40e6279a9a680f9af36a2816a45a32d0.ppt
- Количество слайдов: 24

Intelligent Web Application Firewall WEB INSIGHT SG Product Introduction June – 2008 MONITORAPP Co. , Ltd.
Contents about MONITORAPP Web Security Overview Product Introduction WEB INSIGHT SG Characteristics WEB INSIGHT SG Features
about MONITORAPP Company name : MONITORAPP Co. , Ltd. Established Date : 2005 -2 -22 CEO : Young Kwang. Hoo Lee Business Regions Vision • Be a leading application delivery Solution provider in the world. Mission • We leverage E-business by securing the entire web environment. Application Delivery Technology Research & Development Web Application Security product supply Web Application Acceleration product supply Database Security product supply Web Application Security Service supply Address 306, Ace Techno Tower 1, 197 -17, Guro 3 -Dong, Guro-Gu, Seoul, Korea Tel. )+82 -2 -749 -0799 / Fax. )+82 -2 -749 -0798
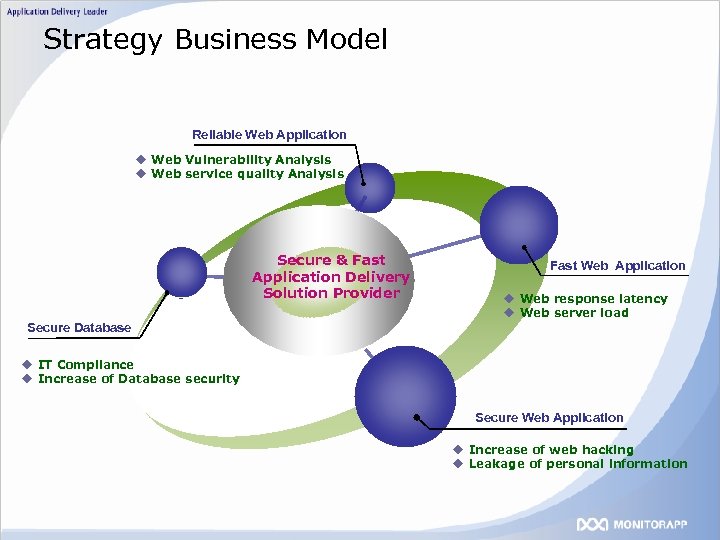
Strategy Business Model Reliable Web Application u Web Vulnerability Analysis u Web service quality Analysis Secure & Fast Application Delivery Solution Provider Fast Web Application u Web response latency u Web server load Secure Database u IT Compliance u Increase of Database security Secure Web Application u Increase of web hacking u Leakage of personal information
Products & Technologies Products For Web Application WEB INSIGHT SG – Web Application Firewall WEB INSIGHT AG – Web Application Accelerator For Database Application DB INSIGHT SG – Database Security & Audit Service Business KT Bizmeka Service Collaboration with MSSP Technologies APPLICATION INSIGHT™ Technology Adaptive Profiling™ Technology Innovative Web Acceleration Technology
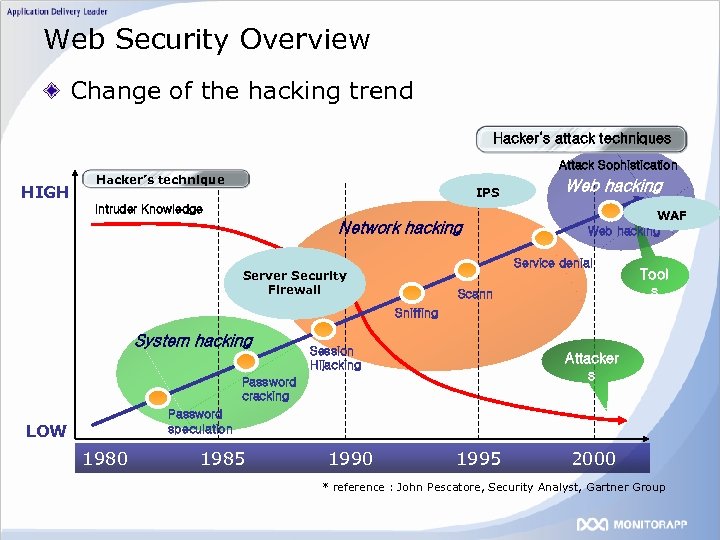
Web Security Overview Change of the hacking trend Hacker’s attack techniques Attack Sophistication HIGH Hacker’s technique IPS Intruder Knowledge Network hacking Web hacking WAF Web hacking Service denial Server Security Firewall Scann Tool s Sniffing System hacking Session Hijacking Attacker s Password cracking Password speculation LOW 1980 1985 1990 1995 2000 * reference : John Pescatore, Security Analyst, Gartner Group

Web Security Overview Critical dangers against web service are increasing. 80 port should be opened for web service, so that has been threatened by hackers. Important information like DB can be drained due to web application hacking. By the limitation of the existing security product like IDS and IPS, Web attacking danger are increasing. The existing web vulnerabilities opened to the public can always be the attacking targets. “ 70~80% of hacking is targeting web!”
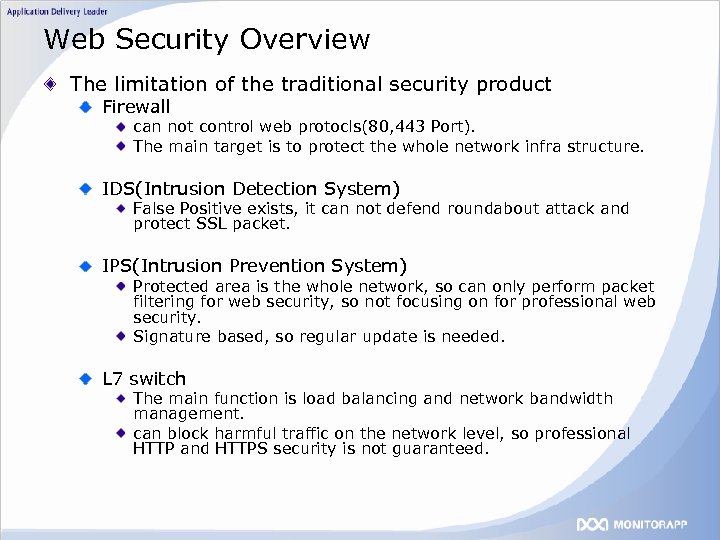
Web Security Overview The limitation of the traditional security product Firewall can not control web protocls(80, 443 Port). The main target is to protect the whole network infra structure. IDS(Intrusion Detection System) False Positive exists, it can not defend roundabout attack and protect SSL packet. IPS(Intrusion Prevention System) Protected area is the whole network, so can only perform packet filtering for web security, so not focusing on for professional web security. Signature based, so regular update is needed. L 7 switch The main function is load balancing and network bandwidth management. can block harmful traffic on the network level, so professional HTTP and HTTPS security is not guaranteed.
Product Introduction WEB INSIGHT SG Intelligent Web Application Firewall WEB INSIGHT SG enables more easier and cost effective web communication to user. Positive Security Model + Negative Security Model Profile based positive security policy User defined positive security policy Negative security policy against OWASP Top 10 attack High Performance Network appliance Support Gigabit Performance Physical Independent Impact Simple Deployment Fail open (LAN Bypass) Fail over (Active – Standby High Availability)
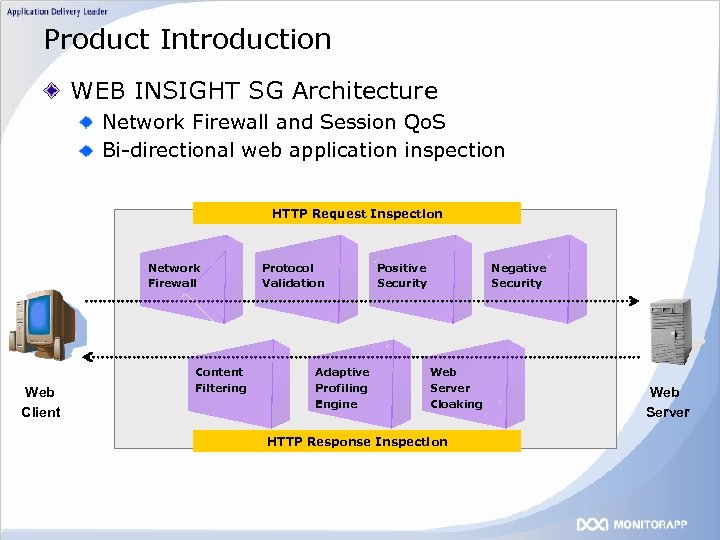
Product Introduction WEB INSIGHT SG Architecture Network Firewall and Session Qo. S Bi-directional web application inspection HTTP Request Inspection Network Firewall Web Client Content Filtering Protocol Validation Adaptive Profiling Engine Positive Security Negative Security Web Server Cloaking HTTP Response Inspection Web Server
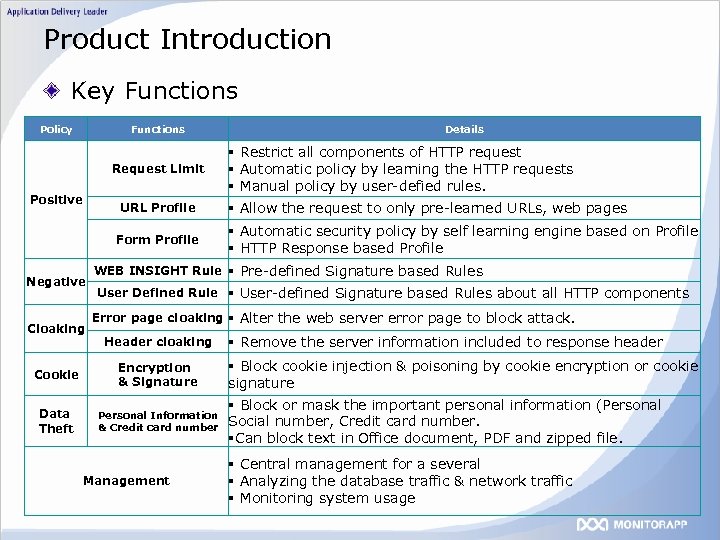
Product Introduction Key Functions Policy Functions Request Limit Positive URL Profile Form Profile Negative Cloaking WEB INSIGHT Rule User Defined Rule Error page cloaking Header cloaking Cookie Encryption & Signature Data Theft Personal Information & Credit card number Management Details § Restrict all components of HTTP request § Automatic policy by learning the HTTP requests § Manual policy by user-defied rules. § Allow the request to only pre-learned URLs, web pages § Automatic security policy by self learning engine based on Profile § HTTP Response based Profile § Pre-defined Signature based Rules § User-defined Signature based Rules about all HTTP components § Alter the web server error page to block attack. § Remove the server information included to response header § Block cookie injection & poisoning by cookie encryption or cookie signature § Block or mask the important personal information (Personal Social number, Credit card number. §Can block text in Office document, PDF and zipped file. § Central management for a several § Analyzing the database traffic & network traffic § Monitoring system usage
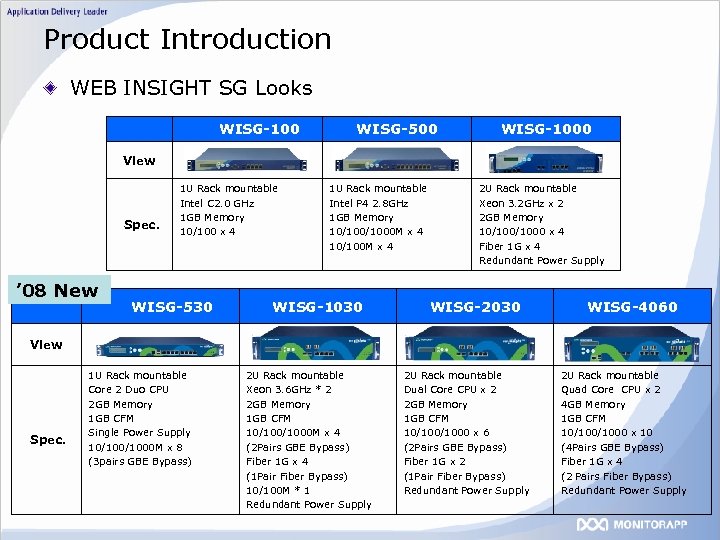
Product Introduction WEB INSIGHT SG Looks WISG-100 WISG-500 WISG-1000 View Spec. ’ 08 New 1 U Rack mountable Intel C 2. 0 GHz 1 GB Memory 10/100 x 4 WISG-530 1 U Rack mountable Intel P 4 2. 8 GHz 1 GB Memory 10/1000 M x 4 10/100 M x 4 WISG-1030 2 U Rack mountable Xeon 3. 2 GHz x 2 2 GB Memory 10/1000 x 4 Fiber 1 G x 4 Redundant Power Supply WISG-2030 WISG-4060 View Spec. 1 U Rack mountable Core 2 Duo CPU 2 GB Memory 1 GB CFM Single Power Supply 10/1000 M x 8 (3 pairs GBE Bypass) 2 U Rack mountable Xeon 3. 6 GHz * 2 2 GB Memory 1 GB CFM 10/1000 M x 4 (2 Pairs GBE Bypass) Fiber 1 G x 4 (1 Pair Fiber Bypass) 10/100 M * 1 Redundant Power Supply 2 U Rack mountable Dual Core CPU x 2 2 GB Memory 1 GB CFM 10/1000 x 6 (2 Pairs GBE Bypass) Fiber 1 G x 2 (1 Pair Fiber Bypass) Redundant Power Supply 2 U Rack mountable Quad Core CPU x 2 4 GB Memory 1 GB CFM 10/1000 x 10 (4 Pairs GBE Bypass) Fiber 1 G x 4 (2 Pairs Fiber Bypass) Redundant Power Supply
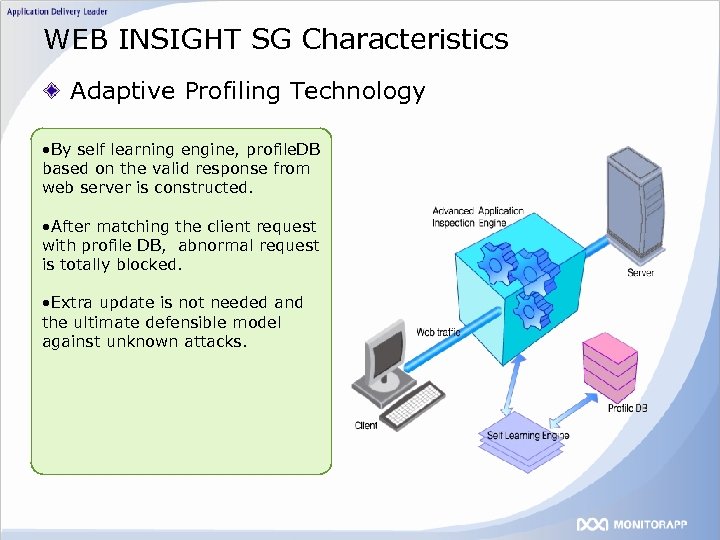
WEB INSIGHT SG Characteristics Adaptive Profiling Technology • By self learning engine, profile. DB based on the valid response from web server is constructed. • After matching the client request with profile DB, abnormal request is totally blocked. • Extra update is not needed and the ultimate defensible model against unknown attacks.
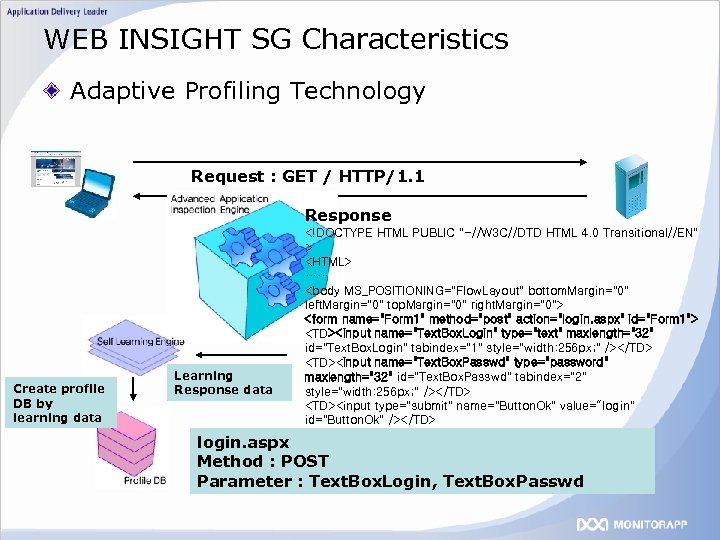
WEB INSIGHT SG Characteristics Adaptive Profiling Technology Request : GET / HTTP/1. 1 Response Create profile DB by learning data Learning Response data <!DOCTYPE HTML PUBLIC "-//W 3 C//DTD HTML 4. 0 Transitional//EN" > <HTML> …… <body MS_POSITIONING="Flow. Layout" bottom. Margin="0" left. Margin="0" top. Margin="0" right. Margin="0"> <form name="Form 1" method="post" action="login. aspx" id="Form 1"> <TD><input name="Text. Box. Login" type="text" maxlength="32" id="Text. Box. Login" tabindex="1" style="width: 256 px; " /></TD> <TD><input name="Text. Box. Passwd" type="password" maxlength="32" id="Text. Box. Passwd" tabindex="2" style="width: 256 px; " /></TD> <TD><input type="submit" name="Button. Ok" value=“login" id="Button. Ok" /></TD> </font> …… login. aspx Method : POST Parameter : Text. Box. Login, Text. Box. Passwd
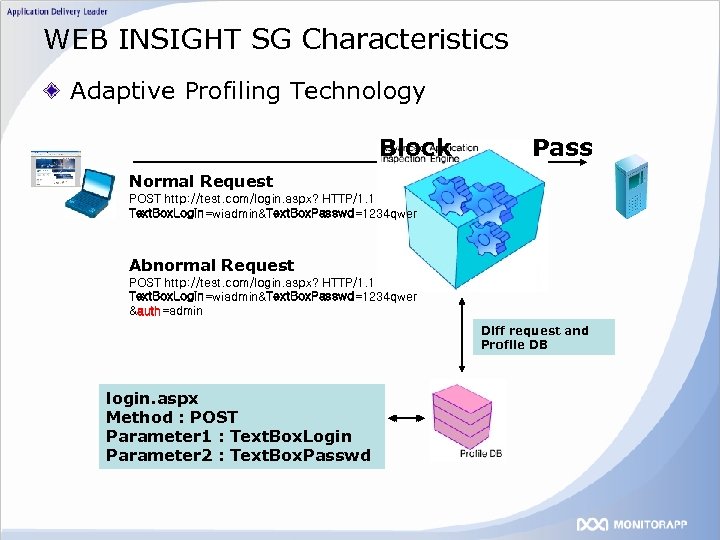
WEB INSIGHT SG Characteristics Adaptive Profiling Technology Block Pass Normal Request POST http: //test. com/login. aspx? HTTP/1. 1 Text. Box. Login=wiadmin&Text. Box. Passwd=1234 qwer Abnormal Request POST http: //test. com/login. aspx? HTTP/1. 1 Text. Box. Login=wiadmin&Text. Box. Passwd=1234 qwer &auth=admin Diff request and Profile EB DB login. aspx Method : POST Parameter 1 : Text. Box. Login Parameter 2 : Text. Box. Passwd
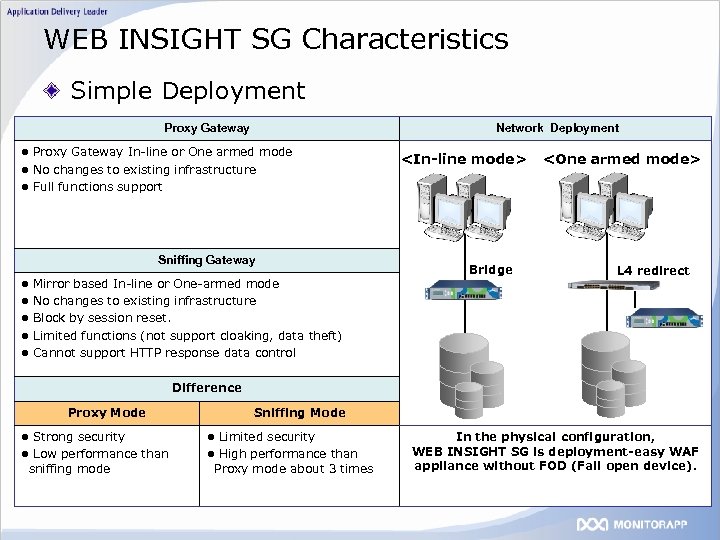
WEB INSIGHT SG Characteristics Simple Deployment Proxy Gateway Network Deployment l Proxy Gateway In-line or One armed mode l No changes to existing infrastructure <In-line mode> <One armed mode> l Full functions support Sniffing Gateway l Mirror based In-line or One-armed mode Bridge L 4 redirect l No changes to existing infrastructure l Block by session reset. l Limited functions (not support cloaking, data theft) l Cannot support HTTP response data control Difference Proxy Mode Sniffing Mode l Strong security l Limited security l Low performance than l High performance than sniffing mode Proxy mode about 3 times In the physical configuration, WEB INSIGHT SG is deployment-easy WAF appliance without FOD (Fail open device).
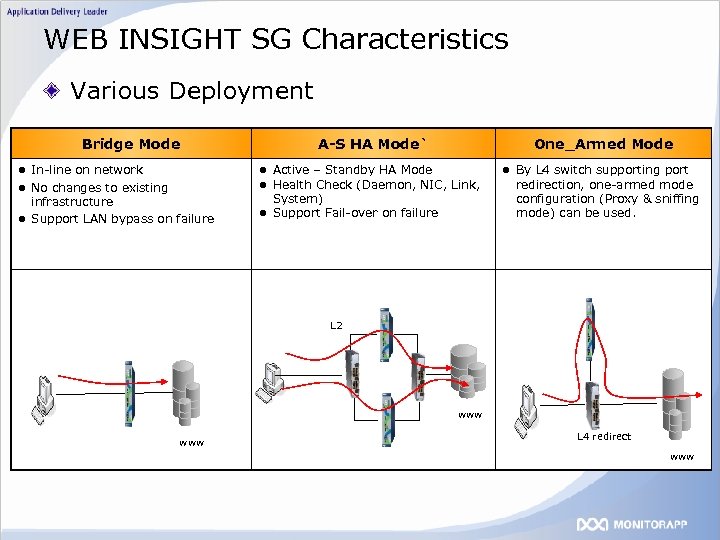
WEB INSIGHT SG Characteristics Various Deployment Bridge Mode l In-line on network A-S HA Mode` One_Armed Mode l Active – Standby HA Mode l Health Check (Daemon, NIC, Link, l No changes to existing infrastructure l Support LAN bypass on failure System) l Support Fail-over on failure l By L 4 switch supporting port redirection, one-armed mode configuration (Proxy & sniffing mode) can be used. L 2 www L 4 redirect www
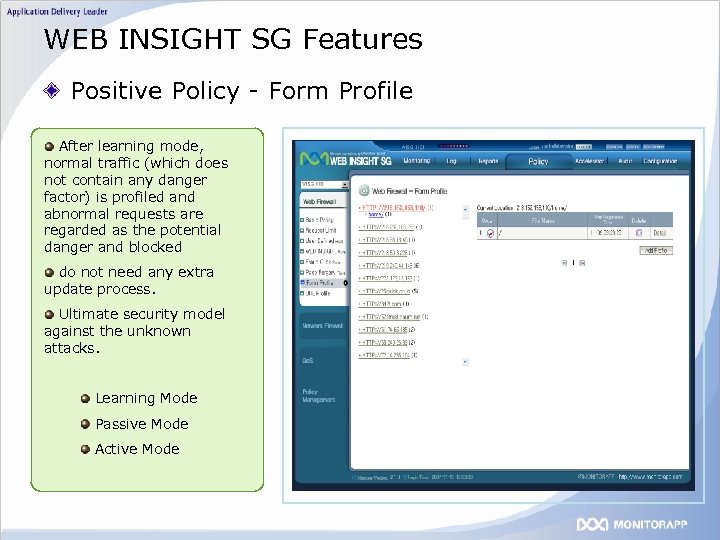
WEB INSIGHT SG Features Positive Policy - Form Profile After learning mode, normal traffic (which does not contain any danger factor) is profiled and abnormal requests are regarded as the potential danger and blocked do not need any extra update process. Ultimate security model against the unknown attacks. Learning Mode Passive Mode Active Mode
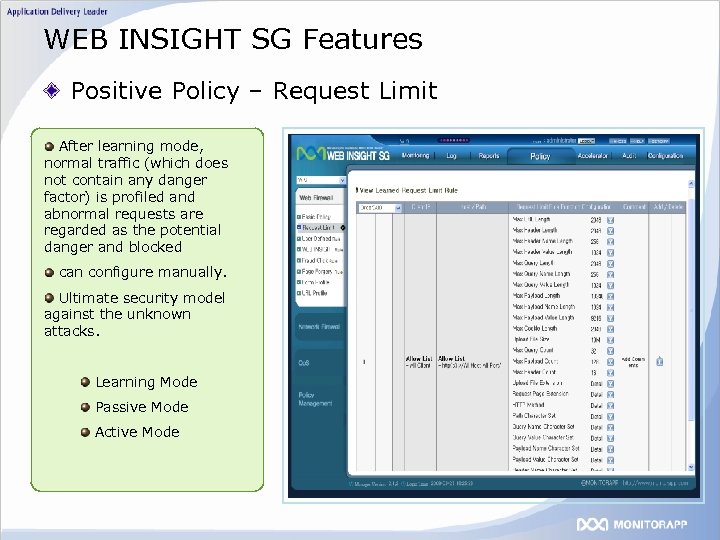
WEB INSIGHT SG Features Positive Policy – Request Limit After learning mode, normal traffic (which does not contain any danger factor) is profiled and abnormal requests are regarded as the potential danger and blocked can configure manually. Ultimate security model against the unknown attacks. Learning Mode Passive Mode Active Mode
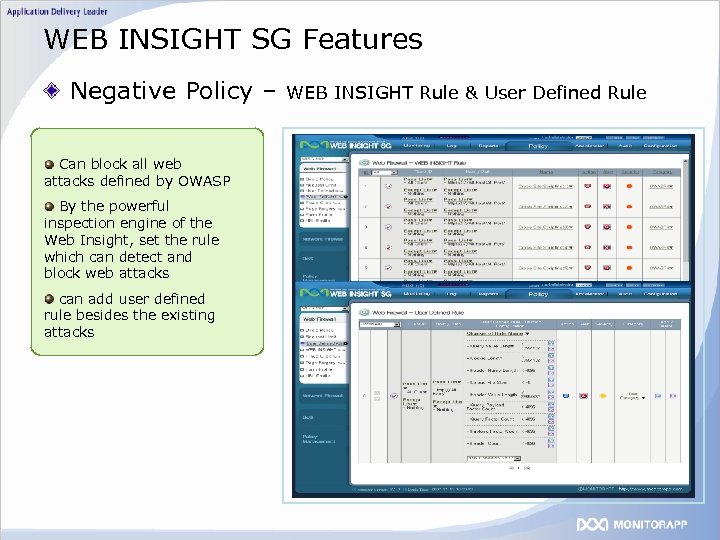
WEB INSIGHT SG Features Negative Policy – Can block all web attacks defined by OWASP By the powerful inspection engine of the Web Insight, set the rule which can detect and block web attacks can add user defined rule besides the existing attacks WEB INSIGHT Rule & User Defined Rule
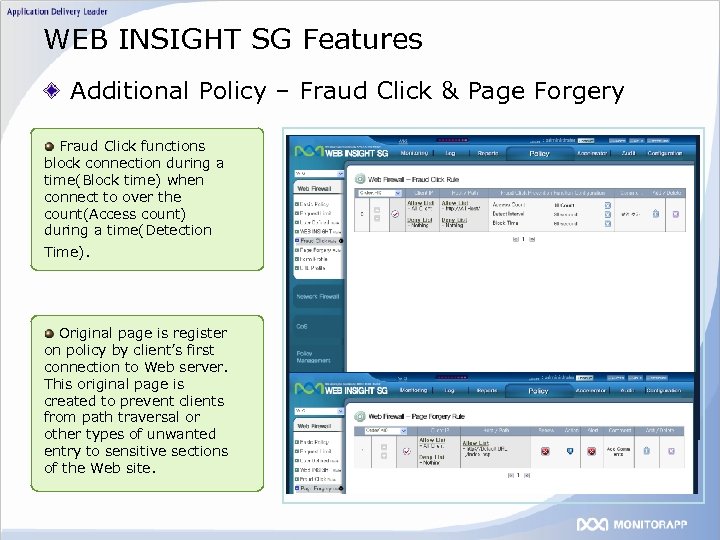
WEB INSIGHT SG Features Additional Policy – Fraud Click & Page Forgery Fraud Click functions block connection during a time(Block time) when connect to over the count(Access count) during a time(Detection Time). Original page is register on policy by client’s first connection to Web server. This original page is created to prevent clients from path traversal or other types of unwanted entry to sensitive sections of the Web site.
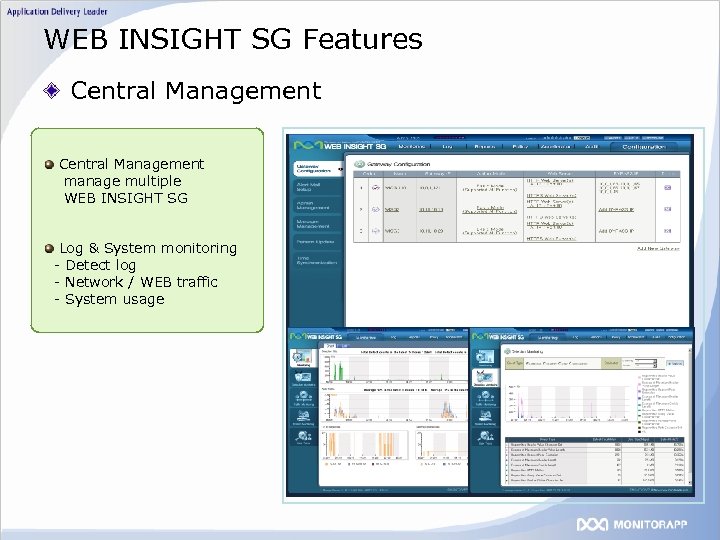
WEB INSIGHT SG Features Central Management manage multiple WEB INSIGHT SG Log & System monitoring - Detect log - Network / WEB traffic - System usage
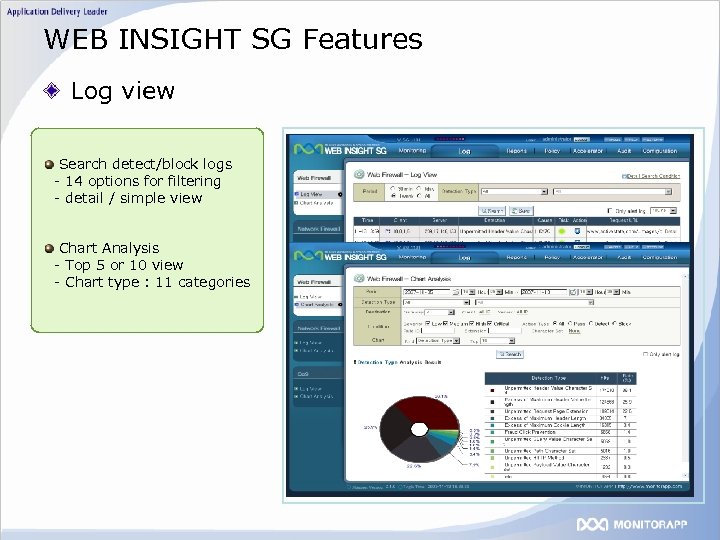
WEB INSIGHT SG Features Log view Search detect/block logs - 14 options for filtering - detail / simple view Chart Analysis - Top 5 or 10 view - Chart type : 11 categories

Thank You MONITORAPP Co. , Ltd. 306, Ace Techno Tower 1, 197 -17, Guro 3 -Dong, Guro-Gu, Seoul, Korea Tel : +82 -2 -749 -0799, Fax) +82 -2 -749 -0798 E-Mail : sales@monitorapp. com Website : www. monitorapp. com
40e6279a9a680f9af36a2816a45a32d0.ppt