c2b104f37d857e302083be59ee284a05.ppt
- Количество слайдов: 31
 Internet Security Seminar Class CS 591 Presentation Topic: VPN
Internet Security Seminar Class CS 591 Presentation Topic: VPN
 Virtual Privacy Network What is VPN? l Extension of an enterprise’s private intranet across a public network by Encrypt the user’s data l Validate the user’s data l Authenticate the source of the data l Establish & maintain cryptographic secrets l
Virtual Privacy Network What is VPN? l Extension of an enterprise’s private intranet across a public network by Encrypt the user’s data l Validate the user’s data l Authenticate the source of the data l Establish & maintain cryptographic secrets l
 Virtual Private Network Why business use VPN? Cost – ISP/NSP vs leased lines l Simplified Infrastructure – No modem bank l Secured – Encrypted, Authenticated, Integrally Safe l Interoperable – supports multiple protocols l Distributed, Deployable, Scalable l
Virtual Private Network Why business use VPN? Cost – ISP/NSP vs leased lines l Simplified Infrastructure – No modem bank l Secured – Encrypted, Authenticated, Integrally Safe l Interoperable – supports multiple protocols l Distributed, Deployable, Scalable l
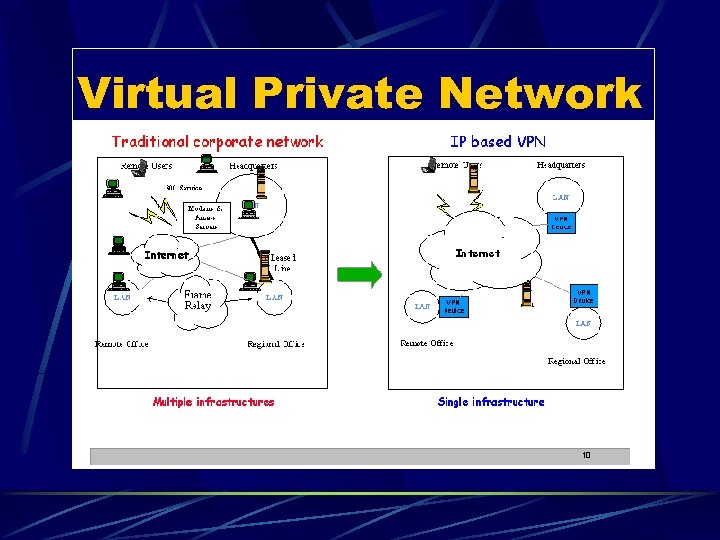 Virtual Private Network
Virtual Private Network
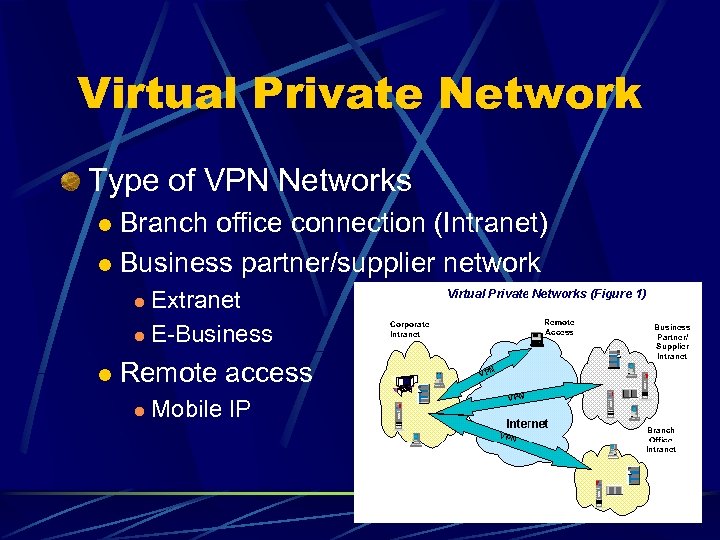 Virtual Private Network Type of VPN Networks Branch office connection (Intranet) l Business partner/supplier network l Extranet l E-Business l l Remote access l Mobile IP
Virtual Private Network Type of VPN Networks Branch office connection (Intranet) l Business partner/supplier network l Extranet l E-Business l l Remote access l Mobile IP
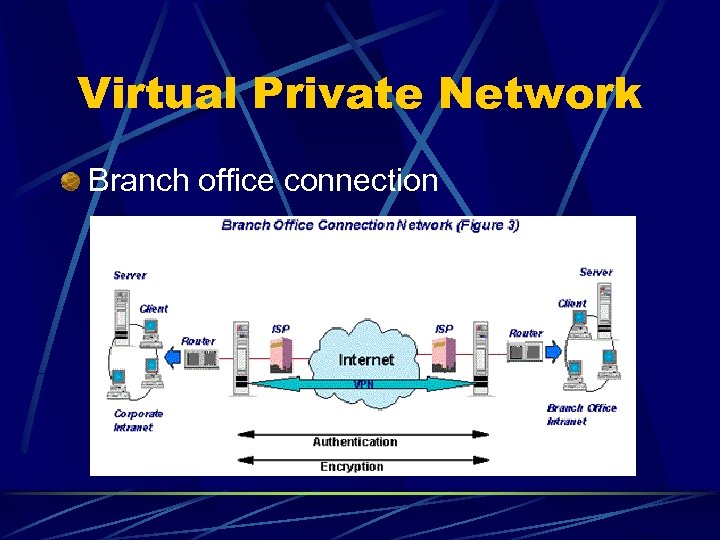 Virtual Private Network Branch office connection
Virtual Private Network Branch office connection
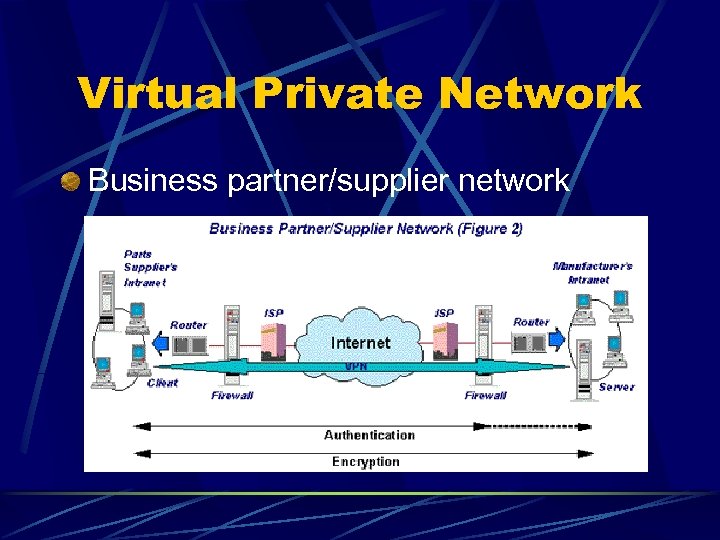 Virtual Private Network Business partner/supplier network
Virtual Private Network Business partner/supplier network
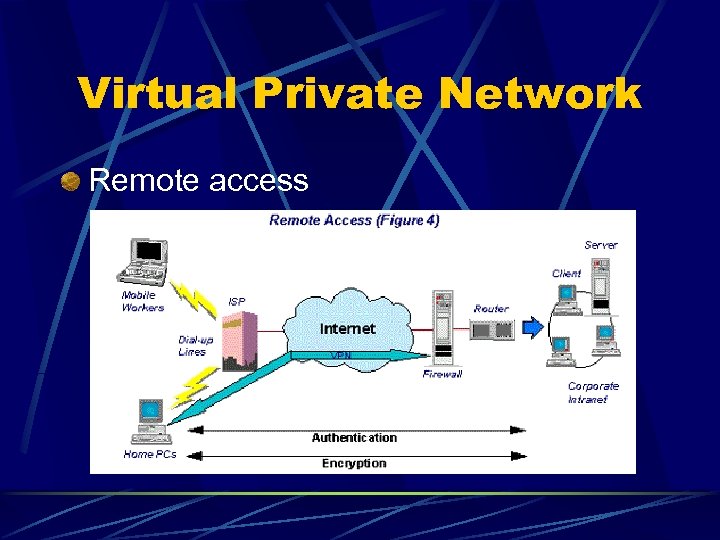 Virtual Private Network Remote access
Virtual Private Network Remote access
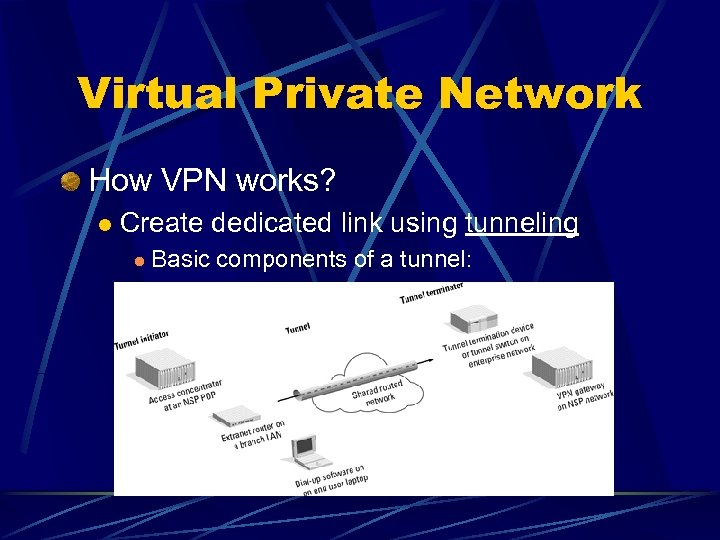 Virtual Private Network How VPN works? l Create dedicated link using tunneling l Basic components of a tunnel: l l A tunnel initiator (TI) A routed network An optional tunnel switch One or more tunnel terminators (TT)
Virtual Private Network How VPN works? l Create dedicated link using tunneling l Basic components of a tunnel: l l A tunnel initiator (TI) A routed network An optional tunnel switch One or more tunnel terminators (TT)
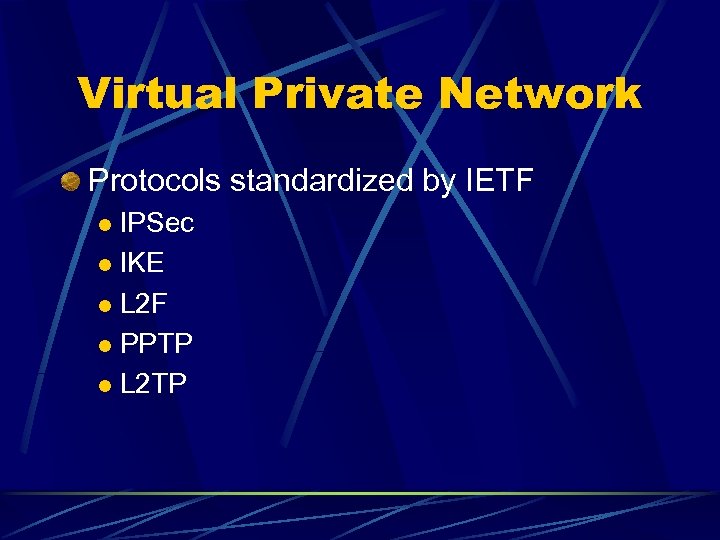 Virtual Private Network Protocols standardized by IETF IPSec l IKE l L 2 F l PPTP l L 2 TP l
Virtual Private Network Protocols standardized by IETF IPSec l IKE l L 2 F l PPTP l L 2 TP l
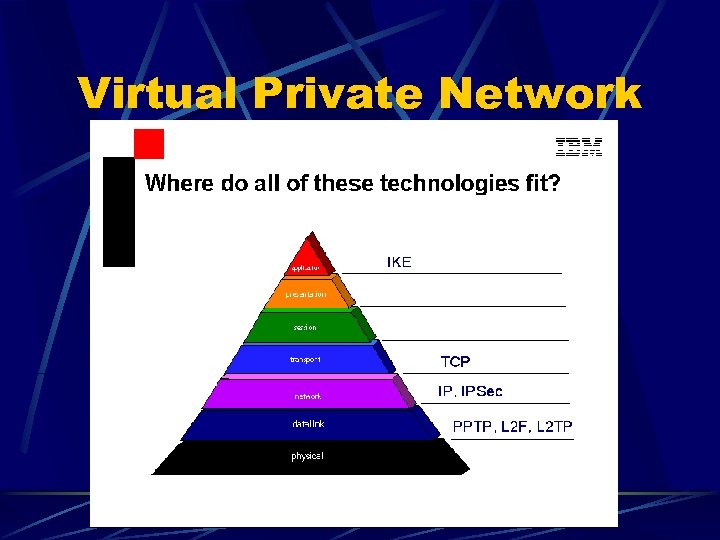 Virtual Private Network
Virtual Private Network
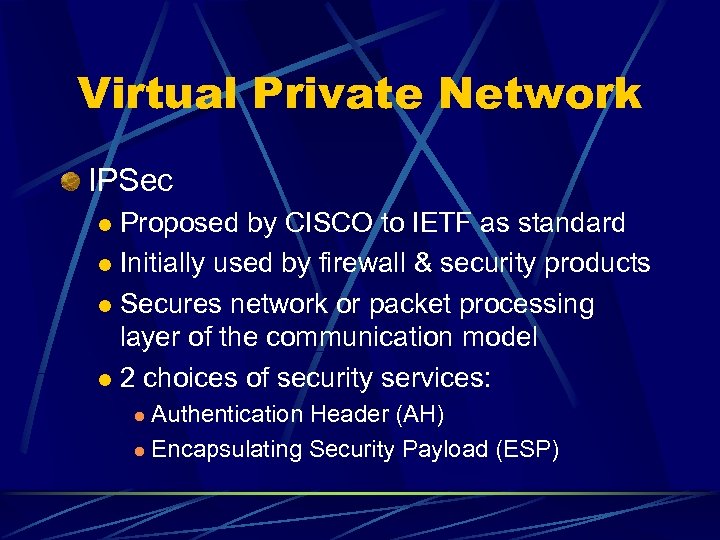 Virtual Private Network IPSec Proposed by CISCO to IETF as standard l Initially used by firewall & security products l Secures network or packet processing layer of the communication model l 2 choices of security services: l Authentication Header (AH) l Encapsulating Security Payload (ESP) l
Virtual Private Network IPSec Proposed by CISCO to IETF as standard l Initially used by firewall & security products l Secures network or packet processing layer of the communication model l 2 choices of security services: l Authentication Header (AH) l Encapsulating Security Payload (ESP) l
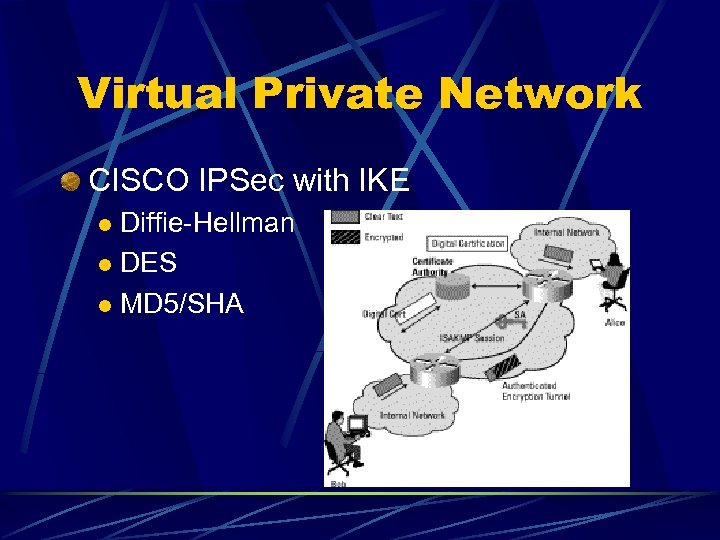 Virtual Private Network CISCO IPSec with IKE Diffie-Hellman l DES l MD 5/SHA l
Virtual Private Network CISCO IPSec with IKE Diffie-Hellman l DES l MD 5/SHA l
 Virtual Private Network IKE l Protocol for Internet Key Exchange l Formerly Internet Security Association & Key Management Protocol (ISAKMP/Oakley) ISAKMP manages negotiation of security l Oakley using Diffie-Hellman establish key l
Virtual Private Network IKE l Protocol for Internet Key Exchange l Formerly Internet Security Association & Key Management Protocol (ISAKMP/Oakley) ISAKMP manages negotiation of security l Oakley using Diffie-Hellman establish key l
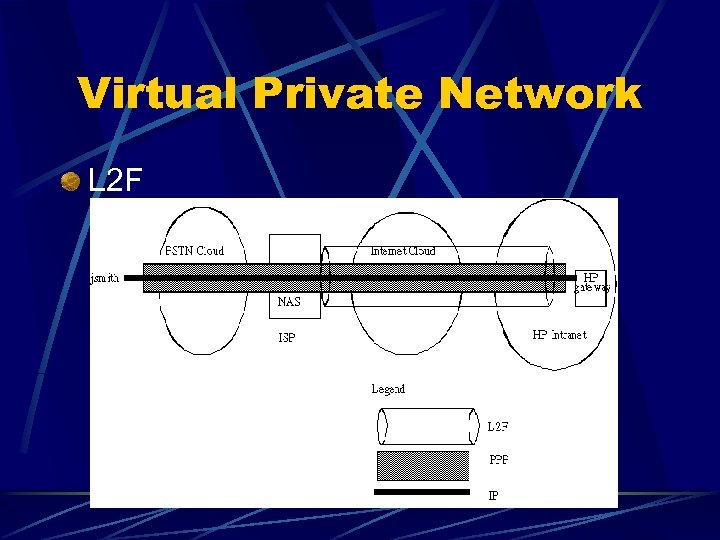 Virtual Private Network L 2 F Tunneling protocol created by CISCO l Mechanism for transporting link-layer frames of higher-layer protocols eg PPP l VPDN l NAS – ISP l Home Gateway - Corporation l
Virtual Private Network L 2 F Tunneling protocol created by CISCO l Mechanism for transporting link-layer frames of higher-layer protocols eg PPP l VPDN l NAS – ISP l Home Gateway - Corporation l
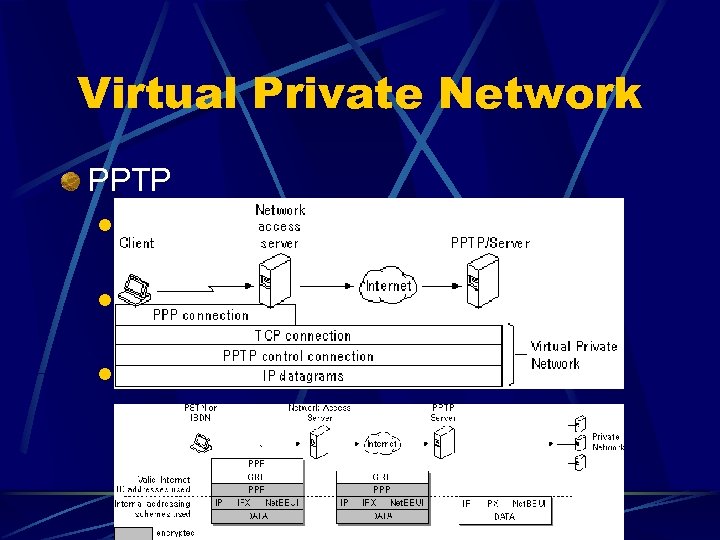 Virtual Private Network PPTP l Point-to-Point Tunneling Protocol l Developed by Microsoft, 3 com, Ascend, ECI Encapsulates PPP packets across IPbased internet l Encryption RSA-RC 4 l
Virtual Private Network PPTP l Point-to-Point Tunneling Protocol l Developed by Microsoft, 3 com, Ascend, ECI Encapsulates PPP packets across IPbased internet l Encryption RSA-RC 4 l
 Virtual Private Network L 2 TP Combination of PPTP and L 2 F l Make multiple simultaneous tunnel btw pt l Allow administrators to dedicate task to specific tunnels l
Virtual Private Network L 2 TP Combination of PPTP and L 2 F l Make multiple simultaneous tunnel btw pt l Allow administrators to dedicate task to specific tunnels l
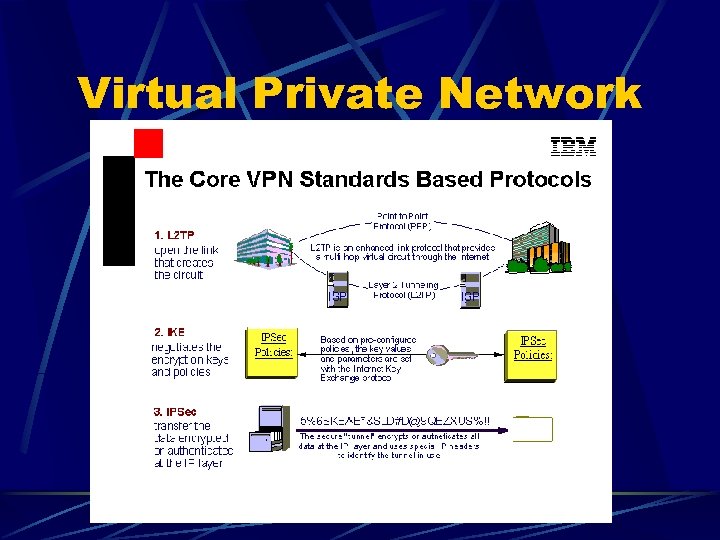 Virtual Private Network
Virtual Private Network
 Virtual Private Network VPN Technology Firewalls l Intrusion Detection Tools l Authentication Servers l Encryption & Key Exchange l
Virtual Private Network VPN Technology Firewalls l Intrusion Detection Tools l Authentication Servers l Encryption & Key Exchange l
 Virtual Private Network l Implementation l Networking Connectivity l l Product or Service Provider l l l Intranet or Extranet or Remote Access VPN Gateway Software only (<1. 5 Mbps connection only) Firewall based Router based Authentication Methods l RADIUS, PKI, X 509 (ITU), LDAP
Virtual Private Network l Implementation l Networking Connectivity l l Product or Service Provider l l l Intranet or Extranet or Remote Access VPN Gateway Software only (<1. 5 Mbps connection only) Firewall based Router based Authentication Methods l RADIUS, PKI, X 509 (ITU), LDAP
 Virtual Private Network Routers and Firewalls with encryption capability. l l l l l Pros: Encryption upgrades, if available, can be cost effective. Cons: Mixing vendor solutions can create compatibility issues that inhibit VPN capability. May not be able to provide PC-to-LAN capability without additional software support. Could require commitment to vendor's proprietary technology. May not provide multi-protocol support. Installation and configuration can add to network complexity. Encryption processing overhead may reduce performance.
Virtual Private Network Routers and Firewalls with encryption capability. l l l l l Pros: Encryption upgrades, if available, can be cost effective. Cons: Mixing vendor solutions can create compatibility issues that inhibit VPN capability. May not be able to provide PC-to-LAN capability without additional software support. Could require commitment to vendor's proprietary technology. May not provide multi-protocol support. Installation and configuration can add to network complexity. Encryption processing overhead may reduce performance.
 Virtual Private Network Traditional Remote Access Server (RAS) with VPN add-on. l l l l Pros: May allow IT to take advantage of an existing hardware investment. Cons: Traditional Remote Access Servers are not optimized for VPN add-ons may only be available for some high-end RAS solutions. May be ISP dependent, requiring the company to adopt the same RAS VPN vendor as the ISP. May not provide multi-protocol support. May require vendor proprietary software.
Virtual Private Network Traditional Remote Access Server (RAS) with VPN add-on. l l l l Pros: May allow IT to take advantage of an existing hardware investment. Cons: Traditional Remote Access Servers are not optimized for VPN add-ons may only be available for some high-end RAS solutions. May be ISP dependent, requiring the company to adopt the same RAS VPN vendor as the ISP. May not provide multi-protocol support. May require vendor proprietary software.
 Virtual Private Network NOS/Server-Based VPN l l l Pros: More robust solution for PC-to-LAN access than that provided by firewalls or routers. Cons: Difficult to set up and manage VPN functionality. Adding VPN services to a network server can impact performance while decreasing fault tolerance. Dedicating a network server to remote access can be prohibitively expensive.
Virtual Private Network NOS/Server-Based VPN l l l Pros: More robust solution for PC-to-LAN access than that provided by firewalls or routers. Cons: Difficult to set up and manage VPN functionality. Adding VPN services to a network server can impact performance while decreasing fault tolerance. Dedicating a network server to remote access can be prohibitively expensive.
 Virtual Private Network VPN Services l l l l Pros: Security and performance can be guaranteed for a price. Requires limited corporate support. Cons: IT gives up control to the service provider. May not provide multi-protocol support. May not provide PC-to-LAN access. VPN services may be cost prohibitive.
Virtual Private Network VPN Services l l l l Pros: Security and performance can be guaranteed for a price. Requires limited corporate support. Cons: IT gives up control to the service provider. May not provide multi-protocol support. May not provide PC-to-LAN access. VPN services may be cost prohibitive.
 Virtual Private Network Dedicated VPN Software l l l Pros: Optimized to create LAN-to-LAN connections via VPN. Dedicated VPN solution creates fault tolerance. Standalone VPN solutions can offer greater performance. Dedicated VPN solutions are generally easier to use and support than solutions originally designed for non-VPN functions such as firewalls, routers, network servers and traditional remote access servers. Eliminates the need for costly frame relay circuits, leased lines, etc. Cons: Vendor proprietary software is needed for each server hosting VPN and each remote client accessing the LAN via VPN. Must invest in a dedicated server for maximum performance. Adding VPN software on an existing, in-use network server decreases fault tolerance and performance. Many solutions support IP-only VPNs and cannot transport packets from multiple protocols.
Virtual Private Network Dedicated VPN Software l l l Pros: Optimized to create LAN-to-LAN connections via VPN. Dedicated VPN solution creates fault tolerance. Standalone VPN solutions can offer greater performance. Dedicated VPN solutions are generally easier to use and support than solutions originally designed for non-VPN functions such as firewalls, routers, network servers and traditional remote access servers. Eliminates the need for costly frame relay circuits, leased lines, etc. Cons: Vendor proprietary software is needed for each server hosting VPN and each remote client accessing the LAN via VPN. Must invest in a dedicated server for maximum performance. Adding VPN software on an existing, in-use network server decreases fault tolerance and performance. Many solutions support IP-only VPNs and cannot transport packets from multiple protocols.
 Virtual Private Network Dedicated VPN Hardware l l l l l Pros: Easy to install, configure and manage. Saves money by reducing equipment needs at corporate site. Stand-alone solution offers greater performance and fault tolerance because it is optimized for VPN functionality. Reduces costs of upgrading hardware as remote access technology changes. Reduces costs of upgrading system as the number of users increases. Cons: Some solutions do not support multiple protocols. Some LAN-to-LAN VPN solutions require costly software add-ons to support remote client PCs. Some solutions require that proprietary software be loaded on the remote client's PC.
Virtual Private Network Dedicated VPN Hardware l l l l l Pros: Easy to install, configure and manage. Saves money by reducing equipment needs at corporate site. Stand-alone solution offers greater performance and fault tolerance because it is optimized for VPN functionality. Reduces costs of upgrading hardware as remote access technology changes. Reduces costs of upgrading system as the number of users increases. Cons: Some solutions do not support multiple protocols. Some LAN-to-LAN VPN solutions require costly software add-ons to support remote client PCs. Some solutions require that proprietary software be loaded on the remote client's PC.
 Virtual Private Network l SECURITY STANCE Permit all access initially; administrator specifically denies individual access according to security policy. l Deny all access initially; administrator specifically permits individual access according to security policy. l
Virtual Private Network l SECURITY STANCE Permit all access initially; administrator specifically denies individual access according to security policy. l Deny all access initially; administrator specifically permits individual access according to security policy. l
 Virtual Private Network l Security Techniques Packet Filters l Circuit-level Gateways l Application-level Gateways l l Possible Security Breach/Risk from RA Unauthorized Remote Access (RA) Computer l RA computer connected to insecure network l Virus infected RA computer l
Virtual Private Network l Security Techniques Packet Filters l Circuit-level Gateways l Application-level Gateways l l Possible Security Breach/Risk from RA Unauthorized Remote Access (RA) Computer l RA computer connected to insecure network l Virus infected RA computer l
 Virtual Private Network l Company supporting VPN Microsoft l IBM l Novell l CISCO l Nokia l 3 com l
Virtual Private Network l Company supporting VPN Microsoft l IBM l Novell l CISCO l Nokia l 3 com l
 Virtual Private Network l FAQ l l l l Difference between VPN and Firewall? Diifference between VPN and Proxy? Build own VPN or outsource to SP? Important critique? Interoperable? Scalability? Can U trust the internet? Any other Questions? Virtual Private Networks By Charlie Scott, Paul Wolfe and Mike Erwin, O'Reilly & Associates, March 1998
Virtual Private Network l FAQ l l l l Difference between VPN and Firewall? Diifference between VPN and Proxy? Build own VPN or outsource to SP? Important critique? Interoperable? Scalability? Can U trust the internet? Any other Questions? Virtual Private Networks By Charlie Scott, Paul Wolfe and Mike Erwin, O'Reilly & Associates, March 1998
 Virtual Private Network
Virtual Private Network


