f69874fd83ca4a7f46249d878cf56489.ppt
- Количество слайдов: 33
 International Telecommunication Union ICT Security - The Need for International Standards reinhard. scholl@itu. int Deputy to the Director Telecommunication Standardization Bureau International Telecommunication Union www. itu. int/ITU-T Confidence & security in the use of ICT Malaysia, 21 August 2003 Page -
International Telecommunication Union ICT Security - The Need for International Standards reinhard. scholl@itu. int Deputy to the Director Telecommunication Standardization Bureau International Telecommunication Union www. itu. int/ITU-T Confidence & security in the use of ICT Malaysia, 21 August 2003 Page -
 Outline 1. Why ICT security is becoming important 2. The complex world of ICT Security 3. Security standards [ICT = Information & Communication Technology] Confidence & security in the use of ICT - Malaysia, 21 August 2003 2
Outline 1. Why ICT security is becoming important 2. The complex world of ICT Security 3. Security standards [ICT = Information & Communication Technology] Confidence & security in the use of ICT - Malaysia, 21 August 2003 2
 1. Why ICT security is becoming important Confidence & security in the use of ICT - Malaysia, 21 August 2003 3
1. Why ICT security is becoming important Confidence & security in the use of ICT - Malaysia, 21 August 2003 3
 Security: Telephony vs. Internet o Telephone network: Control • • • Offers basically one service Network operators control if new service offered Clear distinction: • • o Interface user – network Interface network – network Internet: “Anarchy” (no negative meaning here) • • Lots of services (many of them not yet imagined …) Everyone can set up a new services All links network – network Many protocols Confidence & security in the use of ICT - Malaysia, 21 August 2003 4
Security: Telephony vs. Internet o Telephone network: Control • • • Offers basically one service Network operators control if new service offered Clear distinction: • • o Interface user – network Interface network – network Internet: “Anarchy” (no negative meaning here) • • Lots of services (many of them not yet imagined …) Everyone can set up a new services All links network – network Many protocols Confidence & security in the use of ICT - Malaysia, 21 August 2003 4
 A Fundamental Shift is Happening o o Computers & networks are becoming a utility (like water, electricity, gas, telephone) Business and personal life are more and more dependent on computers Prerequisite: adequate security. [9/11 terrorist attack confirmed the already existing trend of emphasizing security] Confidence & security in the use of ICT - Malaysia, 21 August 2003 5
A Fundamental Shift is Happening o o Computers & networks are becoming a utility (like water, electricity, gas, telephone) Business and personal life are more and more dependent on computers Prerequisite: adequate security. [9/11 terrorist attack confirmed the already existing trend of emphasizing security] Confidence & security in the use of ICT - Malaysia, 21 August 2003 5
 Basic Security Services o Privacy / Confidentiality: • To know that no 3 rd party can read a message exchanged between 2 people o Authentication: • To know that someone is who he/she says he/she is o Integrity: • To know that a message has not been modified in transit o Non-repudiation: • To know that someone is not able to deny later that she/he sent a message Confidence & security in the use of ICT - Malaysia, 21 August 2003 6
Basic Security Services o Privacy / Confidentiality: • To know that no 3 rd party can read a message exchanged between 2 people o Authentication: • To know that someone is who he/she says he/she is o Integrity: • To know that a message has not been modified in transit o Non-repudiation: • To know that someone is not able to deny later that she/he sent a message Confidence & security in the use of ICT - Malaysia, 21 August 2003 6
 Security Applications o The previous basic security services can be used to build many security applications: • • • Digital Signature Anonymous e-cash Certified e-mail Secure elections Simultaneous contract signing [add your ideas …] Confidence & security in the use of ICT - Malaysia, 21 August 2003 7
Security Applications o The previous basic security services can be used to build many security applications: • • • Digital Signature Anonymous e-cash Certified e-mail Secure elections Simultaneous contract signing [add your ideas …] Confidence & security in the use of ICT - Malaysia, 21 August 2003 7
 2. The complex world of ICT security Confidence & security in the use of ICT - Malaysia, 21 August 2003 8
2. The complex world of ICT security Confidence & security in the use of ICT - Malaysia, 21 August 2003 8
 Some Security Risks o “Social engineering” attack: • • “Amateurs hack systems, professionals hack people” (Bruce Schneier) An organizations’ own employees may pose largest risk: • o o o Incompetence, indifference, misconduct New technologies bring new security problems (e. g. , Wi. Fi) Buggy software Viruses Malicious hackers braking into systems Denial of Service attacks … Confidence & security in the use of ICT - Malaysia, 21 August 2003 9
Some Security Risks o “Social engineering” attack: • • “Amateurs hack systems, professionals hack people” (Bruce Schneier) An organizations’ own employees may pose largest risk: • o o o Incompetence, indifference, misconduct New technologies bring new security problems (e. g. , Wi. Fi) Buggy software Viruses Malicious hackers braking into systems Denial of Service attacks … Confidence & security in the use of ICT - Malaysia, 21 August 2003 9
 Non-trivial Insights o o Technology alone can not fix security problems – Technology is necessary but not sufficient Security is everyone’s business, not just the business of security experts Security decisions must be taken by Management, not by technical staff Security is risk management – the art to worry about the right things Confidence & security in the use of ICT - Malaysia, 21 August 2003 10
Non-trivial Insights o o Technology alone can not fix security problems – Technology is necessary but not sufficient Security is everyone’s business, not just the business of security experts Security decisions must be taken by Management, not by technical staff Security is risk management – the art to worry about the right things Confidence & security in the use of ICT - Malaysia, 21 August 2003 10
 Cryptography- the Beauty of Mathematics o o Cryptographic algorithms are “building blocks” to construct secure system Dramatic advances in cryptography in the last 30 years: • • • o Public Key Cryptography (1976) Microprocessor: cheap computing power Quantum cryptography (future) Reminder: security is more a “people problem” than a technical problem Confidence & security in the use of ICT - Malaysia, 21 August 2003 11
Cryptography- the Beauty of Mathematics o o Cryptographic algorithms are “building blocks” to construct secure system Dramatic advances in cryptography in the last 30 years: • • • o Public Key Cryptography (1976) Microprocessor: cheap computing power Quantum cryptography (future) Reminder: security is more a “people problem” than a technical problem Confidence & security in the use of ICT - Malaysia, 21 August 2003 11
 Secret Key Encryption Plain text encrypt message with secret key o o o Plain text decrypt message with same secret key cipher text Both parties share a single, secret key Problem: exchanging keys in complete secrecy is difficult Best-known example: DES (Data Encryption Standard) Confidence & security in the use of ICT - Malaysia, 21 August 2003 12
Secret Key Encryption Plain text encrypt message with secret key o o o Plain text decrypt message with same secret key cipher text Both parties share a single, secret key Problem: exchanging keys in complete secrecy is difficult Best-known example: DES (Data Encryption Standard) Confidence & security in the use of ICT - Malaysia, 21 August 2003 12
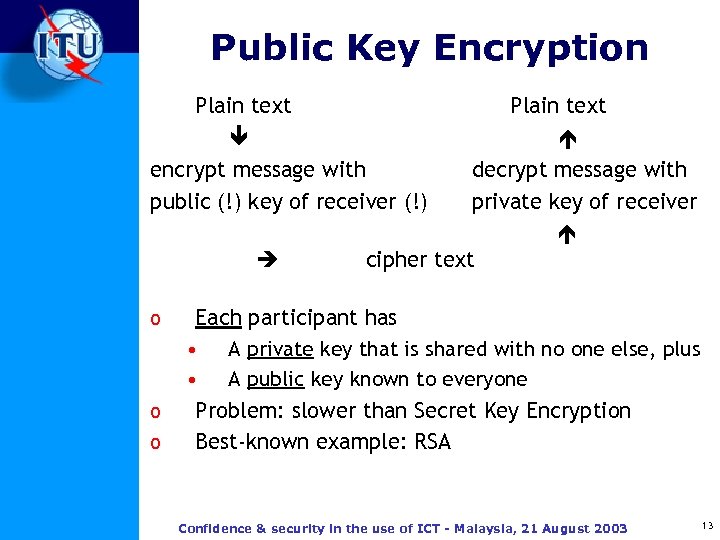 Public Key Encryption Plain text encrypt message with public (!) key of receiver (!) o o o Plain text decrypt message with private key of receiver cipher text Each participant has • A private key that is shared with no one else, plus • A public key known to everyone Problem: slower than Secret Key Encryption Best-known example: RSA Confidence & security in the use of ICT - Malaysia, 21 August 2003 13
Public Key Encryption Plain text encrypt message with public (!) key of receiver (!) o o o Plain text decrypt message with private key of receiver cipher text Each participant has • A private key that is shared with no one else, plus • A public key known to everyone Problem: slower than Secret Key Encryption Best-known example: RSA Confidence & security in the use of ICT - Malaysia, 21 August 2003 13
 Biometrics: your Body – your Password? o Recognize a person upon physiological or behavioral characteristics • • o Fingerprint Face Voice Iris Currently costs outweigh benefits Confidence & security in the use of ICT - Malaysia, 21 August 2003 14
Biometrics: your Body – your Password? o Recognize a person upon physiological or behavioral characteristics • • o Fingerprint Face Voice Iris Currently costs outweigh benefits Confidence & security in the use of ICT - Malaysia, 21 August 2003 14
 Economics & ICT Security o o Perverse incentives explain a lot of current information insecurity (Ross Anderson, Univ of Cambridge, UK) Distributed denial of service attack in 2000: • • o Vandals took over computers on low-security University networks and shut down major websites (e. g. Yahoo) Shouldn’t Universities bear some liability for the damages to 3 rd parties Solution: assign legal liabilities to the parties best able to manage the risk (Hal Varian, Univ of California, Berkeley) Confidence & security in the use of ICT - Malaysia, 21 August 2003 15
Economics & ICT Security o o Perverse incentives explain a lot of current information insecurity (Ross Anderson, Univ of Cambridge, UK) Distributed denial of service attack in 2000: • • o Vandals took over computers on low-security University networks and shut down major websites (e. g. Yahoo) Shouldn’t Universities bear some liability for the damages to 3 rd parties Solution: assign legal liabilities to the parties best able to manage the risk (Hal Varian, Univ of California, Berkeley) Confidence & security in the use of ICT - Malaysia, 21 August 2003 15
 Security is Risk Management o o How much money/time to spend on ICT security? Balance between cost and risk: • • • What are the potential security breaches? What’s the associated loss in each case? What does it cost to defend in each case? • • • o Mitigation (e. g. buy technology) Outsource (s. o. else takes over the risk) Insurance (passing risk to insurance company) Engineers, policymakers, economists, lawyers to forge common approaches Confidence & security in the use of ICT - Malaysia, 21 August 2003 16
Security is Risk Management o o How much money/time to spend on ICT security? Balance between cost and risk: • • • What are the potential security breaches? What’s the associated loss in each case? What does it cost to defend in each case? • • • o Mitigation (e. g. buy technology) Outsource (s. o. else takes over the risk) Insurance (passing risk to insurance company) Engineers, policymakers, economists, lawyers to forge common approaches Confidence & security in the use of ICT - Malaysia, 21 August 2003 16
 3. Security standards Confidence & security in the use of ICT - Malaysia, 21 August 2003 17
3. Security standards Confidence & security in the use of ICT - Malaysia, 21 August 2003 17
 The Need for Int’l. Security Standards o Technical standards should be international: • • o Best practice standards would be very helpful to be international • o Ensures interoperability - the whole point of most of the standards Economies of scale Raises awareness Regulatory issues & law enforcement is a national (or regional, e. g. European Union) matter Confidence & security in the use of ICT - Malaysia, 21 August 2003 18
The Need for Int’l. Security Standards o Technical standards should be international: • • o Best practice standards would be very helpful to be international • o Ensures interoperability - the whole point of most of the standards Economies of scale Raises awareness Regulatory issues & law enforcement is a national (or regional, e. g. European Union) matter Confidence & security in the use of ICT - Malaysia, 21 August 2003 18
 Security in International Standards Organizations o ISO/IEC: • 17799: “Information technology – code of practice for information security management” (71 pages; year 2000) • addresses organizations, companies o IETF: • Protocols, e. g. IPsec, TLS, SMIME … o ITU: see next slides Confidence & security in the use of ICT - Malaysia, 21 August 2003 19
Security in International Standards Organizations o ISO/IEC: • 17799: “Information technology – code of practice for information security management” (71 pages; year 2000) • addresses organizations, companies o IETF: • Protocols, e. g. IPsec, TLS, SMIME … o ITU: see next slides Confidence & security in the use of ICT - Malaysia, 21 August 2003 19
 ITU Plenipo & WSIS o ITU Plenipotentiary Conference 2002: • o “Strengthening the role of ITU in information and communication network security” WSIS = World Summit on Information Society; www. itu. int/wsis: • • UN-event 1 st phase: Geneva 10 -12 Dec 03; 2 nd phase: Tunis 16 -18 Nov 05 Target audience: Heads of State + CEOs + civil society Topics include communication network security Confidence & security in the use of ICT - Malaysia, 21 August 2003 20
ITU Plenipo & WSIS o ITU Plenipotentiary Conference 2002: • o “Strengthening the role of ITU in information and communication network security” WSIS = World Summit on Information Society; www. itu. int/wsis: • • UN-event 1 st phase: Geneva 10 -12 Dec 03; 2 nd phase: Tunis 16 -18 Nov 05 Target audience: Heads of State + CEOs + civil society Topics include communication network security Confidence & security in the use of ICT - Malaysia, 21 August 2003 20
 Security in ITU-T Study Groups o SG 17 = Lead Study Group for Communication System Security: • • o Coordination / prioritization of security efforts Development of core security Recs. Existing Recommendations include: • • • Security architecture, model, frameworks, and protocols for open systems (X. 800 series; X. 270 series, jointly with ISO) Trusted Third Party Services (X. 842/X. 843, jointly with ISO) Public-key and attribute certificate frameworks (X. 509, jointly with ISO) Confidence & security in the use of ICT - Malaysia, 21 August 2003 21
Security in ITU-T Study Groups o SG 17 = Lead Study Group for Communication System Security: • • o Coordination / prioritization of security efforts Development of core security Recs. Existing Recommendations include: • • • Security architecture, model, frameworks, and protocols for open systems (X. 800 series; X. 270 series, jointly with ISO) Trusted Third Party Services (X. 842/X. 843, jointly with ISO) Public-key and attribute certificate frameworks (X. 509, jointly with ISO) Confidence & security in the use of ICT - Malaysia, 21 August 2003 21
 ITU-T SG 17 Security Focus o Authentication (X. 509, jointly with ISO): • o Security Architecture for end-to-end communications: • o Model for security and public safety in telebiometrics Security Management: • o Security for management, control and use of network infrastructure, services and applications Telebiometrics: biometrics via distance • o Ongoing enhancements as a result of more complex uses Risk assessment, identification of assets and implementation characteristics Mobile Security: • For low power, small memory size and small display devices Confidence & security in the use of ICT - Malaysia, 21 August 2003 22
ITU-T SG 17 Security Focus o Authentication (X. 509, jointly with ISO): • o Security Architecture for end-to-end communications: • o Model for security and public safety in telebiometrics Security Management: • o Security for management, control and use of network infrastructure, services and applications Telebiometrics: biometrics via distance • o Ongoing enhancements as a result of more complex uses Risk assessment, identification of assets and implementation characteristics Mobile Security: • For low power, small memory size and small display devices Confidence & security in the use of ICT - Malaysia, 21 August 2003 22
 ITU-T SG 17: Upcoming Joint Work with ISO / IEC o “Information Technology – Security techniques – IT network security” • • • Part 1: Network security management Part 2: Network security architecture Part 3: Securing communications between networks using security gateways Part 4: Remote access Part 5: Securing communications between networks using virtual private networks Confidence & security in the use of ICT - Malaysia, 21 August 2003 23
ITU-T SG 17: Upcoming Joint Work with ISO / IEC o “Information Technology – Security techniques – IT network security” • • • Part 1: Network security management Part 2: Network security architecture Part 3: Securing communications between networks using security gateways Part 4: Remote access Part 5: Securing communications between networks using virtual private networks Confidence & security in the use of ICT - Malaysia, 21 August 2003 23
 Security Studies in other ITU-T Study Groups o o o Security for multimedia systems and services (SG 16) Emergency Telecommunications Services (SG 16) IPCablecom project = interactive services over cable TV networks (SG 9) Telecommunication networks security requirements (SG 2) Framework to support emergency communications (SG 13) Confidence & security in the use of ICT - Malaysia, 21 August 2003 24
Security Studies in other ITU-T Study Groups o o o Security for multimedia systems and services (SG 16) Emergency Telecommunications Services (SG 16) IPCablecom project = interactive services over cable TV networks (SG 9) Telecommunication networks security requirements (SG 2) Framework to support emergency communications (SG 13) Confidence & security in the use of ICT - Malaysia, 21 August 2003 24
 Strengths of ITU-T o Unique mix of industry & government o Truly global o Consensus decisions guarantee wide o o o acceptance Fast procedures Brand name IPR Policy World-class meeting facilities Excellent Secretariat staff Confidence & security in the use of ICT - Malaysia, 21 August 2003 25
Strengths of ITU-T o Unique mix of industry & government o Truly global o Consensus decisions guarantee wide o o o acceptance Fast procedures Brand name IPR Policy World-class meeting facilities Excellent Secretariat staff Confidence & security in the use of ICT - Malaysia, 21 August 2003 25
 Backup Slides on ITU-T (not to be shown in talk) Confidence & security in the use of ICT - Malaysia, 21 August 2003 26
Backup Slides on ITU-T (not to be shown in talk) Confidence & security in the use of ICT - Malaysia, 21 August 2003 26
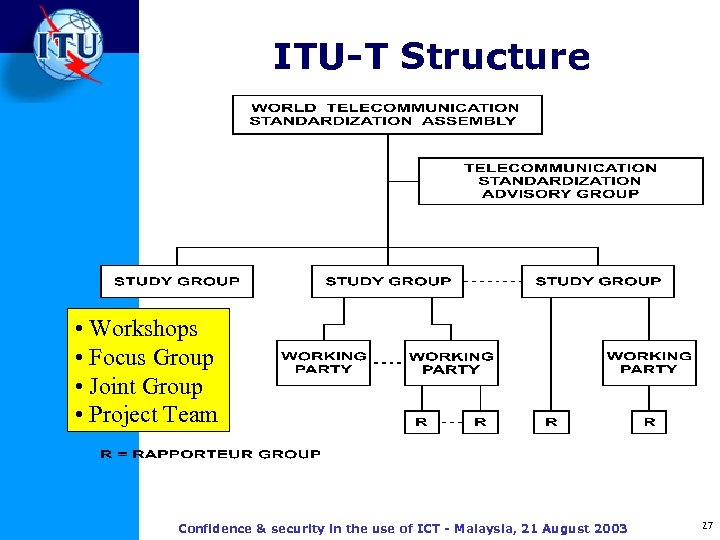 ITU-T Structure • Workshops • Focus Group • Joint Group • Project Team Confidence & security in the use of ICT - Malaysia, 21 August 2003 27
ITU-T Structure • Workshops • Focus Group • Joint Group • Project Team Confidence & security in the use of ICT - Malaysia, 21 August 2003 27
 ITU-T Study Groups o o SG 2 SG 3 o o SG SG o o o o SG 11 SG 12 SG 13 SG 15 SG 16 SG 17 SSG TSAG 4 5 6 9 Operational aspects of service provision, networks and performance Tariff and accounting principles including related telecommunications economic and policy issues Telecommunication management, including TMN Protection against electromagnetic environment effects Outside plant Integrated broadband cable networks and television and sound transmission Signalling requirements and protocols End-to-end transmission performance of networks and terminals Multi-protocol and IP-based networks and their internetworking Optical and other transport networks Multimedia services, systems and terminals Data networks and telecommunication software Special Study Group "IMT-2000 and beyond" Telecommunication Standardization Advisory Group Confidence & security in the use of ICT - Malaysia, 21 August 2003 28
ITU-T Study Groups o o SG 2 SG 3 o o SG SG o o o o SG 11 SG 12 SG 13 SG 15 SG 16 SG 17 SSG TSAG 4 5 6 9 Operational aspects of service provision, networks and performance Tariff and accounting principles including related telecommunications economic and policy issues Telecommunication management, including TMN Protection against electromagnetic environment effects Outside plant Integrated broadband cable networks and television and sound transmission Signalling requirements and protocols End-to-end transmission performance of networks and terminals Multi-protocol and IP-based networks and their internetworking Optical and other transport networks Multimedia services, systems and terminals Data networks and telecommunication software Special Study Group "IMT-2000 and beyond" Telecommunication Standardization Advisory Group Confidence & security in the use of ICT - Malaysia, 21 August 2003 28
 Lead Study Groups o SG 2 o SG 4 o SG 9 o SG 11 o SG 12 o SG 13 o SG 15 o SG 16 o SG 17 o SSG service definition, numbering and routing TMN integrated broadband cable and television networks intelligent networks Quality of Service and performance IP related matters, B-ISDN, Global Information Infrastructure and satellite matters access network transport and optical technology multimedia services, systems and terminals and on e-business and e-commerce frame relay, communication system security, languages and description techniques IMT 2000 and beyond and for mobility Confidence & security in the use of ICT - Malaysia, 21 August 2003 29
Lead Study Groups o SG 2 o SG 4 o SG 9 o SG 11 o SG 12 o SG 13 o SG 15 o SG 16 o SG 17 o SSG service definition, numbering and routing TMN integrated broadband cable and television networks intelligent networks Quality of Service and performance IP related matters, B-ISDN, Global Information Infrastructure and satellite matters access network transport and optical technology multimedia services, systems and terminals and on e-business and e-commerce frame relay, communication system security, languages and description techniques IMT 2000 and beyond and for mobility Confidence & security in the use of ICT - Malaysia, 21 August 2003 29
 IP project study areas o Integrated architecture o Impact to telecommunications access infrastructures of o o o o access to IP applications Interworking between IP based network and switchedcircuit networks, including wireless based networks Multimedia applications over IP Numbering and addressing Transport for IP-structured signals Signalling support, IN and routing for services on IP-based networks Performance Integrated management of telecom and IP-based networks Security aspects Confidence & security in the use of ICT - Malaysia, 21 August 2003 30
IP project study areas o Integrated architecture o Impact to telecommunications access infrastructures of o o o o access to IP applications Interworking between IP based network and switchedcircuit networks, including wireless based networks Multimedia applications over IP Numbering and addressing Transport for IP-structured signals Signalling support, IN and routing for services on IP-based networks Performance Integrated management of telecom and IP-based networks Security aspects Confidence & security in the use of ICT - Malaysia, 21 August 2003 30
 Other areas to consider o IP-based networks and their interconnection with o o o telecommunication networks; IP cablecom project; establishment of GII; IMT-2000 and mobility; e-business and e-commerce; reform of accounting rates and tariff studies; MEDIACOM-2004 project and related multimedia activities; security aspects of networks and services; optical transport network; access networks enhancements with x. DSL techniques; numbering and routing; network performances and quality of services; protocols for new services and intelligent networks. Confidence & security in the use of ICT - Malaysia, 21 August 2003 31
Other areas to consider o IP-based networks and their interconnection with o o o telecommunication networks; IP cablecom project; establishment of GII; IMT-2000 and mobility; e-business and e-commerce; reform of accounting rates and tariff studies; MEDIACOM-2004 project and related multimedia activities; security aspects of networks and services; optical transport network; access networks enhancements with x. DSL techniques; numbering and routing; network performances and quality of services; protocols for new services and intelligent networks. Confidence & security in the use of ICT - Malaysia, 21 August 2003 31
 ITU-T Series (A-L) A. B. C. D. E. F. G. H. I. J. K. L. Organization of the work of ITU-T Means of expression: definitions, symbols, classification General telecommunication statistics General tariff principles Overall network operation, telephone service, service operation and human factors Non-telephone telecommunication services Transmission systems and media, digital systems and networks Audiovisual and multimedia systems Integrated services digital network Transmission of television, sound programme and other multimedia signals Protection against interference Construction, installation and protection of cables and other elements of outside plant Confidence & security in the use of ICT - Malaysia, 21 August 2003 32
ITU-T Series (A-L) A. B. C. D. E. F. G. H. I. J. K. L. Organization of the work of ITU-T Means of expression: definitions, symbols, classification General telecommunication statistics General tariff principles Overall network operation, telephone service, service operation and human factors Non-telephone telecommunication services Transmission systems and media, digital systems and networks Audiovisual and multimedia systems Integrated services digital network Transmission of television, sound programme and other multimedia signals Protection against interference Construction, installation and protection of cables and other elements of outside plant Confidence & security in the use of ICT - Malaysia, 21 August 2003 32
 ITU-T Series (M-Z) M. TMN and network maintenance: international transmission N. O. P. Q. R. S. T. U. V. X. Y. Z. systems, telephone circuits, telegraphy, facsimile and leased circuits Maintenance: international sound programme and television transmission circuits Specifications of measuring equipment Telephone transmission quality, telephone installations, local line networks Switching and signalling Telegraph transmission Telegraph services terminal equipment Terminals for telematic services Telegraph switching Data communication over the telephone network Data networks and open system communications Global information infrastructure and Internet protocol aspects Languages and general software aspects for telecommunication systems Confidence & security in the use of ICT - Malaysia, 21 August 2003 33
ITU-T Series (M-Z) M. TMN and network maintenance: international transmission N. O. P. Q. R. S. T. U. V. X. Y. Z. systems, telephone circuits, telegraphy, facsimile and leased circuits Maintenance: international sound programme and television transmission circuits Specifications of measuring equipment Telephone transmission quality, telephone installations, local line networks Switching and signalling Telegraph transmission Telegraph services terminal equipment Terminals for telematic services Telegraph switching Data communication over the telephone network Data networks and open system communications Global information infrastructure and Internet protocol aspects Languages and general software aspects for telecommunication systems Confidence & security in the use of ICT - Malaysia, 21 August 2003 33


