9fb1486646841017ad5b25e5db65b2ec.ppt
- Количество слайдов: 59
 Introduction to Computer Security Lecture 5 Integrity Policies October 4, 2005 Courtesy of Professors Chris Clifton & Matt Bishop INFSCI 2935: Introduction of Computer Security 1
Introduction to Computer Security Lecture 5 Integrity Policies October 4, 2005 Courtesy of Professors Chris Clifton & Matt Bishop INFSCI 2935: Introduction of Computer Security 1
 Overview l Requirements ¡ l Biba’s models ¡ ¡ ¡ l Low-Water-Mark policy Ring policy Strict Integrity policy Lipner’s model ¡ l Very different than confidentiality policies Combines Bell-La. Padula, Biba Clark-Wilson model IS 2150/TEL 2810: Introduction to Computer Security 2
Overview l Requirements ¡ l Biba’s models ¡ ¡ ¡ l Low-Water-Mark policy Ring policy Strict Integrity policy Lipner’s model ¡ l Very different than confidentiality policies Combines Bell-La. Padula, Biba Clark-Wilson model IS 2150/TEL 2810: Introduction to Computer Security 2
 Requirements of Commercial Integrity Policies (Lipner) 1. 2. 3. 4. 5. Users will not write their own programs, but will use existing production programs and databases. Programmers will develop and test programs on a nonproduction system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. A special process must be followed to install a program from the development system onto the production system. The special process in requirement 3 must be controlled and audited. The managers and auditors must have access to both the system state and the system logs that are generated. IS 2150/TEL 2810: Introduction to Computer Security 3
Requirements of Commercial Integrity Policies (Lipner) 1. 2. 3. 4. 5. Users will not write their own programs, but will use existing production programs and databases. Programmers will develop and test programs on a nonproduction system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. A special process must be followed to install a program from the development system onto the production system. The special process in requirement 3 must be controlled and audited. The managers and auditors must have access to both the system state and the system logs that are generated. IS 2150/TEL 2810: Introduction to Computer Security 3
 Integrity Policy: Principles of operation l Requirements induce principles of operation: ¡ ¡ ¡ Separation of Duty: Single person should not be allowed to carry out all steps of a critical function l Moving a program from Dev. to Prod. system l Developer and Certifier (installer) of a program l Authorizing checks and cashing it Separation of function l Do not process production data on development system Auditing l Emphasis on recovery and accountability l Controlled/audited process for updating code on production system IS 2150/TEL 2810: Introduction to Computer Security 4
Integrity Policy: Principles of operation l Requirements induce principles of operation: ¡ ¡ ¡ Separation of Duty: Single person should not be allowed to carry out all steps of a critical function l Moving a program from Dev. to Prod. system l Developer and Certifier (installer) of a program l Authorizing checks and cashing it Separation of function l Do not process production data on development system Auditing l Emphasis on recovery and accountability l Controlled/audited process for updating code on production system IS 2150/TEL 2810: Introduction to Computer Security 4
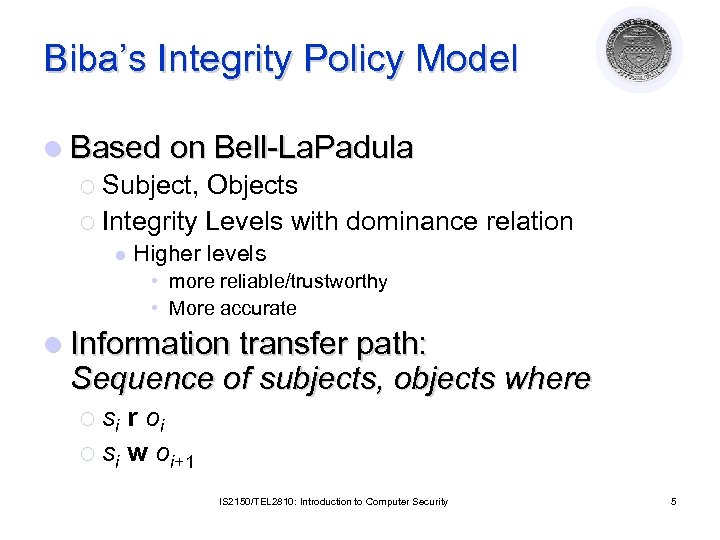 Biba’s Integrity Policy Model l Based on Bell-La. Padula ¡ Subject, Objects ¡ Integrity Levels with dominance relation l Higher levels • more reliable/trustworthy • More accurate l Information transfer path: Sequence of subjects, objects where ¡ si r oi ¡ si w oi+1 IS 2150/TEL 2810: Introduction to Computer Security 5
Biba’s Integrity Policy Model l Based on Bell-La. Padula ¡ Subject, Objects ¡ Integrity Levels with dominance relation l Higher levels • more reliable/trustworthy • More accurate l Information transfer path: Sequence of subjects, objects where ¡ si r oi ¡ si w oi+1 IS 2150/TEL 2810: Introduction to Computer Security 5
 Policies l Low-Water-Mark Policy ¡ ¡ ¡ l Ring Policy ¡ ¡ ¡ l sro s w o i(o) ≤ i(s) s 1 x s 2 i(s 2) ≤ i(s 1) allows any subject to read any object (same as above) s r o i(s) ≤ i(o) s w o i(o) ≤ i(s) s 1 x s 2 i(s 2) ≤ i(s 1) (no read-down) (no write-up) Biba’s Model: Strict Integrity Policy (dual of Bell-La. Padula) ¡ ¡ ¡ l s w o i(o) ≤ i(s) prevents writing to higher level s reads o i’(s) = min(i(s), i(o)) drops subject’s level s 1 x s 2 i(s 2) ≤ i(s 1) prevents executing higher level objects Theorem for each: ¡ If there is an information transfer path from object o 1 to object on+1, then the enforcement of the policy requires that i(on+1) ≤ i(o 1) for all n>1 IS 2150/TEL 2810: Introduction to Computer Security 6
Policies l Low-Water-Mark Policy ¡ ¡ ¡ l Ring Policy ¡ ¡ ¡ l sro s w o i(o) ≤ i(s) s 1 x s 2 i(s 2) ≤ i(s 1) allows any subject to read any object (same as above) s r o i(s) ≤ i(o) s w o i(o) ≤ i(s) s 1 x s 2 i(s 2) ≤ i(s 1) (no read-down) (no write-up) Biba’s Model: Strict Integrity Policy (dual of Bell-La. Padula) ¡ ¡ ¡ l s w o i(o) ≤ i(s) prevents writing to higher level s reads o i’(s) = min(i(s), i(o)) drops subject’s level s 1 x s 2 i(s 2) ≤ i(s 1) prevents executing higher level objects Theorem for each: ¡ If there is an information transfer path from object o 1 to object on+1, then the enforcement of the policy requires that i(on+1) ≤ i(o 1) for all n>1 IS 2150/TEL 2810: Introduction to Computer Security 6
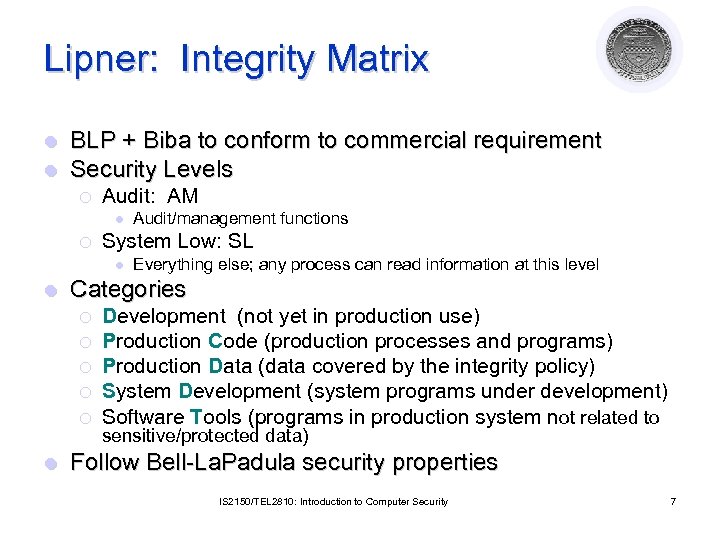 Lipner: Integrity Matrix l l BLP + Biba to conform to commercial requirement Security Levels ¡ Audit: AM l ¡ System Low: SL l l Everything else; any process can read information at this level Categories ¡ ¡ ¡ l Audit/management functions Development (not yet in production use) Production Code (production processes and programs) Production Data (data covered by the integrity policy) System Development (system programs under development) Software Tools (programs in production system not related to sensitive/protected data) Follow Bell-La. Padula security properties IS 2150/TEL 2810: Introduction to Computer Security 7
Lipner: Integrity Matrix l l BLP + Biba to conform to commercial requirement Security Levels ¡ Audit: AM l ¡ System Low: SL l l Everything else; any process can read information at this level Categories ¡ ¡ ¡ l Audit/management functions Development (not yet in production use) Production Code (production processes and programs) Production Data (data covered by the integrity policy) System Development (system programs under development) Software Tools (programs in production system not related to sensitive/protected data) Follow Bell-La. Padula security properties IS 2150/TEL 2810: Introduction to Computer Security 7
 Lipner: Integrity Matrix l Users: ¡ ¡ ¡ l Clearance Ordinary Developers System Programmers System Managers/Aud. Controllers Objects ¡ ¡ ¡ ¡ (SL, {PC, PD}) (SL, {D, T}) (SL, {SD, T}) (AM, {D, PC, PD, SD, T}) (SL, {D, PC, PD, SD, T} + downgrade prv Classification Development code/data Production code Production data Tools System Program update Logs (SL, {D, T}) (SL, {PC, PD}) (SL, {T}) (SL, {SD, T}) (AM, {…}) IS 2150/TEL 2810: Introduction to Computer Security 8
Lipner: Integrity Matrix l Users: ¡ ¡ ¡ l Clearance Ordinary Developers System Programmers System Managers/Aud. Controllers Objects ¡ ¡ ¡ ¡ (SL, {PC, PD}) (SL, {D, T}) (SL, {SD, T}) (AM, {D, PC, PD, SD, T}) (SL, {D, PC, PD, SD, T} + downgrade prv Classification Development code/data Production code Production data Tools System Program update Logs (SL, {D, T}) (SL, {PC, PD}) (SL, {T}) (SL, {SD, T}) (AM, {…}) IS 2150/TEL 2810: Introduction to Computer Security 8
 Check against the requirement l Users will not write their own programs, but will use existing production programs and databases. • l Users have no access to T, so cannot write their own programs Programmers will develop and test programs on a non production system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. • Applications programmers have no access to PD, so cannot access production data; if needed, it must be put into D (downgrade), requiring the system controller to intervene IS 2150/TEL 2810: Introduction to Computer Security 9
Check against the requirement l Users will not write their own programs, but will use existing production programs and databases. • l Users have no access to T, so cannot write their own programs Programmers will develop and test programs on a non production system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. • Applications programmers have no access to PD, so cannot access production data; if needed, it must be put into D (downgrade), requiring the system controller to intervene IS 2150/TEL 2810: Introduction to Computer Security 9
 Check against the requirement l A special process must be followed to install a program from the development system onto the production system. ¡ l The special process in requirement 3 must be controlled and audited. ¡ l Installing a program requires downgrade procedure (from D to PC), so only system controllers can do it Control: only system controllers can downgrade; audit: any such downgrading must be logged The managers and auditors must have access to both the system state and the system logs that are generated. ¡ System management and audit users are in AM and so have access to system state and logs IS 2150/TEL 2810: Introduction to Computer Security 10
Check against the requirement l A special process must be followed to install a program from the development system onto the production system. ¡ l The special process in requirement 3 must be controlled and audited. ¡ l Installing a program requires downgrade procedure (from D to PC), so only system controllers can do it Control: only system controllers can downgrade; audit: any such downgrading must be logged The managers and auditors must have access to both the system state and the system logs that are generated. ¡ System management and audit users are in AM and so have access to system state and logs IS 2150/TEL 2810: Introduction to Computer Security 10
 Problem l Too inflexible ¡ System managers cannot run programs for repairing inconsistent or erroneous production database ¡ A program for repairing an inconsistent database cannot be application level software l An integrity issue l So add more … IS 2150/TEL 2810: Introduction to Computer Security 11
Problem l Too inflexible ¡ System managers cannot run programs for repairing inconsistent or erroneous production database ¡ A program for repairing an inconsistent database cannot be application level software l An integrity issue l So add more … IS 2150/TEL 2810: Introduction to Computer Security 11
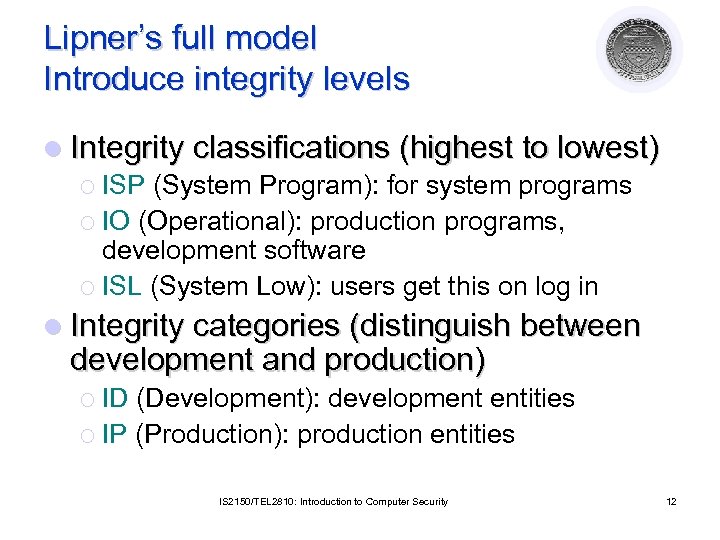 Lipner’s full model Introduce integrity levels l Integrity classifications (highest to lowest) ¡ ISP (System Program): for system programs ¡ IO (Operational): production programs, development software ¡ ISL (System Low): users get this on log in l Integrity categories (distinguish between development and production) ¡ ID (Development): development entities ¡ IP (Production): production entities IS 2150/TEL 2810: Introduction to Computer Security 12
Lipner’s full model Introduce integrity levels l Integrity classifications (highest to lowest) ¡ ISP (System Program): for system programs ¡ IO (Operational): production programs, development software ¡ ISL (System Low): users get this on log in l Integrity categories (distinguish between development and production) ¡ ID (Development): development entities ¡ IP (Production): production entities IS 2150/TEL 2810: Introduction to Computer Security 12
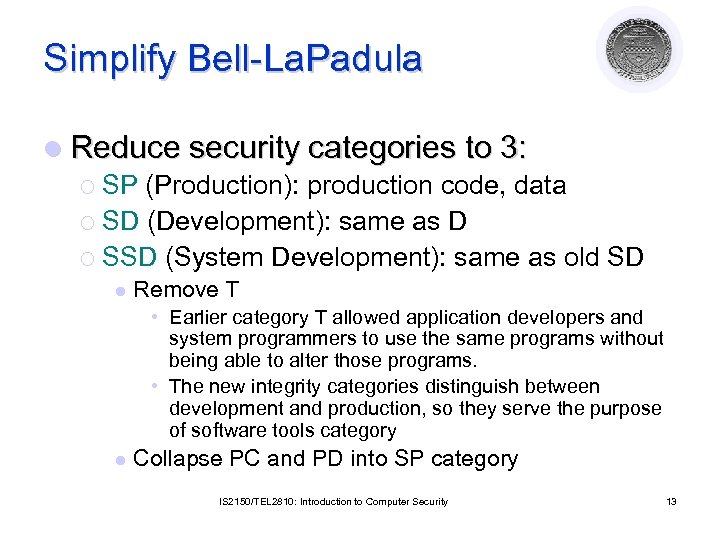 Simplify Bell-La. Padula l Reduce security categories to 3: ¡ SP (Production): production code, data ¡ SD (Development): same as D ¡ SSD (System Development): same as old SD l Remove T • Earlier category T allowed application developers and system programmers to use the same programs without being able to alter those programs. • The new integrity categories distinguish between development and production, so they serve the purpose of software tools category l Collapse PC and PD into SP category IS 2150/TEL 2810: Introduction to Computer Security 13
Simplify Bell-La. Padula l Reduce security categories to 3: ¡ SP (Production): production code, data ¡ SD (Development): same as D ¡ SSD (System Development): same as old SD l Remove T • Earlier category T allowed application developers and system programmers to use the same programs without being able to alter those programs. • The new integrity categories distinguish between development and production, so they serve the purpose of software tools category l Collapse PC and PD into SP category IS 2150/TEL 2810: Introduction to Computer Security 13
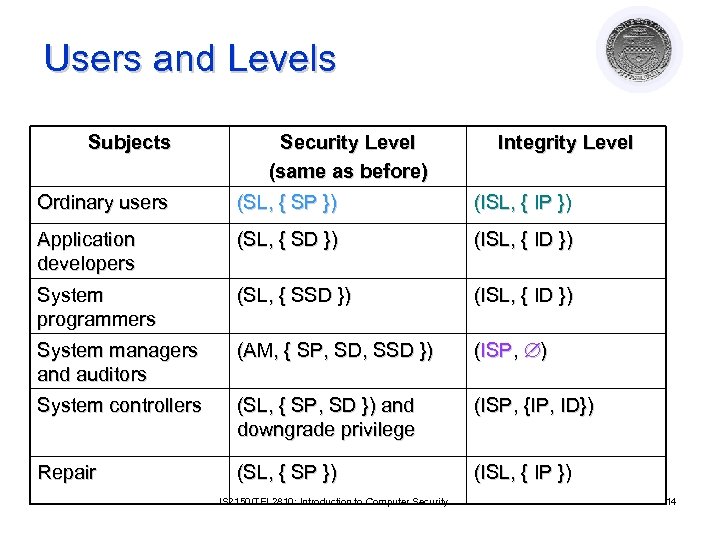 Users and Levels Subjects Security Level (same as before) Integrity Level Ordinary users (SL, { SP }) (ISL, { IP }) Application developers (SL, { SD }) (ISL, { ID }) System programmers (SL, { SSD }) (ISL, { ID }) System managers and auditors (AM, { SP, SD, SSD }) (ISP, ) System controllers (SL, { SP, SD }) and downgrade privilege (ISP, {IP, ID}) Repair (SL, { SP }) (ISL, { IP }) IS 2150/TEL 2810: Introduction to Computer Security 14
Users and Levels Subjects Security Level (same as before) Integrity Level Ordinary users (SL, { SP }) (ISL, { IP }) Application developers (SL, { SD }) (ISL, { ID }) System programmers (SL, { SSD }) (ISL, { ID }) System managers and auditors (AM, { SP, SD, SSD }) (ISP, ) System controllers (SL, { SP, SD }) and downgrade privilege (ISP, {IP, ID}) Repair (SL, { SP }) (ISL, { IP }) IS 2150/TEL 2810: Introduction to Computer Security 14
 Key Ideas for Assigning Integrity Levels to Objects Security clearances of subjects same as without integrity levels l Ordinary users need to modify production data, so ordinary users must have write access to integrity category IP l Ordinary users must be able to write production data but not production code; integrity classes allow this l IS 2150/TEL 2810: Introduction to Computer Security 15
Key Ideas for Assigning Integrity Levels to Objects Security clearances of subjects same as without integrity levels l Ordinary users need to modify production data, so ordinary users must have write access to integrity category IP l Ordinary users must be able to write production data but not production code; integrity classes allow this l IS 2150/TEL 2810: Introduction to Computer Security 15
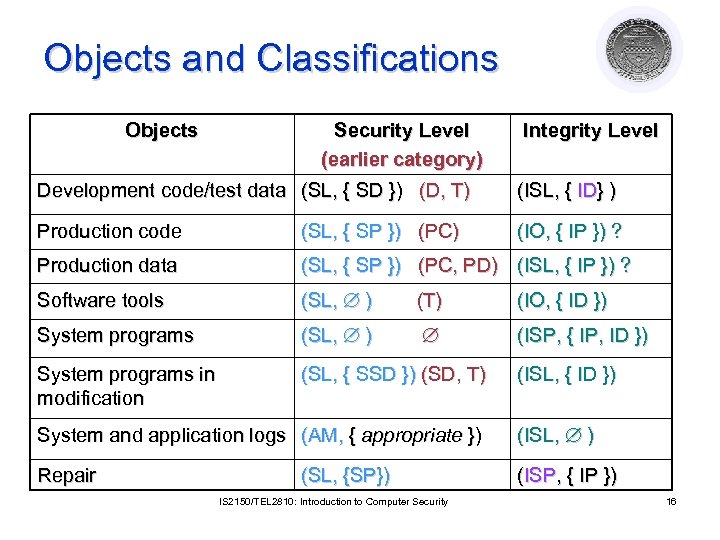 Objects and Classifications Objects Security Level (earlier category) Integrity Level Development code/test data (SL, { SD }) (D, T) (ISL, { ID} ) Production code (SL, { SP }) (PC) (IO, { IP }) ? Production data (SL, { SP }) (PC, PD) (ISL, { IP }) ? Software tools (SL, ) (T) (IO, { ID }) System programs (SL, ) (ISP, { IP, ID }) System programs in modification (SL, { SSD }) (SD, T) (ISL, { ID }) System and application logs (AM, { appropriate }) (ISL, ) Repair (ISP, { IP }) (SL, {SP}) IS 2150/TEL 2810: Introduction to Computer Security 16
Objects and Classifications Objects Security Level (earlier category) Integrity Level Development code/test data (SL, { SD }) (D, T) (ISL, { ID} ) Production code (SL, { SP }) (PC) (IO, { IP }) ? Production data (SL, { SP }) (PC, PD) (ISL, { IP }) ? Software tools (SL, ) (T) (IO, { ID }) System programs (SL, ) (ISP, { IP, ID }) System programs in modification (SL, { SSD }) (SD, T) (ISL, { ID }) System and application logs (AM, { appropriate }) (ISL, ) Repair (ISP, { IP }) (SL, {SP}) IS 2150/TEL 2810: Introduction to Computer Security 16
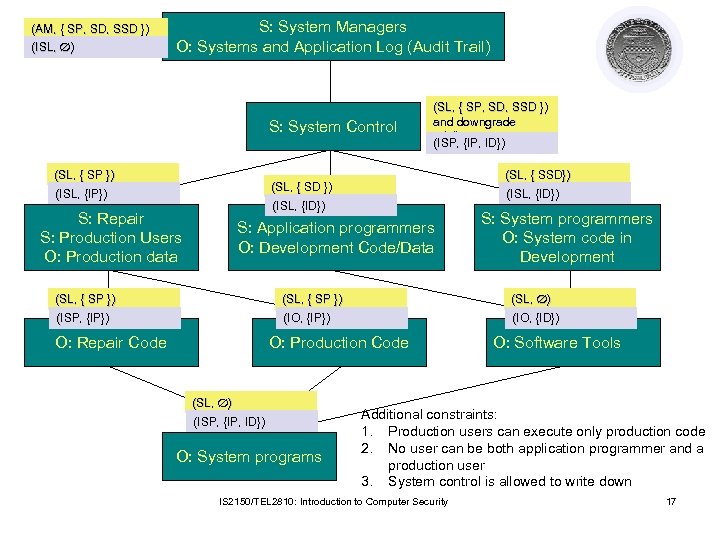 (AM, { SP, SD, SSD }) (ISL, ) S: System Managers O: Systems and Application Log (Audit Trail) S: System Control (SL, { SP }) (SL, { SP, SD, SSD }) and downgrade privilege (ISP, {IP, ID}) (SL, { SSD}) (SL, { SD }) (ISL, {IP}) (ISL, {ID}) S: Repair S: Production Users O: Production data S: Application programmers O: Development Code/Data S: System programmers O: System code in Development (SL, { SP }) (SL, ) (ISP, {IP}) (IO, {ID}) O: Repair Code O: Production Code (SL, ) (ISP, {IP, ID}) O: System programs O: Software Tools Additional constraints: 1. Production users can execute only production code 2. No user can be both application programmer and a production user 3. System control is allowed to write down IS 2150/TEL 2810: Introduction to Computer Security 17
(AM, { SP, SD, SSD }) (ISL, ) S: System Managers O: Systems and Application Log (Audit Trail) S: System Control (SL, { SP }) (SL, { SP, SD, SSD }) and downgrade privilege (ISP, {IP, ID}) (SL, { SSD}) (SL, { SD }) (ISL, {IP}) (ISL, {ID}) S: Repair S: Production Users O: Production data S: Application programmers O: Development Code/Data S: System programmers O: System code in Development (SL, { SP }) (SL, ) (ISP, {IP}) (IO, {ID}) O: Repair Code O: Production Code (SL, ) (ISP, {IP, ID}) O: System programs O: Software Tools Additional constraints: 1. Production users can execute only production code 2. No user can be both application programmer and a production user 3. System control is allowed to write down IS 2150/TEL 2810: Introduction to Computer Security 17
 Additional constraints l Production users can execute production users only l No individual can be both an application programmer and a production users l In contradiction to the *property- system controllers are allowed to write down. IS 2150/TEL 2810: Introduction to Computer Security 18
Additional constraints l Production users can execute production users only l No individual can be both an application programmer and a production users l In contradiction to the *property- system controllers are allowed to write down. IS 2150/TEL 2810: Introduction to Computer Security 18
 Clark-Wilson Integrity Model l l Transactions as the basic operation Integrity defined by a set of constraints ¡ l Example: Bank ¡ ¡ l D today’s deposits, W withdrawals, YB yesterday’s balance, TB today’s balance Integrity constraint: D + YB –W Well-formed transaction ¡ ¡ l Data in a consistent or valid state when it satisfies these A series of operations that move system from one consistent state to another State before transaction consistent state after transaction consistent Issue: who examines, certifies transactions done correctly? ¡ Separation of duty is crucial IS 2150/TEL 2810: Introduction to Computer Security 19
Clark-Wilson Integrity Model l l Transactions as the basic operation Integrity defined by a set of constraints ¡ l Example: Bank ¡ ¡ l D today’s deposits, W withdrawals, YB yesterday’s balance, TB today’s balance Integrity constraint: D + YB –W Well-formed transaction ¡ ¡ l Data in a consistent or valid state when it satisfies these A series of operations that move system from one consistent state to another State before transaction consistent state after transaction consistent Issue: who examines, certifies transactions done correctly? ¡ Separation of duty is crucial IS 2150/TEL 2810: Introduction to Computer Security 19
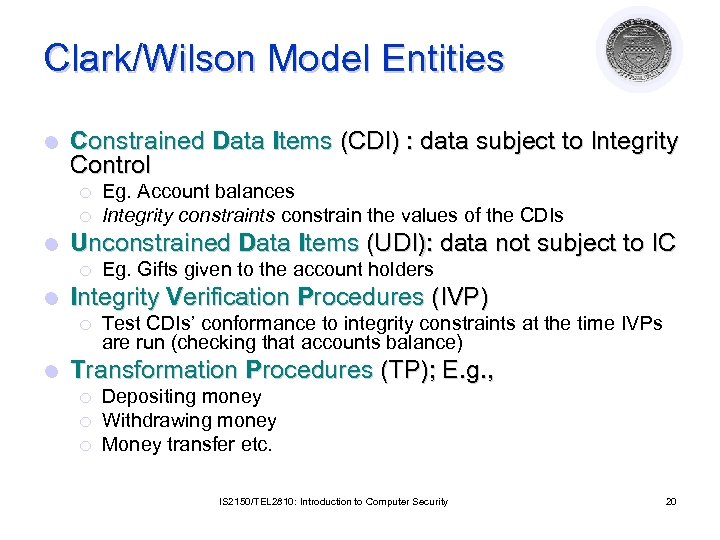 Clark/Wilson Model Entities l Constrained Data Items (CDI) : data subject to Integrity Control ¡ ¡ l Unconstrained Data Items (UDI): data not subject to IC ¡ l Eg. Gifts given to the account holders Integrity Verification Procedures (IVP) ¡ l Eg. Account balances Integrity constraints constrain the values of the CDIs Test CDIs’ conformance to integrity constraints at the time IVPs are run (checking that accounts balance) Transformation Procedures (TP); E. g. , ¡ ¡ ¡ Depositing money Withdrawing money Money transfer etc. IS 2150/TEL 2810: Introduction to Computer Security 20
Clark/Wilson Model Entities l Constrained Data Items (CDI) : data subject to Integrity Control ¡ ¡ l Unconstrained Data Items (UDI): data not subject to IC ¡ l Eg. Gifts given to the account holders Integrity Verification Procedures (IVP) ¡ l Eg. Account balances Integrity constraints constrain the values of the CDIs Test CDIs’ conformance to integrity constraints at the time IVPs are run (checking that accounts balance) Transformation Procedures (TP); E. g. , ¡ ¡ ¡ Depositing money Withdrawing money Money transfer etc. IS 2150/TEL 2810: Introduction to Computer Security 20
 Clark/Wilson: Certification/Enforcement Rules C 1: When any IVP is run, it must ensure all CDIs are in valid state l C 2: A TP must transform a set of CDIs from a valid state to another valid state l ¡ l E 1: System must maintain certified relations ¡ l TR must not be used on CDIs it is not certified for TP/CDI sets enforced E 2: System must control users ¡ user/TP/CDI mappings enforced IS 2150/TEL 2810: Introduction to Computer Security 21
Clark/Wilson: Certification/Enforcement Rules C 1: When any IVP is run, it must ensure all CDIs are in valid state l C 2: A TP must transform a set of CDIs from a valid state to another valid state l ¡ l E 1: System must maintain certified relations ¡ l TR must not be used on CDIs it is not certified for TP/CDI sets enforced E 2: System must control users ¡ user/TP/CDI mappings enforced IS 2150/TEL 2810: Introduction to Computer Security 21
 Clark/Wilson: Certification/Enforcement Rules C 3: Relations between (user, TP, {CDI}) must support separation of duty l E 3: Users must be authenticated to execute TP l ¡ Note, unauthenticated users may manipulate UDIs C 4: All TPs must log undo information to append-only CDI (to reconstruct an operation) l C 5: A TP taking a UDI as input must either reject it or transform it to a CDI l E 4: Only certifier of a TP may change the list of entities associated with that TP l ¡ Enforces separation of duty: if a user could create a TP and associate some set of entities and himself with that TP, he could have the TP perform some unauthorized act IS 2150/TEL 2810: Introduction to Computer Security 22
Clark/Wilson: Certification/Enforcement Rules C 3: Relations between (user, TP, {CDI}) must support separation of duty l E 3: Users must be authenticated to execute TP l ¡ Note, unauthenticated users may manipulate UDIs C 4: All TPs must log undo information to append-only CDI (to reconstruct an operation) l C 5: A TP taking a UDI as input must either reject it or transform it to a CDI l E 4: Only certifier of a TP may change the list of entities associated with that TP l ¡ Enforces separation of duty: if a user could create a TP and associate some set of entities and himself with that TP, he could have the TP perform some unauthorized act IS 2150/TEL 2810: Introduction to Computer Security 22
 Requirements of Commercial Integrity Policies (Lipner) 1. 2. 3. 4. 5. Users will not write their own programs, but will use existing production programs and databases. Programmers will develop and test programs on a nonproduction system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. A special process must be followed to install a program from the development system onto the production system. The special process in requirement 3 must be controlled and audited. The managers and auditors must have access to both the system state and the system logs that are generated. IS 2150/TEL 2810: Introduction to Computer Security 23
Requirements of Commercial Integrity Policies (Lipner) 1. 2. 3. 4. 5. Users will not write their own programs, but will use existing production programs and databases. Programmers will develop and test programs on a nonproduction system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. A special process must be followed to install a program from the development system onto the production system. The special process in requirement 3 must be controlled and audited. The managers and auditors must have access to both the system state and the system logs that are generated. IS 2150/TEL 2810: Introduction to Computer Security 23
 Comparison With Requirements Users can’t (only trusted personnel can) certify TPs, so CR 5 and ER 4 enforce this 2. Procedural, so model doesn’t directly cover it; but special process corresponds to using TP 1. • 3. No technical controls can prevent programmer from developing program on production system; usual control is to delete software tools TP does the installation, trusted personnel do certification IS 2150/TEL 2810: Introduction to Computer Security 24
Comparison With Requirements Users can’t (only trusted personnel can) certify TPs, so CR 5 and ER 4 enforce this 2. Procedural, so model doesn’t directly cover it; but special process corresponds to using TP 1. • 3. No technical controls can prevent programmer from developing program on production system; usual control is to delete software tools TP does the installation, trusted personnel do certification IS 2150/TEL 2810: Introduction to Computer Security 24
 Comparison With Requirements 4. CR 4 provides logging; ER 3 authenticates trusted personnel doing installation; CR 5, ER 4 control installation procedure • New program is UDI before certification, CDI (and TP) after Log is CDI, so appropriate TP can provide managers, auditors access 5. • Access to state handled similarly IS 2150/TEL 2810: Introduction to Computer Security 25
Comparison With Requirements 4. CR 4 provides logging; ER 3 authenticates trusted personnel doing installation; CR 5, ER 4 control installation procedure • New program is UDI before certification, CDI (and TP) after Log is CDI, so appropriate TP can provide managers, auditors access 5. • Access to state handled similarly IS 2150/TEL 2810: Introduction to Computer Security 25
 Summary l Integrity policies deal with trust ¡ ¡ l l As trust is hard to quantify, these policies are hard to evaluate completely Look for assumptions and trusted users to find possible weak points in their implementation Biba, Lipner based on multilevel integrity Clark-Wilson introduce new ideas ¡ ¡ Commercial firms do not classify data using multilevel scheme and they enforce separation of duty Notion of certification is different from enforcement; l l l enforcement rules can be enforced, certification rules need outside intervention, and process of certification is complex and error prone IS 2150/TEL 2810: Introduction to Computer Security 26
Summary l Integrity policies deal with trust ¡ ¡ l l As trust is hard to quantify, these policies are hard to evaluate completely Look for assumptions and trusted users to find possible weak points in their implementation Biba, Lipner based on multilevel integrity Clark-Wilson introduce new ideas ¡ ¡ Commercial firms do not classify data using multilevel scheme and they enforce separation of duty Notion of certification is different from enforcement; l l l enforcement rules can be enforced, certification rules need outside intervention, and process of certification is complex and error prone IS 2150/TEL 2810: Introduction to Computer Security 26
 Hybrid Policies Courtesy of Professors Chris Clifton & Matt Bishop INFSCI 2935: Introduction of Computer Security 27
Hybrid Policies Courtesy of Professors Chris Clifton & Matt Bishop INFSCI 2935: Introduction of Computer Security 27
 Chinese Wall Model l Supports confidentiality and integrity ¡ ¡ l Information can’t flow between items in a Conflict of Interest set Applicable to environment of stock exchange or investment house Models conflict of interest ¡ ¡ Objects: items of information related to a company Company dataset (CD): contains objects related to a single company l ¡ Written CD(O) Conflict of interest class (COI): contains datasets of companies in competition l l Written COI(O) Assume: each object belongs to exactly one COI class IS 2150/TEL 2810: Introduction to Computer Security 28
Chinese Wall Model l Supports confidentiality and integrity ¡ ¡ l Information can’t flow between items in a Conflict of Interest set Applicable to environment of stock exchange or investment house Models conflict of interest ¡ ¡ Objects: items of information related to a company Company dataset (CD): contains objects related to a single company l ¡ Written CD(O) Conflict of interest class (COI): contains datasets of companies in competition l l Written COI(O) Assume: each object belongs to exactly one COI class IS 2150/TEL 2810: Introduction to Computer Security 28
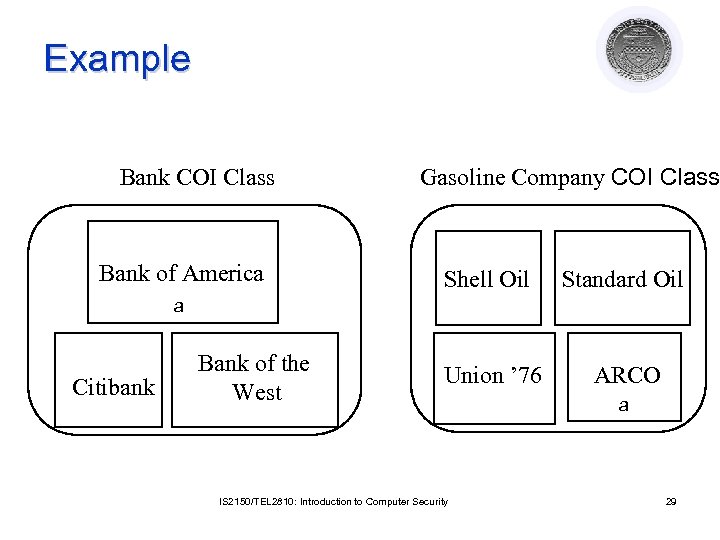 Example Bank COI Class Bank of America Gasoline Company COI Class Shell Oil Standard Oil Union ’ 76 ARCO a Citibank Bank of the West IS 2150/TEL 2810: Introduction to Computer Security a 29
Example Bank COI Class Bank of America Gasoline Company COI Class Shell Oil Standard Oil Union ’ 76 ARCO a Citibank Bank of the West IS 2150/TEL 2810: Introduction to Computer Security a 29
 CW-Simple Security Property (Read rule) l CW-Simple Security Property ¡ s can read o one of the following holds l o’ PR(s) such that CD(o’) = CD(o) l o’, o’ PR(s) COI(o’) COI(o), or l o has been “sanitized” (o’ PR(s) indicates o’ has been previously read by s) ¡ Public information may belong to a CD l l l As is publicly available, no conflicts of interest arise So, should not affect ability of analysts to read Typically, all sensitive data removed from such information before it is released publicly (called sanitization) IS 2150/TEL 2810: Introduction to Computer Security 30
CW-Simple Security Property (Read rule) l CW-Simple Security Property ¡ s can read o one of the following holds l o’ PR(s) such that CD(o’) = CD(o) l o’, o’ PR(s) COI(o’) COI(o), or l o has been “sanitized” (o’ PR(s) indicates o’ has been previously read by s) ¡ Public information may belong to a CD l l l As is publicly available, no conflicts of interest arise So, should not affect ability of analysts to read Typically, all sensitive data removed from such information before it is released publicly (called sanitization) IS 2150/TEL 2810: Introduction to Computer Security 30
 Writing l Anthony, Susan work in same trading house l Anthony can read Bank. Of. Amercia’s CD, l Susan can read Citi. Banks’s CD, l Both can read ARCO’s CD l If Anthony could write to ARCO’s CD, Susan can read it ¡ Hence, indirectly, she can read information from Bank. Of. Amercia’s CD, a clear conflict of interest IS 2150/TEL 2810: Introduction to Computer Security 31
Writing l Anthony, Susan work in same trading house l Anthony can read Bank. Of. Amercia’s CD, l Susan can read Citi. Banks’s CD, l Both can read ARCO’s CD l If Anthony could write to ARCO’s CD, Susan can read it ¡ Hence, indirectly, she can read information from Bank. Of. Amercia’s CD, a clear conflict of interest IS 2150/TEL 2810: Introduction to Computer Security 31
 CW-*-Property (Write rule) l CW-*- Property ¡ s can write o the following holds l The CW-simple security condition permits S to read O. l For all unsanitized objects o’, s can read o’ CD(o’) = CD(o) Says that s can write to an object if all the (unsanitized) objects it can read are in the same dataset ¡ ¡ Anthony can read both CDs hence condition 1 is met He can read unsanitized objects of Bank. Of. Amercia, hence condition 2 is false l Hence Anthony can’t write to objects in ARCO’s CD. IS 2150/TEL 2810: Introduction to Computer Security 32
CW-*-Property (Write rule) l CW-*- Property ¡ s can write o the following holds l The CW-simple security condition permits S to read O. l For all unsanitized objects o’, s can read o’ CD(o’) = CD(o) Says that s can write to an object if all the (unsanitized) objects it can read are in the same dataset ¡ ¡ Anthony can read both CDs hence condition 1 is met He can read unsanitized objects of Bank. Of. Amercia, hence condition 2 is false l Hence Anthony can’t write to objects in ARCO’s CD. IS 2150/TEL 2810: Introduction to Computer Security 32
 Compare to Bell-La. Padula l Fundamentally different ¡ ¡ l CW has no security labels, B-LP does CW has notion of past accesses, B-LP does not Bell-La. Padula can capture state at any time ¡ ¡ ¡ Each (COI, CD) pair gets security category Two clearances, S (sanitized) and U (unsanitized) such that (S dom U) Subjects assigned clearance for compartments without multiple categories corresponding to CDs in same COI class eg. If Susan can read the Bank. Of. America and ARCO CDs, her process would get clearance for compartment (U, {a, n}) IS 2150/TEL 2810: Introduction to Computer Security 33
Compare to Bell-La. Padula l Fundamentally different ¡ ¡ l CW has no security labels, B-LP does CW has notion of past accesses, B-LP does not Bell-La. Padula can capture state at any time ¡ ¡ ¡ Each (COI, CD) pair gets security category Two clearances, S (sanitized) and U (unsanitized) such that (S dom U) Subjects assigned clearance for compartments without multiple categories corresponding to CDs in same COI class eg. If Susan can read the Bank. Of. America and ARCO CDs, her process would get clearance for compartment (U, {a, n}) IS 2150/TEL 2810: Introduction to Computer Security 33
 Compare to Bell-La. Padula l Bell-La. Padula cannot track changes over time ¡ Susan becomes ill, Anna needs to take over l l l C-W history lets Anna know if she can No way for Bell-La. Padula to capture this Access constraints change over time ¡ ¡ Initially, subjects in C-W can read any object Bell-La. Padula constrains set of objects that a subject can access l Can’t clear all subjects for all categories, because this violates CW-simple security condition IS 2150/TEL 2810: Introduction to Computer Security 34
Compare to Bell-La. Padula l Bell-La. Padula cannot track changes over time ¡ Susan becomes ill, Anna needs to take over l l l C-W history lets Anna know if she can No way for Bell-La. Padula to capture this Access constraints change over time ¡ ¡ Initially, subjects in C-W can read any object Bell-La. Padula constrains set of objects that a subject can access l Can’t clear all subjects for all categories, because this violates CW-simple security condition IS 2150/TEL 2810: Introduction to Computer Security 34
 Compare to Clark-Wilson Model covers integrity, CW consider only access control aspects l If “subjects” and “processes” are interchangeable, a single person could use multiple processes to violate CW-simple security condition l If “subject” is a specific person and includes all processes the subject executes, then consistent with Clark-Wilson Model l IS 2150/TEL 2810: Introduction to Computer Security 35
Compare to Clark-Wilson Model covers integrity, CW consider only access control aspects l If “subjects” and “processes” are interchangeable, a single person could use multiple processes to violate CW-simple security condition l If “subject” is a specific person and includes all processes the subject executes, then consistent with Clark-Wilson Model l IS 2150/TEL 2810: Introduction to Computer Security 35
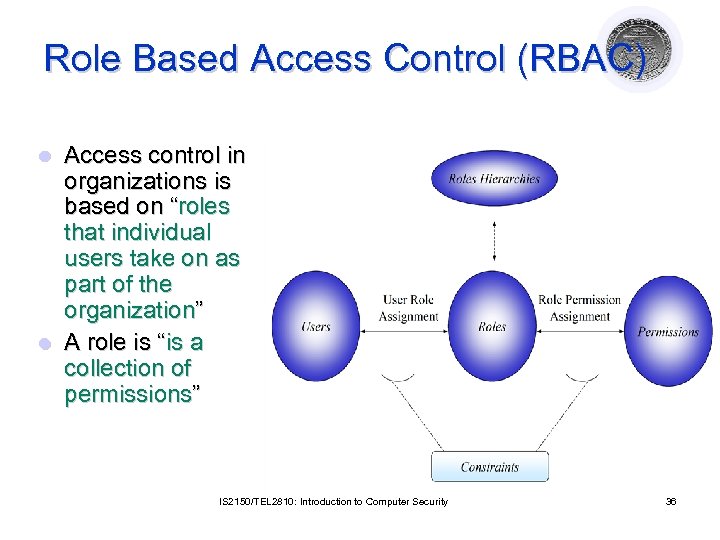 Role Based Access Control (RBAC) Access control in organizations is based on “roles that individual users take on as part of the organization” l A role is “is a collection of permissions” l IS 2150/TEL 2810: Introduction to Computer Security 36
Role Based Access Control (RBAC) Access control in organizations is based on “roles that individual users take on as part of the organization” l A role is “is a collection of permissions” l IS 2150/TEL 2810: Introduction to Computer Security 36
 RBAC l Access depends on function, not identity ¡ Example: Allison is bookkeeper for Math Dept. She has access to financial records. If she leaves and Betty is hired as the new bookkeeper, Betty now has access to those records. The role of “bookkeeper” dictates access, not the identity of the individual. IS 2150/TEL 2810: Introduction to Computer Security 37
RBAC l Access depends on function, not identity ¡ Example: Allison is bookkeeper for Math Dept. She has access to financial records. If she leaves and Betty is hired as the new bookkeeper, Betty now has access to those records. The role of “bookkeeper” dictates access, not the identity of the individual. IS 2150/TEL 2810: Introduction to Computer Security 37
 Advantages of RBAC l Allows Efficient Security Management ¡ l l l Administrative roles, Role hierarchy Principle of least privilege allows minimizing damage Separation of Duties constraints to prevent fraud Allows grouping of objects Policy-neutral - Provides generality Encompasses DAC and MAC policies IS 2150/TEL 2810: Introduction to Computer Security 38
Advantages of RBAC l Allows Efficient Security Management ¡ l l l Administrative roles, Role hierarchy Principle of least privilege allows minimizing damage Separation of Duties constraints to prevent fraud Allows grouping of objects Policy-neutral - Provides generality Encompasses DAC and MAC policies IS 2150/TEL 2810: Introduction to Computer Security 38
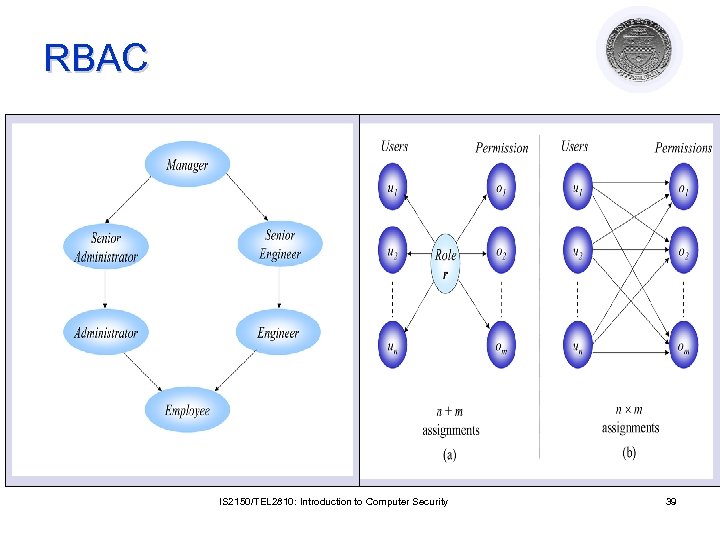 RBAC IS 2150/TEL 2810: Introduction to Computer Security 39
RBAC IS 2150/TEL 2810: Introduction to Computer Security 39
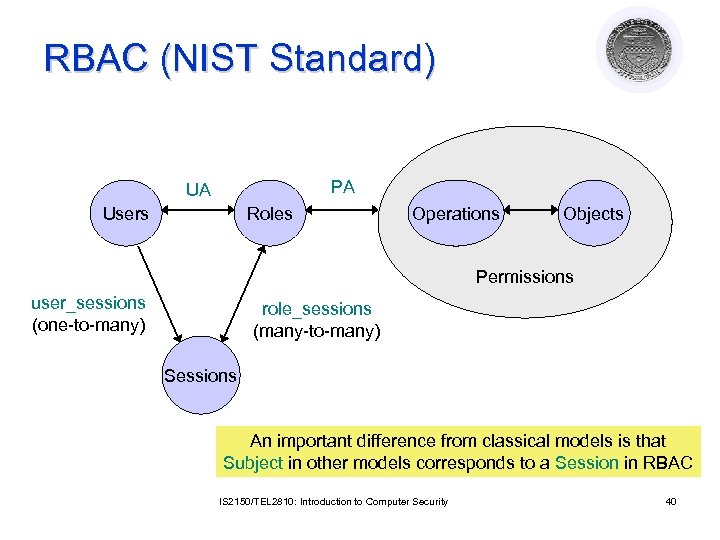 RBAC (NIST Standard) PA UA Users Roles Operations Objects Permissions user_sessions (one-to-many) role_sessions (many-to-many) Sessions An important difference from classical models is that Subject in other models corresponds to a Session in RBAC IS 2150/TEL 2810: Introduction to Computer Security 40
RBAC (NIST Standard) PA UA Users Roles Operations Objects Permissions user_sessions (one-to-many) role_sessions (many-to-many) Sessions An important difference from classical models is that Subject in other models corresponds to a Session in RBAC IS 2150/TEL 2810: Introduction to Computer Security 40
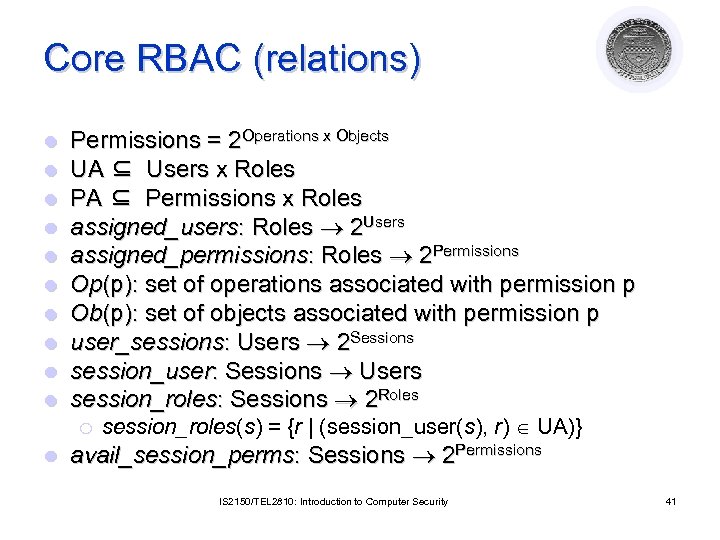 Core RBAC (relations) l l l l l Permissions = 2 Operations x Objects UA ⊆ Users x Roles PA ⊆ Permissions x Roles assigned_users: Roles 2 Users assigned_permissions: Roles 2 Permissions Op(p): set of operations associated with permission p Ob(p): set of objects associated with permission p user_sessions: Users 2 Sessions session_user: Sessions Users session_roles: Sessions 2 Roles ¡ l session_roles(s) = {r | (session_user(s), r) UA)} avail_session_perms: Sessions 2 Permissions IS 2150/TEL 2810: Introduction to Computer Security 41
Core RBAC (relations) l l l l l Permissions = 2 Operations x Objects UA ⊆ Users x Roles PA ⊆ Permissions x Roles assigned_users: Roles 2 Users assigned_permissions: Roles 2 Permissions Op(p): set of operations associated with permission p Ob(p): set of objects associated with permission p user_sessions: Users 2 Sessions session_user: Sessions Users session_roles: Sessions 2 Roles ¡ l session_roles(s) = {r | (session_user(s), r) UA)} avail_session_perms: Sessions 2 Permissions IS 2150/TEL 2810: Introduction to Computer Security 41
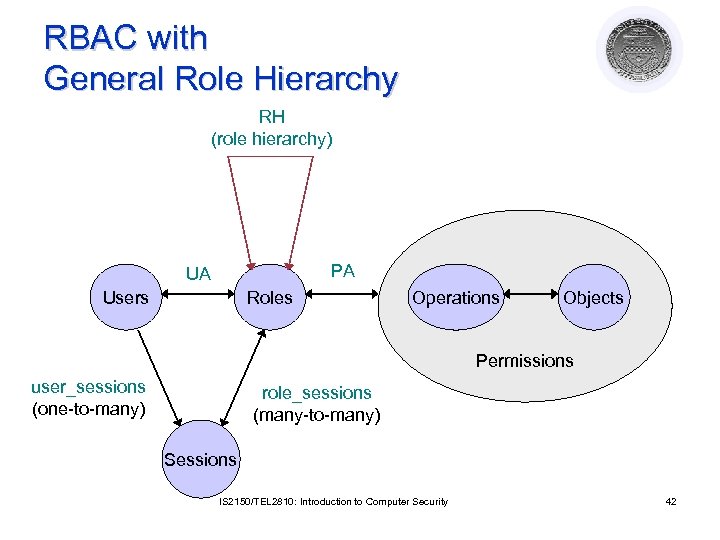 RBAC with General Role Hierarchy RH (role hierarchy) PA UA Users Roles Operations Objects Permissions user_sessions (one-to-many) role_sessions (many-to-many) Sessions IS 2150/TEL 2810: Introduction to Computer Security 42
RBAC with General Role Hierarchy RH (role hierarchy) PA UA Users Roles Operations Objects Permissions user_sessions (one-to-many) role_sessions (many-to-many) Sessions IS 2150/TEL 2810: Introduction to Computer Security 42
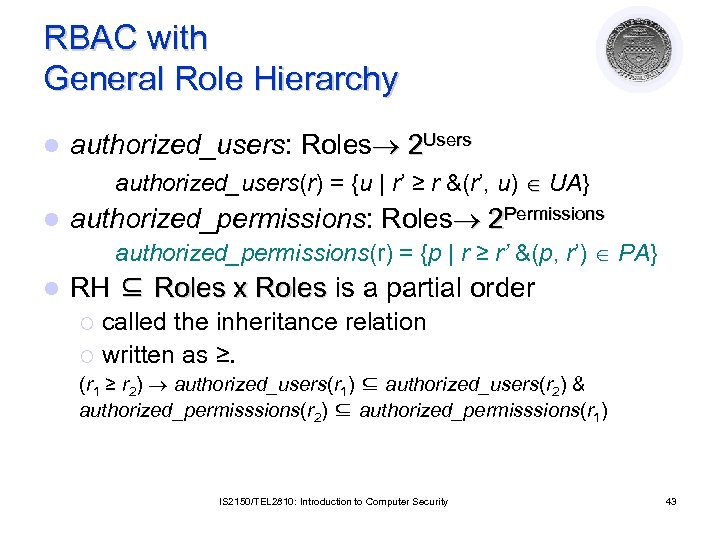 RBAC with General Role Hierarchy l authorized_users: Roles 2 Users authorized_users(r) = {u | r’ ≥ r &(r’, u) UA} l authorized_permissions: Roles 2 Permissions authorized_permissions(r) = {p | r ≥ r’ &(p, r’) PA} l RH ⊆ Roles x Roles is a partial order called the inheritance relation ¡ written as ≥. ¡ (r 1 ≥ r 2) authorized_users(r 1) ⊆ authorized_users(r 2) & authorized_permisssions(r 2) ⊆ authorized_permisssions(r 1) IS 2150/TEL 2810: Introduction to Computer Security 43
RBAC with General Role Hierarchy l authorized_users: Roles 2 Users authorized_users(r) = {u | r’ ≥ r &(r’, u) UA} l authorized_permissions: Roles 2 Permissions authorized_permissions(r) = {p | r ≥ r’ &(p, r’) PA} l RH ⊆ Roles x Roles is a partial order called the inheritance relation ¡ written as ≥. ¡ (r 1 ≥ r 2) authorized_users(r 1) ⊆ authorized_users(r 2) & authorized_permisssions(r 2) ⊆ authorized_permisssions(r 1) IS 2150/TEL 2810: Introduction to Computer Security 43
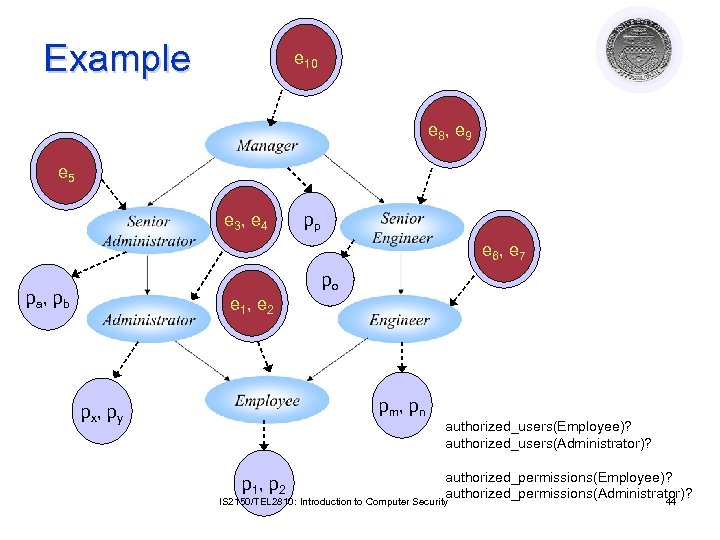 Example pe, 10 y x p e 8 , e 9 px py pxe 5 py , e 3 , e 4 px py pp e 6 , e y px p 7 po pa , pb e 1 , e 2 px py pm, pn px , py authorized_users(Employee)? authorized_users(Administrator)? authorized_permissions(Employee)? authorized_permissions(Administrator)? IS 2150/TEL 2810: Introduction to Computer Security 44 p 1 , p 2
Example pe, 10 y x p e 8 , e 9 px py pxe 5 py , e 3 , e 4 px py pp e 6 , e y px p 7 po pa , pb e 1 , e 2 px py pm, pn px , py authorized_users(Employee)? authorized_users(Administrator)? authorized_permissions(Employee)? authorized_permissions(Administrator)? IS 2150/TEL 2810: Introduction to Computer Security 44 p 1 , p 2
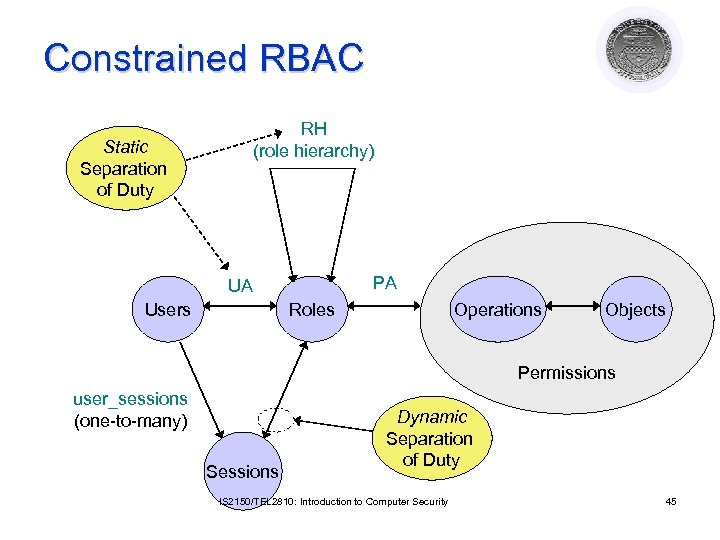 Constrained RBAC RH (role hierarchy) Static Separation of Duty PA UA Users Roles Operations Objects Permissions user_sessions (one-to-many) Sessions Dynamic Separation of Duty IS 2150/TEL 2810: Introduction to Computer Security 45
Constrained RBAC RH (role hierarchy) Static Separation of Duty PA UA Users Roles Operations Objects Permissions user_sessions (one-to-many) Sessions Dynamic Separation of Duty IS 2150/TEL 2810: Introduction to Computer Security 45
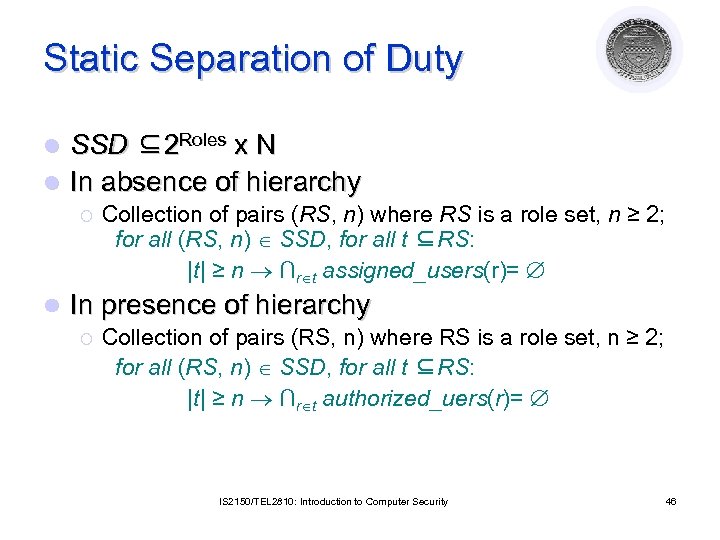 Static Separation of Duty SSD ⊆2 Roles x N l In absence of hierarchy l ¡ l Collection of pairs (RS, n) where RS is a role set, n ≥ 2; for all (RS, n) SSD, for all t ⊆RS: |t| ≥ n ∩r t assigned_users(r)= In presence of hierarchy ¡ Collection of pairs (RS, n) where RS is a role set, n ≥ 2; for all (RS, n) SSD, for all t ⊆RS: |t| ≥ n ∩r t authorized_uers(r)= IS 2150/TEL 2810: Introduction to Computer Security 46
Static Separation of Duty SSD ⊆2 Roles x N l In absence of hierarchy l ¡ l Collection of pairs (RS, n) where RS is a role set, n ≥ 2; for all (RS, n) SSD, for all t ⊆RS: |t| ≥ n ∩r t assigned_users(r)= In presence of hierarchy ¡ Collection of pairs (RS, n) where RS is a role set, n ≥ 2; for all (RS, n) SSD, for all t ⊆RS: |t| ≥ n ∩r t authorized_uers(r)= IS 2150/TEL 2810: Introduction to Computer Security 46
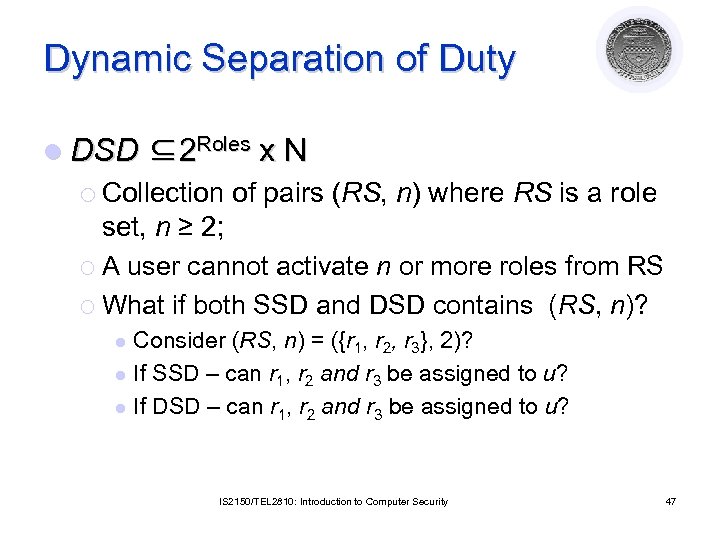 Dynamic Separation of Duty l DSD ⊆2 Roles ¡ Collection x. N of pairs (RS, n) where RS is a role set, n ≥ 2; ¡ A user cannot activate n or more roles from RS ¡ What if both SSD and DSD contains (RS, n)? Consider (RS, n) = ({r 1, r 2, r 3}, 2)? l If SSD – can r 1, r 2 and r 3 be assigned to u? l If DSD – can r 1, r 2 and r 3 be assigned to u? l IS 2150/TEL 2810: Introduction to Computer Security 47
Dynamic Separation of Duty l DSD ⊆2 Roles ¡ Collection x. N of pairs (RS, n) where RS is a role set, n ≥ 2; ¡ A user cannot activate n or more roles from RS ¡ What if both SSD and DSD contains (RS, n)? Consider (RS, n) = ({r 1, r 2, r 3}, 2)? l If SSD – can r 1, r 2 and r 3 be assigned to u? l If DSD – can r 1, r 2 and r 3 be assigned to u? l IS 2150/TEL 2810: Introduction to Computer Security 47
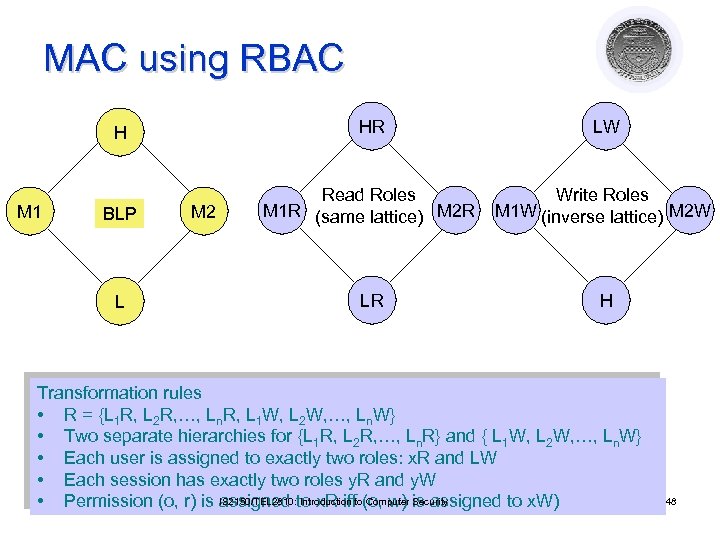 MAC using RBAC H M 1 HR LW BLP Read Roles M 1 R (same lattice) M 2 R Write Roles M 1 W (inverse lattice) M 2 W LR H L M 2 Transformation rules • R = {L 1 R, L 2 R, …, Ln. R, L 1 W, L 2 W, …, Ln. W} • Two separate hierarchies for {L 1 R, L 2 R, …, Ln. R} and { L 1 W, L 2 W, …, Ln. W} • Each user is assigned to exactly two roles: x. R and LW • Each session has exactly two roles y. R and y. W • Permission (o, r) is IS 2150/TEL 2810: to x. R iffto(o, w) is assigned to x. W) assigned Introduction Computer Security 48
MAC using RBAC H M 1 HR LW BLP Read Roles M 1 R (same lattice) M 2 R Write Roles M 1 W (inverse lattice) M 2 W LR H L M 2 Transformation rules • R = {L 1 R, L 2 R, …, Ln. R, L 1 W, L 2 W, …, Ln. W} • Two separate hierarchies for {L 1 R, L 2 R, …, Ln. R} and { L 1 W, L 2 W, …, Ln. W} • Each user is assigned to exactly two roles: x. R and LW • Each session has exactly two roles y. R and y. W • Permission (o, r) is IS 2150/TEL 2810: to x. R iffto(o, w) is assigned to x. W) assigned Introduction Computer Security 48
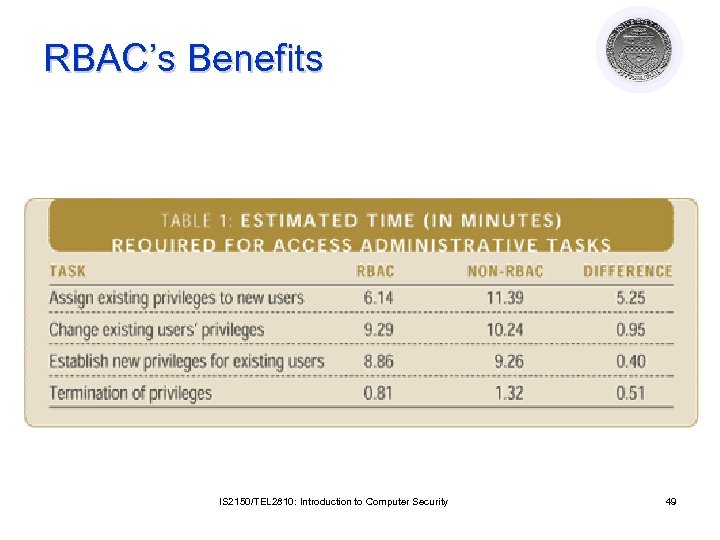 RBAC’s Benefits IS 2150/TEL 2810: Introduction to Computer Security 49
RBAC’s Benefits IS 2150/TEL 2810: Introduction to Computer Security 49
 Cost Benefits l Saves about 7. 01 minutes per employee, per year in administrative functions ¡ ¡ Average IT amin salary - $59. 27 per hour The annual cost saving is: l l $6, 924/1000; $692, 471/100, 000 Reduced Employee downtime ¡ ¡ ¡ if new transitioning employees receive their system privileges faster, their productivity is increased 26. 4 hours for non-RBAC; 14. 7 hours for RBAC For average employee wage of $39. 29/hour, the annual productivity cost savings yielded by an RBAC system: l $75000/1000; $7. 4 M/100, 000 IS 2150/TEL 2810: Introduction to Computer Security 50
Cost Benefits l Saves about 7. 01 minutes per employee, per year in administrative functions ¡ ¡ Average IT amin salary - $59. 27 per hour The annual cost saving is: l l $6, 924/1000; $692, 471/100, 000 Reduced Employee downtime ¡ ¡ ¡ if new transitioning employees receive their system privileges faster, their productivity is increased 26. 4 hours for non-RBAC; 14. 7 hours for RBAC For average employee wage of $39. 29/hour, the annual productivity cost savings yielded by an RBAC system: l $75000/1000; $7. 4 M/100, 000 IS 2150/TEL 2810: Introduction to Computer Security 50
 Time-based Access Control Requirement l Organizational functions and services with temporal requirements ¡ ¡ ¡ A part-time staff is authorized to work only between 9 am -2 pm on weekdays A day doctor must be able to perform his/her duties between 8 am-8 pm An external auditor needs access to organizational financial data for a period of three months A video library allows access to a subscriber to view at most three movies every week In an insurance company, an agent needs access to patient history until Introduction to Computer Security settled a claim has been IS 2150/TEL 2810: 51
Time-based Access Control Requirement l Organizational functions and services with temporal requirements ¡ ¡ ¡ A part-time staff is authorized to work only between 9 am -2 pm on weekdays A day doctor must be able to perform his/her duties between 8 am-8 pm An external auditor needs access to organizational financial data for a period of three months A video library allows access to a subscriber to view at most three movies every week In an insurance company, an agent needs access to patient history until Introduction to Computer Security settled a claim has been IS 2150/TEL 2810: 51
 Policy Composition Courtesy of Professors Chris Clifton & Matt Bishop INFSCI 2935: Introduction of Computer Security 52
Policy Composition Courtesy of Professors Chris Clifton & Matt Bishop INFSCI 2935: Introduction of Computer Security 52
 Problem: Consistent Policies l Policies defined by different organizations ¡ Different needs ¡ But sometimes subjects/objects overlap l Can all policies be met? ¡ Different categories l Build lattice combining them ¡ Different l security levels Need to be levels – thus must be able to order ¡ What if different DAC and MAC policies need to be integrated? IS 2150/TEL 2810: Introduction to Computer Security 53
Problem: Consistent Policies l Policies defined by different organizations ¡ Different needs ¡ But sometimes subjects/objects overlap l Can all policies be met? ¡ Different categories l Build lattice combining them ¡ Different l security levels Need to be levels – thus must be able to order ¡ What if different DAC and MAC policies need to be integrated? IS 2150/TEL 2810: Introduction to Computer Security 53
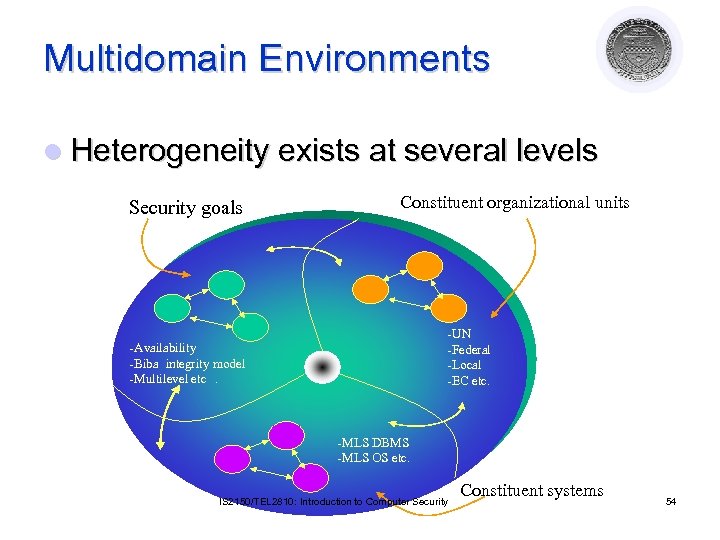 Multidomain Environments l Heterogeneity exists at several levels Security goals Constituent organizational units -UN -Federal -Local -EC etc. -Availability -Biba integrity model -Multilevel etc. -MLS DBMS -MLS OS etc. IS 2150/TEL 2810: Introduction to Computer Security Constituent systems 54
Multidomain Environments l Heterogeneity exists at several levels Security goals Constituent organizational units -UN -Federal -Local -EC etc. -Availability -Biba integrity model -Multilevel etc. -MLS DBMS -MLS OS etc. IS 2150/TEL 2810: Introduction to Computer Security Constituent systems 54
 Multidomain Challenges Key challenges l Semantic heterogeneity l Secure interoperation l Assurance and risk propagation l Security Management IS 2150/TEL 2810: Introduction to Computer Security 55
Multidomain Challenges Key challenges l Semantic heterogeneity l Secure interoperation l Assurance and risk propagation l Security Management IS 2150/TEL 2810: Introduction to Computer Security 55
 Semantic heterogeneity l Different systems use different security policies ¡ l Variations of the same policies ¡ l ¡ Similar roles with different names Similar permission sets with different role names Structural conflict ¡ l e. g. , BLP model and its variations Naming conflict on security attributes ¡ l e. g. , Chinese wall, BLP policies etc. different multilevel lattices / role hierarchies Different Commercial-Off-The-Self (COTS) products IS 2150/TEL 2810: Introduction to Computer Security 56
Semantic heterogeneity l Different systems use different security policies ¡ l Variations of the same policies ¡ l ¡ Similar roles with different names Similar permission sets with different role names Structural conflict ¡ l e. g. , BLP model and its variations Naming conflict on security attributes ¡ l e. g. , Chinese wall, BLP policies etc. different multilevel lattices / role hierarchies Different Commercial-Off-The-Self (COTS) products IS 2150/TEL 2810: Introduction to Computer Security 56
![Secure Interoperability l Principles of secure interoperation [Gong, 96] Principle of autonomy l If Secure Interoperability l Principles of secure interoperation [Gong, 96] Principle of autonomy l If](https://present5.com/presentation/9fb1486646841017ad5b25e5db65b2ec/image-57.jpg) Secure Interoperability l Principles of secure interoperation [Gong, 96] Principle of autonomy l If an access is permitted within an individual system, it must also be permitted under secure interoperation Principle of security l If an access is not permitted within an individual system, it must not be permitted under secure interoperation l Interoperation of secure systems can create new security breaches IS 2150/TEL 2810: Introduction to Computer Security 57
Secure Interoperability l Principles of secure interoperation [Gong, 96] Principle of autonomy l If an access is permitted within an individual system, it must also be permitted under secure interoperation Principle of security l If an access is not permitted within an individual system, it must not be permitted under secure interoperation l Interoperation of secure systems can create new security breaches IS 2150/TEL 2810: Introduction to Computer Security 57
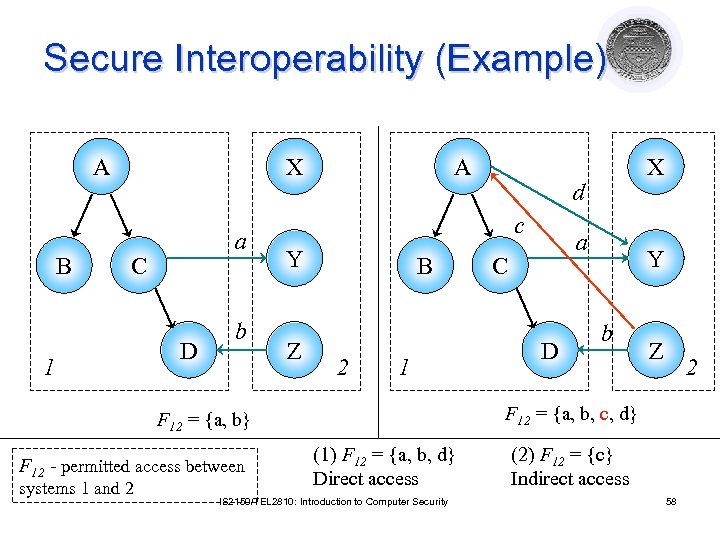 Secure Interoperability (Example) A B X a C 1 D b A Z B 2 1 systems 1 and 2 a C D Y b Z 2 F 12 = {a, b, c, d} F 12 = {a, b} F 12 - permitted access between d c Y X (1) F 12 = {a, b, d} Direct access IS 2150/TEL 2810: Introduction to Computer Security (2) F 12 = {c} Indirect access 58
Secure Interoperability (Example) A B X a C 1 D b A Z B 2 1 systems 1 and 2 a C D Y b Z 2 F 12 = {a, b, c, d} F 12 = {a, b} F 12 - permitted access between d c Y X (1) F 12 = {a, b, d} Direct access IS 2150/TEL 2810: Introduction to Computer Security (2) F 12 = {c} Indirect access 58
 Assurance and Risk Propagation & Security Management l Assurance and Risk propagation ¡ A breach in one component affects the whole environment ¡ Cascading problem l Management ¡ Centralized/Decentralized ¡ Managing metapolicy ¡ Managing policy evolution IS 2150/TEL 2810: Introduction to Computer Security 59
Assurance and Risk Propagation & Security Management l Assurance and Risk propagation ¡ A breach in one component affects the whole environment ¡ Cascading problem l Management ¡ Centralized/Decentralized ¡ Managing metapolicy ¡ Managing policy evolution IS 2150/TEL 2810: Introduction to Computer Security 59


