63348325d4ffdef530b007be7e558a84.ppt
- Количество слайдов: 25
 Introduction to Information Security Management ISM
Introduction to Information Security Management ISM
 Agenda Introduction Physical Security Access Control Cyber Laws Risk Management Framework Procedures / Authorization Preparation Phase
Agenda Introduction Physical Security Access Control Cyber Laws Risk Management Framework Procedures / Authorization Preparation Phase

 Why is Security Difficult • Lack of Cyber Awareness • Technical Capabilities to simulate hacking scenarios and architect defensive approach Expertise Data Retention • Accurate segregation of data based on Confidentiality, Integrity and Availability • Complexity of Cyber Law and its implications Legal
Why is Security Difficult • Lack of Cyber Awareness • Technical Capabilities to simulate hacking scenarios and architect defensive approach Expertise Data Retention • Accurate segregation of data based on Confidentiality, Integrity and Availability • Complexity of Cyber Law and its implications Legal
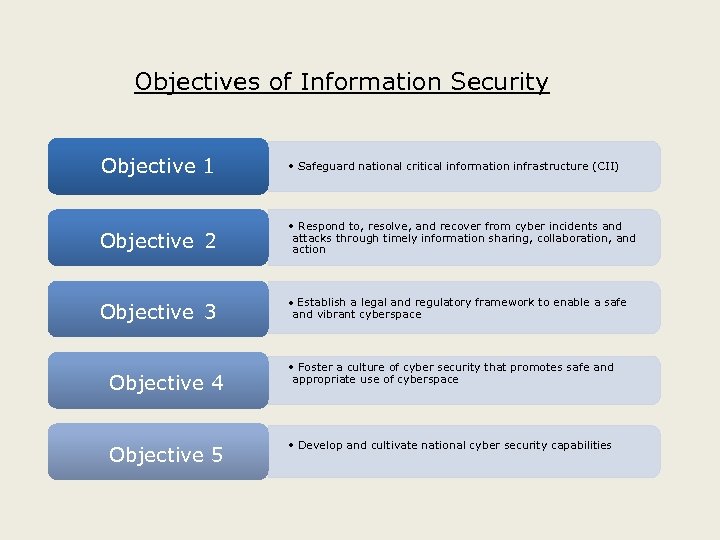 Objectives of Information Security Objective 1 • Safeguard national critical information infrastructure (CII) Objective 2 • Respond to, resolve, and recover from cyber incidents and attacks through timely information sharing, collaboration, and action Objective 3 • Establish a legal and regulatory framework to enable a safe and vibrant cyberspace Objective 4 • Foster a culture of cyber security that promotes safe and appropriate use of cyberspace Objective 5 • Develop and cultivate national cyber security capabilities
Objectives of Information Security Objective 1 • Safeguard national critical information infrastructure (CII) Objective 2 • Respond to, resolve, and recover from cyber incidents and attacks through timely information sharing, collaboration, and action Objective 3 • Establish a legal and regulatory framework to enable a safe and vibrant cyberspace Objective 4 • Foster a culture of cyber security that promotes safe and appropriate use of cyberspace Objective 5 • Develop and cultivate national cyber security capabilities
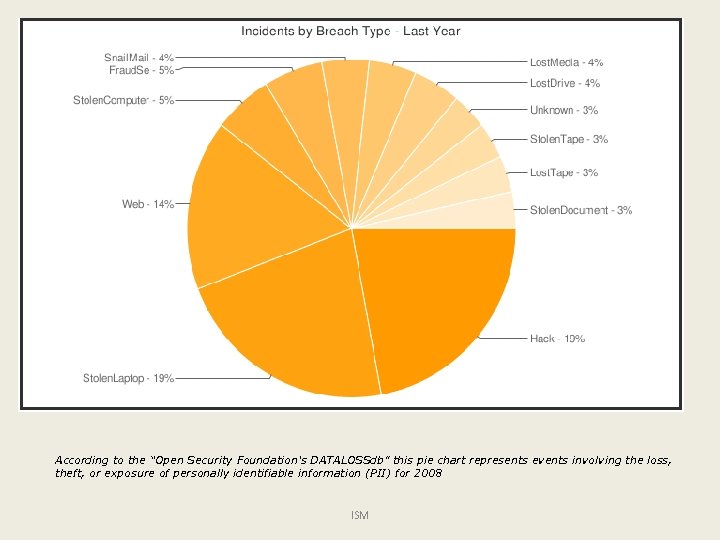 According to the “Open Security Foundation's DATALOSSdb” this pie chart represents events involving the loss, theft, or exposure of personally identifiable information (PII) for 2008 ISM
According to the “Open Security Foundation's DATALOSSdb” this pie chart represents events involving the loss, theft, or exposure of personally identifiable information (PII) for 2008 ISM
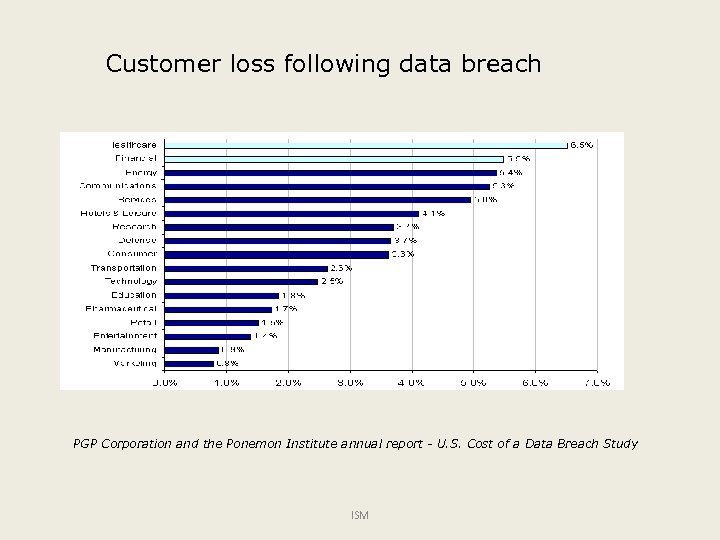 Customer loss following data breach PGP Corporation and the Ponemon Institute annual report - U. S. Cost of a Data Breach Study ISM
Customer loss following data breach PGP Corporation and the Ponemon Institute annual report - U. S. Cost of a Data Breach Study ISM
 Cyber Security
Cyber Security
 Key Definitions Information System • A discrete set of information resources organized for the collection, processing, maintenance, use, sharing, dissemination, or disposition of information Security Authorization • The testing and/or evaluation of management, operational, and technical security controls in an information system to determine the extent to which the controls are implemented correctly, operating as intended and producing the desired outcome with respect to meeting security requirements for the system Security Control Assessment • The testing and/or evaluation of the management, operational, and technical security controls in an information system to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system Security Authorization Boundary • All components of an information system to be authorized for operation by an authorizing official and excludes separately authorized systems, to which the information system is connected Plan of Action and Milestones • A document that identifies tasks needing to be accomplished, resources required to accomplish the elements of the plan, any milestones in meeting the tasks, and scheduled completion dates for the milestones Security Plan • Formal document that provides an overview of the security requirements for the information system and describes the security controls in place or planned for meeting those requirements List not all inclusive – See NIST SP 800 -37, Appendix B for more detailed list
Key Definitions Information System • A discrete set of information resources organized for the collection, processing, maintenance, use, sharing, dissemination, or disposition of information Security Authorization • The testing and/or evaluation of management, operational, and technical security controls in an information system to determine the extent to which the controls are implemented correctly, operating as intended and producing the desired outcome with respect to meeting security requirements for the system Security Control Assessment • The testing and/or evaluation of the management, operational, and technical security controls in an information system to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system Security Authorization Boundary • All components of an information system to be authorized for operation by an authorizing official and excludes separately authorized systems, to which the information system is connected Plan of Action and Milestones • A document that identifies tasks needing to be accomplished, resources required to accomplish the elements of the plan, any milestones in meeting the tasks, and scheduled completion dates for the milestones Security Plan • Formal document that provides an overview of the security requirements for the information system and describes the security controls in place or planned for meeting those requirements List not all inclusive – See NIST SP 800 -37, Appendix B for more detailed list
 Regulatory & Industry Requirements Payment Card Industry (PCI) Requirement # 6 – Develop and maintain secure systems and applications Requirement # 6. 6 – Application security assessment Health Insurance Portability and Accountability Act (HIPAA) § 164. 308 Administrative Safeguards (a)(1)(ii)(A) Risk Analysis Gramm-Leach-Bliley Act (GLBA) Manage & Control Risk requirement Federal Financial Institutions Examination Council (FFIEC) Information Security Booklet -Information Security Risk Assessment -Systems Development, Acquisition, and Maintenance Sarbanes-Oxley (SOX) Section 404, Management Requirements PCAOB Auditing Standard No. 2 Federal Information Security Management Act (FISMA) § 3544. Federal agency responsibilities IRS Publication 1075, Tax Information Security Guidelines for Federal, State and Local Agencies & Entities CA -1 Certification, Accreditation, and Security Assessment Policies and Procedures Federal Energy Regulatory Commission (FERC) – 18 CFR Part 40, Mandatory Reliability Standards for Critical Infrastructure Protection CIP-007 -1 – Cyber Security – Systems Security Management Government Accounting Office (GAO) Federal Information System Controls Audit Manual (FISCAM) Chapter 4 - Evaluating and Testing Business Process Application Controls ISM
Regulatory & Industry Requirements Payment Card Industry (PCI) Requirement # 6 – Develop and maintain secure systems and applications Requirement # 6. 6 – Application security assessment Health Insurance Portability and Accountability Act (HIPAA) § 164. 308 Administrative Safeguards (a)(1)(ii)(A) Risk Analysis Gramm-Leach-Bliley Act (GLBA) Manage & Control Risk requirement Federal Financial Institutions Examination Council (FFIEC) Information Security Booklet -Information Security Risk Assessment -Systems Development, Acquisition, and Maintenance Sarbanes-Oxley (SOX) Section 404, Management Requirements PCAOB Auditing Standard No. 2 Federal Information Security Management Act (FISMA) § 3544. Federal agency responsibilities IRS Publication 1075, Tax Information Security Guidelines for Federal, State and Local Agencies & Entities CA -1 Certification, Accreditation, and Security Assessment Policies and Procedures Federal Energy Regulatory Commission (FERC) – 18 CFR Part 40, Mandatory Reliability Standards for Critical Infrastructure Protection CIP-007 -1 – Cyber Security – Systems Security Management Government Accounting Office (GAO) Federal Information System Controls Audit Manual (FISCAM) Chapter 4 - Evaluating and Testing Business Process Application Controls ISM
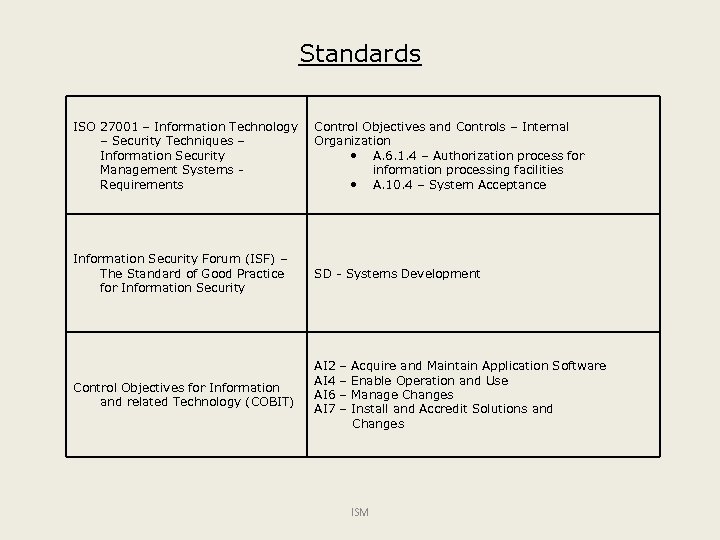 Standards ISO 27001 – Information Technology – Security Techniques – Information Security Management Systems - Requirements Control Objectives and Controls – Internal Organization • A. 6. 1. 4 – Authorization process for information processing facilities • A. 10. 4 – System Acceptance Information Security Forum (ISF) – The Standard of Good Practice for Information Security SD - Systems Development Control Objectives for Information and related Technology (COBIT) AI 2 – Acquire and Maintain Application Software AI 4 – Enable Operation and Use AI 6 – Manage Changes AI 7 – Install and Accredit Solutions and Changes ISM
Standards ISO 27001 – Information Technology – Security Techniques – Information Security Management Systems - Requirements Control Objectives and Controls – Internal Organization • A. 6. 1. 4 – Authorization process for information processing facilities • A. 10. 4 – System Acceptance Information Security Forum (ISF) – The Standard of Good Practice for Information Security SD - Systems Development Control Objectives for Information and related Technology (COBIT) AI 2 – Acquire and Maintain Application Software AI 4 – Enable Operation and Use AI 6 – Manage Changes AI 7 – Install and Accredit Solutions and Changes ISM
 STATE BANK : BPRD Circular No. 07 of 2016 Prevention against Cyber Attacks • The Board shall, preferably on bi-annual basis, evaluate the adequacy of Banks/DFIs/Microfinance Banks’ cyber security action plan with regard to emerging cyber threats. If material gaps are identified, the Board shall ensure that the institution has proper risk management strategy in place for acceptance and controlling the risks arising out of the gaps. The risk management strategy shall be supported by concrete implementation plan with adequate manpower and financial resources to mitigate relevant risks • Senior / Executive Management of the Banks/DFIs/Microfinance Banks shall ensure that an organizational plan of action for cyber security management exists and is reviewed and updated regularly for implementation. Further, senior management shall also periodically inform the Board on the latest developments on cyber security action plan, its implementation status and a summary report on major threats and attacks faced by the institution and their possible impact on its operations.
STATE BANK : BPRD Circular No. 07 of 2016 Prevention against Cyber Attacks • The Board shall, preferably on bi-annual basis, evaluate the adequacy of Banks/DFIs/Microfinance Banks’ cyber security action plan with regard to emerging cyber threats. If material gaps are identified, the Board shall ensure that the institution has proper risk management strategy in place for acceptance and controlling the risks arising out of the gaps. The risk management strategy shall be supported by concrete implementation plan with adequate manpower and financial resources to mitigate relevant risks • Senior / Executive Management of the Banks/DFIs/Microfinance Banks shall ensure that an organizational plan of action for cyber security management exists and is reviewed and updated regularly for implementation. Further, senior management shall also periodically inform the Board on the latest developments on cyber security action plan, its implementation status and a summary report on major threats and attacks faced by the institution and their possible impact on its operations.
 • Risk ownership and management responsibility – Banks/DFIs/Microfinance Banks shall define and establish ownership and management’s responsibility of the risks associated with cyber threats by taking into account the ICT and all relevant business functions. Keeping in view the technical aspects of cyber security management, the Banks/DFIs/Microfinance Banks shall ensure that sufficient resources with relevant skill set and expertise are available within the security function to exercise effective and on-going checks and balances. • Periodic evaluation and monitoring of cyber security controls – Banks/DFIs/Microfinance Banks shall adopt a standard mechanism to ensure that all existing cyber security controls, processes and procedures are continuously being monitored to detect, prevent and respond to any potential cyber security incident in shortest possible time. Further, the Banks/DFIs/Microfinance Banks shall monitor all network communications to detect and/or block unauthorized or atypical network communications amongst servers, systems and endpoint devices.
• Risk ownership and management responsibility – Banks/DFIs/Microfinance Banks shall define and establish ownership and management’s responsibility of the risks associated with cyber threats by taking into account the ICT and all relevant business functions. Keeping in view the technical aspects of cyber security management, the Banks/DFIs/Microfinance Banks shall ensure that sufficient resources with relevant skill set and expertise are available within the security function to exercise effective and on-going checks and balances. • Periodic evaluation and monitoring of cyber security controls – Banks/DFIs/Microfinance Banks shall adopt a standard mechanism to ensure that all existing cyber security controls, processes and procedures are continuously being monitored to detect, prevent and respond to any potential cyber security incident in shortest possible time. Further, the Banks/DFIs/Microfinance Banks shall monitor all network communications to detect and/or block unauthorized or atypical network communications amongst servers, systems and endpoint devices.
 § Regular independent assessment and tests – Banks/DFIs/Microfinance Banks shall ensure that periodic independent assessments are conducted to evaluate the adequacy and effectiveness of cyber security controls and procedures. Such assessments may include vulnerability assessments and penetration testing, which can be conducted by officials independent of the area under review. Where it is not possible to conduct such assessments by internal teams due to unavailability/shortage of skill set, the Banks/DFIs/Microfinance Banks may engage external parties having sufficient expertise in IT security assessments. Further, the Banks/DFIs/Microfinance Banks shall properly enhance and regularly test their Incident Response Mechanism and Business Continuity Plan to prepare for eventualities of cyber attacks. Industry collaboration and contingency plan – Since cyber attacks could aim at multiple institutions within a short period of time, the Banks/DFIs/Microfinance Banks may explore appropriate opportunities of collaborating with other institutions/associations/bodies for sharing and gathering cyber threat intelligence in a timely manner. Such collaboration may help the institutions to prepare for potential cyber attacks
§ Regular independent assessment and tests – Banks/DFIs/Microfinance Banks shall ensure that periodic independent assessments are conducted to evaluate the adequacy and effectiveness of cyber security controls and procedures. Such assessments may include vulnerability assessments and penetration testing, which can be conducted by officials independent of the area under review. Where it is not possible to conduct such assessments by internal teams due to unavailability/shortage of skill set, the Banks/DFIs/Microfinance Banks may engage external parties having sufficient expertise in IT security assessments. Further, the Banks/DFIs/Microfinance Banks shall properly enhance and regularly test their Incident Response Mechanism and Business Continuity Plan to prepare for eventualities of cyber attacks. Industry collaboration and contingency plan – Since cyber attacks could aim at multiple institutions within a short period of time, the Banks/DFIs/Microfinance Banks may explore appropriate opportunities of collaborating with other institutions/associations/bodies for sharing and gathering cyber threat intelligence in a timely manner. Such collaboration may help the institutions to prepare for potential cyber attacks
 Government’s Proposed And Modified Cybercrime Bill 2015 The following act highlights and evaluates access to authorization and intended access to information systems. It communicates the correct utilization of authorization, authentication, transmission, and usage of data. And the consequences of malicious usage of information assets will result in penalties. High level details are mentioned below: • Unauthorized access to information system or data • Unauthorized copying or transmission of data • Interference with information systems or data • Unauthorized access to critical infrastructure information system or data. • Unauthorized copying or transmission of critical infrastructure data. • Interference with critical infrastructure information system or data. • Glorification of an offence. • Cyber terrorism • Hate Speech • Recruitment, funding and planning of terrorism • Electronic forgery • Electronic fraud • Making, obtaining or supplying device for use in offence • Unauthorized use of identify information • Unauthorized issuance of SIM cards • Tampering etc. of communication equipment • Unauthorized interception • Offences against dignity of a natural person and minor • Child Pornography • Malicious code • Cyber Stalking • Spamming • Spoofing
Government’s Proposed And Modified Cybercrime Bill 2015 The following act highlights and evaluates access to authorization and intended access to information systems. It communicates the correct utilization of authorization, authentication, transmission, and usage of data. And the consequences of malicious usage of information assets will result in penalties. High level details are mentioned below: • Unauthorized access to information system or data • Unauthorized copying or transmission of data • Interference with information systems or data • Unauthorized access to critical infrastructure information system or data. • Unauthorized copying or transmission of critical infrastructure data. • Interference with critical infrastructure information system or data. • Glorification of an offence. • Cyber terrorism • Hate Speech • Recruitment, funding and planning of terrorism • Electronic forgery • Electronic fraud • Making, obtaining or supplying device for use in offence • Unauthorized use of identify information • Unauthorized issuance of SIM cards • Tampering etc. of communication equipment • Unauthorized interception • Offences against dignity of a natural person and minor • Child Pornography • Malicious code • Cyber Stalking • Spamming • Spoofing
 Electronic Transaction Ordinance 1999 As per the President Ordinance on fourteenth day of October, 1999, and the Provisional Constitution Order No. 1 of 1999 focuses on the electronic transections and cover following chapters: • RECOGNITION AND PRESUMPTION • ELECTRONIC DOCUMENTS • CERTIFICATION SERVICE PROVIDERS • CERTIFICATION COUNCIL • AMENDMENTS OF CERTAIN LAWS • OTHER LAWS AND JURISDICTION • OFFENCES
Electronic Transaction Ordinance 1999 As per the President Ordinance on fourteenth day of October, 1999, and the Provisional Constitution Order No. 1 of 1999 focuses on the electronic transections and cover following chapters: • RECOGNITION AND PRESUMPTION • ELECTRONIC DOCUMENTS • CERTIFICATION SERVICE PROVIDERS • CERTIFICATION COUNCIL • AMENDMENTS OF CERTAIN LAWS • OTHER LAWS AND JURISDICTION • OFFENCES
 Why Physical Security? • Not all threats are “cyber threats” • Information one commodity that can be stolen without being “taken” • Physically barring access is first line of defense • Forces those concerned to prioritize! • Physical Security can be a deterrent • Security reviews force insights into value of what is being protected
Why Physical Security? • Not all threats are “cyber threats” • Information one commodity that can be stolen without being “taken” • Physically barring access is first line of defense • Forces those concerned to prioritize! • Physical Security can be a deterrent • Security reviews force insights into value of what is being protected
 Layered Security • Physical Barriers • Fences • Alarms • Restricted Access Technology • Physical Restrictions • Air Gapping • Removable Media • Remote Storage • Personnel Security Practices • Limited Access • Training • Consequences/Deterrence
Layered Security • Physical Barriers • Fences • Alarms • Restricted Access Technology • Physical Restrictions • Air Gapping • Removable Media • Remote Storage • Personnel Security Practices • Limited Access • Training • Consequences/Deterrence
 Inner Protective Layers • Several layers • Structure – Door controls, biometrics – Signs, alarms, CCTV’s – Safes, vaults • Environment – Authorized personnel only • Purpose – Establish controlled areas and rooms
Inner Protective Layers • Several layers • Structure – Door controls, biometrics – Signs, alarms, CCTV’s – Safes, vaults • Environment – Authorized personnel only • Purpose – Establish controlled areas and rooms
 Personnel Security Practices • Insider Threat the most serious • Disgruntled employee • Former employee • Agent for hire • Personnel Training • Critical Element • Most often overlooked • Background checks • Critical when access to information required • Must be updated
Personnel Security Practices • Insider Threat the most serious • Disgruntled employee • Former employee • Agent for hire • Personnel Training • Critical Element • Most often overlooked • Background checks • Critical when access to information required • Must be updated
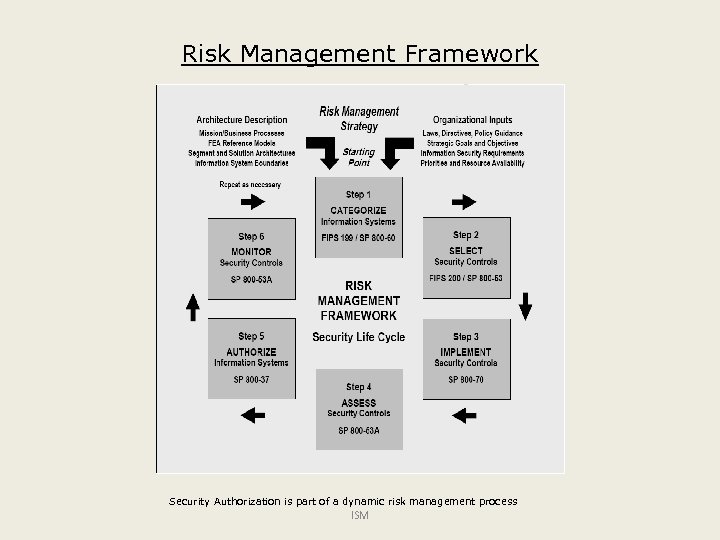 Risk Management Framework Security Authorization is part of a dynamic risk management process ISM
Risk Management Framework Security Authorization is part of a dynamic risk management process ISM
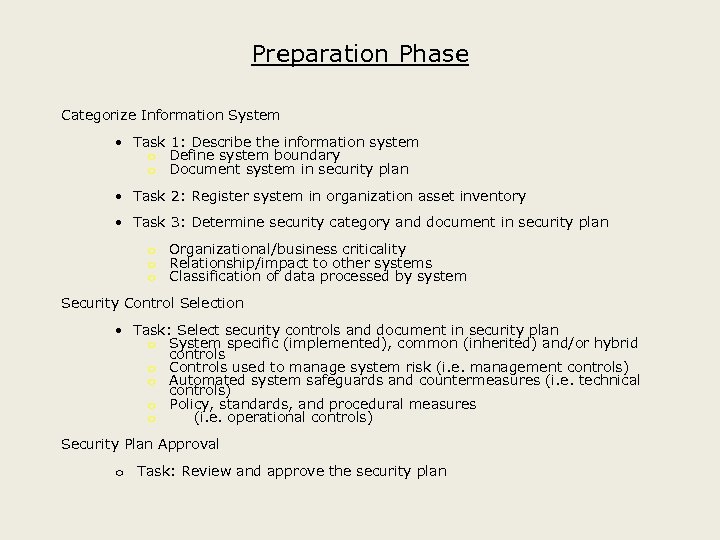 Preparation Phase Categorize Information System • Task 1: Describe the information system o Define system boundary o Document system in security plan • Task 2: Register system in organization asset inventory • Task 3: Determine security category and document in security plan o Organizational/business criticality o Relationship/impact to other systems o Classification of data processed by system Security Control Selection • Task: Select security controls and document in security plan o System specific (implemented), common (inherited) and/or hybrid controls o Controls used to manage system risk (i. e. management controls) o Automated system safeguards and countermeasures (i. e. technical controls) o Policy, standards, and procedural measures o (i. e. operational controls) Security Plan Approval o Task: Review and approve the security plan
Preparation Phase Categorize Information System • Task 1: Describe the information system o Define system boundary o Document system in security plan • Task 2: Register system in organization asset inventory • Task 3: Determine security category and document in security plan o Organizational/business criticality o Relationship/impact to other systems o Classification of data processed by system Security Control Selection • Task: Select security controls and document in security plan o System specific (implemented), common (inherited) and/or hybrid controls o Controls used to manage system risk (i. e. management controls) o Automated system safeguards and countermeasures (i. e. technical controls) o Policy, standards, and procedural measures o (i. e. operational controls) Security Plan Approval o Task: Review and approve the security plan
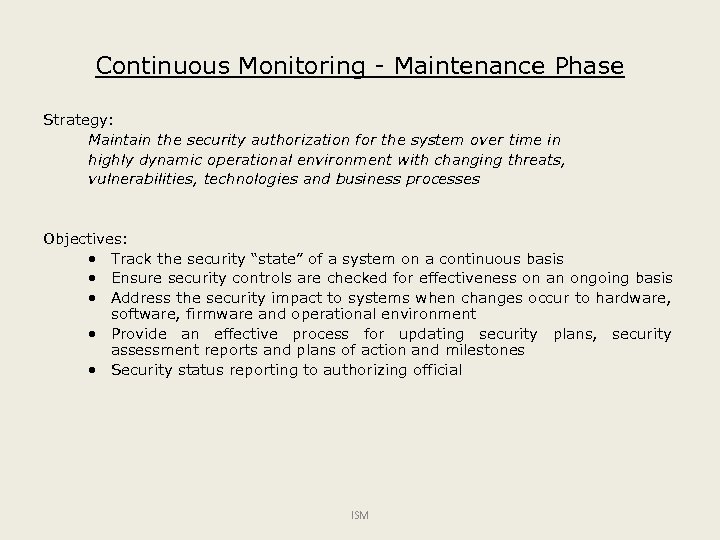 Continuous Monitoring - Maintenance Phase Strategy: Maintain the security authorization for the system over time in highly dynamic operational environment with changing threats, vulnerabilities, technologies and business processes Objectives: • Track the security “state” of a system on a continuous basis • Ensure security controls are checked for effectiveness on an ongoing basis • Address the security impact to systems when changes occur to hardware, software, firmware and operational environment • Provide an effective process for updating security plans, security assessment reports and plans of action and milestones • Security status reporting to authorizing official ISM
Continuous Monitoring - Maintenance Phase Strategy: Maintain the security authorization for the system over time in highly dynamic operational environment with changing threats, vulnerabilities, technologies and business processes Objectives: • Track the security “state” of a system on a continuous basis • Ensure security controls are checked for effectiveness on an ongoing basis • Address the security impact to systems when changes occur to hardware, software, firmware and operational environment • Provide an effective process for updating security plans, security assessment reports and plans of action and milestones • Security status reporting to authorizing official ISM
 Points to Remember • Assess a defined environment (authorization boundary) not the world • Security authorization is an ongoing process • Security control assessors make recommendations, they do not accept risk or approve mitigating controls on behalf of the organization • Risk acceptance is the sole responsibility of the authorizing official • Reuse and share of security control development, implementation, and assessment-related information to reduce cost and time • An active continuous monitoring program reduces time and effort ISM
Points to Remember • Assess a defined environment (authorization boundary) not the world • Security authorization is an ongoing process • Security control assessors make recommendations, they do not accept risk or approve mitigating controls on behalf of the organization • Risk acceptance is the sole responsibility of the authorizing official • Reuse and share of security control development, implementation, and assessment-related information to reduce cost and time • An active continuous monitoring program reduces time and effort ISM


