e53b26c4ab54e3d803696f6e4bd74e17.ppt
- Количество слайдов: 35
 Internet Applications Theory & Applications
Internet Applications Theory & Applications
 Internet Application - Ibrahim Otieno iotieno@uonbi. ac. ke +254 -0722 -429297 SCI/ICT Building 2 nd Floor Rm. 201
Internet Application - Ibrahim Otieno iotieno@uonbi. ac. ke +254 -0722 -429297 SCI/ICT Building 2 nd Floor Rm. 201
 Client-Server Interaction Functionality of Application Software Physical connections & communication protocols useful but most useful function provided by application software Applications provide high-level services and determine how users perceive the capabilities of the internet e. g. email, browsing, transfer of files
Client-Server Interaction Functionality of Application Software Physical connections & communication protocols useful but most useful function provided by application software Applications provide high-level services and determine how users perceive the capabilities of the internet e. g. email, browsing, transfer of files
 Client-Server Interaction Functionality of Application Software Applications determine formatting and access of information They also define symbolic names used to identify physical & abstract resources like computers, printers, mailboxes etc Symbolic names allow access or use of services without understanding low-level details
Client-Server Interaction Functionality of Application Software Applications determine formatting and access of information They also define symbolic names used to identify physical & abstract resources like computers, printers, mailboxes etc Symbolic names allow access or use of services without understanding low-level details
 Functionality of an Internet provides communication infrastructure but does not specify services offered Internet like a telephone system - provides ability to communicate but doesn’t know what computers do with communication service Network h/w and protocol s/w do not know when to initiate contact with remote computer Communication across internet requires pair of application programs to cooperate like placing a telephone call and it is received on other side
Functionality of an Internet provides communication infrastructure but does not specify services offered Internet like a telephone system - provides ability to communicate but doesn’t know what computers do with communication service Network h/w and protocol s/w do not know when to initiate contact with remote computer Communication across internet requires pair of application programs to cooperate like placing a telephone call and it is received on other side
 The Client-Server paradigm Network applications use client-server paradigm Server wait passively for contact and client initiate communication actively Client and server refer to two applications involved in a communication In general, client s/w has following characteristics: ◦ Is application that becomes client temporarily when remote access is needed, and performs computations locally
The Client-Server paradigm Network applications use client-server paradigm Server wait passively for contact and client initiate communication actively Client and server refer to two applications involved in a communication In general, client s/w has following characteristics: ◦ Is application that becomes client temporarily when remote access is needed, and performs computations locally
 The Client-Server paradigm In general, client s/w has following characteristics: ◦ ◦ ◦ Invoked by user and executes for one session it runs locally on a user’s personal computer actively initiates contact with a server actively contacts one remote server at a time but can access many Does not require special h/w or special O/S
The Client-Server paradigm In general, client s/w has following characteristics: ◦ ◦ ◦ Invoked by user and executes for one session it runs locally on a user’s personal computer actively initiates contact with a server actively contacts one remote server at a time but can access many Does not require special h/w or special O/S
 The Client-Server paradigm In contrast, server software: ◦ Is a special-purpose, privileged program dedicated to providing one service, but can handle multiple remote clients at same time ◦ invoked automatically at system boot ◦ runs on a shared computer ◦ waits passively for contact from remote clients ◦ Requires powerful h/w and a sophisticated O/S Server is not computer (with power h/w, O/S etc) on which the server process runs, the computer is referred to as server-class computer
The Client-Server paradigm In contrast, server software: ◦ Is a special-purpose, privileged program dedicated to providing one service, but can handle multiple remote clients at same time ◦ invoked automatically at system boot ◦ runs on a shared computer ◦ waits passively for contact from remote clients ◦ Requires powerful h/w and a sophisticated O/S Server is not computer (with power h/w, O/S etc) on which the server process runs, the computer is referred to as server-class computer
 Requests, Responses and Direction of Data Flow Info flows in either or both directions For example, client may request a file and server sends copy or it may send a copy of a file to server for storage Client may send series of requests & server issues series of responses Like most application programs, a client and server use transport protocol to communicate A server-class computer can offer multiple services at same time to utilize resources; a separate server program needed for each service
Requests, Responses and Direction of Data Flow Info flows in either or both directions For example, client may request a file and server sends copy or it may send a copy of a file to server for storage Client may send series of requests & server issues series of responses Like most application programs, a client and server use transport protocol to communicate A server-class computer can offer multiple services at same time to utilize resources; a separate server program needed for each service
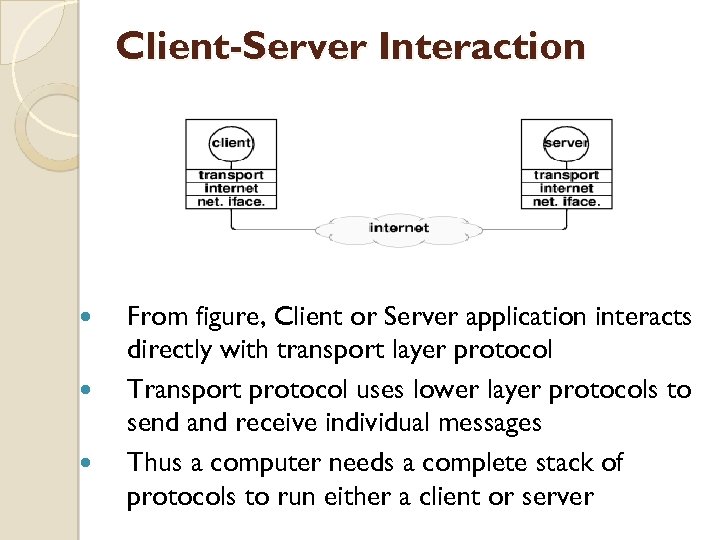 Client-Server Interaction From figure, Client or Server application interacts directly with transport layer protocol Transport protocol uses lower layer protocols to send and receive individual messages Thus a computer needs a complete stack of protocols to run either a client or server
Client-Server Interaction From figure, Client or Server application interacts directly with transport layer protocol Transport protocol uses lower layer protocols to send and receive individual messages Thus a computer needs a complete stack of protocols to run either a client or server
 Identifying a Particular Service TP provides way for client to specify service Mechanism assigns each service a unique id, and requires both client and server to use the id Server registers with local protocol software by specifying identifier for service it offers Client’s protocol specifies id for required service TP software on server’s machine uses the id to determine the server program to handle request
Identifying a Particular Service TP provides way for client to specify service Mechanism assigns each service a unique id, and requires both client and server to use the id Server registers with local protocol software by specifying identifier for service it offers Client’s protocol specifies id for required service TP software on server’s machine uses the id to determine the server program to handle request
 Identifying a Particular Service TCP uses a 16 -bit integer value known as protocol port number (PPN) to identify services and client specifies PPN of desired service. A server computer can allow multiple copies of a server for a single service, i. e. support concurrency Concurrency is fundamental to client-server model of interaction Concurrent server offers service to multiple clients at same time, without requiring each to wait for clients to finish
Identifying a Particular Service TCP uses a 16 -bit integer value known as protocol port number (PPN) to identify services and client specifies PPN of desired service. A server computer can allow multiple copies of a server for a single service, i. e. support concurrency Concurrency is fundamental to client-server model of interaction Concurrent server offers service to multiple clients at same time, without requiring each to wait for clients to finish
 Electronic Mail Originally, electronic mail (email) designed as a extension of the traditional office memo; Individual created a message and specified other individuals as recipients Email software transmitted copy of message to each recipient Email systems evolved and are automated to permit more complex interactions; can receive & send a reply automatically
Electronic Mail Originally, electronic mail (email) designed as a extension of the traditional office memo; Individual created a message and specified other individuals as recipients Email software transmitted copy of message to each recipient Email systems evolved and are automated to permit more complex interactions; can receive & send a reply automatically
 Electronic Mailboxes & Addresses Before sending email sender and recipient must be assigned an electronic mail box Mailbox is passive storage area e. g. file on disk Permissions set to allow email software add incoming message to mailbox, but allow owner right read/remove messages Mailbox assigned unique email address; when someone sends mail; specify recipient address Address has two parts; second specifies a host and first specifies a mailbox on host An “at sign” separates the two components: mailbox@computer
Electronic Mailboxes & Addresses Before sending email sender and recipient must be assigned an electronic mail box Mailbox is passive storage area e. g. file on disk Permissions set to allow email software add incoming message to mailbox, but allow owner right read/remove messages Mailbox assigned unique email address; when someone sends mail; specify recipient address Address has two parts; second specifies a host and first specifies a mailbox on host An “at sign” separates the two components: mailbox@computer
 Electronic Mailboxes & Addresses This division achieves two goals: ◦ Allow each computer to assign mailbox identifiers independently ◦ Permits users to exchange email messages Software on sender uses second part to determine computer to contact and software on recipient uses first to select a particular mailbox to place the message An email message has a simple format Consists of ASCII text separated into two parts First part, header, contains information about message: sender, recipient(s), date … Second part, body, contains text of message Header follows a standard format
Electronic Mailboxes & Addresses This division achieves two goals: ◦ Allow each computer to assign mailbox identifiers independently ◦ Permits users to exchange email messages Software on sender uses second part to determine computer to contact and software on recipient uses first to select a particular mailbox to place the message An email message has a simple format Consists of ASCII text separated into two parts First part, header, contains information about message: sender, recipient(s), date … Second part, body, contains text of message Header follows a standard format
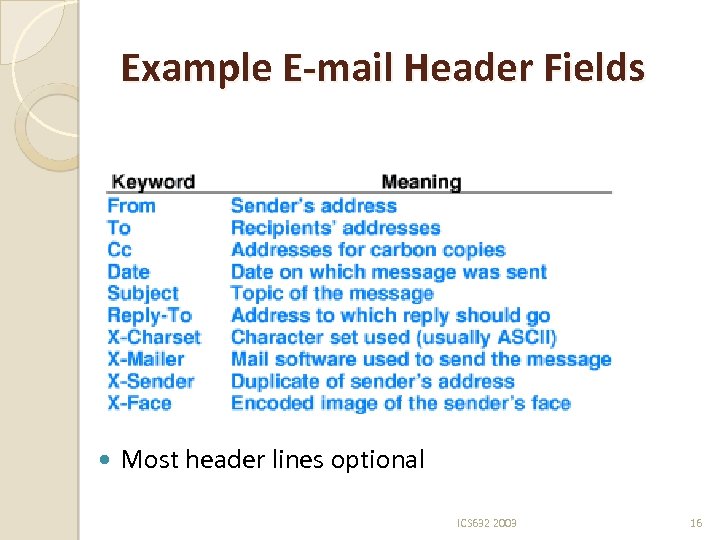 Example E-mail Header Fields Most header lines optional ICS 632 2003 16
Example E-mail Header Fields Most header lines optional ICS 632 2003 16
 Multipurpose Internet Mail Extensions (MIME) Original email system handle text only Body of email message was restricted to printable ASCII characters - one could not transfer a binary file directly as body of an email Need to develop schemes to allow email to be used to transfer binary program or graphics … Schemes encode data in text form; send in email and decoded by recipient back to binary form To help coordinate & unify various schemes for encoding binary data, MIME was invented MIME doesn’t dictate a single format for encoding Permit sender & receiver choose suitable scheme
Multipurpose Internet Mail Extensions (MIME) Original email system handle text only Body of email message was restricted to printable ASCII characters - one could not transfer a binary file directly as body of an email Need to develop schemes to allow email to be used to transfer binary program or graphics … Schemes encode data in text form; send in email and decoded by recipient back to binary form To help coordinate & unify various schemes for encoding binary data, MIME was invented MIME doesn’t dictate a single format for encoding Permit sender & receiver choose suitable scheme
 Multipurpose Internet Mail Extensions (MIME) Lines in header specify message follows MIME format and specify type of data and encoding MIME allows sender divide a message into several parts & specify encoding for each part separately User can send text message and attach graphics When recipient views message, system displays text message and asks user how to handle attachment – save copy or display on screen Major advantage of MIME is flexibility – doesn’t specify single encoding scheme that must be used
Multipurpose Internet Mail Extensions (MIME) Lines in header specify message follows MIME format and specify type of data and encoding MIME allows sender divide a message into several parts & specify encoding for each part separately User can send text message and attach graphics When recipient views message, system displays text message and asks user how to handle attachment – save copy or display on screen Major advantage of MIME is flexibility – doesn’t specify single encoding scheme that must be used
 MIME Encoding Sender ◦ Inserts additional header lines ◦ Encodes binary data in (printable) ASCII Sent like standard message Receiver ◦ Interprets header lines ◦ Extracts and decodes parts Separate standards for content and encoding ICS 632 2003 19
MIME Encoding Sender ◦ Inserts additional header lines ◦ Encodes binary data in (printable) ASCII Sent like standard message Receiver ◦ Interprets header lines ◦ Extracts and decodes parts Separate standards for content and encoding ICS 632 2003 19
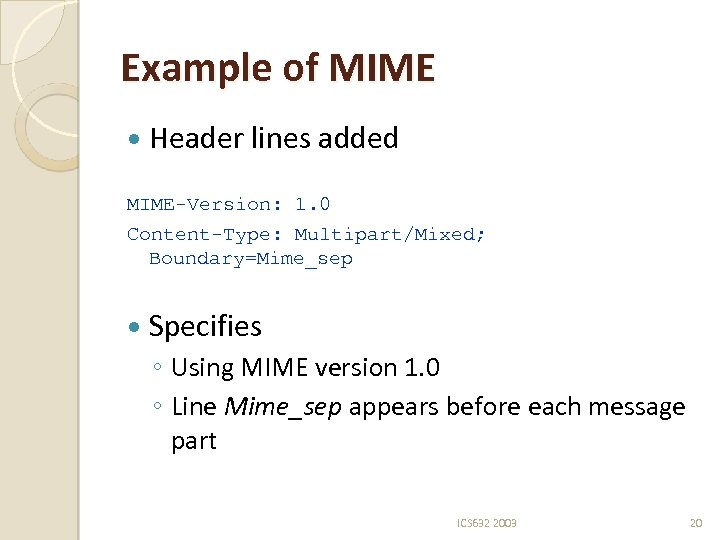 Example of MIME Header lines added MIME-Version: 1. 0 Content-Type: Multipart/Mixed; Boundary=Mime_sep Specifies ◦ Using MIME version 1. 0 ◦ Line Mime_sep appears before each message part ICS 632 2003 20
Example of MIME Header lines added MIME-Version: 1. 0 Content-Type: Multipart/Mixed; Boundary=Mime_sep Specifies ◦ Using MIME version 1. 0 ◦ Line Mime_sep appears before each message part ICS 632 2003 20
 Mail Transfer User creates email and specifies recipients, email software transfers copy of message to recipients In most systems, two separate pieces of software required ◦ Email interface program – interface for composing and reading message ◦ Mail transfer program – handles details of sending copy of message to remote computer
Mail Transfer User creates email and specifies recipients, email software transfers copy of message to recipients In most systems, two separate pieces of software required ◦ Email interface program – interface for composing and reading message ◦ Mail transfer program – handles details of sending copy of message to remote computer
 Mail Transfer After user composes an outgoing message, email interface program places message in queue that mail transfer program handles Mail transfers copy of message to each recipient Sending a copy to a remote user more complex than local host Mail transfer program becomes a client & contacts server on remote machine
Mail Transfer After user composes an outgoing message, email interface program places message in queue that mail transfer program handles Mail transfers copy of message to each recipient Sending a copy to a remote user more complex than local host Mail transfer program becomes a client & contacts server on remote machine
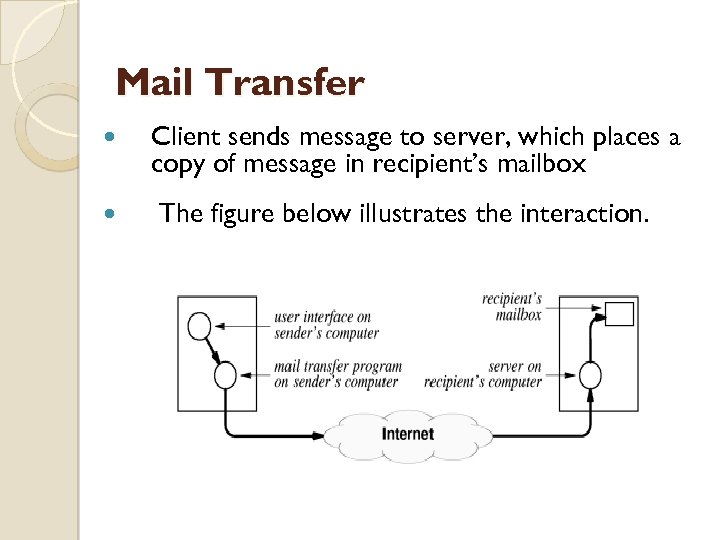 Mail Transfer Client sends message to server, which places a copy of message in recipient’s mailbox The figure below illustrates the interaction.
Mail Transfer Client sends message to server, which places a copy of message in recipient’s mailbox The figure below illustrates the interaction.
 The Simple Mail Transfer Protocol (SMTP) Mail transfer program forms a TCP connection when it contacts a server on remote machine After connection, two programs follow SMTP that allows sender identify itself, specify recipient, and transfer email message Though may seem simple, SMTP protocol handles many details Allows sender to ask whether mailbox exists on remote computer Further, SMTP requires reliable delivery – sender must keep copy of message until receiver has stored a copy in nonvolatile memory
The Simple Mail Transfer Protocol (SMTP) Mail transfer program forms a TCP connection when it contacts a server on remote machine After connection, two programs follow SMTP that allows sender identify itself, specify recipient, and transfer email message Though may seem simple, SMTP protocol handles many details Allows sender to ask whether mailbox exists on remote computer Further, SMTP requires reliable delivery – sender must keep copy of message until receiver has stored a copy in nonvolatile memory
 The Simple Mail Transfer Protocol (SMTP) Most mail transfer programs optimized to handle all recipients remote computer at same time Instead of transferring different copies to different mailboxes on same server, program forms single connection to server, specifies recipients and transfers single copy of message Server then delivers a copy to all recipients This optimization has advantage of: ◦ ◦ ◦ Reducing network bandwidth Reducing delay for users to receive copy of message If internet between sender and receiver fails, either all recipients receive message or none do
The Simple Mail Transfer Protocol (SMTP) Most mail transfer programs optimized to handle all recipients remote computer at same time Instead of transferring different copies to different mailboxes on same server, program forms single connection to server, specifies recipients and transfers single copy of message Server then delivers a copy to all recipients This optimization has advantage of: ◦ ◦ ◦ Reducing network bandwidth Reducing delay for users to receive copy of message If internet between sender and receiver fails, either all recipients receive message or none do
 Mail Access Users prefer to have mailbox located on computer they use, but this not practical Computer must have sufficient CPU capacity, run mail server, and have multithreading O/S Moreover, servers expected to run continuously Mailbox is a storage location on disk; remote programs do not access mail box directly Computer system that has mailboxes must run a mail server program that accepts incoming mail and stores it in correct mailbox Mail server programs operate in background, allow user to run other applications at same time Most mail servers run multiple copies (threads) of server program at same time - concurrency
Mail Access Users prefer to have mailbox located on computer they use, but this not practical Computer must have sufficient CPU capacity, run mail server, and have multithreading O/S Moreover, servers expected to run continuously Mailbox is a storage location on disk; remote programs do not access mail box directly Computer system that has mailboxes must run a mail server program that accepts incoming mail and stores it in correct mailbox Mail server programs operate in background, allow user to run other applications at same time Most mail servers run multiple copies (threads) of server program at same time - concurrency
 Mail Access TCP/IP has protocol that provides remote access to electronic mailbox Post Office Protocol (POP) - allows user’s mailbox to reside on mail server, and allows user to access items in mailbox from another computer The protocol requires an additional server that uses POP protocol to run on mail server User runs email software that becomes client of POP server to access the contents of the mailbox
Mail Access TCP/IP has protocol that provides remote access to electronic mailbox Post Office Protocol (POP) - allows user’s mailbox to reside on mail server, and allows user to access items in mailbox from another computer The protocol requires an additional server that uses POP protocol to run on mail server User runs email software that becomes client of POP server to access the contents of the mailbox
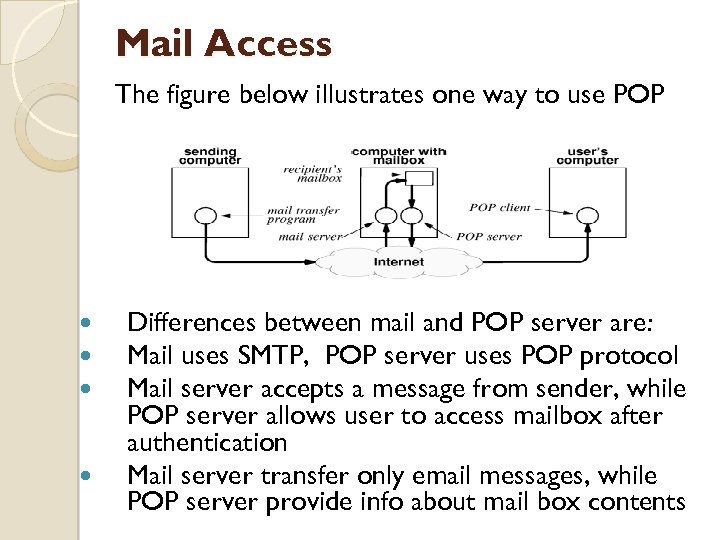 Mail Access The figure below illustrates one way to use POP Differences between mail and POP server are: Mail uses SMTP, POP server uses POP protocol Mail server accepts a message from sender, while POP server allows user to access mailbox after authentication Mail server transfer only email messages, while POP server provide info about mail box contents
Mail Access The figure below illustrates one way to use POP Differences between mail and POP server are: Mail uses SMTP, POP server uses POP protocol Mail server accepts a message from sender, while POP server allows user to access mailbox after authentication Mail server transfer only email messages, while POP server provide info about mail box contents
 Remote Login - TELNET Provide interactive access to computer from remote site Standard protocol is TELNET ICS 632 2003 29
Remote Login - TELNET Provide interactive access to computer from remote site Standard protocol is TELNET ICS 632 2003 29
 TELNET Text-oriented interface User ◦ Invokes client ◦ Specifies remote computer Client ◦ Forms TCP connection to server ◦ Passes keystrokes over connection ◦ Displays output on screen ICS 632 2003 30
TELNET Text-oriented interface User ◦ Invokes client ◦ Specifies remote computer Client ◦ Forms TCP connection to server ◦ Passes keystrokes over connection ◦ Displays output on screen ICS 632 2003 30
 File Transfer - FTP Complete file copy Major protocol is File Transfer Protocol (FTP) ◦ Uses TCP ◦ Supports binary or text transfers ◦ Large set of commands ◦ Until 1995 was major source of packets in Internet ICS 632 2003 31
File Transfer - FTP Complete file copy Major protocol is File Transfer Protocol (FTP) ◦ Uses TCP ◦ Supports binary or text transfers ◦ Large set of commands ◦ Until 1995 was major source of packets in Internet ICS 632 2003 31
 FTP Paradigm Command-line interface User ◦ Forms TCP connection to server (called control connection) ◦ Logs in ◦ Enters commands to list directories, transfer files Server ◦ Established new TCP connection for each transfer ICS 632 2003 32
FTP Paradigm Command-line interface User ◦ Forms TCP connection to server (called control connection) ◦ Logs in ◦ Enters commands to list directories, transfer files Server ◦ Established new TCP connection for each transfer ICS 632 2003 32
 Transfer Modes FTP has two basic transfer modes: one used for text files and the other for all non-text files. Although binary mode produces an exact copy of the bits, the resulting copy may be meaningless because does not convert values to the local representations. ICS 632 2003 33
Transfer Modes FTP has two basic transfer modes: one used for text files and the other for all non-text files. Although binary mode produces an exact copy of the bits, the resulting copy may be meaningless because does not convert values to the local representations. ICS 632 2003 33
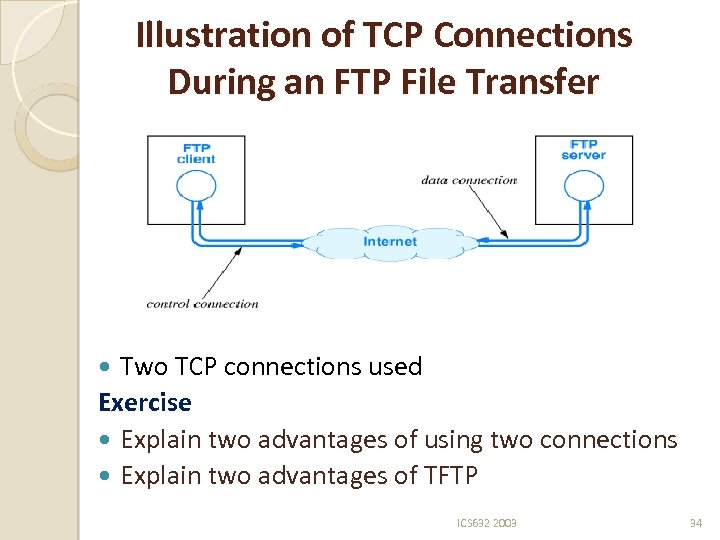 Illustration of TCP Connections During an FTP File Transfer Two TCP connections used Exercise Explain two advantages of using two connections Explain two advantages of TFTP ICS 632 2003 34
Illustration of TCP Connections During an FTP File Transfer Two TCP connections used Exercise Explain two advantages of using two connections Explain two advantages of TFTP ICS 632 2003 34
 TFTP Second file transfer service in TCP/IP: Trivial File Transfer Protocol (TFTP) Uses UDP instead of TCP Only supports file transfer Does not support interaction and does not have large have a large set of commands Does not have authorization; only for files with global access Useful for bootstrapping a hardware device that has no disk for system software ICS 632 2003 35
TFTP Second file transfer service in TCP/IP: Trivial File Transfer Protocol (TFTP) Uses UDP instead of TCP Only supports file transfer Does not support interaction and does not have large have a large set of commands Does not have authorization; only for files with global access Useful for bootstrapping a hardware device that has no disk for system software ICS 632 2003 35


