782d9125b7cf9c40b3da16831c4f487e.ppt
- Количество слайдов: 43
 Introducing Digital Forensics Peter Sommer London School of Economics, UK
Introducing Digital Forensics Peter Sommer London School of Economics, UK
 Peter Sommer • academic at London School of Economics – Information Systems as opposed to “Computer Science” • • • 1 st degree: Oxford Law first forensic investigation – 1985 since then: Rome Labs, Cathedral / Cheshire Cat, Buccaneer, murder, fraud, immigration, software and currency counterfeiting, warez, harassment, paedophilia, hacking, infotheft etc • Shrivenham MSc , Centrex LE training • UK experts have primary duty to the courts
Peter Sommer • academic at London School of Economics – Information Systems as opposed to “Computer Science” • • • 1 st degree: Oxford Law first forensic investigation – 1985 since then: Rome Labs, Cathedral / Cheshire Cat, Buccaneer, murder, fraud, immigration, software and currency counterfeiting, warez, harassment, paedophilia, hacking, infotheft etc • Shrivenham MSc , Centrex LE training • UK experts have primary duty to the courts
 Digital Forensics aka • Computer Forensics • Forensic Computing • Digital Evidence
Digital Forensics aka • Computer Forensics • Forensic Computing • Digital Evidence
 Digital Forensics More than: • Investigating computer-related incidents • Incident Response But: • Collecting evidence and building a story that can be used in court – and if necessary lead to a conviction
Digital Forensics More than: • Investigating computer-related incidents • Incident Response But: • Collecting evidence and building a story that can be used in court – and if necessary lead to a conviction
 Digital Forensics Thus: • Everything you would need to do while investigating a computer incident • Making sure that some-one can test and verify everything you claim • Complying with the needs and peculiarities of the law
Digital Forensics Thus: • Everything you would need to do while investigating a computer incident • Making sure that some-one can test and verify everything you claim • Complying with the needs and peculiarities of the law
 Digital Forensics We are going to look at these issues mostly via a case study • Demonstrates most types of computerderived evidence • Shows how a good complex case is put together • Illustrates various legal needs • Shows how, after all this, a case may fail
Digital Forensics We are going to look at these issues mostly via a case study • Demonstrates most types of computerderived evidence • Shows how a good complex case is put together • Illustrates various legal needs • Shows how, after all this, a case may fail
 Digital Forensics But first, we need to introduce some legal terminology, give a bit of background ….
Digital Forensics But first, we need to introduce some legal terminology, give a bit of background ….
 Evidence in Court Adversarial Criminal Procedure: As used in US, UK and former UK colonies • police investigate; prosecuting authority / DA prosecutes; judge is chairman / enunciator of law; jury decides issues of fact; prosecution and defence arguments presented by lawyers: • proof is what is demonstrated before the court (not what “scientists” or “experts” say they believe)
Evidence in Court Adversarial Criminal Procedure: As used in US, UK and former UK colonies • police investigate; prosecuting authority / DA prosecutes; judge is chairman / enunciator of law; jury decides issues of fact; prosecution and defence arguments presented by lawyers: • proof is what is demonstrated before the court (not what “scientists” or “experts” say they believe)
 Evidence in Court • Admissibility (legal rules decided by judge) hearsay, documents, unfairness in acquisition è Fed. Rules, 4 th Amendment; CALEA, PACE, 1984; CJA, 1988; RIPA, 2000; è • Weight (issues of fact) è what persuades a court is not the same as scientific “proof” - Frye, Daubert, Kuomo Tire
Evidence in Court • Admissibility (legal rules decided by judge) hearsay, documents, unfairness in acquisition è Fed. Rules, 4 th Amendment; CALEA, PACE, 1984; CJA, 1988; RIPA, 2000; è • Weight (issues of fact) è what persuades a court is not the same as scientific “proof” - Frye, Daubert, Kuomo Tire
 Attributes of Good Evidence • • • authentic accurate complete
Attributes of Good Evidence • • • authentic accurate complete
 Attributes of Good Evidence • chain of custody / continuity of evidence • transparent forensic procedures • accuracy of process • accuracy of content • explanations
Attributes of Good Evidence • chain of custody / continuity of evidence • transparent forensic procedures • accuracy of process • accuracy of content • explanations
 The Case Study Rome Labs
The Case Study Rome Labs
 Rome Labs • March-April 1994 - classic teenage hack of USAF, NASA, Lockheed etc sites • Rome Labs, New York, paralysed for nearly 3 weeks • “The most serious attack on the US military without the declaration of hostilities” • … used in 1996 GAO Report, Congressional “Security in Cyberspace” hearings, etc as an examplar of Information Warfare
Rome Labs • March-April 1994 - classic teenage hack of USAF, NASA, Lockheed etc sites • Rome Labs, New York, paralysed for nearly 3 weeks • “The most serious attack on the US military without the declaration of hostilities” • … used in 1996 GAO Report, Congressional “Security in Cyberspace” hearings, etc as an examplar of Information Warfare
 GAO Report
GAO Report
 Rome Labs Sources: • I was hired by UK defense lawyers (in the English legal system) • The evidence before the UK courts • USAF investigators • Scotland Yard investigators • The perpetrators
Rome Labs Sources: • I was hired by UK defense lawyers (in the English legal system) • The evidence before the UK courts • USAF investigators • Scotland Yard investigators • The perpetrators
 • Important perpetrator: “Datastream Cowboy” • USAF investigator recalls IRC session with a “Datastream Cowboy” several months earlier - had provided London, UK, phone number • Via Scotland Yard Computer Crime Unit: phone number linked to Richard Pryce, 16 yrs old
• Important perpetrator: “Datastream Cowboy” • USAF investigator recalls IRC session with a “Datastream Cowboy” several months earlier - had provided London, UK, phone number • Via Scotland Yard Computer Crime Unit: phone number linked to Richard Pryce, 16 yrs old
 R v Richard Pryce
R v Richard Pryce

 Datastream Cowboy Richard Pryce
Datastream Cowboy Richard Pryce
 Datastream Cowboy Richard Pryce The Legal Problem: How do you prove the link?
Datastream Cowboy Richard Pryce The Legal Problem: How do you prove the link?
 How the hack happened
How the hack happened
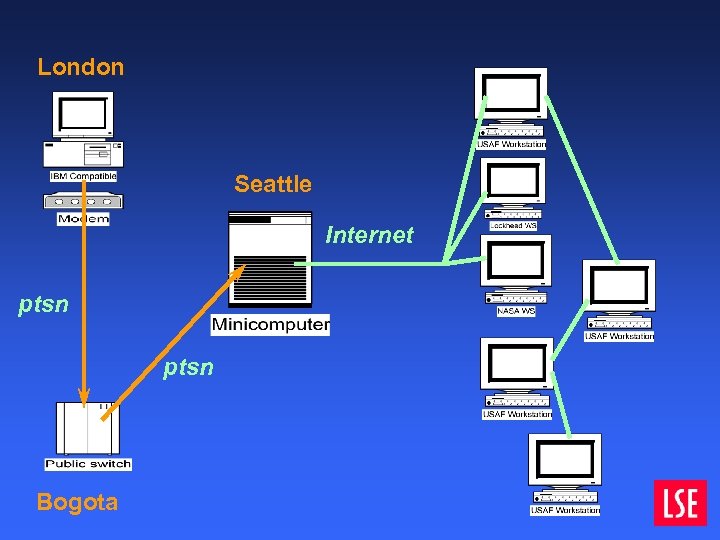 London Seattle Internet ptsn Bogota
London Seattle Internet ptsn Bogota
 How the hack was monitored
How the hack was monitored
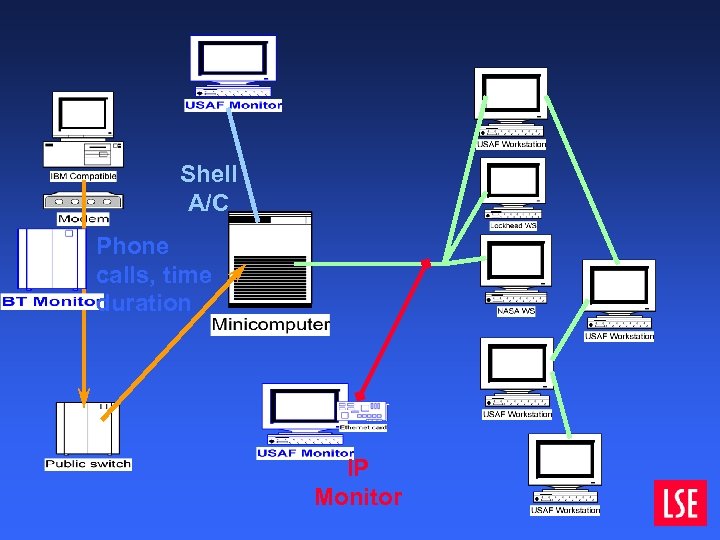 Shell A/C Phone calls, time duration IP Monitor
Shell A/C Phone calls, time duration IP Monitor
 How the hack was monitored: the evidence
How the hack was monitored: the evidence
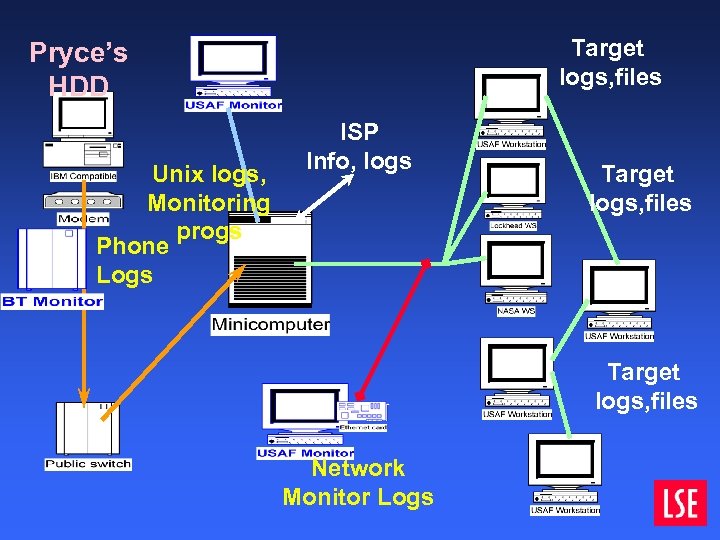 Target logs, files Pryce’s HDD Unix logs, Monitoring progs Phone Logs ISP Info, logs Target logs, files Network Monitor Logs
Target logs, files Pryce’s HDD Unix logs, Monitoring progs Phone Logs ISP Info, logs Target logs, files Network Monitor Logs
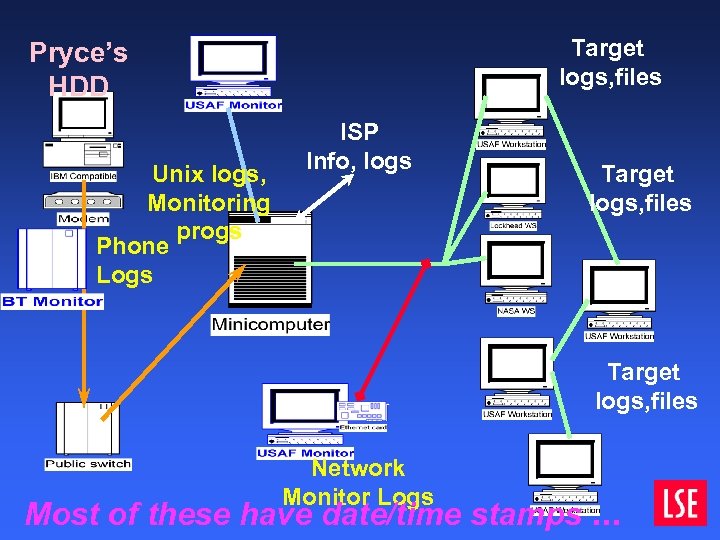 Target logs, files Pryce’s HDD Unix logs, Monitoring progs Phone Logs ISP Info, logs Target logs, files Network Monitor Logs Most of these have date/time stamps. . .
Target logs, files Pryce’s HDD Unix logs, Monitoring progs Phone Logs ISP Info, logs Target logs, files Network Monitor Logs Most of these have date/time stamps. . .
 Role of Defence Expert Prior to trial • explain evidence to lawyers • look for weaknesses At trial • assist lawyers • (perhaps) give evidence fact & opinion è answers must be complete è
Role of Defence Expert Prior to trial • explain evidence to lawyers • look for weaknesses At trial • assist lawyers • (perhaps) give evidence fact & opinion è answers must be complete è
 Role of Defence Expert • Acts under instruction - specific instruction: “Discard any admissions in interview; show us the weaknesses in the digital evidence …”
Role of Defence Expert • Acts under instruction - specific instruction: “Discard any admissions in interview; show us the weaknesses in the digital evidence …”
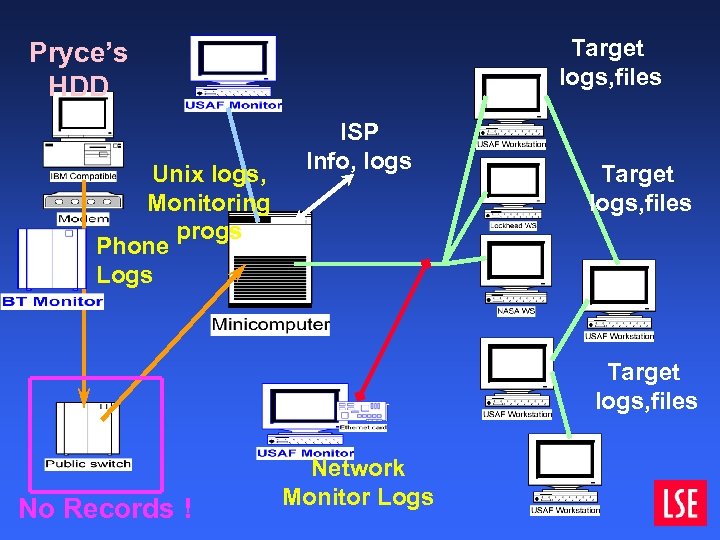 Target logs, files Pryce’s HDD Unix logs, Monitoring progs Phone Logs ISP Info, logs Target logs, files No Records ! Network Monitor Logs
Target logs, files Pryce’s HDD Unix logs, Monitoring progs Phone Logs ISP Info, logs Target logs, files No Records ! Network Monitor Logs
 Breaking the Digital Evidence • • • Pryce’s HDD BT Call Monitor ISP Monitored Shell A/c ISP Own Statements USAF Network Monitors Target Records
Breaking the Digital Evidence • • • Pryce’s HDD BT Call Monitor ISP Monitored Shell A/c ISP Own Statements USAF Network Monitors Target Records
 Breaking the Digital Evidence Pryce’s HDD • 170 MB ! • lots of hacking tools • partial logs of IRC sessions • password and IP address files • files apparently from some target computers • music-related files
Breaking the Digital Evidence Pryce’s HDD • 170 MB ! • lots of hacking tools • partial logs of IRC sessions • password and IP address files • files apparently from some target computers • music-related files
 Breaking the Digital Evidence Pryce’s HDD • disk imaging - evidence preservation • print-outs • PII certificate - sensitive files • recovered data • corrupted files • was there more than one source for target password files?
Breaking the Digital Evidence Pryce’s HDD • disk imaging - evidence preservation • print-outs • PII certificate - sensitive files • recovered data • corrupted files • was there more than one source for target password files?
 Breaking the Digital Evidence BT Call Monitor • records numbers dialled, time, duration, not content • inconsistent print-out
Breaking the Digital Evidence BT Call Monitor • records numbers dialled, time, duration, not content • inconsistent print-out
 Breaking the Digital Evidence ISP Monitored Shell A/c • ps, w, automated, semi-automated, manual • how were evidential print-outs controlled and preserved? • team effort - who reports?
Breaking the Digital Evidence ISP Monitored Shell A/c • ps, w, automated, semi-automated, manual • how were evidential print-outs controlled and preserved? • team effort - who reports?
 Breaking the Digital Evidence ISP Monitored Shell A/c • print-out depends on accuracy of: ISP Cyber. Space machine è computers hosting monitoring facilities è monitoring programs - disclosure è human operators è continuity of evidence è clock timings !! è
Breaking the Digital Evidence ISP Monitored Shell A/c • print-out depends on accuracy of: ISP Cyber. Space machine è computers hosting monitoring facilities è monitoring programs - disclosure è human operators è continuity of evidence è clock timings !! è
 Breaking the Digital Evidence USAF Network Monitor • monitors IP traffic on sub-net • principle is OK, but how achieved? • monitoring point(s) • quality of program - disclosure • continuity of evidence • team work
Breaking the Digital Evidence USAF Network Monitor • monitors IP traffic on sub-net • principle is OK, but how achieved? • monitoring point(s) • quality of program - disclosure • continuity of evidence • team work
 Breaking the Digital Evidence Target Records • freezing of scene • continuity of evidence • “I recognise …. ” • honey traps
Breaking the Digital Evidence Target Records • freezing of scene • continuity of evidence • “I recognise …. ” • honey traps
 Lessons from Rome Labs • Hackers invented no new techniques but used existing ones well with great determination and stamina • USAF computers poorly secured è fixed IP addresses, default passwords è little use of CERT etc advisories è
Lessons from Rome Labs • Hackers invented no new techniques but used existing ones well with great determination and stamina • USAF computers poorly secured è fixed IP addresses, default passwords è little use of CERT etc advisories è
 Lessons from Rome Labs • Hackers were often rejected; would have had many more failures with better elementary security • US investigators hampered by internal jurisdictional boundaries • US investigators had very little training in evidence collection • US/UK collaboration was quite good!
Lessons from Rome Labs • Hackers were often rejected; would have had many more failures with better elementary security • US investigators hampered by internal jurisdictional boundaries • US investigators had very little training in evidence collection • US/UK collaboration was quite good!
 Conclusions • Digital Evidence alone would have been insufficient • Good technical methods alone would not have worked • Effects of team efforts • Poor evidence continuity • Disclosure of methods issues
Conclusions • Digital Evidence alone would have been insufficient • Good technical methods alone would not have worked • Effects of team efforts • Poor evidence continuity • Disclosure of methods issues
 Introducing Digital Forensics Peter Sommer London School of Economics, UK
Introducing Digital Forensics Peter Sommer London School of Economics, UK


