60d2906841d855253740b3d053f5b1c8.ppt
- Количество слайдов: 111
 International Telecommunication Union ITU-T activities in the field of telecommunications security Sami Trabulsi ITU/TSB sami. trabulsi@itu. int Page - IP strategies and IDN issues workshop – Damscus, 16 -18 May 2006
International Telecommunication Union ITU-T activities in the field of telecommunications security Sami Trabulsi ITU/TSB sami. trabulsi@itu. int Page - IP strategies and IDN issues workshop – Damscus, 16 -18 May 2006
 Introduction o ICT security is high in the agenda of many national, regional or international organizations • Computing and networking are an important part of daily life • Increase in widely reported security incidents • Need for effective security measures to protect computer and telecom systems of governments, industry, commerce, critical infrastructure and consumers IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 2
Introduction o ICT security is high in the agenda of many national, regional or international organizations • Computing and networking are an important part of daily life • Increase in widely reported security incidents • Need for effective security measures to protect computer and telecom systems of governments, industry, commerce, critical infrastructure and consumers IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 2
 Security services/dimensions Security services or dimensions X. 800 X. 805 Access control provides protection against unauthorized use of resources accessible protects against unauthorized use of network resources. Ensures that only authorized personnel or devices are allowed access to network elements, stored information, information flows, services and applications Authentication provides for the authentication of a communicating peer entity and the source of data serves to confirm the identities of communicating entities. Ensures validity of the claimed identities of the entities participating in communication (person, device, service or application) and provides assurance that an entity is not attempting a masquerade or unauthorized replay of a previous communication Nonrepudiation with proof of origin or with proof of delivery provides means for preventing an individual or entity from denying having performed a particular action related to data by making available proof of various network-related actions (such as proof of obligation, intent, or commitment; proof of data origin, proof of ownership, proof of resource use). It ensures the availability of evidence that can be presented to a third party and used to prove that some kind of event or action has taken place Data confidentiality provides for the protection of data from unauthorized disclosure protects data from unauthorized disclosure. Ensures that the data content cannot be understood by unauthorized entities. Encryption, access control lists, and file permissions are methods often used to provide data confidentiality IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 3
Security services/dimensions Security services or dimensions X. 800 X. 805 Access control provides protection against unauthorized use of resources accessible protects against unauthorized use of network resources. Ensures that only authorized personnel or devices are allowed access to network elements, stored information, information flows, services and applications Authentication provides for the authentication of a communicating peer entity and the source of data serves to confirm the identities of communicating entities. Ensures validity of the claimed identities of the entities participating in communication (person, device, service or application) and provides assurance that an entity is not attempting a masquerade or unauthorized replay of a previous communication Nonrepudiation with proof of origin or with proof of delivery provides means for preventing an individual or entity from denying having performed a particular action related to data by making available proof of various network-related actions (such as proof of obligation, intent, or commitment; proof of data origin, proof of ownership, proof of resource use). It ensures the availability of evidence that can be presented to a third party and used to prove that some kind of event or action has taken place Data confidentiality provides for the protection of data from unauthorized disclosure protects data from unauthorized disclosure. Ensures that the data content cannot be understood by unauthorized entities. Encryption, access control lists, and file permissions are methods often used to provide data confidentiality IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 3
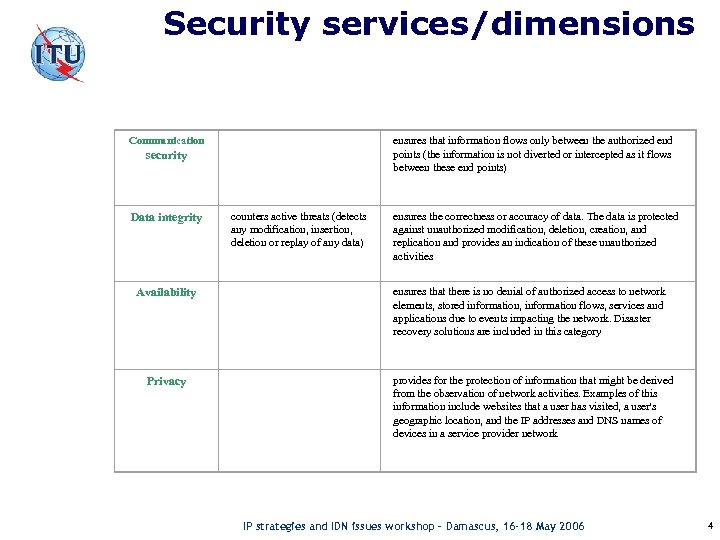 Security services/dimensions Communication ensures that information flows only between the authorized end points (the information is not diverted or intercepted as it flows between these end points) counters active threats (detects any modification, insertion, deletion or replay of any data) ensures the correctness or accuracy of data. The data is protected against unauthorized modification, deletion, creation, and replication and provides an indication of these unauthorized activities Availability ensures that there is no denial of authorized access to network elements, stored information, information flows, services and applications due to events impacting the network. Disaster recovery solutions are included in this category Privacy provides for the protection of information that might be derived from the observation of network activities. Examples of this information include websites that a user has visited, a user's geographic location, and the IP addresses and DNS names of devices in a service provider network security Data integrity IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 4
Security services/dimensions Communication ensures that information flows only between the authorized end points (the information is not diverted or intercepted as it flows between these end points) counters active threats (detects any modification, insertion, deletion or replay of any data) ensures the correctness or accuracy of data. The data is protected against unauthorized modification, deletion, creation, and replication and provides an indication of these unauthorized activities Availability ensures that there is no denial of authorized access to network elements, stored information, information flows, services and applications due to events impacting the network. Disaster recovery solutions are included in this category Privacy provides for the protection of information that might be derived from the observation of network activities. Examples of this information include websites that a user has visited, a user's geographic location, and the IP addresses and DNS names of devices in a service provider network security Data integrity IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 4
 Background o A key concern for ICT security relates to systems vulnerabilities o Statistics on computer-security vulnerabilities Vulnerabilities reported 1995 -1999 1995 1996 1997 1998 1999 171 345 311 262 417 Year 2000 2001 2002 2003 2004 1 Q, 2005 Vulnerabilities Carnegie Mellon Uni. CERT CC Year 1, 090 2, 437 4, 129 3, 784 3, 780 1, 220 Vulnerabilities 2000 -2005 Total vulnerabilities reported (1995 -1 Q, 2005): 17, 946 Symantec Corp. This computer-security company cataloges 11, 000 vulnerabilities in 20, 000 technologies, affecting 2, 000 vendors in the last decade IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 5
Background o A key concern for ICT security relates to systems vulnerabilities o Statistics on computer-security vulnerabilities Vulnerabilities reported 1995 -1999 1995 1996 1997 1998 1999 171 345 311 262 417 Year 2000 2001 2002 2003 2004 1 Q, 2005 Vulnerabilities Carnegie Mellon Uni. CERT CC Year 1, 090 2, 437 4, 129 3, 784 3, 780 1, 220 Vulnerabilities 2000 -2005 Total vulnerabilities reported (1995 -1 Q, 2005): 17, 946 Symantec Corp. This computer-security company cataloges 11, 000 vulnerabilities in 20, 000 technologies, affecting 2, 000 vendors in the last decade IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 5
 Background o An increasing number of countries now have data protection legislation requiring compliance with demonstrated data protection standards o Some SDOs have security in their work programme as a continuous item (e. g. , ITU, ISO, IETF) o Or, other SDOs may be established to respond to a specific issue (e. g. , • e-business: OASIS • SPAM: MAAWG) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 6
Background o An increasing number of countries now have data protection legislation requiring compliance with demonstrated data protection standards o Some SDOs have security in their work programme as a continuous item (e. g. , ITU, ISO, IETF) o Or, other SDOs may be established to respond to a specific issue (e. g. , • e-business: OASIS • SPAM: MAAWG) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 6
 High Level Security Drivers o ITU Plenipotentiary Conference (PP- 02) ØIntensify efforts on security o World Telecommunications Standardization Assembly (WTSA-04) ØSecurity robustness of protocols ØCountering spam o World Summit on the Information Society (WSIS-05) ØCyber security IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 7
High Level Security Drivers o ITU Plenipotentiary Conference (PP- 02) ØIntensify efforts on security o World Telecommunications Standardization Assembly (WTSA-04) ØSecurity robustness of protocols ØCountering spam o World Summit on the Information Society (WSIS-05) ØCyber security IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 7
 ITU Plenipotentiary Conference 2002 Resolution PLEN/2 - Strengthening the role of ITU in information and communication network security resolves 1 to review ITU's current activities in information and communication network security; 2 to intensify work within existing ITU study groups in order to: a) reach a common understanding on the importance of information and communication network security by studying standards on technologies, products and services with a view to developing recommendations, as appropriate; b) seek ways to enhance exchange of technical information in the field of information and communication network security, and promote cooperation among appropriate entities; c) report on the result of these studies annually to the ITU Council. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 8
ITU Plenipotentiary Conference 2002 Resolution PLEN/2 - Strengthening the role of ITU in information and communication network security resolves 1 to review ITU's current activities in information and communication network security; 2 to intensify work within existing ITU study groups in order to: a) reach a common understanding on the importance of information and communication network security by studying standards on technologies, products and services with a view to developing recommendations, as appropriate; b) seek ways to enhance exchange of technical information in the field of information and communication network security, and promote cooperation among appropriate entities; c) report on the result of these studies annually to the ITU Council. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 8
 ITU-T World Telecommunications Standardization Assembly (WTSA) o Resolution 50, Cyberscecurity - Evaluate existing and evolving new Recommendations with respect to their robustness of design and potential for exploitation by malicious parties - Raise awareness of the need to defend against the threat of cyber attack o Resolution 51, Combating spam - Report on international initiatives for countering spam - Member States to take steps within their national legal frameworks to ensure measures are taken to combat spam o Resolution 52, Countering spam by technical means - Study Groups, in cooperation with other relevant groups, to develop as a matter of urgency technical Recommendations on countering spam IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 9
ITU-T World Telecommunications Standardization Assembly (WTSA) o Resolution 50, Cyberscecurity - Evaluate existing and evolving new Recommendations with respect to their robustness of design and potential for exploitation by malicious parties - Raise awareness of the need to defend against the threat of cyber attack o Resolution 51, Combating spam - Report on international initiatives for countering spam - Member States to take steps within their national legal frameworks to ensure measures are taken to combat spam o Resolution 52, Countering spam by technical means - Study Groups, in cooperation with other relevant groups, to develop as a matter of urgency technical Recommendations on countering spam IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 9
 ITU-T Study Groups ITU-T work is divided up between Study Groups (SGs). o SG 2: Operational aspects of service provision, networks and performance o SG 4: Telecommunication management o SG 5: Protection against electromagnetic environment effects o SG 6 Outside Plant and related indoor installations o SG 9 Integrated broadband cable networks and television and sound transmission o SG 11 Signaling requirements and protocols o SG 12 Performance and quality of service o SG 13 Next Generation Networks o SG 15: Optical and other transport networks o SG 16: Multimedia services, systems and terminals o SG 17: Security, languages and telecommunication software o SG 19: Mobile Telecommunications Networks SG 17 is the Lead Study Group on security. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 10
ITU-T Study Groups ITU-T work is divided up between Study Groups (SGs). o SG 2: Operational aspects of service provision, networks and performance o SG 4: Telecommunication management o SG 5: Protection against electromagnetic environment effects o SG 6 Outside Plant and related indoor installations o SG 9 Integrated broadband cable networks and television and sound transmission o SG 11 Signaling requirements and protocols o SG 12 Performance and quality of service o SG 13 Next Generation Networks o SG 15: Optical and other transport networks o SG 16: Multimedia services, systems and terminals o SG 17: Security, languages and telecommunication software o SG 19: Mobile Telecommunications Networks SG 17 is the Lead Study Group on security. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 10
 Overview of ITU-T Security Standardization Collaboration is key factor IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 11
Overview of ITU-T Security Standardization Collaboration is key factor IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 11
 Study Group 17: Security, languages and telecommunication software o SG 17 is the Lead Study Group on telecommunication security - It is responsible for coordination of security across all Study Groups. o Subdivided into three Working Parties (WPs) • WP 1 - Open systems technologies; • WP 2 - Telecommunications security; • WP 3 - Languages and telecommunications software o Most (but not all) security Questions are in WP 2 o Summaries of all draft Recommendations under development in SG 17 are available on the SG 17 web page at www. itu. int/itu-t/studygroups/com 17 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 12
Study Group 17: Security, languages and telecommunication software o SG 17 is the Lead Study Group on telecommunication security - It is responsible for coordination of security across all Study Groups. o Subdivided into three Working Parties (WPs) • WP 1 - Open systems technologies; • WP 2 - Telecommunications security; • WP 3 - Languages and telecommunications software o Most (but not all) security Questions are in WP 2 o Summaries of all draft Recommendations under development in SG 17 are available on the SG 17 web page at www. itu. int/itu-t/studygroups/com 17 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 12
 Current SG 17 security-related Questions Working Party 1: o 1/17 End-to-end Multicast Communications with Qo. S Managing Facility o 2/17 Directory services, Directory systems, and publickey/attribute certificates o 3/17 Open Systems Interconnection (OSI) o 16/17 International Domain Names (IDN) Working Party 2: o 4/17 Communications Systems Security Project o 5/17 Security Architecture and Framework o 6/17 Cyber Security o 7/17 Security Management o 8/17 Telebiometrics o 9/17 Secure Communication services o 17/17 Countering spam by technical means IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 13
Current SG 17 security-related Questions Working Party 1: o 1/17 End-to-end Multicast Communications with Qo. S Managing Facility o 2/17 Directory services, Directory systems, and publickey/attribute certificates o 3/17 Open Systems Interconnection (OSI) o 16/17 International Domain Names (IDN) Working Party 2: o 4/17 Communications Systems Security Project o 5/17 Security Architecture and Framework o 6/17 Cyber Security o 7/17 Security Management o 8/17 Telebiometrics o 9/17 Secure Communication services o 17/17 Countering spam by technical means IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 13
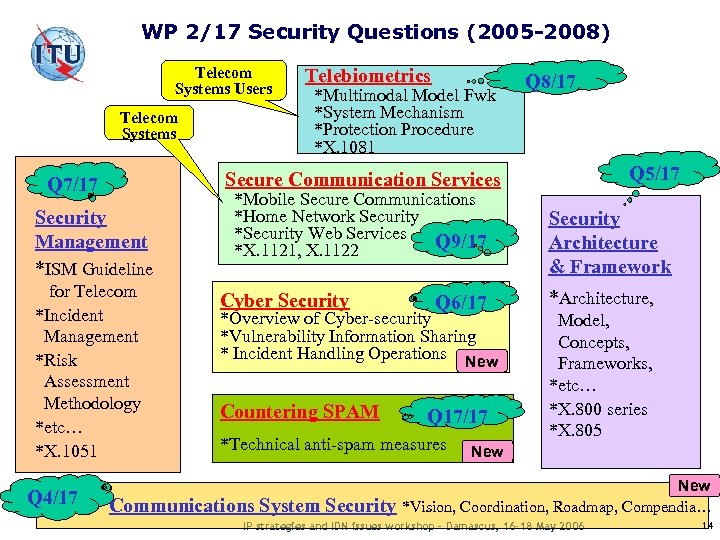 WP 2/17 Security Questions (2005 -2008) Telecom Systems Users Telecom Systems Q 7/17 Security Management *ISM Guideline for Telecom *Incident Management *Risk Assessment Methodology *etc… *X. 1051 Telebiometrics *Multimodal Model Fwk *System Mechanism *Protection Procedure *X. 1081 Q 8/17 Q 5/17 Secure Communication Services *Mobile Secure Communications *Home Network Security *Security Web Services Q 9/17 *X. 1121, X. 1122 Cyber Security Q 6/17 *Overview of Cyber-security *Vulnerability Information Sharing * Incident Handling Operations New Countering SPAM Q 17/17 *Technical anti-spam measures Q 4/17 Communications System Security Architecture & Framework *Architecture, Model, Concepts, Frameworks, *etc… *X. 800 series *X. 805 New *Vision, Coordination, Roadmap, Compendia… IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 14
WP 2/17 Security Questions (2005 -2008) Telecom Systems Users Telecom Systems Q 7/17 Security Management *ISM Guideline for Telecom *Incident Management *Risk Assessment Methodology *etc… *X. 1051 Telebiometrics *Multimodal Model Fwk *System Mechanism *Protection Procedure *X. 1081 Q 8/17 Q 5/17 Secure Communication Services *Mobile Secure Communications *Home Network Security *Security Web Services Q 9/17 *X. 1121, X. 1122 Cyber Security Q 6/17 *Overview of Cyber-security *Vulnerability Information Sharing * Incident Handling Operations New Countering SPAM Q 17/17 *Technical anti-spam measures Q 4/17 Communications System Security Architecture & Framework *Architecture, Model, Concepts, Frameworks, *etc… *X. 800 series *X. 805 New *Vision, Coordination, Roadmap, Compendia… IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 14
 ITU-T SG 17 Question 4 Communications Systems Security Project o Security Workshop o ICT Security Roadmap o Focus Group on Security Baseline For Network Operators IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 15
ITU-T SG 17 Question 4 Communications Systems Security Project o Security Workshop o ICT Security Roadmap o Focus Group on Security Baseline For Network Operators IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 15
 New Horizons for Security Standardization Workshop o o Workshop held in Geneva 3 -4 October 2005 Hosted by ITU-T SG 17 as part of security coordination responsibility ISO/IEC JTC 1 played an important role in planning the program and in providing speakers/panelists. Speakers, panelists, chairs from: • • • ITU-T ISO/IEC IETF Consortia – OASIS, 3 GPP Regional SDOs – ATIS, ETSI, RAIS IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 16
New Horizons for Security Standardization Workshop o o Workshop held in Geneva 3 -4 October 2005 Hosted by ITU-T SG 17 as part of security coordination responsibility ISO/IEC JTC 1 played an important role in planning the program and in providing speakers/panelists. Speakers, panelists, chairs from: • • • ITU-T ISO/IEC IETF Consortia – OASIS, 3 GPP Regional SDOs – ATIS, ETSI, RAIS IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 16
 Workshop Objectives o Provide an overview of key international security standardization activities; o Seek to find out from stakeholders (e. g. , network operators, system developers, manufacturers and end-users) their primary security concerns and issues (including possible issues of adoption or implementation of standards); o Try to determine which issues are amenable to a standards-based solution and how the SDOs can most effectively play a role in helping address these issues; o Identify which SDOs are already working on these issues or are best equipped to do so; and o Consider how SDOs can collaborate to improve the timeliness and effectiveness of security standards and avoid duplication of effort. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 17
Workshop Objectives o Provide an overview of key international security standardization activities; o Seek to find out from stakeholders (e. g. , network operators, system developers, manufacturers and end-users) their primary security concerns and issues (including possible issues of adoption or implementation of standards); o Try to determine which issues are amenable to a standards-based solution and how the SDOs can most effectively play a role in helping address these issues; o Identify which SDOs are already working on these issues or are best equipped to do so; and o Consider how SDOs can collaborate to improve the timeliness and effectiveness of security standards and avoid duplication of effort. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 17
 Workshop Results o Excellent discussions, feedback and suggestions o Documented in detail in the Workshop report o Results are reported under following topics: • What are the crucial problems in ICT security standardization? • Meta issues and need for a global framework; • Standards Requirements and Priorities; • Liaison and information sharing; • User issues; • Technology and threat issues; • Focus for future standardization work; • Process issues; • Follow-on issues o The report is available on-line at: • www. itu. int/ITU-T/worksem/security/200510/index. html IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 18
Workshop Results o Excellent discussions, feedback and suggestions o Documented in detail in the Workshop report o Results are reported under following topics: • What are the crucial problems in ICT security standardization? • Meta issues and need for a global framework; • Standards Requirements and Priorities; • Liaison and information sharing; • User issues; • Technology and threat issues; • Focus for future standardization work; • Process issues; • Follow-on issues o The report is available on-line at: • www. itu. int/ITU-T/worksem/security/200510/index. html IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 18
 ICT Security Standards Roadmap (an SG 17 work-in-progress) o Publicly available under Special Projects and Issues at: • www. itu. int/ITU-T/studygroups/com 17/index o Part 1 contains information about organizations working on ICT security standards o Part 2 is database of existing security standards o Part 3 will be a list of standards in development o Part 4 will identify future needs and proposed new standards IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 19
ICT Security Standards Roadmap (an SG 17 work-in-progress) o Publicly available under Special Projects and Issues at: • www. itu. int/ITU-T/studygroups/com 17/index o Part 1 contains information about organizations working on ICT security standards o Part 2 is database of existing security standards o Part 3 will be a list of standards in development o Part 4 will identify future needs and proposed new standards IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 19
 Roadmap access o Part 2 includes ITU-T, ISO/IEC JTC 1 and IETF standards. It will be expanded to include other standards (e. g. regional and consortia specifications). o It will also be converted to a Database format to allow searching and to allow organizations to manage their own data o We invite you to use the Roadmap, provide feedback and help us develop it to meet your needs IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 20
Roadmap access o Part 2 includes ITU-T, ISO/IEC JTC 1 and IETF standards. It will be expanded to include other standards (e. g. regional and consortia specifications). o It will also be converted to a Database format to allow searching and to allow organizations to manage their own data o We invite you to use the Roadmap, provide feedback and help us develop it to meet your needs IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 20
 Other Q. 4/17 projects o Security in Telecommunications and Information Technology – an overview of existing ITU-T Recommendations for secure telecommunications (Security Manual, v 3) www. itu. int/ITU-T/publications/index. html • Security compendium: • catalogue of approved ITU-T Recommendations related to telecommunication security • extract of ITU-T approved security definitions • listing of ITU-T security related Questions www. itu. int/ITU-T/studygroups/com 17/tel-security. html o We are in the process of establishing a Security Experts Network (SEN) to maintain on-going dialogue on key issues of security standardization. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 21
Other Q. 4/17 projects o Security in Telecommunications and Information Technology – an overview of existing ITU-T Recommendations for secure telecommunications (Security Manual, v 3) www. itu. int/ITU-T/publications/index. html • Security compendium: • catalogue of approved ITU-T Recommendations related to telecommunication security • extract of ITU-T approved security definitions • listing of ITU-T security related Questions www. itu. int/ITU-T/studygroups/com 17/tel-security. html o We are in the process of establishing a Security Experts Network (SEN) to maintain on-going dialogue on key issues of security standardization. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 21
 Focus Group: Security Baseline for Network Operators o Established October 2005 by SG 17 o Objectives: • Define a security baseline against which network operators can assess their network and information security posture in terms of what security standards are available, which of these standards should be used to meet particular requirements, when they should be used, and how they should be applied • Describe a network operator’s readiness and ability to collaborate with other entities (operators, users and law enforcement authorities) to counteract information security threats • Provide meaningful criteria that can be used by network operators against which other network operators can be assessed, if required. o Next Step • Survey network operators by means of a questionnaire • 2 meetings in preparation for 2006 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 22
Focus Group: Security Baseline for Network Operators o Established October 2005 by SG 17 o Objectives: • Define a security baseline against which network operators can assess their network and information security posture in terms of what security standards are available, which of these standards should be used to meet particular requirements, when they should be used, and how they should be applied • Describe a network operator’s readiness and ability to collaborate with other entities (operators, users and law enforcement authorities) to counteract information security threats • Provide meaningful criteria that can be used by network operators against which other network operators can be assessed, if required. o Next Step • Survey network operators by means of a questionnaire • 2 meetings in preparation for 2006 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 22
 ITU-T SG 17 Question 5 Security Architecture and Framework o Brief description of Q. 5 o Milestones o Draft Recommendations under development IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 23
ITU-T SG 17 Question 5 Security Architecture and Framework o Brief description of Q. 5 o Milestones o Draft Recommendations under development IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 23
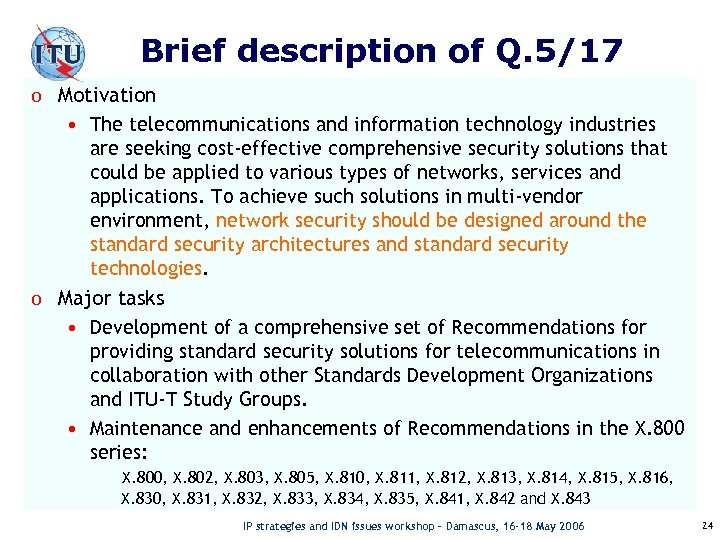 Brief description of Q. 5/17 o Motivation • The telecommunications and information technology industries are seeking cost-effective comprehensive security solutions that could be applied to various types of networks, services and applications. To achieve such solutions in multi-vendor environment, network security should be designed around the standard security architectures and standard security technologies. o Major tasks • Development of a comprehensive set of Recommendations for providing standard security solutions for telecommunications in collaboration with other Standards Development Organizations and ITU-T Study Groups. • Maintenance and enhancements of Recommendations in the X. 800 series: X. 800, X. 802, X. 803, X. 805, X. 810, X. 811, X. 812, X. 813, X. 814, X. 815, X. 816, X. 830, X. 831, X. 832, X. 833, X. 834, X. 835, X. 841, X. 842 and X. 843 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 24
Brief description of Q. 5/17 o Motivation • The telecommunications and information technology industries are seeking cost-effective comprehensive security solutions that could be applied to various types of networks, services and applications. To achieve such solutions in multi-vendor environment, network security should be designed around the standard security architectures and standard security technologies. o Major tasks • Development of a comprehensive set of Recommendations for providing standard security solutions for telecommunications in collaboration with other Standards Development Organizations and ITU-T Study Groups. • Maintenance and enhancements of Recommendations in the X. 800 series: X. 800, X. 802, X. 803, X. 805, X. 810, X. 811, X. 812, X. 813, X. 814, X. 815, X. 816, X. 830, X. 831, X. 832, X. 833, X. 834, X. 835, X. 841, X. 842 and X. 843 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 24
 Q. 5/17 Milestones o ITU-T Recommendation X. 805, Security Architecture for Systems Providing End-to-end Communications, was published in 2003. o ISO Standard 18028 -2, Network security architecture, was developed in collaboration between ITU-T Q. 5/17 and ISO/IEC JTC 1 SC 27 WG 1. The Standard is technically aligned with X. 805. It was published in 2006. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 25
Q. 5/17 Milestones o ITU-T Recommendation X. 805, Security Architecture for Systems Providing End-to-end Communications, was published in 2003. o ISO Standard 18028 -2, Network security architecture, was developed in collaboration between ITU-T Q. 5/17 and ISO/IEC JTC 1 SC 27 WG 1. The Standard is technically aligned with X. 805. It was published in 2006. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 25
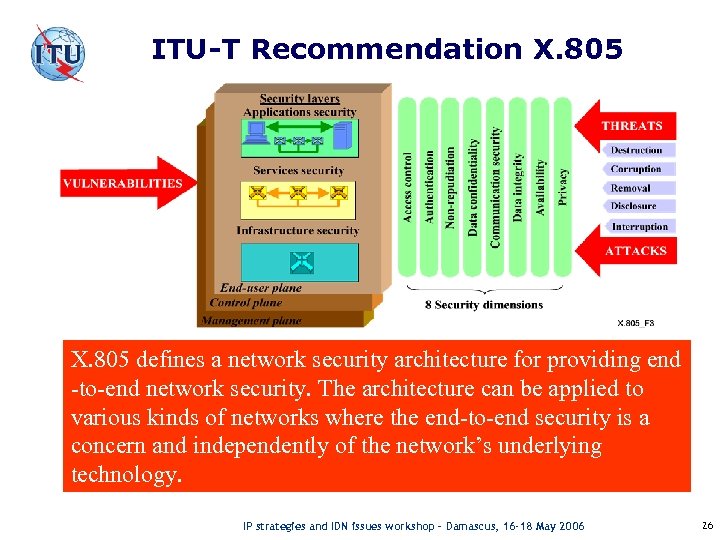 ITU-T Recommendation X. 805 defines a network security architecture for providing end -to-end network security. The architecture can be applied to various kinds of networks where the end-to-end security is a concern and independently of the network’s underlying technology. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 26
ITU-T Recommendation X. 805 defines a network security architecture for providing end -to-end network security. The architecture can be applied to various kinds of networks where the end-to-end security is a concern and independently of the network’s underlying technology. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 26
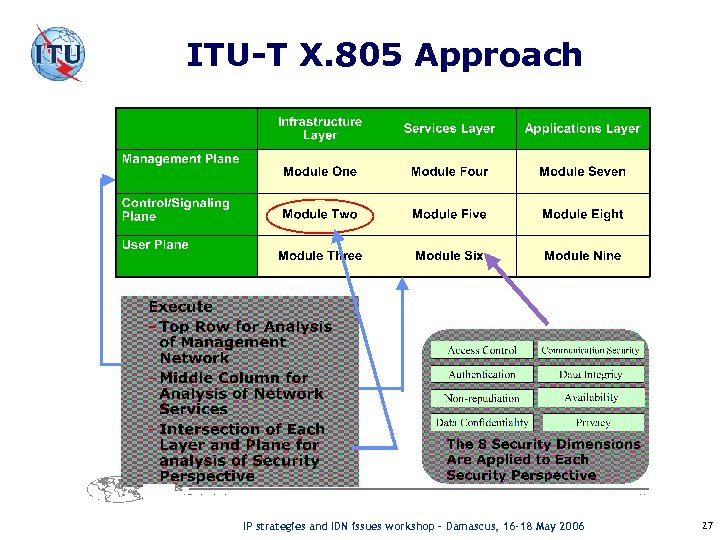 ITU-T X. 805 Approach X. 805 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 27
ITU-T X. 805 Approach X. 805 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 27
 ITU-T X. 805 Provides A Holistic Approach: o Comprehensive, End-to-End Network View of Security o Applies to Any Network Technology • Wireless, Wireline, Optical Networks • Voice, Data, Video, Converged Networks o Applies to Any Scope of Network Function • Service Provider Networks • Enterprise Networks • Government Networks • Management/Operations, Administrative Networks • Data Center Networks o Can Map to Existing Standards o Completes the Missing Piece of the Security Puzzle of what to do next X. 805 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 28
ITU-T X. 805 Provides A Holistic Approach: o Comprehensive, End-to-End Network View of Security o Applies to Any Network Technology • Wireless, Wireline, Optical Networks • Voice, Data, Video, Converged Networks o Applies to Any Scope of Network Function • Service Provider Networks • Enterprise Networks • Government Networks • Management/Operations, Administrative Networks • Data Center Networks o Can Map to Existing Standards o Completes the Missing Piece of the Security Puzzle of what to do next X. 805 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 28
 E. 409: Incident organization and security incident handling o analyze, structure and suggest a method for establishing an incident management organization within a telecommunications organization, where the flow and structure of incident handling is dealt with. o flow and structure of incident handling helps in classifying a problem as: • • event incident security incident crisis o incident flow handling also covers the critical first decisions to be made IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 29
E. 409: Incident organization and security incident handling o analyze, structure and suggest a method for establishing an incident management organization within a telecommunications organization, where the flow and structure of incident handling is dealt with. o flow and structure of incident handling helps in classifying a problem as: • • event incident security incident crisis o incident flow handling also covers the critical first decisions to be made IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 29
 Pyramid of events in E. 409 o Are considered as Information and Communications Networks (ICN) Security Incident any real or suspected adverse event in relation to the security of ICN. This includes: • • • intrusion into ICN computer systems via the network; occurrence of computer viruses; probes for vulnerabilities via the network into a range of computer systems; PABX call leak-through; and any other undesired events arising from unauthorized internal or external actions, including denial of service attacks, disasters and other emergency situations, etc. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 30
Pyramid of events in E. 409 o Are considered as Information and Communications Networks (ICN) Security Incident any real or suspected adverse event in relation to the security of ICN. This includes: • • • intrusion into ICN computer systems via the network; occurrence of computer viruses; probes for vulnerabilities via the network into a range of computer systems; PABX call leak-through; and any other undesired events arising from unauthorized internal or external actions, including denial of service attacks, disasters and other emergency situations, etc. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 30
 E. 409 suggested reactions o telecommunication organizations should create computer security incident response teams (CSIRT), as the first step, declare their use of taxonomy in order to avoid misunderstandings. • Collaboration is much easier when using the same "language". o organizations should use the term Incident and ICN Security Incident (any undesired, unauthorized event: • computer intrusion • denial of service attack • virus attack), define their own subdivisions with regard to severity, depending on motivation, experience and available knowledgeable resources. When an effective virus fighting team has been created, viruses may not be considered as ICN security incidents but rather as incidents IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 31
E. 409 suggested reactions o telecommunication organizations should create computer security incident response teams (CSIRT), as the first step, declare their use of taxonomy in order to avoid misunderstandings. • Collaboration is much easier when using the same "language". o organizations should use the term Incident and ICN Security Incident (any undesired, unauthorized event: • computer intrusion • denial of service attack • virus attack), define their own subdivisions with regard to severity, depending on motivation, experience and available knowledgeable resources. When an effective virus fighting team has been created, viruses may not be considered as ICN security incidents but rather as incidents IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 31
 Q. 5/17 Draft Recommendations 1/2 o Applications and further development of major concepts of ITU-T Recommendation X. 805 • X. 805+, Division of the security features between the network and the users. This Recommendation specifies division of security features between the networks and users. It provides guidance on applying concepts of the X. 805 architecture to securing service provider’s, application provider’s networks and the end user’s equipment. • X. 805 nsa, Network security certification based on ITUT Recommendation X. 805. This Recommendation describes the methodology, processes and controls required for network security certification based on ITU-T Recommendation X. 805, Security Architecture for Systems Providing End-to-End Communications. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 32
Q. 5/17 Draft Recommendations 1/2 o Applications and further development of major concepts of ITU-T Recommendation X. 805 • X. 805+, Division of the security features between the network and the users. This Recommendation specifies division of security features between the networks and users. It provides guidance on applying concepts of the X. 805 architecture to securing service provider’s, application provider’s networks and the end user’s equipment. • X. 805 nsa, Network security certification based on ITUT Recommendation X. 805. This Recommendation describes the methodology, processes and controls required for network security certification based on ITU-T Recommendation X. 805, Security Architecture for Systems Providing End-to-End Communications. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 32
 Q. 5/17 Draft Recommendations 2/2 o Standardization in support of Authentication Security Dimension (defined in X. 805) • X. pak, Password-authenticated Key Exchange Protocol (PAK). This Recommendation specifies a password-based protocol for authentication and key exchange, which ensures mutual authentication of both parties in the act of establishing a symmetric cryptographic key via Diffie-Hellman exchange. • X. ngn-akm, Framework for authentication and key management for link layer security of NGN. This Recommendation establishes a framework for authentication and key management for securing the link layer of NGN. It also provides guidance on selection of the EAP methods for NGN. o Standardization of network security policies • X. spn, Framework for creation, storage, distribution, and enforcement of security policies for networks. This Recommendation establishes security policies that are to drive security controls of a system or service. It also specifies a framework for creation, storage, distribution, and enforcement of policies for network security that can be applied to various environmental conditions and network devices. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 33
Q. 5/17 Draft Recommendations 2/2 o Standardization in support of Authentication Security Dimension (defined in X. 805) • X. pak, Password-authenticated Key Exchange Protocol (PAK). This Recommendation specifies a password-based protocol for authentication and key exchange, which ensures mutual authentication of both parties in the act of establishing a symmetric cryptographic key via Diffie-Hellman exchange. • X. ngn-akm, Framework for authentication and key management for link layer security of NGN. This Recommendation establishes a framework for authentication and key management for securing the link layer of NGN. It also provides guidance on selection of the EAP methods for NGN. o Standardization of network security policies • X. spn, Framework for creation, storage, distribution, and enforcement of security policies for networks. This Recommendation establishes security policies that are to drive security controls of a system or service. It also specifies a framework for creation, storage, distribution, and enforcement of policies for network security that can be applied to various environmental conditions and network devices. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 33
 ITU-T SG 17 Question 6 Cyber Security o o o Definition Motivation Objectives Scope Current area of focus Draft Recommendations under development IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 34
ITU-T SG 17 Question 6 Cyber Security o o o Definition Motivation Objectives Scope Current area of focus Draft Recommendations under development IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 34
 Cybersecurity working definition (SG 17 – SG 2 liaison) o As a working definition within the ITU-T, Cybersecurity means the collection of tools, policies, guidelines, risk management approaches, actions, training, best practices, assurance and technologies that may be used to protect organization and user’s assets on the cyber environment. Organization and user’s assets include connected computing devices, computing users, applications/services, Telecommunications systems, multimedia communication, and the totality of transmitted and/or stored information in the cyber environment. o It encompasses the attainment and maintenance of the security properties of the organization and user’s assets against relevant security risks in the cyber environment. The security properties include one or more of the following: • Availability • Integrity, which may include authenticity and non-repudiation • Confidentiality IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 35
Cybersecurity working definition (SG 17 – SG 2 liaison) o As a working definition within the ITU-T, Cybersecurity means the collection of tools, policies, guidelines, risk management approaches, actions, training, best practices, assurance and technologies that may be used to protect organization and user’s assets on the cyber environment. Organization and user’s assets include connected computing devices, computing users, applications/services, Telecommunications systems, multimedia communication, and the totality of transmitted and/or stored information in the cyber environment. o It encompasses the attainment and maintenance of the security properties of the organization and user’s assets against relevant security risks in the cyber environment. The security properties include one or more of the following: • Availability • Integrity, which may include authenticity and non-repudiation • Confidentiality IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 35
 Q. 6/17 Motivation o Network connectivity and ubiquitous access is central to today’s IT o o o systems Wide spread access and loose coupling of interconnected IT systems is a primary source of widespread vulnerability Threats such as: denial of service, theft of financial and personal data, network failures and disruption of voice and data telecommunications are on the rise Network protocols in use today were developed in an environment of trust. Most new investments and development is dedicated to building new functionality and not on securing that functionality An understanding of cybersecurity is needed in order to build a foundation of knowledge that can aid in securing the networks of tomorrow IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 36
Q. 6/17 Motivation o Network connectivity and ubiquitous access is central to today’s IT o o o systems Wide spread access and loose coupling of interconnected IT systems is a primary source of widespread vulnerability Threats such as: denial of service, theft of financial and personal data, network failures and disruption of voice and data telecommunications are on the rise Network protocols in use today were developed in an environment of trust. Most new investments and development is dedicated to building new functionality and not on securing that functionality An understanding of cybersecurity is needed in order to build a foundation of knowledge that can aid in securing the networks of tomorrow IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 36
 Q. 6/17 Objectives o Perform actions in accordance with Lead Study Group (LSG) o o o responsibility with the focus on cybersecurity Work with Q. 1 of SG 2 on a definition of Cybersecurity Identify and develop standards required for addressing the challenges in cybersecurity, within the scope of Q. 6/17 Provide assistance to other ITU-T Study Groups in applying relevant cybersecurity Recommendations for specific security solutions. Review project-oriented security solutions for consistency. Maintain and update existing Recommendations within the scope of Q. 6/17. Coordinate security activities with other ITU-T SGs, ISO/IEC JTC 1 eg. SC 6, SC 27 and SC 37), and consortia as appropriate. Provide awareness on new security technologies related to cybersecurity IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 37
Q. 6/17 Objectives o Perform actions in accordance with Lead Study Group (LSG) o o o responsibility with the focus on cybersecurity Work with Q. 1 of SG 2 on a definition of Cybersecurity Identify and develop standards required for addressing the challenges in cybersecurity, within the scope of Q. 6/17 Provide assistance to other ITU-T Study Groups in applying relevant cybersecurity Recommendations for specific security solutions. Review project-oriented security solutions for consistency. Maintain and update existing Recommendations within the scope of Q. 6/17. Coordinate security activities with other ITU-T SGs, ISO/IEC JTC 1 eg. SC 6, SC 27 and SC 37), and consortia as appropriate. Provide awareness on new security technologies related to cybersecurity IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 37
 Q. 6/17 Scope o Definition of Cybersecurity o Security of Telecommunications Network Infrastructure o Security Knowledge and Awareness of Telecom Personnel and Users o Security Requirements for Design of New Communications Protocol and Systems o Communications relating to Cybersecurity o Security Processes – Life-cycle Processes relating to Incident and Vulnerability o Security of Identity in Telecommunication Network o Legal/Policy Considerations IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 38
Q. 6/17 Scope o Definition of Cybersecurity o Security of Telecommunications Network Infrastructure o Security Knowledge and Awareness of Telecom Personnel and Users o Security Requirements for Design of New Communications Protocol and Systems o Communications relating to Cybersecurity o Security Processes – Life-cycle Processes relating to Incident and Vulnerability o Security of Identity in Telecommunication Network o Legal/Policy Considerations IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 38
 Q. 6/17 Current area of focus o Work with SG 2 on the definition and requirements of o o o cybersecurity. Collaborate with Q 5, 7, 9, 17/17 and SG 2 in order to achieve better understanding of various aspects of network security. Collaborate with IETF, OASIS, ISO/IEC JTC 1, W 3 C, APEC-TEL and other standardization bodies on cybersecurity. Work on framework for secure network operations to address how telecommunications network providers secure their infrastructure and maintain secure operations. Work on Recommendation for standardization of vulnerability data definition. Study new cybersecurity issues – How should ISPs deal with botnets, evaluating the output of appropriate bodies when available. Call for contributions for the outstanding questions identified in the revised scope. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 39
Q. 6/17 Current area of focus o Work with SG 2 on the definition and requirements of o o o cybersecurity. Collaborate with Q 5, 7, 9, 17/17 and SG 2 in order to achieve better understanding of various aspects of network security. Collaborate with IETF, OASIS, ISO/IEC JTC 1, W 3 C, APEC-TEL and other standardization bodies on cybersecurity. Work on framework for secure network operations to address how telecommunications network providers secure their infrastructure and maintain secure operations. Work on Recommendation for standardization of vulnerability data definition. Study new cybersecurity issues – How should ISPs deal with botnets, evaluating the output of appropriate bodies when available. Call for contributions for the outstanding questions identified in the revised scope. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 39
 Q. 6/17 Draft Recommendations 1/2 Overview of Cybersecurity (X. cso) 1. • • This Recommendation provides a definition for Cybersecurity. The Recommendation provides a taxonomy of security threats from an operator point of view. Cybersecurity vulnerabilities and threats are presented and discussed at various network layers. Various Cybersecurity technologies that are available to remedy the threats include: Routers, Firewalls, Antivirus protection, Intrusion detection systems, Intrusion protection systems, Secure computing, Audit and Monitoring. Network protection principles such as defence in depth, access and identity management with application to Cybersecurity are discussed. Risk Management strategies and techniques are discussed including the value of training and education in protecting the network. A discussion of Cybersecurity Standards, Cybersecurity implementation issues and certification are presented. A vendor-neutral framework for automatic checking of the presence of vulnerabilities information update (X. vds) 2. • This Recommendation provides a framework of automatic notification on vulnerability information. The key point of the framework is that it is a vendor-neutral framework. Once users register their software, updates on the vulnerabilities and patches of the registered software will automatically be made available to the users. Upon notification, users can then apply IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 40
Q. 6/17 Draft Recommendations 1/2 Overview of Cybersecurity (X. cso) 1. • • This Recommendation provides a definition for Cybersecurity. The Recommendation provides a taxonomy of security threats from an operator point of view. Cybersecurity vulnerabilities and threats are presented and discussed at various network layers. Various Cybersecurity technologies that are available to remedy the threats include: Routers, Firewalls, Antivirus protection, Intrusion detection systems, Intrusion protection systems, Secure computing, Audit and Monitoring. Network protection principles such as defence in depth, access and identity management with application to Cybersecurity are discussed. Risk Management strategies and techniques are discussed including the value of training and education in protecting the network. A discussion of Cybersecurity Standards, Cybersecurity implementation issues and certification are presented. A vendor-neutral framework for automatic checking of the presence of vulnerabilities information update (X. vds) 2. • This Recommendation provides a framework of automatic notification on vulnerability information. The key point of the framework is that it is a vendor-neutral framework. Once users register their software, updates on the vulnerabilities and patches of the registered software will automatically be made available to the users. Upon notification, users can then apply IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 40
 Q. 6/17 Draft Recommendations 2/2 Guidelines for Internet Service Providers and End-users for Addressing the Risk of Spyware and Deceptive Software (X. sds) 3. • This Recommendation provides guidelines for Internet Service Providers (ISP) and end-users for addressing the risks of spyware and deceptive software. The Recommendation promotes best practices around principles of clear notices, and users’ consents and controls for ISP web hosting services. The Recommendation also promotes best practices to end-users on the Internet to secure their computing devices and information against the risks of spyware and deceptive software Guidelines on Cybersecurity Vulnerability Life-cycle Management(X. cvlm) 4. • The Recommendation provides a framework for the provision of monitoring, discovering, responding and post-analysis of vulnerabilities. Service providers can use this Recommendation to complement their existing Information Security Management System process in the aspect of regular vulnerability assessment, vulnerability management, incident handling and incident management. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 41
Q. 6/17 Draft Recommendations 2/2 Guidelines for Internet Service Providers and End-users for Addressing the Risk of Spyware and Deceptive Software (X. sds) 3. • This Recommendation provides guidelines for Internet Service Providers (ISP) and end-users for addressing the risks of spyware and deceptive software. The Recommendation promotes best practices around principles of clear notices, and users’ consents and controls for ISP web hosting services. The Recommendation also promotes best practices to end-users on the Internet to secure their computing devices and information against the risks of spyware and deceptive software Guidelines on Cybersecurity Vulnerability Life-cycle Management(X. cvlm) 4. • The Recommendation provides a framework for the provision of monitoring, discovering, responding and post-analysis of vulnerabilities. Service providers can use this Recommendation to complement their existing Information Security Management System process in the aspect of regular vulnerability assessment, vulnerability management, incident handling and incident management. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 41
 ITU-T SG 17 Question 7 Security Management o Tasks o Recommendations planned o Revised X. 1051 o Approach for revised X. 1051 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 42
ITU-T SG 17 Question 7 Security Management o Tasks o Recommendations planned o Revised X. 1051 o Approach for revised X. 1051 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 42
 Q. 7/17 Tasks o Information Security Management Guidelines for telecommunications (Existing X. 1051, Information security management system – Requirements for telecommunications (ISMS-T) ) ・Maintain and revise Recommendation X. 1051, “Information Security Management Guidelines for telecommunications based on ISO/IEC 27002”. ・Jointly develop a guideline of information security management with ISO/IEC JTC 1/SC 27. o Risk Management Methodology ・Study and develop a methodology of risk management for telecommunications in line with Recommendation X. 1051. ・Produce and consent a new ITU-T Recommendation for risk management methodology. o Incident Management ・Study and develop a handling and response procedure on security incidents for the telecommunications in line with Recommendation X. 1051. ・Produce and consent a new ITU-T Recommendation for incident management methodology and procedures. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 43
Q. 7/17 Tasks o Information Security Management Guidelines for telecommunications (Existing X. 1051, Information security management system – Requirements for telecommunications (ISMS-T) ) ・Maintain and revise Recommendation X. 1051, “Information Security Management Guidelines for telecommunications based on ISO/IEC 27002”. ・Jointly develop a guideline of information security management with ISO/IEC JTC 1/SC 27. o Risk Management Methodology ・Study and develop a methodology of risk management for telecommunications in line with Recommendation X. 1051. ・Produce and consent a new ITU-T Recommendation for risk management methodology. o Incident Management ・Study and develop a handling and response procedure on security incidents for the telecommunications in line with Recommendation X. 1051. ・Produce and consent a new ITU-T Recommendation for incident management methodology and procedures. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 43
 Recommendations planned in Q. 7/17 (Security Management) X. 1050: To be proposed X. 1051: In revision process Information Security Management Guidelines for Telecommunications based on ISO/IEC 27002 X. 1052: To be proposed X. 1053: To be proposed (Implementation Guide for Telecoms) X. 1054: To be proposed (Measurements and metrics for Telecommunications) X. 1055 : In the first stage of development Risk Management Guidelines for Telecommunications X. 1056: In the first stage of development Security Incident Management Guidelines for Telecommunications X. 1057: To be proposed (Identity Management for Telecoms) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 44
Recommendations planned in Q. 7/17 (Security Management) X. 1050: To be proposed X. 1051: In revision process Information Security Management Guidelines for Telecommunications based on ISO/IEC 27002 X. 1052: To be proposed X. 1053: To be proposed (Implementation Guide for Telecoms) X. 1054: To be proposed (Measurements and metrics for Telecommunications) X. 1055 : In the first stage of development Risk Management Guidelines for Telecommunications X. 1056: In the first stage of development Security Incident Management Guidelines for Telecommunications X. 1057: To be proposed (Identity Management for Telecoms) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 44
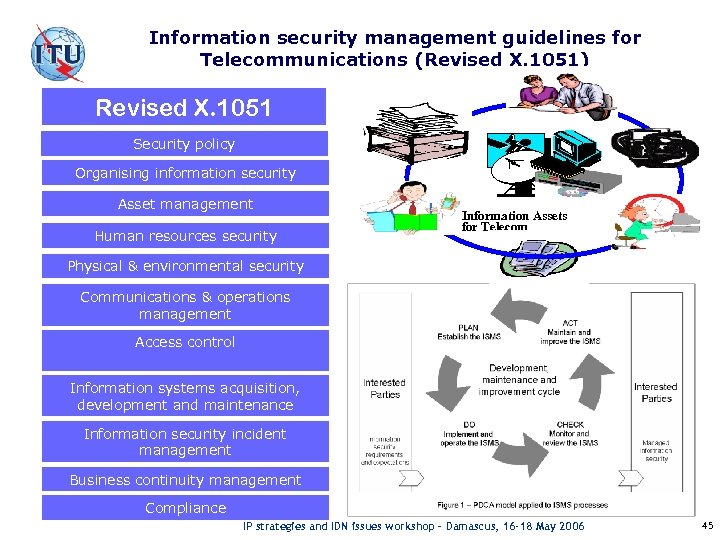 Information security management guidelines for Telecommunications (Revised X. 1051) Revised X. 1051 Security policy Organising information security Asset management Human resources security Information Assets for Telecom Physical & environmental security Communications & operations management Access control Information systems acquisition, development and maintenance Information security incident management Business continuity management Compliance IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 45
Information security management guidelines for Telecommunications (Revised X. 1051) Revised X. 1051 Security policy Organising information security Asset management Human resources security Information Assets for Telecom Physical & environmental security Communications & operations management Access control Information systems acquisition, development and maintenance Information security incident management Business continuity management Compliance IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 45
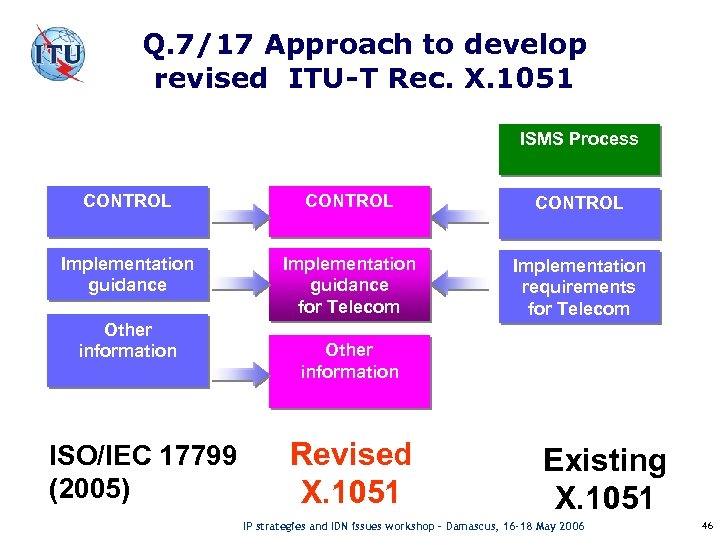 Q. 7/17 Approach to develop revised ITU-T Rec. X. 1051 ISMS Process CONTROL Implementation guidance for Telecom Implementation requirements for Telecom Other information ISO/IEC 17799 (2005) Other information Revised X. 1051 Existing X. 1051 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 46
Q. 7/17 Approach to develop revised ITU-T Rec. X. 1051 ISMS Process CONTROL Implementation guidance for Telecom Implementation requirements for Telecom Other information ISO/IEC 17799 (2005) Other information Revised X. 1051 Existing X. 1051 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 46
 ITU-T SG 17 Question 8 Telebiometrics o Objectives o Study areas on Biometric Processes o X. 1081 and draft Recommendations under development IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 47
ITU-T SG 17 Question 8 Telebiometrics o Objectives o Study areas on Biometric Processes o X. 1081 and draft Recommendations under development IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 47
 Q. 8/17 Objectives 1)To define telebiometric multimodal model framework 2)To specify biometric authentication mechanism in open network 3)To provide protection procedures and countermeasures for telebiometric systems IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 48
Q. 8/17 Objectives 1)To define telebiometric multimodal model framework 2)To specify biometric authentication mechanism in open network 3)To provide protection procedures and countermeasures for telebiometric systems IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 48
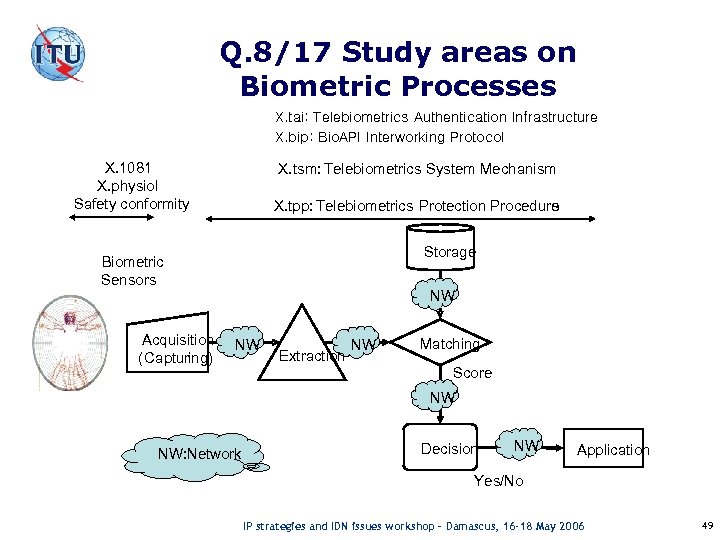 Q. 8/17 Study areas on Biometric Processes X. tai: Telebiometrics Authentication Infrastructure X. bip: Bio. API Interworking Protocol X. 1081 X. physiol Safety conformity X. tsm: Telebiometrics System Mechanism X. tpp: Telebiometrics Protection Procedure s Storage Biometric Sensors Acquisition ( Capturing) NW NW Extraction NW Matching Score NW NW: Network Decision NW Application Yes/No IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 49
Q. 8/17 Study areas on Biometric Processes X. tai: Telebiometrics Authentication Infrastructure X. bip: Bio. API Interworking Protocol X. 1081 X. physiol Safety conformity X. tsm: Telebiometrics System Mechanism X. tpp: Telebiometrics Protection Procedure s Storage Biometric Sensors Acquisition ( Capturing) NW NW Extraction NW Matching Score NW NW: Network Decision NW Application Yes/No IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 49
 Q. 8/17 Recommendations 1/4 - X. 1081 – The telebiometric multimodal model framework – A framework for the specification of security and safety aspects of telebiometrics This Recommendation defines a telebiometric multimodal model that can be used as a framework for identifying and specifying aspects of telebiometrics, and for classifying biometric technologies used for identification (security aspects). - X. physiol – Telebiometrics related to human physiology This Recommendation gives names and symbols for quantities and units concerned with emissions from the human body that can be detected by a sensor, and with effects on the human body produced by the telebiometric devices in his environments. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 50
Q. 8/17 Recommendations 1/4 - X. 1081 – The telebiometric multimodal model framework – A framework for the specification of security and safety aspects of telebiometrics This Recommendation defines a telebiometric multimodal model that can be used as a framework for identifying and specifying aspects of telebiometrics, and for classifying biometric technologies used for identification (security aspects). - X. physiol – Telebiometrics related to human physiology This Recommendation gives names and symbols for quantities and units concerned with emissions from the human body that can be detected by a sensor, and with effects on the human body produced by the telebiometric devices in his environments. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 50
 Q. 8/17 Recommendations 2/4 - X. tsm-1 – General biometric authentication protocol and profile on telecommunication system This Recommendation defines communication mechanism and protocols of biometric authentication for unspecified end‑users and service providers on open network. - X. tsm-2 – Profile of telecomunication device for Telebiometrics System Mechanism (TSM) This Recommendation defines the requirements, security profiles of client terminals for biometric authentication over the open network. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 51
Q. 8/17 Recommendations 2/4 - X. tsm-1 – General biometric authentication protocol and profile on telecommunication system This Recommendation defines communication mechanism and protocols of biometric authentication for unspecified end‑users and service providers on open network. - X. tsm-2 – Profile of telecomunication device for Telebiometrics System Mechanism (TSM) This Recommendation defines the requirements, security profiles of client terminals for biometric authentication over the open network. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 51
 Q. 8/17 Recommendations 3/4 - X. tai – Telebiometrics authentication infrastructure This Recommendation specifies a framework to implement biometric identity authentication with certificate issuance, management, usage and revocation. - X. bip – Bio. API interworking protocol This Recommendation is common text of ITU-T and ISO/IEC JTC 1 SC 37. It specifies the syntax, semantics, and encodings of a set of messages ("BIP messages") that enable Bio. API-conforming application in telebiometric systems. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 52
Q. 8/17 Recommendations 3/4 - X. tai – Telebiometrics authentication infrastructure This Recommendation specifies a framework to implement biometric identity authentication with certificate issuance, management, usage and revocation. - X. bip – Bio. API interworking protocol This Recommendation is common text of ITU-T and ISO/IEC JTC 1 SC 37. It specifies the syntax, semantics, and encodings of a set of messages ("BIP messages") that enable Bio. API-conforming application in telebiometric systems. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 52
 Q. 8/17 Recommendations 4/4 - X. tpp-1 – A guideline of technical and managerial countermeasures for biometric data security This Recommendation defines weakness and threats in operating telebiometric systems and proposes a general guideline of security countermeasures from both technical and managerial perspectives. - X. tpp-2 – A guideline for secure and efficient transmission of multi-modal biometric data This Recommendation defines threat characteristics of multi-modal biometric system, and provides cryptographic methods and network protocols for transmission of multi-modal biometric data. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 53
Q. 8/17 Recommendations 4/4 - X. tpp-1 – A guideline of technical and managerial countermeasures for biometric data security This Recommendation defines weakness and threats in operating telebiometric systems and proposes a general guideline of security countermeasures from both technical and managerial perspectives. - X. tpp-2 – A guideline for secure and efficient transmission of multi-modal biometric data This Recommendation defines threat characteristics of multi-modal biometric system, and provides cryptographic methods and network protocols for transmission of multi-modal biometric data. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 53
 ITU-T SG 17 Question 9 Secure Communication Services o Focus o Position of each topic o Mobile security o Home network security o Web services security o Secure applications services IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 54
ITU-T SG 17 Question 9 Secure Communication Services o Focus o Position of each topic o Mobile security o Home network security o Web services security o Secure applications services IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 54
 Q. 9/17 Focus o Develop a set of standards of secure application services, including • Mobile security Under study • Home network security Under study • Web Services security Under study • Secure application services Under study • Privacy protection for RFID and multimedia content and digital Identity management To be studied IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 55
Q. 9/17 Focus o Develop a set of standards of secure application services, including • Mobile security Under study • Home network security Under study • Web Services security Under study • Secure application services Under study • Privacy protection for RFID and multimedia content and digital Identity management To be studied IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 55
 Position of each topic Web Services security Application Server Mobile Terminal Mobile Network Mobile security Open Network Home network security Secure application services IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 56
Position of each topic Web Services security Application Server Mobile Terminal Mobile Network Mobile security Open Network Home network security Secure application services IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 56
 Q. 9/17 - Mobile Security o X. 1121, Framework of security technologies for mobile end-to-end data communications – Approved 2004 o X. 1122, Guideline for implementing secure mobile systems based on PKI – Approved 2004 o X. msec-3, General security value added service (policy) for mobile data communication • Develops general security service as value added service for secure mobile end-to-end data communication. o X. msec-4, Authentication architecture in mobile end-to-end data communication • Constructs generic authentication architecture for mobile data communication between mobile users and application servers. o X. crs, Correlative reacting system in mobile network • Develops the generic architecture of a correlative reactive system to protect the mobile terminal against virus, worms, trojan-horses or other network attacks to both the mobile network and its mobile users. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 57
Q. 9/17 - Mobile Security o X. 1121, Framework of security technologies for mobile end-to-end data communications – Approved 2004 o X. 1122, Guideline for implementing secure mobile systems based on PKI – Approved 2004 o X. msec-3, General security value added service (policy) for mobile data communication • Develops general security service as value added service for secure mobile end-to-end data communication. o X. msec-4, Authentication architecture in mobile end-to-end data communication • Constructs generic authentication architecture for mobile data communication between mobile users and application servers. o X. crs, Correlative reacting system in mobile network • Develops the generic architecture of a correlative reactive system to protect the mobile terminal against virus, worms, trojan-horses or other network attacks to both the mobile network and its mobile users. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 57
 Q. 9/17 - Home network security o X. homesec-1, Framework for security technologies for home network • Framework of security technologies for home network • Define security threats and security requirements, security function requirements for each entity in the network, and possible implementation layer o X. homesec-2, Certificate profile for the device in the home network • Device certificate profile for the home network • Develops framework of home network device certificate. o X. homesec-3, User authentication mechanisms for home network service • User authentication mechanisms for home network service. • Provides the user authentication mechanism in the home network, which enables various authentication means such as password, certificate, biometrics and so on. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 58
Q. 9/17 - Home network security o X. homesec-1, Framework for security technologies for home network • Framework of security technologies for home network • Define security threats and security requirements, security function requirements for each entity in the network, and possible implementation layer o X. homesec-2, Certificate profile for the device in the home network • Device certificate profile for the home network • Develops framework of home network device certificate. o X. homesec-3, User authentication mechanisms for home network service • User authentication mechanisms for home network service. • Provides the user authentication mechanism in the home network, which enables various authentication means such as password, certificate, biometrics and so on. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 58
 Q. 9/17 - Web Services security o X. websec-1, Security Assertion Markup Language (SAML) • Security assertion markup language • Adoption of OASIS SAML v 2. 0 into ITU-T Recommendation X. 1141 - Consented April 2006 • Define XML-based framework for exchanging security information. • The security information expressed in the form of assertions about subjects, where a subject is an entity (either human or computer) that has an identity in some security domain. o X. websec-2, e. Xtensible Access Control Markup Language (XACML) • e. Xtensible Access Control Markup Language • Adoption of OASIS XACML v 2. 0 into ITU-T Recommendation X. 1142 - Consented April 2006 • Provides an XML vocabulary for expressing access control policies and the syntax of the language and the rules for evaluating policies. o X. websec-3, Security architecture for message security in mobile Web Services • Develops a guideline on message security architecture and service scenarios for securing messages for mobile Web Services. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 59
Q. 9/17 - Web Services security o X. websec-1, Security Assertion Markup Language (SAML) • Security assertion markup language • Adoption of OASIS SAML v 2. 0 into ITU-T Recommendation X. 1141 - Consented April 2006 • Define XML-based framework for exchanging security information. • The security information expressed in the form of assertions about subjects, where a subject is an entity (either human or computer) that has an identity in some security domain. o X. websec-2, e. Xtensible Access Control Markup Language (XACML) • e. Xtensible Access Control Markup Language • Adoption of OASIS XACML v 2. 0 into ITU-T Recommendation X. 1142 - Consented April 2006 • Provides an XML vocabulary for expressing access control policies and the syntax of the language and the rules for evaluating policies. o X. websec-3, Security architecture for message security in mobile Web Services • Develops a guideline on message security architecture and service scenarios for securing messages for mobile Web Services. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 59
 Q. 9/17 - Secure applications services o X. sap-1, Guideline on strong password authentication protocols • Guideline on secure password-based authentication protocol with key exchange. • Define a set of requirements for password-based protocol with key exchange and a selection guideline by setting up criteria that can be used in choosing an optimum authentication protocol for each application. o X. sap-2, Secure communication using TTP service • Secure end-to-end data communication techniques using TTP services • Specifies secure end-to-end data communication techniques using TTP services that are services defined in X. 842 or other services. o X. p 2 p-1, Anonymous authentication architecture in community communication • Requirements of security for peer-to-peer and peer-to-multi peer communications • Investigates threat analysis for P 2 P and P 2 MP communication services and describes security requirements for secure P 2 P and P 2 MP communication services. o X. p 2 p-2, Security architecture and protocols for peer to peer network • Describes the security techniques and protocols in the P 2 P environment. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 60
Q. 9/17 - Secure applications services o X. sap-1, Guideline on strong password authentication protocols • Guideline on secure password-based authentication protocol with key exchange. • Define a set of requirements for password-based protocol with key exchange and a selection guideline by setting up criteria that can be used in choosing an optimum authentication protocol for each application. o X. sap-2, Secure communication using TTP service • Secure end-to-end data communication techniques using TTP services • Specifies secure end-to-end data communication techniques using TTP services that are services defined in X. 842 or other services. o X. p 2 p-1, Anonymous authentication architecture in community communication • Requirements of security for peer-to-peer and peer-to-multi peer communications • Investigates threat analysis for P 2 P and P 2 MP communication services and describes security requirements for secure P 2 P and P 2 MP communication services. o X. p 2 p-2, Security architecture and protocols for peer to peer network • Describes the security techniques and protocols in the P 2 P environment. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 60
 ITU-T SG 17 Question 17 Countering spam by technical means o Objectives o Set of Recommendations IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 61
ITU-T SG 17 Question 17 Countering spam by technical means o Objectives o Set of Recommendations IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 61
 Q. 17/17 Objectives o The aim of this Question is to develop a set of Recommendations on countering spam by technical means for ITU-T, taking into account the need for collaboration with ITU-T other Study Groups and cooperation with other SDOs. The Question focuses particularly on technical requirement, frameworks and new technologies for countering spam. Guidelines on countering spam by technical means are also studied. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 62
Q. 17/17 Objectives o The aim of this Question is to develop a set of Recommendations on countering spam by technical means for ITU-T, taking into account the need for collaboration with ITU-T other Study Groups and cooperation with other SDOs. The Question focuses particularly on technical requirement, frameworks and new technologies for countering spam. Guidelines on countering spam by technical means are also studied. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 62
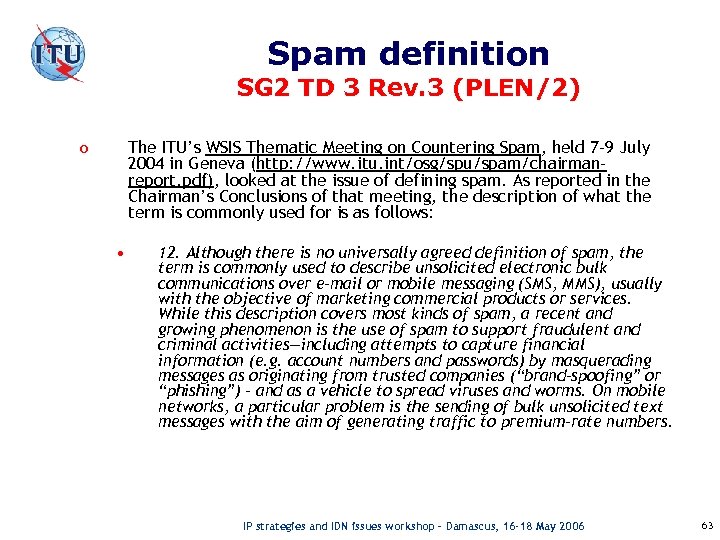 Spam definition SG 2 TD 3 Rev. 3 (PLEN/2) The ITU’s WSIS Thematic Meeting on Countering Spam, held 7 -9 July 2004 in Geneva (http: //www. itu. int/osg/spu/spam/chairmanreport. pdf), looked at the issue of defining spam. As reported in the Chairman’s Conclusions of that meeting, the description of what the term is commonly used for is as follows: o • 12. Although there is no universally agreed definition of spam, the term is commonly used to describe unsolicited electronic bulk communications over e-mail or mobile messaging (SMS, MMS), usually with the objective of marketing commercial products or services. While this description covers most kinds of spam, a recent and growing phenomenon is the use of spam to support fraudulent and criminal activities—including attempts to capture financial information (e. g. account numbers and passwords) by masquerading messages as originating from trusted companies (“brand-spoofing” or “phishing”) – and as a vehicle to spread viruses and worms. On mobile networks, a particular problem is the sending of bulk unsolicited text messages with the aim of generating traffic to premium-rate numbers. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 63
Spam definition SG 2 TD 3 Rev. 3 (PLEN/2) The ITU’s WSIS Thematic Meeting on Countering Spam, held 7 -9 July 2004 in Geneva (http: //www. itu. int/osg/spu/spam/chairmanreport. pdf), looked at the issue of defining spam. As reported in the Chairman’s Conclusions of that meeting, the description of what the term is commonly used for is as follows: o • 12. Although there is no universally agreed definition of spam, the term is commonly used to describe unsolicited electronic bulk communications over e-mail or mobile messaging (SMS, MMS), usually with the objective of marketing commercial products or services. While this description covers most kinds of spam, a recent and growing phenomenon is the use of spam to support fraudulent and criminal activities—including attempts to capture financial information (e. g. account numbers and passwords) by masquerading messages as originating from trusted companies (“brand-spoofing” or “phishing”) – and as a vehicle to spread viruses and worms. On mobile networks, a particular problem is the sending of bulk unsolicited text messages with the aim of generating traffic to premium-rate numbers. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 63
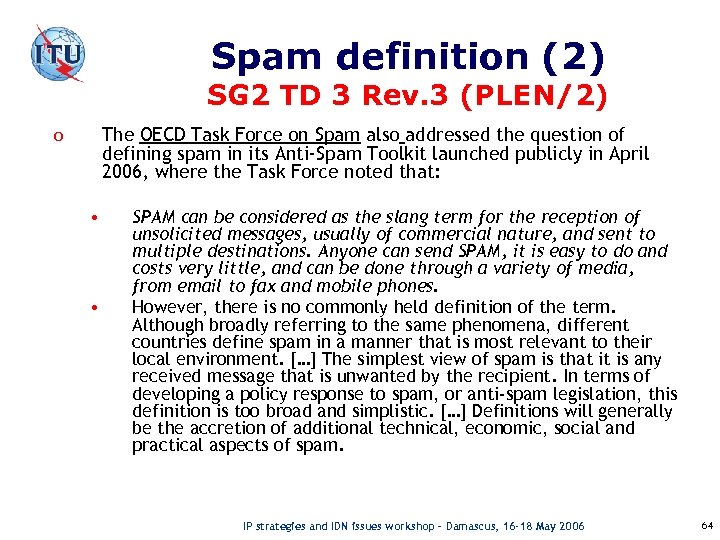 Spam definition (2) SG 2 TD 3 Rev. 3 (PLEN/2) The OECD Task Force on Spam also addressed the question of defining spam in its Anti-Spam Toolkit launched publicly in April 2006, where the Task Force noted that: o • • SPAM can be considered as the slang term for the reception of unsolicited messages, usually of commercial nature, and sent to multiple destinations. Anyone can send SPAM, it is easy to do and costs very little, and can be done through a variety of media, from email to fax and mobile phones. However, there is no commonly held definition of the term. Although broadly referring to the same phenomena, different countries define spam in a manner that is most relevant to their local environment. […] The simplest view of spam is that it is any received message that is unwanted by the recipient. In terms of developing a policy response to spam, or anti-spam legislation, this definition is too broad and simplistic. […] Definitions will generally be the accretion of additional technical, economic, social and practical aspects of spam. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 64
Spam definition (2) SG 2 TD 3 Rev. 3 (PLEN/2) The OECD Task Force on Spam also addressed the question of defining spam in its Anti-Spam Toolkit launched publicly in April 2006, where the Task Force noted that: o • • SPAM can be considered as the slang term for the reception of unsolicited messages, usually of commercial nature, and sent to multiple destinations. Anyone can send SPAM, it is easy to do and costs very little, and can be done through a variety of media, from email to fax and mobile phones. However, there is no commonly held definition of the term. Although broadly referring to the same phenomena, different countries define spam in a manner that is most relevant to their local environment. […] The simplest view of spam is that it is any received message that is unwanted by the recipient. In terms of developing a policy response to spam, or anti-spam legislation, this definition is too broad and simplistic. […] Definitions will generally be the accretion of additional technical, economic, social and practical aspects of spam. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 64
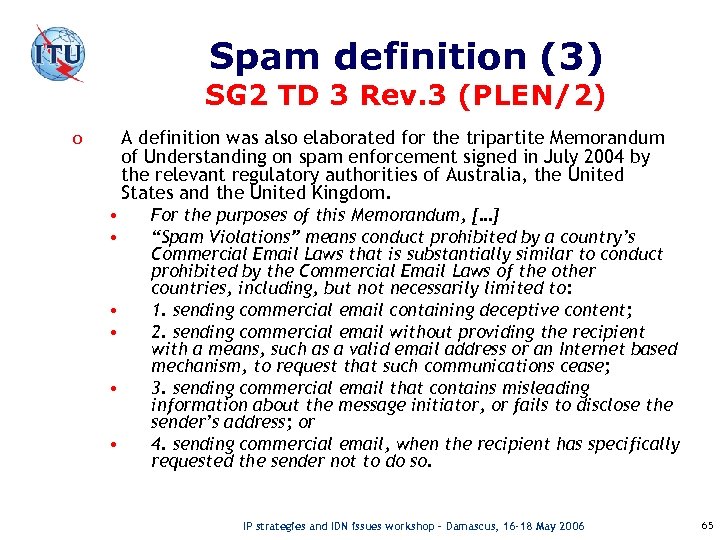 Spam definition (3) SG 2 TD 3 Rev. 3 (PLEN/2) A definition was also elaborated for the tripartite Memorandum of Understanding on spam enforcement signed in July 2004 by the relevant regulatory authorities of Australia, the United States and the United Kingdom. o • • • For the purposes of this Memorandum, […] “Spam Violations” means conduct prohibited by a country’s Commercial Email Laws that is substantially similar to conduct prohibited by the Commercial Email Laws of the other countries, including, but not necessarily limited to: 1. sending commercial email containing deceptive content; 2. sending commercial email without providing the recipient with a means, such as a valid email address or an Internet based mechanism, to request that such communications cease; 3. sending commercial email that contains misleading information about the message initiator, or fails to disclose the sender’s address; or 4. sending commercial email, when the recipient has specifically requested the sender not to do so. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 65
Spam definition (3) SG 2 TD 3 Rev. 3 (PLEN/2) A definition was also elaborated for the tripartite Memorandum of Understanding on spam enforcement signed in July 2004 by the relevant regulatory authorities of Australia, the United States and the United Kingdom. o • • • For the purposes of this Memorandum, […] “Spam Violations” means conduct prohibited by a country’s Commercial Email Laws that is substantially similar to conduct prohibited by the Commercial Email Laws of the other countries, including, but not necessarily limited to: 1. sending commercial email containing deceptive content; 2. sending commercial email without providing the recipient with a means, such as a valid email address or an Internet based mechanism, to request that such communications cease; 3. sending commercial email that contains misleading information about the message initiator, or fails to disclose the sender’s address; or 4. sending commercial email, when the recipient has specifically requested the sender not to do so. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 65
 Q. 17/17 Set of Recommendations Requirement on countering spam (X. csreq) Draft Technical framework for countering email spam (X. fcs) Draft Framework Recommendations: IP multimedia application area (TBD) Technology Recommendations: Technical means for countering spam (X. tcs) TBD Technical means for countering IP multimedia spam (X. tcs)TBD Overview of countering spam for IP multimedia application (X. ocsip) Draft Guideline on countering email spam (X. gcs) Draft Other SDOs IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 66
Q. 17/17 Set of Recommendations Requirement on countering spam (X. csreq) Draft Technical framework for countering email spam (X. fcs) Draft Framework Recommendations: IP multimedia application area (TBD) Technology Recommendations: Technical means for countering spam (X. tcs) TBD Technical means for countering IP multimedia spam (X. tcs)TBD Overview of countering spam for IP multimedia application (X. ocsip) Draft Guideline on countering email spam (X. gcs) Draft Other SDOs IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 66
 Q. 17/17 Brief Summaries of draft Recommendations under development 1/2 o X. csreq, Requirement on countering spam This Recommendation provides the general characteristics of spam, elicits generic objectives and provides an overview of the technical requirements on countering spam. In addition, this Recommendation provides checklist to evaluate the solution on countering spam. o X. fcs, Technical framework for countering email spam This Recommendation specifies the technical framework for network structure for the countering spam. Functions inside the framework are defined. It also includes the commonsensible characteristics of email spam, the universal rules of judgement and the common methods of countering email spam. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 67
Q. 17/17 Brief Summaries of draft Recommendations under development 1/2 o X. csreq, Requirement on countering spam This Recommendation provides the general characteristics of spam, elicits generic objectives and provides an overview of the technical requirements on countering spam. In addition, this Recommendation provides checklist to evaluate the solution on countering spam. o X. fcs, Technical framework for countering email spam This Recommendation specifies the technical framework for network structure for the countering spam. Functions inside the framework are defined. It also includes the commonsensible characteristics of email spam, the universal rules of judgement and the common methods of countering email spam. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 67
 Q. 17/17 Brief Summaries of draft Recommendations under development 2/2 o X. gcs, Guideline on countering email spam (X. gcs) This Recommendation specifies technical issues on countering email spam. It provides the current technical solutions and related activities from various SDOs and relevant organizations on countering email Spam. It will be used as a basis for further development of technical Recommendations on countering email spam. o X. ocsip, Overview of countering spam for IP multimedia application This Recommendation specifies basic concepts, characteristics, and effects of Spam in IP multimedia applications such as IP Telephony, video on demand, IP TV, instant messaging, multimedia conference, etc. It will provide basis and guideline for developing further technical solutions on countering Spam. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 68
Q. 17/17 Brief Summaries of draft Recommendations under development 2/2 o X. gcs, Guideline on countering email spam (X. gcs) This Recommendation specifies technical issues on countering email spam. It provides the current technical solutions and related activities from various SDOs and relevant organizations on countering email Spam. It will be used as a basis for further development of technical Recommendations on countering email spam. o X. ocsip, Overview of countering spam for IP multimedia application This Recommendation specifies basic concepts, characteristics, and effects of Spam in IP multimedia applications such as IP Telephony, video on demand, IP TV, instant messaging, multimedia conference, etc. It will provide basis and guideline for developing further technical solutions on countering Spam. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 68
 Security Work in other ITU-T Study Groups o SG 4 – Security of Management plane o SG 9 – IPCablecom o SG 13 – NGN security o SG 16 – Multimedia security o SG 19 – Security in IMT-2000 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 69
Security Work in other ITU-T Study Groups o SG 4 – Security of Management plane o SG 9 – IPCablecom o SG 13 – NGN security o SG 16 – Multimedia security o SG 19 – Security in IMT-2000 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 69
 SG 4: Security of the management plane (M. 3016 series) o Approved last year, the M. 3016 series is viewed as a key aspect of NGN Management; it is included • in the NGN Management Roadmap issued by the NGNMFG • In M. 3060 on the Principles of NGN Management o The M. 3016 series consists of 5 parts: • M. 3016. 0: Overview • M. 3016. 1: Requirements • M. 3016. 2: Services • M. 3016. 3: Mechanisms • M. 3016. 4: Profile proforma o The role of M. 3016. 4 is unique in that it provides a template for other SDOs and forums to indicate for their membership what parts of M. 3016 are mandatory or optional IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 70
SG 4: Security of the management plane (M. 3016 series) o Approved last year, the M. 3016 series is viewed as a key aspect of NGN Management; it is included • in the NGN Management Roadmap issued by the NGNMFG • In M. 3060 on the Principles of NGN Management o The M. 3016 series consists of 5 parts: • M. 3016. 0: Overview • M. 3016. 1: Requirements • M. 3016. 2: Services • M. 3016. 3: Mechanisms • M. 3016. 4: Profile proforma o The role of M. 3016. 4 is unique in that it provides a template for other SDOs and forums to indicate for their membership what parts of M. 3016 are mandatory or optional IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 70
 SG 9: IPCablecom Evolution o Enhance cable’s existing IP service environment to accelerate the convergence of voice, video, data, and mobility o Define an application agnostic architecture that allows cable operators to rapidly innovate new services o Provide a suite of Recommendations that define the elements and interfaces needed to facilitate multi-vendor interoperability o Incorporate leading communications technologies from the IETF and 3 GPP IMS IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 71
SG 9: IPCablecom Evolution o Enhance cable’s existing IP service environment to accelerate the convergence of voice, video, data, and mobility o Define an application agnostic architecture that allows cable operators to rapidly innovate new services o Provide a suite of Recommendations that define the elements and interfaces needed to facilitate multi-vendor interoperability o Incorporate leading communications technologies from the IETF and 3 GPP IMS IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 71
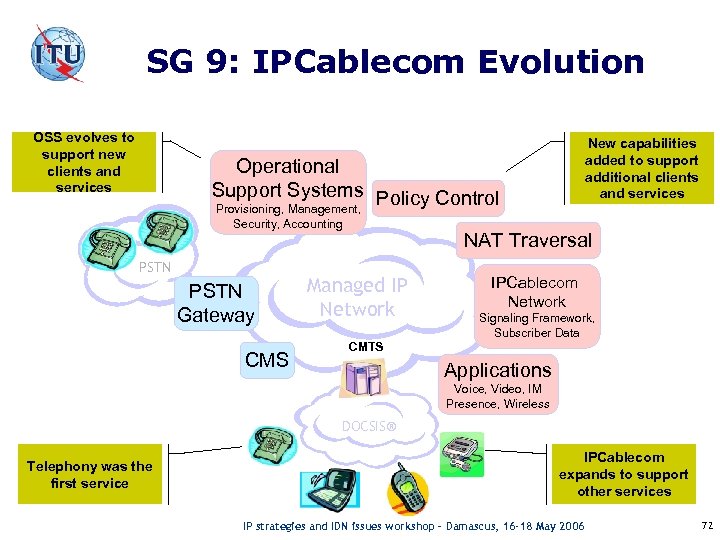 SG 9: IPCablecom Evolution OSS evolves to support new clients and services New capabilities added to support additional clients and services Operational Support Systems Policy Control Provisioning, Management, Security, Accounting PSTN Gateway CMS NAT Traversal Managed IP Network IPCablecom Network Signaling Framework, Subscriber Data CMTS Applications Voice, Video, IM Presence, Wireless DOCSIS® Telephony was the first service IPCablecom expands to support other services IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 72
SG 9: IPCablecom Evolution OSS evolves to support new clients and services New capabilities added to support additional clients and services Operational Support Systems Policy Control Provisioning, Management, Security, Accounting PSTN Gateway CMS NAT Traversal Managed IP Network IPCablecom Network Signaling Framework, Subscriber Data CMTS Applications Voice, Video, IM Presence, Wireless DOCSIS® Telephony was the first service IPCablecom expands to support other services IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 72
 SG 9: Targeted Applications o Enhanced Cable Voice and Video IP Telephony • Support for new media and client types (e. g. , video telephony, soft clients) • Call treatment based on presence, device capability, identity • Maintain support for cable telephony features enabled by current IPCablecom Recommendations o Fixed-mobile Convergence over Cable • Support for dual mode cellular/Wi. Fi handsets over DOCSIS • Call handover between IPCablecom Vo. IP networks and cellular networks • Integrated features and call control between cellular and Vo. IP platforms o Cable Cross-Platform Features • Cross platform notification, messaging (e. g. , Caller-ID on TV) • Third-party call control features, such as ‘Click to dial’ IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 73
SG 9: Targeted Applications o Enhanced Cable Voice and Video IP Telephony • Support for new media and client types (e. g. , video telephony, soft clients) • Call treatment based on presence, device capability, identity • Maintain support for cable telephony features enabled by current IPCablecom Recommendations o Fixed-mobile Convergence over Cable • Support for dual mode cellular/Wi. Fi handsets over DOCSIS • Call handover between IPCablecom Vo. IP networks and cellular networks • Integrated features and call control between cellular and Vo. IP platforms o Cable Cross-Platform Features • Cross platform notification, messaging (e. g. , Caller-ID on TV) • Third-party call control features, such as ‘Click to dial’ IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 73
 SG 9: Design Approach o Incorporate new IP communication technologies • Focus on the Session Initiation Protocol (SIP) and supporting protocols • Leverage the 3 GPP IMS as a service delivery platform o Develop a modular and extensible architecture that allows new services to be added without impacting the core IPCablecom infrastructure o Ensure backward compatibility with existing IPCablecom Recommendations o Support a wide variety of client devices IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 74
SG 9: Design Approach o Incorporate new IP communication technologies • Focus on the Session Initiation Protocol (SIP) and supporting protocols • Leverage the 3 GPP IMS as a service delivery platform o Develop a modular and extensible architecture that allows new services to be added without impacting the core IPCablecom infrastructure o Ensure backward compatibility with existing IPCablecom Recommendations o Support a wide variety of client devices IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 74
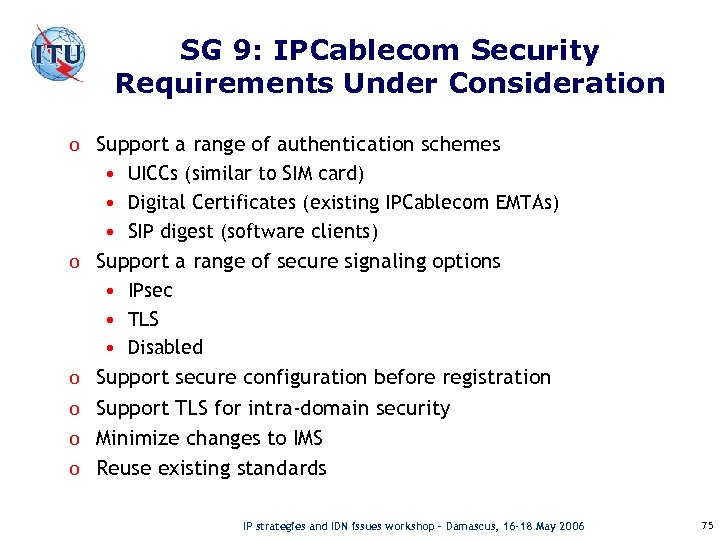 SG 9: IPCablecom Security Requirements Under Consideration o Support a range of authentication schemes • UICCs (similar to SIM card) • Digital Certificates (existing IPCablecom EMTAs) • SIP digest (software clients) o Support a range of secure signaling options • IPsec • TLS • Disabled o Support secure configuration before registration o Support TLS for intra-domain security o Minimize changes to IMS o Reuse existing standards IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 75
SG 9: IPCablecom Security Requirements Under Consideration o Support a range of authentication schemes • UICCs (similar to SIM card) • Digital Certificates (existing IPCablecom EMTAs) • SIP digest (software clients) o Support a range of secure signaling options • IPsec • TLS • Disabled o Support secure configuration before registration o Support TLS for intra-domain security o Minimize changes to IMS o Reuse existing standards IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 75
 SG 9: DOCSIS base line privacy + o The primary goals of DOCSIS BPI+ are to provide privacy of customer traffic, integrity of software downloads, and prevent theft of service. o DOCSIS BPI+ provides a number of tools to support these goals: • Traffic encryption for privacy/confidentiality. • Secure Software Download to assure a valid CM image. • Configuration file authentication to help secure the provisioning process. o Focus is on the link layer between the CMTS and CM. Security outside the DOCSIS network is provided by applications and other networks. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 76
SG 9: DOCSIS base line privacy + o The primary goals of DOCSIS BPI+ are to provide privacy of customer traffic, integrity of software downloads, and prevent theft of service. o DOCSIS BPI+ provides a number of tools to support these goals: • Traffic encryption for privacy/confidentiality. • Secure Software Download to assure a valid CM image. • Configuration file authentication to help secure the provisioning process. o Focus is on the link layer between the CMTS and CM. Security outside the DOCSIS network is provided by applications and other networks. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 76
 SG 9: DOCSIS BPI+ Security Algorithms o A Cable Modem Terminations System (CMTS) authenticates cable modems (CM) using X. 509 certificates and RSA public key cryptography. o Subscriber Traffic encryption • 3 DES used for key exchange • DES used for traffic encryption. AES being considered for future DOCSIS versions. o SW download image validation is performed using X. 509 certificates and digital signatures using RSA public key cryptography. o Message integrity checks (MIC) with keyed MD 5 hash used for CM configuration file security. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 77
SG 9: DOCSIS BPI+ Security Algorithms o A Cable Modem Terminations System (CMTS) authenticates cable modems (CM) using X. 509 certificates and RSA public key cryptography. o Subscriber Traffic encryption • 3 DES used for key exchange • DES used for traffic encryption. AES being considered for future DOCSIS versions. o SW download image validation is performed using X. 509 certificates and digital signatures using RSA public key cryptography. o Message integrity checks (MIC) with keyed MD 5 hash used for CM configuration file security. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 77
 SG 13: NGN Security Outline o o o Why NGN security? The ITU-T work on NGN Security Relationship to other SDOs Output of the NGN Focus Group Recent developments—starting the SG 13 Security work Top NGN security issues that need resolution Security is among the key differentiators of the NGN. It is also among its biggest challenges!. . All SG 13 Recommendations have a security section IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 78
SG 13: NGN Security Outline o o o Why NGN security? The ITU-T work on NGN Security Relationship to other SDOs Output of the NGN Focus Group Recent developments—starting the SG 13 Security work Top NGN security issues that need resolution Security is among the key differentiators of the NGN. It is also among its biggest challenges!. . All SG 13 Recommendations have a security section IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 78
 SG 13: Why Security? (Threat examples) o Subscriber’s perspective • Eavesdropping, theft of PIN codes • Tele-spam • Identity theft • Infection by viruses, worms, and spyware • Loss of privacy (call patterns, location, etc. ) • Flooding attacks on the end point o Provider’s perspective • Theft of service • Denial of service • Disclosure of network topology • Non-audited configuration changes • Additional related risks to the PSTN… In NGN, known IP security vulnerabilities can make PSTN vulnerable, too! IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 79
SG 13: Why Security? (Threat examples) o Subscriber’s perspective • Eavesdropping, theft of PIN codes • Tele-spam • Identity theft • Infection by viruses, worms, and spyware • Loss of privacy (call patterns, location, etc. ) • Flooding attacks on the end point o Provider’s perspective • Theft of service • Denial of service • Disclosure of network topology • Non-audited configuration changes • Additional related risks to the PSTN… In NGN, known IP security vulnerabilities can make PSTN vulnerable, too! IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 79
 SG 13: The ITU-T work on NGN Security o SG 13: Lead Study Group on the NGN standardization. o o (Question 15/13 is responsible for X. 805 -based NGN security) SG 17: Lead Study Group on Telecommunication Security—the fundamental X. 800 series, PKI, etc. SG 4: Lead Study Group on Telecommunication Management— Management Plane security SG 11: Lead Study Group on signaling and protocols—security of the Control and Signaling planes SG 16: Lead Study Group on multimedia terminals, systems and applications—Multimedia security FGNGN has concluded; IDN issues workshop – Damascus, 16 -18 May 2006 13 its work has moved to SG IP strategies and 80
SG 13: The ITU-T work on NGN Security o SG 13: Lead Study Group on the NGN standardization. o o (Question 15/13 is responsible for X. 805 -based NGN security) SG 17: Lead Study Group on Telecommunication Security—the fundamental X. 800 series, PKI, etc. SG 4: Lead Study Group on Telecommunication Management— Management Plane security SG 11: Lead Study Group on signaling and protocols—security of the Control and Signaling planes SG 16: Lead Study Group on multimedia terminals, systems and applications—Multimedia security FGNGN has concluded; IDN issues workshop – Damascus, 16 -18 May 2006 13 its work has moved to SG IP strategies and 80
 Collaboration of ITU-T with other SDOs and fora on NGN security Recommendations ISO/IEC JTC 1 SC 27, … IETF ITU-T SG 13, 17, 4, 11, 16 … ATIS 3 GPP ETSI TISPAN Fora (such as OASIS) 3 GPP 2 TIA SG 13 is the Lead Study Group for NGN SG 17 is the Lead Study Group for Security IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 81
Collaboration of ITU-T with other SDOs and fora on NGN security Recommendations ISO/IEC JTC 1 SC 27, … IETF ITU-T SG 13, 17, 4, 11, 16 … ATIS 3 GPP ETSI TISPAN Fora (such as OASIS) 3 GPP 2 TIA SG 13 is the Lead Study Group for NGN SG 17 is the Lead Study Group for Security IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 81
 SG 13: Question 15 NGN security o Question 15 (NGN security) of SG 13 – ITU-T lead study group for NGN and satellite matters - will continue standards work started by FGNGN WG 5. o Q. 15/13 major tasks are: • Lead the NGN-specific security project-level issues within SG 13 and with other Study Groups. Recognizing SG 17’s overall role as the Lead Study Group for Telecommunication Security, advise and assist SG 17 on NGN security coordination issues. • Apply the X. 805 Security architecture for systems providing end-to-end communication within the context of an NGN environment • Ensure that • the developed NGN architecture is consistent with accepted security principles • Ensure that AAA principles are integrated as required throughout the NGN IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 82
SG 13: Question 15 NGN security o Question 15 (NGN security) of SG 13 – ITU-T lead study group for NGN and satellite matters - will continue standards work started by FGNGN WG 5. o Q. 15/13 major tasks are: • Lead the NGN-specific security project-level issues within SG 13 and with other Study Groups. Recognizing SG 17’s overall role as the Lead Study Group for Telecommunication Security, advise and assist SG 17 on NGN security coordination issues. • Apply the X. 805 Security architecture for systems providing end-to-end communication within the context of an NGN environment • Ensure that • the developed NGN architecture is consistent with accepted security principles • Ensure that AAA principles are integrated as required throughout the NGN IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 82
 SG 13: FGNGN output: Security Requirements for NGN Release 1 (highlights) o Security requirements for the Service Stratum • IMS securty • Transport domain to NGN core network interface • Open service platforms and applications security • Vo. IP • Emergency Telecommunication Services and Telecommunications for Disaster Relief o Security requirements for the Transport Stratum • NGN customer network domain • Customer network to IPConnectivity Access Network (IP-CAN) interface • Core network functions • NGN customer network to NGN customer network interface IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 83
SG 13: FGNGN output: Security Requirements for NGN Release 1 (highlights) o Security requirements for the Service Stratum • IMS securty • Transport domain to NGN core network interface • Open service platforms and applications security • Vo. IP • Emergency Telecommunication Services and Telecommunications for Disaster Relief o Security requirements for the Transport Stratum • NGN customer network domain • Customer network to IPConnectivity Access Network (IP-CAN) interface • Core network functions • NGN customer network to NGN customer network interface IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 83
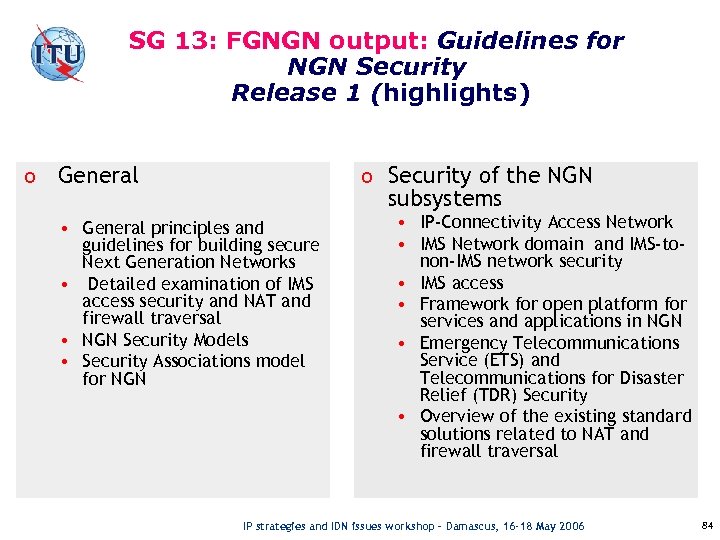 SG 13: FGNGN output: Guidelines for NGN Security Release 1 (highlights) o General o Security of the NGN subsystems • General principles and guidelines for building secure Next Generation Networks • Detailed examination of IMS access security and NAT and firewall traversal • NGN Security Models • Security Associations model for NGN • IP-Connectivity Access Network • IMS Network domain and IMS-tonon-IMS network security • IMS access • Framework for open platform for services and applications in NGN • Emergency Telecommunications Service (ETS) and Telecommunications for Disaster Relief (TDR) Security • Overview of the existing standard solutions related to NAT and firewall traversal IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 84
SG 13: FGNGN output: Guidelines for NGN Security Release 1 (highlights) o General o Security of the NGN subsystems • General principles and guidelines for building secure Next Generation Networks • Detailed examination of IMS access security and NAT and firewall traversal • NGN Security Models • Security Associations model for NGN • IP-Connectivity Access Network • IMS Network domain and IMS-tonon-IMS network security • IMS access • Framework for open platform for services and applications in NGN • Emergency Telecommunications Service (ETS) and Telecommunications for Disaster Relief (TDR) Security • Overview of the existing standard solutions related to NAT and firewall traversal IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 84
 SG 13: Focus of the current work of Question 15, NGN security o Security Requirements for NGN Release 1 o Authentication requirements for NGN Release 1 o AAA Service for Network Access to NGN o Guidelines for NGN Security Release 1 o Security considerations for Pseudowire (PWE) technology At the heart of securing network protocols, the biggest challenge is authentication. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 85
SG 13: Focus of the current work of Question 15, NGN security o Security Requirements for NGN Release 1 o Authentication requirements for NGN Release 1 o AAA Service for Network Access to NGN o Guidelines for NGN Security Release 1 o Security considerations for Pseudowire (PWE) technology At the heart of securing network protocols, the biggest challenge is authentication. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 85
 SG 13: Major issues for NGN security standardization o Key distribution (for end-users and network elements) and o o o Public Key Infrastructure “Network privacy”—topology hiding and NAT/Firewall traversal for real-time applications Convergence with IT security Management of security functions (e. g. , policy) Guidelines on the implementation of the IETF protocols (e. g. , IPsec options) Security for supporting access: DSL, WLAN, and cable access scenarios Guidelines for handling 3 GPP vs. 3 GPP 2 differences in IMS Security Both—network assets and network traffic—must be protected. Proper management procedures will help prevent attacks from within. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 86
SG 13: Major issues for NGN security standardization o Key distribution (for end-users and network elements) and o o o Public Key Infrastructure “Network privacy”—topology hiding and NAT/Firewall traversal for real-time applications Convergence with IT security Management of security functions (e. g. , policy) Guidelines on the implementation of the IETF protocols (e. g. , IPsec options) Security for supporting access: DSL, WLAN, and cable access scenarios Guidelines for handling 3 GPP vs. 3 GPP 2 differences in IMS Security Both—network assets and network traffic—must be protected. Proper management procedures will help prevent attacks from within. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 86
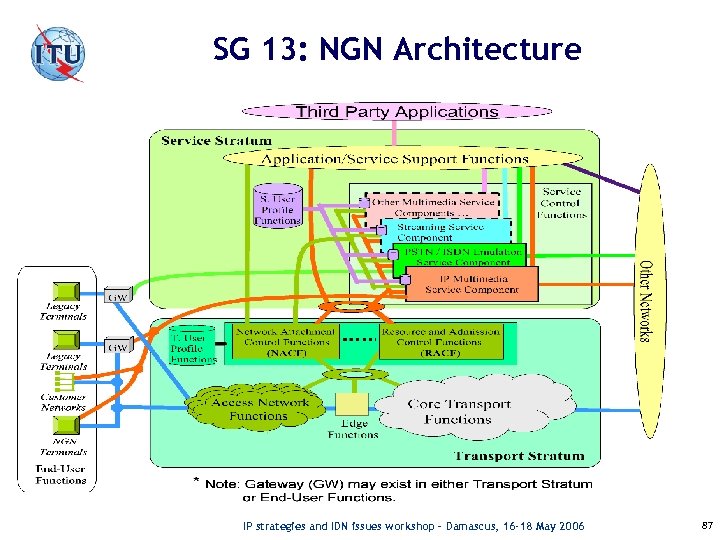 SG 13: NGN Architecture IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 87
SG 13: NGN Architecture IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 87
 SG 16: Multimedia security in Next Generation Networks o ITU-T SG 16 MM-security activities – Overview (Q. 25 and Q. 5) o Status and results within SG 16. o Ongoing and future activities within SG 16. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 88
SG 16: Multimedia security in Next Generation Networks o ITU-T SG 16 MM-security activities – Overview (Q. 25 and Q. 5) o Status and results within SG 16. o Ongoing and future activities within SG 16. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 88
 Question 25/16 “Multimedia Security in Next-Generation Networks” (NGN-MM-SEC) o o Study Group 16 concentrates on Multimedia systems. Q. 25/16 focuses on the application-security issues of MM applications in next generation networks Standardizes Multimedia Security So far Q. 25 has been standardizing MM-security for the “ 1 st generation MM/pre-NGN? -systems”: • H. 323/H. 248 -based systems. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 89
Question 25/16 “Multimedia Security in Next-Generation Networks” (NGN-MM-SEC) o o Study Group 16 concentrates on Multimedia systems. Q. 25/16 focuses on the application-security issues of MM applications in next generation networks Standardizes Multimedia Security So far Q. 25 has been standardizing MM-security for the “ 1 st generation MM/pre-NGN? -systems”: • H. 323/H. 248 -based systems. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 89
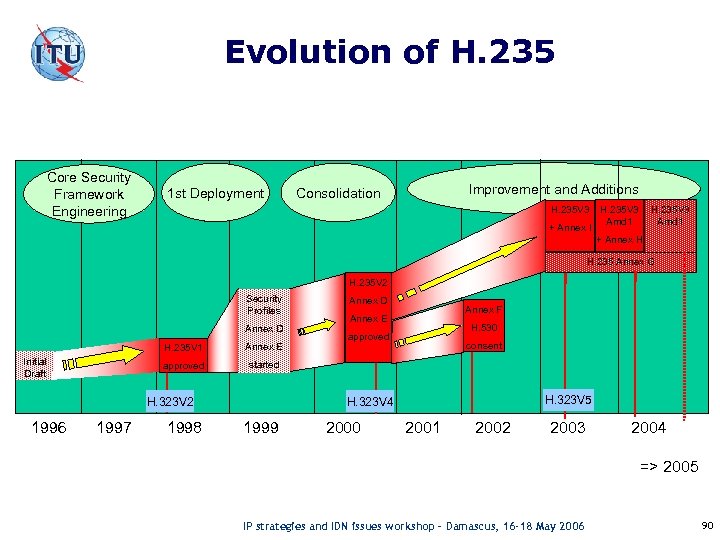 Evolution of H. 235 Core Security Framework Engineering 1 st Deployment Improvement and Additions Consolidation H. 235 V 3 + Annex I H. 235 V 3 Amd 1 + Annex H H. 235 Annex G H. 235 V 2 Security Profiles Annex D H. 235 V 1 approved Initial Draft Annex E 1997 Annex F Annex E H. 530 approved consent started 1998 H. 323 V 5 H. 323 V 4 H. 323 V 2 1996 Annex D 1999 2000 2001 2002 2003 2004 => 2005 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 90
Evolution of H. 235 Core Security Framework Engineering 1 st Deployment Improvement and Additions Consolidation H. 235 V 3 + Annex I H. 235 V 3 Amd 1 + Annex H H. 235 Annex G H. 235 V 2 Security Profiles Annex D H. 235 V 1 approved Initial Draft Annex E 1997 Annex F Annex E H. 530 approved consent started 1998 H. 323 V 5 H. 323 V 4 H. 323 V 2 1996 Annex D 1999 2000 2001 2002 2003 2004 => 2005 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 90
 H. 235 v 4 subseries Recommendations o o Major restructuring of H. 235 v 3 Amd 1 and annexes in stand-alone subseries Recommendations H. 235. x subseries specify scenario-specific MMsecurity procedures as H. 235 -profiles for H. 323 o o Some new parts added Some enhancements and extensions Incorporated corrections o Approved in Sept. 2005 o IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 91
H. 235 v 4 subseries Recommendations o o Major restructuring of H. 235 v 3 Amd 1 and annexes in stand-alone subseries Recommendations H. 235. x subseries specify scenario-specific MMsecurity procedures as H. 235 -profiles for H. 323 o o Some new parts added Some enhancements and extensions Incorporated corrections o Approved in Sept. 2005 o IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 91
 H. 323 Security Recommendations (1) o H. 235. 0 “Security framework for H-series (H. 323 and other H. 245 -based) multimedia systems” Þ Overview of H. 235. x subseries and common procedures with baseline text o H. 235. 1 "Baseline Security Profile” Þ Authentication & integrity for H. 225. 0 signaling using shared secrets o H. 235. 2 "Signature Security Profile” Þ Authentication & integrity for H. 225. 0 signaling using X. 509 digital certificates and signatures IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 92
H. 323 Security Recommendations (1) o H. 235. 0 “Security framework for H-series (H. 323 and other H. 245 -based) multimedia systems” Þ Overview of H. 235. x subseries and common procedures with baseline text o H. 235. 1 "Baseline Security Profile” Þ Authentication & integrity for H. 225. 0 signaling using shared secrets o H. 235. 2 "Signature Security Profile” Þ Authentication & integrity for H. 225. 0 signaling using X. 509 digital certificates and signatures IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 92
 H. 323 Security Recommendations (2) o Þ Authentication & integrity for H. 225. 0 signaling using an optimized combination of X. 509 digital certificates, signatures and shared secret key management; specification of an optional proxy-based security processor enhanced o extended H. 235. 3 "Hybrid Security Profile" H. 235. 4 "Direct and Selective Routed Call Security" Þ Key management procedures in corporate and in interdomain environments to obtain key material for securing H. 225. 0 call signaling in GK directrouted/selective routed scenarios IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 93
H. 323 Security Recommendations (2) o Þ Authentication & integrity for H. 225. 0 signaling using an optimized combination of X. 509 digital certificates, signatures and shared secret key management; specification of an optional proxy-based security processor enhanced o extended H. 235. 3 "Hybrid Security Profile" H. 235. 4 "Direct and Selective Routed Call Security" Þ Key management procedures in corporate and in interdomain environments to obtain key material for securing H. 225. 0 call signaling in GK directrouted/selective routed scenarios IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 93
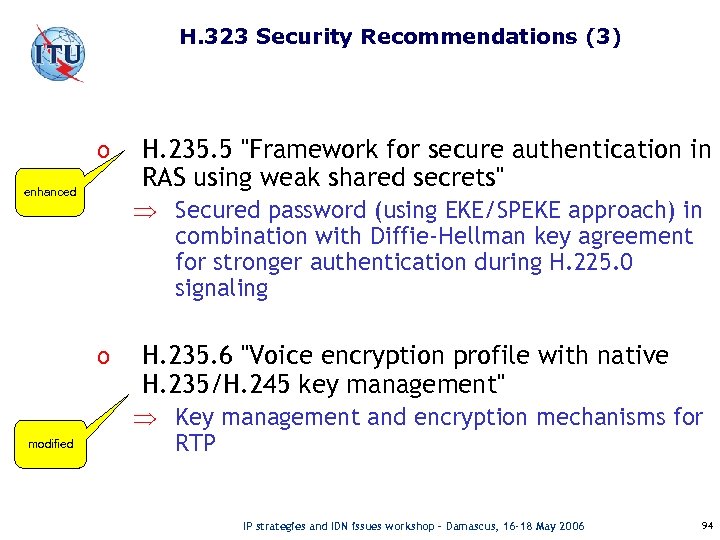 H. 323 Security Recommendations (3) o enhanced Þ Secured password (using EKE/SPEKE approach) in combination with Diffie-Hellman key agreement for stronger authentication during H. 225. 0 signaling o modified H. 235. 5 "Framework for secure authentication in RAS using weak shared secrets" H. 235. 6 "Voice encryption profile with native H. 235/H. 245 key management" Þ Key management and encryption mechanisms for RTP IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 94
H. 323 Security Recommendations (3) o enhanced Þ Secured password (using EKE/SPEKE approach) in combination with Diffie-Hellman key agreement for stronger authentication during H. 225. 0 signaling o modified H. 235. 5 "Framework for secure authentication in RAS using weak shared secrets" H. 235. 6 "Voice encryption profile with native H. 235/H. 245 key management" Þ Key management and encryption mechanisms for RTP IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 94
 H. 323 Security Recommendations (4) o H. 235. 7 "Usage of the MIKEY Key Management Protocol for the Secure Real Time Transport Protocol (SRTP) within H. 235" Þ Usage of the MIKEY key management for SRTP o H. 235. 8 "Key Exchange for SRTP using secure Signalling Channels" Þ SRTP keying parameter transport over secured signaling channels (IPsec, TLS, CMS) o H. 235. 9 "Security Gateway Support for H. 323" Þ Discovery of H. 323 Security Gateways (SG = H. 323 NAT/FW ALG) and key management for H. 225. 0 signaling IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 95
H. 323 Security Recommendations (4) o H. 235. 7 "Usage of the MIKEY Key Management Protocol for the Secure Real Time Transport Protocol (SRTP) within H. 235" Þ Usage of the MIKEY key management for SRTP o H. 235. 8 "Key Exchange for SRTP using secure Signalling Channels" Þ SRTP keying parameter transport over secured signaling channels (IPsec, TLS, CMS) o H. 235. 9 "Security Gateway Support for H. 323" Þ Discovery of H. 323 Security Gateways (SG = H. 323 NAT/FW ALG) and key management for H. 225. 0 signaling IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 95
 Other SG 16 MM-SEC Results o H. 350. 2 (2003) “H. 350. 2 Directory Services Architecture for H. 235” Þ An LDAP schema to represent H. 235 elements (PWs, certificates, ID information) o H. 530 (Revision 2003) “Symmetric security procedures for H. 323 mobility in H. 510” Þ Authentication, access control and key management in mobile H. 323 -based corporate networks IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 96
Other SG 16 MM-SEC Results o H. 350. 2 (2003) “H. 350. 2 Directory Services Architecture for H. 235” Þ An LDAP schema to represent H. 235 elements (PWs, certificates, ID information) o H. 530 (Revision 2003) “Symmetric security procedures for H. 323 mobility in H. 510” Þ Authentication, access control and key management in mobile H. 323 -based corporate networks IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 96
 Q. 5/16 (H. 300 NAT/FW traversal) Results (1) o H. 460. 18 “Traversal of H. 323 signalling across FWs and NATs” Þ H. 323 protocol enhancements and new client/server proxies to allow H. 323 signalling protocols traverse NATs & FWs; H. 323 endpoints can remain unchanged o H. 460. 19 “NAT & FW traversal procedures for RTP in H. 323 systems” Þ uses multiplexed RTP media mode and symmetric RTP in conjunction with H. 460. 18 as a short-term solution IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 97
Q. 5/16 (H. 300 NAT/FW traversal) Results (1) o H. 460. 18 “Traversal of H. 323 signalling across FWs and NATs” Þ H. 323 protocol enhancements and new client/server proxies to allow H. 323 signalling protocols traverse NATs & FWs; H. 323 endpoints can remain unchanged o H. 460. 19 “NAT & FW traversal procedures for RTP in H. 323 systems” Þ uses multiplexed RTP media mode and symmetric RTP in conjunction with H. 460. 18 as a short-term solution IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 97
 More Q. 5/16 Results (2) o Technical Paper “Requirements for Network Address Translator and Firewall Traversal of H. 323 Multimedia Systems” Þ Documentation of scenarios and requirements for NAT & FW traversal in H. 323 o Technical Paper “Firewall and NAT traversal Problems in H. 323 Systems” Þ An analysis of scenarios and various problems encountered by H. 323 around NAT & FW traversal IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 98
More Q. 5/16 Results (2) o Technical Paper “Requirements for Network Address Translator and Firewall Traversal of H. 323 Multimedia Systems” Þ Documentation of scenarios and requirements for NAT & FW traversal in H. 323 o Technical Paper “Firewall and NAT traversal Problems in H. 323 Systems” Þ An analysis of scenarios and various problems encountered by H. 323 around NAT & FW traversal IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 98
 New Q. 25/16 items under current study (1) o Draft H. 460. spn “Security protocol negotiation” ° o Goal: Negotiate security protocols (IPsec or TLS) for H. 323 signaling) (Draft) H. FSIC “Federated Architecture for Secure Internet Conferencing” ° Goal: Define a generic protocol independent security profile for globally scalable security conferencing using trust federations. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 99
New Q. 25/16 items under current study (1) o Draft H. 460. spn “Security protocol negotiation” ° o Goal: Negotiate security protocols (IPsec or TLS) for H. 323 signaling) (Draft) H. FSIC “Federated Architecture for Secure Internet Conferencing” ° Goal: Define a generic protocol independent security profile for globally scalable security conferencing using trust federations. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 99
 New Q. 25/16 items under current study (2) o Study Anti-DDo. S (Denial-of-Service) countermeasures for (H. 323 -based) NAT/FW proxy and MM applications o Security for MM-Qo. S (H. mmqos. security) o MM security aspects of Vision H. 325 “Next-generation Multimedia Terminals and Systems” ° Goal: MM-security for H. 325, MM security for Audiovisual on Demand services, Multimedia Conferencing, Distant learning, . . . IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 100
New Q. 25/16 items under current study (2) o Study Anti-DDo. S (Denial-of-Service) countermeasures for (H. 323 -based) NAT/FW proxy and MM applications o Security for MM-Qo. S (H. mmqos. security) o MM security aspects of Vision H. 325 “Next-generation Multimedia Terminals and Systems” ° Goal: MM-security for H. 325, MM security for Audiovisual on Demand services, Multimedia Conferencing, Distant learning, . . . IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 100
 New Q. 25/16 items under current study (3) o Study Multimedia-Security aspects of Digital Rights Management (MM-DRM) • What does MM-DRM mean? • Understand DRM security needs for MM content of MM applications (e. g. IPTV, …) • Contributions are solicited. • Which other groups are active/interested in this area? IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 101
New Q. 25/16 items under current study (3) o Study Multimedia-Security aspects of Digital Rights Management (MM-DRM) • What does MM-DRM mean? • Understand DRM security needs for MM content of MM applications (e. g. IPTV, …) • Contributions are solicited. • Which other groups are active/interested in this area? IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 101
 Ongoing Q. 5/16 work items o Draft H. proxy ° Goal: Specify signaling & media client/server proxies connected with a (UDP) tunneling protocol for H. 323 NAT & FW traversal IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 102
Ongoing Q. 5/16 work items o Draft H. proxy ° Goal: Specify signaling & media client/server proxies connected with a (UDP) tunneling protocol for H. 323 NAT & FW traversal IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 102
 SG 16: Summary o Multimedia systems and applications as being studied by SG 16 face important security challenges: • MM-security and NAT/FW traversal o Q. 25/16 and Q. 5/16 are addressing these issues and have provided various Recommendations o The work continues in the scope of NGN-Multimedia Security. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 103
SG 16: Summary o Multimedia systems and applications as being studied by SG 16 face important security challenges: • MM-security and NAT/FW traversal o Q. 25/16 and Q. 5/16 are addressing these issues and have provided various Recommendations o The work continues in the scope of NGN-Multimedia Security. IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 103
 ITU-T SG 19 Work on Security IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 104
ITU-T SG 19 Work on Security IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 104
 Security Work in SG 19 (1/3) o Q. 1/19 Service and network capability requirements and network architecture • PDNR Q. FNAB “Functional Network Architecture for Systems Beyond IMT-2000” has included security requirements from the beginning, building on existing material in related domains o Q. 2/19 Mobility management • Security is included as a fundamental component of the analysis mobility management mechanisms in Q-series Supplement 47 “Technical Report on NNI Mobility Management Requirements” • Currently progressing, on the same basis and jointly with Q. 6/13: • • Rec. MMR Mobility Management Requirements (Stage 1) Rec. MMF Mobility Management Framework (Stage 2) Rec. LMF Location Mobility Management Framework (Stage 2) Rec. HMF Handover Management Framework (Stage 2) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 105
Security Work in SG 19 (1/3) o Q. 1/19 Service and network capability requirements and network architecture • PDNR Q. FNAB “Functional Network Architecture for Systems Beyond IMT-2000” has included security requirements from the beginning, building on existing material in related domains o Q. 2/19 Mobility management • Security is included as a fundamental component of the analysis mobility management mechanisms in Q-series Supplement 47 “Technical Report on NNI Mobility Management Requirements” • Currently progressing, on the same basis and jointly with Q. 6/13: • • Rec. MMR Mobility Management Requirements (Stage 1) Rec. MMF Mobility Management Framework (Stage 2) Rec. LMF Location Mobility Management Framework (Stage 2) Rec. HMF Handover Management Framework (Stage 2) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 105
 Security Work in SG 19 (2/3) o Q. 3/19 Identification of existing and evolving IMT-2000 systems • Q. 1741 and Q. 1742 series of Recommendations include security as a key aspect of its referencing Recommendations for IMT-2000 (3 G) Family Members identified in its Q. 1741. x (3 GPP) and Q. 1742. x (3 GPP 2) series Recommendations, including: • • an evaluation of perceived threats a list of security requirements to address the threats security objectives and principles a defined security architecture (i. e. , security features and mechanisms) • cryptographic algorithm requirements • lawful interception architecture and functions • Additional information in backup charts IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 106
Security Work in SG 19 (2/3) o Q. 3/19 Identification of existing and evolving IMT-2000 systems • Q. 1741 and Q. 1742 series of Recommendations include security as a key aspect of its referencing Recommendations for IMT-2000 (3 G) Family Members identified in its Q. 1741. x (3 GPP) and Q. 1742. x (3 GPP 2) series Recommendations, including: • • an evaluation of perceived threats a list of security requirements to address the threats security objectives and principles a defined security architecture (i. e. , security features and mechanisms) • cryptographic algorithm requirements • lawful interception architecture and functions • Additional information in backup charts IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 106
 Security in SG 19 Work (3/3) o Q. 4/19 Preparation of a handbook on IMT- 2000 • Next edition of “Handbook of evolving IMT 2000 Systems (Core Network Aspects)” in progress includes a new chapter “Safety and security issues for IMT-2000” o Q. 5/19 Convergence of evolving IMT-2000 networks with evolving fixed networks • Includes security consideration for such areas as user identification and authentication, including IMS security (see Q. 3/19) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 107
Security in SG 19 Work (3/3) o Q. 4/19 Preparation of a handbook on IMT- 2000 • Next edition of “Handbook of evolving IMT 2000 Systems (Core Network Aspects)” in progress includes a new chapter “Safety and security issues for IMT-2000” o Q. 5/19 Convergence of evolving IMT-2000 networks with evolving fixed networks • Includes security consideration for such areas as user identification and authentication, including IMS security (see Q. 3/19) IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 107
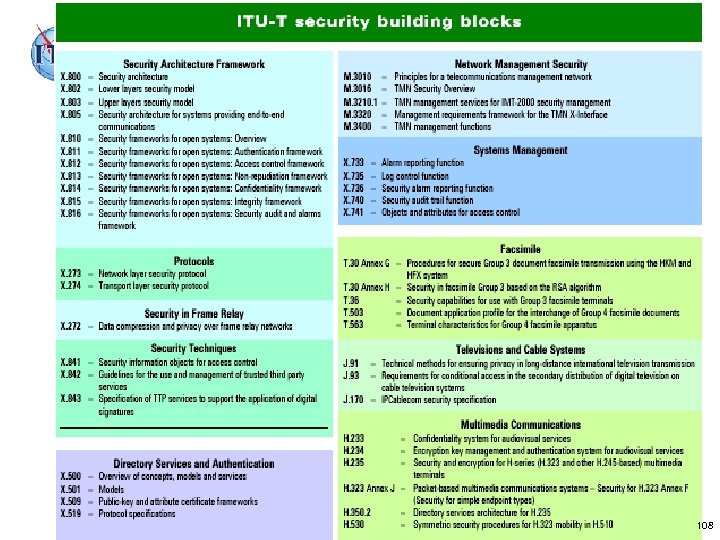 IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 108
IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 108
 Conclusions 1. Security is everybody's business 2. Collaboration with other SDOs is necessary 3. Security needs to be designed in upfront 4. Security must be an ongoing effort 5. Systematically addressing vulnerabilities (intrinsic properties of networks/systems) is key so that protection can be provided independent of what the threats (which are constantly changing and may be unknown) may be – X. 805 is helpful here IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 109
Conclusions 1. Security is everybody's business 2. Collaboration with other SDOs is necessary 3. Security needs to be designed in upfront 4. Security must be an ongoing effort 5. Systematically addressing vulnerabilities (intrinsic properties of networks/systems) is key so that protection can be provided independent of what the threats (which are constantly changing and may be unknown) may be – X. 805 is helpful here IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 109
 Some useful web resources o ITU-T Home page o Study Group 17 e-mail: www. itu. int/itu-t/studygroups/com 17 tsbsg 17@itu. int o Recommendations www. itu. int/ITU-T/publications/recs. html o ITU-T Lighthouse www. itu. int/ITU-T/lighthouse o ITU-T Workshops www. itu. int/ITU-T/worksem o Security Roadmap www. itu. int/ITU-T/studygroups/com 17/index IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 110
Some useful web resources o ITU-T Home page o Study Group 17 e-mail: www. itu. int/itu-t/studygroups/com 17 tsbsg 17@itu. int o Recommendations www. itu. int/ITU-T/publications/recs. html o ITU-T Lighthouse www. itu. int/ITU-T/lighthouse o ITU-T Workshops www. itu. int/ITU-T/worksem o Security Roadmap www. itu. int/ITU-T/studygroups/com 17/index IP strategies and IDN issues workshop – Damascus, 16 -18 May 2006 110
 International Telecommunication Union Thank You ! Page - IP strategies and IDN issues workshop – Damscus, 16 -18 May 2006
International Telecommunication Union Thank You ! Page - IP strategies and IDN issues workshop – Damscus, 16 -18 May 2006


