d9ad3912a005c926e512a5417e0a3fd9.ppt
- Количество слайдов: 57
 Internet Security & Worms Prasad S. Athawale Department of Computer Science, University at Buffalo State University of New York, Buffalo
Internet Security & Worms Prasad S. Athawale Department of Computer Science, University at Buffalo State University of New York, Buffalo
 Outline ¡ ¡ ¡ ¡ ¡ Security Overview Intent History Worms Vs Viruses Worm Modelling Simulation techniques Results/Deductions Future of Worms Possible Research Work
Outline ¡ ¡ ¡ ¡ ¡ Security Overview Intent History Worms Vs Viruses Worm Modelling Simulation techniques Results/Deductions Future of Worms Possible Research Work
 Internet Security Covers a broad range of issues – from Data Integrity to Availability ¡ Attack types ¡ l l l Denial of Service Viruses/Worms Snooping/Sniffing etc
Internet Security Covers a broad range of issues – from Data Integrity to Availability ¡ Attack types ¡ l l l Denial of Service Viruses/Worms Snooping/Sniffing etc
 Intent The primary intent of this presentation is to explore the world of Internet Worms, in particular look at current research areas, their propagation mechanisms etc and defense measure if any
Intent The primary intent of this presentation is to explore the world of Internet Worms, in particular look at current research areas, their propagation mechanisms etc and defense measure if any
 History Morris Worm ¡ 2 November 1988 ¡ Exploited flaws in fingerd and sendmail ¡ Password guessing /etc/passwd file ¡ Trusted Hosts ¡ The Internet Worm Incident Technical Report CSD-TR-933* Eugene H. Spafford Department of Computer Sciences Purdue University
History Morris Worm ¡ 2 November 1988 ¡ Exploited flaws in fingerd and sendmail ¡ Password guessing /etc/passwd file ¡ Trusted Hosts ¡ The Internet Worm Incident Technical Report CSD-TR-933* Eugene H. Spafford Department of Computer Sciences Purdue University
 Definition ¡ ¡ Worms: Programs that selfpropagate across the internet by exploiting security flaws in widely used services 1 John Bruner in his novel “The Shockwave Rider” coined the term “worm” How to Own the Internet in your Spare Time Stuart Staniford, Vern Paxson, Nicholas Weaver
Definition ¡ ¡ Worms: Programs that selfpropagate across the internet by exploiting security flaws in widely used services 1 John Bruner in his novel “The Shockwave Rider” coined the term “worm” How to Own the Internet in your Spare Time Stuart Staniford, Vern Paxson, Nicholas Weaver
 Worms Vs Viruses A Virus is a malicious program that spreads using a propagation technique that generally requires user intervention, and always possess a malicious intent ¡ A worm on the other hand, has ability to self-propagate, and may or may not have malicious intent ¡
Worms Vs Viruses A Virus is a malicious program that spreads using a propagation technique that generally requires user intervention, and always possess a malicious intent ¡ A worm on the other hand, has ability to self-propagate, and may or may not have malicious intent ¡
 Requirements!!! Autonomy ¡ Replicability ¡ Reconnaissance Capabilities ¡ Attack Capabilities ¡ Worms as Attack Vectors: Theory, Threats, and Defenses Matthew Todd, Ph. D. January 31, 2003
Requirements!!! Autonomy ¡ Replicability ¡ Reconnaissance Capabilities ¡ Attack Capabilities ¡ Worms as Attack Vectors: Theory, Threats, and Defenses Matthew Todd, Ph. D. January 31, 2003
 Intended Uses/Applications ? Launch a D-Do. S ¡ Access to Sensitive Information ¡ Spread Disinformation ¡ Unknown reasons ¡
Intended Uses/Applications ? Launch a D-Do. S ¡ Access to Sensitive Information ¡ Spread Disinformation ¡ Unknown reasons ¡
 Mechanism? Target Selection ¡ Exploit ¡ Propagation Mechanism ¡ Deployment Tactics ¡ Defensive Measures ? ¡
Mechanism? Target Selection ¡ Exploit ¡ Propagation Mechanism ¡ Deployment Tactics ¡ Defensive Measures ? ¡
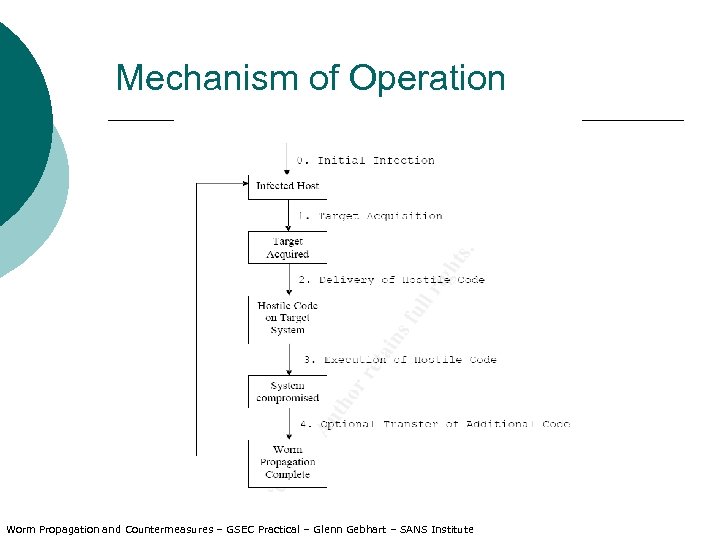 Mechanism of Operation Worm Propagation and Countermeasures – GSEC Practical – Glenn Gebhart – SANS Institute
Mechanism of Operation Worm Propagation and Countermeasures – GSEC Practical – Glenn Gebhart – SANS Institute
 Spread of a Worm Red Dots indicate the infected machines ¡ Bottom left corner number of infected hosts ¡
Spread of a Worm Red Dots indicate the infected machines ¡ Bottom left corner number of infected hosts ¡
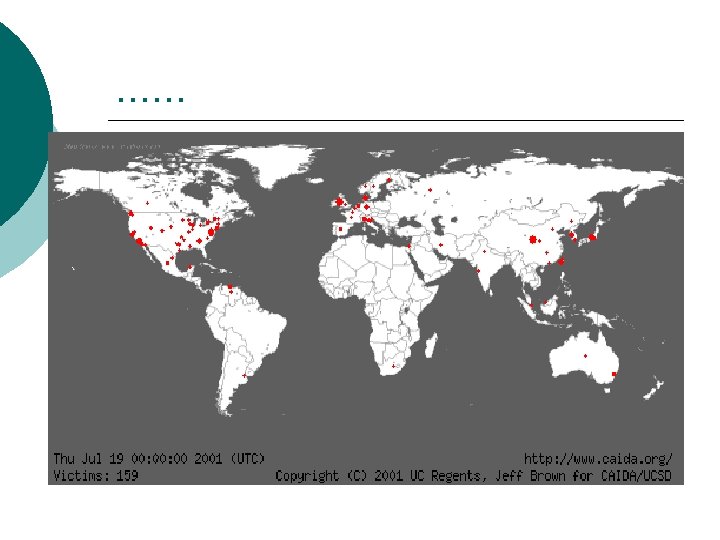 …… ¡ Display Propagation Speed
…… ¡ Display Propagation Speed
 Why Study Worms ? Capable of severely hampering the working of the internet ¡ To unable us to build better defense systems ¡ To unable possible good application ¡ The worst is yet to come! ¡ Applications of a self propagating piece of code – capable of reaching everywhere really fast ?
Why Study Worms ? Capable of severely hampering the working of the internet ¡ To unable us to build better defense systems ¡ To unable possible good application ¡ The worst is yet to come! ¡ Applications of a self propagating piece of code – capable of reaching everywhere really fast ?
 Current research Focus Modelling ¡ Scanning Techniques ¡ Propagation Mechanisms ¡ Prevention Techniques ? ¡
Current research Focus Modelling ¡ Scanning Techniques ¡ Propagation Mechanisms ¡ Prevention Techniques ? ¡
 Modelling ¡ Simple Epidemic Model l l Uses the time tested model of Infectious diseases to model Worm propagation Three possible states – Susceptible, Infected, Quarantined/Removed
Modelling ¡ Simple Epidemic Model l l Uses the time tested model of Infectious diseases to model Worm propagation Three possible states – Susceptible, Infected, Quarantined/Removed
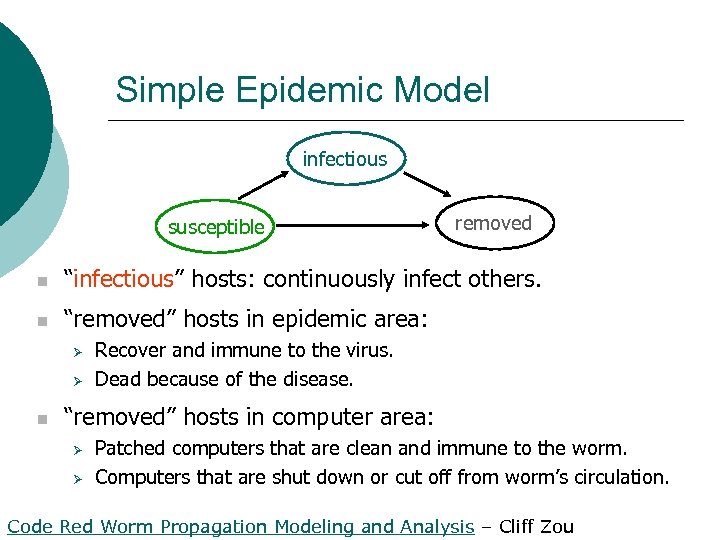 Simple Epidemic Model infectious susceptible removed n “infectious” hosts: continuously infect others. n “removed” hosts in epidemic area: Ø Ø n Recover and immune to the virus. Dead because of the disease. “removed” hosts in computer area: Ø Ø Patched computers that are clean and immune to the worm. Computers that are shut down or cut off from worm’s circulation. Code Red Worm Propagation Modeling and Analysis – Cliff Zou
Simple Epidemic Model infectious susceptible removed n “infectious” hosts: continuously infect others. n “removed” hosts in epidemic area: Ø Ø n Recover and immune to the virus. Dead because of the disease. “removed” hosts in computer area: Ø Ø Patched computers that are clean and immune to the worm. Computers that are shut down or cut off from worm’s circulation. Code Red Worm Propagation Modeling and Analysis – Cliff Zou
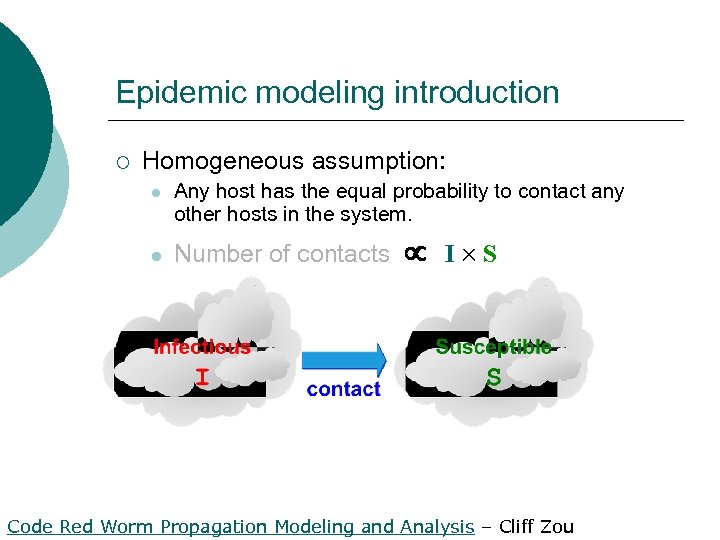 Epidemic modeling introduction ¡ Homogeneous assumption: l l Any host has the equal probability to contact any other hosts in the system. Number of contacts I S Code Red Worm Propagation Modeling and Analysis – Cliff Zou
Epidemic modeling introduction ¡ Homogeneous assumption: l l Any host has the equal probability to contact any other hosts in the system. Number of contacts I S Code Red Worm Propagation Modeling and Analysis – Cliff Zou
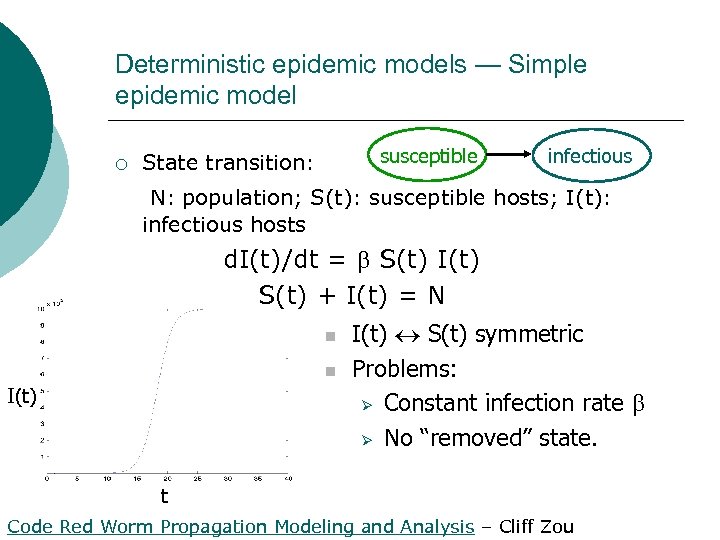 Deterministic epidemic models — Simple epidemic model ¡ susceptible State transition: infectious N: population; S(t): susceptible hosts; I(t): infectious hosts d. I(t)/dt = S(t) I(t) S(t) + I(t) = N n n I(t) S(t) symmetric Problems: Ø Constant infection rate Ø No “removed” state. t Code Red Worm Propagation Modeling and Analysis – Cliff Zou
Deterministic epidemic models — Simple epidemic model ¡ susceptible State transition: infectious N: population; S(t): susceptible hosts; I(t): infectious hosts d. I(t)/dt = S(t) I(t) S(t) + I(t) = N n n I(t) S(t) symmetric Problems: Ø Constant infection rate Ø No “removed” state. t Code Red Worm Propagation Modeling and Analysis – Cliff Zou
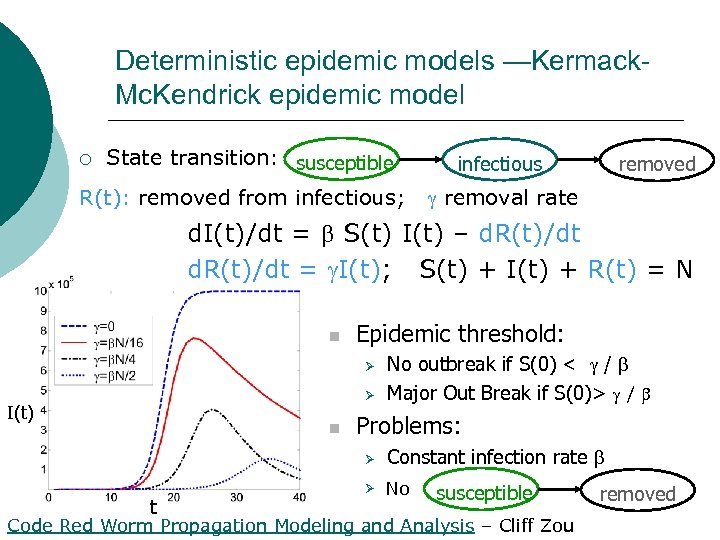 Deterministic epidemic models —Kermack. Mc. Kendrick epidemic model ¡ State transition: susceptible R(t): removed from infectious; removed infectious removal rate d. I(t)/dt = S(t) I(t) – d. R(t)/dt = I(t); S(t) + I(t) + R(t) = N n Epidemic threshold: Ø Ø I(t) n No outbreak if S(0) < / Major Out Break if S(0)> / Problems: Ø t Constant infection rate Ø No susceptible Code Red Worm Propagation Modeling and Analysis – Cliff Zou removed
Deterministic epidemic models —Kermack. Mc. Kendrick epidemic model ¡ State transition: susceptible R(t): removed from infectious; removed infectious removal rate d. I(t)/dt = S(t) I(t) – d. R(t)/dt = I(t); S(t) + I(t) + R(t) = N n Epidemic threshold: Ø Ø I(t) n No outbreak if S(0) < / Major Out Break if S(0)> / Problems: Ø t Constant infection rate Ø No susceptible Code Red Worm Propagation Modeling and Analysis – Cliff Zou removed
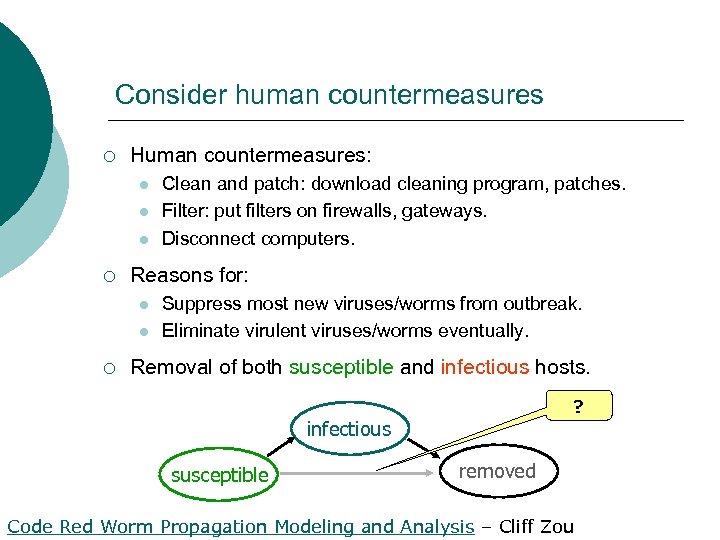 Consider human countermeasures ¡ Human countermeasures: l l l ¡ Reasons for: l l ¡ Clean and patch: download cleaning program, patches. Filter: put filters on firewalls, gateways. Disconnect computers. Suppress most new viruses/worms from outbreak. Eliminate virulent viruses/worms eventually. Removal of both susceptible and infectious hosts. ? infectious susceptible removed Code Red Worm Propagation Modeling and Analysis – Cliff Zou
Consider human countermeasures ¡ Human countermeasures: l l l ¡ Reasons for: l l ¡ Clean and patch: download cleaning program, patches. Filter: put filters on firewalls, gateways. Disconnect computers. Suppress most new viruses/worms from outbreak. Eliminate virulent viruses/worms eventually. Removal of both susceptible and infectious hosts. ? infectious susceptible removed Code Red Worm Propagation Modeling and Analysis – Cliff Zou
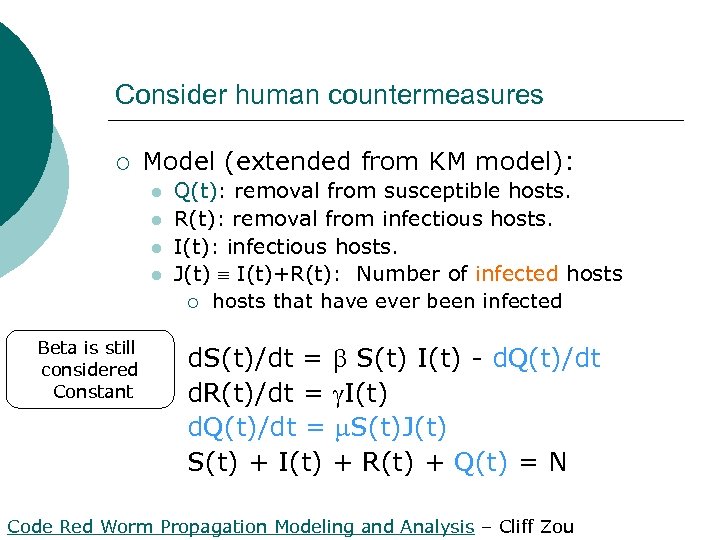 Consider human countermeasures ¡ Model (extended from KM model): l l Beta is still considered Constant Q(t): removal from susceptible hosts. R(t): removal from infectious hosts. I(t): infectious hosts. J(t) I(t)+R(t): Number of infected hosts ¡ hosts that have ever been infected d. S(t)/dt = S(t) I(t) - d. Q(t)/dt d. R(t)/dt = I(t) d. Q(t)/dt = S(t)J(t) S(t) + I(t) + R(t) + Q(t) = N Code Red Worm Propagation Modeling and Analysis – Cliff Zou
Consider human countermeasures ¡ Model (extended from KM model): l l Beta is still considered Constant Q(t): removal from susceptible hosts. R(t): removal from infectious hosts. I(t): infectious hosts. J(t) I(t)+R(t): Number of infected hosts ¡ hosts that have ever been infected d. S(t)/dt = S(t) I(t) - d. Q(t)/dt d. R(t)/dt = I(t) d. Q(t)/dt = S(t)J(t) S(t) + I(t) + R(t) + Q(t) = N Code Red Worm Propagation Modeling and Analysis – Cliff Zou
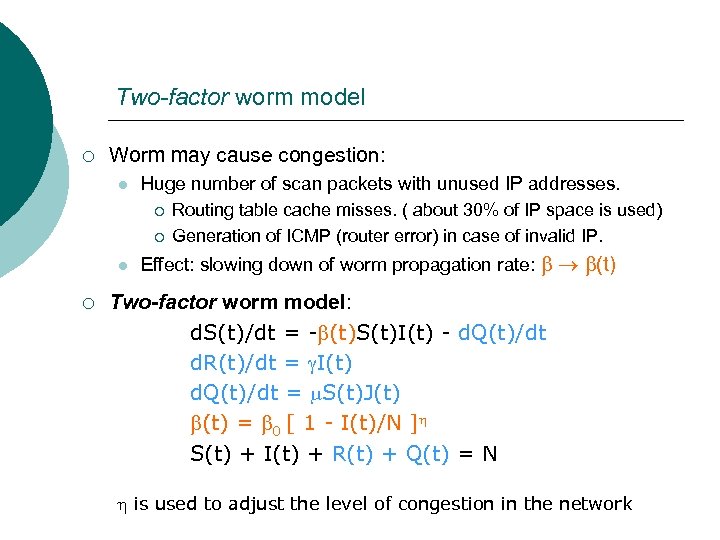 Two-factor worm model ¡ Worm may cause congestion: l Huge number of scan packets with unused IP addresses. ¡ ¡ l ¡ Routing table cache misses. ( about 30% of IP space is used) Generation of ICMP (router error) in case of invalid IP. Effect: slowing down of worm propagation rate: (t) Two-factor worm model: d. S(t)/dt = - (t)S(t)I(t) - d. Q(t)/dt d. R(t)/dt = I(t) d. Q(t)/dt = S(t)J(t) = 0 [ 1 - I(t)/N ] S(t) + I(t) + R(t) + Q(t) = N is used to adjust the level of congestion in the network
Two-factor worm model ¡ Worm may cause congestion: l Huge number of scan packets with unused IP addresses. ¡ ¡ l ¡ Routing table cache misses. ( about 30% of IP space is used) Generation of ICMP (router error) in case of invalid IP. Effect: slowing down of worm propagation rate: (t) Two-factor worm model: d. S(t)/dt = - (t)S(t)I(t) - d. Q(t)/dt d. R(t)/dt = I(t) d. Q(t)/dt = S(t)J(t) = 0 [ 1 - I(t)/N ] S(t) + I(t) + R(t) + Q(t) = N is used to adjust the level of congestion in the network
 Perfect Worm ? ¡ A ‘perfect worm’ would have: All vulnerable hosts known l No dual scanning l Immediate infection l Using Code Red parameters, N=360000, initially infected = 10 and scan rate of 358/min Time Taken = 1. 758 seconds!! l On the Performance of Internet Worm Scanning Strategies Cliff Changchun Zou. , Don Towsley†, Weibo Gong. . Department of Electrical & Computer Engineering †Department of Computer Science Univ. Massachusetts, Amherst
Perfect Worm ? ¡ A ‘perfect worm’ would have: All vulnerable hosts known l No dual scanning l Immediate infection l Using Code Red parameters, N=360000, initially infected = 10 and scan rate of 358/min Time Taken = 1. 758 seconds!! l On the Performance of Internet Worm Scanning Strategies Cliff Changchun Zou. , Don Towsley†, Weibo Gong. . Department of Electrical & Computer Engineering †Department of Computer Science Univ. Massachusetts, Amherst
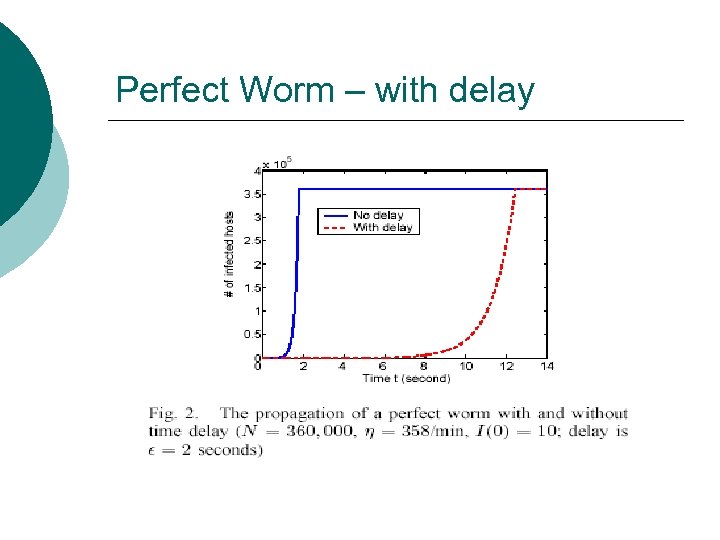 Perfect Worm – with delay
Perfect Worm – with delay
 Scanning Techniques ¡ Hit-List Based Scanning l l l Stealthy Scans – using nmap ? Distributed Scanning – multiple attackers ? DNS Searches Spiders Just Listen!
Scanning Techniques ¡ Hit-List Based Scanning l l l Stealthy Scans – using nmap ? Distributed Scanning – multiple attackers ? DNS Searches Spiders Just Listen!
 Scanning Techniques Sequential Scanning ¡ Hit List Based Scanning ¡ Permutation Scanning ¡ Preferential Subnet Scanning ¡
Scanning Techniques Sequential Scanning ¡ Hit List Based Scanning ¡ Permutation Scanning ¡ Preferential Subnet Scanning ¡
 Co-ordinated Permutation Scanning ¡ ¡ ¡ Assumption – A copy of the worm can detect whether a given host is infected Common permutation of IP address space known to all worms Any machine starts scanning just after it’s point of infection. If an infected host is found, there onwards random point scanning ‘Self –Coordinating', as minimizing duplication of effort Number of such infected hosts – stops scanning assuming infection complete Partitioned Scanning – Initially responsible for some set – divides and hands over to child worm
Co-ordinated Permutation Scanning ¡ ¡ ¡ Assumption – A copy of the worm can detect whether a given host is infected Common permutation of IP address space known to all worms Any machine starts scanning just after it’s point of infection. If an infected host is found, there onwards random point scanning ‘Self –Coordinating', as minimizing duplication of effort Number of such infected hosts – stops scanning assuming infection complete Partitioned Scanning – Initially responsible for some set – divides and hands over to child worm
 Subnet Scanning Cross Network Scanning is too noisy ¡ Can create congestion killing own spread ¡ Use different probabilities to target IP’s in own subnet’s e. g. Code Red own class B 3/8, class A ½, others 1/8 – Code Red, Nimda ¡
Subnet Scanning Cross Network Scanning is too noisy ¡ Can create congestion killing own spread ¡ Use different probabilities to target IP’s in own subnet’s e. g. Code Red own class B 3/8, class A ½, others 1/8 – Code Red, Nimda ¡
 Defense Mechanisms La Brea Tarpit – We can actually do something about it! ¡ Hold Connection Attempts from a Infected Computer ¡ A byte stream flow of only 1215 bytes/hour is sufficient to keep the connection alive ¡
Defense Mechanisms La Brea Tarpit – We can actually do something about it! ¡ Hold Connection Attempts from a Infected Computer ¡ A byte stream flow of only 1215 bytes/hour is sufficient to keep the connection alive ¡
 Defense Mechanisms La. Brea can be defeated using asynchronous mode ¡ Dependent on per host throttling – each host restricts the rate at which a host can connect to new hosts – universal deployment may reduce scanning speed by an order of magnitude ¡
Defense Mechanisms La. Brea can be defeated using asynchronous mode ¡ Dependent on per host throttling – each host restricts the rate at which a host can connect to new hosts – universal deployment may reduce scanning speed by an order of magnitude ¡
 Defense Mechanism Automatically detecting infected hosts and using firewall filters to contain spread ¡ Practical Application Cisco’s NBAR – Network Based Application Recognition ¡ l Ability to block particular TCP streams active on a router based on signature recognition
Defense Mechanism Automatically detecting infected hosts and using firewall filters to contain spread ¡ Practical Application Cisco’s NBAR – Network Based Application Recognition ¡ l Ability to block particular TCP streams active on a router based on signature recognition
 Defense: Internet Quarantine ¡ Prevention l ¡ Treatment l ¡ Generally patches take days to release – only now that relatively reliable distribution networks for patches are springing up Containment l ¡ This aims to reduce the size of the vulnerable population Firewalls, Content Filtering, Automated Routing Blacklists Intervention ?
Defense: Internet Quarantine ¡ Prevention l ¡ Treatment l ¡ Generally patches take days to release – only now that relatively reliable distribution networks for patches are springing up Containment l ¡ This aims to reduce the size of the vulnerable population Firewalls, Content Filtering, Automated Routing Blacklists Intervention ?
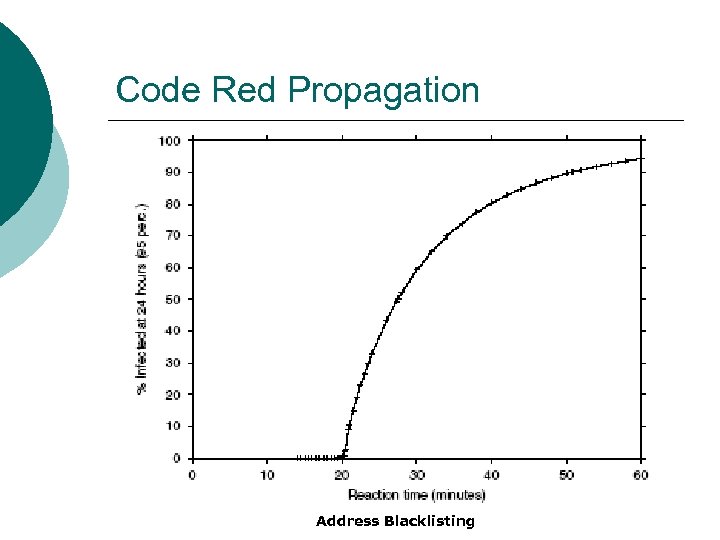 Code Red Propagation Address Blacklisting
Code Red Propagation Address Blacklisting
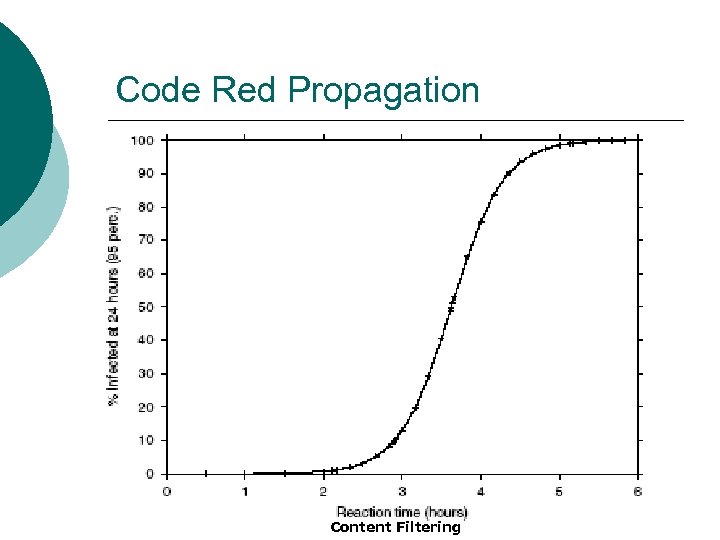 Code Red Propagation Content Filtering
Code Red Propagation Content Filtering
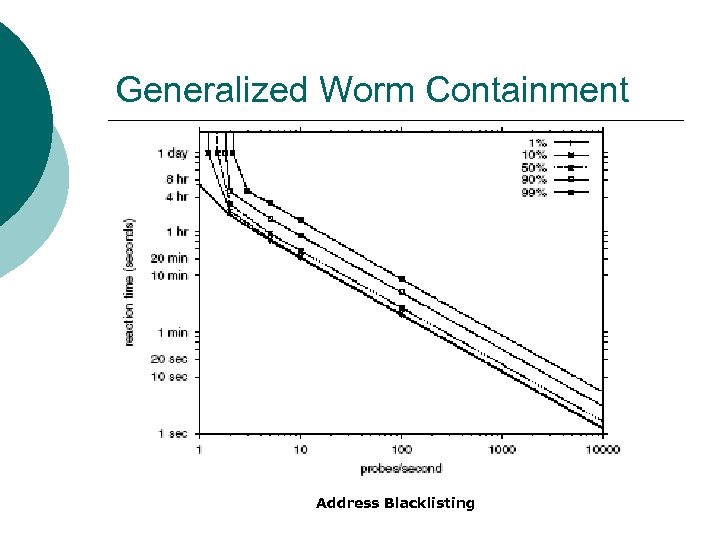 Generalized Worm Containment Address Blacklisting
Generalized Worm Containment Address Blacklisting
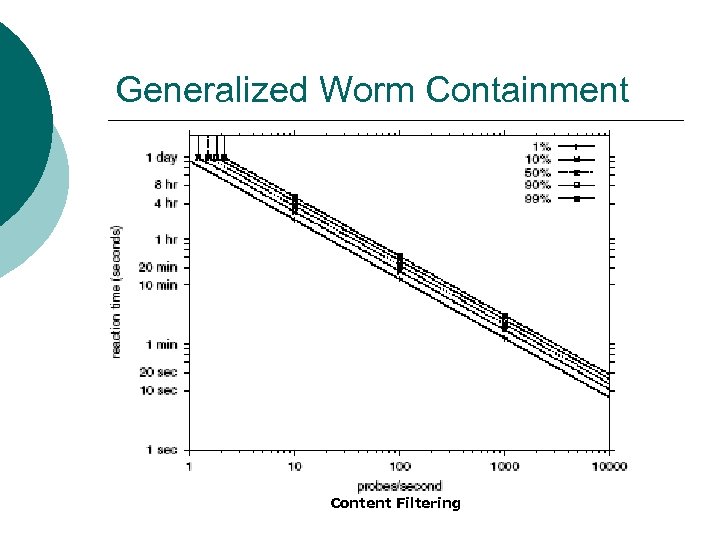 Generalized Worm Containment Content Filtering
Generalized Worm Containment Content Filtering
 Containment Results ¡ ¡ ¡ Not possible to limit infection to less than 18% of the vulnerable hosts for sufficiently aggressive worms (100 scans/second) Used scenarios: ‘Top 100 ISPs’ and 50% home users – for address blacklisting Reason: 99. 7% paths blocked but there still exist alternate paths for propagation – works even when reaction time reduced to 0!
Containment Results ¡ ¡ ¡ Not possible to limit infection to less than 18% of the vulnerable hosts for sufficiently aggressive worms (100 scans/second) Used scenarios: ‘Top 100 ISPs’ and 50% home users – for address blacklisting Reason: 99. 7% paths blocked but there still exist alternate paths for propagation – works even when reaction time reduced to 0!
 Dynamic Quarantine ¡ ¡ Based on Methods used in Epidemic Control – ‘Assume guilty till proven innocent’ Non-Intrusive : Block certain ports for a short time, automatic release Able to reduce/control the propagation speed Assumption : System is assumed homogeneous and contact rate is constant
Dynamic Quarantine ¡ ¡ Based on Methods used in Epidemic Control – ‘Assume guilty till proven innocent’ Non-Intrusive : Block certain ports for a short time, automatic release Able to reduce/control the propagation speed Assumption : System is assumed homogeneous and contact rate is constant
 Defense Mechanisms A lot of researchers have researched this area – Staniford, Kephart and White, Wang ¡ Epidemiological analysis of Computer Viruses – suggested that it can be contained but only till the infection rate doesn’t exceed a critical threshold ¡
Defense Mechanisms A lot of researchers have researched this area – Staniford, Kephart and White, Wang ¡ Epidemiological analysis of Computer Viruses – suggested that it can be contained but only till the infection rate doesn’t exceed a critical threshold ¡
 Containment l l l Automated mechanisms required Content Filtering works the best Blocking Point – At Core ISPs
Containment l l l Automated mechanisms required Content Filtering works the best Blocking Point – At Core ISPs
 Defense: Active Worm Detection Uses ICMP Destination Unreachable Messages ¡ Collection Point for all ICMP-T 3 packets ¡ Correlator – identify threshold crossing occurrences ¡ ICMP T 3 copy generated for collector by router ¡
Defense: Active Worm Detection Uses ICMP Destination Unreachable Messages ¡ Collection Point for all ICMP-T 3 packets ¡ Correlator – identify threshold crossing occurrences ¡ ICMP T 3 copy generated for collector by router ¡
 Defense: Active Worm Detection ¡ Multiple Cases l l l One IP to Many IP’s on port p Many IPs to 1 IP on port p One IP to other IP on number of ports p Many IPs to 1 IP on a number of ports If instances of such activity exceed threshold N, an alert is generated 4 -6 alerts have shown good response
Defense: Active Worm Detection ¡ Multiple Cases l l l One IP to Many IP’s on port p Many IPs to 1 IP on port p One IP to other IP on number of ports p Many IPs to 1 IP on a number of ports If instances of such activity exceed threshold N, an alert is generated 4 -6 alerts have shown good response
 Active Vs Passive – Prevent spreading of Worms by blocking Worm Traffic ¡ Active – Proactive approach by patching vulnerable systems or quickly removing infected systems ¡
Active Vs Passive – Prevent spreading of Worms by blocking Worm Traffic ¡ Active – Proactive approach by patching vulnerable systems or quickly removing infected systems ¡
 Comparison of Active and Passive Mechanisms ¡ ¡ Content Filtering defense mechanism limits infections Address filtering defense requires near perfect deployment Content Filtering mechanism deployed in the top 30 most connected ASes can outperform active defense Active defense worms might have to be pre-deployed in the network to be activated as required
Comparison of Active and Passive Mechanisms ¡ ¡ Content Filtering defense mechanism limits infections Address filtering defense requires near perfect deployment Content Filtering mechanism deployed in the top 30 most connected ASes can outperform active defense Active defense worms might have to be pre-deployed in the network to be activated as required
 Force Multipliers!! Multiple Attack Capabilities ¡ Defense ¡ Command Interface ¡ Polymorphism ¡ Worms as Attack Vectors: Theory, Threats, and Defenses Matthew Todd, Ph. D. January 31, 2003
Force Multipliers!! Multiple Attack Capabilities ¡ Defense ¡ Command Interface ¡ Polymorphism ¡ Worms as Attack Vectors: Theory, Threats, and Defenses Matthew Todd, Ph. D. January 31, 2003
 Upgrade Modular Design ¡ Multiple vulnerabilities pre-identified ¡ Subsequent ‘ 0’ day exploits could be released ¡ Signature Alteration (Polymorphism) ¡
Upgrade Modular Design ¡ Multiple vulnerabilities pre-identified ¡ Subsequent ‘ 0’ day exploits could be released ¡ Signature Alteration (Polymorphism) ¡
 Communication Channels ‘Drop-Box’ Concept ¡ E-Mail ¡ IRC ¡ Specific channels on IRC ¡ Ka. Zaa File shares ¡ Covert Channels ? ¡
Communication Channels ‘Drop-Box’ Concept ¡ E-Mail ¡ IRC ¡ Specific channels on IRC ¡ Ka. Zaa File shares ¡ Covert Channels ? ¡
 Communication Channels Encrypted channels ¡ Public Key, Simple XOR ? ¡ l ¡ Encrypted data might draw attention – simple XOR might help protect entropy Distributed Hash Tables l Principle used by software like Kazaa to determine location of files etc
Communication Channels Encrypted channels ¡ Public Key, Simple XOR ? ¡ l ¡ Encrypted data might draw attention – simple XOR might help protect entropy Distributed Hash Tables l Principle used by software like Kazaa to determine location of files etc
 Curious Yellow Vs Curious Blue Curious Yellow – a high coordination worm – uses techniques for fast propagation, and distributed control ¡ Curious Blue to counter it – with distribution of patches carried out in a similar manner ¡ Since both accept updates – can be easily
Curious Yellow Vs Curious Blue Curious Yellow – a high coordination worm – uses techniques for fast propagation, and distributed control ¡ Curious Blue to counter it – with distribution of patches carried out in a similar manner ¡ Since both accept updates – can be easily
 Proposed ‘Conceptual’ Worms Flash ¡ Warhol ¡ BGP ¡ Curious Yellow ¡
Proposed ‘Conceptual’ Worms Flash ¡ Warhol ¡ BGP ¡ Curious Yellow ¡
 Flash Worms Closest thing to a perfect worm ¡ IP addresses of all vulnerable hosts known beforehand ¡ Scanning space reduced ¡ 99% hosts infected in 2. 53 seconds assuming no delay ¡ Tremendous speed of infection – no time for human intervention
Flash Worms Closest thing to a perfect worm ¡ IP addresses of all vulnerable hosts known beforehand ¡ Scanning space reduced ¡ 99% hosts infected in 2. 53 seconds assuming no delay ¡ Tremendous speed of infection – no time for human intervention
 Warhol Worm Uses combination of Hit-List & Permutation Scanning ¡ This combination improves initial speed – quickly achieving a set base & permutation scanning keeps the worms infection rate high for longer period ¡ Provides a very practical design of a worm – and achieves 99% infection in around 15 mins
Warhol Worm Uses combination of Hit-List & Permutation Scanning ¡ This combination improves initial speed – quickly achieving a set base & permutation scanning keeps the worms infection rate high for longer period ¡ Provides a very practical design of a worm – and achieves 99% infection in around 15 mins
 BGP Routing Worm Based on BGP Routing Tables ¡ Freely Available on the Internet ¡ Geographical Information – ISP, AS, company, country etc. ¡ Reduce the scanning space to 28. 6% of all IP space Routing Worm: A Fast, Selective Attack Worm based on IP Address Information Cliff C. Zou. , Don Towsley†, Weibo Gong. , Songlin Cai. , . Department of Electrical & Computer Engineering †Department of Computer Science, Univ. Massachusetts, Amherst
BGP Routing Worm Based on BGP Routing Tables ¡ Freely Available on the Internet ¡ Geographical Information – ISP, AS, company, country etc. ¡ Reduce the scanning space to 28. 6% of all IP space Routing Worm: A Fast, Selective Attack Worm based on IP Address Information Cliff C. Zou. , Don Towsley†, Weibo Gong. , Songlin Cai. , . Department of Electrical & Computer Engineering †Department of Computer Science, Univ. Massachusetts, Amherst
 Contagion ¡ ¡ ¡ Slowly spreading worm to avoid detection P 2 P based High Bandwidth traffic usual – not detected One client/server program may dominate e. g. Ka. Zaa Not strictly a worm – but can be used to support a worm! Potential ? - A University 9 million distinct IP’s in one month!
Contagion ¡ ¡ ¡ Slowly spreading worm to avoid detection P 2 P based High Bandwidth traffic usual – not detected One client/server program may dominate e. g. Ka. Zaa Not strictly a worm – but can be used to support a worm! Potential ? - A University 9 million distinct IP’s in one month!
 Takeaway ¡ ¡ ¡ Stealth would play a major role in the next generation of Worms Bandwidth, Network Capacity, Widespread use of Computers & a predominantly Ignorant User Community are a given, and these would be exploited to the maximum Proactive defense mechanisms rather than ‘observing’ mechanisms – l ¡ ¡ ¡ Observe ‘periphery’ of ones network ? For Content Based Systems – Ability to identify signatures at an early stage Espionage, Rivalry & Enemity + Non-cooperative Govts/Corporations Design to Security has to be the additional component along with Reliability, Scalability and Availability
Takeaway ¡ ¡ ¡ Stealth would play a major role in the next generation of Worms Bandwidth, Network Capacity, Widespread use of Computers & a predominantly Ignorant User Community are a given, and these would be exploited to the maximum Proactive defense mechanisms rather than ‘observing’ mechanisms – l ¡ ¡ ¡ Observe ‘periphery’ of ones network ? For Content Based Systems – Ability to identify signatures at an early stage Espionage, Rivalry & Enemity + Non-cooperative Govts/Corporations Design to Security has to be the additional component along with Reliability, Scalability and Availability
 References ¡ ¡ ¡ ¡ Worm Propagation Modeling and Analysis under Dynamic Quarantine Defense Cliff Changchun Zou, Weibo Gong, Don Towsley, Univ. Massachusetts Amherst, MA On the Performance of Internet Worm Scanning Strategies Cliff Changchun Zou. , Don Towsley†, Weibo Gong. Univ. Massachusetts, Amherst Modelling the Spread of Active Worm Zesheng Chen (Georgia Tect), Lixin Gai(U Mass), Kevin Kwiat (AFRL) Slowing down Internet Worms Shigang Chen, Yong Tang (UFL, Gainsville) Comparing Active and Passive Worm Defenses Michael Liljenstam David M. Nicol (UIUC, Urbana Champaigne) Internet Qurantine: Requirements for Containing Self- Propagating Code David Moore, Colleen Shannon, Geoffrey M. Voelker, Stefan Savage, UCSD Routing Worm: A Fast, Selective Attack Worm based on IP Address Information Cliff C. Zou. , Don Towsley†, Weibo Gong. , Songlin Cai Univ. Massachusetts, Amherst Worms as Attack Vectors: Theory, Threats, and Defenses A Practical Assignment, submitted in partial requirement for GSEC certification (GIAC Security Essentials Certification Matthew Todd, Ph. D. "I don't think I really love you“ or writing internet worms for fun and profit (C) 1998 -2000 Michal Zalewski The Internet Worm Incident Technical Report CSD-TR-933* Eugene H. Spafford Purdue University How to Own the Internet in your Spare Time Stuart Staniford (Silicon Defense), Vern Paxson (ICSI Center for Internet Research), Nicholas Weaver (UC Berkeley) The Future of Internet Worms Jose Nazario, with Jeremy Anderson, Rick Wash and Chris Connelly Crimelabs research Curious Yellow: The first coordinated Worm Design By Brandon Wiley
References ¡ ¡ ¡ ¡ Worm Propagation Modeling and Analysis under Dynamic Quarantine Defense Cliff Changchun Zou, Weibo Gong, Don Towsley, Univ. Massachusetts Amherst, MA On the Performance of Internet Worm Scanning Strategies Cliff Changchun Zou. , Don Towsley†, Weibo Gong. Univ. Massachusetts, Amherst Modelling the Spread of Active Worm Zesheng Chen (Georgia Tect), Lixin Gai(U Mass), Kevin Kwiat (AFRL) Slowing down Internet Worms Shigang Chen, Yong Tang (UFL, Gainsville) Comparing Active and Passive Worm Defenses Michael Liljenstam David M. Nicol (UIUC, Urbana Champaigne) Internet Qurantine: Requirements for Containing Self- Propagating Code David Moore, Colleen Shannon, Geoffrey M. Voelker, Stefan Savage, UCSD Routing Worm: A Fast, Selective Attack Worm based on IP Address Information Cliff C. Zou. , Don Towsley†, Weibo Gong. , Songlin Cai Univ. Massachusetts, Amherst Worms as Attack Vectors: Theory, Threats, and Defenses A Practical Assignment, submitted in partial requirement for GSEC certification (GIAC Security Essentials Certification Matthew Todd, Ph. D. "I don't think I really love you“ or writing internet worms for fun and profit (C) 1998 -2000 Michal Zalewski The Internet Worm Incident Technical Report CSD-TR-933* Eugene H. Spafford Purdue University How to Own the Internet in your Spare Time Stuart Staniford (Silicon Defense), Vern Paxson (ICSI Center for Internet Research), Nicholas Weaver (UC Berkeley) The Future of Internet Worms Jose Nazario, with Jeremy Anderson, Rick Wash and Chris Connelly Crimelabs research Curious Yellow: The first coordinated Worm Design By Brandon Wiley


