step Guide to Computer Attacks and Effective Defenses, Skoudis, Prentice Hall, 2001 q Shellcoder’s Handbook: Discovering and Exploiting Security Holes, Koziol et al, Wiley, 2004 q Hacker Disassembling Uncovered, Kaspersky, A-List, 2003 q Reversing: Secrets of Reverse Engineering, Eilam, Wiley, 2005 Intro to Information Security 33
 My Book q Information Security: Principles and Practice, Stamp, John Wiley & Sons, Inc. , 2005 q Plusses o Too many to list… q Minuses o Can’t think of any… Intro to Information Security 34
My Book q Information Security: Principles and Practice, Stamp, John Wiley & Sons, Inc. , 2005 q Plusses o Too many to list… q Minuses o Can’t think of any… Intro to Information Security 34
 Crypto Intro to Information Security 35
Crypto Intro to Information Security 35
 Crypto Topics Crypto Basics q Symmetric ciphers q o Stream ciphers, Block ciphers q Public key crypto o Knapsack, RSA, DH, ECC, signatures, etc. Hash functions q Advanced cryptanalysis q Intro to Information Security 36
Crypto Topics Crypto Basics q Symmetric ciphers q o Stream ciphers, Block ciphers q Public key crypto o Knapsack, RSA, DH, ECC, signatures, etc. Hash functions q Advanced cryptanalysis q Intro to Information Security 36
 Crypto q Cryptology The art and science of making and breaking “secret codes” q Cryptography making “secret codes” q Cryptanalysis breaking “secret codes” q Crypto all of the above (and more) Intro to Information Security 37
Crypto q Cryptology The art and science of making and breaking “secret codes” q Cryptography making “secret codes” q Cryptanalysis breaking “secret codes” q Crypto all of the above (and more) Intro to Information Security 37
 How to Speak Crypto q q q A cipher or cryptosystem is used to encrypt the plaintext The result of encryption is ciphertext We decrypt ciphertext to recover plaintext A key is used to configure a cryptosystem A symmetric key cryptosystem uses the same key to encrypt as to decrypt A public key cryptosystem uses a public key to encrypt and a private key to decrypt (sign) Intro to Information Security 38
How to Speak Crypto q q q A cipher or cryptosystem is used to encrypt the plaintext The result of encryption is ciphertext We decrypt ciphertext to recover plaintext A key is used to configure a cryptosystem A symmetric key cryptosystem uses the same key to encrypt as to decrypt A public key cryptosystem uses a public key to encrypt and a private key to decrypt (sign) Intro to Information Security 38
 Crypto q Basis assumption o The system is completely known to the attacker o Only the key is secret q Also known as Kerckhoffs Principle o Crypto algorithms are not secret q Why do we make this assumption? o Experience has shown that secret algorithms are weak when exposed o Secret algorithms never remain secret o Better to find weaknesses beforehand Intro to Information Security 39
Crypto q Basis assumption o The system is completely known to the attacker o Only the key is secret q Also known as Kerckhoffs Principle o Crypto algorithms are not secret q Why do we make this assumption? o Experience has shown that secret algorithms are weak when exposed o Secret algorithms never remain secret o Better to find weaknesses beforehand Intro to Information Security 39
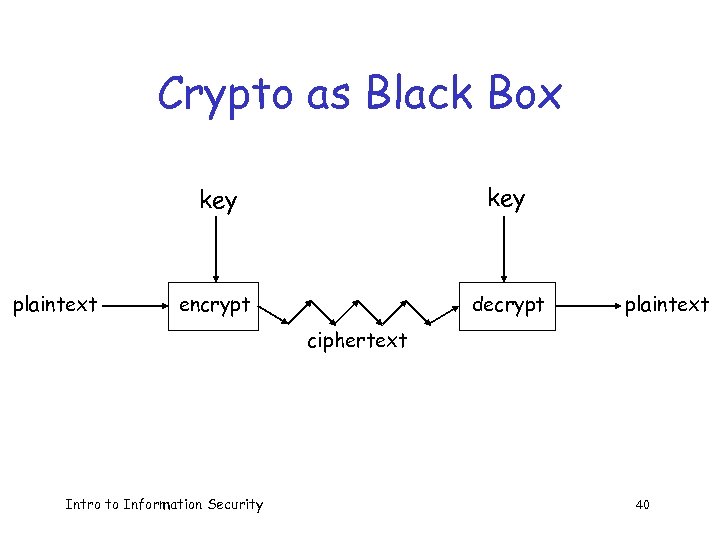 Crypto as Black Box key plaintext key encrypt decrypt plaintext ciphertext Intro to Information Security 40
Crypto as Black Box key plaintext key encrypt decrypt plaintext ciphertext Intro to Information Security 40
 Taxonomy of Cryptography q Symmetric Key o Same key for encryption as for decryption o Stream ciphers o Block ciphers q Public Key o Two keys, one for encryption (public), and one for decryption (private) o Digital signatures --- nothing comparable in symmetric key crypto q Hash algorithms Intro to Information Security 41
Taxonomy of Cryptography q Symmetric Key o Same key for encryption as for decryption o Stream ciphers o Block ciphers q Public Key o Two keys, one for encryption (public), and one for decryption (private) o Digital signatures --- nothing comparable in symmetric key crypto q Hash algorithms Intro to Information Security 41
 Taxonomy of Cryptanalysis Ciphertext only q Known plaintext q Chosen plaintext o “Lunchtime attack” o Protocols might encrypt chosen text q Adaptively chosen plaintext q Related key q Forward search (public key crypto only) q Etc. , etc. q Intro to Information Security 42
Taxonomy of Cryptanalysis Ciphertext only q Known plaintext q Chosen plaintext o “Lunchtime attack” o Protocols might encrypt chosen text q Adaptively chosen plaintext q Related key q Forward search (public key crypto only) q Etc. , etc. q Intro to Information Security 42
 Symmetric Key Crypto q Stream cipher --- like a one-time pad o Key is relatively short o Key is stretched into a long keystream o Keystream is then used like a one-time pad q Block cipher --- based on codebook concept o Block cipher key determines a codebook o Each key yields a different codebook o Employ both “confusion” and “diffusion” Intro to Information Security 43
Symmetric Key Crypto q Stream cipher --- like a one-time pad o Key is relatively short o Key is stretched into a long keystream o Keystream is then used like a one-time pad q Block cipher --- based on codebook concept o Block cipher key determines a codebook o Each key yields a different codebook o Employ both “confusion” and “diffusion” Intro to Information Security 43
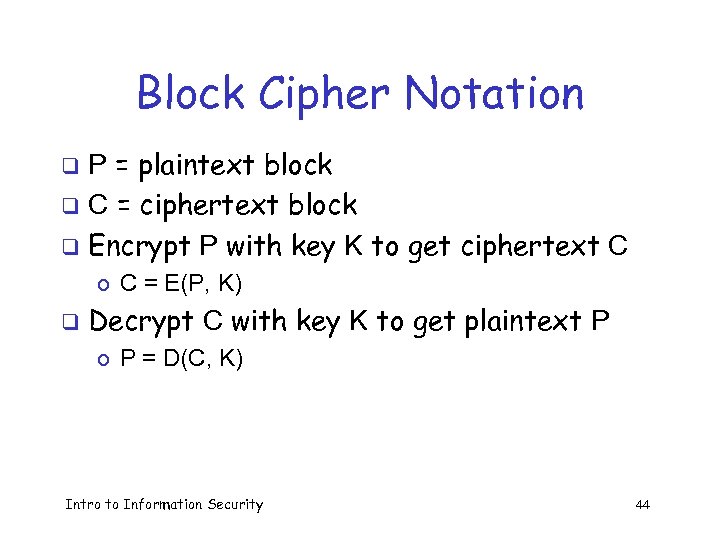 Block Cipher Notation P = plaintext block q C = ciphertext block q Encrypt P with key K to get ciphertext C q o C = E(P, K) q Decrypt C with key K to get plaintext P o P = D(C, K) Intro to Information Security 44
Block Cipher Notation P = plaintext block q C = ciphertext block q Encrypt P with key K to get ciphertext C q o C = E(P, K) q Decrypt C with key K to get plaintext P o P = D(C, K) Intro to Information Security 44
 Block Cipher Modes q Many modes of operation o We discuss two q Electronic Codebook (ECB) mode o Obvious thing to do o Encrypt each block independently o There is a serious weakness q Cipher Block Chaining (CBC) mode o Chain the blocks together o More secure than ECB, virtually no extra work Intro to Information Security 45
Block Cipher Modes q Many modes of operation o We discuss two q Electronic Codebook (ECB) mode o Obvious thing to do o Encrypt each block independently o There is a serious weakness q Cipher Block Chaining (CBC) mode o Chain the blocks together o More secure than ECB, virtually no extra work Intro to Information Security 45
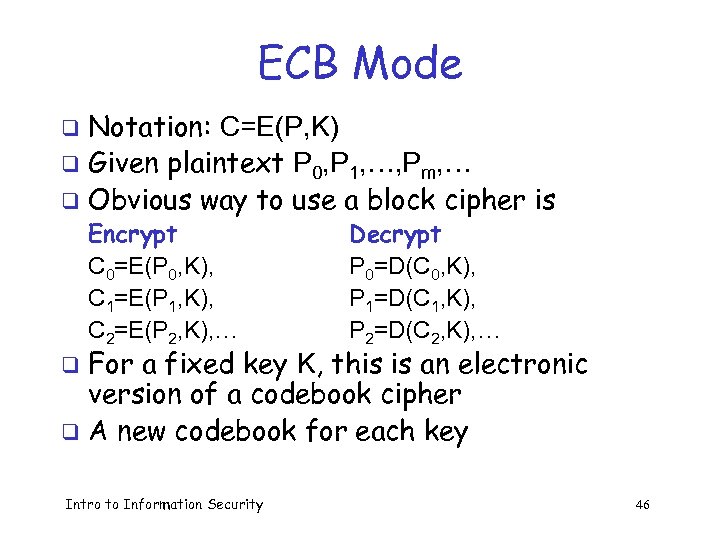 ECB Mode Notation: C=E(P, K) q Given plaintext P 0, P 1, …, Pm, … q Obvious way to use a block cipher is q Encrypt C 0=E(P 0, K), C 1=E(P 1, K), C 2=E(P 2, K), … Decrypt P 0=D(C 0, K), P 1=D(C 1, K), P 2=D(C 2, K), … For a fixed key K, this is an electronic version of a codebook cipher q A new codebook for each key q Intro to Information Security 46
ECB Mode Notation: C=E(P, K) q Given plaintext P 0, P 1, …, Pm, … q Obvious way to use a block cipher is q Encrypt C 0=E(P 0, K), C 1=E(P 1, K), C 2=E(P 2, K), … Decrypt P 0=D(C 0, K), P 1=D(C 1, K), P 2=D(C 2, K), … For a fixed key K, this is an electronic version of a codebook cipher q A new codebook for each key q Intro to Information Security 46
 ECB Weaknesses q Suppose Pi=Pj q Then Ci=Cj and Trudy knows Pi=Pj q This gives Trudy some information, even if she does not know Pi or Pj q Trudy might know Pi q A “cut and paste” attack also possible Intro to Information Security 47
ECB Weaknesses q Suppose Pi=Pj q Then Ci=Cj and Trudy knows Pi=Pj q This gives Trudy some information, even if she does not know Pi or Pj q Trudy might know Pi q A “cut and paste” attack also possible Intro to Information Security 47
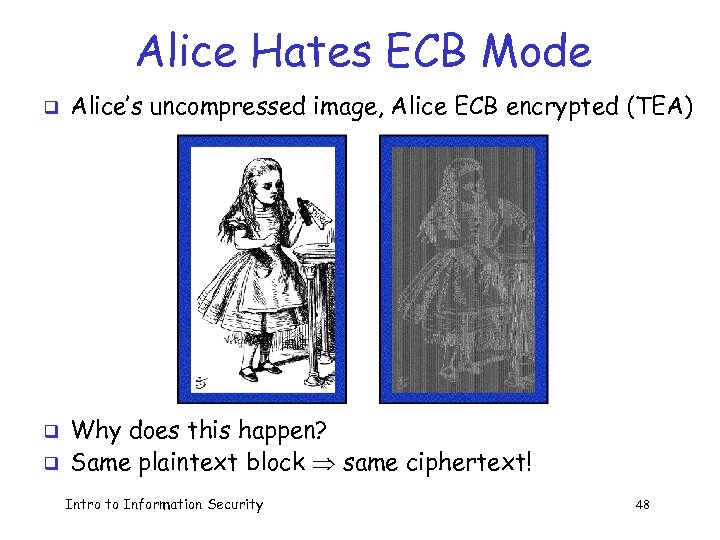 Alice Hates ECB Mode q q q Alice’s uncompressed image, Alice ECB encrypted (TEA) Why does this happen? Same plaintext block same ciphertext! Intro to Information Security 48
Alice Hates ECB Mode q q q Alice’s uncompressed image, Alice ECB encrypted (TEA) Why does this happen? Same plaintext block same ciphertext! Intro to Information Security 48
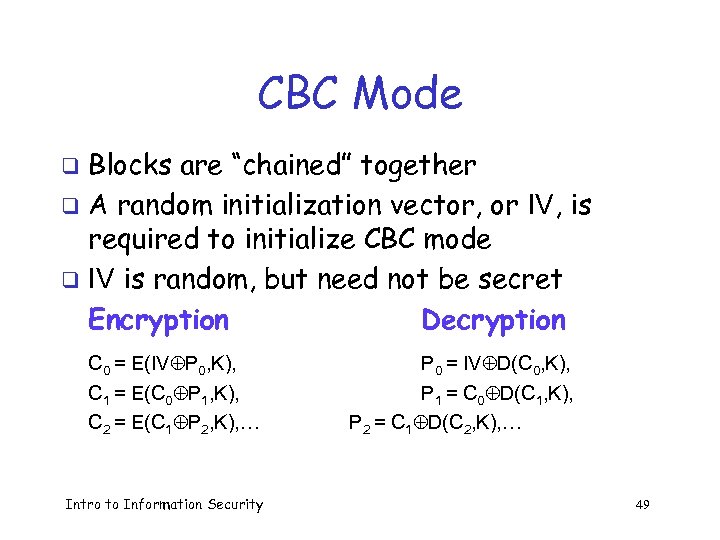 CBC Mode Blocks are “chained” together q A random initialization vector, or IV, is required to initialize CBC mode q IV is random, but need not be secret Encryption Decryption q C 0 = E(IV P 0, K), C 1 = E(C 0 P 1, K), C 2 = E(C 1 P 2, K), … Intro to Information Security P 0 = IV D(C 0, K), P 1 = C 0 D(C 1, K), P 2 = C 1 D(C 2, K), … 49
CBC Mode Blocks are “chained” together q A random initialization vector, or IV, is required to initialize CBC mode q IV is random, but need not be secret Encryption Decryption q C 0 = E(IV P 0, K), C 1 = E(C 0 P 1, K), C 2 = E(C 1 P 2, K), … Intro to Information Security P 0 = IV D(C 0, K), P 1 = C 0 D(C 1, K), P 2 = C 1 D(C 2, K), … 49
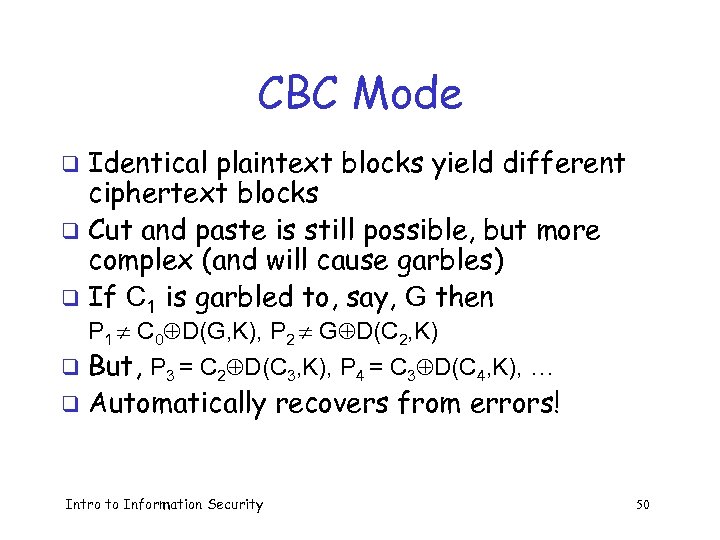 CBC Mode Identical plaintext blocks yield different ciphertext blocks q Cut and paste is still possible, but more complex (and will cause garbles) q If C 1 is garbled to, say, G then q P 1 C 0 D(G, K), P 2 G D(C 2, K) q But, P 3 = C 2 D(C 3, K), P 4 = C 3 D(C 4, K), … q Automatically recovers from errors! Intro to Information Security 50
CBC Mode Identical plaintext blocks yield different ciphertext blocks q Cut and paste is still possible, but more complex (and will cause garbles) q If C 1 is garbled to, say, G then q P 1 C 0 D(G, K), P 2 G D(C 2, K) q But, P 3 = C 2 D(C 3, K), P 4 = C 3 D(C 4, K), … q Automatically recovers from errors! Intro to Information Security 50
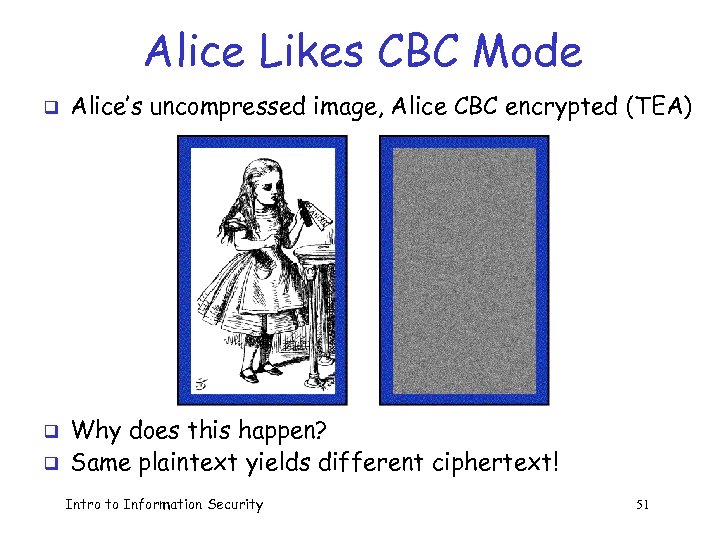 Alice Likes CBC Mode q q q Alice’s uncompressed image, Alice CBC encrypted (TEA) Why does this happen? Same plaintext yields different ciphertext! Intro to Information Security 51
Alice Likes CBC Mode q q q Alice’s uncompressed image, Alice CBC encrypted (TEA) Why does this happen? Same plaintext yields different ciphertext! Intro to Information Security 51
 Access Control Intro to Information Security 52
Access Control Intro to Information Security 52
 Access Control Topics q Authentication o Something you know (passwords) o Something you have (smartcard) o Something you are (biometrics) q Authorization o ACLs/capabilities, MLS, CAPTCHA o Firewalls, IDS Intro to Information Security 53
Access Control Topics q Authentication o Something you know (passwords) o Something you have (smartcard) o Something you are (biometrics) q Authorization o ACLs/capabilities, MLS, CAPTCHA o Firewalls, IDS Intro to Information Security 53
 Turing Test Proposed by Alan Turing in 1950 q Human asks questions to one other human and one computer (without seeing either) q If human questioner cannot distinguish the human from the computer responder, the computer passes the test q The gold standard in artificial intelligence q No computer can pass this today q Intro to Information Security 54
Turing Test Proposed by Alan Turing in 1950 q Human asks questions to one other human and one computer (without seeing either) q If human questioner cannot distinguish the human from the computer responder, the computer passes the test q The gold standard in artificial intelligence q No computer can pass this today q Intro to Information Security 54
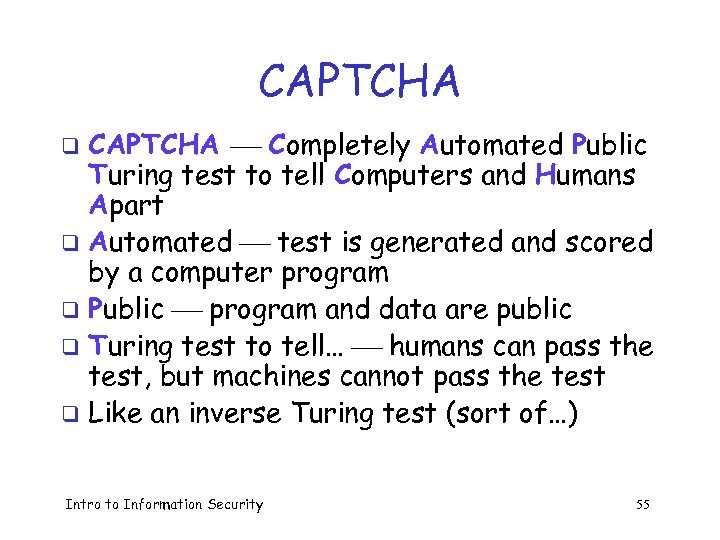 CAPTCHA Completely Automated Public Turing test to tell Computers and Humans Apart q Automated test is generated and scored by a computer program q Public program and data are public q Turing test to tell… humans can pass the test, but machines cannot pass the test q Like an inverse Turing test (sort of…) q Intro to Information Security 55
CAPTCHA Completely Automated Public Turing test to tell Computers and Humans Apart q Automated test is generated and scored by a computer program q Public program and data are public q Turing test to tell… humans can pass the test, but machines cannot pass the test q Like an inverse Turing test (sort of…) q Intro to Information Security 55
 CAPTCHA Paradox “…CAPTCHA is a program that can generate and grade tests that it itself cannot pass…” q “…much like some professors…” q Paradox computer creates and scores test that it cannot pass! q CAPTCHA used to restrict access to resources to humans (no computers) q CAPTCHA useful for access control q Intro to Information Security 56
CAPTCHA Paradox “…CAPTCHA is a program that can generate and grade tests that it itself cannot pass…” q “…much like some professors…” q Paradox computer creates and scores test that it cannot pass! q CAPTCHA used to restrict access to resources to humans (no computers) q CAPTCHA useful for access control q Intro to Information Security 56
 CAPTCHA Uses? Original motivation: automated “bots” stuffed ballot box in vote for best CS school q Free email services spammers used bots sign up for 1000’s of email accounts q o CAPTCHA employed so only humans can get accts q Sites that do not want to be automatically indexed by search engines o HTML tag only says “please do not index me” o CAPTCHA would force human intervention Intro to Information Security 57
CAPTCHA Uses? Original motivation: automated “bots” stuffed ballot box in vote for best CS school q Free email services spammers used bots sign up for 1000’s of email accounts q o CAPTCHA employed so only humans can get accts q Sites that do not want to be automatically indexed by search engines o HTML tag only says “please do not index me” o CAPTCHA would force human intervention Intro to Information Security 57
 CAPTCHA: Rules of the Game Must be easy for most humans to pass q Must be difficult or impossible for machines to pass q o Even with access to CAPTCHA software The only unknown is some random number q Desirable to have different CAPTCHAs in case some person cannot pass one type q o Blind person could not pass visual test, etc. Intro to Information Security 58
CAPTCHA: Rules of the Game Must be easy for most humans to pass q Must be difficult or impossible for machines to pass q o Even with access to CAPTCHA software The only unknown is some random number q Desirable to have different CAPTCHAs in case some person cannot pass one type q o Blind person could not pass visual test, etc. Intro to Information Security 58
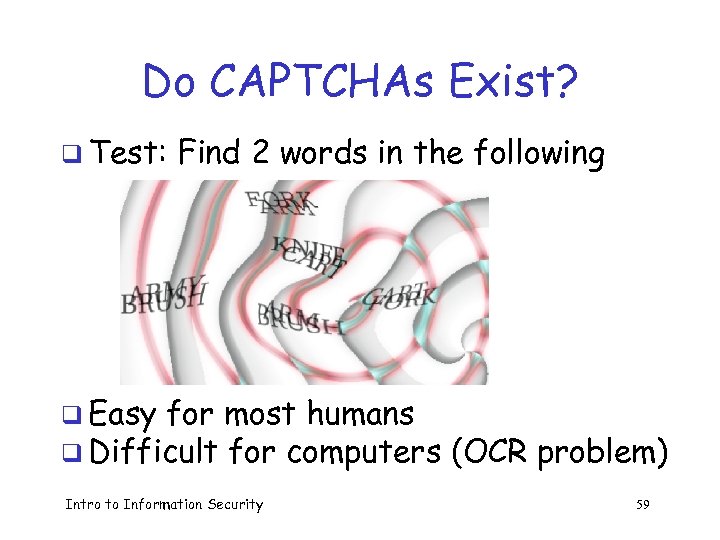 Do CAPTCHAs Exist? q Test: Find 2 words in the following q Easy for most humans q Difficult for computers (OCR problem) Intro to Information Security 59
Do CAPTCHAs Exist? q Test: Find 2 words in the following q Easy for most humans q Difficult for computers (OCR problem) Intro to Information Security 59
 CAPTCHAs q Current types of CAPTCHAs o Visual § Like previous example § Many others o Audio § Distorted words or music q No text-based CAPTCHAs o Maybe this is not possible… Intro to Information Security 60
CAPTCHAs q Current types of CAPTCHAs o Visual § Like previous example § Many others o Audio § Distorted words or music q No text-based CAPTCHAs o Maybe this is not possible… Intro to Information Security 60
 CAPTCHA’s and AI q Computer recognition of distorted text is a challenging AI problem o But humans can solve this problem q Same is true of distorted sound o Humans also good at solving this Hackers who break such a CAPTCHA have solved a hard AI problem q Putting hacker’s effort to good use! q Intro to Information Security 61
CAPTCHA’s and AI q Computer recognition of distorted text is a challenging AI problem o But humans can solve this problem q Same is true of distorted sound o Humans also good at solving this Hackers who break such a CAPTCHA have solved a hard AI problem q Putting hacker’s effort to good use! q Intro to Information Security 61
 Protocols Intro to Information Security 62
Protocols Intro to Information Security 62
 Protocol Topics q Simple authentication protocols o Nonces, session keys, timestamps, etc. o Perfect forward secrecy, zero knowledge proofs q Real-world security protocols o o SSL IPSec Kerberos GSM Intro to Information Security 63
Protocol Topics q Simple authentication protocols o Nonces, session keys, timestamps, etc. o Perfect forward secrecy, zero knowledge proofs q Real-world security protocols o o SSL IPSec Kerberos GSM Intro to Information Security 63
 Authentication q Authentication on a stand-alone computer is relatively simple o “Secure path” is the primary issue o Main concern is an attack on authentication software (we discuss software attacks later) q Authentication over a network is much more complex o Attacker can passively observe messages o Attacker can replay messages o Active attacks may be possible (insert, delete, change messages) Intro to Information Security 64
Authentication q Authentication on a stand-alone computer is relatively simple o “Secure path” is the primary issue o Main concern is an attack on authentication software (we discuss software attacks later) q Authentication over a network is much more complex o Attacker can passively observe messages o Attacker can replay messages o Active attacks may be possible (insert, delete, change messages) Intro to Information Security 64
 Symmetric Key Authentication q Alice and Bob share symmetric key KAB q Key KAB known only to Alice and Bob q Authenticate by proving knowledge of shared symmetric key q How to accomplish this? o Must not reveal key o Must not allow replay attack Intro to Information Security 65
Symmetric Key Authentication q Alice and Bob share symmetric key KAB q Key KAB known only to Alice and Bob q Authenticate by proving knowledge of shared symmetric key q How to accomplish this? o Must not reveal key o Must not allow replay attack Intro to Information Security 65
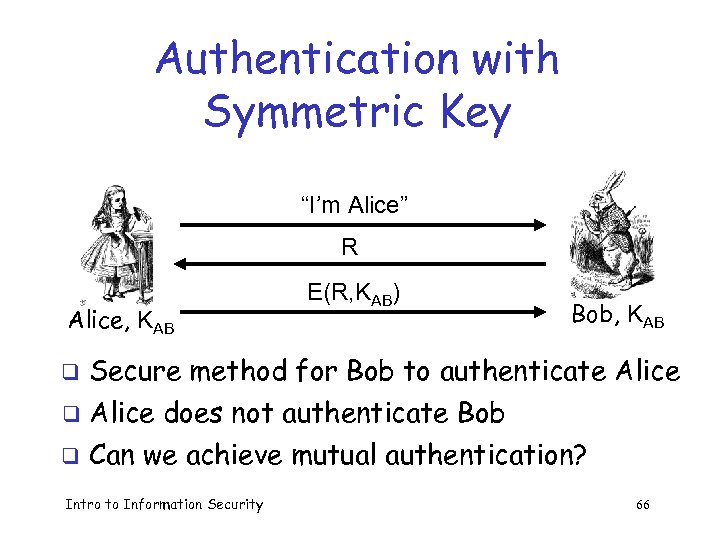 Authentication with Symmetric Key “I’m Alice” R Alice, KAB E(R, KAB) Bob, KAB Secure method for Bob to authenticate Alice q Alice does not authenticate Bob q Can we achieve mutual authentication? q Intro to Information Security 66
Authentication with Symmetric Key “I’m Alice” R Alice, KAB E(R, KAB) Bob, KAB Secure method for Bob to authenticate Alice q Alice does not authenticate Bob q Can we achieve mutual authentication? q Intro to Information Security 66
 Mutual Authentication q Since we have a secure one-way authentication protocol… q The obvious thing to do is to use the protocol twice o Once for Bob to authenticate Alice o Once for Alice to authenticate Bob q This has to work… Intro to Information Security 67
Mutual Authentication q Since we have a secure one-way authentication protocol… q The obvious thing to do is to use the protocol twice o Once for Bob to authenticate Alice o Once for Alice to authenticate Bob q This has to work… Intro to Information Security 67
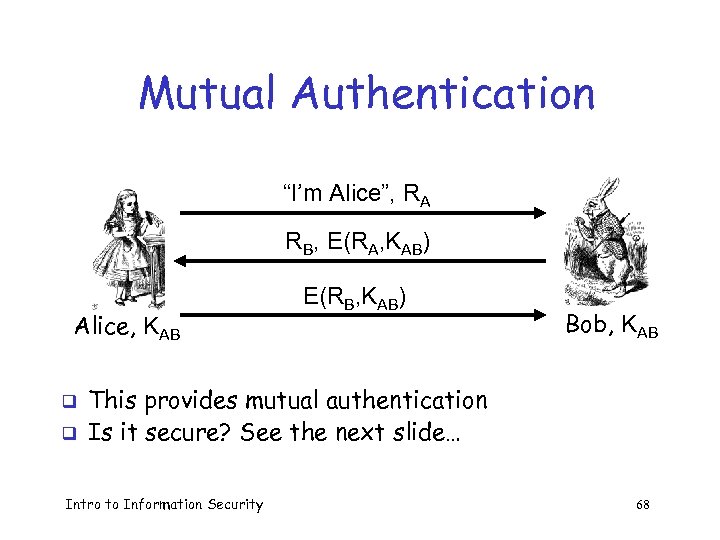 Mutual Authentication “I’m Alice”, RA RB, E(RA, KAB) Alice, KAB q q E(RB, KAB) Bob, KAB This provides mutual authentication Is it secure? See the next slide… Intro to Information Security 68
Mutual Authentication “I’m Alice”, RA RB, E(RA, KAB) Alice, KAB q q E(RB, KAB) Bob, KAB This provides mutual authentication Is it secure? See the next slide… Intro to Information Security 68
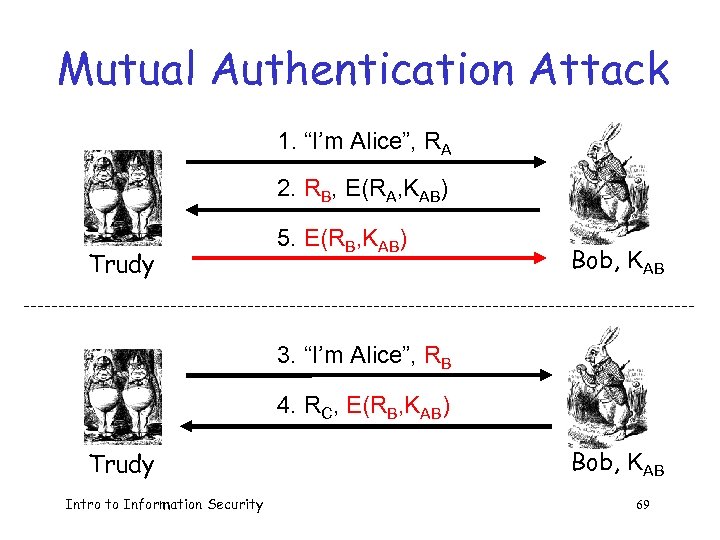 Mutual Authentication Attack 1. “I’m Alice”, RA 2. RB, E(RA, KAB) Trudy 5. E(RB, KAB) Bob, KAB 3. “I’m Alice”, RB 4. RC, E(RB, KAB) Trudy Intro to Information Security Bob, KAB 69
Mutual Authentication Attack 1. “I’m Alice”, RA 2. RB, E(RA, KAB) Trudy 5. E(RB, KAB) Bob, KAB 3. “I’m Alice”, RB 4. RC, E(RB, KAB) Trudy Intro to Information Security Bob, KAB 69
 Mutual Authentication Our one-way authentication protocol not secure for mutual authentication q Protocols are subtle! q The “obvious” thing may not be secure q Also, if assumptions or environment changes, protocol may not work q o This is a common source of security failure o For example, Internet protocols Intro to Information Security 70
Mutual Authentication Our one-way authentication protocol not secure for mutual authentication q Protocols are subtle! q The “obvious” thing may not be secure q Also, if assumptions or environment changes, protocol may not work q o This is a common source of security failure o For example, Internet protocols Intro to Information Security 70
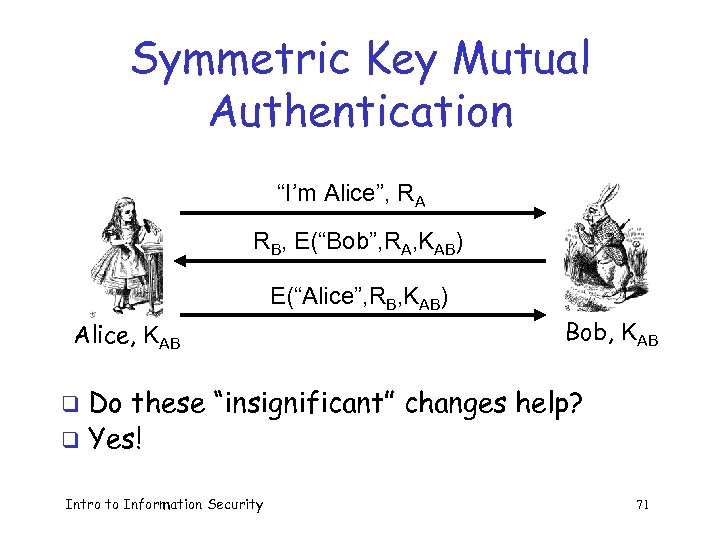 Symmetric Key Mutual Authentication “I’m Alice”, RA RB, E(“Bob”, RA, KAB) E(“Alice”, RB, KAB) Alice, KAB Bob, KAB Do these “insignificant” changes help? q Yes! q Intro to Information Security 71
Symmetric Key Mutual Authentication “I’m Alice”, RA RB, E(“Bob”, RA, KAB) E(“Alice”, RB, KAB) Alice, KAB Bob, KAB Do these “insignificant” changes help? q Yes! q Intro to Information Security 71
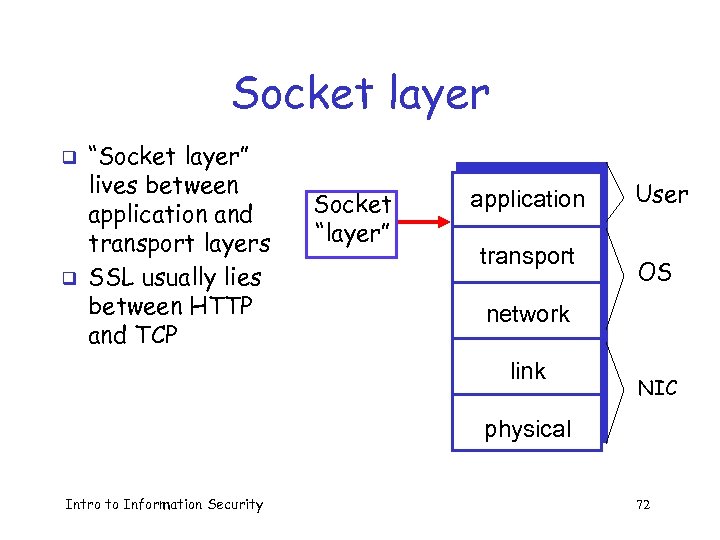 Socket layer q q “Socket layer” lives between application and transport layers SSL usually lies between HTTP and TCP Socket “layer” application User transport OS network link NIC physical Intro to Information Security 72
Socket layer q q “Socket layer” lives between application and transport layers SSL usually lies between HTTP and TCP Socket “layer” application User transport OS network link NIC physical Intro to Information Security 72
 What is SSL? SSL is the protocol used for most secure transactions over the Internet q For example, if you want to buy a book at amazon. com… q o You want to be sure you are dealing with Amazon (authentication) o Your credit card information must be protected in transit (confidentiality and/or integrity) o As long as you have money, Amazon doesn’t care who you are (authentication need not be mutual) Intro to Information Security 73
What is SSL? SSL is the protocol used for most secure transactions over the Internet q For example, if you want to buy a book at amazon. com… q o You want to be sure you are dealing with Amazon (authentication) o Your credit card information must be protected in transit (confidentiality and/or integrity) o As long as you have money, Amazon doesn’t care who you are (authentication need not be mutual) Intro to Information Security 73
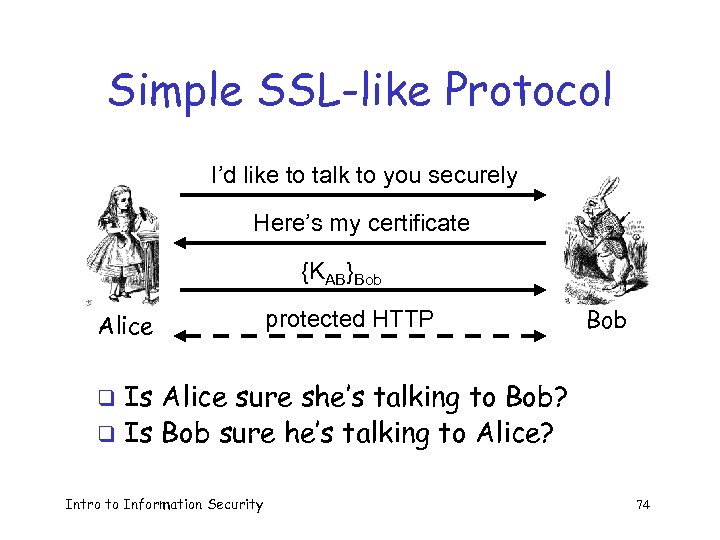 Simple SSL-like Protocol I’d like to talk to you securely Here’s my certificate {KAB}Bob Alice protected HTTP Bob Is Alice sure she’s talking to Bob? q Is Bob sure he’s talking to Alice? q Intro to Information Security 74
Simple SSL-like Protocol I’d like to talk to you securely Here’s my certificate {KAB}Bob Alice protected HTTP Bob Is Alice sure she’s talking to Bob? q Is Bob sure he’s talking to Alice? q Intro to Information Security 74
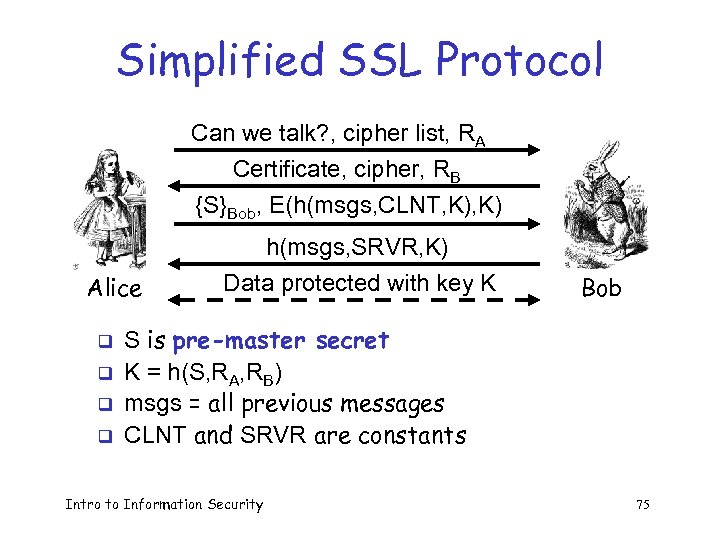 Simplified SSL Protocol Can we talk? , cipher list, RA Certificate, cipher, RB {S}Bob, E(h(msgs, CLNT, K) Alice q q h(msgs, SRVR, K) Data protected with key K Bob S is pre-master secret K = h(S, RA, RB) msgs = all previous messages CLNT and SRVR are constants Intro to Information Security 75
Simplified SSL Protocol Can we talk? , cipher list, RA Certificate, cipher, RB {S}Bob, E(h(msgs, CLNT, K) Alice q q h(msgs, SRVR, K) Data protected with key K Bob S is pre-master secret K = h(S, RA, RB) msgs = all previous messages CLNT and SRVR are constants Intro to Information Security 75
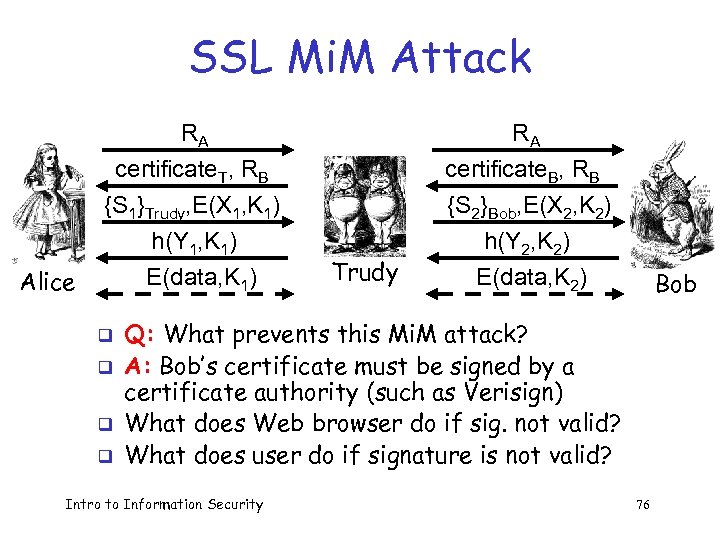 SSL Mi. M Attack RA Alice RA certificate. T, RB {S 1}Trudy, E(X 1, K 1) h(Y 1, K 1) E(data, K 1) certificate. B, RB {S 2}Bob, E(X 2, K 2) h(Y 2, K 2) E(data, K 2) q q Trudy Bob Q: What prevents this Mi. M attack? A: Bob’s certificate must be signed by a certificate authority (such as Verisign) What does Web browser do if sig. not valid? What does user do if signature is not valid? Intro to Information Security 76
SSL Mi. M Attack RA Alice RA certificate. T, RB {S 1}Trudy, E(X 1, K 1) h(Y 1, K 1) E(data, K 1) certificate. B, RB {S 2}Bob, E(X 2, K 2) h(Y 2, K 2) E(data, K 2) q q Trudy Bob Q: What prevents this Mi. M attack? A: Bob’s certificate must be signed by a certificate authority (such as Verisign) What does Web browser do if sig. not valid? What does user do if signature is not valid? Intro to Information Security 76
 Software Intro to Information Security 77
Software Intro to Information Security 77
 Software Topics Flaws q Malware q Software-based attacks q Software reverse engineering (SRE) q Digital rights management (DRM) q Software development q Operating systems/trusted OS q NGSCB q Intro to Information Security 78
Software Topics Flaws q Malware q Software-based attacks q Software reverse engineering (SRE) q Digital rights management (DRM) q Software development q Operating systems/trusted OS q NGSCB q Intro to Information Security 78
 Why Software? Why is software as important to security as crypto, access control and protocols? q Virtually all of information security is implemented in software q If your software is subject to attack, your security is broken q o Regardless of strength of crypto, access control or protocols q Software is a poor foundation for security Intro to Information Security 79
Why Software? Why is software as important to security as crypto, access control and protocols? q Virtually all of information security is implemented in software q If your software is subject to attack, your security is broken q o Regardless of strength of crypto, access control or protocols q Software is a poor foundation for security Intro to Information Security 79
 Bad Software is Everywhere q NASA Mars Lander (cost $165 million) o Crashed into Mars o Error in converting English and metric units q Denver airport o Buggy baggage handling system o Delayed airport opening by 11 months o Cost of delay exceeded $1 million/day q MV-22 Osprey o Advanced military aircraft o Lives have been lost due to faulty software Intro to Information Security 80
Bad Software is Everywhere q NASA Mars Lander (cost $165 million) o Crashed into Mars o Error in converting English and metric units q Denver airport o Buggy baggage handling system o Delayed airport opening by 11 months o Cost of delay exceeded $1 million/day q MV-22 Osprey o Advanced military aircraft o Lives have been lost due to faulty software Intro to Information Security 80
 Software Issues “Normal” users q Find bugs and flaws by accident q Hate bad software… q …but must learn to live with it q Must make bad software work Intro to Information Security Attackers q Actively look for bugs and flaws q Like bad software… q …and try to make it misbehave q Attack systems thru bad software 81
Software Issues “Normal” users q Find bugs and flaws by accident q Hate bad software… q …but must learn to live with it q Must make bad software work Intro to Information Security Attackers q Actively look for bugs and flaws q Like bad software… q …and try to make it misbehave q Attack systems thru bad software 81
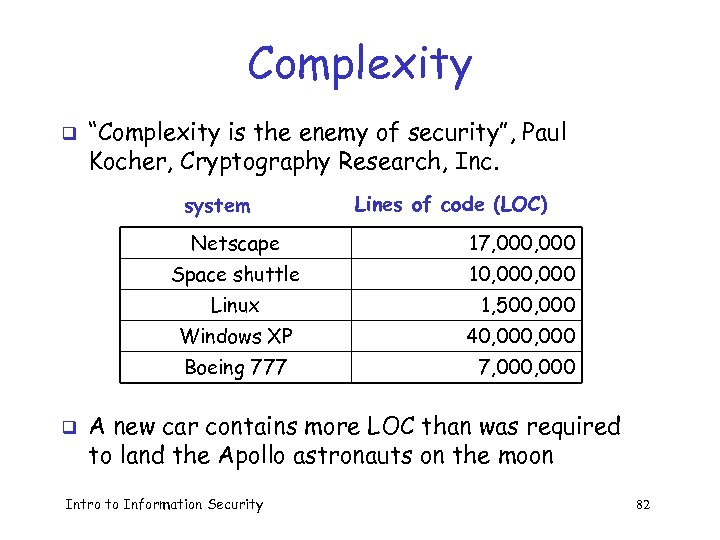 Complexity q “Complexity is the enemy of security”, Paul Kocher, Cryptography Research, Inc. system Lines of code (LOC) Netscape 17, 000 Space shuttle 10, 000 Linux 1, 500, 000 Windows XP Boeing 777 q 40, 000 7, 000 A new car contains more LOC than was required to land the Apollo astronauts on the moon Intro to Information Security 82
Complexity q “Complexity is the enemy of security”, Paul Kocher, Cryptography Research, Inc. system Lines of code (LOC) Netscape 17, 000 Space shuttle 10, 000 Linux 1, 500, 000 Windows XP Boeing 777 q 40, 000 7, 000 A new car contains more LOC than was required to land the Apollo astronauts on the moon Intro to Information Security 82
 Buffer Overflow Attack Scenario Users enter data into a Web form q Web form is sent to server q Server writes data to buffer, without checking length of input data q Data overflows from buffer q Sometimes, overflow can enable an attack q Web form attack could be carried out by anyone with an Internet connection q Intro to Information Security 83
Buffer Overflow Attack Scenario Users enter data into a Web form q Web form is sent to server q Server writes data to buffer, without checking length of input data q Data overflows from buffer q Sometimes, overflow can enable an attack q Web form attack could be carried out by anyone with an Internet connection q Intro to Information Security 83
![Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when](https://present5.com/presentation/87b85115d6672723922a181c64a66fc3/image-84.jpg) Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when this is executed? q A: Depending on what resides in memory at location “buffer[20]” q o Might overwrite user data or code o Might overwrite system data or code Intro to Information Security 84
Buffer Overflow int main(){ int buffer[10]; buffer[20] = 37; } Q: What happens when this is executed? q A: Depending on what resides in memory at location “buffer[20]” q o Might overwrite user data or code o Might overwrite system data or code Intro to Information Security 84
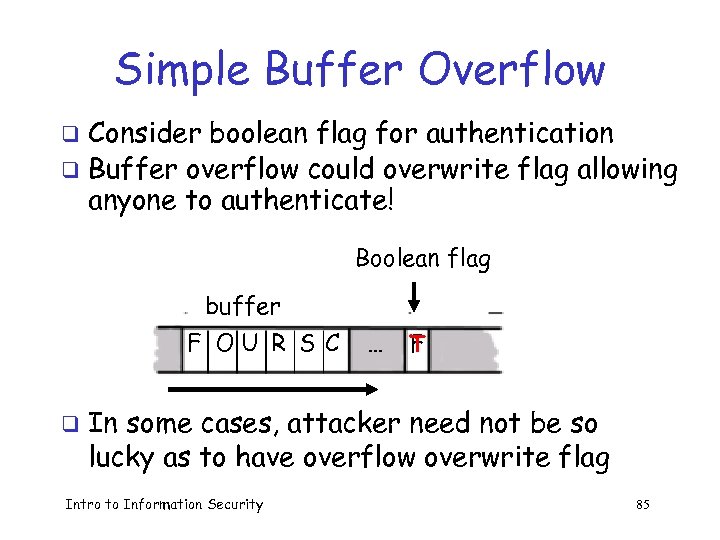 Simple Buffer Overflow Consider boolean flag for authentication q Buffer overflow could overwrite flag allowing anyone to authenticate! q Boolean flag buffer F OU R S C q … T F In some cases, attacker need not be so lucky as to have overflow overwrite flag Intro to Information Security 85
Simple Buffer Overflow Consider boolean flag for authentication q Buffer overflow could overwrite flag allowing anyone to authenticate! q Boolean flag buffer F OU R S C q … T F In some cases, attacker need not be so lucky as to have overflow overwrite flag Intro to Information Security 85
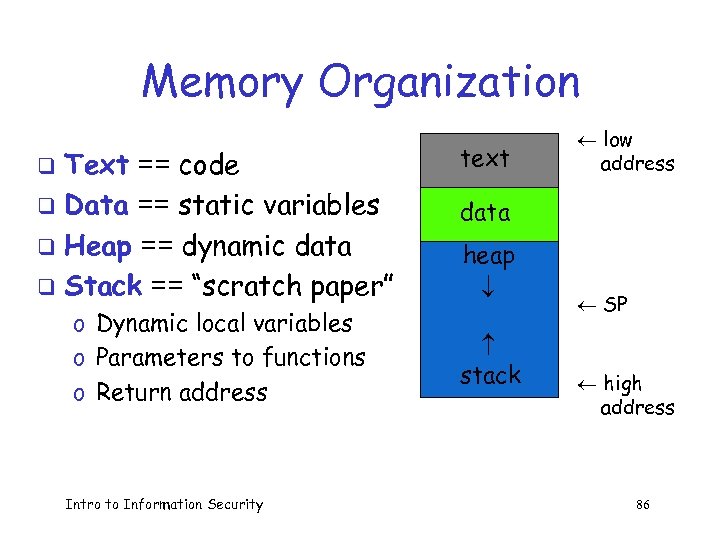 Memory Organization Text == code q Data == static variables q Heap == dynamic data q Stack == “scratch paper” q o Dynamic local variables o Parameters to functions o Return address Intro to Information Security text ¬ low address data heap stack ¬ SP ¬ high address 86
Memory Organization Text == code q Data == static variables q Heap == dynamic data q Stack == “scratch paper” q o Dynamic local variables o Parameters to functions o Return address Intro to Information Security text ¬ low address data heap stack ¬ SP ¬ high address 86
![Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; } Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; }](https://present5.com/presentation/87b85115d6672723922a181c64a66fc3/image-87.jpg) Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; } void main(){ func(1, 2); } buffer high Intro to Information Security ret a b ¬ SP ¬ return SP address ¬ SP 87
Simplified Stack Example low : : void func(int a, int b){ char buffer[10]; } void main(){ func(1, 2); } buffer high Intro to Information Security ret a b ¬ SP ¬ return SP address ¬ SP 87
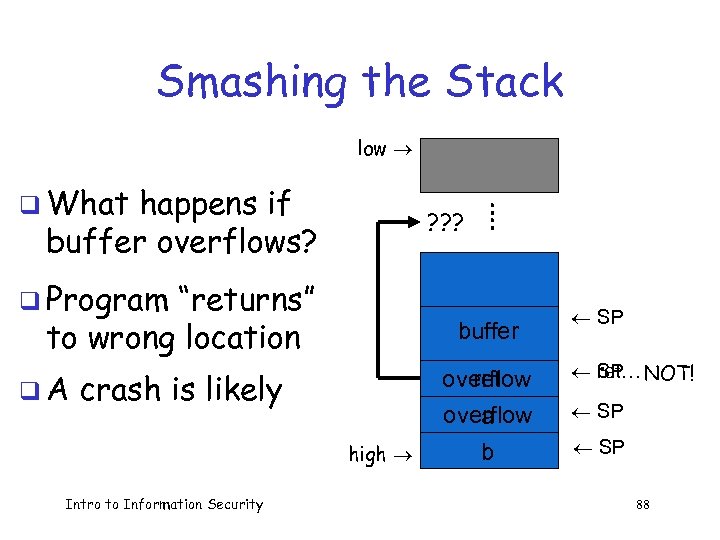 Smashing the Stack low q What happens if buffer overflows? : ? ? ? : q Program “returns” to wrong location q. A buffer crash is likely overflow ret overflow a high Intro to Information Security b ¬ SP ¬ ret… NOT! SP ¬ SP 88
Smashing the Stack low q What happens if buffer overflows? : ? ? ? : q Program “returns” to wrong location q. A buffer crash is likely overflow ret overflow a high Intro to Information Security b ¬ SP ¬ ret… NOT! SP ¬ SP 88
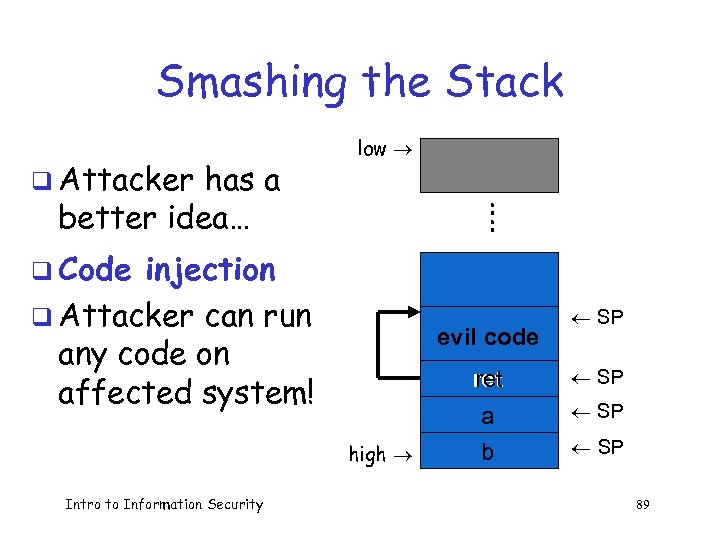 Smashing the Stack q Attacker has a better idea… low : : q Code injection q Attacker can run any code on affected system! evil code ret high Intro to Information Security ¬ SP a b ¬ SP 89
Smashing the Stack q Attacker has a better idea… low : : q Code injection q Attacker can run any code on affected system! evil code ret high Intro to Information Security ¬ SP a b ¬ SP 89
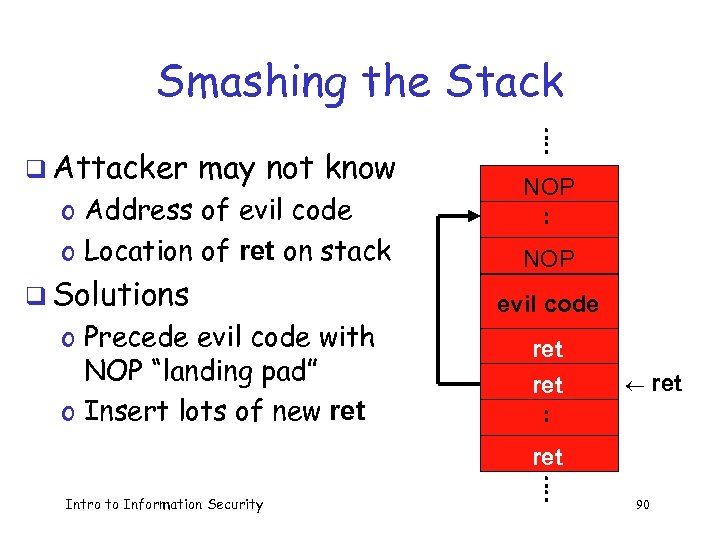 Smashing the Stack q Attacker may not know o Address of evil code o Location of ret on stack q Solutions o Precede evil code with NOP “landing pad” o Insert lots of new ret Intro to Information Security : : NOP evil code ret : : ¬ ret 90
Smashing the Stack q Attacker may not know o Address of evil code o Location of ret on stack q Solutions o Precede evil code with NOP “landing pad” o Insert lots of new ret Intro to Information Security : : NOP evil code ret : : ¬ ret 90
 Stack Smashing Summary A buffer overflow must exist in the code q Not all buffer overflows are exploitable q o Things must line up correctly If exploitable, attacker can inject code q Trial and error likely required q o Lots of help available online o Smashing the Stack for Fun and Profit, Aleph One Also possible to overflow the heap q Stack smashing is “attack of the decade” q Intro to Information Security 91
Stack Smashing Summary A buffer overflow must exist in the code q Not all buffer overflows are exploitable q o Things must line up correctly If exploitable, attacker can inject code q Trial and error likely required q o Lots of help available online o Smashing the Stack for Fun and Profit, Aleph One Also possible to overflow the heap q Stack smashing is “attack of the decade” q Intro to Information Security 91
 Stack Smashing Example Program asks for a serial number that the attacker does not know q Attacker also does not have source code q Attacker does have the executable (exe) q q Program quits on incorrect serial number Intro to Information Security 92
Stack Smashing Example Program asks for a serial number that the attacker does not know q Attacker also does not have source code q Attacker does have the executable (exe) q q Program quits on incorrect serial number Intro to Information Security 92
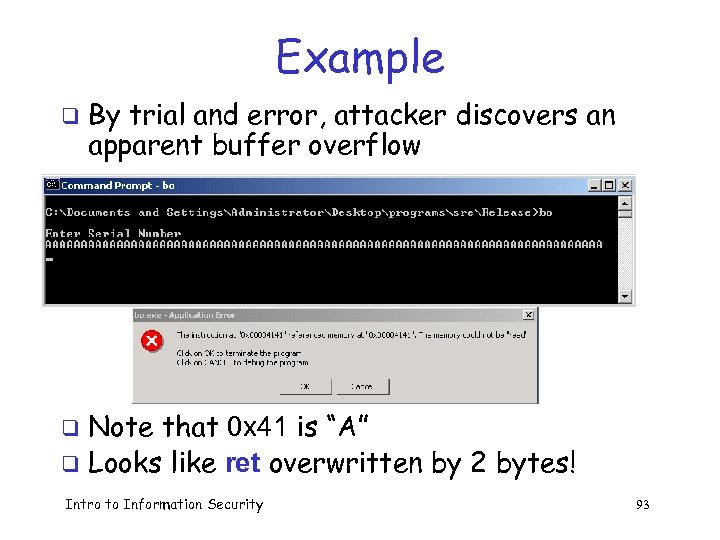 Example q By trial and error, attacker discovers an apparent buffer overflow Note that 0 x 41 is “A” q Looks like ret overwritten by 2 bytes! q Intro to Information Security 93
Example q By trial and error, attacker discovers an apparent buffer overflow Note that 0 x 41 is “A” q Looks like ret overwritten by 2 bytes! q Intro to Information Security 93
 Example q Next, disassemble bo. exe to find q The goal is to exploit buffer overflow to jump to address 0 x 401034 Intro to Information Security 94
Example q Next, disassemble bo. exe to find q The goal is to exploit buffer overflow to jump to address 0 x 401034 Intro to Information Security 94
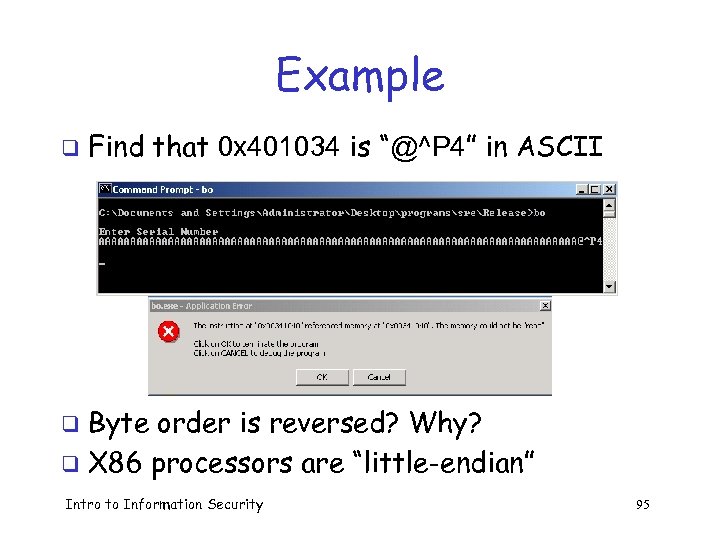 Example q Find that 0 x 401034 is “@^P 4” in ASCII Byte order is reversed? Why? q X 86 processors are “little-endian” q Intro to Information Security 95
Example q Find that 0 x 401034 is “@^P 4” in ASCII Byte order is reversed? Why? q X 86 processors are “little-endian” q Intro to Information Security 95
 Example q Reverse the byte order to “ 4^P@” and… Success! We’ve bypassed serial number check by exploiting a buffer overflow q Overwrote the return address on the stack q Intro to Information Security 96
Example q Reverse the byte order to “ 4^P@” and… Success! We’ve bypassed serial number check by exploiting a buffer overflow q Overwrote the return address on the stack q Intro to Information Security 96
 Example q Attacker did not require access to the source code q Only tool used was a disassembler to determine address to jump to o Can find address by trial and error o Necessary if attacker does not have exe o For example, a remote attack Intro to Information Security 97
Example q Attacker did not require access to the source code q Only tool used was a disassembler to determine address to jump to o Can find address by trial and error o Necessary if attacker does not have exe o For example, a remote attack Intro to Information Security 97
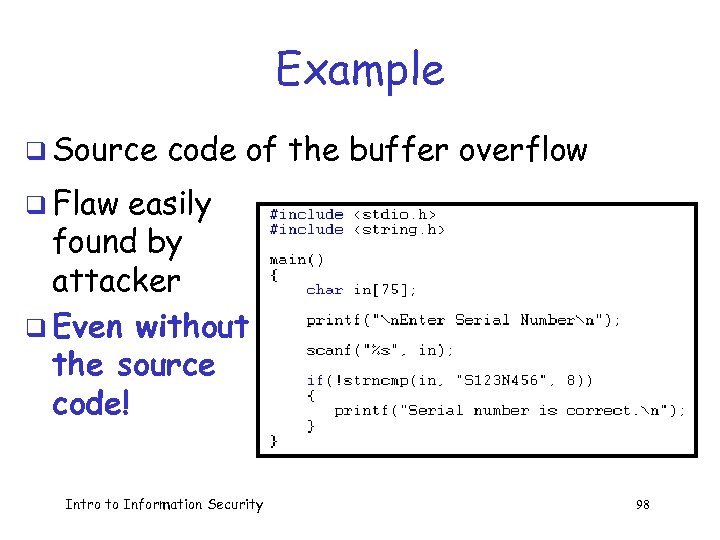 Example q Source code of the buffer overflow q Flaw easily found by attacker q Even without the source code! Intro to Information Security 98
Example q Source code of the buffer overflow q Flaw easily found by attacker q Even without the source code! Intro to Information Security 98
 Malicious Software q q Malware is not new! Fred Cohen’s initial virus work in 1980’s o o o q Used viruses to break MLS systems Virus passive propagation Worm active propagation Trojan horse unexpected functionality Trapdoor/backdoor unauthorized access Rabbit exhaust system resources Types of malware (lots of overlap) Intro to Information Security 99
Malicious Software q q Malware is not new! Fred Cohen’s initial virus work in 1980’s o o o q Used viruses to break MLS systems Virus passive propagation Worm active propagation Trojan horse unexpected functionality Trapdoor/backdoor unauthorized access Rabbit exhaust system resources Types of malware (lots of overlap) Intro to Information Security 99
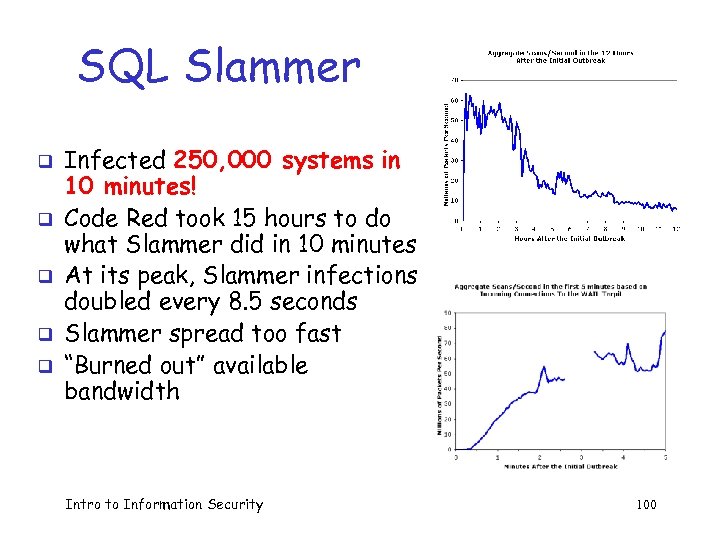 SQL Slammer q q q Infected 250, 000 systems in 10 minutes! Code Red took 15 hours to do what Slammer did in 10 minutes At its peak, Slammer infections doubled every 8. 5 seconds Slammer spread too fast “Burned out” available bandwidth Intro to Information Security 100
SQL Slammer q q q Infected 250, 000 systems in 10 minutes! Code Red took 15 hours to do what Slammer did in 10 minutes At its peak, Slammer infections doubled every 8. 5 seconds Slammer spread too fast “Burned out” available bandwidth Intro to Information Security 100
 SQL Slammer q Why was Slammer so successful? o Worm fit in one 376 byte UDP packet o Firewalls often let small packet thru, assuming it could do no harm by itself o Then firewall monitors the connection o Expectation was that much more data would be required for an attack o Slammer defied assumptions of “experts” Intro to Information Security 101
SQL Slammer q Why was Slammer so successful? o Worm fit in one 376 byte UDP packet o Firewalls often let small packet thru, assuming it could do no harm by itself o Then firewall monitors the connection o Expectation was that much more data would be required for an attack o Slammer defied assumptions of “experts” Intro to Information Security 101
 Polymorphic Malware Polymorphic worm (usually) encrypted q New key is used each time worm propagates q o o q The encryption is weak (repeated XOR) Worm body has no fixed signature Worm must include code to decrypt itself Signature detection searches for decrypt code Detectable by signature-based method o Though more challenging than non-polymorphic… Intro to Information Security 102
Polymorphic Malware Polymorphic worm (usually) encrypted q New key is used each time worm propagates q o o q The encryption is weak (repeated XOR) Worm body has no fixed signature Worm must include code to decrypt itself Signature detection searches for decrypt code Detectable by signature-based method o Though more challenging than non-polymorphic… Intro to Information Security 102
 Metamorphic Malware A metamorphic worm mutates before infecting a new system q Such a worm can avoid signature-based detection systems q The mutated worm must do the same thing as the original q And it must be “different enough” to avoid detection q Detection is currently unsolved problem q Intro to Information Security 103
Metamorphic Malware A metamorphic worm mutates before infecting a new system q Such a worm can avoid signature-based detection systems q The mutated worm must do the same thing as the original q And it must be “different enough” to avoid detection q Detection is currently unsolved problem q Intro to Information Security 103
 Metamorphic Worm To replicate, the worm is disassembled q Worm is stripped to a base form q Random variations inserted into code q o Rearrange jumps o Insert dead code o Many other possibilities Assemble the resulting code q Result is a worm with same functionality as original, but very different signature q Intro to Information Security 104
Metamorphic Worm To replicate, the worm is disassembled q Worm is stripped to a base form q Random variations inserted into code q o Rearrange jumps o Insert dead code o Many other possibilities Assemble the resulting code q Result is a worm with same functionality as original, but very different signature q Intro to Information Security 104
 Warhol Worm “In the future everybody will be worldfamous for 15 minutes” Andy Warhol q A Warhol Worm is designed to infect the entire Internet in 15 minutes q Slammer infected 250, 000 systems in 10 minutes q o “Burned out” bandwidth o Slammer could not have infected all of Internet in 15 minutes too bandwidth intensive q Can a worm do “better” than Slammer? Intro to Information Security 105
Warhol Worm “In the future everybody will be worldfamous for 15 minutes” Andy Warhol q A Warhol Worm is designed to infect the entire Internet in 15 minutes q Slammer infected 250, 000 systems in 10 minutes q o “Burned out” bandwidth o Slammer could not have infected all of Internet in 15 minutes too bandwidth intensive q Can a worm do “better” than Slammer? Intro to Information Security 105
 Warhol Worm One approach to a Warhol worm… q Seed worm with an initial hit list containing a set of vulnerable IP addresses q o Depends on the particular exploit o Tools exist for finding vulnerable systems Each successful initial infection would attack selected part of IP address space q No worm this sophisticated has yet been seen in the wild (as of 2004) q o Slammer generated random IP addresses q Could infect entire Internet in 15 minutes! Intro to Information Security 106
Warhol Worm One approach to a Warhol worm… q Seed worm with an initial hit list containing a set of vulnerable IP addresses q o Depends on the particular exploit o Tools exist for finding vulnerable systems Each successful initial infection would attack selected part of IP address space q No worm this sophisticated has yet been seen in the wild (as of 2004) q o Slammer generated random IP addresses q Could infect entire Internet in 15 minutes! Intro to Information Security 106
 Flash Worm Possible to do “better” than Warhol worm? q Can entire Internet be attacked in < 15 min? q Searching for vulnerable IP addresses is slow part of any worm attack q Searching might be bandwidth limited q o Like Slammer q A “flash worm” is designed to infect entire Internet almost instantly Intro to Information Security 107
Flash Worm Possible to do “better” than Warhol worm? q Can entire Internet be attacked in < 15 min? q Searching for vulnerable IP addresses is slow part of any worm attack q Searching might be bandwidth limited q o Like Slammer q A “flash worm” is designed to infect entire Internet almost instantly Intro to Information Security 107
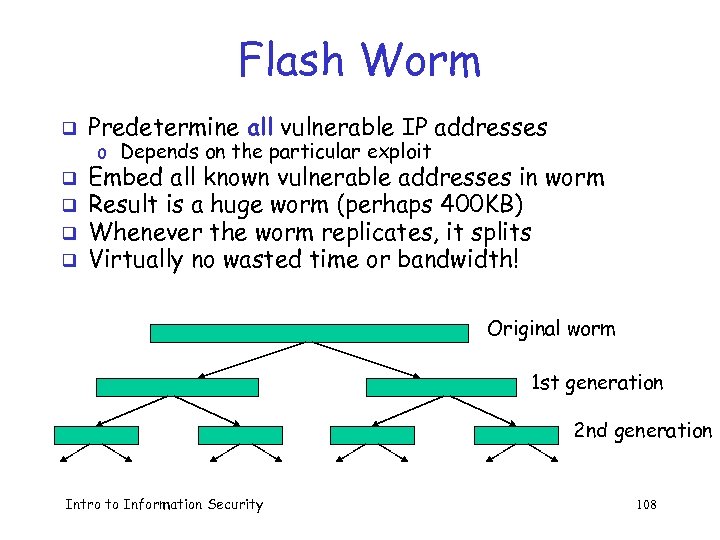 Flash Worm q Predetermine all vulnerable IP addresses q q Embed all known vulnerable addresses in worm Result is a huge worm (perhaps 400 KB) Whenever the worm replicates, it splits Virtually no wasted time or bandwidth! o Depends on the particular exploit Original worm 1 st generation 2 nd generation Intro to Information Security 108
Flash Worm q Predetermine all vulnerable IP addresses q q Embed all known vulnerable addresses in worm Result is a huge worm (perhaps 400 KB) Whenever the worm replicates, it splits Virtually no wasted time or bandwidth! o Depends on the particular exploit Original worm 1 st generation 2 nd generation Intro to Information Security 108
 Flash Worm Estimated that an ideal flash worm could infect the entire Internet in 15 seconds! q Much faster than humans could respond q How to defend against this? q Intro to Information Security 109
Flash Worm Estimated that an ideal flash worm could infect the entire Internet in 15 seconds! q Much faster than humans could respond q How to defend against this? q Intro to Information Security 109


