813e1bbc4f78d19191e670d9736f3f2d.ppt
- Количество слайдов: 18

Interacting with NDG Bryan Lawrence (on behalf of a big team) + + +[ BADC, BODC, CCLRC, PML and SOC ]=
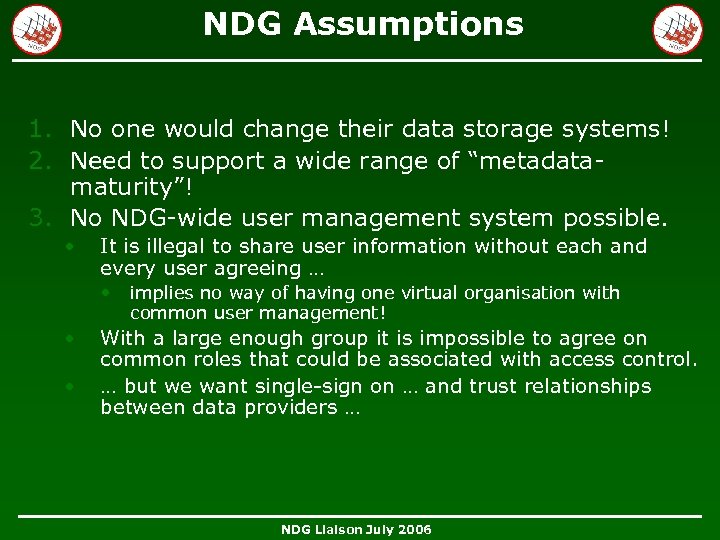
NDG Assumptions 1. No one would change their data storage systems! 2. Need to support a wide range of “metadatamaturity”! 3. No NDG-wide user management system possible. • It is illegal to share user information without each and every user agreeing … • • • implies no way of having one virtual organisation with common user management! With a large enough group it is impossible to agree on common roles that could be associated with access control. … but we want single-sign on … and trust relationships between data providers … NDG Liaison July 2006
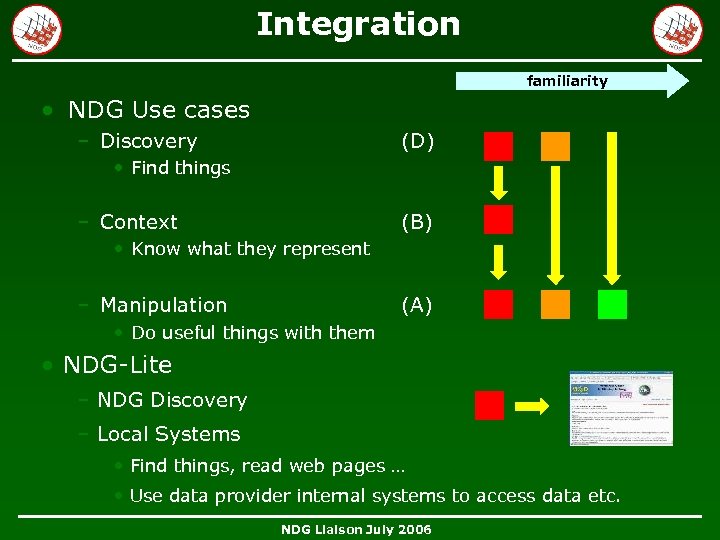
Integration familiarity • NDG Use cases – Discovery (D) • Find things – Context (B) • Know what they represent – Manipulation (A) • Do useful things with them • NDG-Lite – NDG Discovery – Local Systems • Find things, read web pages … • Use data provider internal systems to access data etc. NDG Liaison July 2006
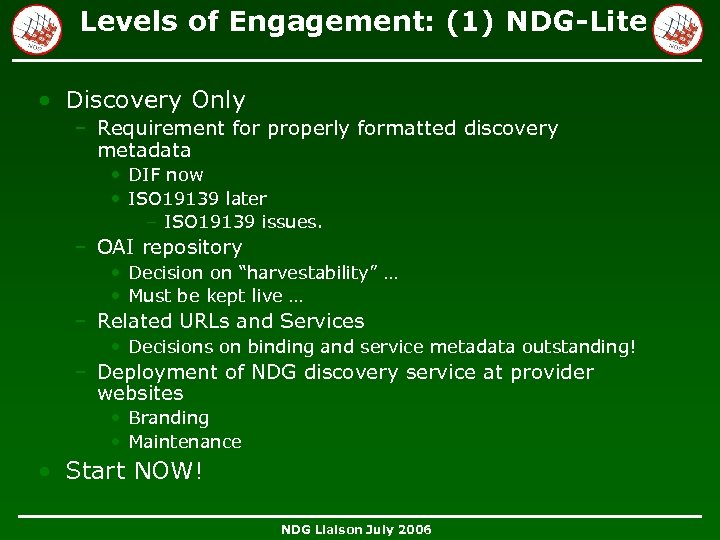
Levels of Engagement: (1) NDG-Lite • Discovery Only – Requirement for properly formatted discovery metadata • DIF now • ISO 19139 later – ISO 19139 issues. – OAI repository • Decision on “harvestability” … • Must be kept live … – Related URLs and Services • Decisions on binding and service metadata outstanding! – Deployment of NDG discovery service at provider websites • Branding • Maintenance • Start NOW! NDG Liaison July 2006
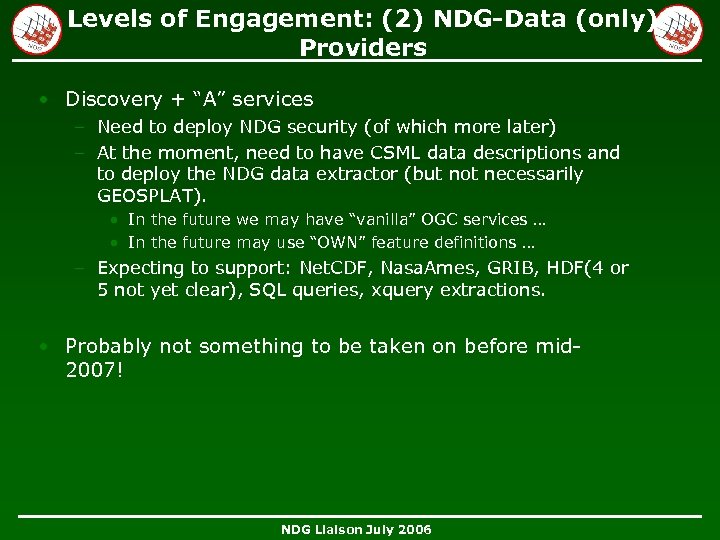
Levels of Engagement: (2) NDG-Data (only) Providers • Discovery + “A” services – Need to deploy NDG security (of which more later) – At the moment, need to have CSML data descriptions and to deploy the NDG data extractor (but not necessarily GEOSPLAT). • In the future we may have “vanilla” OGC services … • In the future may use “OWN” feature definitions … – Expecting to support: Net. CDF, Nasa. Ames, GRIB, HDF(4 or 5 not yet clear), SQL queries, xquery extractions. • Probably not something to be taken on before mid 2007! NDG Liaison July 2006
Levels of Engagement (3): Data Centres and Browse • We only expect data centres to engage in the time and expense of producing browse metadata! – MOLES is/will be a coat-hanger for discipline specific metadata, with some holes for common concepts. – We will provide tooling for a MOLES repository to autogenerate discovery metadata (one less job to do!) – Provides the basis for cross-data centre thematic repositories (e. g. RAPID) – Can be secure metadata in own right! NDG Liaison July 2006

Authentication and Authorisation Clean separation between concepts: • Authentication – Identity - Who you are – Users are identified between data providers and services by means of Proxy Certificates – Proxy Certificates issued by My. Proxy services – Users are identified between sessions at the same browser by means of a cookie which points to the location of a proxy certificate. • Authorisation – For a user: what you can do e. g. what data they can access – For a data provider: how you determine what a user can and can’t do – NDG Attribute Certificates determine access – Attribute Certificates issued by Attribute. Authorities. NDG Liaison July 2006
Controlling Access to Data • NDG Attribute Certificate – Issued to a user by an ATTRIBUTE-AUTHORITY – Contain roles – these determine what the user is authorised to do • An attribute authority determines on behalf of a data provider what roles a user has, from the list of roles known to that data provider • e. g. badc has the coapec role which allows access to the coapec data set. If a badc user has a badc issued Attribute Certificate containing coapec then badc will grant access. – XML based – Issued by the Attribute Authorities on receipt of a valid user Proxy Certificate – Digitally signed by the Attribute Authority issuer – Contain the user’s identity expressed as a Distinguished Name as derived from the user’s Proxy Certificate – Has a timebound validity NDG Liaison July 2006
Key Concepts thus far • All data providers deploy, or have access to, a myproxy database capable of delivering proxy certificates on request. • All data providers deploy or have access to a Session Manager instance. – No requirement for the myproxy to visible outside a firewall, access can be mediated by a Session Manager. • All data providers secure resources by coupling resources to roles. – There is no assumption that data providers share the same role names or role definitions. • All data providers deploy, or have access to, Attribute Authorities that grant NDG Attribute Certificates to users based on their “rights”. NDG Liaison July 2006
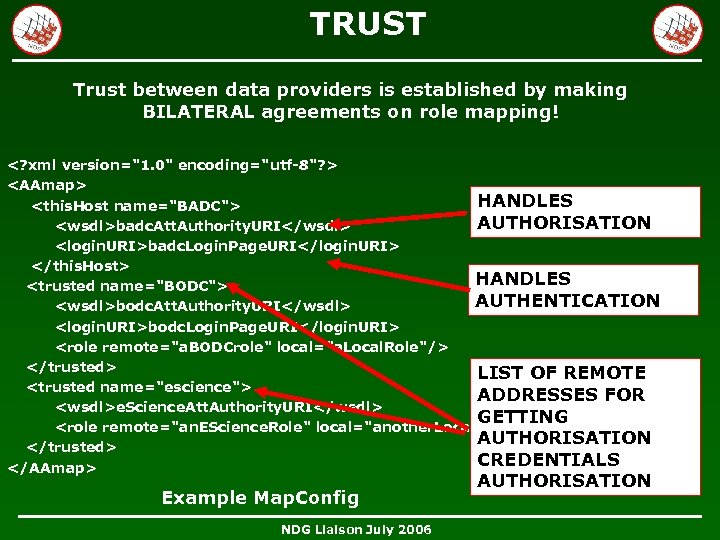
TRUST Trust between data providers is established by making BILATERAL agreements on role mapping! <? xml version="1. 0" encoding="utf-8"? > <AAmap> HANDLES <this. Host name="BADC"> AUTHORISATION <wsdl>badc. Att. Authority. URI</wsdl> <login. URI>badc. Login. Page. URI</login. URI> </this. Host> HANDLES <trusted name="BODC"> AUTHENTICATION <wsdl>bodc. Att. Authority. URI</wsdl> <login. URI>bodc. Login. Page. URI</login. URI> <role remote="a. BODCrole" local="a. Local. Role"/> </trusted> LIST OF REMOTE <trusted name="escience"> ADDRESSES FOR <wsdl>e. Science. Att. Authority. URI</wsdl> GETTING <role remote="an. EScience. Role" local="another. Local. Role"/> AUTHORISATION </trusted> CREDENTIALS </AAmap> Example Map. Config NDG Liaison July 2006 AUTHORISATION
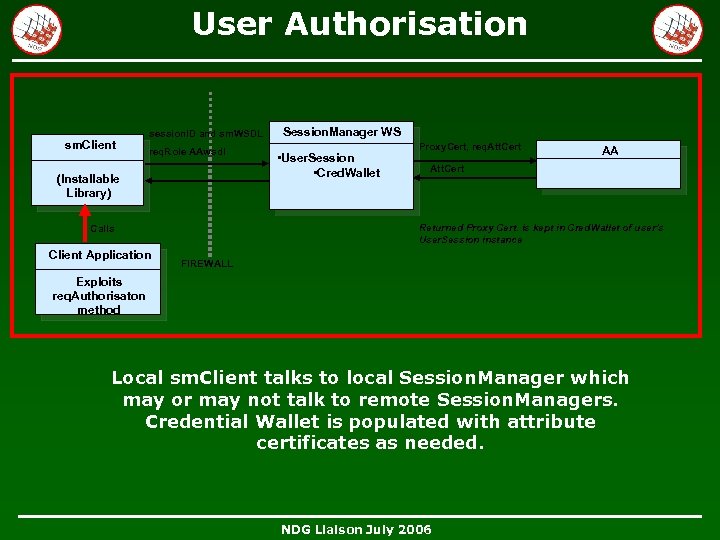
User Authorisation sm. Client session. ID and sm. WSDL req. Role AAwsdl (Installable Library) • User. Session • Cred. Wallet Proxy. Cert, req. Att. Cert AA Att. Cert Returned Proxy Cert. is kept in Cred. Wallet of user’s User. Session instance Calls Client Application Session. Manager WS FIREWALL Exploits req. Authorisaton method Local sm. Client talks to local Session. Manager which may or may not talk to remote Session. Managers. Credential Wallet is populated with attribute certificates as needed. NDG Liaison July 2006
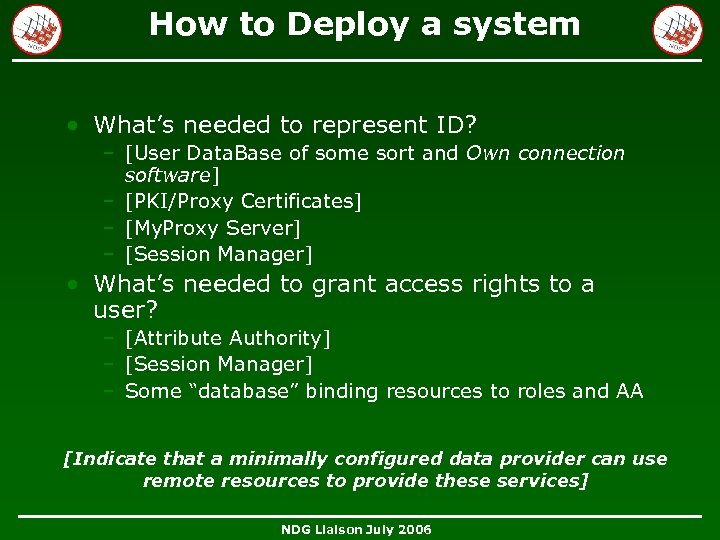
How to Deploy a system • What’s needed to represent ID? – [User Data. Base of some sort and Own connection software] – [PKI/Proxy Certificates] – [My. Proxy Server] – [Session Manager] • What’s needed to grant access rights to a user? – [Attribute Authority] – [Session Manager] – Some “database” binding resources to roles and AA [Indicate that a minimally configured data provider can use remote resources to provide these services] NDG Liaison July 2006

Python Browser Application class Your. Class: ''' Dummy class encapsulating key ndg security concepts from a browser application developerspective ''' def __init__(self, stuff): . . . self. cookie=. . . #set cookie self. config=. . . #read from config file, includes local sm. WSDL …. self. make. Gateway(). . . def make. Gateway(self, cookie=None): ''' Make connection to NDG security and load what is necessary for an NDG cookie to be written ''' # - the request. URL so that a redirect can come back, and to pass # any URL components which have come back from one. . . # - your local sm. WSDL address, and your cookie. . . self. ndg. Gate=security. Gateway(self. request. URL, self. cookie, self. config) def goforit(self): ''' your actions. . . trying to access a URI for which you may have constraints'''. . . if constraints. exist: result=self. ndg. Gate. check((role, AAwsdl)) if result=='Access. Granted': access=1 else: access=0 NDG Liaison July 2006
Vocab Services Users NDG GUI Interface(s) Architecture: Deployment NDG Core Services NDG Liaison July 2006 Data Providers
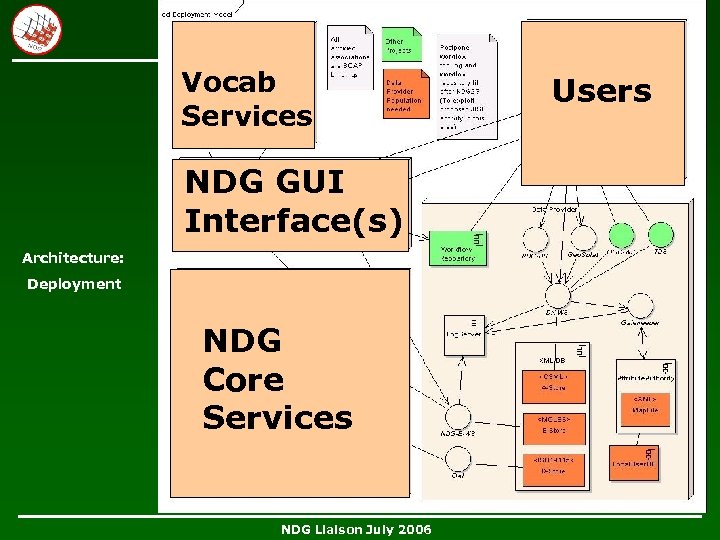
Vocab Services NDG GUI Interface(s) Architecture: Deployment NDG Core Services NDG Liaison July 2006 Users
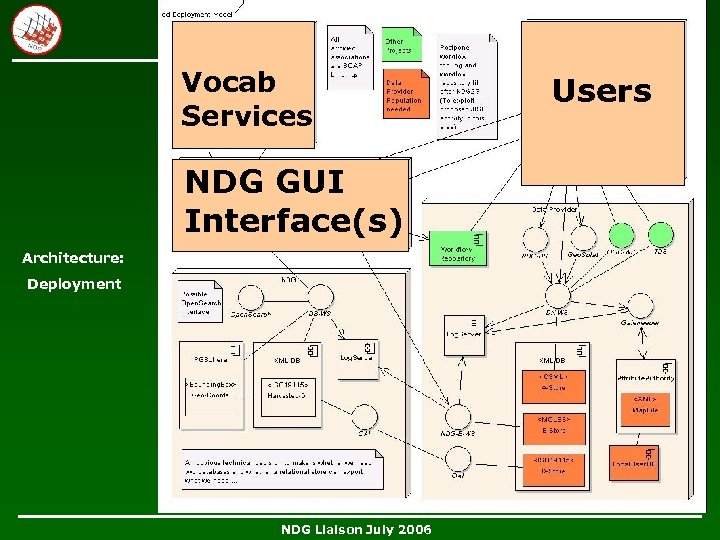
Vocab Services NDG GUI Interface(s) Architecture: Deployment NDG Liaison July 2006 Users
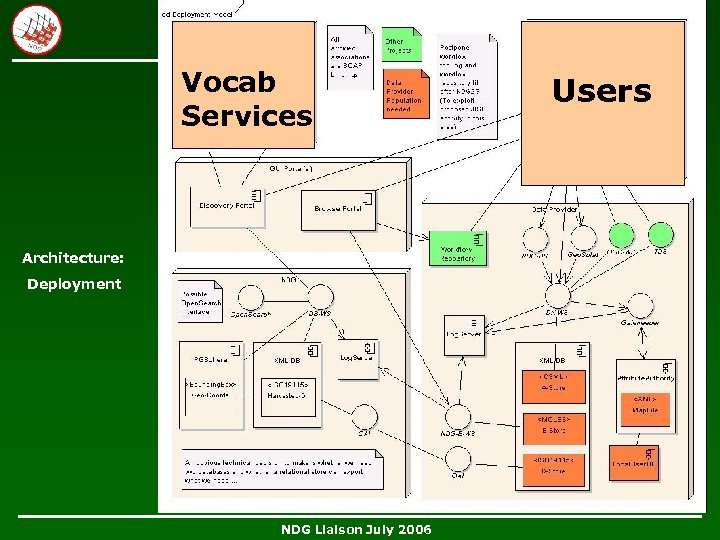
Vocab Services Architecture: Deployment NDG Liaison July 2006 Users
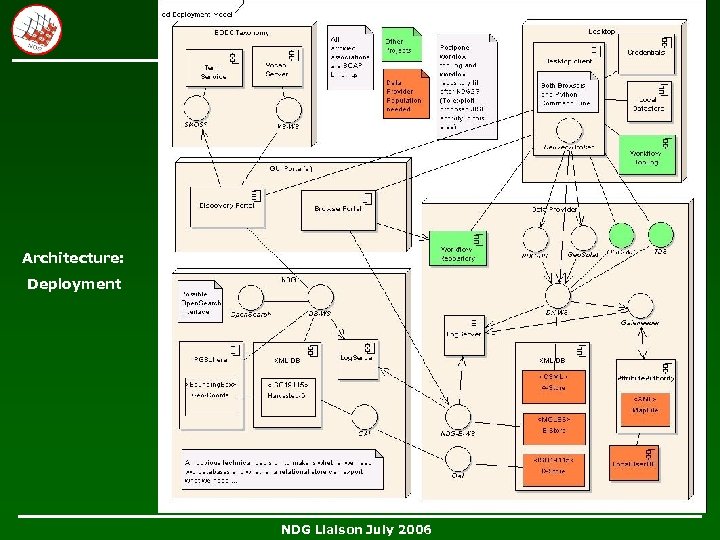
Architecture: Deployment NDG Liaison July 2006
813e1bbc4f78d19191e670d9736f3f2d.ppt