ab1ca4fd9ae76952fb64b89ba1291f8c.ppt
- Количество слайдов: 27
 Inter. Scan Gateway Security Appliance 1. 0 Filip Demianiuk Sales Engineer Eastern Europe 08. 11. 06
Inter. Scan Gateway Security Appliance 1. 0 Filip Demianiuk Sales Engineer Eastern Europe 08. 11. 06
 What is a Mid-Market customer? • Limited security expertise – A few generalists -often < 5 • • Networks can be complex Don’t have time to become experts But still like to feel in control Need to be seen to have taken appropriate security measures • More price sensitive than Enterprise • IT owns budget and makes purchase decision Copyright 2005 - Trend Micro Inc. ?
What is a Mid-Market customer? • Limited security expertise – A few generalists -often < 5 • • Networks can be complex Don’t have time to become experts But still like to feel in control Need to be seen to have taken appropriate security measures • More price sensitive than Enterprise • IT owns budget and makes purchase decision Copyright 2005 - Trend Micro Inc. ?
 What products do they want? THEY DON’T! They want SOLUTIONS which: • • • Solve recognizable business problems Employ best of breed technology Are simple to buy, deploy and manage Are flexible and scaleable Help IT staff to feel in control Copyright 2005 - Trend Micro Inc.
What products do they want? THEY DON’T! They want SOLUTIONS which: • • • Solve recognizable business problems Employ best of breed technology Are simple to buy, deploy and manage Are flexible and scaleable Help IT staff to feel in control Copyright 2005 - Trend Micro Inc.
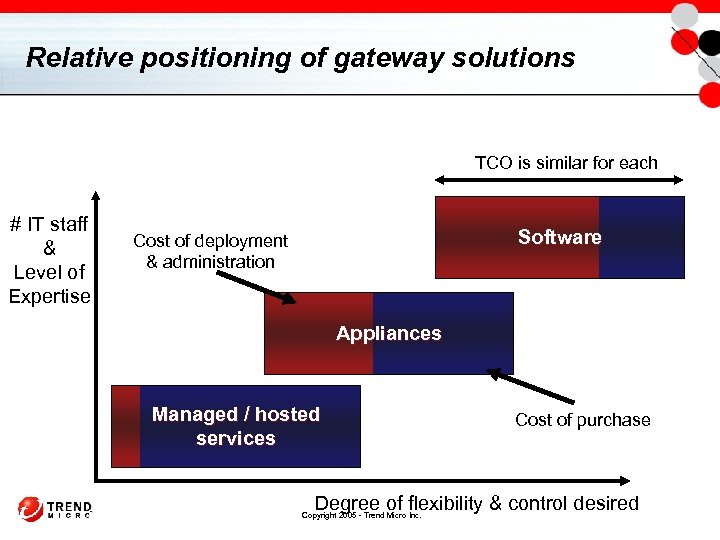 Relative positioning of gateway solutions TCO is similar for each # IT staff & Level of Expertise Software Cost of deployment & administration Appliances Managed / hosted services Cost of purchase Degree of flexibility & control desired Copyright 2005 - Trend Micro Inc.
Relative positioning of gateway solutions TCO is similar for each # IT staff & Level of Expertise Software Cost of deployment & administration Appliances Managed / hosted services Cost of purchase Degree of flexibility & control desired Copyright 2005 - Trend Micro Inc.
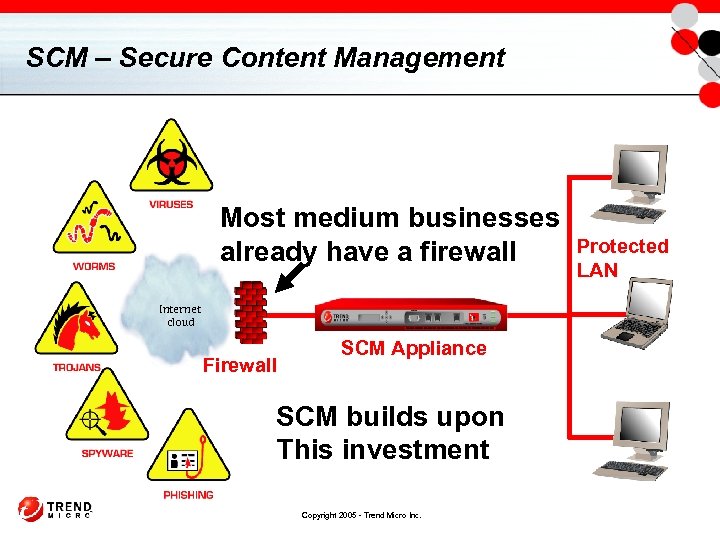 SCM – Secure Content Management Most medium businesses already have a firewall Internet cloud Firewall SCM Appliance SCM builds upon This investment Copyright 2005 - Trend Micro Inc. Protected LAN
SCM – Secure Content Management Most medium businesses already have a firewall Internet cloud Firewall SCM Appliance SCM builds upon This investment Copyright 2005 - Trend Micro Inc. Protected LAN
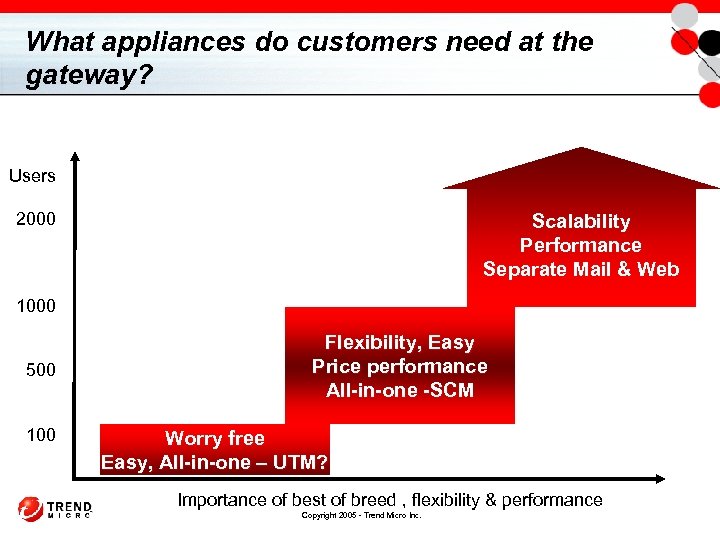 What appliances do customers need at the gateway? Users 2000 Scalability Performance Separate Mail & Web 1000 500 100 Flexibility, Easy Price performance All-in-one -SCM Worry free Easy, All-in-one – UTM? Importance of best of breed , flexibility & performance Copyright 2005 - Trend Micro Inc.
What appliances do customers need at the gateway? Users 2000 Scalability Performance Separate Mail & Web 1000 500 100 Flexibility, Easy Price performance All-in-one -SCM Worry free Easy, All-in-one – UTM? Importance of best of breed , flexibility & performance Copyright 2005 - Trend Micro Inc.
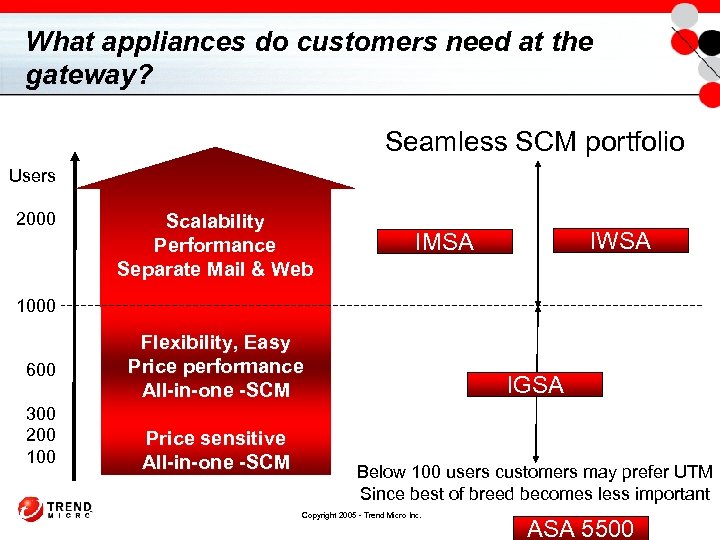 What appliances do customers need at the gateway? Seamless SCM portfolio Users 2000 Scalability Performance Separate Mail & Web IWSA IMSA 1000 600 300 200 100 Flexibility, Easy Price performance All-in-one -SCM Price sensitive All-in-one -SCM IGSA Below 100 users customers may prefer UTM Since best of breed becomes less important Copyright 2005 - Trend Micro Inc. ASA 5500
What appliances do customers need at the gateway? Seamless SCM portfolio Users 2000 Scalability Performance Separate Mail & Web IWSA IMSA 1000 600 300 200 100 Flexibility, Easy Price performance All-in-one -SCM Price sensitive All-in-one -SCM IGSA Below 100 users customers may prefer UTM Since best of breed becomes less important Copyright 2005 - Trend Micro Inc. ASA 5500
 Customer Pain
Customer Pain
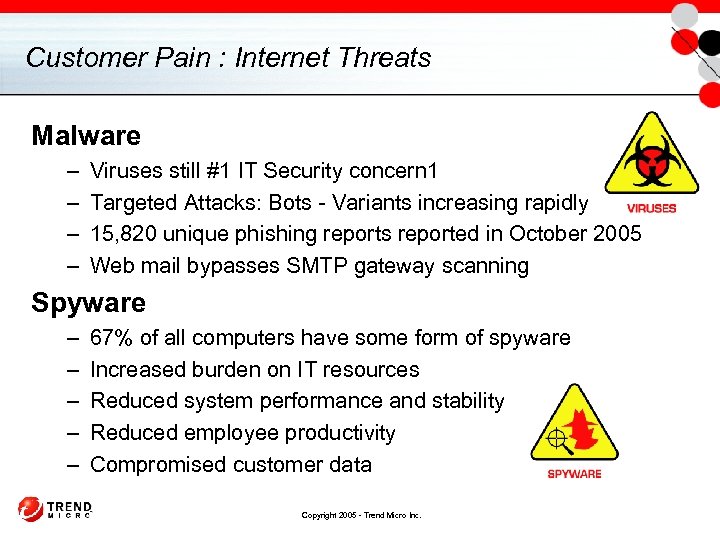 Customer Pain : Internet Threats Malware – – Viruses still #1 IT Security concern 1 Targeted Attacks: Bots - Variants increasing rapidly 15, 820 unique phishing reports reported in October 2005 Web mail bypasses SMTP gateway scanning Spyware – – – 67% of all computers have some form of spyware Increased burden on IT resources Reduced system performance and stability Reduced employee productivity Compromised customer data Copyright 2005 - Trend Micro Inc.
Customer Pain : Internet Threats Malware – – Viruses still #1 IT Security concern 1 Targeted Attacks: Bots - Variants increasing rapidly 15, 820 unique phishing reports reported in October 2005 Web mail bypasses SMTP gateway scanning Spyware – – – 67% of all computers have some form of spyware Increased burden on IT resources Reduced system performance and stability Reduced employee productivity Compromised customer data Copyright 2005 - Trend Micro Inc.
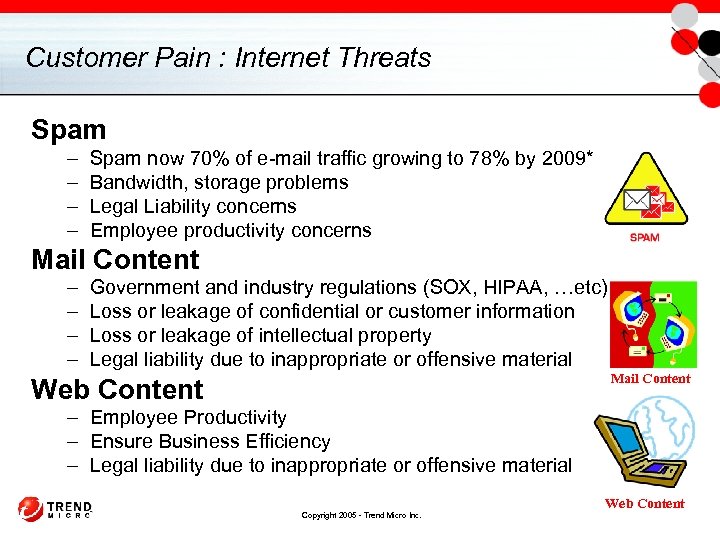 Customer Pain : Internet Threats Spam – – Spam now 70% of e-mail traffic growing to 78% by 2009* Bandwidth, storage problems Legal Liability concerns Employee productivity concerns Mail Content – – Government and industry regulations (SOX, HIPAA, …etc) Loss or leakage of confidential or customer information Loss or leakage of intellectual property Legal liability due to inappropriate or offensive material Mail Content Web Content – Employee Productivity – Ensure Business Efficiency – Legal liability due to inappropriate or offensive material Copyright 2005 - Trend Micro Inc. Web Content
Customer Pain : Internet Threats Spam – – Spam now 70% of e-mail traffic growing to 78% by 2009* Bandwidth, storage problems Legal Liability concerns Employee productivity concerns Mail Content – – Government and industry regulations (SOX, HIPAA, …etc) Loss or leakage of confidential or customer information Loss or leakage of intellectual property Legal liability due to inappropriate or offensive material Mail Content Web Content – Employee Productivity – Ensure Business Efficiency – Legal liability due to inappropriate or offensive material Copyright 2005 - Trend Micro Inc. Web Content
 Inter. Scan Gateway Security Appliance 1. 0 The Gateway Solution for MB
Inter. Scan Gateway Security Appliance 1. 0 The Gateway Solution for MB
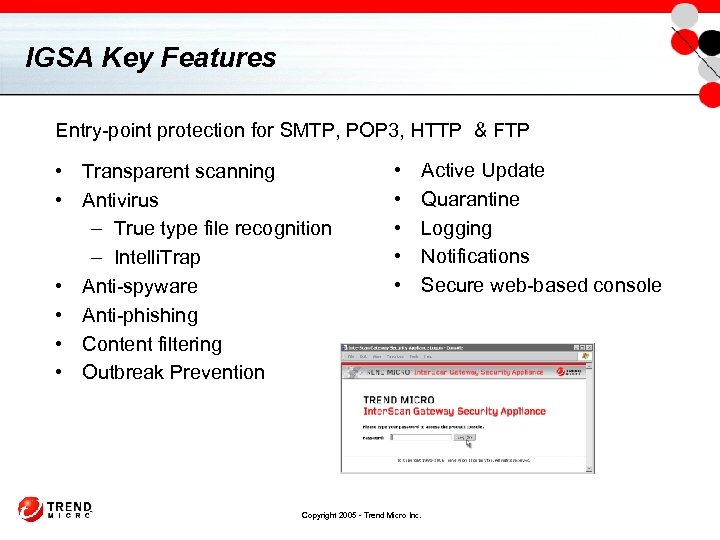 IGSA Key Features Entry-point protection for SMTP, POP 3, HTTP & FTP • Transparent scanning • Antivirus – True type file recognition – Intelli. Trap • Anti-spyware • Anti-phishing • Content filtering • Outbreak Prevention • • • Active Update Quarantine Logging Notifications Secure web-based console Copyright 2005 - Trend Micro Inc.
IGSA Key Features Entry-point protection for SMTP, POP 3, HTTP & FTP • Transparent scanning • Antivirus – True type file recognition – Intelli. Trap • Anti-spyware • Anti-phishing • Content filtering • Outbreak Prevention • • • Active Update Quarantine Logging Notifications Secure web-based console Copyright 2005 - Trend Micro Inc.
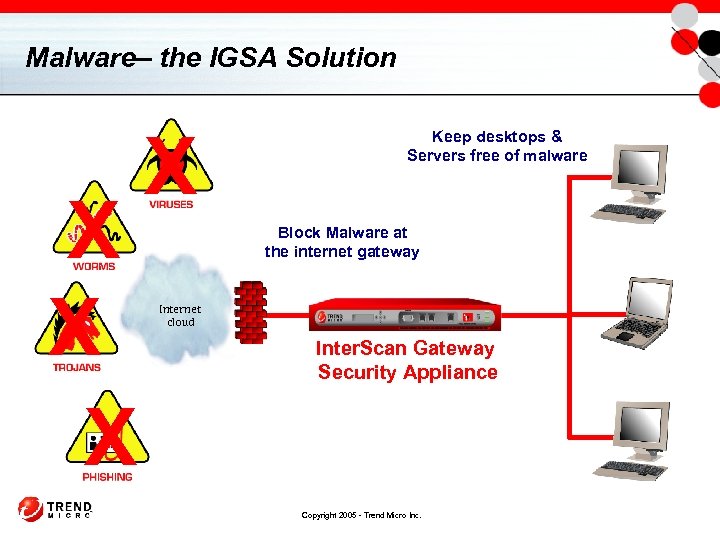 Malware– the IGSA Solution X X Keep desktops & Servers free of malware Block Malware at the internet gateway Internet cloud Inter. Scan Gateway Security Appliance Copyright 2005 - Trend Micro Inc.
Malware– the IGSA Solution X X Keep desktops & Servers free of malware Block Malware at the internet gateway Internet cloud Inter. Scan Gateway Security Appliance Copyright 2005 - Trend Micro Inc.
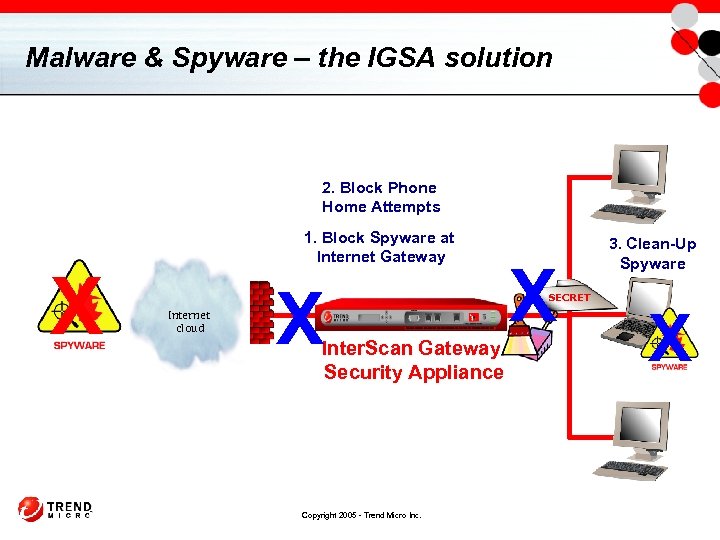 Malware & Spyware – the IGSA solution 2. Block Phone Home Attempts X 1. Block Spyware at Internet Gateway Internet cloud X Inter. Scan Gateway Security Appliance Copyright 2005 - Trend Micro Inc. X SECRET 3. Clean-Up Spyware X
Malware & Spyware – the IGSA solution 2. Block Phone Home Attempts X 1. Block Spyware at Internet Gateway Internet cloud X Inter. Scan Gateway Security Appliance Copyright 2005 - Trend Micro Inc. X SECRET 3. Clean-Up Spyware X
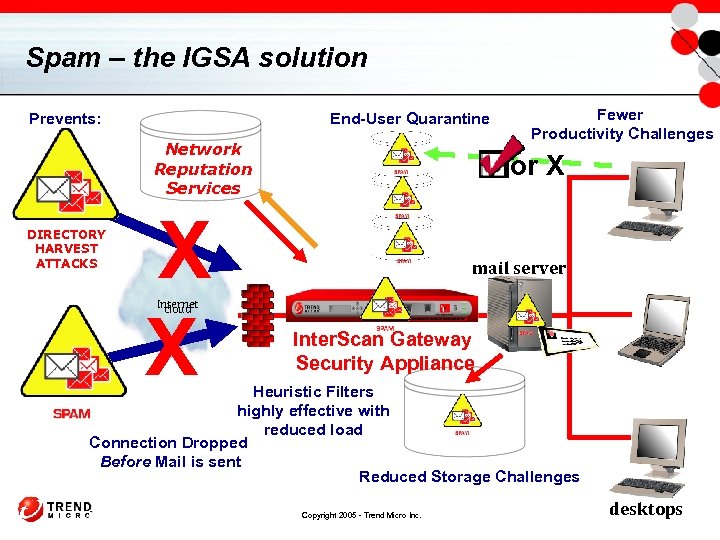 Spam – the IGSA solution End-User Quarantine Prevents: Network Reputation Services DIRECTORY HARVEST ATTACKS X X Fewer Productivity Challenges or X mail server Internet cloud Inter. Scan Gateway Security Appliance Heuristic Filters highly effective with reduced load Connection Dropped Before Mail is sent Reduced Storage Challenges Copyright 2005 - Trend Micro Inc. desktops
Spam – the IGSA solution End-User Quarantine Prevents: Network Reputation Services DIRECTORY HARVEST ATTACKS X X Fewer Productivity Challenges or X mail server Internet cloud Inter. Scan Gateway Security Appliance Heuristic Filters highly effective with reduced load Connection Dropped Before Mail is sent Reduced Storage Challenges Copyright 2005 - Trend Micro Inc. desktops
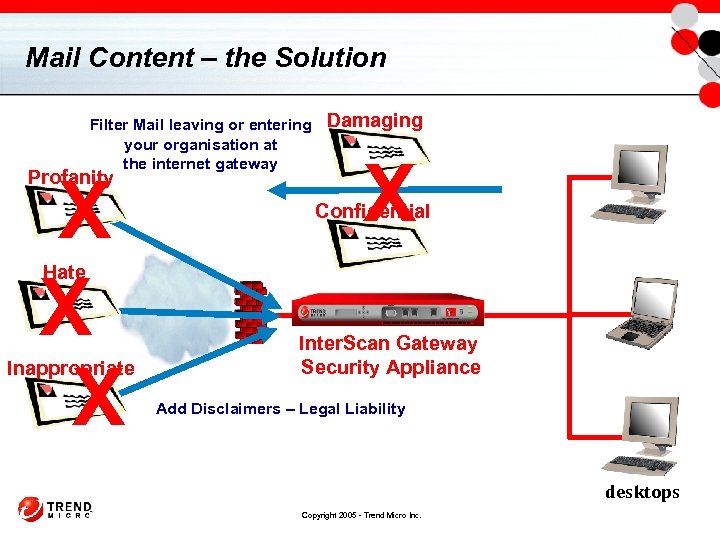 Mail Content – the Solution Filter Mail leaving or entering your organisation at the internet gateway X X X Profanity Damaging X Confidential Hate Inappropriate Inter. Scan Gateway Security Appliance Add Disclaimers – Legal Liability desktops Copyright 2005 - Trend Micro Inc.
Mail Content – the Solution Filter Mail leaving or entering your organisation at the internet gateway X X X Profanity Damaging X Confidential Hate Inappropriate Inter. Scan Gateway Security Appliance Add Disclaimers – Legal Liability desktops Copyright 2005 - Trend Micro Inc.
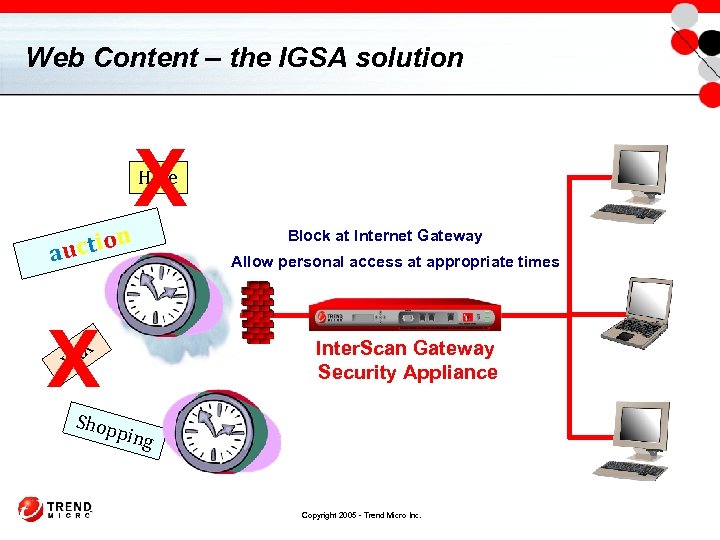 Web Content – the IGSA solution X Hate n uc t i o a X Block at Internet Gateway Allow personal access at appropriate times Inter. Scan Gateway Security Appliance X XX Shop ping Copyright 2005 - Trend Micro Inc.
Web Content – the IGSA solution X Hate n uc t i o a X Block at Internet Gateway Allow personal access at appropriate times Inter. Scan Gateway Security Appliance X XX Shop ping Copyright 2005 - Trend Micro Inc.
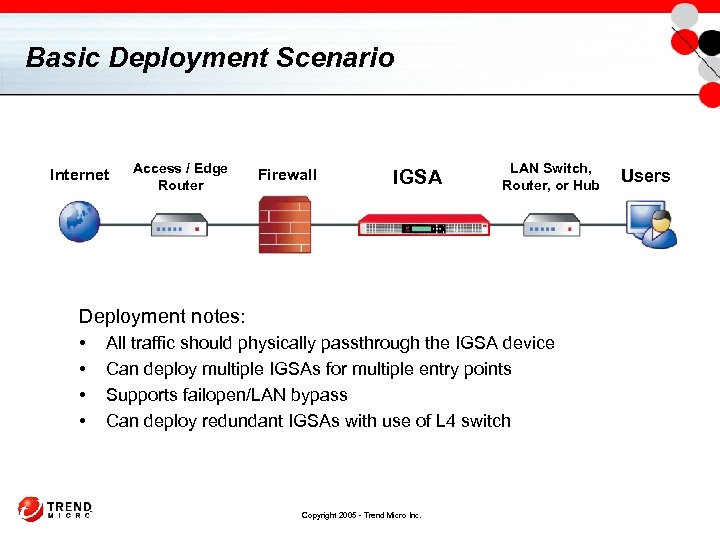 Basic Deployment Scenario Internet Access / Edge Router Firewall IGSA LAN Switch, Router, or Hub Deployment notes: • • All traffic should physically passthrough the IGSA device Can deploy multiple IGSAs for multiple entry points Supports failopen/LAN bypass Can deploy redundant IGSAs with use of L 4 switch Copyright 2005 - Trend Micro Inc. Users
Basic Deployment Scenario Internet Access / Edge Router Firewall IGSA LAN Switch, Router, or Hub Deployment notes: • • All traffic should physically passthrough the IGSA device Can deploy multiple IGSAs for multiple entry points Supports failopen/LAN bypass Can deploy redundant IGSAs with use of L 4 switch Copyright 2005 - Trend Micro Inc. Users
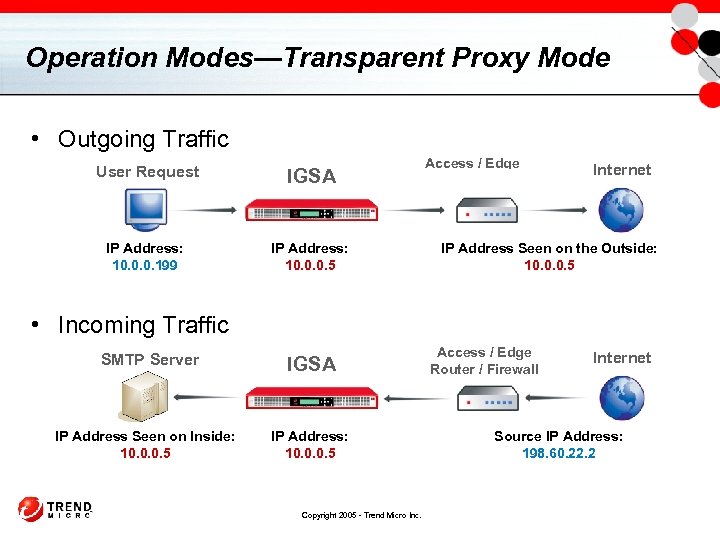 Operation Modes—Transparent Proxy Mode • Outgoing Traffic User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Internet IP Address Seen on the Outside: 10. 0. 0. 5 • Incoming Traffic SMTP Server IP Address Seen on Inside: 10. 0. 0. 5 IGSA IP Address: 10. 0. 0. 5 Copyright 2005 - Trend Micro Inc. Access / Edge Router / Firewall Internet Source IP Address: 198. 60. 22. 2
Operation Modes—Transparent Proxy Mode • Outgoing Traffic User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Internet IP Address Seen on the Outside: 10. 0. 0. 5 • Incoming Traffic SMTP Server IP Address Seen on Inside: 10. 0. 0. 5 IGSA IP Address: 10. 0. 0. 5 Copyright 2005 - Trend Micro Inc. Access / Edge Router / Firewall Internet Source IP Address: 198. 60. 22. 2
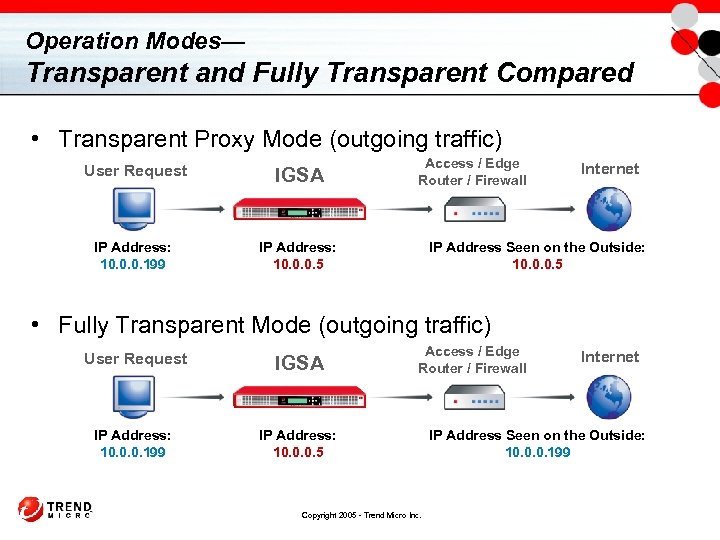 Operation Modes— Transparent and Fully Transparent Compared • Transparent Proxy Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Internet IP Address Seen on the Outside: 10. 0. 0. 5 • Fully Transparent Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Copyright 2005 - Trend Micro Inc. Internet IP Address Seen on the Outside: 10. 0. 0. 199
Operation Modes— Transparent and Fully Transparent Compared • Transparent Proxy Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Internet IP Address Seen on the Outside: 10. 0. 0. 5 • Fully Transparent Mode (outgoing traffic) User Request IGSA IP Address: 10. 0. 0. 199 Access / Edge Router / Firewall IP Address: 10. 0. 0. 5 Copyright 2005 - Trend Micro Inc. Internet IP Address Seen on the Outside: 10. 0. 0. 199
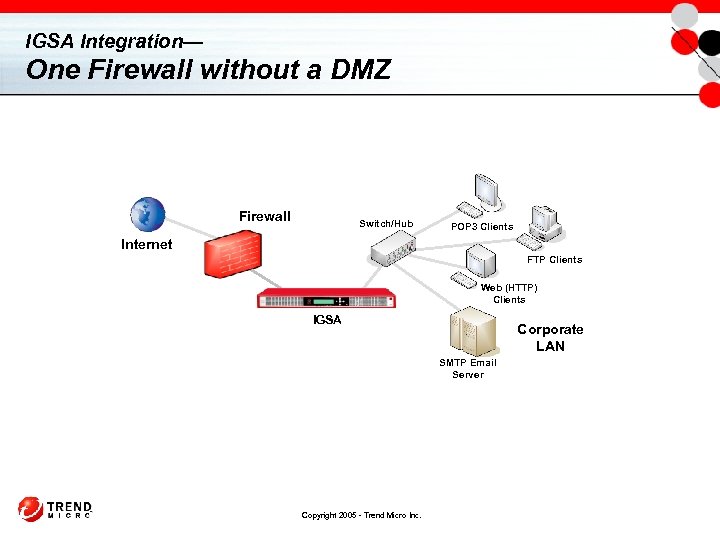 IGSA Integration— One Firewall without a DMZ Firewall Switch/Hub POP 3 Clients Internet FTP Clients Web (HTTP) Clients IGSA Corporate LAN SMTP Email Server Copyright 2005 - Trend Micro Inc.
IGSA Integration— One Firewall without a DMZ Firewall Switch/Hub POP 3 Clients Internet FTP Clients Web (HTTP) Clients IGSA Corporate LAN SMTP Email Server Copyright 2005 - Trend Micro Inc.
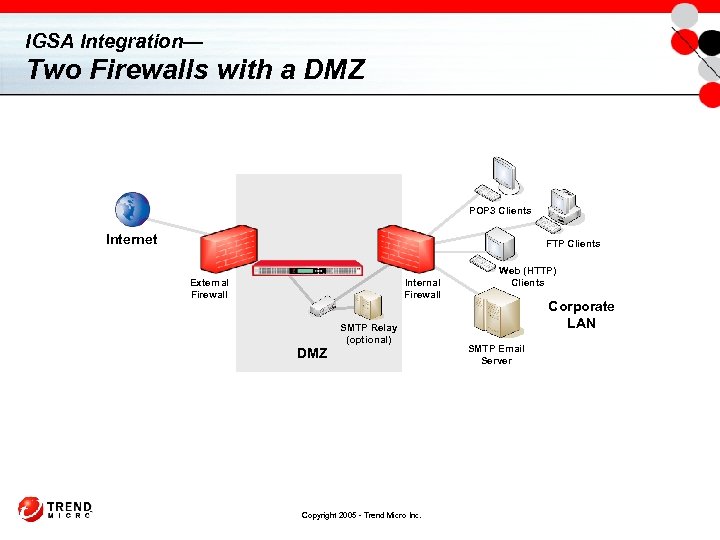 IGSA Integration— Two Firewalls with a DMZ POP 3 Clients Internet FTP Clients External Firewall Internal Firewall DMZ SMTP Relay (optional) Copyright 2005 - Trend Micro Inc. Web (HTTP) Clients Corporate LAN SMTP Email Server
IGSA Integration— Two Firewalls with a DMZ POP 3 Clients Internet FTP Clients External Firewall Internal Firewall DMZ SMTP Relay (optional) Copyright 2005 - Trend Micro Inc. Web (HTTP) Clients Corporate LAN SMTP Email Server
 Features and Benefits
Features and Benefits
 Why Gateway? • All-in-one, Internet Gateway Secure Content Management – Protects at the most effective point in your infrastructure – Scan all potentially infected traffic at the gateway to your infrastructure – Protect un-patched/out-of date PCs /Servers – Filter mail from viruses and spam before it gets to your mail servers – Ensure employee productivity – Limit legal liability/leakage of confidential documents Copyright 2005 - Trend Micro Inc.
Why Gateway? • All-in-one, Internet Gateway Secure Content Management – Protects at the most effective point in your infrastructure – Scan all potentially infected traffic at the gateway to your infrastructure – Protect un-patched/out-of date PCs /Servers – Filter mail from viruses and spam before it gets to your mail servers – Ensure employee productivity – Limit legal liability/leakage of confidential documents Copyright 2005 - Trend Micro Inc.
 Top 5 IGSA Customer Silver Bullets 1. First in Internet gateway antivirus, six years running 2. Only gateway appliance with automated desktop cleanup of spyware and malware • Saves time and removes the need for sneakernet solution 3. All-in-one solution, no hidden add-ons or extra costs 4. Automated threat protection closes the window of vulnerability quickly • Improving your security and reducing your stress 24 by 7 5. Simplified purchase, one decision, one price, one device Copyright 2005 - Trend Micro Inc.
Top 5 IGSA Customer Silver Bullets 1. First in Internet gateway antivirus, six years running 2. Only gateway appliance with automated desktop cleanup of spyware and malware • Saves time and removes the need for sneakernet solution 3. All-in-one solution, no hidden add-ons or extra costs 4. Automated threat protection closes the window of vulnerability quickly • Improving your security and reducing your stress 24 by 7 5. Simplified purchase, one decision, one price, one device Copyright 2005 - Trend Micro Inc.
 IGSA Global pricing model Pricing and licensing: – IGSA Hardware replacement – IGSA 100 users * – IGSA 200 users * – IGSA 300 users * – IGSA 600 users * – IGSA 800 users * – IGSA 1000 users * * Includes hardware and software license with all functionality enabled so NRS, URL etc. become differentiators rather than optional add-ons. Hardware Warranty is included in 1 st year price. Copyright 2005 - Trend Micro Inc.
IGSA Global pricing model Pricing and licensing: – IGSA Hardware replacement – IGSA 100 users * – IGSA 200 users * – IGSA 300 users * – IGSA 600 users * – IGSA 800 users * – IGSA 1000 users * * Includes hardware and software license with all functionality enabled so NRS, URL etc. become differentiators rather than optional add-ons. Hardware Warranty is included in 1 st year price. Copyright 2005 - Trend Micro Inc.
 Q&A and Thank You!
Q&A and Thank You!


