773f00304aa2f8c08ecb52384bf64383.ppt
- Количество слайдов: 33
 Internet Applications Theory & Applications
Internet Applications Theory & Applications
 Internet Applications - Ibrahim Otieno iotieno@uonbi. ac. ke +254 -0722 -429297 SCI/ICT Building 2 nd Floor Rm. 201
Internet Applications - Ibrahim Otieno iotieno@uonbi. ac. ke +254 -0722 -429297 SCI/ICT Building 2 nd Floor Rm. 201
 Communication Protocols Networking h/w without software is useless Software for network systems are necessary as part of solution to communication problems Normally large and very complicated Most networking software structured into layers for modularity, each with a specific function Layering is a structuring technique to organize networking software design and implementation
Communication Protocols Networking h/w without software is useless Software for network systems are necessary as part of solution to communication problems Normally large and very complicated Most networking software structured into layers for modularity, each with a specific function Layering is a structuring technique to organize networking software design and implementation
 Why Network software? Sending data through raw hardware is complex Equivalent to accessing files by making calls to disk controller to position read/write head and accessing individual sectors Network software provides interface to applications and hides the intricacies involved in sending information to a remote destination
Why Network software? Sending data through raw hardware is complex Equivalent to accessing files by making calls to disk controller to position read/write head and accessing individual sectors Network software provides interface to applications and hides the intricacies involved in sending information to a remote destination
 Why network software? Networks (devices) need some protocol in order to communicate and understand each other Protocols implemented by protocol software Computer communication complicated problem Network solution may require multiple protocols, each managing a part of the problem Protocols may be simple or complex, but all work together.
Why network software? Networks (devices) need some protocol in order to communicate and understand each other Protocols implemented by protocol software Computer communication complicated problem Network solution may require multiple protocols, each managing a part of the problem Protocols may be simple or complex, but all work together.
 Why network software? Designers analyze communication problem, divide into sub-problems then design a protocol for each sub-problem Well-designed protocol suite: ◦ ◦ efficient and effective – no redundancy, use of resources allows replacement of individual protocols without changes to other protocols Layering model is a solution to the problem of complexity in network protocols Model suggests dividing network protocol into layers, each solving part of comm. problem Layers have constraints that ease design
Why network software? Designers analyze communication problem, divide into sub-problems then design a protocol for each sub-problem Well-designed protocol suite: ◦ ◦ efficient and effective – no redundancy, use of resources allows replacement of individual protocols without changes to other protocols Layering model is a solution to the problem of complexity in network protocols Model suggests dividing network protocol into layers, each solving part of comm. problem Layers have constraints that ease design
 ISO OSI Reference Model Group called ISO introduced OSI Model OSI model - layered network architecture, with goal of standardization of network protocols OSI model an open system architecture because it connects systems open for communications with other systems Systems don’t have to be from same vendor or have the same O/S
ISO OSI Reference Model Group called ISO introduced OSI Model OSI model - layered network architecture, with goal of standardization of network protocols OSI model an open system architecture because it connects systems open for communications with other systems Systems don’t have to be from same vendor or have the same O/S
 The Seven-Layer OSI Model OSI model is composed of seven layers that define functions of communication protocols Each layer represents function performed on transfer of data between two applications A layer doesn’t have to define a single protocol; Defines function performed by any number of protocols
The Seven-Layer OSI Model OSI model is composed of seven layers that define functions of communication protocols Each layer represents function performed on transfer of data between two applications A layer doesn’t have to define a single protocol; Defines function performed by any number of protocols
 ISO OSI Reference Model Layers were defined with the following in mind: ◦ Created where different level of abstraction is needed ◦ ◦ Each layer performs a well-defined function Function of each layer should be chosen with the goal of defining standardized protocols ◦ Boundaries defined to minimize info flow across interfaces ◦ Number of layers large enough for distinct functions but small enough that the architecture not unwieldy
ISO OSI Reference Model Layers were defined with the following in mind: ◦ Created where different level of abstraction is needed ◦ ◦ Each layer performs a well-defined function Function of each layer should be chosen with the goal of defining standardized protocols ◦ Boundaries defined to minimize info flow across interfaces ◦ Number of layers large enough for distinct functions but small enough that the architecture not unwieldy
 ISO OSI Reference Model Related modules at same level are called a protocol stack or a stack Two constraints to be observed: ◦ Each layer depends on services by lower layers ◦ ◦ Layer n of destination receives same message sent by layer n of sender
ISO OSI Reference Model Related modules at same level are called a protocol stack or a stack Two constraints to be observed: ◦ Each layer depends on services by lower layers ◦ ◦ Layer n of destination receives same message sent by layer n of sender
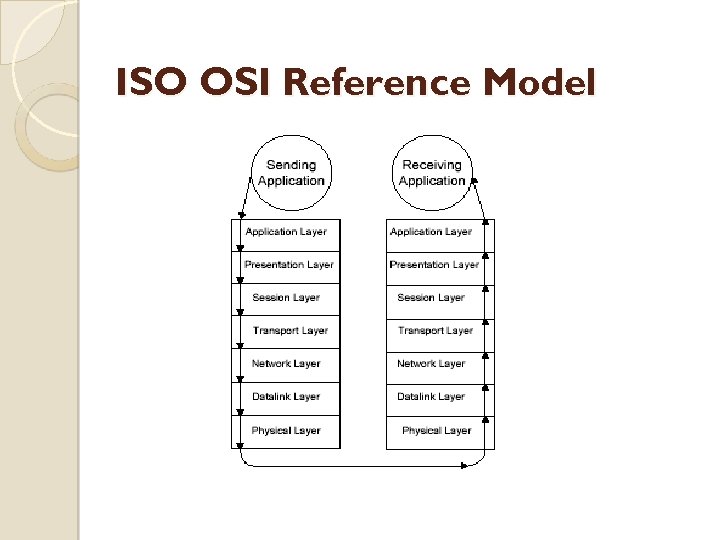 ISO OSI Reference Model
ISO OSI Reference Model
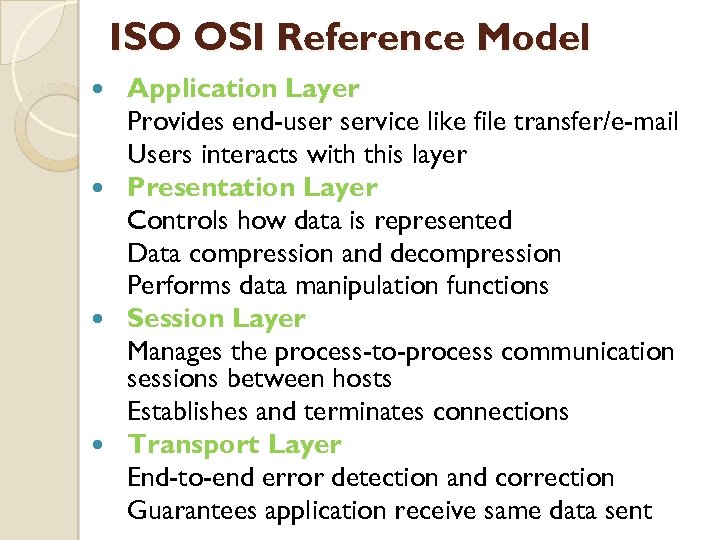 ISO OSI Reference Model Application Layer Provides end-user service like file transfer/e-mail Users interacts with this layer Presentation Layer Controls how data is represented Data compression and decompression Performs data manipulation functions Session Layer Manages the process-to-process communication sessions between hosts Establishes and terminates connections Transport Layer End-to-end error detection and correction Guarantees application receive same data sent
ISO OSI Reference Model Application Layer Provides end-user service like file transfer/e-mail Users interacts with this layer Presentation Layer Controls how data is represented Data compression and decompression Performs data manipulation functions Session Layer Manages the process-to-process communication sessions between hosts Establishes and terminates connections Transport Layer End-to-end error detection and correction Guarantees application receive same data sent
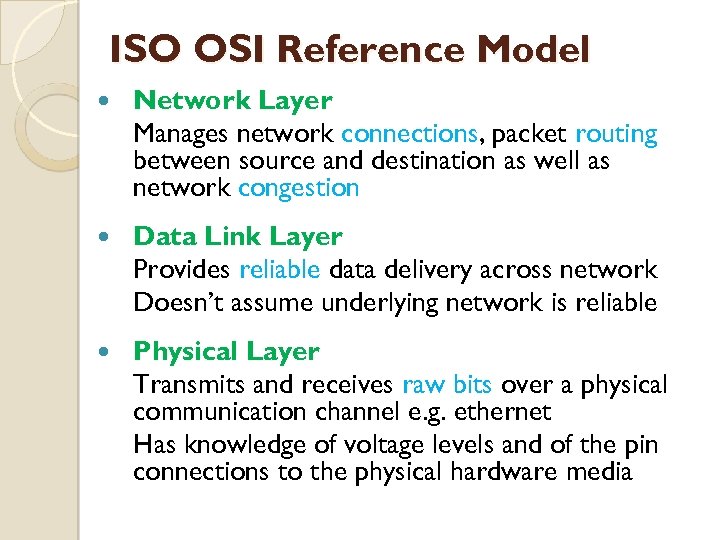 ISO OSI Reference Model Network Layer Manages network connections, packet routing between source and destination as well as network congestion Data Link Layer Provides reliable data delivery across network Doesn’t assume underlying network is reliable Physical Layer Transmits and receives raw bits over a physical communication channel e. g. ethernet Has knowledge of voltage levels and of the pin connections to the physical hardware media
ISO OSI Reference Model Network Layer Manages network connections, packet routing between source and destination as well as network congestion Data Link Layer Provides reliable data delivery across network Doesn’t assume underlying network is reliable Physical Layer Transmits and receives raw bits over a physical communication channel e. g. ethernet Has knowledge of voltage levels and of the pin connections to the physical hardware media
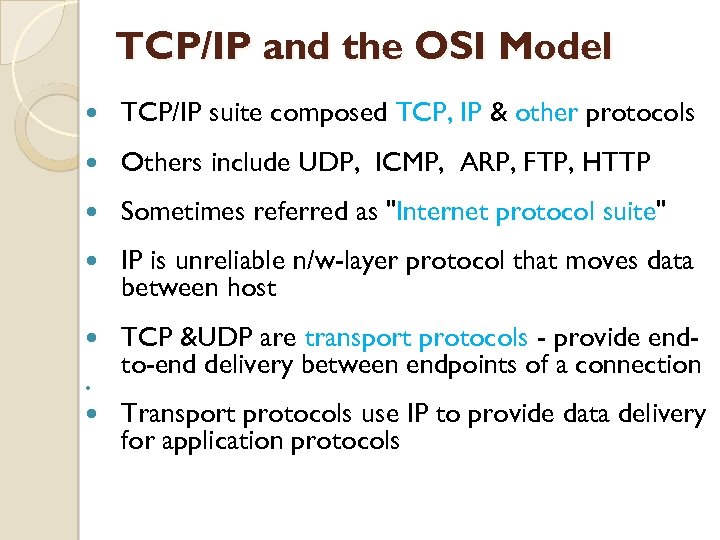 TCP/IP and the OSI Model TCP/IP suite composed TCP, IP & other protocols Others include UDP, ICMP, ARP, FTP, HTTP Sometimes referred as "Internet protocol suite" IP is unreliable n/w-layer protocol that moves data between host TCP &UDP are transport protocols - provide endto-end delivery between endpoints of a connection Transport protocols use IP to provide data delivery for application protocols
TCP/IP and the OSI Model TCP/IP suite composed TCP, IP & other protocols Others include UDP, ICMP, ARP, FTP, HTTP Sometimes referred as "Internet protocol suite" IP is unreliable n/w-layer protocol that moves data between host TCP &UDP are transport protocols - provide endto-end delivery between endpoints of a connection Transport protocols use IP to provide data delivery for application protocols
 TCP/IP and the OSI Model User Datagram Protocol (UDP) Simple transport-layer protocol, faster, less reliable Delivers independent datagrams between applications by use of headers with 3 parts: port no, message length & checksum Uses "best effort'' delivery - datagrams may be lost, delivered out of order, etc. Checksum guarantees integrity of data delivered Unlike TCP, UDP is not 'receipted’
TCP/IP and the OSI Model User Datagram Protocol (UDP) Simple transport-layer protocol, faster, less reliable Delivers independent datagrams between applications by use of headers with 3 parts: port no, message length & checksum Uses "best effort'' delivery - datagrams may be lost, delivered out of order, etc. Checksum guarantees integrity of data delivered Unlike TCP, UDP is not 'receipted’
 TCP/IP and the OSI Model TCP is the most widely reliable transport-layer protocol TCP moves data between applications with no losses, duplication or errors Compensates for loss, delay, duplication etc TCP – connection-oriented: application requests connection to destination and uses it to transfer data
TCP/IP and the OSI Model TCP is the most widely reliable transport-layer protocol TCP moves data between applications with no losses, duplication or errors Compensates for loss, delay, duplication etc TCP – connection-oriented: application requests connection to destination and uses it to transfer data
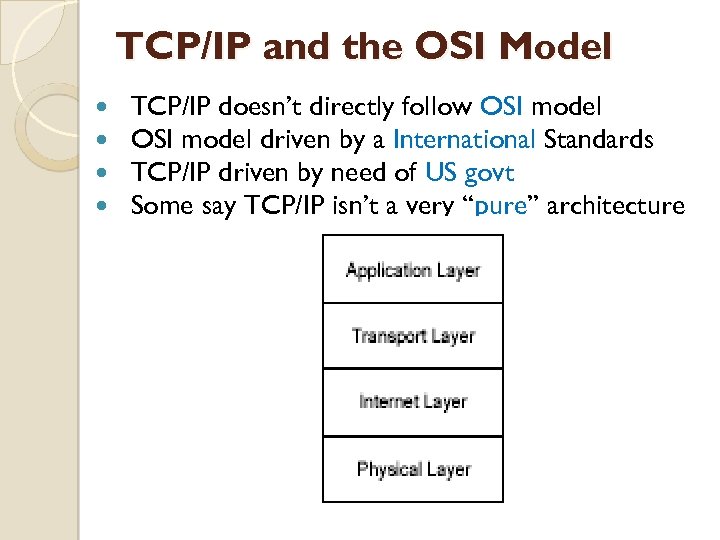 TCP/IP and the OSI Model TCP/IP doesn’t directly follow OSI model driven by a International Standards TCP/IP driven by need of US govt Some say TCP/IP isn’t a very “pure” architecture
TCP/IP and the OSI Model TCP/IP doesn’t directly follow OSI model driven by a International Standards TCP/IP driven by need of US govt Some say TCP/IP isn’t a very “pure” architecture
 TCP/IP and the OSI Model Application Layer Consists of applications that make use of network e. g. file-transfer utility Application and presentation layers of OSI model fit into this layer - compression & decompression Transport layer absorbed this layer, however, still consider its function as a logical layer Transport Layer Provides end-to-end data delivery OSI’s session & transport layers fit into this layer Uses sockets - end-point of communication composed of address and port on computer TCP provides for reliable data delivery
TCP/IP and the OSI Model Application Layer Consists of applications that make use of network e. g. file-transfer utility Application and presentation layers of OSI model fit into this layer - compression & decompression Transport layer absorbed this layer, however, still consider its function as a logical layer Transport Layer Provides end-to-end data delivery OSI’s session & transport layers fit into this layer Uses sockets - end-point of communication composed of address and port on computer TCP provides for reliable data delivery
 TCP/IP and the OSI Model Internet Layer Defines datagram & handles routing and delivery Datagram contains the source & destination address, data, as well as other control fields OSI’s network and data link layers fit into this layer IP is analogous to the network layer Data link layer usually not represented but IP could be used to support this function Physical Layer TCP/IP makes no effort to define the underlying network physical connectivity, instead, makes use of existing standards such as (IEEE)
TCP/IP and the OSI Model Internet Layer Defines datagram & handles routing and delivery Datagram contains the source & destination address, data, as well as other control fields OSI’s network and data link layers fit into this layer IP is analogous to the network layer Data link layer usually not represented but IP could be used to support this function Physical Layer TCP/IP makes no effort to define the underlying network physical connectivity, instead, makes use of existing standards such as (IEEE)
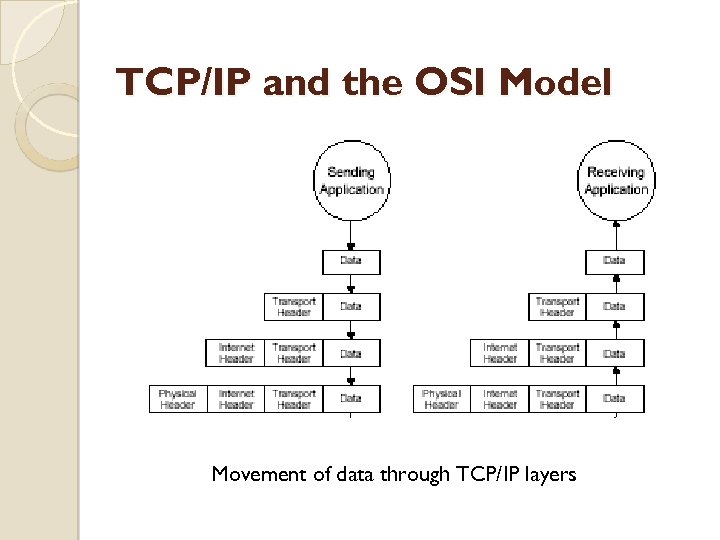 TCP/IP and the OSI Model Movement of data through TCP/IP layers
TCP/IP and the OSI Model Movement of data through TCP/IP layers
 Internet Protocol What is the difference between a repeater, bridge and a router ? What is the role of a router in internetworking? Internet is a virtual network created by software?
Internet Protocol What is the difference between a repeater, bridge and a router ? What is the role of a router in internetworking? Internet is a virtual network created by software?
 Addresses for the Virtual Internet Goal of internetworking to provide a seamless communication system Achieved by IP software hiding physical details of n/w and provide large virtual network (VN) VN operate like normal n/w, computers send & receive packets of data Difference between internet and physical network is that internet is an abstraction created entirely by software
Addresses for the Virtual Internet Goal of internetworking to provide a seamless communication system Achieved by IP software hiding physical details of n/w and provide large virtual network (VN) VN operate like normal n/w, computers send & receive packets of data Difference between internet and physical network is that internet is an abstraction created entirely by software
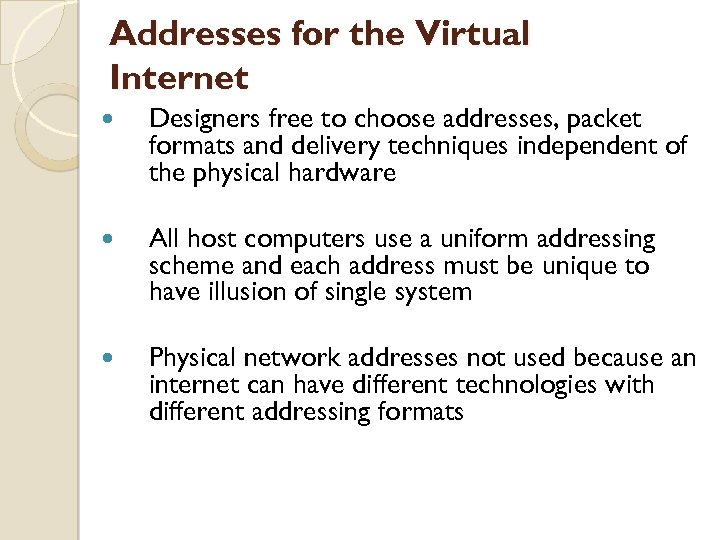 Addresses for the Virtual Internet Designers free to choose addresses, packet formats and delivery techniques independent of the physical hardware All host computers use a uniform addressing scheme and each address must be unique to have illusion of single system Physical network addresses not used because an internet can have different technologies with different addressing formats
Addresses for the Virtual Internet Designers free to choose addresses, packet formats and delivery techniques independent of the physical hardware All host computers use a uniform addressing scheme and each address must be unique to have illusion of single system Physical network addresses not used because an internet can have different technologies with different addressing formats
 Addresses for the Virtual Internet Protocol s/w defines uniform addressing scheme independent of underlying physical address Sender places destination’s address in packet and passes packet to protocol software for delivery Software uses destination protocol address to forward the packet to the destination computer Uniform address create illusion of large seamless network hiding details of physical addresses Applications communicate without knowing their hardware addresses
Addresses for the Virtual Internet Protocol s/w defines uniform addressing scheme independent of underlying physical address Sender places destination’s address in packet and passes packet to protocol software for delivery Software uses destination protocol address to forward the packet to the destination computer Uniform address create illusion of large seamless network hiding details of physical addresses Applications communicate without knowing their hardware addresses
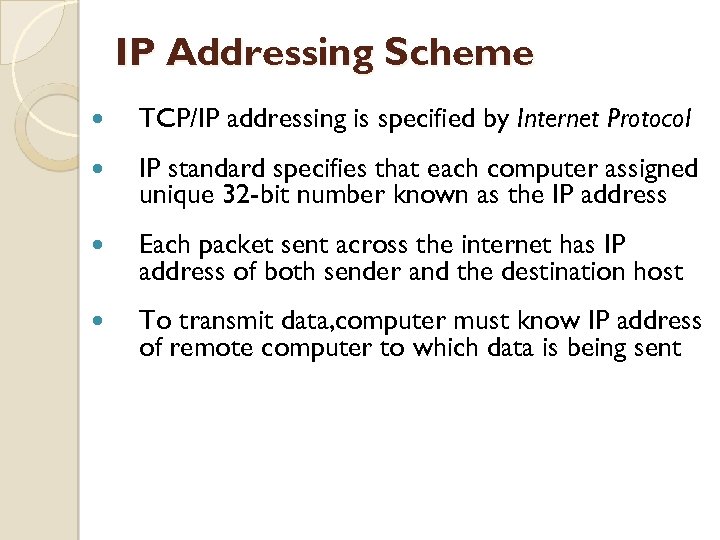 IP Addressing Scheme TCP/IP addressing is specified by Internet Protocol IP standard specifies that each computer assigned unique 32 -bit number known as the IP address Each packet sent across the internet has IP address of both sender and the destination host To transmit data, computer must know IP address of remote computer to which data is being sent
IP Addressing Scheme TCP/IP addressing is specified by Internet Protocol IP standard specifies that each computer assigned unique 32 -bit number known as the IP address Each packet sent across the internet has IP address of both sender and the destination host To transmit data, computer must know IP address of remote computer to which data is being sent
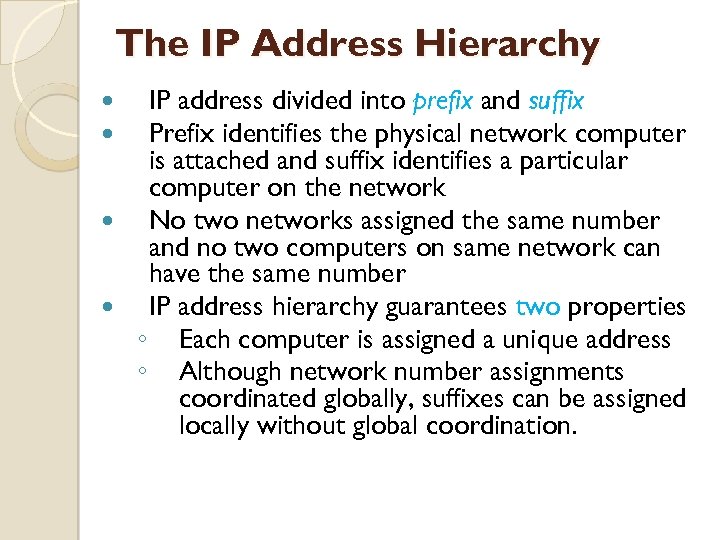 The IP Address Hierarchy IP address divided into prefix and suffix Prefix identifies the physical network computer is attached and suffix identifies a particular computer on the network No two networks assigned the same number and no two computers on same network can have the same number IP address hierarchy guarantees two properties ◦ Each computer is assigned a unique address ◦ Although network number assignments coordinated globally, suffixes can be assigned locally without global coordination.
The IP Address Hierarchy IP address divided into prefix and suffix Prefix identifies the physical network computer is attached and suffix identifies a particular computer on the network No two networks assigned the same number and no two computers on same network can have the same number IP address hierarchy guarantees two properties ◦ Each computer is assigned a unique address ◦ Although network number assignments coordinated globally, suffixes can be assigned locally without global coordination.
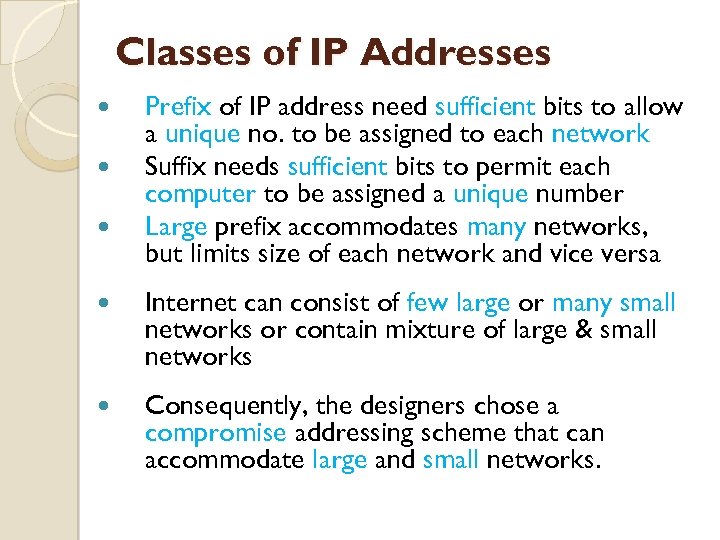 Classes of IP Addresses Prefix of IP address need sufficient bits to allow a unique no. to be assigned to each network Suffix needs sufficient bits to permit each computer to be assigned a unique number Large prefix accommodates many networks, but limits size of each network and vice versa Internet can consist of few large or many small networks or contain mixture of large & small networks Consequently, the designers chose a compromise addressing scheme that can accommodate large and small networks.
Classes of IP Addresses Prefix of IP address need sufficient bits to allow a unique no. to be assigned to each network Suffix needs sufficient bits to permit each computer to be assigned a unique number Large prefix accommodates many networks, but limits size of each network and vice versa Internet can consist of few large or many small networks or contain mixture of large & small networks Consequently, the designers chose a compromise addressing scheme that can accommodate large and small networks.
 Classes of IP Addresses … ◦ ◦ ◦ Original scheme, divides IP address space into 3 primary classes, each with different size prefix/suffix First 4 bits determine class to which the address belongs, and specifies how the remainder is divided into prefix and suffix: Class A – First bit 0 used for class identification, prefix consists of next 7 and rest 24 for suffix Class B – First 2 bits start with 10 (class identification) prefix consists of next 14 and rest 16 for suffix Class C – First 3 bits start with 110 (class identification) prefix consists of next 21 and rest 8 for suffix Class D – First 4 bits start with 1110 (class identification) and rest used as multicast address Class E – First 4 bits start with 1111 used for class identification, and rest reserved for future use
Classes of IP Addresses … ◦ ◦ ◦ Original scheme, divides IP address space into 3 primary classes, each with different size prefix/suffix First 4 bits determine class to which the address belongs, and specifies how the remainder is divided into prefix and suffix: Class A – First bit 0 used for class identification, prefix consists of next 7 and rest 24 for suffix Class B – First 2 bits start with 10 (class identification) prefix consists of next 14 and rest 16 for suffix Class C – First 3 bits start with 110 (class identification) prefix consists of next 21 and rest 8 for suffix Class D – First 4 bits start with 1110 (class identification) and rest used as multicast address Class E – First 4 bits start with 1111 used for class identification, and rest reserved for future use
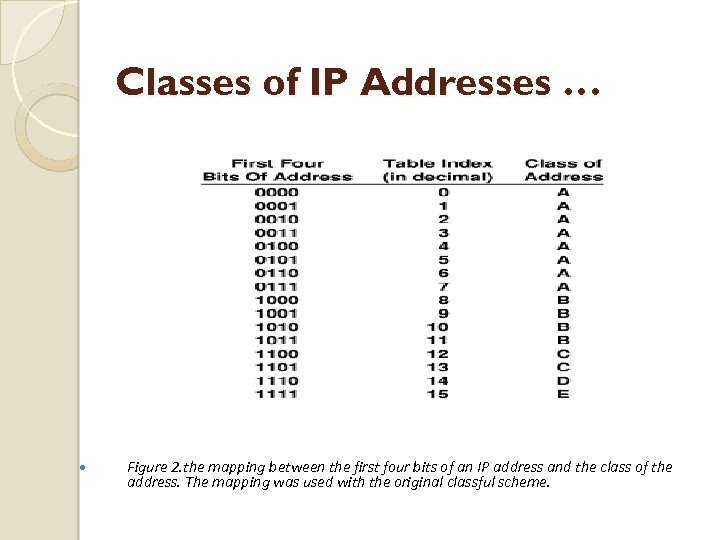 Classes of IP Addresses … Figure 2. the mapping between the first four bits of an IP address and the class of the address. The mapping was used with the original classful scheme.
Classes of IP Addresses … Figure 2. the mapping between the first four bits of an IP address and the class of the address. The mapping was used with the original classful scheme.
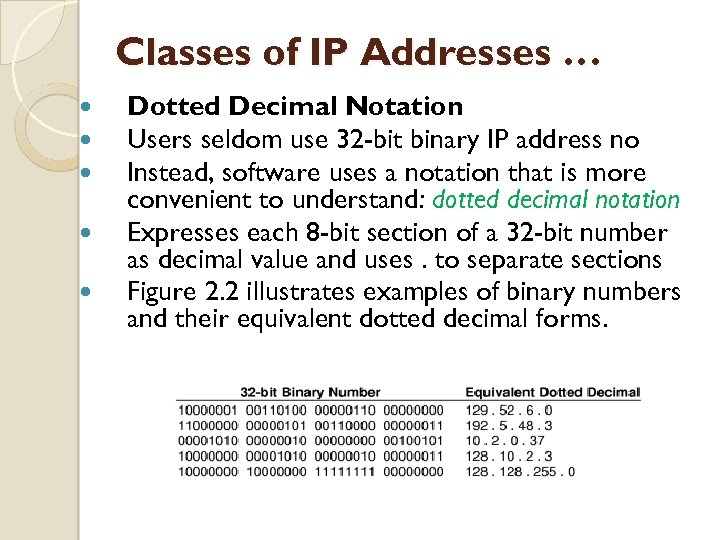 Classes of IP Addresses … Dotted Decimal Notation Users seldom use 32 -bit binary IP address no Instead, software uses a notation that is more convenient to understand: dotted decimal notation Expresses each 8 -bit section of a 32 -bit number as decimal value and uses. to separate sections Figure 2. 2 illustrates examples of binary numbers and their equivalent dotted decimal forms.
Classes of IP Addresses … Dotted Decimal Notation Users seldom use 32 -bit binary IP address no Instead, software uses a notation that is more convenient to understand: dotted decimal notation Expresses each 8 -bit section of a 32 -bit number as decimal value and uses. to separate sections Figure 2. 2 illustrates examples of binary numbers and their equivalent dotted decimal forms.
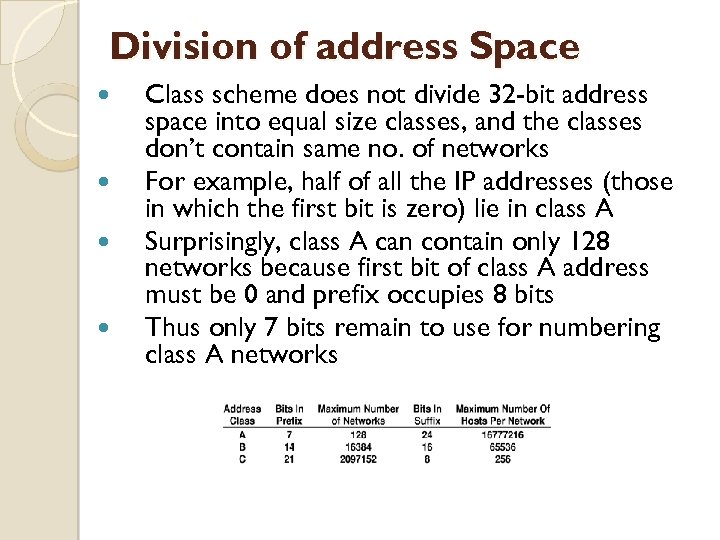 Division of address Space Class scheme does not divide 32 -bit address space into equal size classes, and the classes don’t contain same no. of networks For example, half of all the IP addresses (those in which the first bit is zero) lie in class A Surprisingly, class A can contain only 128 networks because first bit of class A address must be 0 and prefix occupies 8 bits Thus only 7 bits remain to use for numbering class A networks
Division of address Space Class scheme does not divide 32 -bit address space into equal size classes, and the classes don’t contain same no. of networks For example, half of all the IP addresses (those in which the first bit is zero) lie in class A Surprisingly, class A can contain only 128 networks because first bit of class A address must be 0 and prefix occupies 8 bits Thus only 7 bits remain to use for numbering class A networks
 Routers and IP Addressing The IP protocol specifies that routers be given IP addresses as well Each router assigned two or more IP addresses To understand why, recall two facts: ◦ Router has connections to multiple networks ◦ Each IP address contains a prefix that specifies a physical n/w
Routers and IP Addressing The IP protocol specifies that routers be given IP addresses as well Each router assigned two or more IP addresses To understand why, recall two facts: ◦ Router has connections to multiple networks ◦ Each IP address contains a prefix that specifies a physical n/w
 Routers and IP Addressing A single IP address does not suffice for a router because each router connects multiple networks This is the fundamental principle of IP addresses: ◦ ◦ ◦ An IP address does not identify a specific computer Instead, each IP address identifies a connection between a computer and a network Computer with multiple network connections (e. g. router) must be assigned one IP address for each connection
Routers and IP Addressing A single IP address does not suffice for a router because each router connects multiple networks This is the fundamental principle of IP addresses: ◦ ◦ ◦ An IP address does not identify a specific computer Instead, each IP address identifies a connection between a computer and a network Computer with multiple network connections (e. g. router) must be assigned one IP address for each connection


