7c958063c22c2d4f6be427b271d078dc.ppt
- Количество слайдов: 41
 Introduction to Computer Security Lecture 6 Windows/Unix/Solaris 10 Design Principles October 18, 2005 IS 2150/TEL 2810: Introduction of Computer Security 1
Introduction to Computer Security Lecture 6 Windows/Unix/Solaris 10 Design Principles October 18, 2005 IS 2150/TEL 2810: Introduction of Computer Security 1
 Two implementation concepts l Access control list (ACL) ¡ Store column of matrix with the resource l Capability ¡ User holds a “ticket” for each resource ¡ Two variations store row of matrix with user l unforgeable ticket in user space l IS 2150/TEL 2810: Introduction of Computer Security 2
Two implementation concepts l Access control list (ACL) ¡ Store column of matrix with the resource l Capability ¡ User holds a “ticket” for each resource ¡ Two variations store row of matrix with user l unforgeable ticket in user space l IS 2150/TEL 2810: Introduction of Computer Security 2
 Unix l Developed at AT&T Bell Labs l Single monolithic kernel ¡ Kernel mode l File system, device drivers, process management ¡ User l programs run in user mode networking IS 2150/TEL 2810: Introduction of Computer Security 3
Unix l Developed at AT&T Bell Labs l Single monolithic kernel ¡ Kernel mode l File system, device drivers, process management ¡ User l programs run in user mode networking IS 2150/TEL 2810: Introduction of Computer Security 3
 Unix Identification and authentication l Users have username ¡ ¡ ¡ Internally identified with a user ID (UID) Username to UID info in /etc/passwd Super UID = 0 l ¡ l can access any file Every user belong to a group – has GID Passwords to authenticate ¡ in /etc/passwd l Shadow file /etc/shadow IS 2150/TEL 2810: Introduction of Computer Security 4
Unix Identification and authentication l Users have username ¡ ¡ ¡ Internally identified with a user ID (UID) Username to UID info in /etc/passwd Super UID = 0 l ¡ l can access any file Every user belong to a group – has GID Passwords to authenticate ¡ in /etc/passwd l Shadow file /etc/shadow IS 2150/TEL 2810: Introduction of Computer Security 4
 Unix file security Each file has owner and group l Permissions set by owner l ¡ ¡ ¡ l Read, write, execute Owner, group, other Represented by vector of four octal values Only owner, root can change permissions ¡ This privilege cannot be delegated or shared IS 2150/TEL 2810: Introduction of Computer Security 5
Unix file security Each file has owner and group l Permissions set by owner l ¡ ¡ ¡ l Read, write, execute Owner, group, other Represented by vector of four octal values Only owner, root can change permissions ¡ This privilege cannot be delegated or shared IS 2150/TEL 2810: Introduction of Computer Security 5
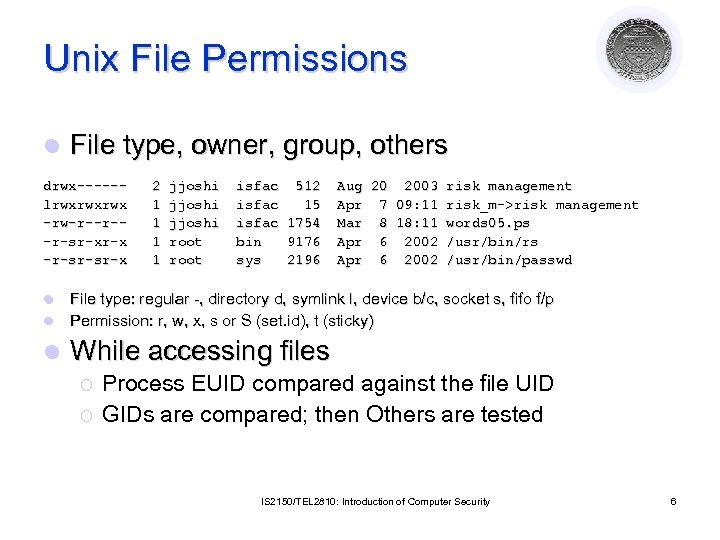 Unix File Permissions l File type, owner, group, others drwx-----lrwxrwxrwx -rw-r--r--r-sr-xr-x -r-sr-sr-x 2 1 1 jjoshi root isfac 512 isfac 15 isfac 1754 bin 9176 sys 2196 Aug 20 2003 risk management Apr 7 09: 11 risk_m->risk management Mar 8 18: 11 words 05. ps Apr 6 2002 /usr/bin/rs Apr 6 2002 /usr/bin/passwd l File type: regular -, directory d, symlink l, device b/c, socket s, fifo f/p Permission: r, w, x, s or S (set. id), t (sticky) l While accessing files l ¡ ¡ Process EUID compared against the file UID GIDs are compared; then Others are tested IS 2150/TEL 2810: Introduction of Computer Security 6
Unix File Permissions l File type, owner, group, others drwx-----lrwxrwxrwx -rw-r--r--r-sr-xr-x -r-sr-sr-x 2 1 1 jjoshi root isfac 512 isfac 15 isfac 1754 bin 9176 sys 2196 Aug 20 2003 risk management Apr 7 09: 11 risk_m->risk management Mar 8 18: 11 words 05. ps Apr 6 2002 /usr/bin/rs Apr 6 2002 /usr/bin/passwd l File type: regular -, directory d, symlink l, device b/c, socket s, fifo f/p Permission: r, w, x, s or S (set. id), t (sticky) l While accessing files l ¡ ¡ Process EUID compared against the file UID GIDs are compared; then Others are tested IS 2150/TEL 2810: Introduction of Computer Security 6
 Effective user id (EUID) l Each process has three Ids ¡ Real user ID (RUID) same as the user ID of parent (unless changed) l used to determine which user started the process Effective user ID (EUID) l from set user ID bit on the file being executed, or sys call l determines the permissions for process Saved user ID (SUID) l Allows restoring previous EUID l ¡ ¡ l Similarly we have ¡ Real group ID, effective group ID, IS 2150/TEL 2810: Introduction of Computer Security 7
Effective user id (EUID) l Each process has three Ids ¡ Real user ID (RUID) same as the user ID of parent (unless changed) l used to determine which user started the process Effective user ID (EUID) l from set user ID bit on the file being executed, or sys call l determines the permissions for process Saved user ID (SUID) l Allows restoring previous EUID l ¡ ¡ l Similarly we have ¡ Real group ID, effective group ID, IS 2150/TEL 2810: Introduction of Computer Security 7
 IDs/Operations Root can access any file l Fork and Exec l ¡ Inherit three IDs, l l except exec of file with setuid bit Setuid system calls ¡ seteuid(newid) can set EUID to l l ¡ Real ID or saved ID, regardless of current EUID Any ID, if EUID=0 Related calls: setuid, seteuid, setreuid IS 2150/TEL 2810: Introduction of Computer Security 8
IDs/Operations Root can access any file l Fork and Exec l ¡ Inherit three IDs, l l except exec of file with setuid bit Setuid system calls ¡ seteuid(newid) can set EUID to l l ¡ Real ID or saved ID, regardless of current EUID Any ID, if EUID=0 Related calls: setuid, seteuid, setreuid IS 2150/TEL 2810: Introduction of Computer Security 8
 Setid bits on executable Unix file l Three setid bits ¡ Setuid l ¡ Setgid l ¡ set EGID of process to GID of file Setuid/Setgid used when a process executes a file l ¡ set EUID of process to ID of file owner If setuid (setgid) bit is on – change the EUID of the process changed to UID (GUID) of the file Sticky l l Off: if user has write permission on directory, can rename or remove files, even if not owner On: only file owner, directory owner, and root can rename or remove file in the directory IS 2150/TEL 2810: Introduction of Computer Security 9
Setid bits on executable Unix file l Three setid bits ¡ Setuid l ¡ Setgid l ¡ set EGID of process to GID of file Setuid/Setgid used when a process executes a file l ¡ set EUID of process to ID of file owner If setuid (setgid) bit is on – change the EUID of the process changed to UID (GUID) of the file Sticky l l Off: if user has write permission on directory, can rename or remove files, even if not owner On: only file owner, directory owner, and root can rename or remove file in the directory IS 2150/TEL 2810: Introduction of Computer Security 9
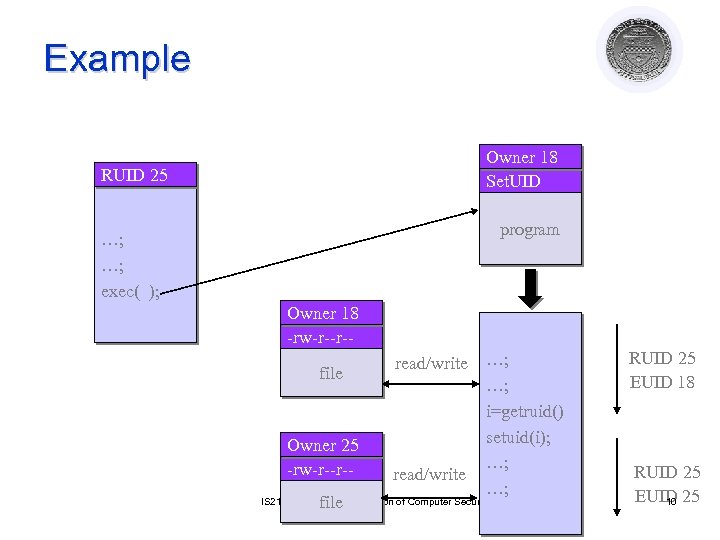 Example Owner 18 Set. UID RUID 25 program …; …; exec( ); Owner 18 -rw-r--r-file Owner 25 -rw-r--r-file read/write …; …; i=getruid() setuid(i); …; …; IS 2150/TEL 2810: Introduction of Computer Security RUID 25 EUID 18 RUID 25 EUID 25 10
Example Owner 18 Set. UID RUID 25 program …; …; exec( ); Owner 18 -rw-r--r-file Owner 25 -rw-r--r-file read/write …; …; i=getruid() setuid(i); …; …; IS 2150/TEL 2810: Introduction of Computer Security RUID 25 EUID 18 RUID 25 EUID 25 10
 Careful with Setuid ! Can do anything that owner of file is allowed to do Anything possible l Be sure not to if root l ¡ ¡ l Principle of least privilege ¡ l Take action for untrusted user Return secret data to untrusted user change EUID when root privileges no longer needed Setuid scripts (bad idea) ¡ Race conditions: begin executing setuid program; change contents of program before it loads and is executed IS 2150/TEL 2810: Introduction of Computer Security 11
Careful with Setuid ! Can do anything that owner of file is allowed to do Anything possible l Be sure not to if root l ¡ ¡ l Principle of least privilege ¡ l Take action for untrusted user Return secret data to untrusted user change EUID when root privileges no longer needed Setuid scripts (bad idea) ¡ Race conditions: begin executing setuid program; change contents of program before it loads and is executed IS 2150/TEL 2810: Introduction of Computer Security 11
 Windows NT l Windows 9 x, Me ¡ ¡ ¡ Never meant for security FAT file system – no file level security PWL password scheme – not secure l l Can be simply deleted Windows NT ¡ ¡ Username mapped to Security ID (SID) SID is unique within a domain l SID + password stored in a database handled by the Security Accounts Manager (SAM) subsystem IS 2150/TEL 2810: Introduction of Computer Security 12
Windows NT l Windows 9 x, Me ¡ ¡ ¡ Never meant for security FAT file system – no file level security PWL password scheme – not secure l l Can be simply deleted Windows NT ¡ ¡ Username mapped to Security ID (SID) SID is unique within a domain l SID + password stored in a database handled by the Security Accounts Manager (SAM) subsystem IS 2150/TEL 2810: Introduction of Computer Security 12
 Windows NT l Some basic functionality similar to Unix ¡ Specify access for groups and users l l Some additional concepts ¡ ¡ l Read, modify, change owner, delete Tokens Security attributes Generally ¡ More flexibility than Unix l l Can define new permissions Can give some but not all administrator privileges IS 2150/TEL 2810: Introduction of Computer Security 13
Windows NT l Some basic functionality similar to Unix ¡ Specify access for groups and users l l Some additional concepts ¡ ¡ l Read, modify, change owner, delete Tokens Security attributes Generally ¡ More flexibility than Unix l l Can define new permissions Can give some but not all administrator privileges IS 2150/TEL 2810: Introduction of Computer Security 13
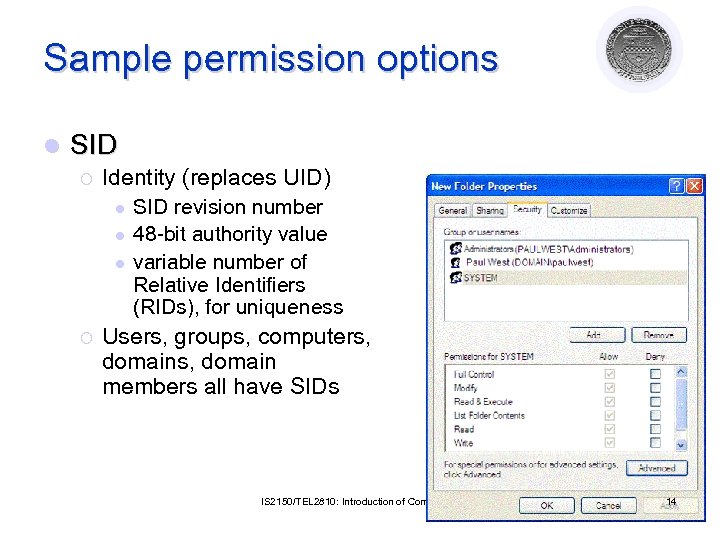 Sample permission options l SID ¡ Identity (replaces UID) l l l ¡ SID revision number 48 -bit authority value variable number of Relative Identifiers (RIDs), for uniqueness Users, groups, computers, domain members all have SIDs IS 2150/TEL 2810: Introduction of Computer Security 14
Sample permission options l SID ¡ Identity (replaces UID) l l l ¡ SID revision number 48 -bit authority value variable number of Relative Identifiers (RIDs), for uniqueness Users, groups, computers, domain members all have SIDs IS 2150/TEL 2810: Introduction of Computer Security 14
 Permission Inheritance l Static permission inheritance (Win NT) ¡ Initially, subfolders inherit permissions of folder ¡ Folder, subfolder changed independently ¡ Replace Permissions on Subdirectories command l Eliminates any differences in permissions IS 2150/TEL 2810: Introduction of Computer Security 15
Permission Inheritance l Static permission inheritance (Win NT) ¡ Initially, subfolders inherit permissions of folder ¡ Folder, subfolder changed independently ¡ Replace Permissions on Subdirectories command l Eliminates any differences in permissions IS 2150/TEL 2810: Introduction of Computer Security 15
 Permission Inheritance l Dynamic permission inheritance (Win 2000) ¡ ¡ ¡ Child inherits parent permission, remains linked Parent changes are inherited, except explicit settings Inherited and explicitly-set permissions may conflict l Resolution rules • Positive permissions are additive • Negative permission (deny access) takes priority IS 2150/TEL 2810: Introduction of Computer Security 16
Permission Inheritance l Dynamic permission inheritance (Win 2000) ¡ ¡ ¡ Child inherits parent permission, remains linked Parent changes are inherited, except explicit settings Inherited and explicitly-set permissions may conflict l Resolution rules • Positive permissions are additive • Negative permission (deny access) takes priority IS 2150/TEL 2810: Introduction of Computer Security 16
 Tokens l Security context ¡ l Security Reference Monitor ¡ l privileges, accounts, and groups associated with the process or thread uses tokens to identify the security context of a process or thread Impersonation token ¡ ¡ Each thread can have two tokens – primary & impersonation thread uses temporarily to adopt a different security context, usually of another user IS 2150/TEL 2810: Introduction of Computer Security 17
Tokens l Security context ¡ l Security Reference Monitor ¡ l privileges, accounts, and groups associated with the process or thread uses tokens to identify the security context of a process or thread Impersonation token ¡ ¡ Each thread can have two tokens – primary & impersonation thread uses temporarily to adopt a different security context, usually of another user IS 2150/TEL 2810: Introduction of Computer Security 17
 Security Descriptor l Information associated with an object ¡ l who can perform what actions on the object Several fields ¡ Header l l Descriptor revision number Control flags, attributes of the descriptor • E. g. , memory layout of the descriptor ¡ ¡ ¡ SID of the object's owner SID of the primary group of the object Two attached optional lists: l l Discretionary Access Control List (DACL) – users, groups, … System Access Control List (SACL) – system logs, . . IS 2150/TEL 2810: Introduction of Computer Security 18
Security Descriptor l Information associated with an object ¡ l who can perform what actions on the object Several fields ¡ Header l l Descriptor revision number Control flags, attributes of the descriptor • E. g. , memory layout of the descriptor ¡ ¡ ¡ SID of the object's owner SID of the primary group of the object Two attached optional lists: l l Discretionary Access Control List (DACL) – users, groups, … System Access Control List (SACL) – system logs, . . IS 2150/TEL 2810: Introduction of Computer Security 18
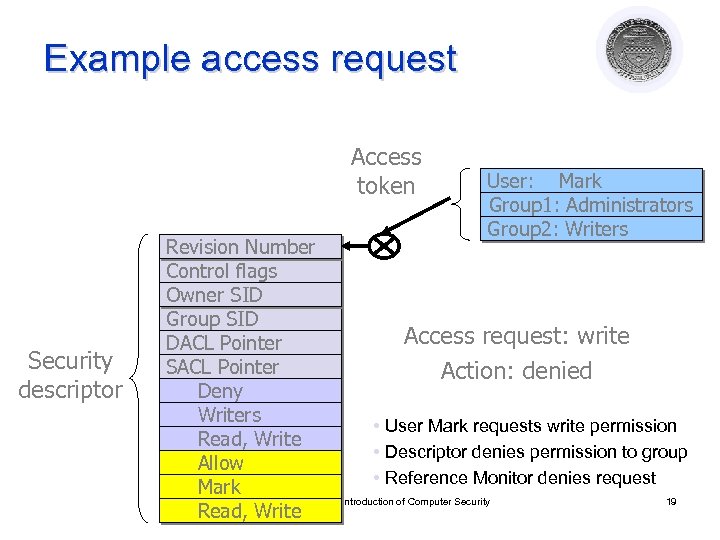 Example access request Access token Security descriptor User: Mark Group 1: Administrators Group 2: Writers Revision Number Control flags Owner SID Group SID Access request: write DACL Pointer SACL Pointer Action: denied Deny Writers • User Mark requests write permission Read, Write • Descriptor denies permission to group Allow • Reference Monitor denies request Mark IS 2150/TEL 2810: Introduction of Computer Security 19 Read, Write
Example access request Access token Security descriptor User: Mark Group 1: Administrators Group 2: Writers Revision Number Control flags Owner SID Group SID Access request: write DACL Pointer SACL Pointer Action: denied Deny Writers • User Mark requests write permission Read, Write • Descriptor denies permission to group Allow • Reference Monitor denies request Mark IS 2150/TEL 2810: Introduction of Computer Security 19 Read, Write
 Impersonation Tokens (setuid? ) l Process uses security attributes of another ¡ l Client passes impersonation token to server Client specifies impersonation level of server ¡ Anonymous l ¡ Identification l ¡ server obtains the SIDs of client and client's privileges, but server cannot impersonate the client Impersonation l ¡ Token has no information about the client server identifies and impersonate the client Delegation l lets server impersonate client on local, remote systems IS 2150/TEL 2810: Introduction of Computer Security 20
Impersonation Tokens (setuid? ) l Process uses security attributes of another ¡ l Client passes impersonation token to server Client specifies impersonation level of server ¡ Anonymous l ¡ Identification l ¡ server obtains the SIDs of client and client's privileges, but server cannot impersonate the client Impersonation l ¡ Token has no information about the client server identifies and impersonate the client Delegation l lets server impersonate client on local, remote systems IS 2150/TEL 2810: Introduction of Computer Security 20
 Encrypted File Systems (EFS) l Store files in encrypted form ¡ Key management: user’s key decrypts file ¡ Useful protection if someone steals disk l Windows – EFS ¡ User marks a file for encryption ¡ Unique file encryption key is created ¡ Key is encrypted, can be stored on smart card IS 2150/TEL 2810: Introduction of Computer Security 21
Encrypted File Systems (EFS) l Store files in encrypted form ¡ Key management: user’s key decrypts file ¡ Useful protection if someone steals disk l Windows – EFS ¡ User marks a file for encryption ¡ Unique file encryption key is created ¡ Key is encrypted, can be stored on smart card IS 2150/TEL 2810: Introduction of Computer Security 21
 SELinux Security Policy Abstractions l Type enforcement ¡ ¡ ¡ Each process has an associated domain Each object has an associated type Configuration files specify l l l How domains are allowed to access types Allowable interactions and transitions between domains Role-based access control ¡ Each process has an associated role l ¡ Separate system and user processes configuration files specify l Set of domains that may be entered by each role IS 2150/TEL 2810: Introduction of Computer Security 22
SELinux Security Policy Abstractions l Type enforcement ¡ ¡ ¡ Each process has an associated domain Each object has an associated type Configuration files specify l l l How domains are allowed to access types Allowable interactions and transitions between domains Role-based access control ¡ Each process has an associated role l ¡ Separate system and user processes configuration files specify l Set of domains that may be entered by each role IS 2150/TEL 2810: Introduction of Computer Security 22
 Sample Features of Trusted OS l Mandatory access control ¡ l Object reuse protection ¡ l Prevent any access that circumvents monitor Audit ¡ l Write over old data when file space is allocated Complete mediation ¡ l MAC not under user control, precedence over DAC Log security-related events Intrusion detection ¡ Anomaly detection l ¡ Learn normal activity, Report abnormal actions Attack detection l Recognize patterns associated with known attacks IS 2150/TEL 2810: Introduction of Computer Security 23
Sample Features of Trusted OS l Mandatory access control ¡ l Object reuse protection ¡ l Prevent any access that circumvents monitor Audit ¡ l Write over old data when file space is allocated Complete mediation ¡ l MAC not under user control, precedence over DAC Log security-related events Intrusion detection ¡ Anomaly detection l ¡ Learn normal activity, Report abnormal actions Attack detection l Recognize patterns associated with known attacks IS 2150/TEL 2810: Introduction of Computer Security 23
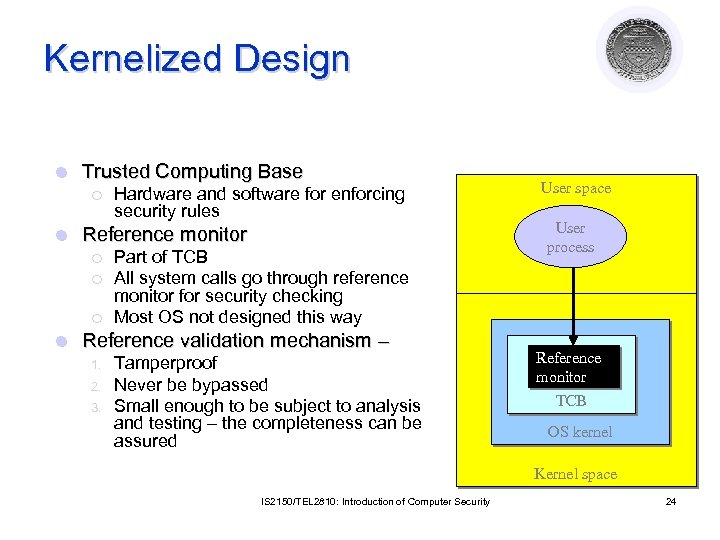 Kernelized Design l Trusted Computing Base ¡ l Reference monitor ¡ ¡ ¡ l Hardware and software for enforcing security rules Part of TCB All system calls go through reference monitor for security checking Most OS not designed this way Reference validation mechanism – 1. 2. 3. Tamperproof Never be bypassed Small enough to be subject to analysis and testing – the completeness can be assured User space User process Reference monitor TCB OS kernel Kernel space IS 2150/TEL 2810: Introduction of Computer Security 24
Kernelized Design l Trusted Computing Base ¡ l Reference monitor ¡ ¡ ¡ l Hardware and software for enforcing security rules Part of TCB All system calls go through reference monitor for security checking Most OS not designed this way Reference validation mechanism – 1. 2. 3. Tamperproof Never be bypassed Small enough to be subject to analysis and testing – the completeness can be assured User space User process Reference monitor TCB OS kernel Kernel space IS 2150/TEL 2810: Introduction of Computer Security 24
 Is Windows is “Secure”? l Good things ¡ ¡ l Design goals include security goals Independent review, configuration guidelines But … ¡ “Secure” is a complex concept l ¡ What properties protected against what attacks? Typical installation includes more than just OS l l Many problems arise from applications, device drivers Windows driver certification program IS 2150/TEL 2810: Introduction of Computer Security 25
Is Windows is “Secure”? l Good things ¡ ¡ l Design goals include security goals Independent review, configuration guidelines But … ¡ “Secure” is a complex concept l ¡ What properties protected against what attacks? Typical installation includes more than just OS l l Many problems arise from applications, device drivers Windows driver certification program IS 2150/TEL 2810: Introduction of Computer Security 25
 Window 2000 l Newer features than NT l NTFS file system redesigned for performance l Active directory ¡ Kerberos for authentication ¡ IPSec/L 2 TP IS 2150/TEL 2810: Introduction of Computer Security 26
Window 2000 l Newer features than NT l NTFS file system redesigned for performance l Active directory ¡ Kerberos for authentication ¡ IPSec/L 2 TP IS 2150/TEL 2810: Introduction of Computer Security 26
 Windows XP l Improvement over Win 2000 Professional ¡ Personalized login l ¡ User switching l ¡ ¡ ¡ Multiple users to be logged in Internet connection firewall (ICF) l ¡ Multiple users to have secure profiles Active packet filtering Blank password restriction (null sessions) Encrypting File System (EFS) using PKI Smart card support (uses X. 509 certificate for authentication) IS 2150/TEL 2810: Introduction of Computer Security 27
Windows XP l Improvement over Win 2000 Professional ¡ Personalized login l ¡ User switching l ¡ ¡ ¡ Multiple users to be logged in Internet connection firewall (ICF) l ¡ Multiple users to have secure profiles Active packet filtering Blank password restriction (null sessions) Encrypting File System (EFS) using PKI Smart card support (uses X. 509 certificate for authentication) IS 2150/TEL 2810: Introduction of Computer Security 27
 Active Directory l Core for the flexibility of Win 2000 ¡ l l l Information about all objects Group policy and remote OS operations Replaces SAM database ¡ l AD is trusted component of the LSA Stores ¡ ¡ l Centralized management for clients, servers and user accounts Access control information – authorization User credentials – authentication Supports ¡ PKI, Kerberos and LDAP IS 2150/TEL 2810: Introduction of Computer Security 28
Active Directory l Core for the flexibility of Win 2000 ¡ l l l Information about all objects Group policy and remote OS operations Replaces SAM database ¡ l AD is trusted component of the LSA Stores ¡ ¡ l Centralized management for clients, servers and user accounts Access control information – authorization User credentials – authentication Supports ¡ PKI, Kerberos and LDAP IS 2150/TEL 2810: Introduction of Computer Security 28
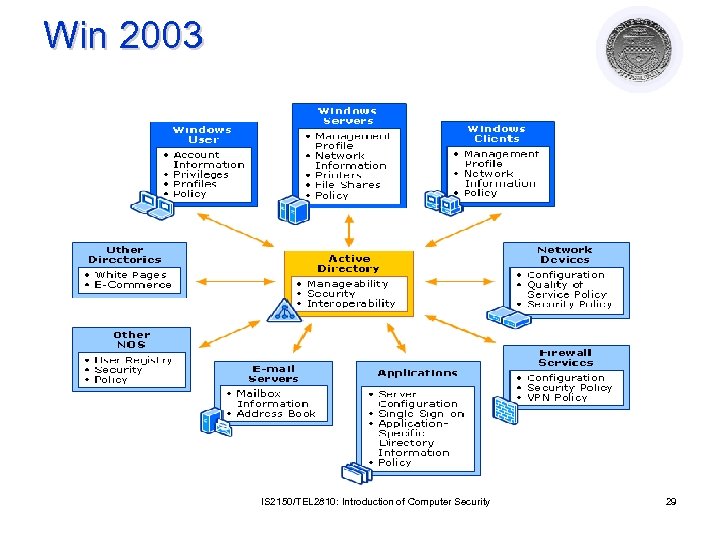 Win 2003 IS 2150/TEL 2810: Introduction of Computer Security 29
Win 2003 IS 2150/TEL 2810: Introduction of Computer Security 29
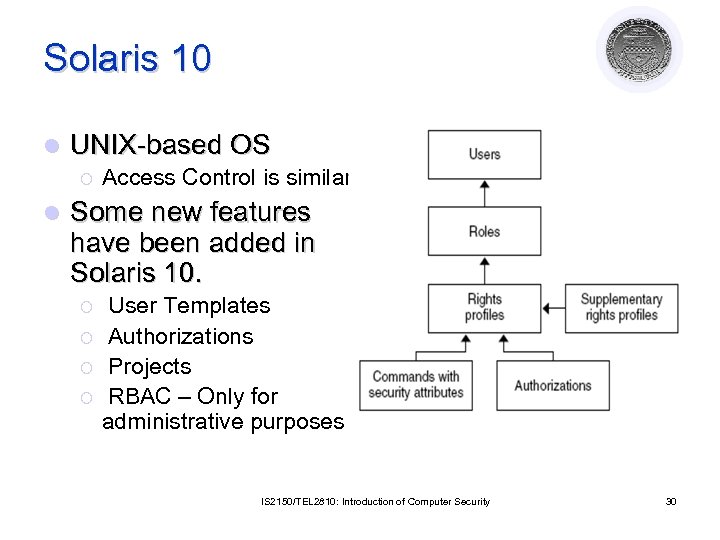 Solaris 10 l UNIX-based OS ¡ l Access Control is similar. Some new features have been added in Solaris 10. ¡ ¡ User Templates Authorizations Projects RBAC – Only for administrative purposes IS 2150/TEL 2810: Introduction of Computer Security 30
Solaris 10 l UNIX-based OS ¡ l Access Control is similar. Some new features have been added in Solaris 10. ¡ ¡ User Templates Authorizations Projects RBAC – Only for administrative purposes IS 2150/TEL 2810: Introduction of Computer Security 30
 Design Principles IS 2150/TEL 2810: Introduction of Computer Security 31
Design Principles IS 2150/TEL 2810: Introduction of Computer Security 31
 Design Principles for Security Mechanisms l Principles Least Privilege ¡ Fail-Safe Defaults ¡ Economy of Mechanism ¡ Complete Mediation ¡ Open Design ¡ Separation of Privilege ¡ Least Common Mechanism ¡ Psychological Acceptability ¡ l Based on the idea of simplicity and restriction IS 2150/TEL 2810: Introduction of Computer Security 32
Design Principles for Security Mechanisms l Principles Least Privilege ¡ Fail-Safe Defaults ¡ Economy of Mechanism ¡ Complete Mediation ¡ Open Design ¡ Separation of Privilege ¡ Least Common Mechanism ¡ Psychological Acceptability ¡ l Based on the idea of simplicity and restriction IS 2150/TEL 2810: Introduction of Computer Security 32
 Overview l Simplicity ¡ Less to go wrong ¡ Fewer possible inconsistencies ¡ Easy to understand l Restriction ¡ Minimize access power (need to know) ¡ Inhibit communication IS 2150/TEL 2810: Introduction of Computer Security 33
Overview l Simplicity ¡ Less to go wrong ¡ Fewer possible inconsistencies ¡ Easy to understand l Restriction ¡ Minimize access power (need to know) ¡ Inhibit communication IS 2150/TEL 2810: Introduction of Computer Security 33
 Least Privilege l A subject should be given only those privileges necessary to complete its task ¡ Function, l RBAC! ¡ Rights l added as needed, discarded after use Active sessions and dynamic separation of duty ¡ Minimal l not identity, controls protection domain A subject should not have a right if the task does not need it IS 2150/TEL 2810: Introduction of Computer Security 34
Least Privilege l A subject should be given only those privileges necessary to complete its task ¡ Function, l RBAC! ¡ Rights l added as needed, discarded after use Active sessions and dynamic separation of duty ¡ Minimal l not identity, controls protection domain A subject should not have a right if the task does not need it IS 2150/TEL 2810: Introduction of Computer Security 34
 Fail-Safe Defaults l Default action is to deny access l If action fails, system as secure as when action began ¡ Undo changes if actions do not complete ¡ Transactions (commit) IS 2150/TEL 2810: Introduction of Computer Security 35
Fail-Safe Defaults l Default action is to deny access l If action fails, system as secure as when action began ¡ Undo changes if actions do not complete ¡ Transactions (commit) IS 2150/TEL 2810: Introduction of Computer Security 35
 Economy of Mechanism l Keep the design and implementation as simple as possible ¡ KISS Principle (Keep It Simple, Silly!) l Simpler means less can go wrong ¡ And when errors occur, they are easier to understand fix l Interfaces and interactions IS 2150/TEL 2810: Introduction of Computer Security 36
Economy of Mechanism l Keep the design and implementation as simple as possible ¡ KISS Principle (Keep It Simple, Silly!) l Simpler means less can go wrong ¡ And when errors occur, they are easier to understand fix l Interfaces and interactions IS 2150/TEL 2810: Introduction of Computer Security 36
 Complete Mediation l Check every access to an object to ensure that access is allowed l Usually done once, on first action ¡ UNIX: Access checked on open, not checked thereafter l If permissions change after, may get unauthorized access IS 2150/TEL 2810: Introduction of Computer Security 37
Complete Mediation l Check every access to an object to ensure that access is allowed l Usually done once, on first action ¡ UNIX: Access checked on open, not checked thereafter l If permissions change after, may get unauthorized access IS 2150/TEL 2810: Introduction of Computer Security 37
 Open Design l Security should not depend on secrecy of design or implementation ¡ Popularly misunderstood to mean that source code should be public ¡ “Security through obscurity” ¡ Does not apply to information such as passwords or cryptographic keys IS 2150/TEL 2810: Introduction of Computer Security 38
Open Design l Security should not depend on secrecy of design or implementation ¡ Popularly misunderstood to mean that source code should be public ¡ “Security through obscurity” ¡ Does not apply to information such as passwords or cryptographic keys IS 2150/TEL 2810: Introduction of Computer Security 38
 Separation of Privilege l Require multiple conditions to grant privilege ¡ Example: Checks of $70000 must be signed by two people ¡ Separation of duty ¡ Defense in depth l Multiple levels of protection IS 2150/TEL 2810: Introduction of Computer Security 39
Separation of Privilege l Require multiple conditions to grant privilege ¡ Example: Checks of $70000 must be signed by two people ¡ Separation of duty ¡ Defense in depth l Multiple levels of protection IS 2150/TEL 2810: Introduction of Computer Security 39
 Least Common Mechanism l Mechanisms should not be shared ¡ Information can flow along shared channels ¡ Covert channels l Isolation ¡ Virtual machines ¡ Sandboxes IS 2150/TEL 2810: Introduction of Computer Security 40
Least Common Mechanism l Mechanisms should not be shared ¡ Information can flow along shared channels ¡ Covert channels l Isolation ¡ Virtual machines ¡ Sandboxes IS 2150/TEL 2810: Introduction of Computer Security 40
 Psychological Acceptability l Security mechanisms should not add to difficulty of accessing resource ¡ Hide complexity introduced by security mechanisms ¡ Ease of installation, configuration, use ¡ Human factors critical here IS 2150/TEL 2810: Introduction of Computer Security 41
Psychological Acceptability l Security mechanisms should not add to difficulty of accessing resource ¡ Hide complexity introduced by security mechanisms ¡ Ease of installation, configuration, use ¡ Human factors critical here IS 2150/TEL 2810: Introduction of Computer Security 41


