35e5376ff7e8456b09383162514ec200.ppt
- Количество слайдов: 42
 Intellectual Property Issues in Data Management How Copyright and State Laws Affect Your Ownership and Use of Factual Information Emmett Weindruch & Suzanne Gainey Moore & Van Allen PLLC April 20, 2017
Intellectual Property Issues in Data Management How Copyright and State Laws Affect Your Ownership and Use of Factual Information Emmett Weindruch & Suzanne Gainey Moore & Van Allen PLLC April 20, 2017
 Data Disputes Are Becoming Common • NYSE and various banking firms are currently disputing ownership and use of trading data. • NYSE requires brokers to execute a “NYSE Master User Agreement” which has been revised to note that NYSE owns all data submitted when they buy/sell stocks. • NYSE aggregates this data and then resells it to the firms in the form of a real-time data subscription. What IP laws protect this data? Who owns this data? How can other parties use it?
Data Disputes Are Becoming Common • NYSE and various banking firms are currently disputing ownership and use of trading data. • NYSE requires brokers to execute a “NYSE Master User Agreement” which has been revised to note that NYSE owns all data submitted when they buy/sell stocks. • NYSE aggregates this data and then resells it to the firms in the form of a real-time data subscription. What IP laws protect this data? Who owns this data? How can other parties use it?
 WHAT DO WE MEAN BY “DATA”?
WHAT DO WE MEAN BY “DATA”?
 What Is “Data”? “Data” means any type of factual information that is used in connection with you business. Examples include: • Factual information relating to your business (e. g. , names, addresses, phone numbers, email addresses, etc. ); • Information about products or services (e. g. , part nos. , specifications, etc. ); • Results from calculations (e. g. , financial information, interest rates, statistical data, values of metrics, etc. ); • Factual news or summaries (e. g. , press releases, current events, etc. ).
What Is “Data”? “Data” means any type of factual information that is used in connection with you business. Examples include: • Factual information relating to your business (e. g. , names, addresses, phone numbers, email addresses, etc. ); • Information about products or services (e. g. , part nos. , specifications, etc. ); • Results from calculations (e. g. , financial information, interest rates, statistical data, values of metrics, etc. ); • Factual news or summaries (e. g. , press releases, current events, etc. ).
 How Is Data Available to Others? Your “data” is made available to third parties via: • Your website (i. e. , web-scraping); • Software and information subscription services; • Marketing, promotional, and other informational materials; • Other publicly available materials (newspapers, press releases, etc. ).
How Is Data Available to Others? Your “data” is made available to third parties via: • Your website (i. e. , web-scraping); • Software and information subscription services; • Marketing, promotional, and other informational materials; • Other publicly available materials (newspapers, press releases, etc. ).
 Risks to Your Business • If you make your data available to others: • Third party use of your data for unauthorized products or services; • • • Someone else benefiting from the time, money, and effort your put into creating your data; Loss of control over who receives and uses your data. If you use third party data: • Risk that the third party objects to your use.
Risks to Your Business • If you make your data available to others: • Third party use of your data for unauthorized products or services; • • • Someone else benefiting from the time, money, and effort your put into creating your data; Loss of control over who receives and uses your data. If you use third party data: • Risk that the third party objects to your use.
 SCOPE OF PROTECTION UNDER COPYRIGHT LAWS
SCOPE OF PROTECTION UNDER COPYRIGHT LAWS
 Scope of Copyright Protection • Copyright protection extends to: • An original work of authorship; • • • Fixed in a tangible medium of expression ; From which it can be perceived, reproduced or otherwise communicated. This includes literary works, musical works, dramatic works, pantomimes and choreographic works, pictorial, graphic and sculptural works, motion pictures and other audiovisual works, sound recordings and architectural works.
Scope of Copyright Protection • Copyright protection extends to: • An original work of authorship; • • • Fixed in a tangible medium of expression ; From which it can be perceived, reproduced or otherwise communicated. This includes literary works, musical works, dramatic works, pantomimes and choreographic works, pictorial, graphic and sculptural works, motion pictures and other audiovisual works, sound recordings and architectural works.
 Limits of Copyright Protection • Copyright protection does not extend to any idea, procedure, process, system, method of operation, concept, principle or discovery regardless of the form in which it is described, explained, illustrated or embodied in a work. • Merger Doctrine: If there is just one way to express an idea, the idea and expression are said to merge and the expression is not protectable. • A basic tenant of copyright law is that there can be no valid copyright in facts.
Limits of Copyright Protection • Copyright protection does not extend to any idea, procedure, process, system, method of operation, concept, principle or discovery regardless of the form in which it is described, explained, illustrated or embodied in a work. • Merger Doctrine: If there is just one way to express an idea, the idea and expression are said to merge and the expression is not protectable. • A basic tenant of copyright law is that there can be no valid copyright in facts.
 Facts are not Protectable • Feist Pubs. v. Rural Telephone Serv. Co. , 499 U. S. 340 (1991) • Publishing company used telephone company’s “white pages” to create its own phone book with individuals from a wider geographic area. • Tenth Circuit affirmed the district court’s grant of summary judgment in favor of the telephone company’s copyright claim. • The Supreme Court reversed, finding that the names, towns and telephone numbers in the white pages were uncopyrightable facts. • The telephone company did not select, coordinate or arrange the facts in an original way sufficient to satisfy the minimum standards for copyright protection.
Facts are not Protectable • Feist Pubs. v. Rural Telephone Serv. Co. , 499 U. S. 340 (1991) • Publishing company used telephone company’s “white pages” to create its own phone book with individuals from a wider geographic area. • Tenth Circuit affirmed the district court’s grant of summary judgment in favor of the telephone company’s copyright claim. • The Supreme Court reversed, finding that the names, towns and telephone numbers in the white pages were uncopyrightable facts. • The telephone company did not select, coordinate or arrange the facts in an original way sufficient to satisfy the minimum standards for copyright protection.
 Facts are not Protectable • NYMEX v. ICE, 389 F. Supp. 2 d 527 (S. D. N. Y. 2005) • NYMEX offered an exchange for commodity futures contracts and calculated a daily settlement price for each futures contract. • ICE offered “swap” contracts where the fixed price of the swap contract was swapped for the variable price of underlying • The numerical settlement price of the futures contract reflects no more than a pure fact or idea of the present price of the contract. • ICE’s issuance of swap contracts did not infringe any of NYMEX’s copyrights in the settlement values. Ø “NYMEX settlement prices are a matter of basic market fact, and therefore, they are not copyrightable. ” Id. at 543.
Facts are not Protectable • NYMEX v. ICE, 389 F. Supp. 2 d 527 (S. D. N. Y. 2005) • NYMEX offered an exchange for commodity futures contracts and calculated a daily settlement price for each futures contract. • ICE offered “swap” contracts where the fixed price of the swap contract was swapped for the variable price of underlying • The numerical settlement price of the futures contract reflects no more than a pure fact or idea of the present price of the contract. • ICE’s issuance of swap contracts did not infringe any of NYMEX’s copyrights in the settlement values. Ø “NYMEX settlement prices are a matter of basic market fact, and therefore, they are not copyrightable. ” Id. at 543.
 Facts are Not Protectable • Banxcorp v. Costco Wholesale Corp. , 978 F. Supp. 2 d 280 (S. D. N. Y. 2013) • A national average interest rate calculated by Banxcorp was an uncopyrightable fact because: • The raw data used to calculate the interest rate are facts; • The method of converting the raw data into the final value is industry standard, or widely accepted as an objective methodology; and • The final value measures an empirical reality. “[Copyright] law should not allow a select group of people to gain a legal monopoly on information widely influential as a benchmark in financial markets. ” Id. at 302 -03.
Facts are Not Protectable • Banxcorp v. Costco Wholesale Corp. , 978 F. Supp. 2 d 280 (S. D. N. Y. 2013) • A national average interest rate calculated by Banxcorp was an uncopyrightable fact because: • The raw data used to calculate the interest rate are facts; • The method of converting the raw data into the final value is industry standard, or widely accepted as an objective methodology; and • The final value measures an empirical reality. “[Copyright] law should not allow a select group of people to gain a legal monopoly on information widely influential as a benchmark in financial markets. ” Id. at 302 -03.
 What Does this Mean? • • As a data owner: • Consider arranging or compiling the data in a unique manner as to bring the arrangement or compilation within the scope of copyright protection. • Basic calculations (i. e. , averaging well-known values) and formatting (i. e. , alphabetizing) are not sufficient authorship under copyright laws. • Copyright law only extends to your expression of an idea, the underlying facts are not protectable. As a data user: • You can use factual data without risk of a copyright claim. • It appears to becoming harder to use copyright law to stop use of influential “benchmark” information. • There are other claims that could affect your use of factual data.
What Does this Mean? • • As a data owner: • Consider arranging or compiling the data in a unique manner as to bring the arrangement or compilation within the scope of copyright protection. • Basic calculations (i. e. , averaging well-known values) and formatting (i. e. , alphabetizing) are not sufficient authorship under copyright laws. • Copyright law only extends to your expression of an idea, the underlying facts are not protectable. As a data user: • You can use factual data without risk of a copyright claim. • It appears to becoming harder to use copyright law to stop use of influential “benchmark” information. • There are other claims that could affect your use of factual data.
 SCOPE OF PROTECTION UNDER THE TORT OF “MISAPPROPRIATION”
SCOPE OF PROTECTION UNDER THE TORT OF “MISAPPROPRIATION”
 Origins of the Misappropriation Tort Int’l News Service v. Associated Press, 248 U. S. 215 (1918) • INS and the AP were both in the business of reporting the news from WWI. • INS stole news stories from the AP and sold them as its own. • The Court affirmed an injunction against INS. Ø Ø • “We need spend no time, however, upon the general question of property in news matter at common law, or the application of the copyright act, since it seems to us the case must turn upon the question of unfair competition in business. ” Id. at 234 -35. “[D]efendant, by its very act, admits that it is taking material that has been acquired by complainant as the result of organization and the expenditure of labor, skill, and money. . . and that defendant is appropriating it and selling it as its own. . . ” Id. at 240. Case was later abolished as Federal common law under Erie Doctrine.
Origins of the Misappropriation Tort Int’l News Service v. Associated Press, 248 U. S. 215 (1918) • INS and the AP were both in the business of reporting the news from WWI. • INS stole news stories from the AP and sold them as its own. • The Court affirmed an injunction against INS. Ø Ø • “We need spend no time, however, upon the general question of property in news matter at common law, or the application of the copyright act, since it seems to us the case must turn upon the question of unfair competition in business. ” Id. at 234 -35. “[D]efendant, by its very act, admits that it is taking material that has been acquired by complainant as the result of organization and the expenditure of labor, skill, and money. . . and that defendant is appropriating it and selling it as its own. . . ” Id. at 240. Case was later abolished as Federal common law under Erie Doctrine.
 Application of INS: Financial Services Industry S&P Corp. v. Comex, 683 F. Supp. 704 (2 d Cir. 1982) • COMEX created the “COMEX 500” index that duplicated the S&P 500. • Preliminary injunction was granted in favor of S&P. Ø “Comex is taking S&P’s Index, on which S&P expends substantial money, labor and expertise, and is planning to use it as an integral part of a commercial venture. . ” Board of Trade of City of Chicago v. Dow Jones, 98 Ill. 2 d 109 (Ill. 1983) • Board of Trade could not offer unlicensed derivative contracts linked to indices that were identical to the Dow Jones Industrial Average. Ø “We conclude that the possibility of any detriment to the public that might result [from our decision] is outweighed by the resultant encouragement to develop new indexes. . ” Id. at 588.
Application of INS: Financial Services Industry S&P Corp. v. Comex, 683 F. Supp. 704 (2 d Cir. 1982) • COMEX created the “COMEX 500” index that duplicated the S&P 500. • Preliminary injunction was granted in favor of S&P. Ø “Comex is taking S&P’s Index, on which S&P expends substantial money, labor and expertise, and is planning to use it as an integral part of a commercial venture. . ” Board of Trade of City of Chicago v. Dow Jones, 98 Ill. 2 d 109 (Ill. 1983) • Board of Trade could not offer unlicensed derivative contracts linked to indices that were identical to the Dow Jones Industrial Average. Ø “We conclude that the possibility of any detriment to the public that might result [from our decision] is outweighed by the resultant encouragement to develop new indexes. . ” Id. at 588.
 Narrowing the Scope of INS: Barclays Capital v. Theflyonthewall. com The scope of the misappropriation tort is changing. • The current trend is towards a narrow misappropriation tort. • Less of a focus on equitable issues. • Use of a specific element-by-element test. Barclays Capital v. Theflyonthewall. com, 650 F. 3 d 876 (2 d. 2011) • Barclays and other financial institutions provided their research reports and investment “recommendations” to authorized recipients (i. e. , clients). • Theflyonthewall would acquire copies of the investment recommendations and add short summaries of them to its online newsfeed. • The misappropriation claim by Barclays and the other financial firms was dismissed.
Narrowing the Scope of INS: Barclays Capital v. Theflyonthewall. com The scope of the misappropriation tort is changing. • The current trend is towards a narrow misappropriation tort. • Less of a focus on equitable issues. • Use of a specific element-by-element test. Barclays Capital v. Theflyonthewall. com, 650 F. 3 d 876 (2 d. 2011) • Barclays and other financial institutions provided their research reports and investment “recommendations” to authorized recipients (i. e. , clients). • Theflyonthewall would acquire copies of the investment recommendations and add short summaries of them to its online newsfeed. • The misappropriation claim by Barclays and the other financial firms was dismissed.
 Why Theflyonthewall was Different • The court applied principles from intellectual property law as opposed to reaching a decision solely based on equities. • Preemption. The financial firms plaintiffs’ misappropriation claim failed the preemption analysis required by the Copyright Act: • A state law claim is preempted if: (1) if the work in question is a type of work that is protected under copyright law (the “Subject Matter Requirement”); and (2) § it seeks to vindicate rights that are equivalent to one of the exclusive rights protected under copyright law (the “General Scope Requirement”) No Extra Elements. The financial firm plaintiffs’ could not show that Theflyonthewall’s acts amounted to a cause of action have “extra elements” beyond a copyright claim.
Why Theflyonthewall was Different • The court applied principles from intellectual property law as opposed to reaching a decision solely based on equities. • Preemption. The financial firms plaintiffs’ misappropriation claim failed the preemption analysis required by the Copyright Act: • A state law claim is preempted if: (1) if the work in question is a type of work that is protected under copyright law (the “Subject Matter Requirement”); and (2) § it seeks to vindicate rights that are equivalent to one of the exclusive rights protected under copyright law (the “General Scope Requirement”) No Extra Elements. The financial firm plaintiffs’ could not show that Theflyonthewall’s acts amounted to a cause of action have “extra elements” beyond a copyright claim.
 Elements of a Misappropriation Claim • The Second Circuit identified several “extra elements” that are required for a misappropriation claim to survive preemption by federal Copyright law: 1. 2. Free-riding by a defendant. 3. • Time-sensitive value of factual information. Threat to the very existence of the product or service provided by the plaintiff. Additionally, the Second Circuit identified several other relevant elements: 1. Plaintiff generates or collects information at some cost or expense. 2. Defendant’s use of the information is in direct competition with a product or service offered by the plaintiff. 3. The ability of other parties to free-ride on the efforts of the plaintiff would so reduce the incentive to produce the product or service that its existence or quality would be substantially threatened.
Elements of a Misappropriation Claim • The Second Circuit identified several “extra elements” that are required for a misappropriation claim to survive preemption by federal Copyright law: 1. 2. Free-riding by a defendant. 3. • Time-sensitive value of factual information. Threat to the very existence of the product or service provided by the plaintiff. Additionally, the Second Circuit identified several other relevant elements: 1. Plaintiff generates or collects information at some cost or expense. 2. Defendant’s use of the information is in direct competition with a product or service offered by the plaintiff. 3. The ability of other parties to free-ride on the efforts of the plaintiff would so reduce the incentive to produce the product or service that its existence or quality would be substantially threatened.
 What Does “Free-Riding” Really Mean? • The definition of “Free-riding” is based on the INS v. AP case: Ø • Free-riding is “taking material that has been acquired by complainant as the result of organization and the expenditure of labor, skill, and money, and which is salable by the complainant for money, and. . . appropriating it and selling it as the defendant’s own. ” Theflyonthewall did not commit misappropriation because it did not take the financial firm’s recommendations and appropriate them as its own. Ø “The Firms are making the news; Fly, despite the Firms’ understandable desire to protect their business model, is breaking it. ”
What Does “Free-Riding” Really Mean? • The definition of “Free-riding” is based on the INS v. AP case: Ø • Free-riding is “taking material that has been acquired by complainant as the result of organization and the expenditure of labor, skill, and money, and which is salable by the complainant for money, and. . . appropriating it and selling it as the defendant’s own. ” Theflyonthewall did not commit misappropriation because it did not take the financial firm’s recommendations and appropriate them as its own. Ø “The Firms are making the news; Fly, despite the Firms’ understandable desire to protect their business model, is breaking it. ”
 Example No. 1 Facts: § TV broadcaster publicly broadcasts its programs on its own cable channels. § Software company monitors and records TV content and transforms the recordings into a searchable database of clips. § Is the software company misappropriating the TV broadcaster’s programs? No – Fox News Network v. TVEyes, 43 F. Supp. 3 d 379 (S. D. N. Y. 2014) “TVEyes is not a valuable service because its subscribers credit it as a reliable news outlet, it is valuable because it reports what the news outlets and commentators are saying and therefore does not "scoop" or free-ride on the news services. Thus, the hot news misappropriation claim is preempted. . . because if fails the extra element test. ”
Example No. 1 Facts: § TV broadcaster publicly broadcasts its programs on its own cable channels. § Software company monitors and records TV content and transforms the recordings into a searchable database of clips. § Is the software company misappropriating the TV broadcaster’s programs? No – Fox News Network v. TVEyes, 43 F. Supp. 3 d 379 (S. D. N. Y. 2014) “TVEyes is not a valuable service because its subscribers credit it as a reliable news outlet, it is valuable because it reports what the news outlets and commentators are saying and therefore does not "scoop" or free-ride on the news services. Thus, the hot news misappropriation claim is preempted. . . because if fails the extra element test. ”
 Example No. 2 Facts: § Promoter of chess competitions organizes and runs live chess tournaments. § Website collects information about the chess matches from secondary sources and creates a virtual chess board that recreates each match. § Is the website owner misappropriating the Chess promoter’s matches? No – World Chess US v. Chessgame Servs. , 2016 U. S. Dist. LEXIS 165318 (S. D. N. Y. 2016) “[Defendants’] virtual chessboard and compilation of players' moves display factual data that [Defendant] has assembled and transmitted. . . themselves. ”
Example No. 2 Facts: § Promoter of chess competitions organizes and runs live chess tournaments. § Website collects information about the chess matches from secondary sources and creates a virtual chess board that recreates each match. § Is the website owner misappropriating the Chess promoter’s matches? No – World Chess US v. Chessgame Servs. , 2016 U. S. Dist. LEXIS 165318 (S. D. N. Y. 2016) “[Defendants’] virtual chessboard and compilation of players' moves display factual data that [Defendant] has assembled and transmitted. . . themselves. ”
 Example No. 3 Facts: Newspaper collects information and publishes its own news stories. § A rival newspaper publishes similar news stories that are factual in nature (i. e. , civil lawsuits filed, the reduction of hours at local businesses, planned road projects, etc. ) but the similar articles are not published until 2 to 5 days later. § No – Ste. Genevieve Media, LLC v. Pulitzer Missouri Newspapers, Inc. , 2016 U. S. Dist. LEXIS 143686 (S. E. MO 2016) “The facts in this case are quite different from those in INS, in which. . . the defendant published news obtained from the plaintiff prior to or simultaneously with the plaintiff's publication. ”
Example No. 3 Facts: Newspaper collects information and publishes its own news stories. § A rival newspaper publishes similar news stories that are factual in nature (i. e. , civil lawsuits filed, the reduction of hours at local businesses, planned road projects, etc. ) but the similar articles are not published until 2 to 5 days later. § No – Ste. Genevieve Media, LLC v. Pulitzer Missouri Newspapers, Inc. , 2016 U. S. Dist. LEXIS 143686 (S. E. MO 2016) “The facts in this case are quite different from those in INS, in which. . . the defendant published news obtained from the plaintiff prior to or simultaneously with the plaintiff's publication. ”
 Some States Don’t Apply Theflyonthewall § Illinois appears to have not adopted Theflyonthewall and instead continues to apply the broader tort of misappropriation. Chicago Board of Option Exchange v. Int’l Sercurities Exchange, 973 N. E. 2 d 390, 407 (Ill. App. Ct. 2012) § Affirmed an injunction preventing ISE’s unlicensed sale of index options linked to plaintiff’s indices (e. g. , DJIA, S&P 500). § Court did not look at the 5 factors outlined in Theflyonthewall. “It is also clear that the plaintiff’s claims are not predicated on wrongful copying. . . Rather, plaintiff’s misappropriation claim is premised on ISE’s unauthorized use of the research, expertise, reputation and goodwill associated with plaintiffs’ product for ISE’s own gain. ” Narrow misappropriation (e. g. , Second Circuit) versus broad misappropriation (e. g. , Illinois). Ø •
Some States Don’t Apply Theflyonthewall § Illinois appears to have not adopted Theflyonthewall and instead continues to apply the broader tort of misappropriation. Chicago Board of Option Exchange v. Int’l Sercurities Exchange, 973 N. E. 2 d 390, 407 (Ill. App. Ct. 2012) § Affirmed an injunction preventing ISE’s unlicensed sale of index options linked to plaintiff’s indices (e. g. , DJIA, S&P 500). § Court did not look at the 5 factors outlined in Theflyonthewall. “It is also clear that the plaintiff’s claims are not predicated on wrongful copying. . . Rather, plaintiff’s misappropriation claim is premised on ISE’s unauthorized use of the research, expertise, reputation and goodwill associated with plaintiffs’ product for ISE’s own gain. ” Narrow misappropriation (e. g. , Second Circuit) versus broad misappropriation (e. g. , Illinois). Ø •
 “Hot News” Misappropriation Isn’t Recognized By All States § States that recognize hot news misappropriation: § Pennsylvania – Scranton Times v. Wilkes-Barre Pub. Co. , 2009 U. S. Dist. LEXIS 87261 (M. D. Pa. 2009) § Missouri - Fred Wehrenberg Circuit of Theatres v. Moviefone, 73 F. Supp. 2 d 1044, 1050 (E. D. Mo. 1999) § Wisconsin - Atlantic Mut. Ins. v. Badger Medical Supply, 528 N. W. 2 d 486 (Wis. 1999) § States that don’t recognize hot news misappropriation: § Ohio - Allure Jewelers, v. Ulu, 2012 U. S. Dist. LEXIS 13440 (S. D. Oh. 2012) § Tennessee - Brainard v. Vassar, 561 F. Supp. 2 d 922 (M. D. Tenn. 2008) § Virginia - Thousand Oaks Barrel v. Deep South Barrel, 2017 U. S. Dist. LEXIS 40011 (E. D. Va. 2017)
“Hot News” Misappropriation Isn’t Recognized By All States § States that recognize hot news misappropriation: § Pennsylvania – Scranton Times v. Wilkes-Barre Pub. Co. , 2009 U. S. Dist. LEXIS 87261 (M. D. Pa. 2009) § Missouri - Fred Wehrenberg Circuit of Theatres v. Moviefone, 73 F. Supp. 2 d 1044, 1050 (E. D. Mo. 1999) § Wisconsin - Atlantic Mut. Ins. v. Badger Medical Supply, 528 N. W. 2 d 486 (Wis. 1999) § States that don’t recognize hot news misappropriation: § Ohio - Allure Jewelers, v. Ulu, 2012 U. S. Dist. LEXIS 13440 (S. D. Oh. 2012) § Tennessee - Brainard v. Vassar, 561 F. Supp. 2 d 922 (M. D. Tenn. 2008) § Virginia - Thousand Oaks Barrel v. Deep South Barrel, 2017 U. S. Dist. LEXIS 40011 (E. D. Va. 2017)
 OTHER FEDERAL AND STATE LAWS
OTHER FEDERAL AND STATE LAWS
 State Unfair Competition Laws Framing copyright claims as various state law claims in order to avoid preemption have been largely rejected by the courts. • R. W. Beck, Inc. v. E 3 Consulting, LLC, 577 F. 3 d 1133 (10 th Cir. 2009) • • Allegations that the defendant committed unfair competition by “knowingly” copying material was insufficient to avoid preemption. Baltimore Orioles, Inc. v. Major League Baseball Players Ass’n, 805 F. 2 d 663 (7 th Cir. 1986) • MLB clubs and the players association were in a dispute over ownership of broadcast rights in players’ performances. • Seventh Circuit rejected an attempt by players association to avoid preemption by framing their claim as a state law right of publicity claim.
State Unfair Competition Laws Framing copyright claims as various state law claims in order to avoid preemption have been largely rejected by the courts. • R. W. Beck, Inc. v. E 3 Consulting, LLC, 577 F. 3 d 1133 (10 th Cir. 2009) • • Allegations that the defendant committed unfair competition by “knowingly” copying material was insufficient to avoid preemption. Baltimore Orioles, Inc. v. Major League Baseball Players Ass’n, 805 F. 2 d 663 (7 th Cir. 1986) • MLB clubs and the players association were in a dispute over ownership of broadcast rights in players’ performances. • Seventh Circuit rejected an attempt by players association to avoid preemption by framing their claim as a state law right of publicity claim.
 Trade Secret Protection • A Trade Secret is information that (1) derives independent economic value (2) from not being generally known to, and not being readily ascertainable by proper means by, other persons and (3) is the subject of reasonable efforts to maintain its secrecy. • United States of America v. Nosal, 828 F. 3 d 865 (9 th Cir. 2016) • Nosal used the passwords of colleagues to access former employers’ records in order to assist him in starting a competing business. • Nosal argued the data was not a trade secret because it was composed largely of public information. • The Ninth Circuit disagreed, stating that a trade secret “may consist of a compilation of data, public sources or a combination of proprietary and public sources” and upheld Nosal’s conviction.
Trade Secret Protection • A Trade Secret is information that (1) derives independent economic value (2) from not being generally known to, and not being readily ascertainable by proper means by, other persons and (3) is the subject of reasonable efforts to maintain its secrecy. • United States of America v. Nosal, 828 F. 3 d 865 (9 th Cir. 2016) • Nosal used the passwords of colleagues to access former employers’ records in order to assist him in starting a competing business. • Nosal argued the data was not a trade secret because it was composed largely of public information. • The Ninth Circuit disagreed, stating that a trade secret “may consist of a compilation of data, public sources or a combination of proprietary and public sources” and upheld Nosal’s conviction.
 Trespass to Chattels • Courts have recognized that the unauthorized use of web crawling or scraping tools can give rise to a trespass to chattels claim, but generally only where there is evidence of tangible interference with systems. • e. Bay, Inc. v. Bidder’s Edge, Inc. , 100 F. Supp. 2 d 1058 (N. D. Cal. 2000) • • Court focused on the fact that defendant’s spiders (which hit e. Bay’s site about 100, 000 times per day) deprived e. Bay of the ability to use a portion of its servers and server capacity. Ticketmaster Corp. v. Tickets. com, Inc. , No. CV 997654 HLHVBKX, 2003 BL 2425 (C. D. Cal. Mar. 7, 2003) • Ticketmaster failed to present any evidence that defendant’s scraping of its website caused physical harm to Ticketmaster or impeded Ticketmaster’s ability to use its servers.
Trespass to Chattels • Courts have recognized that the unauthorized use of web crawling or scraping tools can give rise to a trespass to chattels claim, but generally only where there is evidence of tangible interference with systems. • e. Bay, Inc. v. Bidder’s Edge, Inc. , 100 F. Supp. 2 d 1058 (N. D. Cal. 2000) • • Court focused on the fact that defendant’s spiders (which hit e. Bay’s site about 100, 000 times per day) deprived e. Bay of the ability to use a portion of its servers and server capacity. Ticketmaster Corp. v. Tickets. com, Inc. , No. CV 997654 HLHVBKX, 2003 BL 2425 (C. D. Cal. Mar. 7, 2003) • Ticketmaster failed to present any evidence that defendant’s scraping of its website caused physical harm to Ticketmaster or impeded Ticketmaster’s ability to use its servers.
 Computer Fraud and Abuse Act • Prohibits access to a computer, website, server or database either “without authorization” or in a way that “exceeds authorized access. ” • Does accessing a website in a manner prohibited by the terms of use invoke the CFAA? The courts are split: • Am. Online, Inc. v. LCGM, Inc. , 46 F. Supp. 2 d 444 (E. D. Va. 1998) • Virginia court found that LCGM’s use of software to collect email addresses of AOL members violated the Terms of Service. • U. S. v. Nosal, 676 F. 3 d 854 (9 th Cir. 2012) • Ninth Circuit found that the phrase “exceeds authorized access” in the CFAA does not extend to violations of use restrictions, but rather concerns “hacking – the circumvention of technological access barriers. ”
Computer Fraud and Abuse Act • Prohibits access to a computer, website, server or database either “without authorization” or in a way that “exceeds authorized access. ” • Does accessing a website in a manner prohibited by the terms of use invoke the CFAA? The courts are split: • Am. Online, Inc. v. LCGM, Inc. , 46 F. Supp. 2 d 444 (E. D. Va. 1998) • Virginia court found that LCGM’s use of software to collect email addresses of AOL members violated the Terms of Service. • U. S. v. Nosal, 676 F. 3 d 854 (9 th Cir. 2012) • Ninth Circuit found that the phrase “exceeds authorized access” in the CFAA does not extend to violations of use restrictions, but rather concerns “hacking – the circumvention of technological access barriers. ”
 FLOWCHART FOR ANALYZING CLAIMS RELATING TO “DATA”
FLOWCHART FOR ANALYZING CLAIMS RELATING TO “DATA”
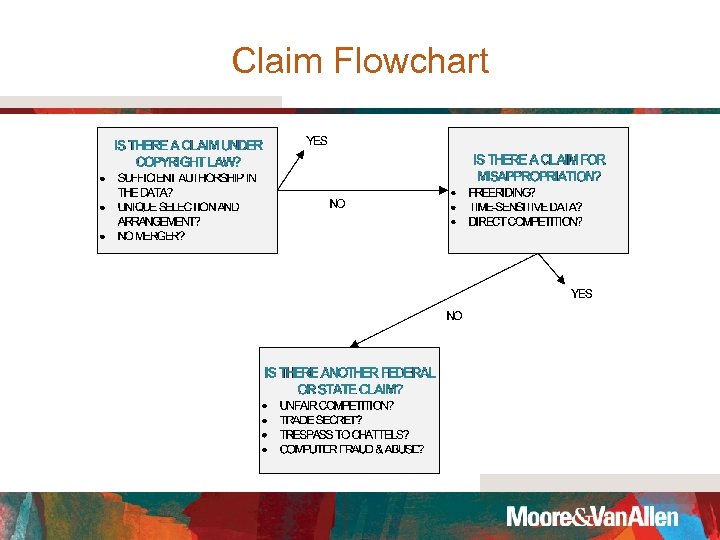 Claim Flowchart
Claim Flowchart
 PRACTICE TIPS FOR PROTECTING YOUR DATA
PRACTICE TIPS FOR PROTECTING YOUR DATA
 Website: Terms of Use • Make sure your website has an appropriate terms of use. • Recite ownership of all content, data, etc. available on the website. • Prohibit access by webcrawlers, scrapers, robots, etc. License use of the site for informational purposes only. Prohibit data collection. Prohibit any re-use or re-distribution of web content. Reserve the right to block users and/or remove content. • • • Include a liquidated damages clause. • Make sure your website terms of use is enforceable. • Click-wrap versus browse-wrap terms.
Website: Terms of Use • Make sure your website has an appropriate terms of use. • Recite ownership of all content, data, etc. available on the website. • Prohibit access by webcrawlers, scrapers, robots, etc. License use of the site for informational purposes only. Prohibit data collection. Prohibit any re-use or re-distribution of web content. Reserve the right to block users and/or remove content. • • • Include a liquidated damages clause. • Make sure your website terms of use is enforceable. • Click-wrap versus browse-wrap terms.
 Website: Other Technological Measures Use other technical measures to use on your website: • Block troublesome IP addresses; • Require a login for certain sections of your website; • Embed information in media objects, such as images, videos, . pdfs, and other non-text objects; • Create “honey pot” pages that only automated crawlers will visit.
Website: Other Technological Measures Use other technical measures to use on your website: • Block troublesome IP addresses; • Require a login for certain sections of your website; • Embed information in media objects, such as images, videos, . pdfs, and other non-text objects; • Create “honey pot” pages that only automated crawlers will visit.
 Provide Access to Data as Part of a Service • Provide access to your data only as part of a larger service (data feed, subscription service, etc. ). • “Stadium Theory” – User access is contingent on certain terms and conditions. • Examples include financial subscription services (e. g. , Bloomberg terminals), real-time sports streams, subscription-based web portals, etc.
Provide Access to Data as Part of a Service • Provide access to your data only as part of a larger service (data feed, subscription service, etc. ). • “Stadium Theory” – User access is contingent on certain terms and conditions. • Examples include financial subscription services (e. g. , Bloomberg terminals), real-time sports streams, subscription-based web portals, etc.
 Other Contract Considerations • Issues to consider when sharing data with a contractor, vendor, service provider, etc. : • Confirm ownership of data and all derivative works thereof. • Limited, revocable license to use data for specific purpose. • Prohibit use of data with third party products or services. • Require the destruction or return of all data.
Other Contract Considerations • Issues to consider when sharing data with a contractor, vendor, service provider, etc. : • Confirm ownership of data and all derivative works thereof. • Limited, revocable license to use data for specific purpose. • Prohibit use of data with third party products or services. • Require the destruction or return of all data.
 PRACTICE TIPS FOR USING THIRD PARTY DATA
PRACTICE TIPS FOR USING THIRD PARTY DATA
 Avoid Copyright and Trade Secret Issues • If you use factual data of a third party, DON’T use the unique compilation or arrangement of the data in whole. • • Third party may have copyrights in the compilation or arrangement of all of the data, but that protection will not extend to individual factual elements. DON’T forget that the compilation or arrangement of data can be considered a trade secret. • But if data is publicly available without confidentiality or usage restrictions, then it is likely not a trade secret.
Avoid Copyright and Trade Secret Issues • If you use factual data of a third party, DON’T use the unique compilation or arrangement of the data in whole. • • Third party may have copyrights in the compilation or arrangement of all of the data, but that protection will not extend to individual factual elements. DON’T forget that the compilation or arrangement of data can be considered a trade secret. • But if data is publicly available without confidentiality or usage restrictions, then it is likely not a trade secret.
 Avoid “Hot News” Misappropriation • DON’T free ride – do not pass off third party data as your own. • DO include an attribution – give credit to the owner of any data that you use by including their name or a link to where the data was obtained. • DON’T imply any endorsement or sponsorship by the third party. • DON’T use information that might be time sensitive – let the data “cool off” before using it. • DON’T use information in a directly competing product or service.
Avoid “Hot News” Misappropriation • DON’T free ride – do not pass off third party data as your own. • DO include an attribution – give credit to the owner of any data that you use by including their name or a link to where the data was obtained. • DON’T imply any endorsement or sponsorship by the third party. • DON’T use information that might be time sensitive – let the data “cool off” before using it. • DON’T use information in a directly competing product or service.
 Avoid Screen Scraping Issues • DON’T violate a third party’s posted Terms of Use or Terms of Service. • DO ensure that any screen-scraping or web crawling tools used do not impact the third party’s system or server performance. • DON’T use any access credentials that belong to a third party to access data you would not otherwise have access to. • DON’T ask a third party to obtain data for you that you otherwise are unauthorized to access.
Avoid Screen Scraping Issues • DON’T violate a third party’s posted Terms of Use or Terms of Service. • DO ensure that any screen-scraping or web crawling tools used do not impact the third party’s system or server performance. • DON’T use any access credentials that belong to a third party to access data you would not otherwise have access to. • DON’T ask a third party to obtain data for you that you otherwise are unauthorized to access.
 Emmett Weindruch emmettweindruch@mvalaw. com (704) 331 -1074 Suzanne Gainey suzannegainey@mvalaw. com (704) 331 -3559
Emmett Weindruch emmettweindruch@mvalaw. com (704) 331 -1074 Suzanne Gainey suzannegainey@mvalaw. com (704) 331 -3559


