55424b5a4b7af8ad87b39e499a5a968b.ppt
- Количество слайдов: 62
 Intro to Info Tech Computer Issues This presentation can be viewed on line at: Copyright 2007 http: //web. fscj. edu/Janson/cgs 1060/wk 14. Issues. ppt by Janson Industries 1
Intro to Info Tech Computer Issues This presentation can be viewed on line at: Copyright 2007 http: //web. fscj. edu/Janson/cgs 1060/wk 14. Issues. ppt by Janson Industries 1
 Objectives n Discuss major issues impeding the spread of computers u u Privacy u n Security: H/W, S/W and data Health Show IT companies combat these issues 2 Copyright 2012 by Janson Industries
Objectives n Discuss major issues impeding the spread of computers u u Privacy u n Security: H/W, S/W and data Health Show IT companies combat these issues 2 Copyright 2012 by Janson Industries
 Security n Issue: unauthorized access to computing resources u Not just destruction u Changing, even copying Your Visa balance is now 0 F SSNs, Grand Theft Auto 17 F n People minimize because it's impersonal (just files, non-violent) 3 Copyright 2012 by Janson Industries
Security n Issue: unauthorized access to computing resources u Not just destruction u Changing, even copying Your Visa balance is now 0 F SSNs, Grand Theft Auto 17 F n People minimize because it's impersonal (just files, non-violent) 3 Copyright 2012 by Janson Industries
 Cybercriminal types n Hacker u Non-malicious u Trying n to "show security problems" Cracker u Malicious n access Script kiddie u Follow instructions or use s/w u No technical skills 4 Copyright 2012 by Janson Industries
Cybercriminal types n Hacker u Non-malicious u Trying n to "show security problems" Cracker u Malicious n access Script kiddie u Follow instructions or use s/w u No technical skills 4 Copyright 2012 by Janson Industries
 Cybercriminal types n Corporate spies u Usually u Trying not destructive to steal or gather info Hitachi F http: //www. businesspundit. com/10 most-notorious-acts-of-corporateespionage/ F n Unethical employees u Revenge u For F Copyright 2012 by Janson Industries – destructive profit Salami shaving 5
Cybercriminal types n Corporate spies u Usually u Trying not destructive to steal or gather info Hitachi F http: //www. businesspundit. com/10 most-notorious-acts-of-corporateespionage/ F n Unethical employees u Revenge u For F Copyright 2012 by Janson Industries – destructive profit Salami shaving 5
 Cybercriminal types n Cyberextortionist u Threatens to harm computer resources or expose info Overwhelm a company's servers F Delete data F u Looking F n to be paid off Is this any better then Somali pirates? Cyberterrorist u Attack and destroy computer resources F Copyright 2012 by Janson Industries US in Gulf War 1 6
Cybercriminal types n Cyberextortionist u Threatens to harm computer resources or expose info Overwhelm a company's servers F Delete data F u Looking F n to be paid off Is this any better then Somali pirates? Cyberterrorist u Attack and destroy computer resources F Copyright 2012 by Janson Industries US in Gulf War 1 6
 Attack Types n n n Attacks rarely done by hand at a computer Usually involves unleashing some malware (malicious s/w) Viruses u S/W that is installed unknowingly u May harm or simply copy Keep track of accounts and pws F Relay info back F u May Copyright 2012 by Janson Industries replicate onto other computers 7
Attack Types n n n Attacks rarely done by hand at a computer Usually involves unleashing some malware (malicious s/w) Viruses u S/W that is installed unknowingly u May harm or simply copy Keep track of accounts and pws F Relay info back F u May Copyright 2012 by Janson Industries replicate onto other computers 7
 Attack Types n Worm u Replicates itself over and over, impeding the system F n "I love you" email Trojan horse u S/W that is inside legitimate s/w u Usually F an event kicks it off Michaelangelo 8 Copyright 2012 by Janson Industries
Attack Types n Worm u Replicates itself over and over, impeding the system F n "I love you" email Trojan horse u S/W that is inside legitimate s/w u Usually F an event kicks it off Michaelangelo 8 Copyright 2012 by Janson Industries
 Attack Types n Malware can do many things u Slow system performance u Destroy F s/w and data Even operating system u Change system settings u Deny system usage (Do. S – Denial of Service attack) Lock out the keyboard F Flood an email server F Yankee Doodle F Copyright 2012 by Janson Industries 9
Attack Types n Malware can do many things u Slow system performance u Destroy F s/w and data Even operating system u Change system settings u Deny system usage (Do. S – Denial of Service attack) Lock out the keyboard F Flood an email server F Yankee Doodle F Copyright 2012 by Janson Industries 9
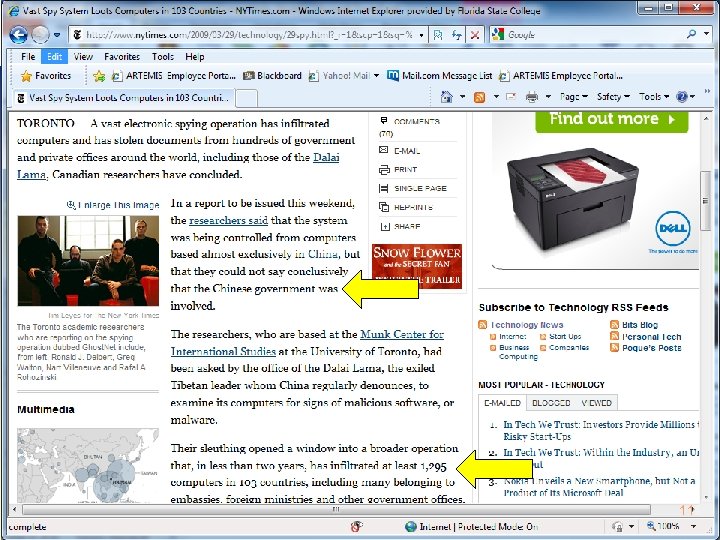
 Attack Types n Botnets u. A network of infected computers u Infected computers called zombies F User doesn’t know that the computer is being controlled remotely u Your good IP address used to: Send spam F Attack servers F Access other computers F n Headline from NYT 3/29/09 Vast Spy System Loots Computers in 103 Countries Copyright 2012 by Janson Industries 10
Attack Types n Botnets u. A network of infected computers u Infected computers called zombies F User doesn’t know that the computer is being controlled remotely u Your good IP address used to: Send spam F Attack servers F Access other computers F n Headline from NYT 3/29/09 Vast Spy System Loots Computers in 103 Countries Copyright 2012 by Janson Industries 10
 11 Copyright 2012 by Janson Industries
11 Copyright 2012 by Janson Industries
 Attack Types n Backdoors: access that circumvents security u Programmer created when s/w written u Installed after initial illegal access Certain key combination F Create a new user id and pw F n Copyright 2012 by Janson Industries Spoofing: make your computer resources look like someone else's u Make your ip or email address look like BOAs 12
Attack Types n Backdoors: access that circumvents security u Programmer created when s/w written u Installed after initial illegal access Certain key combination F Create a new user id and pw F n Copyright 2012 by Janson Industries Spoofing: make your computer resources look like someone else's u Make your ip or email address look like BOAs 12
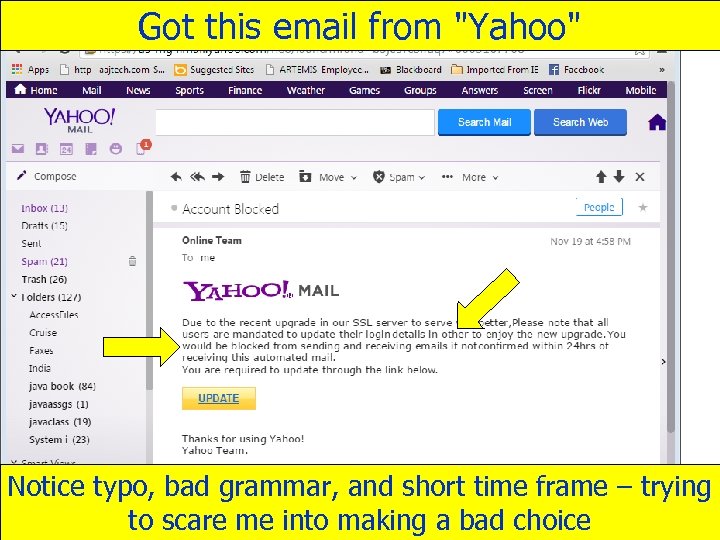 Got this email from "Yahoo" Notice typo, bad grammar, and short time frame – trying 13 to scare me into making a bad choice Copyright 2012 by Janson Industries
Got this email from "Yahoo" Notice typo, bad grammar, and short time frame – trying 13 to scare me into making a bad choice Copyright 2012 by Janson Industries
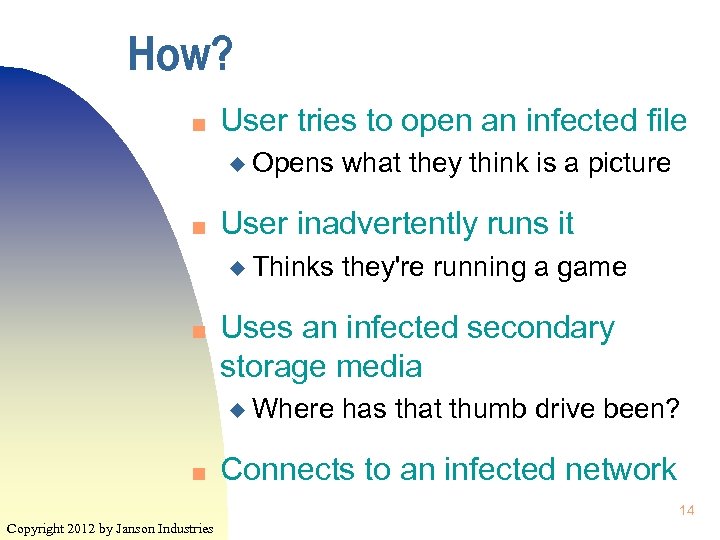 How? n User tries to open an infected file u Opens n User inadvertently runs it u Thinks n they're running a game Uses an infected secondary storage media u Where n what they think is a picture has that thumb drive been? Connects to an infected network 14 Copyright 2012 by Janson Industries
How? n User tries to open an infected file u Opens n User inadvertently runs it u Thinks n they're running a game Uses an infected secondary storage media u Where n what they think is a picture has that thumb drive been? Connects to an infected network 14 Copyright 2012 by Janson Industries
 Prevention? n n n Never open a file from an unknown source Don't use unknown secondary storage media Don't open email attachments unless they are expected u Even n if it is from someone you trust Install antivirus s/w u Most Copyright 2012 by Janson Industries computers come with some u Lots of free stuff available 15
Prevention? n n n Never open a file from an unknown source Don't use unknown secondary storage media Don't open email attachments unless they are expected u Even n if it is from someone you trust Install antivirus s/w u Most Copyright 2012 by Janson Industries computers come with some u Lots of free stuff available 15
 Antivirus S/W n Initially will scan all files looking for malware If found will delete u If can't delete will quarantine u n n Thereafter will check any downloaded files Update s/w often u Updates will protect against the latest threats 16 Copyright 2012 by Janson Industries
Antivirus S/W n Initially will scan all files looking for malware If found will delete u If can't delete will quarantine u n n Thereafter will check any downloaded files Update s/w often u Updates will protect against the latest threats 16 Copyright 2012 by Janson Industries
 Some OS let you automate the updates 17 Copyright 2012 by Janson Industries
Some OS let you automate the updates 17 Copyright 2012 by Janson Industries
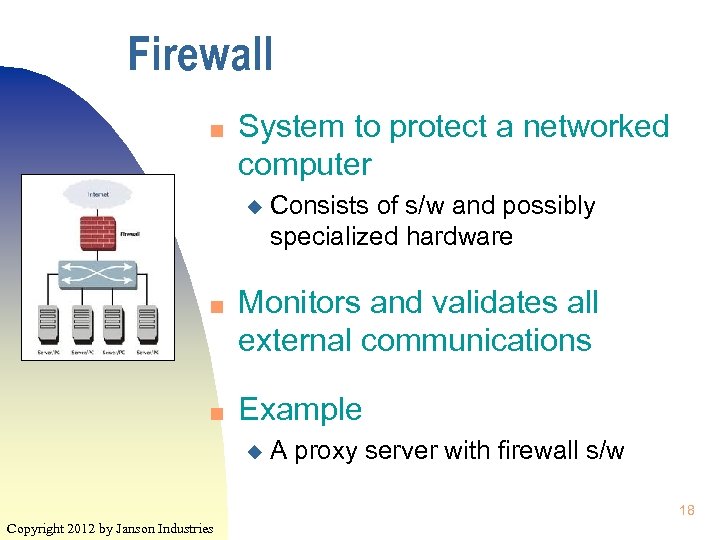 Firewall n System to protect a networked computer u n n Consists of s/w and possibly specialized hardware Monitors and validates all external communications Example u A proxy server with firewall s/w 18 Copyright 2012 by Janson Industries
Firewall n System to protect a networked computer u n n Consists of s/w and possibly specialized hardware Monitors and validates all external communications Example u A proxy server with firewall s/w 18 Copyright 2012 by Janson Industries
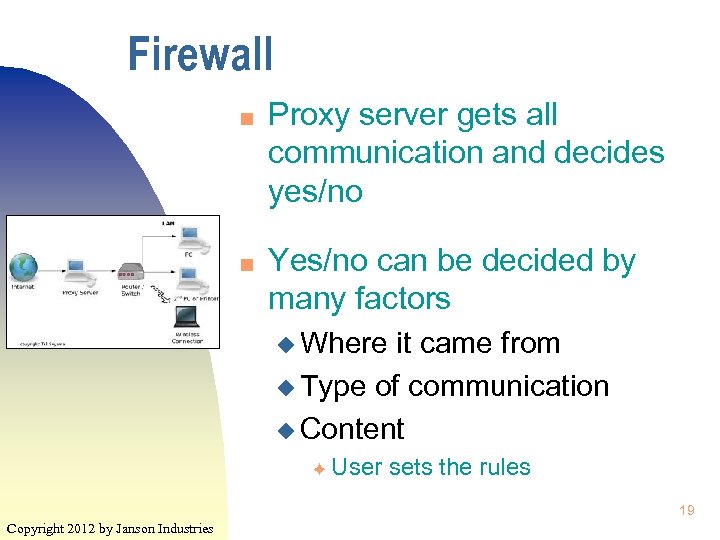 Firewall n n Proxy server gets all communication and decides yes/no Yes/no can be decided by many factors u Where it came from u Type of communication u Content F User sets the rules 19 Copyright 2012 by Janson Industries
Firewall n n Proxy server gets all communication and decides yes/no Yes/no can be decided by many factors u Where it came from u Type of communication u Content F User sets the rules 19 Copyright 2012 by Janson Industries
 Firewall n Examples: u No FTP communications allowed u No executable files u Only these IP addresses allowed n Additional advantage u No direct access to internal network External systems don't know location of internal resources F Can only attack the proxy F 20 Copyright 2012 by Janson Industries
Firewall n Examples: u No FTP communications allowed u No executable files u Only these IP addresses allowed n Additional advantage u No direct access to internal network External systems don't know location of internal resources F Can only attack the proxy F 20 Copyright 2012 by Janson Industries
 User Authentication n Create user id and pw u Person must specify before access granted u Not perfect: can be hacked Hacker tries every possible combo F System only allows 5 unsuccessful attempts F n Physical objects like FOBs Every minute generates a new code u Or, like a car, unlocks the computer u n Copyright 2012 by Janson Industries Biometric devices 21
User Authentication n Create user id and pw u Person must specify before access granted u Not perfect: can be hacked Hacker tries every possible combo F System only allows 5 unsuccessful attempts F n Physical objects like FOBs Every minute generates a new code u Or, like a car, unlocks the computer u n Copyright 2012 by Janson Industries Biometric devices 21
 User Authentication n Digital signature u Encrypted code added to a message Confirms who you are F Can also confirm content not changed (like a check bit) F n Digital certificate u Given to a site that has been certified secure u When communicating encrypted certificate sent with msg 22 Copyright 2012 by Janson Industries
User Authentication n Digital signature u Encrypted code added to a message Confirms who you are F Can also confirm content not changed (like a check bit) F n Digital certificate u Given to a site that has been certified secure u When communicating encrypted certificate sent with msg 22 Copyright 2012 by Janson Industries
 System Security n Audit Trail: a record of u Sign on attempts u Date and time u Resources accessed F n Like chain of custody on CSI Additional security for individual resources u Shippers can access shipping data u Only bldg F computers can access the bldg F printer 23 Copyright 2012 by Janson Industries
System Security n Audit Trail: a record of u Sign on attempts u Date and time u Resources accessed F n Like chain of custody on CSI Additional security for individual resources u Shippers can access shipping data u Only bldg F computers can access the bldg F printer 23 Copyright 2012 by Janson Industries
 Hardware Theft n Kept behind locked doors n Cabled to desk n Need physical device to operate n Policies u. I can't leave students unattended in lab 24 Copyright 2012 by Janson Industries
Hardware Theft n Kept behind locked doors n Cabled to desk n Need physical device to operate n Policies u. I can't leave students unattended in lab 24 Copyright 2012 by Janson Industries
 Information Theft n n Both from storage and when transmitted over network Encryption u Windows allows you to encrypt files and folders F Just another property u Takes longer to access cause it must be decrypted u DVDs are encrypted (CSS – Content Scrambling System) Copyright 2012 by Janson Industries 25
Information Theft n n Both from storage and when transmitted over network Encryption u Windows allows you to encrypt files and folders F Just another property u Takes longer to access cause it must be decrypted u DVDs are encrypted (CSS – Content Scrambling System) Copyright 2012 by Janson Industries 25
 Software Piracy n Illegally copying u Retards n new development Many levels u Government u Corporate u Private Copying for friends F Copying to sell F n n Copyright 2012 by Janson Industries License agreement Product activation key 26
Software Piracy n Illegally copying u Retards n new development Many levels u Government u Corporate u Private Copying for friends F Copying to sell F n n Copyright 2012 by Janson Industries License agreement Product activation key 26
 Software Piracy n n In addition, laws are sometimes vague Copyright gives "fair use" to purchasers u Can you install a game on multiple computers? u Can you "rip" a movie DVD so you can watch it on your laptop? u Can a restaurant show the movie? u Can you post the movie on your website so others can watch? Copyright 2012 by Janson Industries 27
Software Piracy n n In addition, laws are sometimes vague Copyright gives "fair use" to purchasers u Can you install a game on multiple computers? u Can you "rip" a movie DVD so you can watch it on your laptop? u Can a restaurant show the movie? u Can you post the movie on your website so others can watch? Copyright 2012 by Janson Industries 27
 Software Piracy n SOPA – Stop Online Piracy Act n What is it? u HR 3261 u Legal action can be taken by Do. J or copyright owner against any site deemed to have "only limited purpose or use other than infringement” 28 Copyright 2012 by Janson Industries
Software Piracy n SOPA – Stop Online Piracy Act n What is it? u HR 3261 u Legal action can be taken by Do. J or copyright owner against any site deemed to have "only limited purpose or use other than infringement” 28 Copyright 2012 by Janson Industries
 Software Piracy u Can demand that search engines, social networking sites and domain name services block access to the targeted site F If these companies fail to comply, Do. J or copyright owner can begin legal proceedings against them u Makes unauthorized web streaming of copyrighted content a felony with a penalty up to five years in prison 29 Copyright 2012 by Janson Industries
Software Piracy u Can demand that search engines, social networking sites and domain name services block access to the targeted site F If these companies fail to comply, Do. J or copyright owner can begin legal proceedings against them u Makes unauthorized web streaming of copyrighted content a felony with a penalty up to five years in prison 29 Copyright 2012 by Janson Industries
 SOPA n Who’s fer it? u Motion Picture Assoc of America u Entertainment S/W Assoc u Go. Daddy. com n Who’s agin it? u Google u Wikipedia u Major League Gaming u Obama Copyright 2012 by Janson Industries 30
SOPA n Who’s fer it? u Motion Picture Assoc of America u Entertainment S/W Assoc u Go. Daddy. com n Who’s agin it? u Google u Wikipedia u Major League Gaming u Obama Copyright 2012 by Janson Industries 30
 Software Piracy n What about PIPA (Protect IP Act) u Stop search engines (Google, Yahoo) from directing users to sites with stolen content n Came before the Senate 1/24/2012 31 Copyright 2012 by Janson Industries
Software Piracy n What about PIPA (Protect IP Act) u Stop search engines (Google, Yahoo) from directing users to sites with stolen content n Came before the Senate 1/24/2012 31 Copyright 2012 by Janson Industries
 System Failure n Power surges u Surge n protector Power outage u UPS (uninterruptible power supply) u Usually include a surge protector n Disaster recovery u Backup data u Can automate 32 Copyright 2012 by Janson Industries
System Failure n Power surges u Surge n protector Power outage u UPS (uninterruptible power supply) u Usually include a surge protector n Disaster recovery u Backup data u Can automate 32 Copyright 2012 by Janson Industries
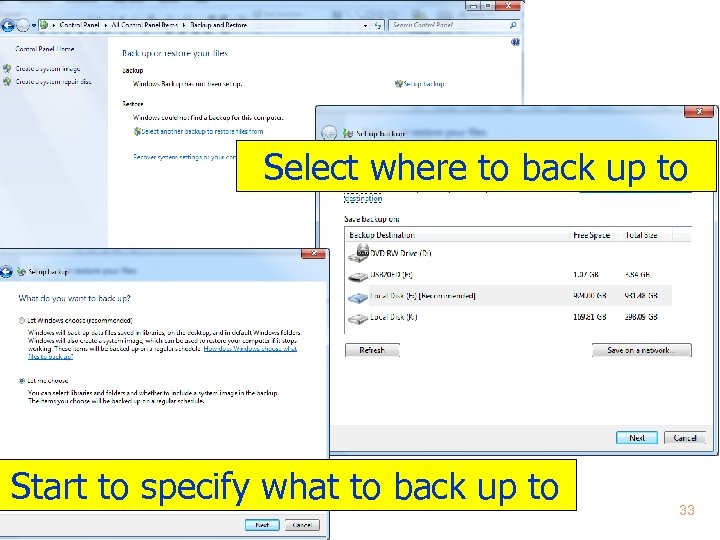 Select where to back up to Start to specify what to back up to Copyright 2012 by Janson Industries 33
Select where to back up to Start to specify what to back up to Copyright 2012 by Janson Industries 33
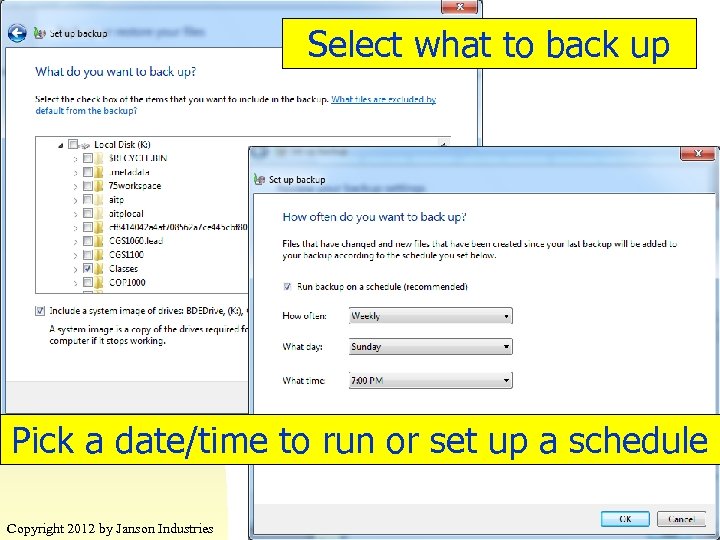 Select what to back up Pick a date/time to run or set up a schedule 34 Copyright 2012 by Janson Industries
Select what to back up Pick a date/time to run or set up a schedule 34 Copyright 2012 by Janson Industries
 Information Privacy n Concerns: u What u Is is being collected? it lawful to collect? u Who has access? u How well is it protected? 35 Copyright 2012 by Janson Industries
Information Privacy n Concerns: u What u Is is being collected? it lawful to collect? u Who has access? u How well is it protected? 35 Copyright 2012 by Janson Industries
 Unknowing Shoppers in Japan n n Security cameras film all customers in store If person shoplifts or makes an unreasonable complaint u Put on blacklist as "shoplifter" or "complainer" n When customer enters other stores, warning issued to store staff (that only they can see) 36 Copyright 2012 by Janson Industries
Unknowing Shoppers in Japan n n Security cameras film all customers in store If person shoplifts or makes an unreasonable complaint u Put on blacklist as "shoplifter" or "complainer" n When customer enters other stores, warning issued to store staff (that only they can see) 36 Copyright 2012 by Janson Industries
 Unknowing Shoppers in Japan n n Customers notified they are listed No recourse u If erroneous, no way to fix 37 Copyright 2012 by Janson Industries
Unknowing Shoppers in Japan n n Customers notified they are listed No recourse u If erroneous, no way to fix 37 Copyright 2012 by Janson Industries
 Event Data Recorder n Installed in cars, tracks u Direction u Speed u Seat n belt usage Will be mandatory in all cars 9/2014 u No warrant required for law enforcement to access 38 Copyright 2012 by Janson Industries
Event Data Recorder n Installed in cars, tracks u Direction u Speed u Seat n belt usage Will be mandatory in all cars 9/2014 u No warrant required for law enforcement to access 38 Copyright 2012 by Janson Industries
 Event Data Recorder n "We know everyone who breaks the law. We have GPS in your car, so we know what your doing. " u Jim Farley, Ford Motors Sales Executive n What about cameras in cars u Who has rights to those images? 39 Copyright 2012 by Janson Industries
Event Data Recorder n "We know everyone who breaks the law. We have GPS in your car, so we know what your doing. " u Jim Farley, Ford Motors Sales Executive n What about cameras in cars u Who has rights to those images? 39 Copyright 2012 by Janson Industries
 Event Data Recorder n 2015 Stingray has windshield mounted camera and microphone in cabin u Performance u Real n data recorder time feedback on driving GAO says some automakers keep data from onboard Nav systems and mapping apps 40 Copyright 2012 by Janson Industries
Event Data Recorder n 2015 Stingray has windshield mounted camera and microphone in cabin u Performance u Real n data recorder time feedback on driving GAO says some automakers keep data from onboard Nav systems and mapping apps 40 Copyright 2012 by Janson Industries
 What is Being Collected n Obviously: u Your doctor has your medical records u Amazon knows what you have bought, has your address, & CC # u Visa knows everything you bought, how much $, when, and where u Email provider, Face. Book, & My. Space have copies of all your emails and postings F Copyright 2012 by Janson Industries Google and Yahoo keep login records for 18 months 41
What is Being Collected n Obviously: u Your doctor has your medical records u Amazon knows what you have bought, has your address, & CC # u Visa knows everything you bought, how much $, when, and where u Email provider, Face. Book, & My. Space have copies of all your emails and postings F Copyright 2012 by Janson Industries Google and Yahoo keep login records for 18 months 41
 What is Being Collected n Not so obviously: u Cookies: files that store preferences Can be read to keep track of web sites you visit F Can be read to see what you like and appropriate ads displayed F u Spyware: tracks what sites you visit Installed surreptitiously on consumers F Employers use to track employee computer usage F Parents/husband-wife/boy-girl friend F 42 Copyright 2012 by Janson Industries
What is Being Collected n Not so obviously: u Cookies: files that store preferences Can be read to keep track of web sites you visit F Can be read to see what you like and appropriate ads displayed F u Spyware: tracks what sites you visit Installed surreptitiously on consumers F Employers use to track employee computer usage F Parents/husband-wife/boy-girl friend F 42 Copyright 2012 by Janson Industries
 What is Being Collected n Not so obviously: u Phishing: official looking email that solicits information F SSN, Bank Account #'s and PINs u Pharming: official looking website that solicits information F You try to go to BOA website and are directed to a look alike u Posted F info Your email address on your home page • Can I gather that and send you spam? • Can I sell that to spammers? Copyright 2012 by Janson Industries F Your pictures on My. Space, Facebook 43
What is Being Collected n Not so obviously: u Phishing: official looking email that solicits information F SSN, Bank Account #'s and PINs u Pharming: official looking website that solicits information F You try to go to BOA website and are directed to a look alike u Posted F info Your email address on your home page • Can I gather that and send you spam? • Can I sell that to spammers? Copyright 2012 by Janson Industries F Your pictures on My. Space, Facebook 43
 Is it Lawful to Collect n Obviously not u Phishing, n Pharming Obviously u Email, Face. Book, My. Space u Info used to conduct business Amazon, your doctor, Visa F But only info needed to do business F n Not so obviously u Cookies, Spyware, Posted info u If deleted, can Face. Book keep copy? 44 Copyright 2012 by Janson Industries
Is it Lawful to Collect n Obviously not u Phishing, n Pharming Obviously u Email, Face. Book, My. Space u Info used to conduct business Amazon, your doctor, Visa F But only info needed to do business F n Not so obviously u Cookies, Spyware, Posted info u If deleted, can Face. Book keep copy? 44 Copyright 2012 by Janson Industries
 Is it Lawful to Collect n Not so obviously u Cookies: provide convenience u Spyware: Parent/employer have the right to monitor F Aren't your activities on the web just like walking into different stores in a mall? F • So, it's public domain information u Monitoring F Lawsuits pending re: whether employer can read your email? Currently – YES! u Cameras F Copyright 2012 by Janson Industries Email in the workplace Should the college be able to put cameras 45 in all the classrooms?
Is it Lawful to Collect n Not so obviously u Cookies: provide convenience u Spyware: Parent/employer have the right to monitor F Aren't your activities on the web just like walking into different stores in a mall? F • So, it's public domain information u Monitoring F Lawsuits pending re: whether employer can read your email? Currently – YES! u Cameras F Copyright 2012 by Janson Industries Email in the workplace Should the college be able to put cameras 45 in all the classrooms?
 Is it Lawful to Collect n Not so obviously u Posted F F F info: public domain Can I use your images on my website? Why can't a company use to sell a product? Even if deleted, wasn’t it made available to everyone? • Face. Book tried to change its usage policy to imply they had rights to everything forever 46 Copyright 2012 by Janson Industries
Is it Lawful to Collect n Not so obviously u Posted F F F info: public domain Can I use your images on my website? Why can't a company use to sell a product? Even if deleted, wasn’t it made available to everyone? • Face. Book tried to change its usage policy to imply they had rights to everything forever 46 Copyright 2012 by Janson Industries
 Who Can See It n Authorities need a search warrant from a judge to see emails that are u Less n than 180 days old and unread In some cases: u Prosecutors can obtain a court order by presenting facts that suggest the messages are relevant u Prosecutors can issue subpoenas without any court involvement 47 Copyright 2012 by Janson Industries
Who Can See It n Authorities need a search warrant from a judge to see emails that are u Less n than 180 days old and unread In some cases: u Prosecutors can obtain a court order by presenting facts that suggest the messages are relevant u Prosecutors can issue subpoenas without any court involvement 47 Copyright 2012 by Janson Industries
 Who Can See It n After arrests police have been searching cell phones u See where arrestee has been, who called, etc. n 6/25/14 ruling by Supreme Court requires police to get warrant u The fact that the new technology make private life portable renders it no "less worthy of the protection for which the Founders fought" – CJ Roberts 48 Copyright 2012 by Janson Industries
Who Can See It n After arrests police have been searching cell phones u See where arrestee has been, who called, etc. n 6/25/14 ruling by Supreme Court requires police to get warrant u The fact that the new technology make private life portable renders it no "less worthy of the protection for which the Founders fought" – CJ Roberts 48 Copyright 2012 by Janson Industries
 Who Can See It n n The Supreme Court ruling only affects gov't searches Corporate, commercial, and workplace privacy still not fully settled 49 Copyright 2012 by Janson Industries
Who Can See It n n The Supreme Court ruling only affects gov't searches Corporate, commercial, and workplace privacy still not fully settled 49 Copyright 2012 by Janson Industries
 Who Can See It n There are some laws that clarify: u Companies can't release: Video rental history F Cable subscribers records F Credit records F u Limits on: Educational records F Government records F Disclosure of health records F 50 Copyright 2012 by Janson Industries
Who Can See It n There are some laws that clarify: u Companies can't release: Video rental history F Cable subscribers records F Credit records F u Limits on: Educational records F Government records F Disclosure of health records F 50 Copyright 2012 by Janson Industries
 Who Can See It n How accurate is it? u If credit card company lists your income as $3 K instead of $30 K u Will you get: A mortgage from a bank? F A second credit card? F n Some rules u Must be able to see you credit report for free u Access to educational records F Copyright 2012 by Janson Industries 1974 51
Who Can See It n How accurate is it? u If credit card company lists your income as $3 K instead of $30 K u Will you get: A mortgage from a bank? F A second credit card? F n Some rules u Must be able to see you credit report for free u Access to educational records F Copyright 2012 by Janson Industries 1974 51
 Is It Protected n How safe is it? n A hospital is good at healing u How good is it at protecting the data? u How good is it at preventing unauthorized access? F Jax girl sent out 20 letters 52 Copyright 2012 by Janson Industries
Is It Protected n How safe is it? n A hospital is good at healing u How good is it at protecting the data? u How good is it at preventing unauthorized access? F Jax girl sent out 20 letters 52 Copyright 2012 by Janson Industries
 How email is Protected n Digital Signatures u Some encrypted code attached to email to prove it is authentic n Certificates u 3 rd party validation that email is authentic n DMARC u Common spec for email authentication u Yahoo, MS, FB, Google support it 53 Copyright 2012 by Janson Industries
How email is Protected n Digital Signatures u Some encrypted code attached to email to prove it is authentic n Certificates u 3 rd party validation that email is authentic n DMARC u Common spec for email authentication u Yahoo, MS, FB, Google support it 53 Copyright 2012 by Janson Industries
 How to Protect Privacy n Anonymizers u Proxy server between client and the Internet u Hides who you are from sites and where you go on the Internet F Of course, it can be tracked that you are using an anonymizer u Some repressive govts ban the use u Anonymizer. com 54 Copyright 2012 by Janson Industries
How to Protect Privacy n Anonymizers u Proxy server between client and the Internet u Hides who you are from sites and where you go on the Internet F Of course, it can be tracked that you are using an anonymizer u Some repressive govts ban the use u Anonymizer. com 54 Copyright 2012 by Janson Industries
 How to Protect Privacy n Onion Router s/w u Pass communications between a network of servers F Conceals original location u Data F encrypted multiple times At each relayed server, one layer of decryption is performed u www. torproject. org F Browser that hides you location 55 Copyright 2012 by Janson Industries
How to Protect Privacy n Onion Router s/w u Pass communications between a network of servers F Conceals original location u Data F encrypted multiple times At each relayed server, one layer of decryption is performed u www. torproject. org F Browser that hides you location 55 Copyright 2012 by Janson Industries
 56 Copyright 2012 by Janson Industries
56 Copyright 2012 by Janson Industries
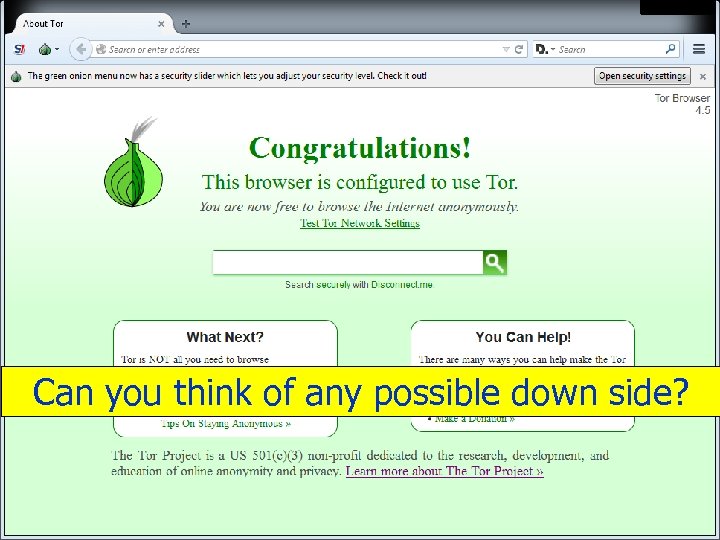 Can you think of any possible down side? 57 Copyright 2012 by Janson Industries
Can you think of any possible down side? 57 Copyright 2012 by Janson Industries
 How to Protect Privacy n Encrypt your messages/files u Some email services offer this service along with other options such as timed destruction of msgs and email addrs u Software F to encrypt Windows provides encryption capability u Wickr – mobile app to encrypt photos, text, etc. F When file erased, writes over metadata that could be used to recreate info 58 Copyright 2012 by Janson Industries
How to Protect Privacy n Encrypt your messages/files u Some email services offer this service along with other options such as timed destruction of msgs and email addrs u Software F to encrypt Windows provides encryption capability u Wickr – mobile app to encrypt photos, text, etc. F When file erased, writes over metadata that could be used to recreate info 58 Copyright 2012 by Janson Industries
 Computers and Health n Any health issues? n Dropping one on your foot would hurt. u RSI F (repetitive strain/stress injury) Keyboard, mouse, joy stick u Eye strain u Backaches, headaches u "Play. Station" palm n Solution: ergonomics and common sense u “Maybe you should take a break” 59 Copyright 2012 by Janson Industries
Computers and Health n Any health issues? n Dropping one on your foot would hurt. u RSI F (repetitive strain/stress injury) Keyboard, mouse, joy stick u Eye strain u Backaches, headaches u "Play. Station" palm n Solution: ergonomics and common sense u “Maybe you should take a break” 59 Copyright 2012 by Janson Industries
 Computers and Health n Computer addiction u Is there something inherent in the computer to make it addictive? u People get addicted to: Shoes F Shopping F Gambling F u Has more to do with the person than the thing u What Copyright 2012 by Janson Industries about games? 60
Computers and Health n Computer addiction u Is there something inherent in the computer to make it addictive? u People get addicted to: Shoes F Shopping F Gambling F u Has more to do with the person than the thing u What Copyright 2012 by Janson Industries about games? 60
 Computers and Health n Huge amount of electronic waste n Toxic materials in the devices n Electricity usage n Solutions u Laws about recycling devices u Green computing Use energy star devices F When possible print on both sides of paper F Recycle paper, toner and ink cartridges F 61 Copyright 2012 by Janson Industries
Computers and Health n Huge amount of electronic waste n Toxic materials in the devices n Electricity usage n Solutions u Laws about recycling devices u Green computing Use energy star devices F When possible print on both sides of paper F Recycle paper, toner and ink cartridges F 61 Copyright 2012 by Janson Industries
 Points to Remember n People resist using computers because of concerns re: Crime/safety u Privacy u Health u n n Copyright 2012 by Janson Industries Computer and s/w mfgs continue to improve products to solve these issues Govt passing laws to clarify what can and cannot be done 62
Points to Remember n People resist using computers because of concerns re: Crime/safety u Privacy u Health u n n Copyright 2012 by Janson Industries Computer and s/w mfgs continue to improve products to solve these issues Govt passing laws to clarify what can and cannot be done 62


