789228d192bc8343b4326f3f1d541337.ppt
- Количество слайдов: 17

Integrity Through Mediated Interfaces PI Meeting: Feb 22 -23, 2000 Bob Balzer Information Sciences Institute balzer@isi. edu Legend: Changes from previous PI meeting

Technical Objectives • Wrap Data with Integrity Marks – Insure its Integrity – Record its processing history – Reconstruct it from this history if it is corrupted • by program bugs • by malicious attacks • Demo these capabilities on major COTS product – Microsoft Office Suite (Power. Point & Word only) – Also demo on a mission critical military system

Existing Practice • • • Integrity Stove-Piped on Tool-by-Tool Basis End-to-End Integrity Not Supported Persistent Data only Safeguarded by OS This Slide Intentionally Blank Corruption Detection is Ad-Hoc Corruption Repair – Based on Backups – Not Integrated with Detection
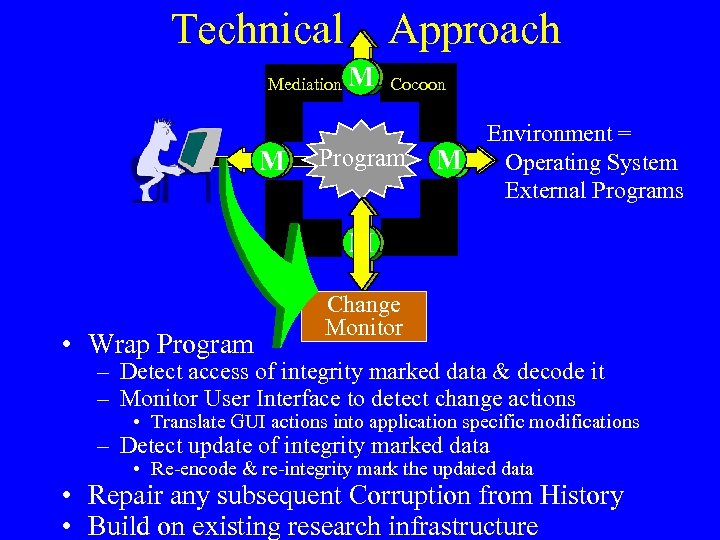
Technical Mediation M Approach M Cocoon Program M Environment = Operating System External Programs M • Wrap Program Change Monitor – Detect access of integrity marked data & decode it – Monitor User Interface to detect change actions • Translate GUI actions into application specific modifications – Detect update of integrity marked data • Re-encode & re-integrity mark the updated data • Repair any subsequent Corruption from History • Build on existing research infrastructure

Major Risks and Planned Mitigation • Ability to detect application-level modifications Application Openness Spectrum: – Event-Generators: Capture as transaction history – Scripting API: Examine state to infer action – Black-Box: Mediate GUI to infer action => Generic Mediators + Tool Specific mapping Mediation M M Cocoon Program M Environment = Operating System External Programs M Two Level Architecture Change Monitor 1. Application Independent GUI Monitor signals action types 2. Application Dependent Change Monitor • Determines Action Parameters • Logs Modification History

Major Risks and Planned Mitigation • Ability to detect application-level modifications Application Openness Spectrum: – Event-Generators: Capture as transaction history – Scripting API: Examine state to infer action – Black-Box: Mediate GUI to infer action => Generic Mediators + Tool Specific mapping • Ability to protect transaction history => Hide the location of the transaction history • Virtual File System wrapper • System-level Randomization Techniques • Tool-Specific Modification Trackers Expensive => Automate common portions => Provide rule-based scripting language

Accomplishments To Date • Corruption Detector (for MS Word 2000) – IDs Document Version on Save (in Document) – Records Document Cryptographic Digest on Save – Checks Document Cryptographic Digest on Load Demo GUI Monitor • – Application Independent • Prototype Change Monitor for MS Word – Signals types of actions (e. g. buttonclick, typing) – Determines parameters for application-level action Demo – Records transaction history (for possible Replay)

Accomplishments To Date Other IA Projects • IFE 2. 3 Re. Run:
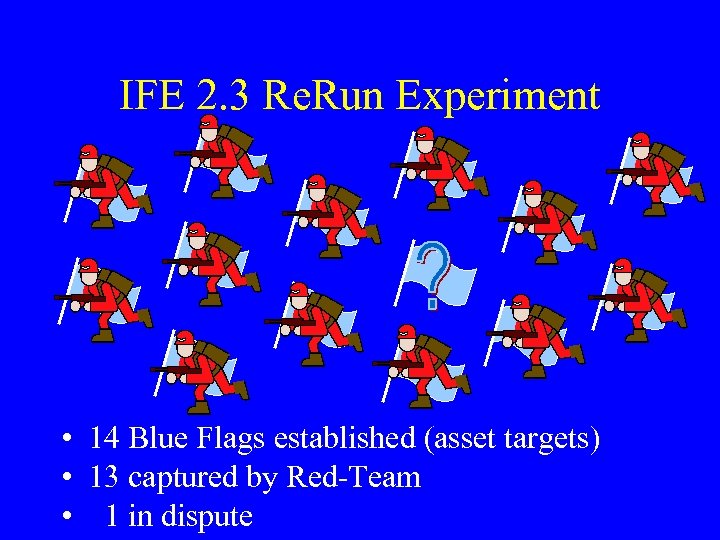
IFE 2. 3 Re. Run Experiment • 14 Blue Flags established (asset targets) • 13 captured by Red-Team • 1 in dispute

IFE 2. 3 Re. Run Wrapper Defenses Tolerance Detection Prevention Attacks Layered Protection • Prevent modification of – Database – EDI Orders – Executables – Execution by anyone other than DB Manager by anyone other than FTP Server by anyone (during “production”) of unauthorized processes of detected modified executables • Detect modification of – Executables by checking hidden digital signature • Tolerate modification of – Executables by reinstalling hidden saved copy

Accomplishments To Date Other IA Projects • IFE 2. 3 Re. Run: only uncaptured blue flag(in dispute) • NT Security Manager – Policy specifies Demo • which processes can run • whether executables should be integrity checked • how processes should be wrapped – All processes wrapped before execution • New AIA Project : Enterprise Wrappers (ISI/ NAI) – Goal: Network Management of Host Wrappers Common NT/Linux Interface & Infrastructure

Measures of Success • Widespread Deployment of Integrity Manager for MS-Office • Extensibility of Integrity Manager to other COTS products • Ease of creating Modification Trackers • Resistance to Malicious Attacks – Corruption Avoidance – Corruption Detection – Corruption Repair => Red-Team Experiment

Expected Major Achievements • for Integrity Marked Documents: – End-To-End Data Integrity (through multiple tools/sessions) – Modifications Monitored, Authorized, & Recorded • Authorization Control of Users, Tools, and Operations • All Changes Attributed and Time Stamped – Assured Detection of Corruption – Ability to Restore Corrupted Data • Ability to operate with COTS products • MS-Office Documents Integrity Marked • Mission Critical Military System Integrity Marked

Task Schedule • Dec 99: Tool-Level Integrity Manager – Monitor & Authorize Tool access & updates • Jun 00: Operation-Level Integrity Manager – Monitor, Authorize, & Record Modifications • Dec 00: Integrity Management for MS-Office • Jun 01: Corruption Repair • Dec 01: Integrity Management for Mission Critical Military System • Jun 02: Automated Modification Tracking

Key Outstanding Issues • None Yet

Transition of Technology • Piggyback our Technology on a widely used Target Product (MS Office) – Integrity Manager automatically invoked as needed • Make technology available for COTS products • Work with Vendors to encourage publication of modification events

Needed PM Assistance • None Yet Watch this space (Summer PI meeting) Help identifying suitable mission critical military system
789228d192bc8343b4326f3f1d541337.ppt