ef5efa2eb164df4ab3609d7fe7ca1be2.ppt
- Количество слайдов: 13
 Intro to DNS SOEN 321 - Information Systems Security October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 1
Intro to DNS SOEN 321 - Information Systems Security October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 1
 Contents • Intro to DNS and Security October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 2
Contents • Intro to DNS and Security October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 2
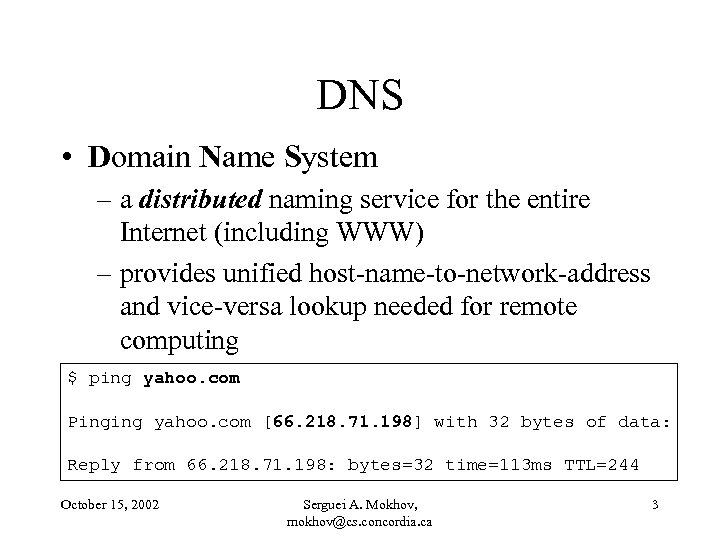 DNS • Domain Name System – a distributed naming service for the entire Internet (including WWW) – provides unified host-name-to-network-address and vice-versa lookup needed for remote computing $ ping yahoo. com Pinging yahoo. com [66. 218. 71. 198] with 32 bytes of data: Reply from 66. 218. 71. 198: bytes=32 time=113 ms TTL=244 October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 3
DNS • Domain Name System – a distributed naming service for the entire Internet (including WWW) – provides unified host-name-to-network-address and vice-versa lookup needed for remote computing $ ping yahoo. com Pinging yahoo. com [66. 218. 71. 198] with 32 bytes of data: Reply from 66. 218. 71. 198: bytes=32 time=113 ms TTL=244 October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 3
 DNS • Other capabilities: – Info about Name Servers – Canonical host names – Mail Exchange (MX) records October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 4
DNS • Other capabilities: – Info about Name Servers – Canonical host names – Mail Exchange (MX) records October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 4
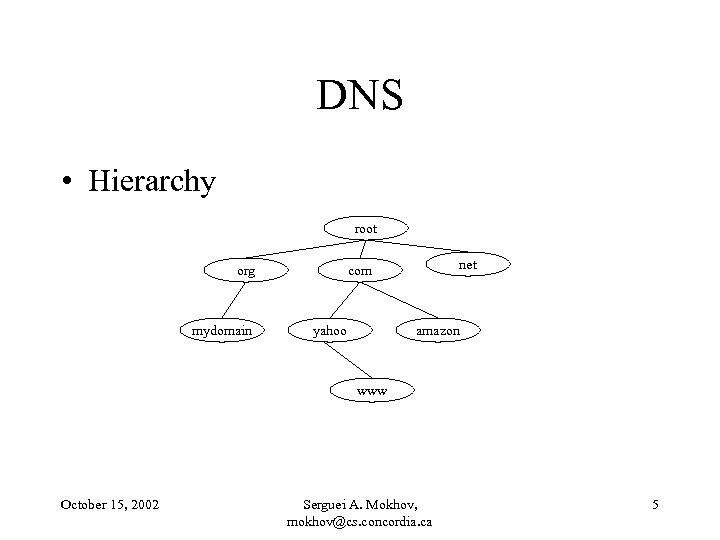 DNS • Hierarchy root org mydomain net com yahoo amazon www October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 5
DNS • Hierarchy root org mydomain net com yahoo amazon www October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 5
 DNS Tools in UNIX • Tools – host – dig – nslookup (deprecated) October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 6
DNS Tools in UNIX • Tools – host – dig – nslookup (deprecated) October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 6
![DNS Tools Example haida. mokhov [~] % host -a www Trying DNS Tools Example haida. mokhov [~] % host -a www Trying](https://present5.com/presentation/ef5efa2eb164df4ab3609d7fe7ca1be2/image-7.jpg) DNS Tools Example haida. mokhov [~] % host -a www Trying "www. cs. concordia. ca" ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 3704 ; ; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 5, ADDITIONAL: 4 ; ; QUESTION SECTION: ; www. cs. concordia. ca. IN ANY ; ; ANSWER SECTION: www. cs. concordia. ca. 86400 IN CNAME spider. cs. concordia. ca. ; ; AUTHORITY SECTION: cs. concordia. ca. 86400 86400 IN IN IN NS NS NS clyde. concordia. ca. Jerome. Mc. RCIM. Mc. Gill. EDU. pollen. cs. concordia. ca. manitou. cs. concordia. ca. alcor. concordia. ca. IN IN A A 132. 205. 7. 51 132. 205. 1. 1 132. 205. 44. 61 132. 205. 4. 3 ; ; ADDITIONAL SECTION: alcor. concordia. ca. 81883 clyde. concordia. ca. 81827 pollen. cs. concordia. ca. 86400 manitou. cs. concordia. ca. 86400 Received 243 bytes from 132. 205. 64. 63#53 in 3 ms October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 7
DNS Tools Example haida. mokhov [~] % host -a www Trying "www. cs. concordia. ca" ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 3704 ; ; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 5, ADDITIONAL: 4 ; ; QUESTION SECTION: ; www. cs. concordia. ca. IN ANY ; ; ANSWER SECTION: www. cs. concordia. ca. 86400 IN CNAME spider. cs. concordia. ca. ; ; AUTHORITY SECTION: cs. concordia. ca. 86400 86400 IN IN IN NS NS NS clyde. concordia. ca. Jerome. Mc. RCIM. Mc. Gill. EDU. pollen. cs. concordia. ca. manitou. cs. concordia. ca. alcor. concordia. ca. IN IN A A 132. 205. 7. 51 132. 205. 1. 1 132. 205. 44. 61 132. 205. 4. 3 ; ; ADDITIONAL SECTION: alcor. concordia. ca. 81883 clyde. concordia. ca. 81827 pollen. cs. concordia. ca. 86400 manitou. cs. concordia. ca. 86400 Received 243 bytes from 132. 205. 64. 63#53 in 3 ms October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 7
 Name Serves • Manage certain part of the name space • Help clients to find info within the hierarchy • DNS Query - returns list of name servers – One of the NS resolves client’s query – If name not found, pass on to another NS – The one that has the answer, sends it back, and the previous NS caches it for the future. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 8
Name Serves • Manage certain part of the name space • Help clients to find info within the hierarchy • DNS Query - returns list of name servers – One of the NS resolves client’s query – If name not found, pass on to another NS – The one that has the answer, sends it back, and the previous NS caches it for the future. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 8
 DNS Threats • Recall from firewalls and the rest (D. Probst): – Filtering DNS: How does one prevent DNS contamination (corruption)? Mail can be rerouted, passwords captured, etc. We need separate DNS for inside and outside. – Tunneling over DNS is used to gain command-line access to remote utilities. With a proxy-based firewall, deny external DNS access to anything other than your proxy server. If you are using a packet filter, your options for blocking a DNS tunnel are limited. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 9
DNS Threats • Recall from firewalls and the rest (D. Probst): – Filtering DNS: How does one prevent DNS contamination (corruption)? Mail can be rerouted, passwords captured, etc. We need separate DNS for inside and outside. – Tunneling over DNS is used to gain command-line access to remote utilities. With a proxy-based firewall, deny external DNS access to anything other than your proxy server. If you are using a packet filter, your options for blocking a DNS tunnel are limited. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 9
 DNS Cache Poisoning • Was more actual in the past: – A NS doesn’t have a name for a requested host – Asks another NS, another NS may have been weak and compromised, or for some other reason had invalid name for the host requested. – Our NS would cache the wrong name, and this can propagate over – So, real amazon. com might have been redirected to elsewhere, get the consequences. . . October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 10
DNS Cache Poisoning • Was more actual in the past: – A NS doesn’t have a name for a requested host – Asks another NS, another NS may have been weak and compromised, or for some other reason had invalid name for the host requested. – Our NS would cache the wrong name, and this can propagate over – So, real amazon. com might have been redirected to elsewhere, get the consequences. . . October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 10
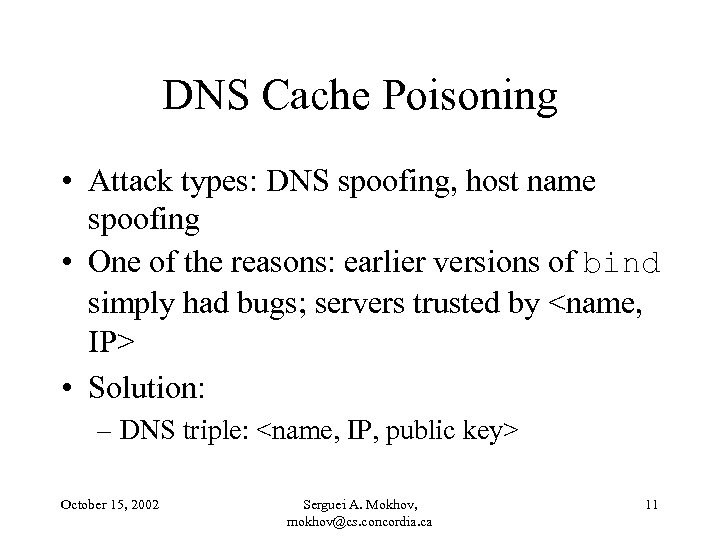 DNS Cache Poisoning • Attack types: DNS spoofing, host name spoofing • One of the reasons: earlier versions of bind simply had bugs; servers trusted by
DNS Cache Poisoning • Attack types: DNS spoofing, host name spoofing • One of the reasons: earlier versions of bind simply had bugs; servers trusted by
 Host Name Spoofing • PTR records • Mapping IP to a domain name • All the transactions a legitimate – DNS server according to the protocol tries to resolve a query using legitimate DNS Server, but the PTR deliberately was made to point elsewhere. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 12
Host Name Spoofing • PTR records • Mapping IP to a domain name • All the transactions a legitimate – DNS server according to the protocol tries to resolve a query using legitimate DNS Server, but the PTR deliberately was made to point elsewhere. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 12
 DNS Spoofing • In combo with hostname spoofing: – Messing up the PTR – And forcing the NS to have invalid resource record (RR) in their cache. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 13
DNS Spoofing • In combo with hostname spoofing: – Messing up the PTR – And forcing the NS to have invalid resource record (RR) in their cache. October 15, 2002 Serguei A. Mokhov, mokhov@cs. concordia. ca 13


