 Intelligence Gathering Techniques
Intelligence Gathering Techniques
 Gathering Process Overview
Gathering Process Overview
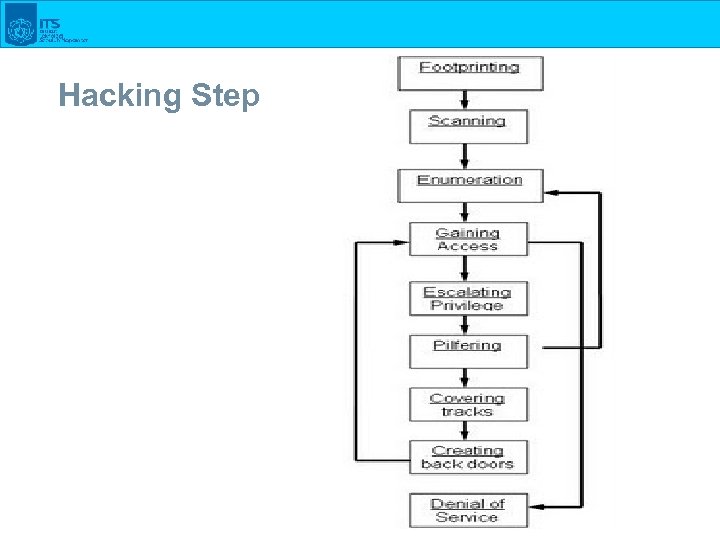 Hacking Step
Hacking Step
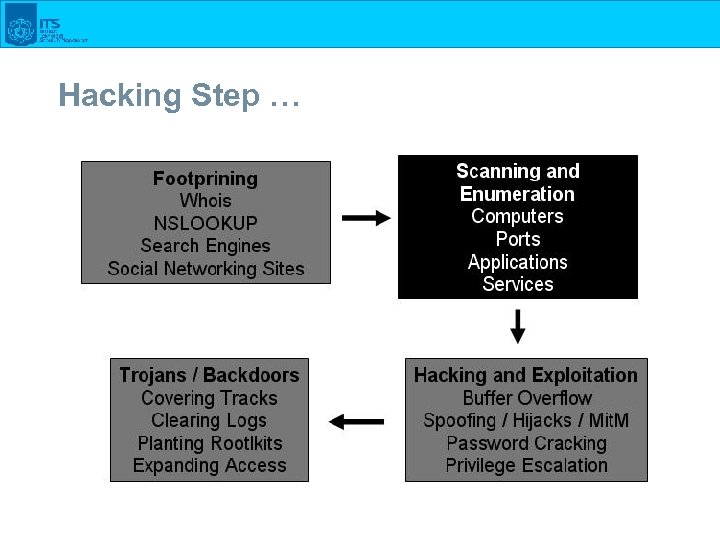 Hacking Step …
Hacking Step …
 Gathering Process overview
Gathering Process overview
 Footprinting
Footprinting
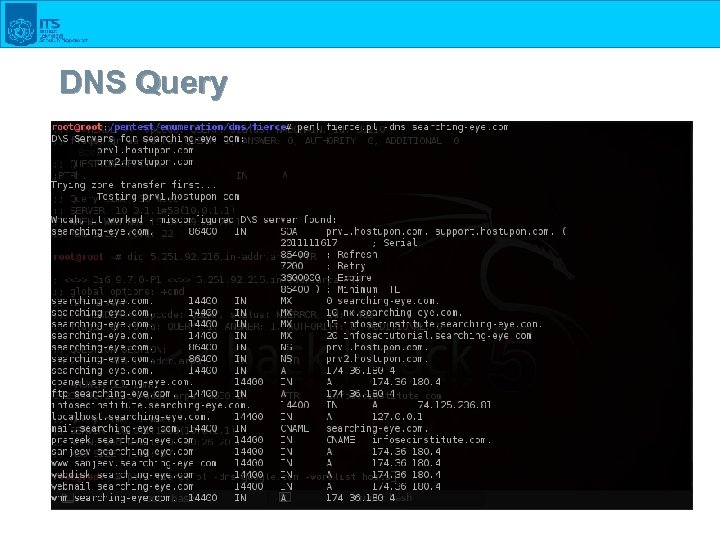 DNS Query
DNS Query
 Network Query Tools
Network Query Tools
 Information to Gather
Information to Gather
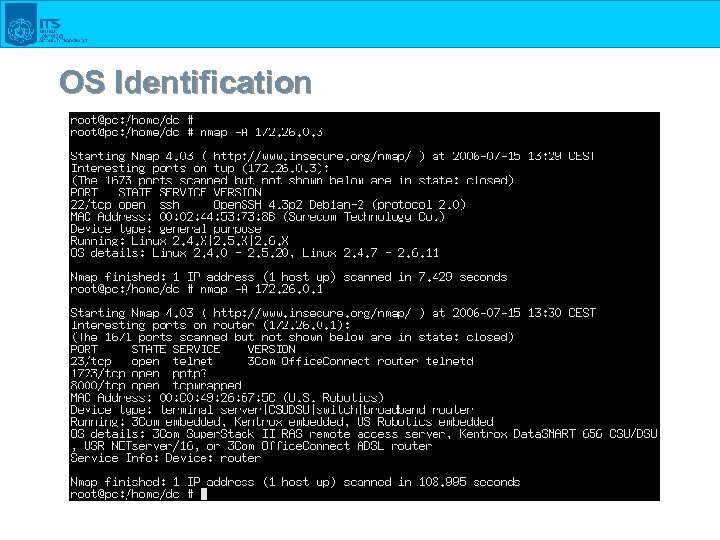 OS Identification
OS Identification
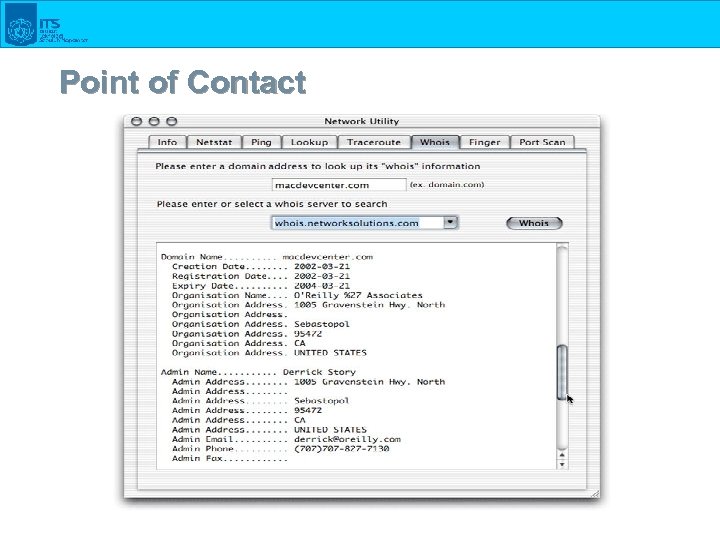 Point of Contact
Point of Contact
 Tools - Linux
Tools - Linux
 Tools – Linux (2)
Tools – Linux (2)
 Tools - Windows
Tools - Windows
 Traceroute
Traceroute
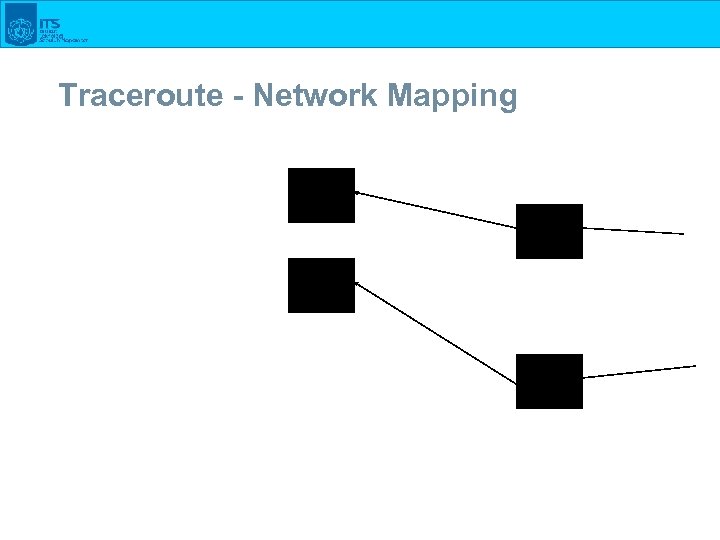
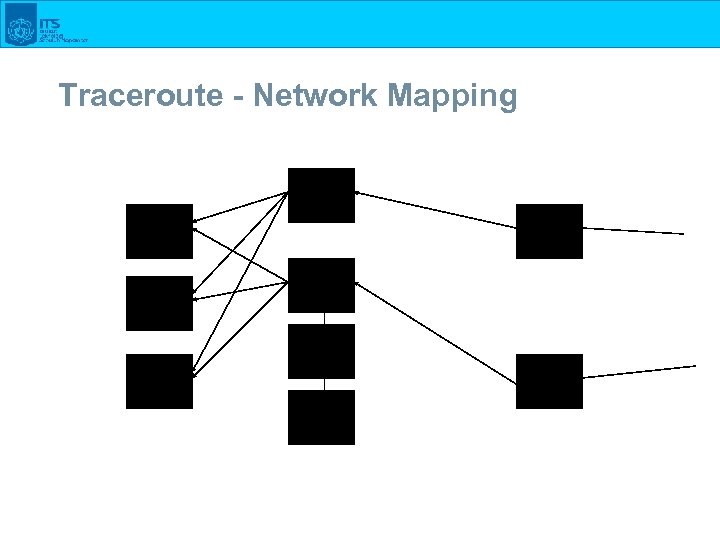
 Traceroute - Network Mapping
Traceroute - Network Mapping
 Traceroute - Network Mapping
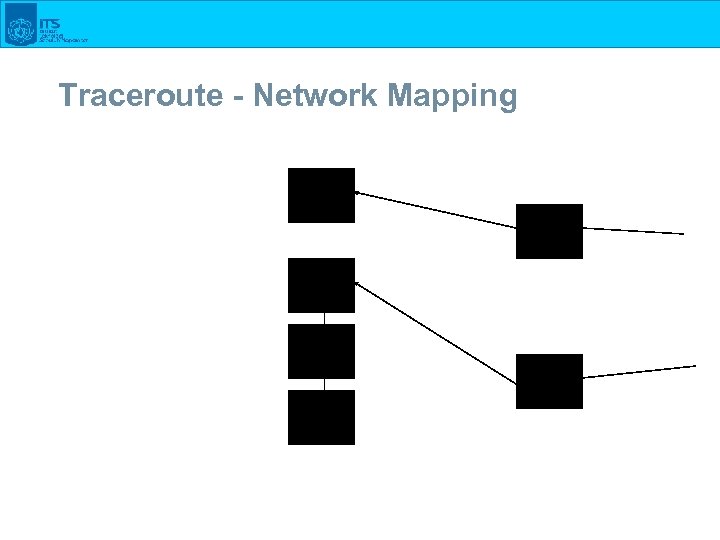
Traceroute - Network Mapping
 Traceroute - Network Mapping
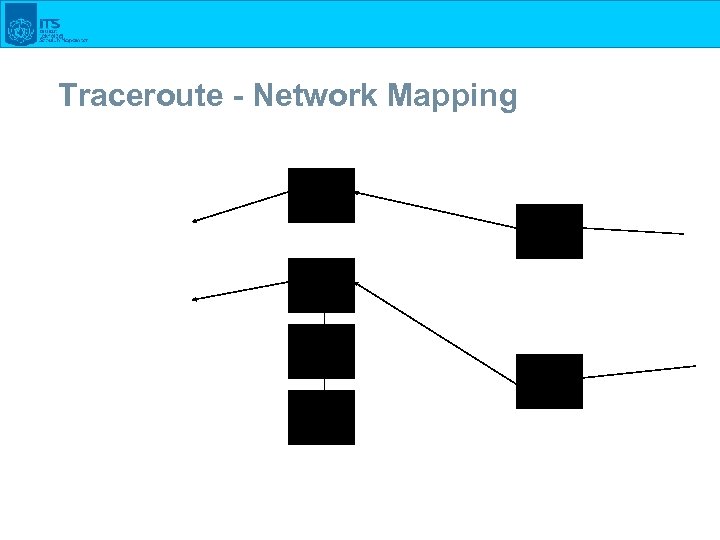
Traceroute - Network Mapping
 Traceroute - Network Mapping
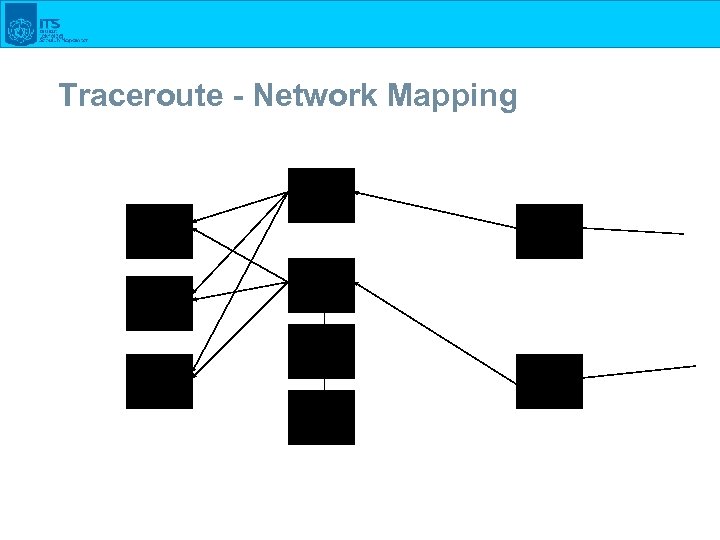
Traceroute - Network Mapping
 Traceroute - Network Mapping
Traceroute - Network Mapping
 Traceroute - Network Mapping
Traceroute - Network Mapping
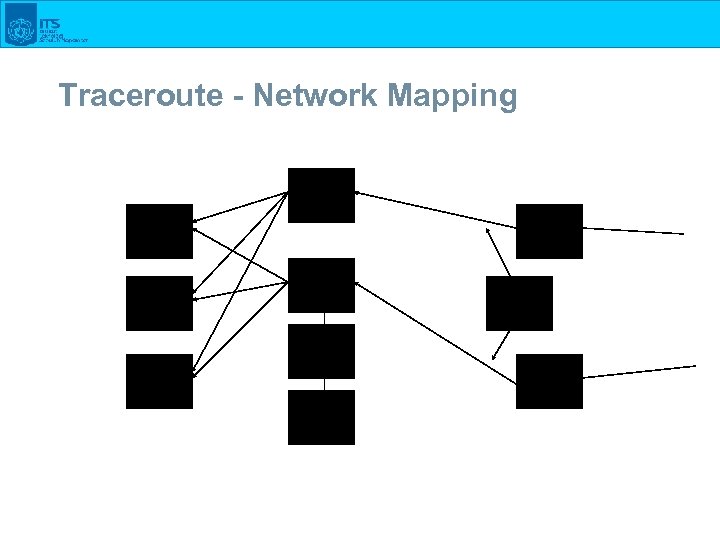 Traceroute - Network Mapping
Traceroute - Network Mapping
 Whois
Whois
 Introduction
Introduction
 Ping Sweeps
Ping Sweeps
 PING SWEEPS
PING SWEEPS
 Broadcast ICMP
Broadcast ICMP
![PING Sweeps S (SYN & ISN) + ACK[ C (SYN+!) ] RESET (not active) PING Sweeps S (SYN & ISN) + ACK[ C (SYN+!) ] RESET (not active)](https://present5.com/presentation/04dba388a2590808a15e387ca1a8c671/image-32.jpg) PING Sweeps S (SYN & ISN) + ACK[ C (SYN+!) ] RESET (not active)
PING Sweeps S (SYN & ISN) + ACK[ C (SYN+!) ] RESET (not active)
 PING Sweeps Target System
PING Sweeps Target System
 PORT SCANNING
PORT SCANNING
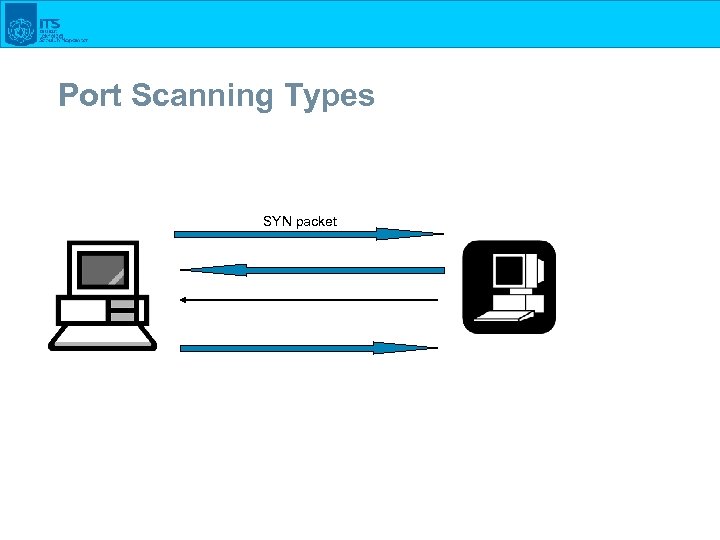 Port Scanning Types SYN packet
Port Scanning Types SYN packet
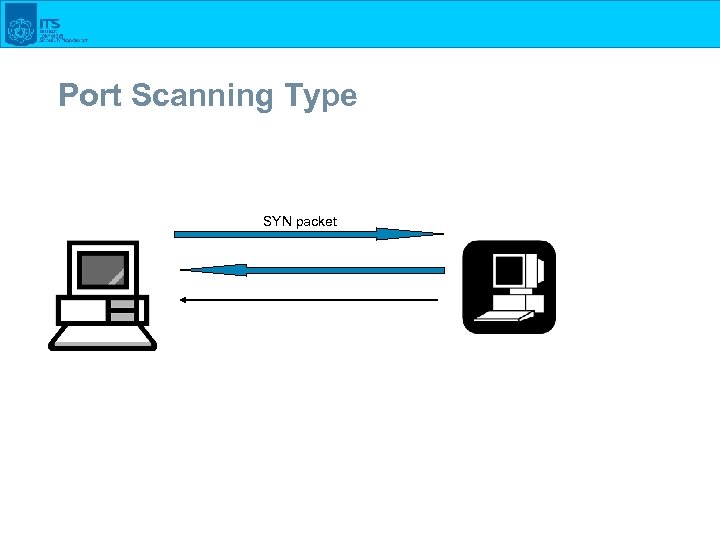 Port Scanning Type SYN packet
Port Scanning Type SYN packet
 Port Scanning Type
Port Scanning Type
 PORT Scanning
PORT Scanning
 PORT Scanning
PORT Scanning
 Operating System Detection
Operating System Detection
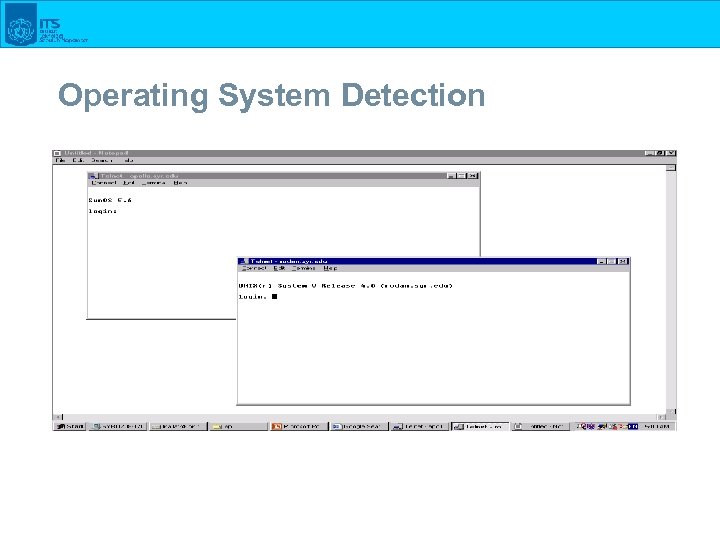 Operating System Detection
Operating System Detection
 Operating System Detection
Operating System Detection
 Operating System Detection
Operating System Detection
 Firewalking
Firewalking
 How does Firewalking work?
How does Firewalking work?
 What Firewalking needs?
What Firewalking needs?
 Getting the Waypoint
Getting the Waypoint
 Getting the Destination
Getting the Destination
 How to identify/avoid threats?
How to identify/avoid threats?
 Some tools to help us
Some tools to help us
 Introduction to Enumeration
Introduction to Enumeration
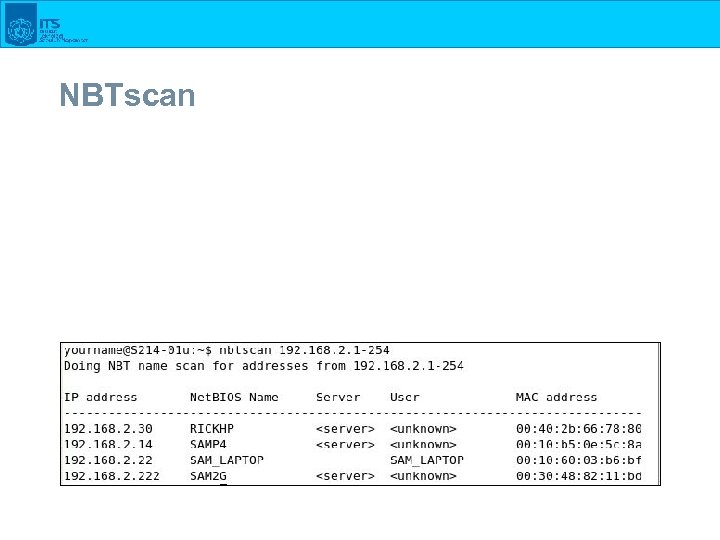 NBTscan
NBTscan
 Null Session Information
Null Session Information
 Demonstration of Null Sessions
Demonstration of Null Sessions
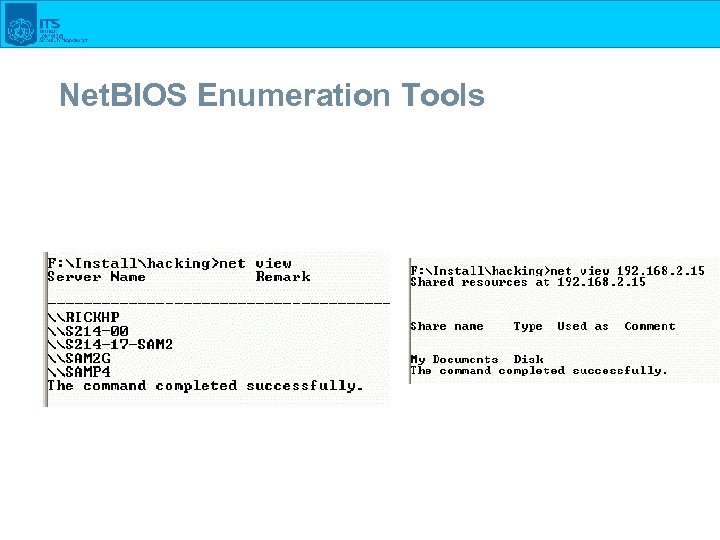 Net. BIOS Enumeration Tools
Net. BIOS Enumeration Tools
 Net. BIOS Enumeration Tools (continued)
Net. BIOS Enumeration Tools (continued)
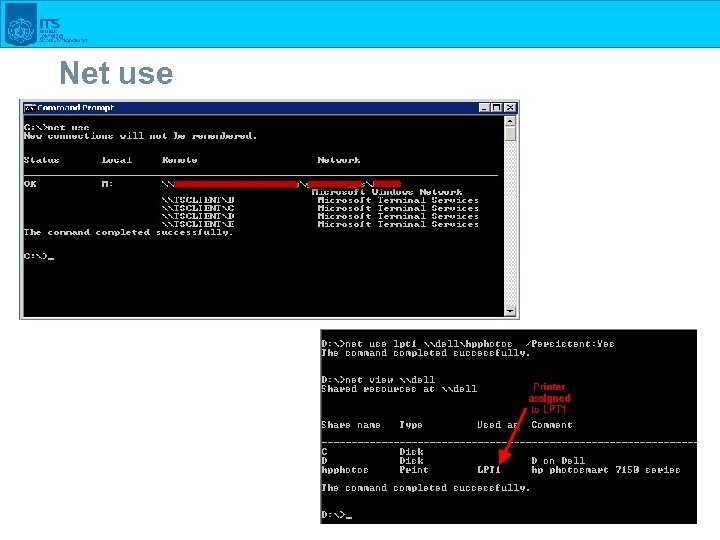 Net use
Net use
 Additional Enumeration Tools
Additional Enumeration Tools
 Net. Scan. Tools Pro
Net. Scan. Tools Pro
 Dump. Sec
Dump. Sec
 Hyena
Hyena
 Nessus. WX
Nessus. WX
 Nessus. WX (continued)
Nessus. WX (continued)
 Enumerating the *NIX Operating System
Enumerating the *NIX Operating System
 UNIX Enumeration
UNIX Enumeration