e71188fd33eb7948e7ce7ba2d1bf2677.ppt
- Количество слайдов: 66

Internet dan Jaringan Komputer Electronic Commerce and Mobile Commerce Dr. Tb. Maulana Kusuma mkusuma@staff. gunadarma. ac. id http: //staffsite. gunadarma. ac. id/mkusuma Magister Manajemen Sistem Informasi 0
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma Definition of E-Commerce “A modern business methodology that addresses the needs of organizations, merchants, and consumers to cut costs while improving the quality of goods and services and increasing the speed of service delivery”
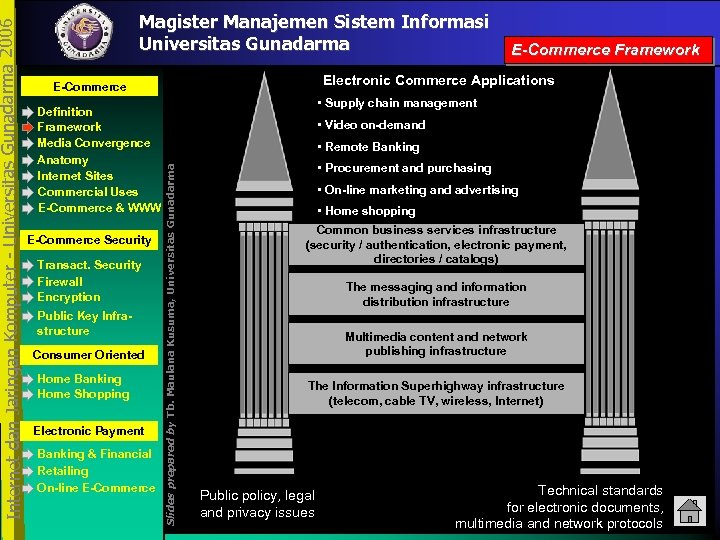
Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Framework Electronic Commerce Applications E-Commerce • Supply chain management • Video on-demand • Remote Banking Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma • Procurement and purchasing • On-line marketing and advertising • Home shopping Common business services infrastructure (security / authentication, electronic payment, directories / catalogs) The messaging and information distribution infrastructure Multimedia content and network publishing infrastructure The Information Superhighway infrastructure (telecom, cable TV, wireless, Internet) Public policy, legal and privacy issues Technical standards for electronic documents, multimedia and network protocols
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma E-Commerce & Media Convergence “Convergence, broadly defined, is the melding of consumer electronics, television, publishing, telecommunications, and computers for the purpose of facilitating new forms of informationbased commerce” · Convergence of content Translates all types of information content -- books, business documents, videos, movies, music -- into digital information. · Convergence of transmission Compresses and stores digitized information so it can travel through existing phone and cable wiring. · Convergence of information access device To function as both computers and televisions.
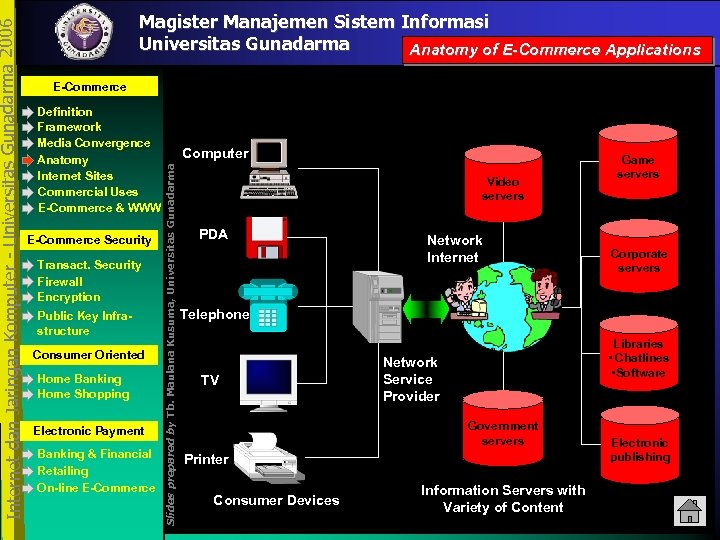
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Computer Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma Anatomy of E-Commerce Applications Video servers PDA Network Internet Game servers Corporate servers Telephone TV Libraries • Chatlines • Software Network Service Provider Government servers Printer Consumer Devices Information Servers with Variety of Content Electronic publishing
Types of Internet Sites E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce There are broadly speaking two main types of commercial Internet sites available to companies at present: Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma · Static Sites It can be used for displaying large amounts of information provided the information does not require regular updating and a high degree of functionality is not required. · Databased Sites Sometimes referred to as Database Front-end Systems or dynamically generated Internet sites. It can be designed to interact with existing systems such as order processing, stock control systems and sources of information such as product databases.
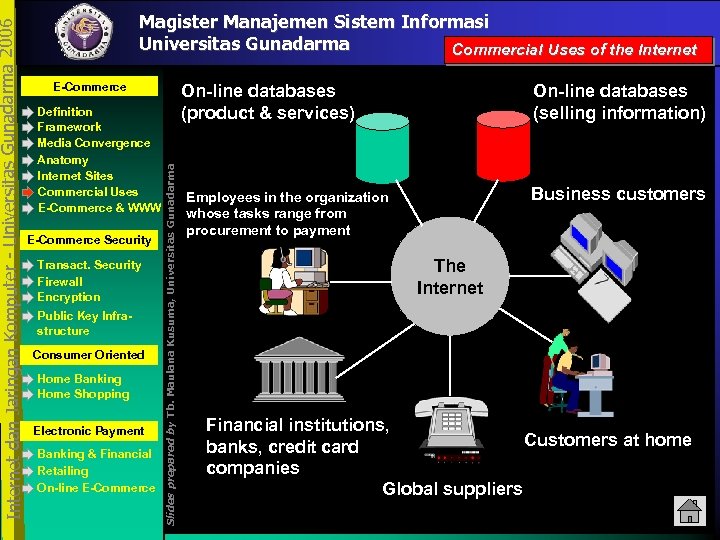
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce On-line databases (product & services) Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma Commercial Uses of the Internet On-line databases (selling information) Business customers Employees in the organization whose tasks range from procurement to payment The Internet Financial institutions, Customers at home banks, credit card companies Global suppliers
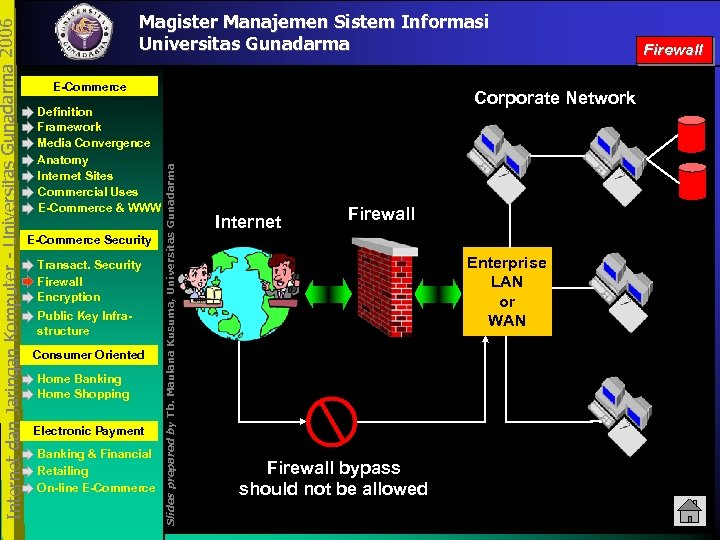
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Corporate Network Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma Internet Firewall Enterprise LAN or WAN Firewall bypass should not be allowed Firewall
Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Encryption is the mutation of information in any form (text, video, graphics) into a representation unreadable by anyone without a decryption key. E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma · Secret Key Cryptography Involved the use of a shared key for both encryption by the transmitter and decryption by the receiver. This technique suffer from the problem of key distribution, since shared keys must be securely distributed to each pair of communicating parties. · Public Key Cryptography Public-key techniques involve a pair of keys; a private key and a public key associated with each user. Information encrypted by the private key can be decrypted only using the corresponding public key. The private key, used to encrypt transmitted information by the user, is kept secret. The public key is used to decrypt information at the receiver and is not kept secret.
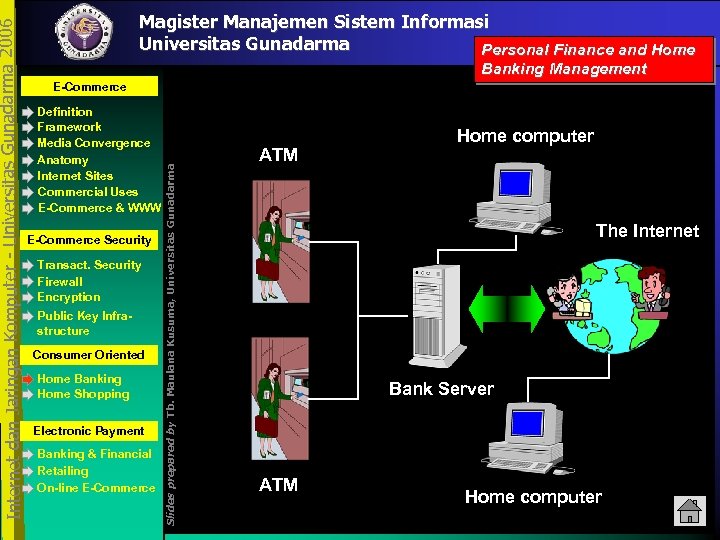
Banking Management E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma Personal Finance and Home ATM Home computer The Internet Bank Server ATM Home computer
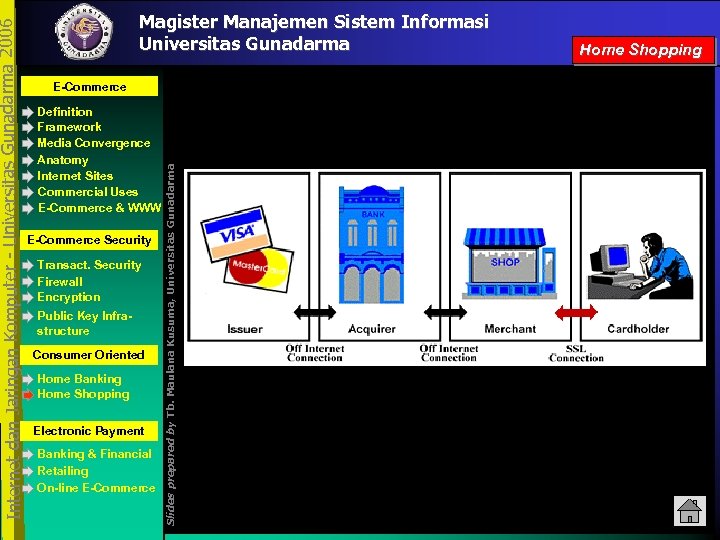
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma Home Shopping
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma Banking & Financial Payments · Large-scale or wholesale payments e. g. , bank-to-bank transfer · Small-scale or retail payments e. g. , automated teler machines and cash dispenser · Home Banking e. g. , bill payment
Retailing Payments E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma · Credit cards e. g. , VISA or Master. Card · Private label credit / debit cards e. g. , J. C. Penney Card, BCA Debit · Charge cards e. g. , American Express
E-Commerce Definition Framework Media Convergence Anatomy Internet Sites Commercial Uses E-Commerce & WWW E-Commerce Security Transact. Security Firewall Encryption Public Key Infrastructure Consumer Oriented Home Banking Home Shopping Electronic Payment Banking & Financial Retailing On-line E-Commerce Slides prepared by Tb. Maulana Kusuma, Universitas Gunadarma Internet dan Jaringan Komputer - Universitas Gunadarma 2006 Magister Manajemen Sistem Informasi Universitas Gunadarma On-line E-Commerce Payment Systems · Token-based payment systems · Electronic cash (e. g. , Digi. Cash) · Electronic checks (e. g. , Net. Cheque) · Smart cards or debit cards (e. g. , Mondex) · Credit card-based payment systems · Encrypted Credit cards (e. g. , WWW formbased encryption) · Third-party authorization numbers (e. g. , First Virtual)

Outline m-Commerce Overview Infrastructure m-Commerce Applications Mobile Payment Limitations Security in m-Commerce Magister Manajemen Sistem Informasi 14

Mobile Commerce: Overview Mobile commerce (m-Commerce, m-Business)—any e-Commerce done in a wireless environment, especially via the Internet n n Can be done via the Internet, private communication lines, smart cards, etc. Creates opportunity to deliver new services to existing customers and to attract new ones Magister Manajemen Sistem Informasi 15

Mobile commerce from the Customer‘s point of view The customer wants to access information, goods and services any time and in any place on his mobile device. He can use his mobile device to purchase tickets for events or public transport, pay for parking, download content and even order books and CDs. He should be offered appropriate payment methods. They can range from secure mobile micropayment to service subscriptions. Magister Manajemen Sistem Informasi 16

Mobile commerce from the Provider‘s point of view The future development of the mobile telecommunication sector is heading more and more towards value-added services. Analysts forecast that soon half of mobile operators‘ revenue will be earned through mobile commerce. Consequently operators as well as third party providers will focus on value-added-services. To enable mobile services, providers with expertise on different sectors will have to cooperate. Innovative service scenarios will be needed that meet the customer‘s expectations and business models that satisfy all partners involved. Magister Manajemen Sistem Informasi 17

m-Commerce Terminology Generations n 1 G: 1979 -1992 wireless technology n 2 G: current wireless technology; mainly accommodates text n 2. 5 G: interim technology accommodates graphics rd generation technology (2001 -2005) n 3 G: 3 supports rich media (video clips) n 4 G: will provide faster multimedia display (20062010) Magister Manajemen Sistem Informasi 18

Terminology and Standards GPS: Satellite-based Global Positioning System PDA: Personal Digital Assistant—handheld wireless computer SMS: Short Message Service EMS: Enhanced Messaging Service MMS: Multimedia Messaging Service WAP: Wireless Application Protocol Smart-phones—Internet-enabled cell phones with attached applications Magister Manajemen Sistem Informasi 19

Attributes of m-Commerce and Its Economic Advantages n n n n Mobility—users carry cell phones or other mobile devices Broad reach—people can be reached at any time Ubiquity—easier information access in real-time Convenience—devices that store data and have Internet, intranet, extranet connections Instant connectivity—easy and quick connection to Internet, intranets, other mobile devices, databases Personalization—preparation of information for individual consumers Localization of products and services—knowing where the user is located at any given time and match service to them Magister Manajemen Sistem Informasi 20

Outline m-Commerce Infrastructure m-Commerce Applications Mobile Payment Limitations Security in m-Commerce Magister Manajemen Sistem Informasi 21
Mobile Computing Infrastructure Hardware Cellular (mobile) phones Attachable keyboard PDAs Interactive pagers Other devices n Notebooks n Handhelds n Smartpads Screenphones—a telephone equipped with color screen, keyboard, email, and Internet capabilities E-mail handhelds Wirelined—connected by wires to a network Magister Manajemen Sistem Informasi 22
Mobile Computing Infrastructure (cont. ) Unseen infrastructure requirements n n n Suitably configured wireline or wireless WAN modem Web server with wireless support Application or database server Large enterprise application server GPS locator used to determine the location of mobile computing device carrier Magister Manajemen Sistem Informasi 23
Mobile Computing Infrastructure (cont. ) Software n n n n Micro browser Mobile client operating system (OS) Bluetooth—a chip technology and WPAN standard that enables voice and data communications between wireless devices over short-range radio frequency (RF) Mobile application user interface Back-end legacy application software Application middleware Wireless middleware Magister Manajemen Sistem Informasi 24
Mobile Computing Infrastructure (cont. ) Networks and access n Wireless transmission media Microwave Satellites Radio Infrared Cellular radio technology n Wireless systems Magister Manajemen Sistem Informasi 25

Outline m-Commerce Overview Infrastructure m-Commerce Applications Mobile Payment Limitations Security in m-Commerce Magister Manajemen Sistem Informasi 26

Mobile Service Scenarios Financial Services. Entertainment. Shopping. Information Services. Payment. Advertising. And more. . . Magister Manajemen Sistem Informasi 27
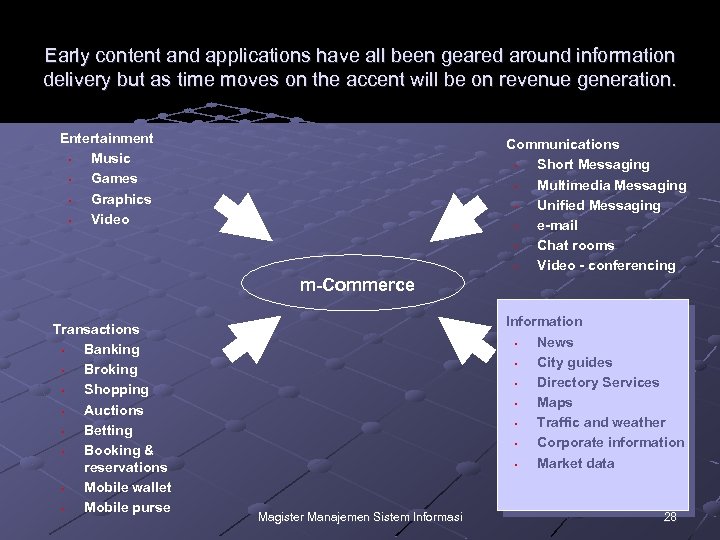
Early content and applications have all been geared around information delivery but as time moves on the accent will be on revenue generation. Entertainment • Music • Games • Graphics • Video Communications • Short Messaging • Multimedia Messaging • Unified Messaging • e-mail • Chat rooms • Video - conferencing m-Commerce Transactions • Banking • Broking • Shopping • Auctions • Betting • Booking & reservations • Mobile wallet • Mobile purse Information • News • City guides • Directory Services • Maps • Traffic and weather • Corporate information • Market data Magister Manajemen Sistem Informasi 28

Classes of M-Commerce Applications Magister Manajemen Sistem Informasi 29

Mobile Application: Financial Tool As mobile devices become more secure Mobile banking Bill payment services m-Brokerage services Mobile money transfers Mobile micro payments Replace ATM’s and credit cards? ? Magister Manajemen Sistem Informasi 30
Financial Tool: Wireless Electronic Payment Systems “transform mobile phones into secure, self-contained purchasing tools capable of instantly authorizing payments…” Types: n n n Micro payments Wireless wallets (m-Wallet) Bill payments Magister Manajemen Sistem Informasi 31
Examples Swedish Postal Bank n Check Balances/Make Payments & Conduct some transactions Dagens Industri n Receive Financial Data and Trade on Stockholm Exchange Citibank n Access balances, pay bills & transfer funds using SMS Magister Manajemen Sistem Informasi 32

Mobile Applications : Marketing, Advertising, And Customer Service Shopping from Wireless Devices n Have access to services similar to those of wireline shoppers Shopping carts Price comparisons Order status n Future Will be able to view and purchase products using handheld mobile devices Magister Manajemen Sistem Informasi 33

Mobile Applications : Marketing, Advertising, And Customer Service Targeted Advertising n n Using demographic information can personalize wireless services (barnesandnoble. com) Knowing users’ preferences and surfing habits marketers can send: User-specific advertising messages Location-specific advertising messages Magister Manajemen Sistem Informasi 34

Mobile Applications : Marketing, Advertising, And Customer Service CRM applications n n n Mobile. CRM Comparison shopping using Internet capable phones Voice Portals Enhanced customer service improved access to data for employees Magister Manajemen Sistem Informasi 35
Mobile Portals “A customer interaction channel that aggregates content and services for mobile users. ” n Charge per time for service or subscription based Example: I-Mode in Japan n Mobile corporate portal Serves corporations customers and suppliers Magister Manajemen Sistem Informasi 36

Mobile Intrabusiness and Enterprise Applications Support of Mobile Employees by 2005 25% of all workers could be mobile employees n sales people in the field, traveling executives, telecommuters, consultants working on-site, repair or installation employees need same corporate data as those working inside company’s offices n solution: wireless devices wearable devices: cameras, screen, keyboard, touch-panel display Magister Manajemen Sistem Informasi 37

Mobile B 2 B and Supply Chain Applications “mobile computing solutions enable organizations to respond faster to supply chain disruptions by proactively adjusting plans or shifting resources related to critical supply chain events as they occur. ” n accurate and timely information n opportunity to collaborate along supply chain n must integrate mobile devices into information exchanges n example: “telemetry” integration of wireless communications, vehicle monitoring systems, and vehicle location devices leads to reduced overhead and faster service responsiveness (vending machines) Magister Manajemen Sistem Informasi 38

Applications of Mobile Devices for Consumers/Industries Personal Service Applications n example airport Mobile Gaming and Gambling Mobile Entertainment n music and video Hotels Intelligent Homes and Appliances Wireless Telemedicine Other Services for Consumers Magister Manajemen Sistem Informasi 39

Outline m-Commerce Overview Infrastructure m-Commerce Applications Mobile Payment Limitations Security in m-Commerce Magister Manajemen Sistem Informasi 40

Mobile Payment for m-Commerce Mobile Payment can be offered as a stand-alone service. Mobile Payment could also be an important enabling service for other m-commerce services (e. g. mobile ticketing, shopping, gambling…) : n n It could improve user acceptance by making the services more secure and user-friendly. In many cases offering mobile payment methods is the only chance the service providers have to gain revenue from an m-Commerce service. Magister Manajemen Sistem Informasi 41

Mobile Payment (cont. ) the consumer must be informed of: n n n what is being bought, and how much to pay options to pay; the payment must be made payments must be traceable. Magister Manajemen Sistem Informasi 42

Mobile Payment (cont. ) Customer requirements: · · a larger selection of merchants with whom they can trade a more consistent payment interface when making the purchase with multiple payment schemes, like: • Credit Card payment • Bank Account/Debit Card Payment Merchant benefits: • • brands to offer a wider variety of payment Easy-to-use payment interface development Bank and financial institution benefits • to offer a consistent payment interface to consumer and merchants Magister Manajemen Sistem Informasi 43
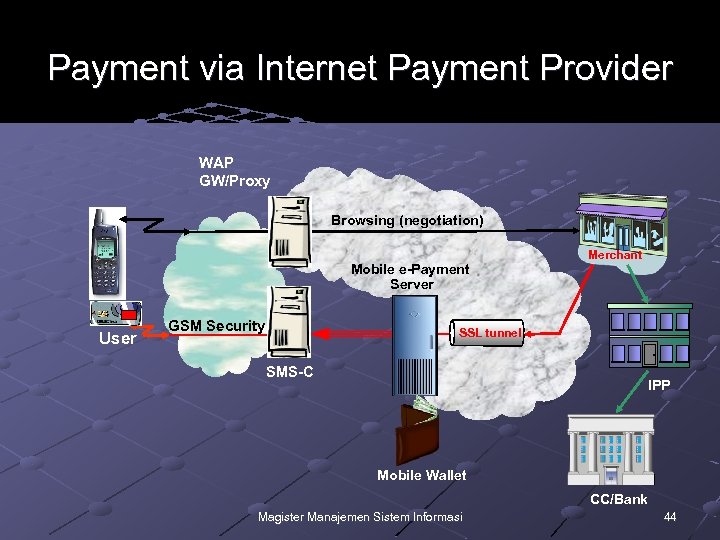
Payment via Internet Payment Provider WAP GW/Proxy Browsing (negotiation) Mobile e-Payment Server User GSM Security Merchant SSL tunnel SMS-C IPP Mobile Wallet CC/Bank Magister Manajemen Sistem Informasi 44
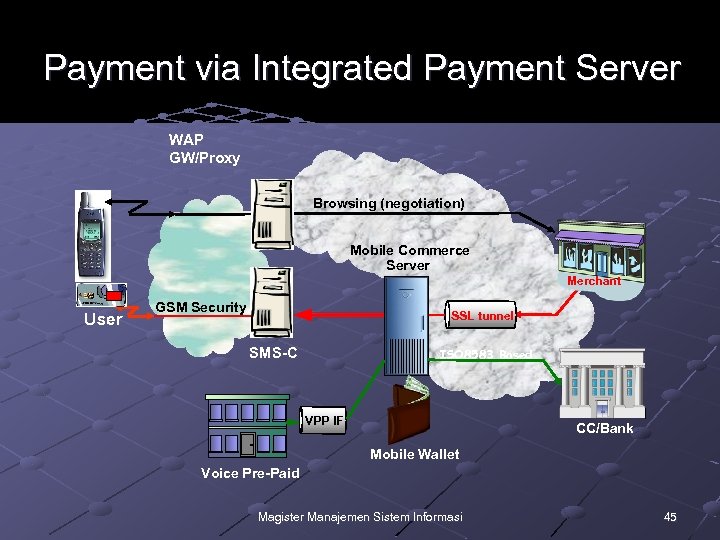
Payment via Integrated Payment Server WAP GW/Proxy Browsing (negotiation) Mobile Commerce Server Merchant User GSM Security SSL tunnel SMS-C ISO 8583 Based VPP IF CP CC/Bank Mobile Wallet Voice Pre-Paid Magister Manajemen Sistem Informasi 45

Outline m-Commerce Overview Infrastructure m-Commerce Applications Mobile Payment Limitations Security in m-Commerce Magister Manajemen Sistem Informasi 46
Limitations of m-Commerce Usability Problem small size of mobile devices (screens, keyboards, etc) limited storage capacity of devices hard to browse sites Technical Limitations lack of a standardized security protocol insufficient bandwidth 3 G licenses Magister Manajemen Sistem Informasi 47

Limitations of m-Commerce Technical Limitations… transmission and power consumption limitations n n poor reception in tunnels and certain buildings multi-path interference, weather, and terrain problems and distance-limited connections WAP Limitations Speed Cost Accessibility Magister Manajemen Sistem Informasi 48
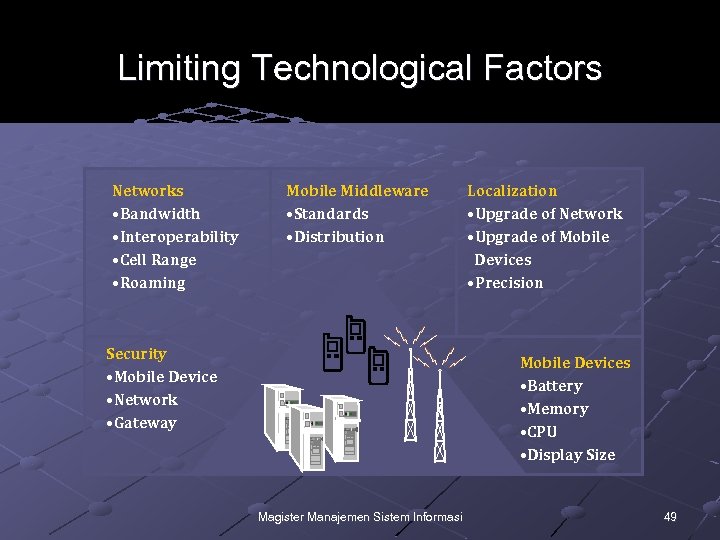
Limiting Technological Factors Networks • Bandwidth • Interoperability • Cell Range • Roaming Mobile Middleware • Standards • Distribution Security • Mobile Device • Network • Gateway Localization • Upgrade of Network • Upgrade of Mobile Devices • Precision Mobile Devices • Battery • Memory • CPU • Display Size Magister Manajemen Sistem Informasi 49

Potential Health Hazards Cellular radio signals = cancer? n n n No conclusive evidence yet could allow for myriad of lawsuits mobile devices may interfere with sensitive medical devices such as pacemakers Magister Manajemen Sistem Informasi 50

Outline m-Commerce Overview Infrastructure m-Commerce Applications Mobile Payment Limitations Security in m-Commerce Magister Manajemen Sistem Informasi 51
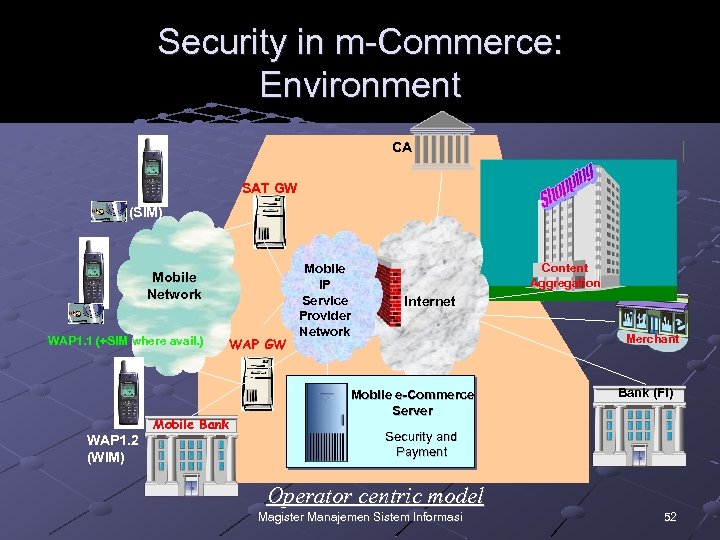
Security in m-Commerce: Environment CA SAT GW (SIM) Mobile Network WAP 1. 1 (+SIM where avail. ) WAP 1. 2 (WIM) Mobile Bank WAP GW Mobile IP Service Provider Network Content Aggregation Internet Merchant Mobile e-Commerce Server Bank (FI) Security and Payment Operator centric model Magister Manajemen Sistem Informasi 52
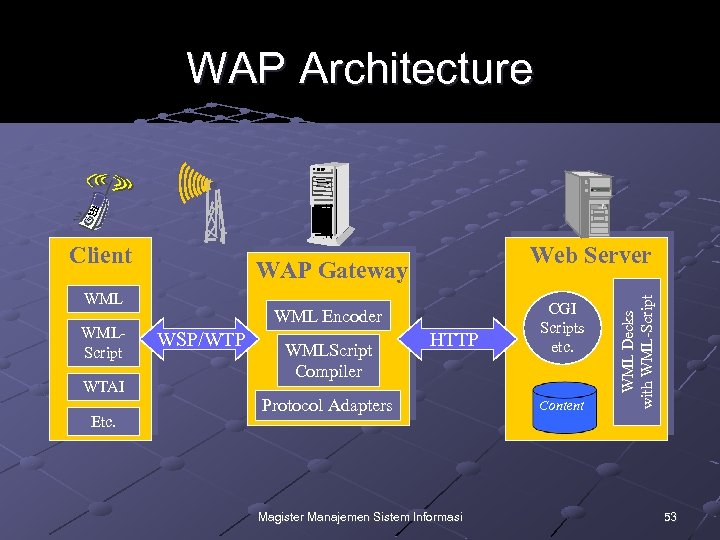
WAP Architecture WAP Gateway WMLScript WTAI Etc. Web Server WML Encoder WSP/WTP WMLScript Compiler HTTP Protocol Adapters Magister Manajemen Sistem Informasi CGI Scripts etc. Content WML Decks with WML-Script Client 53
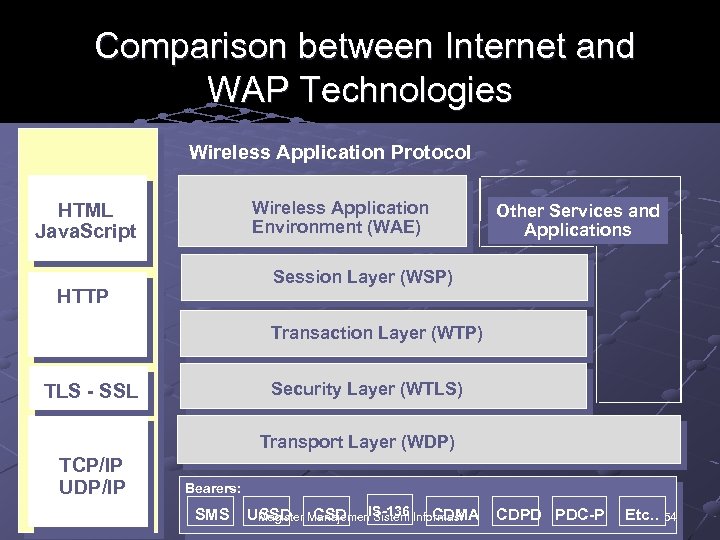
Comparison between Internet and WAP Technologies Wireless Application Protocol Wireless Application Environment (WAE) HTML Java. Script Other Services and Applications Session Layer (WSP) HTTP Transaction Layer (WTP) Security Layer (WTLS) TLS - SSL Transport Layer (WDP) TCP/IP UDP/IP Bearers: SMS CDMA USSD Manajemen. IS-136 Informasi Magister CSD Sistem CDPD PDC-P Etc. . 54
WAP Risks WAP Gap n n n Claim: WTLS protects WAP as SSL protects HTTP Problem: In the process of translating one protocol to another, information is decrypted and re-encrypted Solution: Doing decryption/re-encryption in the same process on the WAP gateway Wireless gateways as single point of failure Magister Manajemen Sistem Informasi 55

Platform Risks Without a secure OS, achieving security on mobile devices is almost impossible Learned lessons: n n n n Memory protection of processes Protected kernel rings File access control Authentication of principles to resources Differentiated user and process privileges Sandboxes for untrusted code Biometric authentication Magister Manajemen Sistem Informasi 56

WMLScripting is heavily used for client-side processing to offload servers and reduce demand on bandwidth Wireless Markup Language (WML) is the equivalent to HTML, but derived from XML WMLScript is WAP’s equivalent to Java. Script n Derived from Java. Script™ Magister Manajemen Sistem Informasi 57
WMLScript (cont. ) Integrated with WML n Reduces network traffic Has procedural logic, loops, conditionals, etc Optimized for small-memory, small-CPU devices Bytecode-based virtual machine Compiler in network Works with Wireless Telephony Application (WTA) to provide telephony functions Magister Manajemen Sistem Informasi 58

Risks of WMLScript • Lack of Security Model • Does not differentiate trusted local code from untrusted code downloaded from the Internet. So, there is no access control!! • WML Script is not type-safe. • Scripts can be scheduled to be pushed to the client device without the user’s knowledge • Does not prevent access to persistent storage • Possible attacks: • Theft or damage of personal information • Abusing user’s authentication information • Maliciously offloading money saved on smart cards Magister Manajemen Sistem Informasi 59
Bluetooth u u Bluetooth is the codename for a small, low-cost, short range wireless technology specification Enables users to connect a wide range of computing and telecommunication devices easily and simply, without the need to buy, carry, or connect cables. Bluetooth enables mobile phones, computers and PDAs to connect with each other using short-range radio waves, allowing them to "talk" to each other It is also cheap Magister Manajemen Sistem Informasi 60

Bluetooth Security Bluetooth provides security between any two Bluetooth devices for user protection and secrecy § mutual and unidirectional authentication § encrypts data between two devices § Session key generation • configurable encryption key length • keys can be changed at any time during a connection § Authorization (whether device X is allowed to have access service Y) • Trusted Device: The device has been previously authenticated, a link key is stored and the device is marked as “trusted” in the Device Database. • Untrusted Device: The device has been previously authenticated, link key is stored but the device is not marked as “trusted” in the Device Database • Unknown Device: No security information is available for this device. This is also an untrusted device. § automatic output power adaptation to reduce the range exactly to requirement, makes the system extremely difficult to eavesdrop Magister Manajemen Sistem Informasi 61

New Security Risks in m-Commerce • Abuse of cooperative nature of ad-hoc networks • An adversary that compromises one node can disseminate false routing information. • Malicious domains • A single malicious domain can compromise devices by downloading malicious code • Roaming (are you going to the bad guys ? ) • Users roam among non-trustworthy domains Magister Manajemen Sistem Informasi 62

New Security Risks (cont. ) • Launching attacks from mobile devices • With mobility, it is difficult to identify attackers • Loss or theft of device • More private information than desktop computers • Security keys might have been saved on the device • Access to corporate systems • Bluetooth provides security at the lower layers only: a stolen device can still be trusted Magister Manajemen Sistem Informasi 63

New Security Risks (cont. ) • Problems with Wireless Transport Layer Security (WTLS) protocol • Security Classes: • No certificates • Server only certificate (Most Common) • Server and client Certificates • Re-establishing connection without re-authentication • Requests can be redirected to malicious sites Magister Manajemen Sistem Informasi 64

New Privacy Risks • Monitoring user’s private information • Offline telemarketing • Who is going to read the “legal jargon” • Value added services based on location awareness (Location-Based Services) Magister Manajemen Sistem Informasi 65
e71188fd33eb7948e7ce7ba2d1bf2677.ppt