f069f70057e59e37e27beeffb9d7ee5f.ppt
- Количество слайдов: 117

Interface between Criminal Law & Cyber Crimes Dr K VK Santhy NALSAR UNIVERSITY OF LAW SHAMIRPET HYDERABAD

Emile Durkheim Every organized society has its own quota of transgressive acts and correlated to these its own socially regulated forms of sanction, deterrence and punishment

Cyber Crimes n 1994 – 2008 countries from 83 to 200 countries n 2008 – 1. 59 billion (20 % of the world estimated population) n India 5 th in cyber crime cases n ARPA NET : Pentagon US

Classification of offences • • General law and special law Cognizable and non cognizable Bailable and Non Bailable Compoundable and non compoundable

Cyber Crimes 1. Computer assisted 2. Computer Oriented Computer Assisted Cyber Crimes • Selling non existent, defective, substandard or counterfeit goods, theft of credit card, bank fraud, fake stock shares, intellectual property offences including unauthtorised sharing of the copy righted content of movies, music, digitised books • Selling obscene and prohibited sexual representations.

• Malicious Software: viruses, trojans (which corrupt server) Computer Oriented Cyber Crimes • Cyber terrorism : • Child pornographylders • Violent and extreme pornography • Internet inspired homicides and suicides
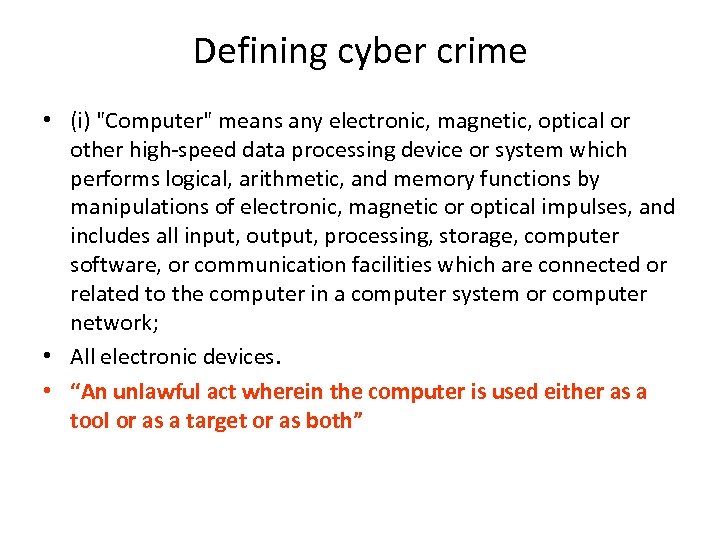
Defining cyber crime • (i) "Computer" means any electronic, magnetic, optical or other high-speed data processing device or system which performs logical, arithmetic, and memory functions by manipulations of electronic, magnetic or optical impulses, and includes all input, output, processing, storage, computer software, or communication facilities which are connected or related to the computer in a computer system or computer network; • All electronic devices. • “An unlawful act wherein the computer is used either as a tool or as a target or as both”

Features of Cyber Crime • • • Uncontrollable and un imaginable damage Anonymity of the accused Transnational Pushing generations into moral depravity Economic aspects of the society Criminalization of the conduct

CHARACTERISTICS OF CYBER CRIME ØANNONIMYTY ØALMOST NO PHYSICAL EVIDENCE/ CLUES ØHIGH IMPACT & INTENSITY ØMANY TIMES FAR AWAY FROM THE SCENE OF CRIME

Electronic devices • • • Karnataka Naxalite Case : casio digital diary Washing machine Mobiles Calculators Pendrives CDs

E-MAIL CHEATING • MR. VIJAY NINWANE WORKS AT ABUDHABI – MADE FRIENDSHIP WITH “X” (A BEAUTIFUL GIRL)CHATING, NUDE PHOTOS, EROTIC STORIES. – “X” INTRODUCED HER FRIENDS Y 1, Y 2, Y 3, Y 4, -----– VIJAY COULDNOT MEET X AS PROMISED – X COMMITED SUICIDE. • VIJAY RECEIVED MAIL FROM – WWW. KOLKATTA_POLICE. COM – WWW. CBI_HQ. COM • VIJAY CONTACTED Y 1 FOR HELP • Y 1 APPOINTED Mr. Pranab mitra of mitra & mitra associates leading lawyers • TOTAL Rs. 70 LAKHS (RS. 1. 19 CRORE AS PER I. O)

WHAT ANALYSIS REVEALED---– ALL WAS DONE BY A SINGLE MAN NAMED MR. PRANAB MITRA, GENERAL MANAGER, -----

KILLING A PATIENT IN COMA BY INJECTING EXCESS OF INSULIN • PATIENT ADMITTED IN NEWYORK HOSPITAL – COMPUTERISED ENVIRONMENT • 3 MODULES • • CRACKER ENTERED THE SYSTEM MODIFIED THE DATA OF 60 mg INTO 260 mg NURSE INJECTED PATIENT DIED

DATA DIDLING • INVOLVES ALTERING THE RAW DATA JUST BEFORE A COMPUTER PROCESSES IT AND THEN CHANGING IT BACK AFTER PROCESSING IS COMPLETED • SECONDARY STATE BOARD : Bihar • PRIVATE STUDENTS TOPPED OVER GOVT STUDENTS – 6 DIGIT ROLL NUMBER • GOVT STUDENTS STARTS WITH 3 • PRIVATE STUDENTS STARTS WITH 4 • SOFTWARE MANIPULATION – FOR ROLL_ NO 3 > 68 <= 100 DEDUCT 9 – FOR ROLL_ NO 4 > 68 < 88 ADD 9

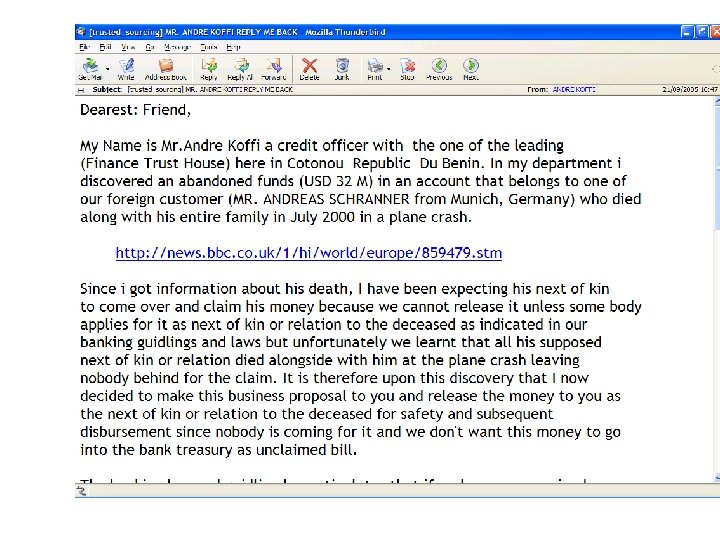
Nigerian Letter Scam • Section 419 of Nigerian Criminal Code • Losses at $5 billion worldwide • Common themes – Child of a dead gold/cocoa merchant. – Son of the most popular (black/white) farmer in Zimbabwe. – The dead bank customer with no heir – Social engineering

PHISHING & PHARMING • PHISHING: – USING SPOOF E-MAILS OR DIRECTING PEOPLE TO FAKE WEB SITES TO FOOL THEM INTO DIVULGING PERSONAL FINANCIAL DETAILS SO CRIMINALS CAN ACCESS THEIR ACCOUNTS. • PHARMING: – TECHNICALLY MORE SOPHISTICATED – EXPLOITATION OF A VULNERABILITY IN THE DNS SERVER SOFTWARE. • 7. 9 MILLION PHISHING ATTACKS PER DAY- – AN INCREASE OF 39% OVER FIRST HALF OF 2005

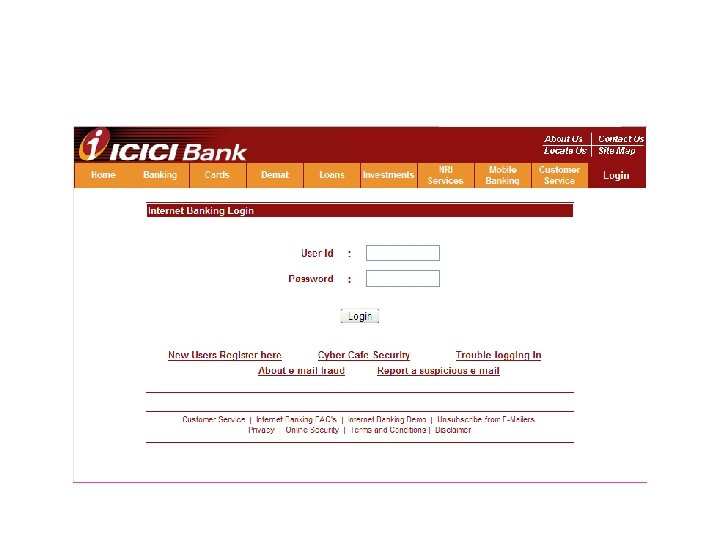
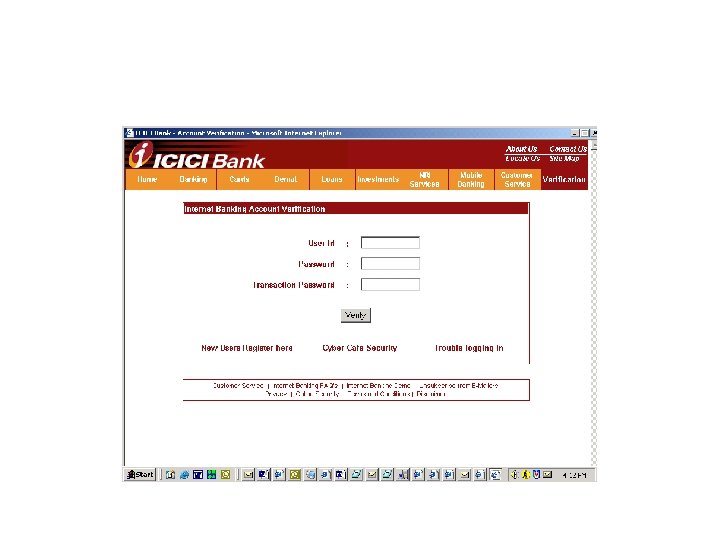
CASE OF ICICI BANK • SUPPORT@ICICI. COM – Asked to validate or conform their account details for verification details – User id’s, login password & transaction password • http: //infinity. icicibank. co. in/verify. jsp • ON CLICKING – TWO WINDOWS – PRESS “ VERIFY TAB” , THE WEB PAGE TAKES YOU TO http: //icici. com WHICH REDIRECTS TO www. icicibank. com • URL http: //all-about-notebooks. com/icici/verify. php • ICICI NEITHER OWNS NOR IN ANY CONNECTED WITH THE SAID URL • IP ADDRESS 61. 141. 32. 181

PARLIAMENT ATTACK CASE • DELHI POLICE SEIZED A LAPTOP WHERE THEY STORED THE INCRIMINATING MATERIAL. • ON FORENSIC ANALYSIS: – HOW THE COMPUTER WAS USED TO PRODUCE THE MHA STICKER – IP ADDRESSES OF PAKISTAN – TELEPHONE NUMBERS – CODED MESSAGES


QUESTIONS DEFENCE RAISED (IN P-ATTACK CASE) • CAN THE HARD DISK OF A COMPUTER CAN BE CHANGED ? • CAN THE CLOCK OF A COMPUTER CAN BE CHANGED ? • WHY A BACK-UP OF HARD DISK WAS NOT TAKEN? • TIME STAMPS ?

Malicious Software • Virus : a self replicating programme that spreads by infecting some form of existing entity as a ‘carrier’. Ex, Boot sector viruses – disks programme virus – executable files. macro virus – documents and spread sheets.

Worm- Trojan- Spy ware v. Worm : Self replicating programmes, spread Worm autonomously without a carrier. Ex. Via mail, Scanning remote systems v. Trojan : installed during downloading some Trojan programme as a back ground activity causing irreparable damage v. Spyware : parasitic software-invades privacy. Spyware divulging details- through tracking cookies. v. National Cyber Security Alliance, 2005, 6 out of 10 domestic pc had spyware.

Some examples • Melissa Virus (1999) : contained some important information they had requested. • Love Bug worm (2000) : Love Letter • Aka dworf worm (2007) : e card greeting • Strom Worm Jan 2007 to 2008 : 18 months • Zombie army and bot net

Hacking • Refers to activities involved in attempting or gaining un authorised access to IT systems. • Attacks against systems in the office of the US Secy of defence in June 2007, alleged to be sponsored by chinese hackers backed by the Peoples Liberation Army. • Targetting the web mail of US vice presidential candidate and Alaskan Governor, Saarah Palin during 2008 campaign, leading to her messages being posted in a public website. • Sec 66 of IT Act

Email Spoofing • a Pune based businessman received an email from the Vice President of the Asia Development Bank (ADB) offering him a lucrative contract in return for Rs 10 lakh. The businessman verified the email address of the Vice President from the web site of the ADB and subsequently transferred the money to the bank account mentioned in the email. It later turned out that the email was a spoofed one and was actually sent by an Indian based in Nigeria.

Cyber Stalking • Cyber stalking is when a person is followed and pursued online. Their privacy is invaded, their every move watched. It is a form of harassment, and can disrupt the life of the victim and leave them feeling very afraid and threatened

Hacking • Refers to activities involved in attempting or gaining un authorised access to IT systems. • Attacks against systems in the office of the US Secy of defence in June 2007, alleged to be sponsored by chinese hackers backed by the Peoples Liberation Army. • Targetting the web mail of US vice presidential candidate and Alaskan Governor, Saarah Palin during 2008 campaign, leading to her messages being posted in a public website. • Sec 66 of IT Act

What is crime? • Latin ‘Crimen’ – Sanskrit ‘krama’ – crime • Section 32 IPC when a penal statute prescribes punishment for an act or illegal omission, it becomes crime. • Crimes are invasions of primary personal rights, abhorrent to the moral sense, prescribed by positive law, crime is inherently evil.

Criminal law principles Deviant or crooked conduct prohibited by law can attract either civil or criminal or at times both criminal and civil liabilities. Crime has two victims: individual and societal State wants criminal to be punished. Individual has a civil remedy – civil wrong Punishment is organized and legally sanctioned state revenge against the offender.

Criminals in virtual world Omnipresence of Cyber space links online activity to physical location. Local Governments are not in a position to control online mis-behavior nor have physical jurisdiction. While crime is individual, cyber crime generally is international and against many persons at a time. Criminal is invisible. Privacy, emotional physical safety and data security is threatened.

Civil & Criminal Justice: Differences • Criminal Justice • to punish wrongs • purpose- penal-except warning, censure • Trial on Charges, guilt or innocence • public wrongs-More harmful • State is a party • Civil Justice system • to enforce rights • purpose is remedial, - heavy damage • On issues, determining rights and liabilities • Pvt wrongs injury to private individuals • Pvt individuals

Criminal law • • Retribution – Criminal law, penology Restitution – civil law – victimology Crime should be predefined, Article 20 Civil wrong need not be. Natural justice and violation of rights.

Criminal, not crime • I Love you (information resources under seize) introduced by student of Philippines, during 2000. • He could not be punished because the ‘introduction of virus’ was not an offence under Philippines law. • Virus is very advanced, it hides itself from being detected. Hits target silently, destroy data and cause banking frauds.

Constitution and criminal law Article 20: No person shall be convicted of any offence except for violation of a law in force at the time of the commission of the act charged as an offence, nor be subjected to a penalty greater than that which might have been inflicted under the law in force at the time of the commission of the crime. No person shall be prosecuted and punished for the same offence more than once. No person accused of any offence shall be compelled to be a witness against himself. Art 21: No person shall be deprived of life or personal liberty except according to procedure established by law.

Elements of crime • Actus reus – prohibited conduct, ie there should be a prohibition by law. Not retrospective, always prospective. • Mens rea – blameworthy state of mind – bad intention, recklessness, negligence, criminal knowledge, voluntarily, dishonestly, fraudulently

Constituent elements of crime • Actus non facit reum nisi mens sit rea = • Act does not constitute guilt unless done with a guilty intent, legally blameworthy attitude of mind • Two elements; physical element - actus reus and mental element – mens rea, guilty knowledge or intention.
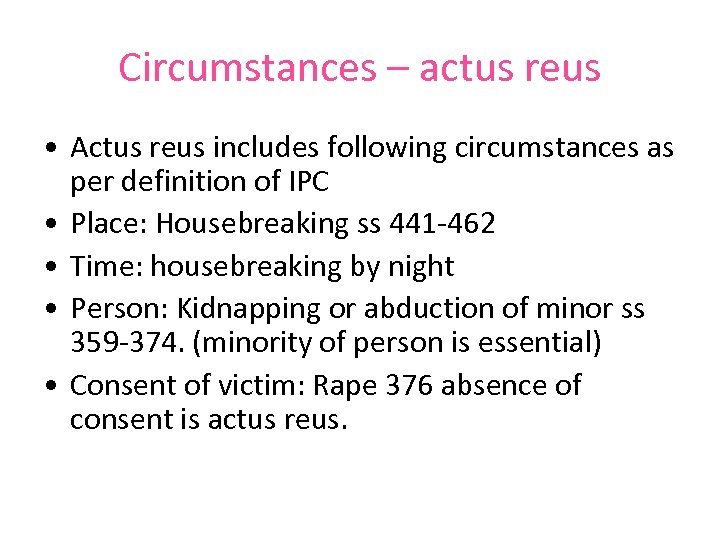
Circumstances – actus reus • Actus reus includes following circumstances as per definition of IPC • Place: Housebreaking ss 441 -462 • Time: housebreaking by night • Person: Kidnapping or abduction of minor ss 359 -374. (minority of person is essential) • Consent of victim: Rape 376 absence of consent is actus reus.

Actus reus - circumstances • State of mind of victim: Putting a victim in fear of death or hurt for rape, s 375(3) • Possession: of Stolen Property S 410 -412 • Preparation: to commit robbery, s 399

Participation & causation • It is participation and causation of crime including indirect participants like accessories, abettors, conspirators, • Participation may be thru innocent agents

Thought & Action • Actus reus sometimes combines both the act and intention which constitute criminal conduct. • Unless evil thoughts are put to action, not punishable. • It is unjust, impracticable and inequitable to punish a mere criminal thought

Participation & causation • Harris gives an example: A, intending to kill B shot at him but wounds him slightly, here actus reus is to the extent of attempt and causing injury not murder. B is killed when he is on ambulance, there is participation by A initially but there is no causation of death.

Causation & Intervention A wounded B, B refused to get his finger amputated, which might have saved him. Is A guilty of Murder? Whether intervention is strong to break the chain of causation? (R. v. Holland, 1981 Kenny 25 held guilty) R v Jordan, 1956 40 Cr App Rep 153 J stabbed D, who was stitched, healed and treated. Not tolerant to terromycin, caused pneumonia and died. Is the injury caused by J immediate cause of death? no

R v. Smith, 1959 A, soldier accused of killing B, another soldier. B suffered bayonet injuries, bled & suffered hemorrhage. While C took him to hospital he was dropped twice. There was no blood transfusion at hospital. Soldier died within 2 hrs of injury. Is A guilty? Death should be natural and sole cause of injury. If chain of causation is established, A is guilty.

DG of Prosecution v Smith • 1960 (3) AER 161. X was driving car with stolen property. A police officer chased, hung on to that car, he was thrown off and killed in the process. Is he guilty? • Examine intention, knowledge, recklessness of driver for imputing liability. • Any reasonable man contemplates consequences of fatal driving.

R v Blaue, 1975 AER 446 • Accused stabbed a Jehova witness, who refused blood transfusion, which might have saved her life. • Whether accused can be held guilty? • What decides the liability issue?

Was he guilty? Whether stab wound is operative cause of death? What about contributory negligence of victim? Accused held guilty because refusal for transfusion of blood was held not to be a substantial factor which did not break causal connection and contributory negligence is not relevant in fixing criminal liability. Stab wound was operative cause of death because of intensity of stabbing, which also spoke about intention.

Causa causance • Immediate cause of the effect • If result is remote or accidental, there is no liability • Intervention breaks the causation • Intervener may be liable if proved to be cause of death. Participation and causation is important in actus reus

Mens rea and Law in India • Each definition of crime is complete and it constitutes mens rea as part of it. • IPC does not separately mention mens rea generally. • Mens rea applied in different ways such as fraudulently, dishonestly, voluntarily, and intentionally etc indicate need of criminal intent.

No mens rea • In offences like waging war, s 121, sedition s 124 A counterfeiting of coins s 232 etc mens rea is avoided totally • Separate chapter on General Exceptions ss 76 – 106 indicate circumstances where absence of criminal intent may be presumed it is negative method of applying mens rea in IPC

Dishonestly • S 24 defines: intention of causing wrongful gain to one person or wrongful loss to another, dishonestly refers to property • S 25 : A person is said to do a thing fraudulently, if he does that thing with intent to defraud but not otherwise • Legal fraud includes intention to injure besides deception.

Deception and fraud Deception could be moral wrong, fraud in legal sense is an offence (inclusive of injury), deception may not be fraud, but fraud involves deception S 206 IPC fraudulent removal or concealment of property from execution is an offence S 208 to cause a decree for a sum not due or for a larger sum than is due S 463 making false document with intent to commit fraud is forgery.

Knowingly • Personal knowledge • It may also be implied, when he deliberately omits to inquiry, willful blindness • A child brings new bicycle, father does not question. He realised probability of cycle being stolen, guilty.

Strict Liability • Criminal liability independent of wrongful state of mind or culpable negligence • Strict or absolute liability principles • Three kinds of crimes which do not require legal fault on accused: • Public welfare offences: quasi criminal in nature, drugs, foods, weights & Measures, licensing, traffic, revenue offences etc.

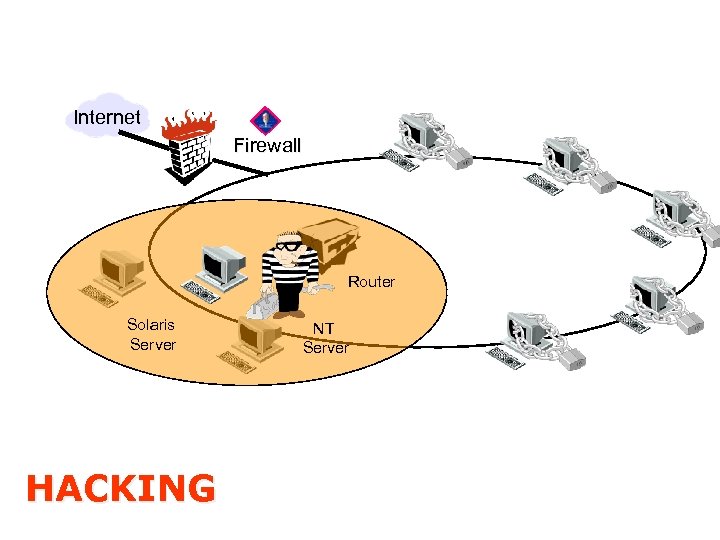
Cyber Crimes • Criminal activities in cyberspace, using internet • Unlawful acts where computer is either a tool or target • Crimes that can be committed ordinarily and in cyber space • Crimes that can be committed only in cyber space
lnternet Firewall Router Solaris Server HACKING NT Server

Crimes and Cyber crimes IPC, Section 441: Criminal Trespass Unauthorized entry Unlawful stay Intention to commit crime S 43 + S 66 IT Act: Hacking Unauthorized access to information systems Disruption, interference Introduction of malicious software Downloading, extraction copying Destroying altering info Stealing, concealing, altering computer source code. 1 crore, 3 yrs, 1 lakh

Trespassing Occupying / taking over possession of others property Destroying the property Denying the access to original owner of property Committing crimes from that property Cyber-squatting or Hacking: Cyber version of trespassing- Occupying other’s space, Destroying their data. Virus. Launch of malicious programs - consisting of payload, damaging source code. Remains dormant, unaffected until triggered. It ranges from innocuous message to collapse of system.

Cyber wrongs and cyber crimes Unauthorized access, Unauthorized downloading or extracting of information Introduction of virus Damages the system of data Disruption of the system etc Denies the person authorized, access to his own system or data Facilitates access to unauthorized persons Charges for the services to another’s account by manipulating Destroys the data or diminishes its value, Steals, conceals, or destroyes or alters the computer source code, (One Crore Compensation) Any Corporate neglects to adopt and maintain reasonable security practices (compensation five crore Rupees) (S 43 A) If the same act is committed dishonestly, or fraudulently he shall be punished with imprisonment up to 3 years plus fine up to 5 lakh rupees, as per Section 66

Who is hacker? a hacker is ‘a person or thing that cuts roughly’ or ‘a person who uses computers for a hobby especially in gaining unauthorised access to data (Oxford English Dictionary): Six hackers are (a) A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to many users, who prefer to learn only the minimum necessary; (b) A person who enjoys the intellectual challenge of overcoming or circumventing limitations; (c) A person good at programming quickly; (d) An expert in a particular language; (e) A person who programs enthusiastically; (f) A malicious meddler who tries to discover sensitive information by poking around.
WEB DEFACEMENT You’ve been hacked. . . Dept of Justice US
WEB DEFACEMENT You’ve been hacked. . . CIA

Hacked Liverpool hospital in 1994 and changed the medical prescriptions. A nine-year-old patient who was given a highly toxic mixture was saved by a nurse who decided to re-check his prescription. Wanted to see confusion and mayhem arising out of tampering with hospital computers. An underworld don who was injured by a gun shot was killed by a drug overdose which was caused by alteration of the original prescription by a hacker. (New York) A hacker altered 60 mg to 260 mg insulin prescription, led to death Cyber murder

Destroying Code • S 65 IT Act: Knowingly or intentionally, himself or through another – Conceals – Destroys – Alter Any computer source code – Used for computer – Computer programme – Computer system – Computer network Where such source code is required to be kept or maintained • Punishment : 3 Years or Fine 2 Lakh INR or Both

Crimes on cyber space Sending offensive messages, causing annoyance, inconvenience, to deceive etc , S 66 A Dishonestly receiving stolen computer resource or device. 66 B (3 yrs imp + one lakh) Identity theft, stealing password, 3 years plus one lakh, 66 C Cheating by personation using computer source, 66 D, 3 yrs + One lakh Violation of privacy, S 66 E 3 yrs + 2 Lakh
![Other Offences • Misrepresentation [section 71] – 2 Years or Fine or Both • Other Offences • Misrepresentation [section 71] – 2 Years or Fine or Both •](https://present5.com/presentation/f069f70057e59e37e27beeffb9d7ee5f/image-68.jpg)
Other Offences • Misrepresentation [section 71] – 2 Years or Fine or Both • Breach of confidentiality and privacy [section 72] – 2 Years or Fine or Both • Publication for fraudulent purpose [section 74] – 2 Years or Fine or Both

Fraud and cyber fraud • Fraud • 415 to 420 IPC • S 25 what is fraudulently • Intention to deceive • Actual or possible injury Cyber fraud Spam emails Email frauds Online investment newsletters • Nigerian fraud • •

Cyber cheating • Online fraud and cheating are some of the most lucrative businesses that are growing today in the cyber space. Credit card crimes, contractual crimes, offering jobs, prizes etc • (R. v. Preddy (1996)3 ALL ER 481 - traditional criminal concepts should not be applied to online fraud or any other form of intangible information)

Fraud: Maxim Scam • 19 -year old Russian student using the name `Maxim' stole 300, 000 credit card numbers from the computer server of CD Universe. Maxim extorted CD Universe by agreeing to destroy the customer data he had stolen in exchange for $100, 000 cash. Maxim is still at large.
Levin Hacking fraud -1 Russian hacker Vladimir Levin accessed the computers of Citibank’s central wire transfer department, and transferred funds from large corporate accounts to other accounts which had been opened by his accomplices in the United States, Netherlands, Finland, Germany and Israel

Fraud - 2 • Officials from one of the corporate victims in Argentina notified the bank and the suspected accounts, located in San Francisco were frozen. • Accomplices were arrested when came to withdraw amounts. • Levin arrested when visited US and imprisoned in 1999

Kola Mohan’s cyber lottery fraud Kola Mohan (AP) created website & email 'eurolottery@usa. net. ‘ showing him as beneficiary of 12. 5 million pound in Euro lottery. After confirmation of email address, a telugu newspaper published this as news. Using this, he gathered huge sums from the public as well as from some banks. Fraud came to light when a cheque for Rs 1. 73 million discounted by him with Andhra bank got dishonored.

Modifying routines • Trojan horse can be programmed to self destruct, leaving no evidence of its existence except the damage that it caused • 13 remote access capabilities also allow criminal to easily run modified routines concurrently with legitimate programmes
Output manipulation • Example is cash dispenser fraud, achieved by falsifying instruction to the computer at the input stage. This fraud involves the use of stolen bank cards. • Now specialized hardware and software is used to encode falsified electronic information on the magnetic strips of bank cards and credit cards.

Automatic repetitions • Another species of fraud: by computer manipulation that takes advantage of the automatic repetitions of computer processes • Thin slices of financial transactions are repeatedly removed and transferred to another account, not at all noticeable.

Spoofing • Electronic impersonation is colloquially called spoofing, which can be used in furtherance of variety of cyber crimes • Technologies of anonymity further complicate the task of identifying a suspect • Fraudsters escape by means of ‘looping’ or ‘weaving’ through multiple sites in a variety of nations.
Mischief • Mischief 425 to 440 IPC • Intention to cause wrongful loss • Act causing destruction of property • • • Section 43 of IT Program manipulation Output manipulation Data alteration Computer vandalism
Forgery – Electronic forgery “ A person is guility of Computer forgery - forgery if he makes a criminal gets access to false instrument with the data kept on a computer intension that he or and alters it making another shall use it to computers as targets for induce somebody to criminal acts. accept it as genuine”. IPC 464 amended to Chris Reed and John include electronic Angel “ Computer Law” forgery. 4 th Ed, Blackstone Press 29 A defined it. p. 281

Electronic forgery • Section 463 of the IPC (after amendment) defines forgery, in relation to the electronic record, as making any false electronic record or part therefore with an intent to cause damage or injury to the public or to any person, or to enter into any express or implied contract, or with intent to commit fraud or that fraud may be committed.

Computer forgery in AP tax case • Rs. 22 Crore was recovered from the house of the owner of a plastic firm by the sleuths of vigilance department, • Generated 6000 vouchers to legitimize the amount recovered, • Made after the raids were conducted. • Fake computerized vouchers
IPC sections changed • Section 468, 469, 470, 471, 474, 466 amended to include ‘electronic records’ to punish electronic forgery.
Theft – cyber theft Physical theft, possession of property shifts from owner S 378: Intends to take dishonestly any movable property out of possession of any person, without consent moves that property. (s 22 corporeal property, not attached s moveable property) Cyber theft – no complete shifting of possession of property from owner Data theft (s 2 ‘data’) S 43 Data theft – illegally copied, or taken without knowledge. Data is intangible so not movable property, data stored in a medium (CD pen-drive computer) medium is property so covered by IPC.

Data is property HSBC – customer credit card info was passed on, which led to Rs. 1. 8 crore scam. ACME Telepower Pvt Ltd. Patented Product Power Interface Unit, valued 750 crore, an employee leaked to rival Lambda Eastern Telecom ltd, ACME shifted its 10 million R&D unit to Australia. Abhinav Guptha v State of Haryana, 2008 Cr. LJ 4536, JCB India’s employee resigned on a condition that he would not join a rival company. He was uploading the data, drawings of JCB. Data, trade secrets was stolen, amounts to hacking, anticipatory bail rejected.

Theft on high scale Criminals hacked the data base of Card system solutions and took up to 200, 000 visa, Master. Card and American Express credit cards. High tech companies in Israel where alleged to have planted surveillance software on computers of their business rivals. In 2004 the United Kingdom lost approximately 3 billion pounds due to unauthorised access to computer systems, data threat, virus attacks and financial frauds. See: Nuurrie weekly newspaper http: //www. nuurrie. com/section. asp? section=10 ( accessed on 26 -03 -08)

Outraging – cyber stalking • 354: Outraging modesty of woman • Unwarranted advancement – harassment • 509 insult to modesty of woman, intrudes upon privacy etc • Cyber stalking – sexual harassment • Section 72 IT • Breach of confidentiality • Privacy • Showing or sending porn etc.

Harassment: Online abuse • “A course of conduct directed at a specific person that causes substantial emotional distress in such person and serves no legitimate purpose” or words, gestures and actions which tend to annoy, alarm and abuse (verbally) another person”. Black’s law dictionary. • ‘Working to halt online abuse, http: //www. haltabuse. org/help/isit. shtml

Cyber stalking is the use of the internet, e-mail or other electronic communication devices to stalk another person. Repeated threatening, harassing phone calls, sending harassing messages or objects or even destroying victim’s property. Track their targets through the net in chartrooms, message boards, newsgroups or even mailing lists in which their victims actively take part. befriending their target’s friend’s to get more information about victims.

Try CS under s 509 • Ritu Kohli, registered first cyber stalking case. • A friend of her husband gave her phone number and name on a chat site for immoral purposes. • Being a computer expert, Kohli was able to trace the culprit. • Trial began for "outraging the modesty of a woman", under Section 509 of IPC.
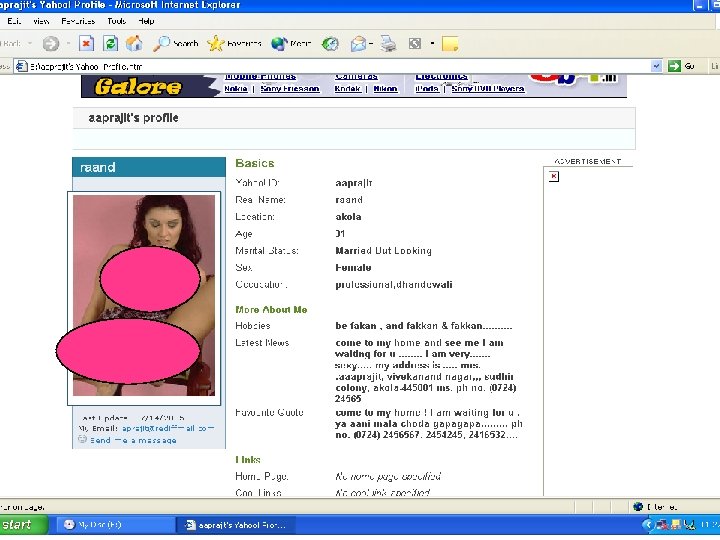

Cyber harassment • “Like to have sex with any person of age group above 30, Call My Residence” • - Mrs X, email id, phone, address etc • This was posted on www. indiatimes. com in romance column • Her mail id, phone etc were real. • Content is created to harass her. Sangeetha Rane complained to PS.

Case of obscene, defamatory and annoying message about a divorcee in the yahoo message group. E-Mails were also forwarded to the victim from a false e -mail in the name of the victim. Annoying phone calls flooded believing that she solicited sexual relationship. Accused was her family friend. Interested in marrying her. Her marriage with another ended in divorce. His proposal was refused. Convicted under sections 469, 509 IPC and 67 of IT Act 2000 First case of conviction under IT Act. (2+1+2 yrs of Imp concurrent. Rs 500 x 2 fine imposed. Nov 4, 2005, Judge Arulraj, Addl Chief Metro Mag, Egmore. Tamil Nadu Vs Suhas Katti
Cyber Defamation Crime of Defamation IPC s 499 Both a crime and a civil wrong. Online: SMC Pnumatics v Jogesh Kwatra, J was sending malicious emails to SMC bosses. Delhi HC Held, Abusive, vulgar, obscene, intimidating humiliating etc, Permanently restrained as prayed by SMC

Cyber terrorism • Cyber terrorism, with an intention to threaten integrity or security of nation denying access to computer source, or penetrating into, or introducing computer contaminant, (B) exceeding the authority to access or unauthorizedly access to the restricted data with an intention to threaten security, sovereignty etc. imp for life, 66 F

• Hidden messages behind photos and music albums: “broche varevarura” : how to use a missile • Aiswarya Rai Photo: Where to bomb Steganography
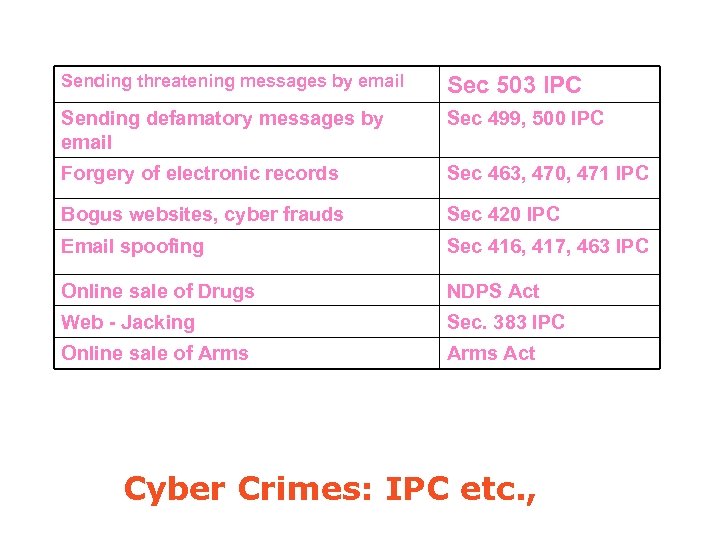
Sending threatening messages by email Sec 503 IPC Sending defamatory messages by email Sec 499, 500 IPC Forgery of electronic records Sec 463, 470, 471 IPC Bogus websites, cyber frauds Sec 420 IPC Email spoofing Sec 416, 417, 463 IPC Online sale of Drugs NDPS Act Web - Jacking Sec. 383 IPC Online sale of Arms Act Cyber Crimes: IPC etc. ,

• Criminal breach of trust/Fraud- Sec. 405, 406, 408, 409 IPC • Destruction of electronic evidence. Sec. 204, 477 IPC • False electronic evidence-Sec. 193 IPC • Offences by or against public servant. Sec. 167, 172, 173, 175 IPC Cyber Offences IPC

• If punishable with death, imprisonment for life or imprisonment for more than 7 years: cognizable, Non- Bailable, Court of Session • If punishable with imprisonment for 3 years and upwards but not more than 7 years: Cognizable, Non-Bailable, Magistrate of First Class • If punishable with imprisonment of less than 3 years: Non-Cognizable, Bailable, Any Magistrate ( or Controller of CAs) Cognizable, Bailable…

Compounding offences • Compounding offences, Except those which are punishable with imp for more than three years and life, are compoundable offences, Sec 77 A • Offences with three years shall be cognizable, others not. 77 B • Inspector rank officer to investigate, 78

Investigation ss 28, 29 • Controller/any officer authorised by him • shall exercise powers such as those of Incometax authorities • have access to any computer system, any apparatus, data or any other material connected with such system, for the purpose of searching or causing a search to be made.

Proof / Evidence • • Fragile Collection of evidence Preservation of evidence Seizure Need to have an Expert Daubert rule : repeatable, reproducible and retested. Daubert rule Locard Exchange Principle : “Wherever he steps, whatever he Locard Exchange Principle touches, whatever he leaves, even unconsciously, will serve as a silent witness against him. Not only his fingerprints or his footprints, but his hair, the fibers from his clothes, the glass he breaks, the tool mark he leaves, the paint he scratches, the blood or semen he deposits or collects. All of these and more, bear mute witness against him. This is evidence that does not forget. It is not confused by the excitement of the moment. It is not absent because human witnesses are. It is factual evidence. Physical evidence cannot be wrong, it cannot perjure itself, it cannot be wholly absent. Only human failure to find it, study and understand it, can diminish its value. ”

FEW QUESTIONS-- • ANY DIFFICULTY IN GATHERING THE EVIDENCE – IDENTIFICATION OF THE EVIDENCE – CAN YOU SWITCH ON THE COMPUTER TO SEE WHERE IS THE EVIDENCE ? • BY KEEPING QUICK LEADS TO INVESTIGATION IN MIND – DATE & TIME STAMPS » EVIDENTIAL INTEGRITY • IS IT IN A READABLE FORMAT ? – MAY BE » ENCRYPTED » PASSWORD PROTECTED – CAN YOU SWITCH OFF THE COMPUTER IF THE SYSTEM IN ON MODE • FATE OF VOLATILE DATA (EVIDENCE) • LEGAL ADMISSIBILITY OF EVIDENCE ?

WHAT YOU CAN EXPECT FROM CYBER FORENSIC ANALYST ? v. DATA RETRIVEL FROM FORMATTED DISKS, DEFRAGMENTATION DISKS ---v. E- MAIL TRACING v. E-MAIL BOX RECOVERY v. RECYCLE BIN v. FORENSIC ANALYSIS OF MOBILE PHONES

CYBER FORENSICS Investigation • WHAT’S POSSIBLE? – RECOVERY OF DELETED DATA – DISCOVERY OF WHEN FILES WERE MODIFIED, CREATED, DELETED, ORGANIZED – CAN DETERMINE WHICH STORAGE DEVICES WERE ATTACHED TO A SPECIFIC COMPUTER – WHICH APPLICATIONS WERE INSTALLED, EVEN IF THEY WERE UNINSTALLED BY THE USER – WHICH WEB SITES A USER VISITED… • WHAT’S NOT… – IF DIGITAL MEDIA IS COMPLETELY (PHYSICALLY) DESTROYED, RECOVERY IS IMPOSSIBLE – IF DIGITAL MEDIA IS SECURELY OVERWRITTEN, RECOVERY IS VERY, VERY COMPLICATED, OR IMPOSSIBLE

Police Powers S 80 Any police officer[ not below the rank of a Inspector of Police or any other officer of the Central Government / State Government authorised by the Central Government in this behalf may enter any public place and search and arrest without warrant any person found therein person who is reasonably suspected or having committed or of committing or of being about to commit any offence under this Act

An appeal from an order made by Controller or an adjudicating officer under this Act lies to Cyber Appellate Tribunal having jurisdiction in the matter. However, no appeal shall lie to the Cyber Appellate Tribunal from an order made by an adjudicating officer with the consent of the parties. Every appeal shall be filed within a period of forty-five days from the date on which a copy of the order made by the Controller or the adjudicating officer is receive Endeavour shall be made to dispose off the appeal finally within six months from the date of receipt of the appeal. Cyber Appellate Tribunal [S 57]

Extension of IPC Any person liable by any Indian Law, to be tried for offence committed beyond India shall be dealt with under IPC, in the same manner as if such act had been committed in India. (Section 3) IPC applies to any offence committed by any citizen of India in any place without and beyond India; any person on any ship or aircraft registered in India wherever he may be.

Crimes outside India • Section 75 of the IT Act clearly lays down that its provisions shall also apply to "any offence or contravention committed outside India by any person, irrespective of his nationality", provided that such act involves a computer, a computer system or computer network located in India.

State’s arm extends Attorney General of Minnesota sought to regulate online gambling by asserting that a state will have jurisdiction over any cyber issue since accessing a webpage is as good as ‘bringing’ the site into the territorial jurisdiction of the state in which it is viewed. The Minnesota Attorney General’s Office distributed a Warning to All Internet Users and Providers, available at <http: //www. state. mn. us/cbranch/ag/memo/txt> (visited 26/03/2008).

Cyber Transactions & Electronic Evidence • International Organization on Computer Evidence IOCE 1995 • With accredited Government Agencies involved in cyber forensic investigations • For exchange of information • Task is to develop international standards for exchange and recovery of electronic evidence

Working group • Working groups in Canada, Europe, UK and USA proposed standards: • Consistency with all legal systems • Allowance for use of a common language • Durability, ability to cross international borders • Ability to instill confidence in the integrity of evidence

Standards • Applicability to all forensic evidence and • Applicability at every level – individual, agency and country level

Approval International Hi-Tech Crime & Forensics Conference IHCFC October 1999 discussed and developed these principles into: Upon seizing digital evidence, actions taken should not change that evidence Forensically competent person alone should access original digital evidence All activity relating to seizure, access, storage, transfer of digital evidence must be fully documented, preserved, and available for review

Principles approved • The individual will be responsible for all actions taken with respect to digital evidence in his possession • any agency that deal with the digital evidence should be responsible for compliance of these principles.

Conclusion Prevention and punishment of crime is responsibility of the state. There should be uniform criminal law to curb these crimes in the whole of the world. Law has to recognize electronic documents, transactions and accept them in the court of law Further investigation to secure the identity of the cyber criminals, so that the state agencies can detect, prosecute and punish.
Thank you for your attention Any questions?
f069f70057e59e37e27beeffb9d7ee5f.ppt