82100f2e459ccc7d07f7b5904d302f03.ppt
- Количество слайдов: 67

Introduction to Digital Libraries Week 3: Intellectual Property, Economics Old Dominion University Department of Computer Science CS 751/851 Spring 2011 Michael L. Nelson <mln@cs. odu. edu> 01/25/11 ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Intellectual Property (IP) • “Issues related to intellectual property law are the most serious problems facing digital libraries. ” - Lesk, p. 223 – similarly, Gladney’s 1999 D-Lib paper • Economic motivation: – “The U. S. balance of payments in intellectual property is positive by $46 billion, but it is believed that another $15 -17 billion is lost to piracy” - Lesk, p. 235 • Caveat: I am neither a lawyer nor an economist. . . – this lecture guaranteed to be incomplete and incorrect. . . ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Forms of IP Protection • Applicable to DLs: – copyright – patent • Less applicable to DLs: – trade secrets • you must sign a non-disclosure agreement before you can see the information – trademarks • the Internet has caused some issues to be revisited: Sun Oil, Sun Microsystems, Sun Records: who gets www. sun. com? ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Constitutional Provision • Article I, Section 8 lets Congress: – “Clause 8: To promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries; ” • Note primary motivation: to promote progress, not to reward authors! from: http: //www. house. gov/Constitution. html ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Copyright • The purpose of copyright is protect a form of expression and to encourage authors to be prolific • Copyright prevents others from: making copies of your work, providing a public performance of it, or making derivative works ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Copyright • “Copyright does not protect useful objects. In fact, if something is useful, that will be a legal argument that it should not be protected by copyright. Nor does it protect ideas, as opposed to the way they are expressed. ” - Lesk, pp. 225 -226 ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Copyright • Copyright law is in flux, but: – since 1992 you no longer have to explicitly apply for copyright, or display a copyright notice – "Sonny Bono Act": • personal: life + 70 • corporate: min(95 since publication, 120 since authorship) – non-creative work is not copyrightable • e. g. , alphabetizing phonebook entries: – http: //en. wikipedia. org/wiki/Feist_v. _Rural ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
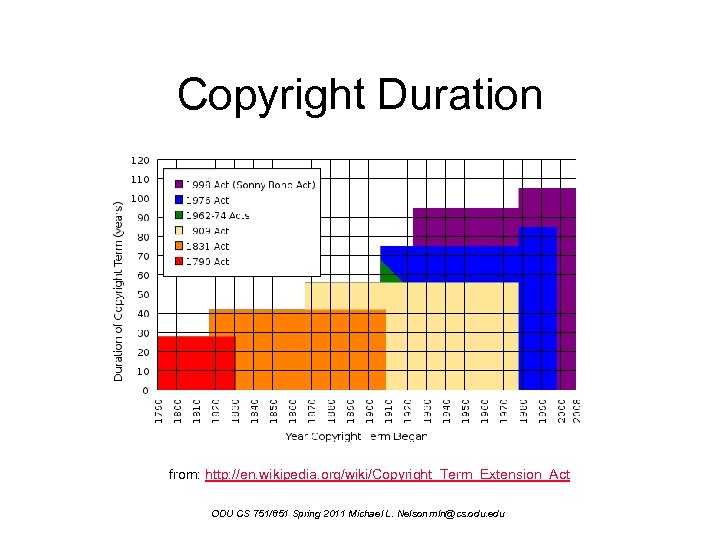
Copyright Duration from: http: //en. wikipedia. org/wiki/Copyright_Term_Extension_Act ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Who Really Controls Copyright in the U. S. ? http: //en. wikipedia. org/wiki/Steamboat_Willie#Copyright ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Life + 70? ! 7+ posthumous LPs http: //en. wikipedia. org/wiki/Tupac_Shakur_discography#Posthumous 10+ posthumous books http: //en. wikipedia. org/wiki/L. _Ron_Hubbard#Bibliography ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
Copyright Crushing My Groove… http: //www. youtube. com/watch? v=z. F 7 y 67 o. Og. FI ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Picking a Fight With This Man… http: //entertainment. howstuffworks. com/music-licensing 3. htm http: //hamptonroads. com/2009/06/suffolk-bar-may-have-back-down-over-copyright-suit ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
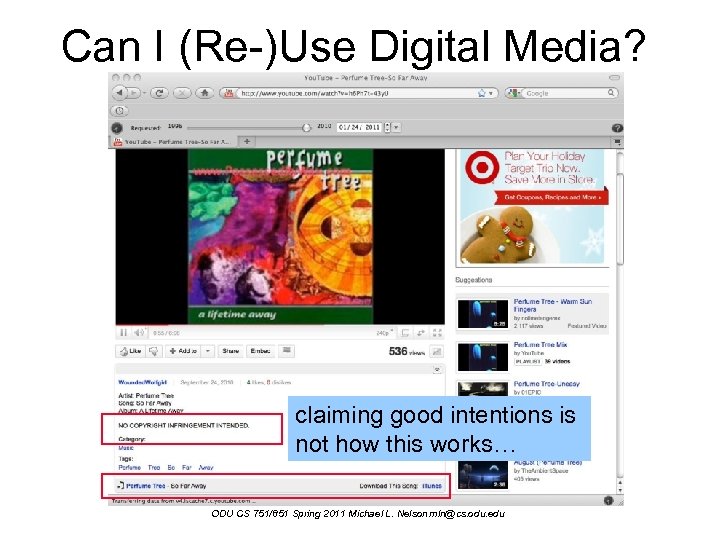
Can I (Re-)Use Digital Media? claiming good intentions is not how this works… ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Fair Use - 17 U. S. C. Sec 107 • Factor 1: Purpose and character of use – commercial or non-profit educational purpose – preamble purpose: criticism, comment, news reporting, teaching, scholarship, research – degree of transformation • Factor 2: Nature of copyrighted work • Factor 3: Relative amount • Factor 4: Effect upon potential market see: http: //fairuse. stanford. edu/Copyright_and_Fair_Use_Overview/chapter 9/9 -b. html see: http: //www. benedict. com/fairtest. htm ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Campbell v. Acuff-Rose Music, Inc. vs. • • http: //en. wikipedia. org/wiki/Campbell_v. _Acuff-Rose_Music, _Inc. http: //www. youtube. com/watch? v=JJjux. Da 9 s. WM ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Patents • “Patents are to protect devices or processes. Patents must cover something useful, new, and not obvious” - Lesk, p. 229 • Patent protect method, not just form of expression or representation (cf. copyright) • Shorter life span: 20 years from filing date ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
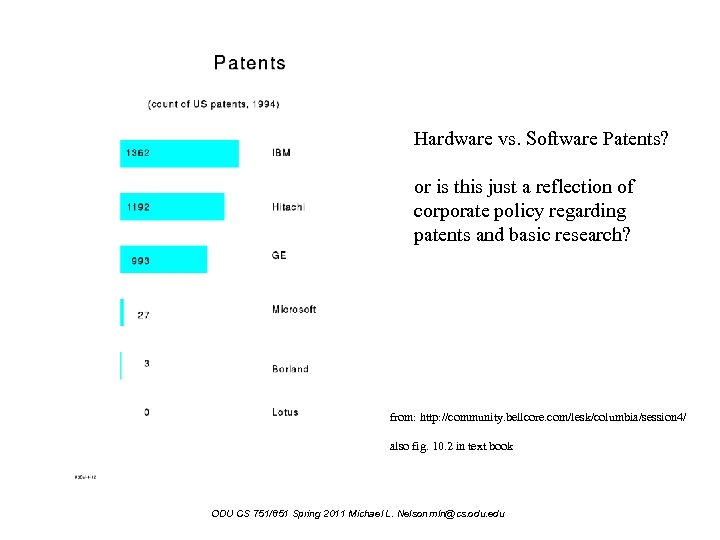
Hardware vs. Software Patents? or is this just a reflection of corporate policy regarding patents and basic research? from: http: //community. bellcore. com/lesk/columbia/session 4/ also fig. 10. 2 in text book ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
1998 - Top 10 Patents source: http: //dailynews. yahoo. com/headlines/tc/story. html? s=v/nm/19990111/tc/patents_1. html For IBM, > 700 patents are s/w related; > 375 are network computing related “software patents now account for as much as 15% of the 120, 000 patents issued annually” - IEEE Software, 16(2), March/April 1999, p. 33 ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
2000 - Top 10 Patents sources: http: //www. baypatents. com/News/news_briefs_display. asp? ID=125 http: //news. cnet. com/news/0 -1003 -200 -4433170. html US. Govt = 920 patents ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

(Preliminary *) 2001 Rank # Patents Organization * ------------- ( Final ) ( Rank ) (in 2000) ----- ( Final ) (# Patents) ( in 2000 ) ----- 1 2 3 4 5 6 7 8 9 10 3, 411 1, 953 1, 877 1, 643 1, 450 1, 440 1, 363 1, 271 1, 184 1, 166 International Business Machines Corp. NEC Corporation Canon Kabushiki Kaisha Micron Technology, Inc. Samsung Electronics Co. , Ltd. Matsushita Electric Industrial Co. , Ltd. Sony Corporation Hitachi, Ltd Mitsubishi Denki Kabushiki Kaisha Fujitsu Limited (1) (2) (3) (7) (4) (11) (6) (13) (14) (10) (2, 886) (2, 021) (1, 890) (1, 304) (1, 441) (1, 137) (1, 385) (1, 036) (1, 010) (1, 147) 11 12 13 14 15 16 17 18 19 20 1, 149 1, 107 1, 086 978 809 793 778 719 Toshiba Corporation Lucent Technologies Inc. General Electric Company Advanced Micro Devices, Inc. Hewlett-Packard Company Intel Corporation Texas Instruments, Incorporated Siemens Aktiengesellschaft Motorola Inc. Eastman Kodak Company (8) (5) (19) (12) (16) (18) (21) (15) (9) (17) 2002 Top Patents (1, 232) (1, 411) (787) (1, 053) (901) (795) (686) (912) (1, 196) (875) 954 U. S. GOVERNMENT from: http: //www. uspto. gov/web/offices/ac/ido/oeip/taf/top 01 cos. htm (928) see also: http: //www. ipo. org/Top 300 -2001. htm ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
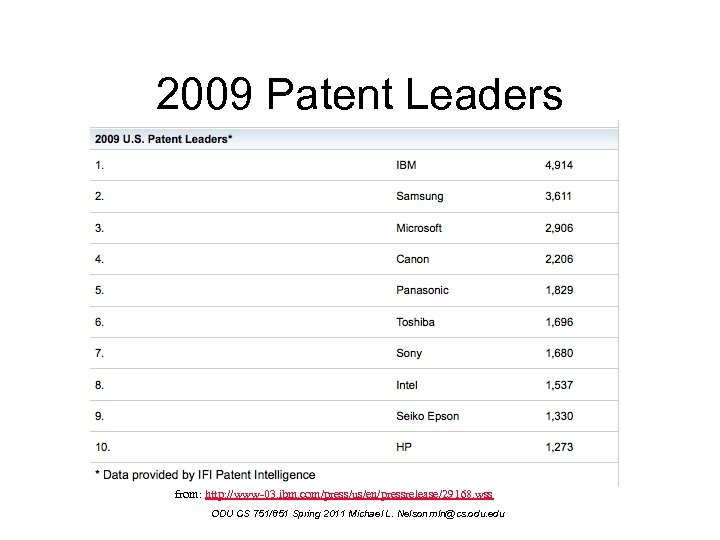
2009 Patent Leaders from: http: //www-03. ibm. com/press/us/en/pressrelease/29168. wss ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
Software: Copyright and Patents • Algorithms, methods, etc. can be patented • Form of expression, representation, source code, etc. can be copyrighted • Submarine / “Time bomb” patent – a popular program / method could be independently created, can be well established, then you discover you have violated a patent! • under old law, patents were 17 years after issue date, not filing date. . . – Pardo (spreadsheet) patent, LZW (GIF) patent – League of Programming Freedom (lpf. ai. mit. edu) fights s/w patents ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

What Happens When the USPTO Snoozes… • "Method and system for placing a purchase order via a communications network" – US Patent 5, 960, 411 – http: //www. google. com/patents? id= O 2 YXAAAAEBAJ – http: //en. wikipedia. org/wiki/1 -Click ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Piracy, Theft, Loss… ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
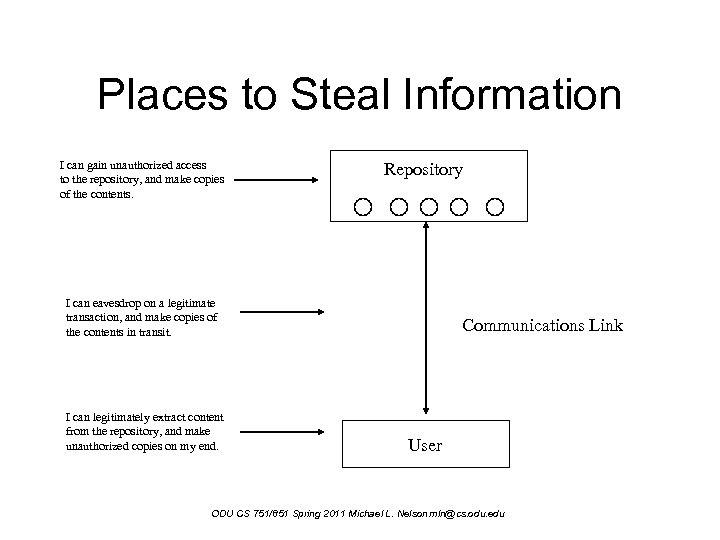
Places to Steal Information I can gain unauthorized access to the repository, and make copies of the contents. Repository I can eavesdrop on a legitimate transaction, and make copies of the contents in transit. I can legitimately extract content from the repository, and make unauthorized copies on my end. Communications Link User ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

IP and Security in a DL Setting • Typical things we would want to do in a DL: – authenticate the user – authenticate the DL – authenticate the contents – secure the contents • storage and transmission – negotiate terms and conditions of use ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Methods of Protection Adapted from Lesk text book and Kohl, Lostpeich, Kaplan, 1997 • Fractional access – information is doled out in small quantities (presumably a small percentage of the total available) – its “hard” to capture enough to information to be useful – e. g. , Google Books • Control of interface – access is only through proprietary interface – WWW is phasing out this approach… – (update: i. Tunes bringing it back…) ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Methods of Protection • Hardware locks / special hardware / dongles – the information (easy to copy) depends on a separate h/w device that is not easily copyable; – or, the output device has a unique key for decryption (audio board, video board, etc. ) • Repositories – keep a list of copyrighted stuff – generate checksums – to see if object X has been copied, compare checksums – e. g. , http: //www. turnitin. com/ ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
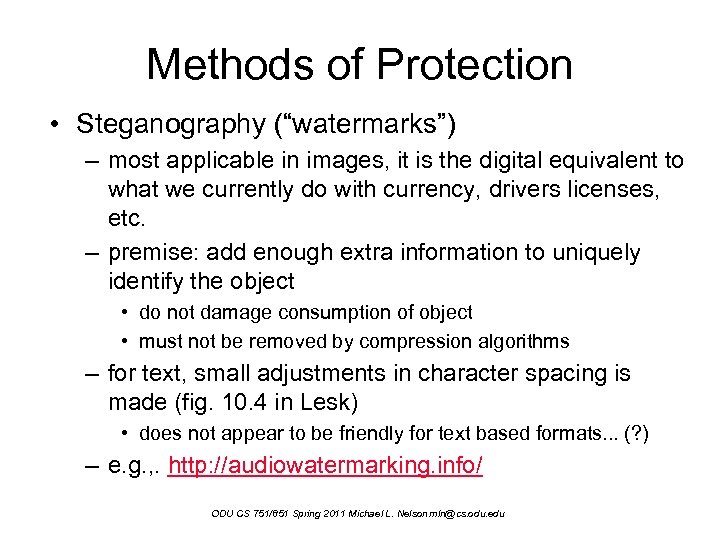
Methods of Protection • Steganography (“watermarks”) – most applicable in images, it is the digital equivalent to what we currently do with currency, drivers licenses, etc. – premise: add enough extra information to uniquely identify the object • do not damage consumption of object • must not be removed by compression algorithms – for text, small adjustments in character spacing is made (fig. 10. 4 in Lesk) • does not appear to be friendly for text based formats. . . (? ) – e. g. , . http: //audiowatermarking. info/ ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Methods of Protection • Economic incentives – make it not worth the time or the effort to steal • provide extra copies very cheap • site licenses • e. g. , i. Tunes – recover costs in other ways • advertising • request donations • e. g. , Radiohead's 2007 LP "In Rainbows" ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Securing the Content and Session • Alternatives more commonly seen in a WWW DL environment are: – securing the session • to protect against eavesdroppers • can also be used to authenticate the repository and the user – securing the content • to protect against copying the object • can also be used to authenticate the object – Can be used together • but first, lets briefly review cryptography. . . ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

A Brief Review of Cryptography • An excellent book is Applied Cryptography, by Bruce Schneier, 1996 • Secret key encryption: – you and I share a single key (typically a password or phrase) that can both encrypt and decrypt a message – trick: must share the key out of band ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Cryptography • Public/Private keys – each party has 2 keys: a public key that they share with the world, and a private key that they share with no one – the 2 keys are linked, so that if I encrypt a message to you with your public key, the only way the message can be decrypted is with your private key • even I, the sender, cannot decrypt the message that I just encrypted – a common example is PGP e-mail • key management becomes the trick. . . ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Digital Signatures • I can add a “signature” to a message (or object) if I encrypt some text with my private key and include it with the message – since my public key widely known, you can decrypt my signature using my public key – since I am the only one that knows my private key, you can safely assume that I am the one that originated the message • no one can generate a signature w/o knowing my private key ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Cryptography • Public/Private keys – use 1 -way hashing functions, based on the premise that large numbers are hard to factor • see Schneier, 1996 for details – public/private is slower than secret • Common trick – pick a secret key, encrypt and exchange that with public/private, and do all the bulk transfer with the symmetric secret key ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Securing the Session • Two common WWW methods of secure communication: – Secure Socket Layer (SSL) • Freier, Karlton, Kocher, 1996 – http: //tools. ietf. org/html/rfc 5246 – http: //en. wikipedia. org/wiki/Transport_Layer_Security • encrypts all network traffic, regardless of protocol (http, smtp, ftp, etc. ) – Secure HTTP ( SHTTP) • Rescorla & Schiffman, 1999 – http: //www. ietf. org/rfc 2660. txt • a superset of http, protects only http traffic • of historical interest only ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Session Security Drawbacks • From a providers point of view, you have protected only against eavesdroppers – if your repository is compromised, your information can be copied – nothing prevents legitimate clients from making local copies too. . . • SSL & SHTTP are not rich enough to express terms and conditions – Review of Rights Expression Languages (REL): • http: //www. loc. gov/standards/relreport. pdf ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Securing the Content • If the content were secured, then it would be safe from repository attacks, eavesdroppers, and local copying. . . – securing the session is not precluded; SSL/SHTTP would still be available for the very paranoid • Moving security higher up the OSI model allows for richer expressions, such as terms and conditions ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
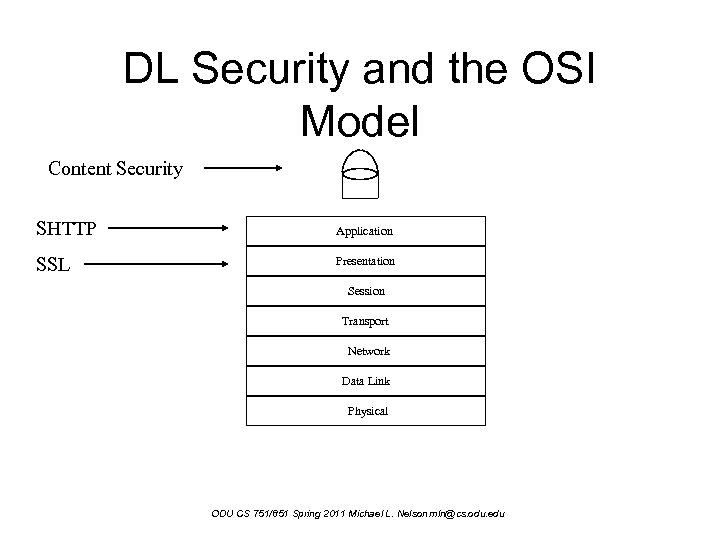
DL Security and the OSI Model Content Security SHTTP Application SSL Presentation Session Transport Network Data Link Physical ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Superdistribution • If the content is secure, then let copies be made! – the content can only be accessed by obtaining the right key, presumably through some authentication/payment mechanism – demo software with significant functionality “turned off” that can be turned on by purchasing a key is an example of superdistribution ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
IBM Cryptolopes • Cryptographic Envelopes – Kohl, Lotspiech & Kaplan, 1997 – used in the IBM info. Market since 1995 • Cryptolopes appear to be an e-business concept repackaged for DLs – similar to Digiboxes in that regard • http: //scholar. google. com/scholar? cluster=1425 0155739809853002 ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
Cryptolope Architecture • Architecture: – manifest: lists all components along w/ their checksums – abstract / metadata: textual description of the cryptolope and its attributes (size, date, etc. ) – encrypted content part: the good stuff • each part has a part encryption key (PEK) – all PEKs are encrypted with a master key ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Cryptolope Architecture – terms and conditions: describe usage and rights of the parts – watermarking: instructions on how to add/decode any watermarks that might be used – digital certificates: signature to prove the authenticity of the cryptolope ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
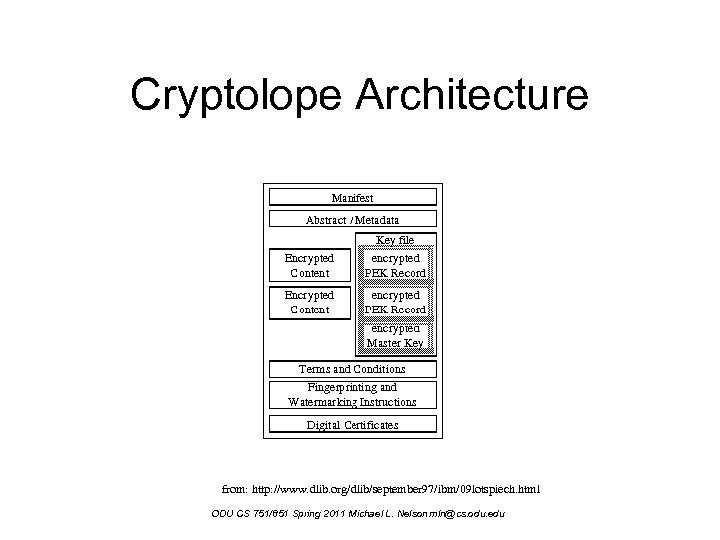
Cryptolope Architecture from: http: //www. dlib. org/dlib/september 97/ibm/09 lotspiech. html ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
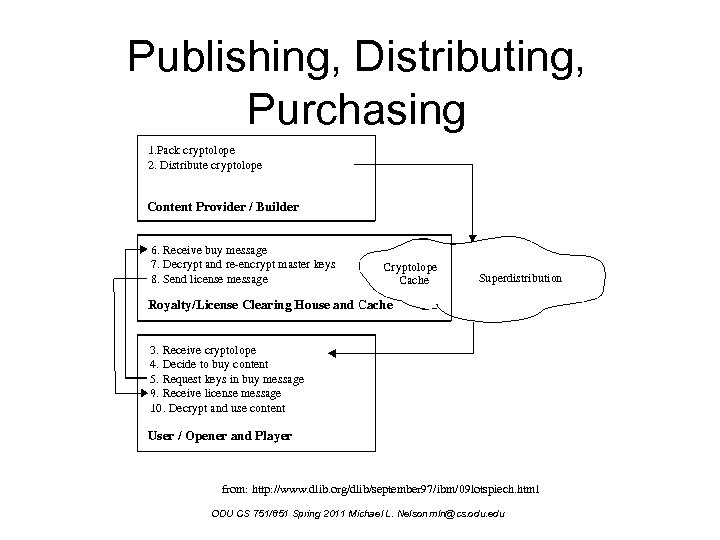
Publishing, Distributing, Purchasing from: http: //www. dlib. org/dlib/september 97/ibm/09 lotspiech. html ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Content Security Advantages • Client verifies document authenticity – not “librarian” • Customer authenticates only to purchasing entity, not to publisher or librarian • Customer drives the messaging / signing process • Checksums and signatures verify integrity of the contents From: Kohl, Lotspiech & Kaplan, 1997 ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Content Security Advantages • The clearing house only “sells” keys; it does not decrypt content – only the purchaser sees the content • Dedicated opener/viewer software for viewing cryptolopes discourages client side copying – the phrase “dedicated software” is almost always bad, and could be considered a showstopper. . . ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Content Security Questions • This technology seems to be sufficient for electronic commerce. . . – if the unit price is $19. 95, there is generally a limit to how much effort you will expend to crack the content • But is it sufficient for classified information? trade secrets? ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
Renting vs. Owning • We are used to “owning” the content, or at least the presentation of the content, in a traditional information sense – the library has control over the hard copy serials in their possession – I have control over the PDF files I have downloaded • Digital media allows for more complex usage agreements ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
Renting vs. Owning • If I get my content from E-Journal projects (e. g. , JSTOR), or purchase keys to unlock objects (e. g. , cryptolopes) there are possible: – advantages: • purchase only the pieces that I need • access to more material than I would normally be able to afford – disadvantages: • will my information persist over time? will the provider raise the cost? go out of business? give poor service (key server frequently down, etc. )? ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Right of First Sale • If I buy a book/CD/DVD/art/etc. , I can do what I want with it: sell, destroy, repurpose, etc. • If I buy software, I'm not really purchasing the software, I'm purchasing a license to use the software • http: //en. wikipedia. org/wiki/First-sale_doctrine ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Does Technology Supercede Laws? http: //www. lessig. org/ ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

The Case Against IP. . . • Most discussions assume that copyright, patents, etc. are unalienable rights – remember that the U. S. constitution allows (not requires) an IP protection mechanism to foster progress, not reward authors • Question: can the economy sustain a world of looser IP protection? – can the information freedom minority only exist within a strong IP protection context? ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

The Case Against IP. . . • Fonts are copyrightable in Europe, but not the U. S. – most font innovation comes from the U. S. (Lesk, p. 224) • Did DATs, CD-Rs, DVDs hurt music CD sales? – did MP 3 s really hurt? – or was the market artificially inflated? • Why are gcc, Apache, Linux, etc. so good? – it is my experience that gcc is always better than the vendor supplied C compilers. . . ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

The Long Tail… • Chris Anderson – http: //www. wired. com/wired/archive/12. 10/tail. html – http: //en. wikipedia. org/wiki/Long_Tail – http: //www. amazon. com/Long-Tail-Future-Business-Selling/dp/1401302378 ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
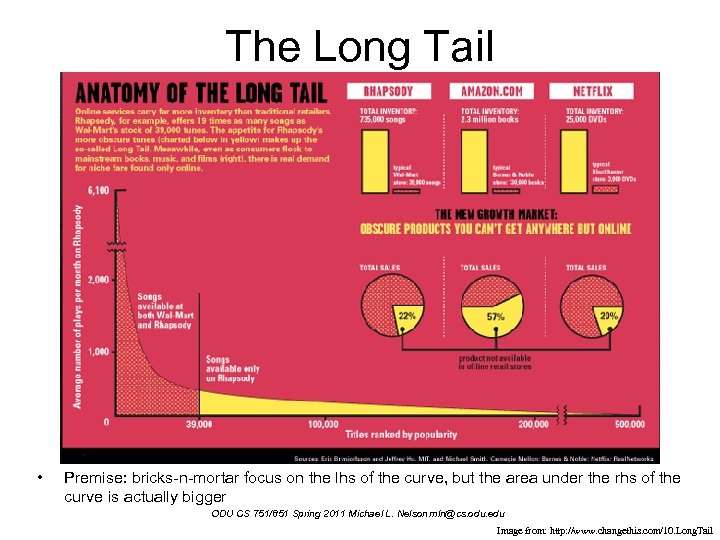
The Long Tail • Premise: bricks-n-mortar focus on the lhs of the curve, but the area under the rhs of the curve is actually bigger ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu Image from: http: //www. changethis. com/10. Long. Tail
“The Cathedral and the Bazaar” • Eric Raymond – old URI: http: //www. firstmonday. dk/issues/issue 3_3/raymond/ – new URI: http: //firstmonday. org/htbin/cgiwrap/bin/ojs/index. php/fm/article/view/578/499 • The canonical text on open source software development – work on s/w you care about – develop a user community & co-developers • delegate as much as possible – release early & often – evolution sometimes means feature removal • "Perfection (in design) is achieved not when there is nothing more to add, but rather when there is nothing more to take away. ” -- Antoine de Saint-Exupery ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

GNU & Free Software • The freedom to run the program, for any purpose (freedom 0). • The freedom to study how the program works, and change it to make it do what you wish (freedom 1). Access to the source code is a precondition for this. • The freedom to redistribute copies so you can help your neighbor (freedom 2). • The freedom to distribute copies of your modified versions to others (freedom 3). By doing this you can give the whole community a chance to benefit from your changes. Access to the source code is a precondition for this. http: //www. gnu. org/philosophy/free-sw. html ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Free Speech, Not Free Beer If nature has made any one thing less susceptible than all others of exclusive property, it is the action of the thinking power called an idea, which an individual may exclusively possess as long as he keeps it to himself; but the moment it is divulged, it forces itself into the possession of every one, and the receiver cannot dispossess himself of it. Its peculiar character, too, is that no one possesses the less, because every other possesses the whole of it. He who receives an idea from me, receives instruction himself without lessening mine; as he who lights his taper at mine, receives light without darkening me. - Thomas Jefferson, Letter to Isaac Mc. Pherson, August 13, 1813 http: //en. wikipedia. org/wiki/Zero-sum http: //en. wikipedia. org/wiki/Gratis_versus_Libre ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

"Piracy" or "Copying"? http: //www. debianhelp. org/node/14417 see also: http: //www. gnu. org/philosophy/why-free. html ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

Copyright and Copyleft In the GNU project, our aim is to give all users the freedom to redistribute and change GNU software. If middlemen could strip off the freedom, we might have many users, but those users would not have freedom. So instead of putting GNU software in the public domain, we ``copyleft'' it. Copyleft says that anyone who redistributes the software, with or without changes, must pass along the freedom to further copy and change it. Copyleft guarantees that every user has freedom. from: http: //www. gnu. org/copyleft. html a viral intellectual property model? ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
How to Fix Copyright? (1) http: //en. wikipedia. org/wiki/Compulsory_license ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

How to Fix Copyright? (2) • Public Domain Enhancement Act – http: //en. wikipedia. org/wiki/Public_Domain_ Enhancement_Act – pay $1 every 10 years to renew copyright – if not renewed, it joins the public domain ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

James Boyle The law locks up the man or woman Who steals the goose from the common But leaves the greater villain loose Who steals the common from off the goose. The law demands that we atone When we take things we do not own But leaves the lords and ladies fine Who take things that are yours and mine. The Raisin and the Pudding… The poor and wretched don't escape If they conspire the law to break; This must be so but they endure Those who conspire to make the law. http: //www. dlib. org/dlib/july 03/nelson/07 nelson. html http: //james-boyle. com/ http: //en. wikipedia. org/wiki/Orphan_works The law locks up the man or woman Who steals the goose from off the common And geese will still a common lack Till they go and steal it back. ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

http: //creativecommons. org/choose/ http: //wiki. creativecommons. org/Cc. REL ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu

• Example license for: – machines • http: //creativecommons. org/licenses/by/3. 0/rdf – people • http: //creativecommons. org/licenses/by/3. 0/ – lawyers • http: //creativecommons. org/licenses/by/3. 0/legalcode ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
Summary • Certain portions of Intellectual Property law are especially relevant to Web & DLs • Much of our IP law tradition comes from a non -digital era. . . – how many of the concepts should be mapped into the modern era? • Tensions between IP protection & preservation? ODU CS 751/851 Spring 2011 Michael L. Nelson mln@cs. odu. edu
82100f2e459ccc7d07f7b5904d302f03.ppt