357fc5ca512f19b8282372cced2a79d1.ppt
- Количество слайдов: 26

Integrating Web Application Security into the IT Curriculum James Walden Northern Kentucky University SIGITE 2008: 16 -18 Oct

Topics 1. 2. 3. 4. Why should we teach web application security? What material do we need to cover? How should we cover that material? Where do we go from here? SIGITE 2008: 16 -18 Oct
Is Web Hacking Really That Easy? SIGITE 2008: 16 -18 Oct “Exploits of a Mom”, XKCD
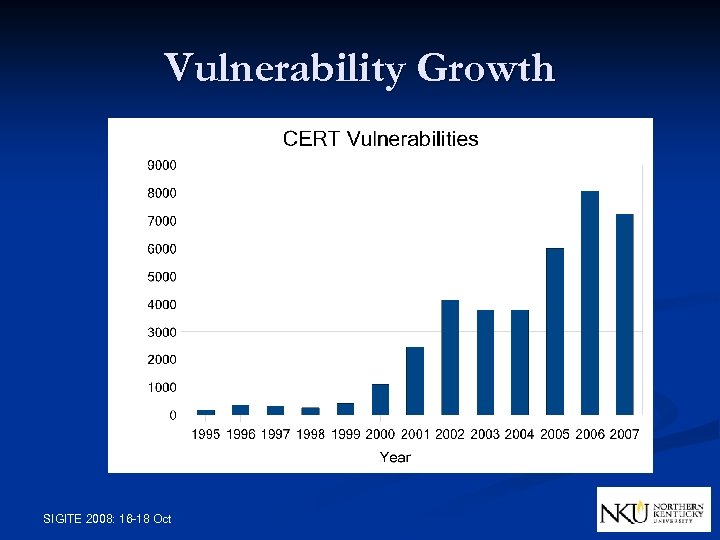
Vulnerability Growth SIGITE 2008: 16 -18 Oct
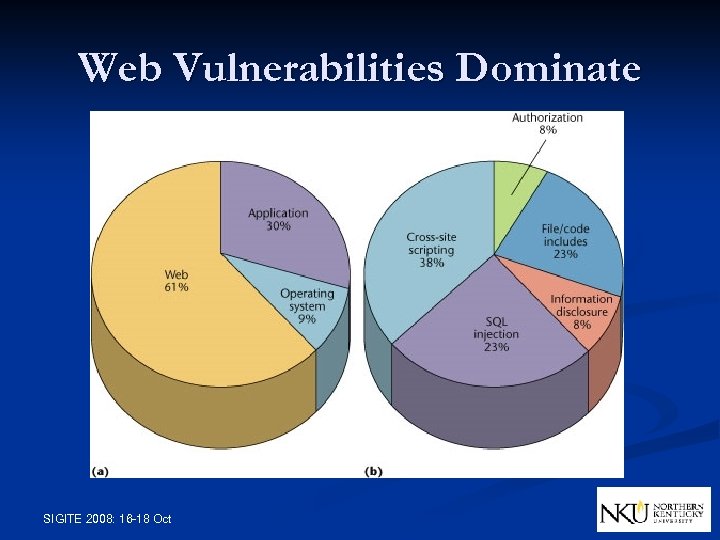
Web Vulnerabilities Dominate SIGITE 2008: 16 -18 Oct
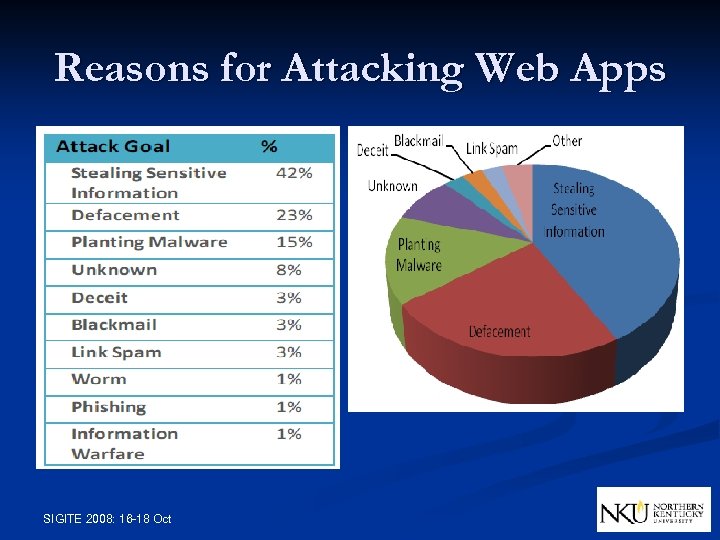
Reasons for Attacking Web Apps SIGITE 2008: 16 -18 Oct
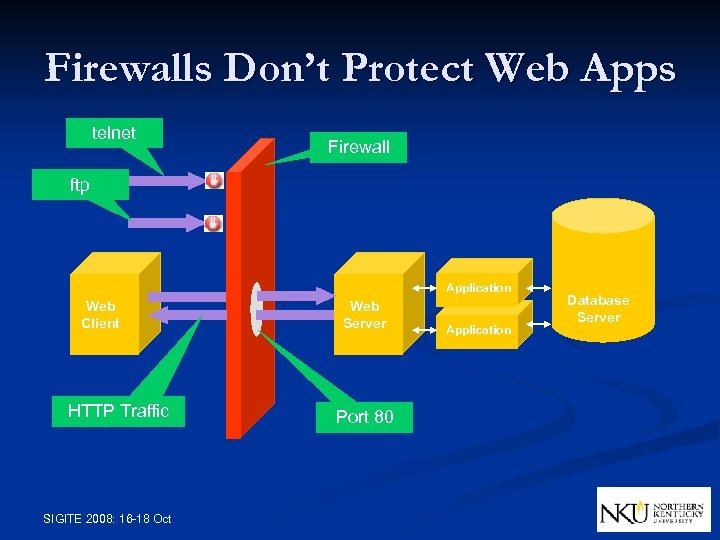
Firewalls Don’t Protect Web Apps telnet Firewall ftp Application Web Client HTTP Traffic SIGITE 2008: 16 -18 Oct Web Server Port 80 Application Database Server
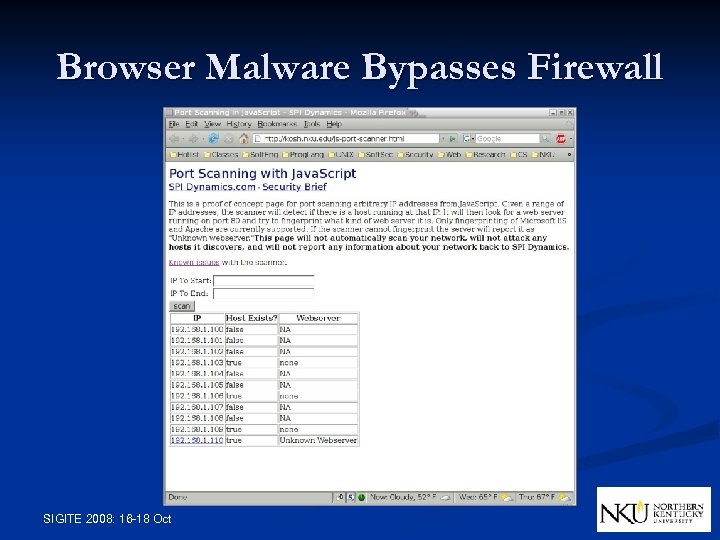
Browser Malware Bypasses Firewall SIGITE 2008: 16 -18 Oct

Goals 1. 2. 3. 4. 5. Identify and explain common vulnerabilities. Explain security implications of client-side technologies like Javascript and Active. X. Detect security vulnerabilities in web applications using appropriate tools. Design and implement web applications that do not contain common vulnerabilities. Deploy and configure a web application in a secure manner. SIGITE 2008: 16 -18 Oct

Topic Outline 1. 2. 3. 4. 5. 6. 7. 8. Web Application Input Client-side Technologies Input-based Attacks Injection Attacks Cross-site Attacks Authentication Secure Programming Operational Security SIGITE 2008: 16 -18 Oct
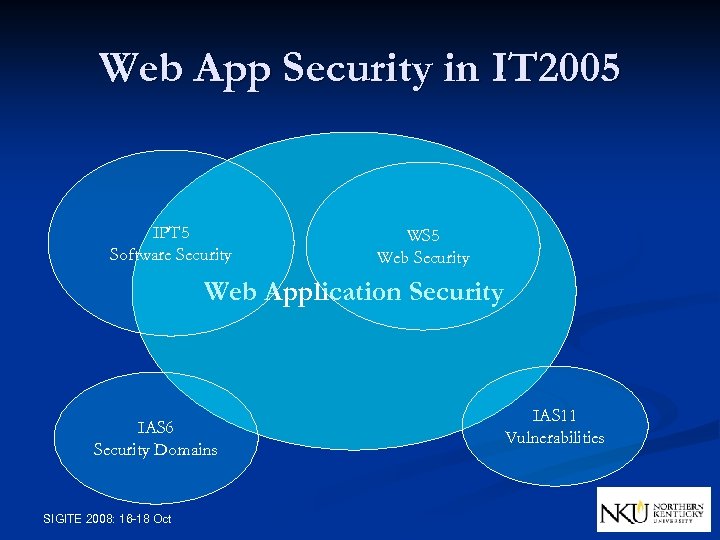
Web App Security in IT 2005 IPT 5 Software Security WS 5 Web Security Web Application Security IAS 6 Security Domains SIGITE 2008: 16 -18 Oct IAS 11 Vulnerabilities

Labs 1. 2. 3. 4. 5. 6. 7. Web. Goat exercises on specific vulnerabilities. Using a testing proxy to solve more advanced Web. Goat exercises. Assessing an application using a web vulnerability scanner. Assessing a web application using a testing proxy. Reviewing the code of an application using a static analysis tool. Deploying a web application firewall. Participating in the international CTF competition. SIGITE 2008: 16 -18 Oct
Web. Goat SIGITE 2008: 16 -18 Oct
Tools Web Proxies Web Application Firewalls Vulnerability Scanners Static Analysis SIGITE 2008: 16 -18 Oct
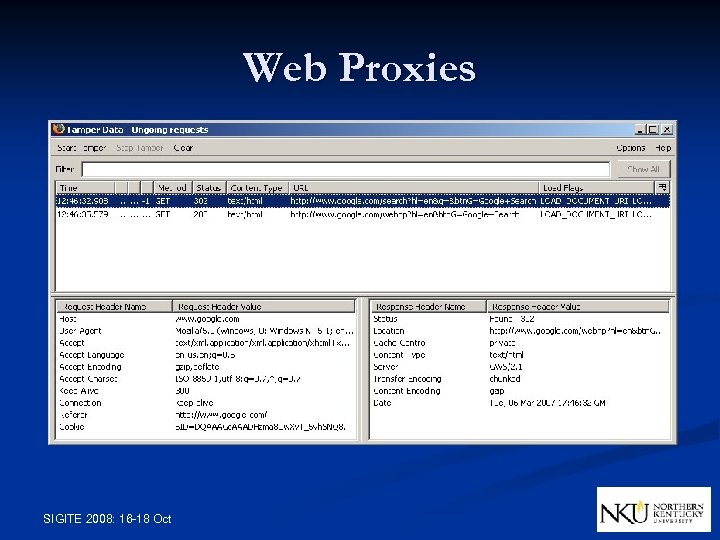
Web Proxies SIGITE 2008: 16 -18 Oct
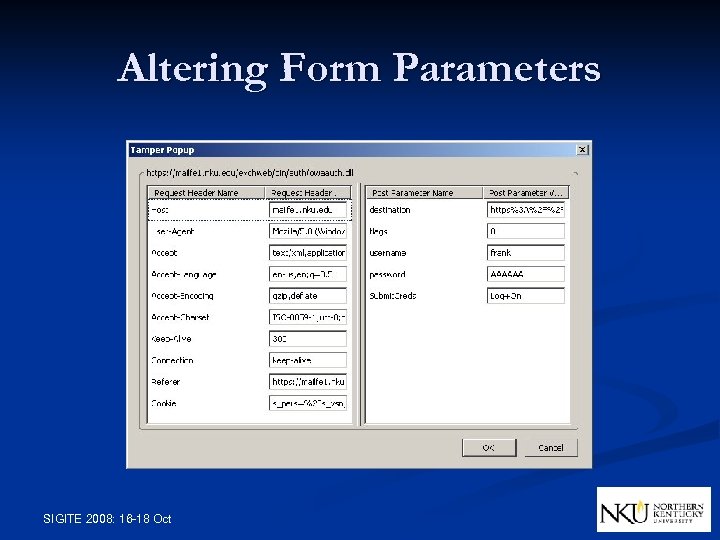
Altering Form Parameters SIGITE 2008: 16 -18 Oct
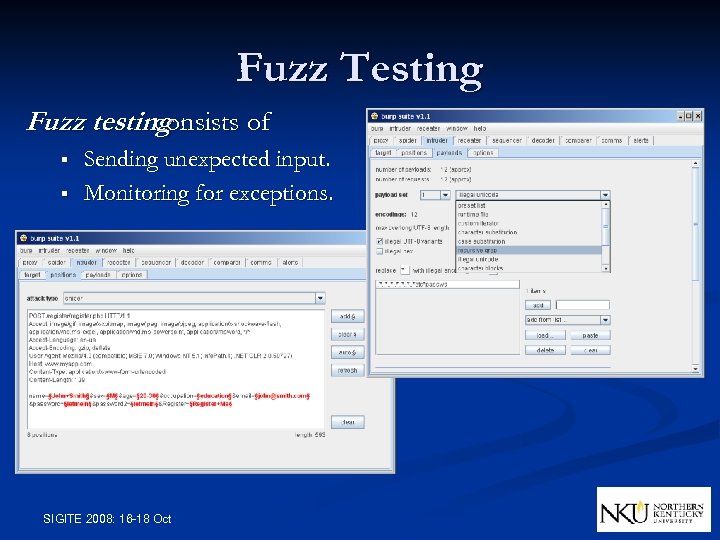
Fuzz Testing Fuzz testing consists of § § Sending unexpected input. Monitoring for exceptions. SIGITE 2008: 16 -18 Oct
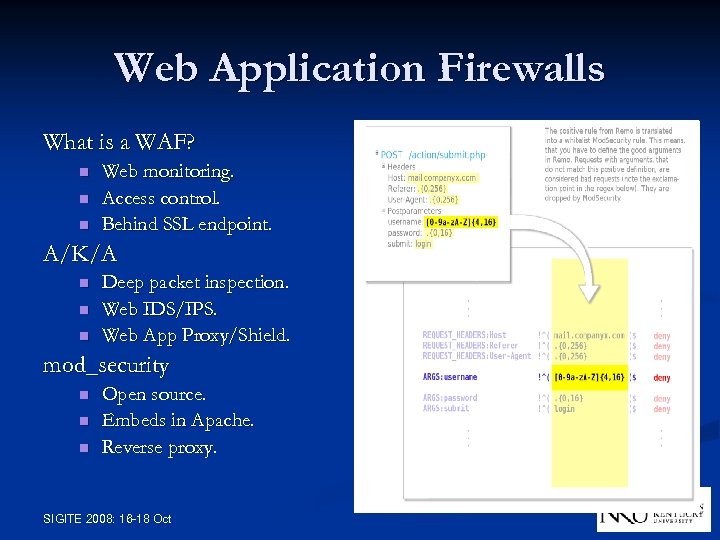
Web Application Firewalls What is a WAF? n n n Web monitoring. Access control. Behind SSL endpoint. A/K/A n n n Deep packet inspection. Web IDS/IPS. Web App Proxy/Shield. mod_security n n n Open source. Embeds in Apache. Reverse proxy. SIGITE 2008: 16 -18 Oct
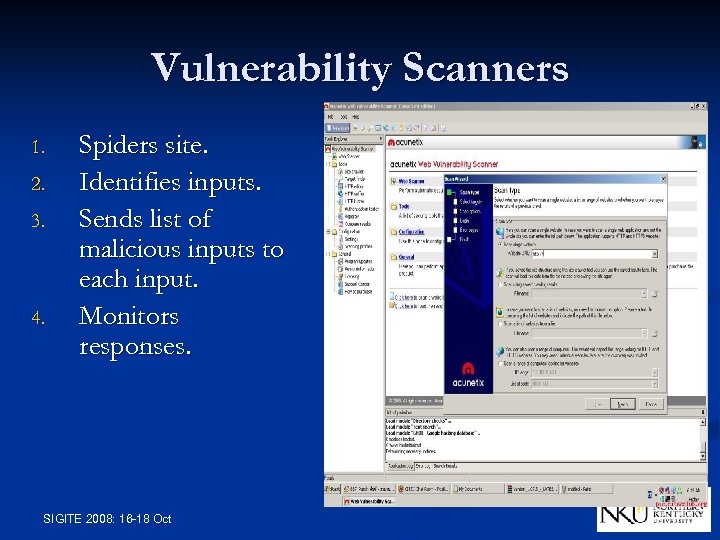
Vulnerability Scanners 1. 2. 3. 4. Spiders site. Identifies inputs. Sends list of malicious inputs to each input. Monitors responses. SIGITE 2008: 16 -18 Oct
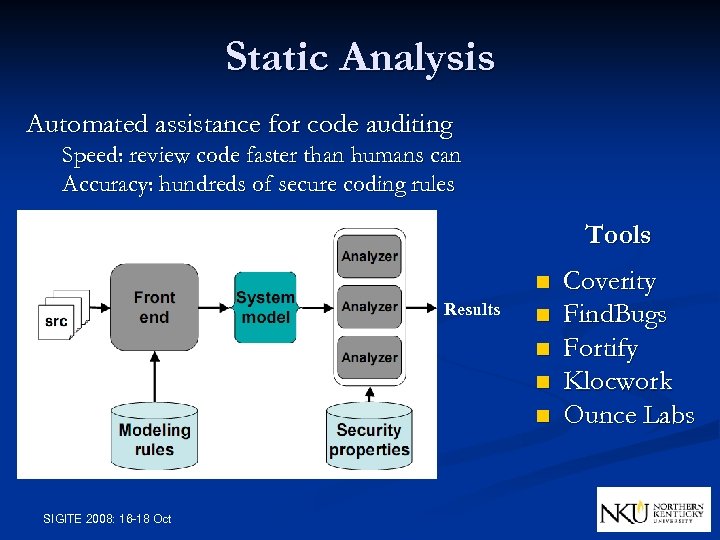
Static Analysis Automated assistance for code auditing Speed: review code faster than humans can Accuracy: hundreds of secure coding rules Tools n Results n n SIGITE 2008: 16 -18 Oct Coverity Find. Bugs Fortify Klocwork Ounce Labs

Labs 1. 2. 3. 4. 5. 6. 7. Web. Goat exercises on specific vulnerabilities. Using a testing proxy to solve more advanced Web. Goat exercises. Assessing an application using a web vulnerability scanner. Assessing a web application using a testing proxy. Reviewing the code of an application using a static analysis tool. Deploying a web application firewall. Participating in the international CTF competition. SIGITE 2008: 16 -18 Oct

Approaches 1. Students evaluate and fix their own code. 1. 2. Students evaluate and fix your code. 1. 3. Students learn about their own coding mistakes. Scale of project limited to what students can write. Write a web application designed for teaching students. Students evaluate and fix someone else’s code. 1. 2. Use a web application designed for teaching. Analyze an open source web application with known vulnerabilities reported in NVD or other bug db. SIGITE 2008: 16 -18 Oct
Teaching Applications SIGITE 2008: 16 -18 Oct Hacme Bank, Books, Casino, Travel
Future Directions: AJAX Security Asynchronous Javascript and XML § § Expanded server side API. Server API calls can be issued in any order by attacker; cannot assume calls issued in order by your client. Larger amount of client state. Client/server communication using data (XML/JSON) rather than presentation (HTML. ) SIGITE 2008: 16 -18 Oct

Future Directions: Web Sec Class 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. Web Application Input Client-side Technologies Service Oriented Architectures AJAX Input-based Attacks Injection Attacks Race Conditions Cross-site Attacks Authentication Secure Programming Operational Security SIGITE 2008: 16 -18 Oct

Conclusions 1. Defense is shifting from network to application layer. Firewalls, anti-virus, SSL 2. Students need to learn to identify vulnerabilities. 1. 2. 3. input validation, WAF Static analysis of source code. Web proxies and scanners for testing. Students need to learn to remediate vulnerabiliites. 1. 2. Web application firewalls for immediate short-term fixes. Repairing source code for long term fixes. SIGITE 2008: 16 -18 Oct
357fc5ca512f19b8282372cced2a79d1.ppt