4cf825a02a57bcf0cfa25111d486d168.ppt
- Количество слайдов: 22

Institute for Cyber Security Constraints Specification for Virtual Resource Orchestration in Cloud Iaa. S Khalid Bijon, Ram Krishnan and Ravi Sandhu University of Texas at San Antonio 5 th ACM Conference on Data and Applications Security and Privacy (CODASPY 2015) World-Leading Research with Real-World Impact! 1
Outline Introduction Motivation Goal Methodology Enforcement (in Cloud Iaa. S) Implementation (in Open. Stack) Conclusion World-Leading Research with Real-World Impact! 2
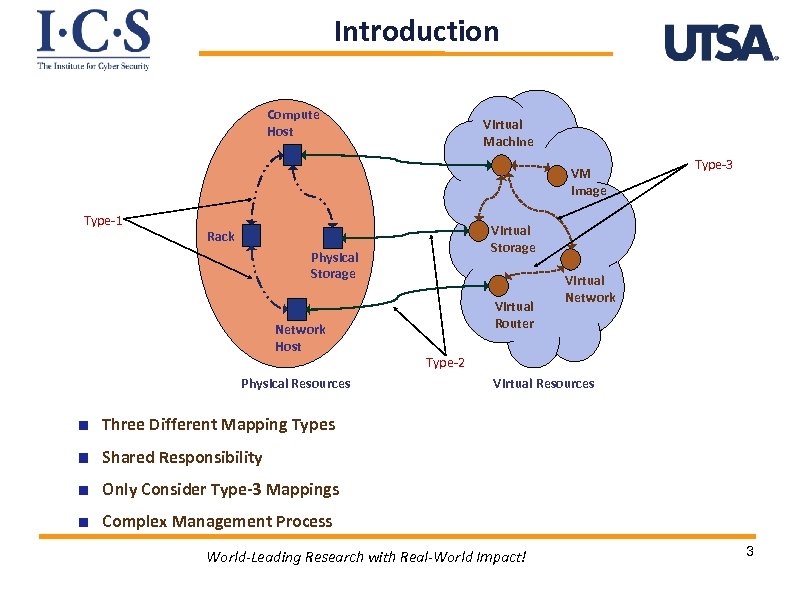
Introduction Compute Host Virtual Machine VM Image Type-1 Virtual Storage Rack Physical Storage Network Host Physical Resources Type-3 Virtual Router Virtual Network Type-2 Virtual Resources Three Different Mapping Types Shared Responsibility Only Consider Type-3 Mappings Complex Management Process World-Leading Research with Real-World Impact! 3
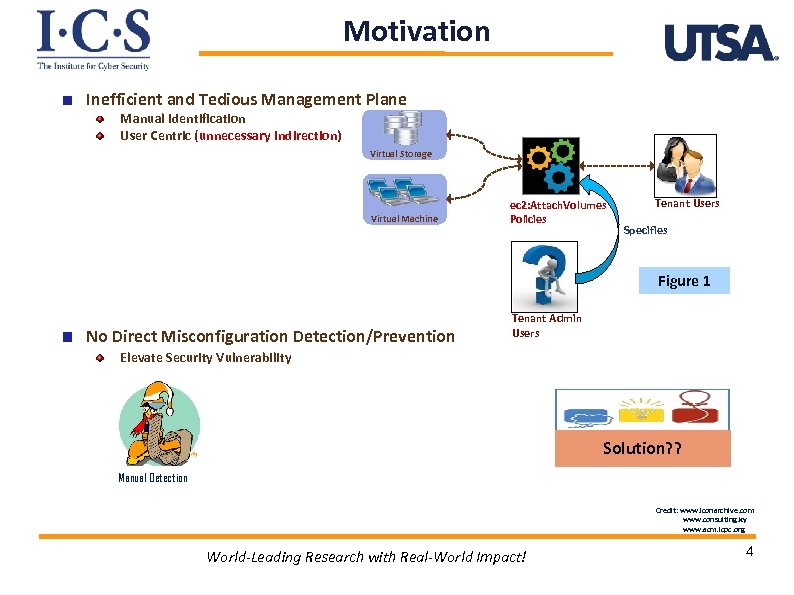
Motivation Inefficient and Tedious Management Plane Manual Identification User Centric (unnecessary indirection) Virtual Storage Virtual Machine ec 2: Attach. Volumes Policies Tenant Users Specifies Figure 1 No Direct Misconfiguration Detection/Prevention Tenant Admin Users Elevate Security Vulnerability Solution? ? Manual Detection Credit: www. iconarchive. com www. consulting. ky www. acm. icpc. org World-Leading Research with Real-World Impact! 4
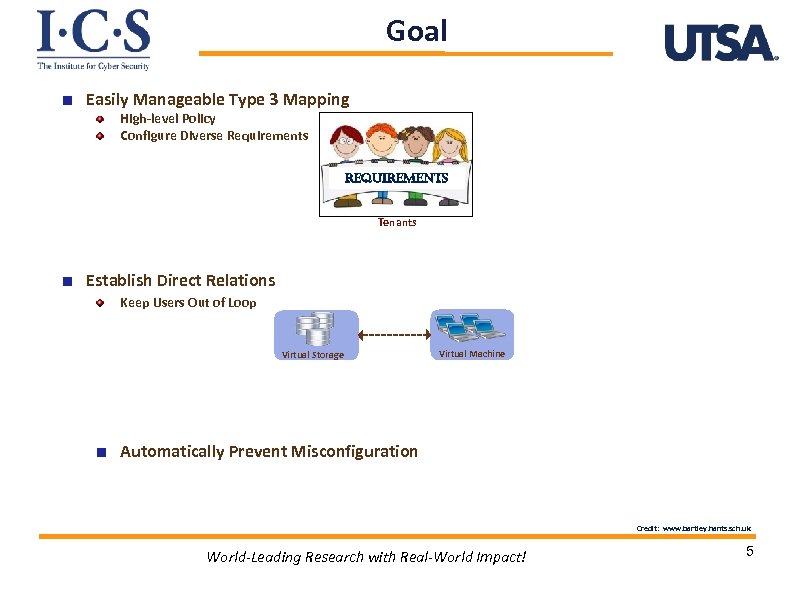
Goal Easily Manageable Type 3 Mapping High-level Policy Configure Diverse Requirements requirements Tenants Establish Direct Relations Keep Users Out of Loop Virtual Storage Virtual Machine Automatically Prevent Misconfiguration Credit: www. bartley. hants. sch. uk World-Leading Research with Real-World Impact! 5
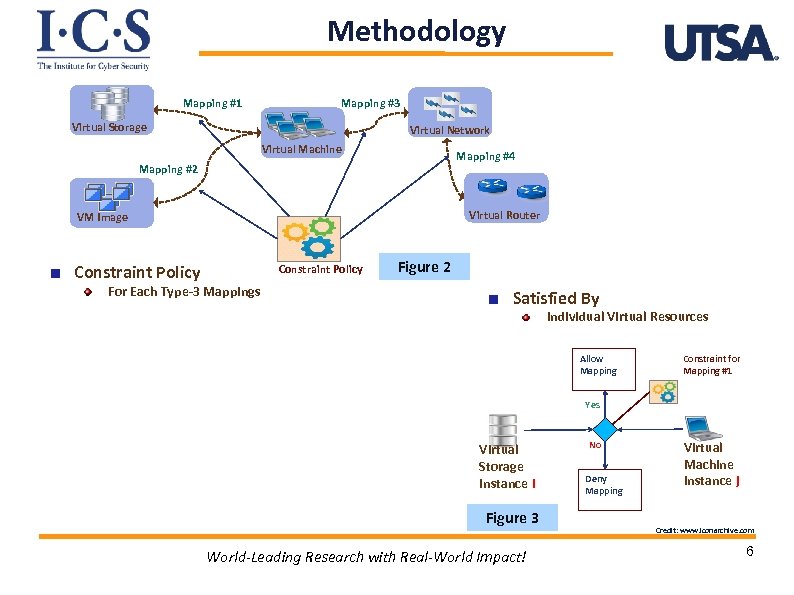
Methodology Mapping #1 Mapping #3 Virtual Storage Virtual Network Virtual Machine Mapping #4 Mapping #2 Virtual Router VM Image Constraint Policy For Each Type-3 Mappings Figure 2 Satisfied By Individual Virtual Resources Allow Mapping Constraint for Mapping #1 Yes Virtual Storage Instance i Figure 3 World-Leading Research with Real-World Impact! No Deny Mapping Virtual Machine Instance j Credit: www. iconarchive. com 6
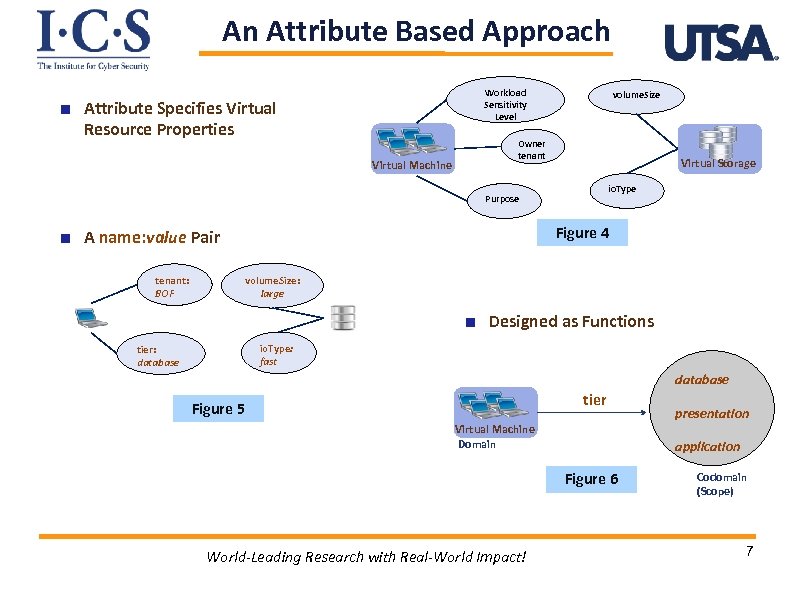
An Attribute Based Approach Workload Sensitivity Level Attribute Specifies Virtual Resource Properties Virtual Machine volume. Size Owner tenant Virtual Storage io. Type Purpose Figure 4 A name: value Pair volume. Size: large tenant: BOF Designed as Functions io. Type: fast tier: database tier Figure 5 Virtual Machine Domain application Figure 6 World-Leading Research with Real-World Impact! presentation Codomain (Scope) 7
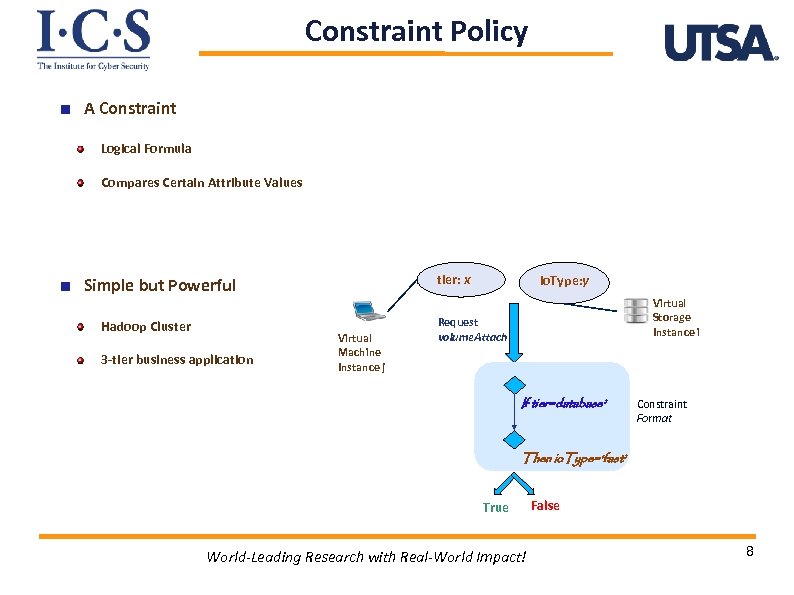
Constraint Policy A Constraint Logical Formula Compares Certain Attribute Values tier: x Simple but Powerful Hadoop Cluster 3 -tier business application Virtual Machine Instance j io. Type: y Virtual Storage Instance i Request volume. Attach If tier=database’ Constraint Format Then io. Type=‘fast’ True World-Leading Research with Real-World Impact! False 8
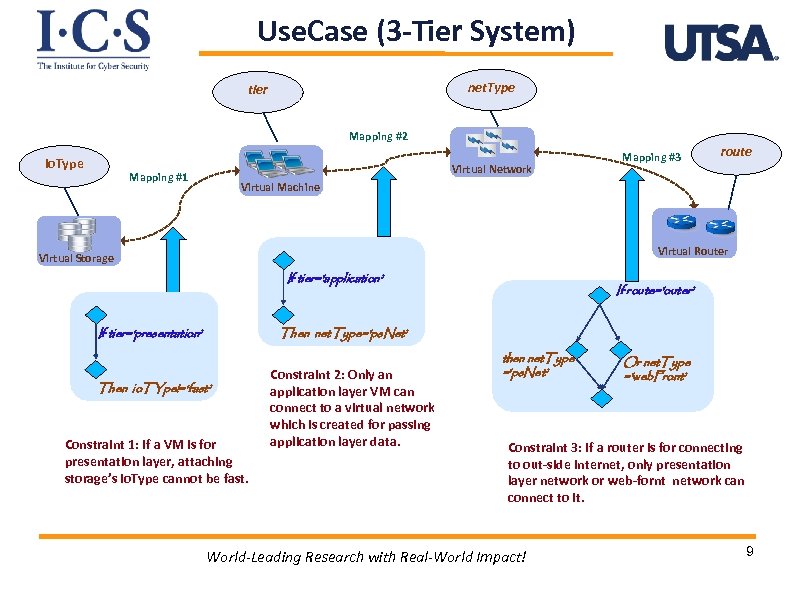
Use. Case (3 -Tier System) net. Type tier Mapping #2 io. Type Virtual Network Mapping #1 Mapping #3 route Virtual Machine Virtual Router Virtual Storage If tier=‘application’ If tier=‘presentation’ If route=‘outer’ Then net. Type=‘ps. Net’ Then io. TYpe!=‘fast’ Constraint 1: If a VM is for presentation layer, attaching storage’s io. Type cannot be fast. Constraint 2: Only an application layer VM can connect to a virtual network which is created for passing application layer data. then net. Type =‘ps. Net’ Or net. Type =‘web. Front’ Constraint 3: If a router is for connecting to out-side internet, only presentation layer network or web-fornt network can connect to it. World-Leading Research with Real-World Impact! 9
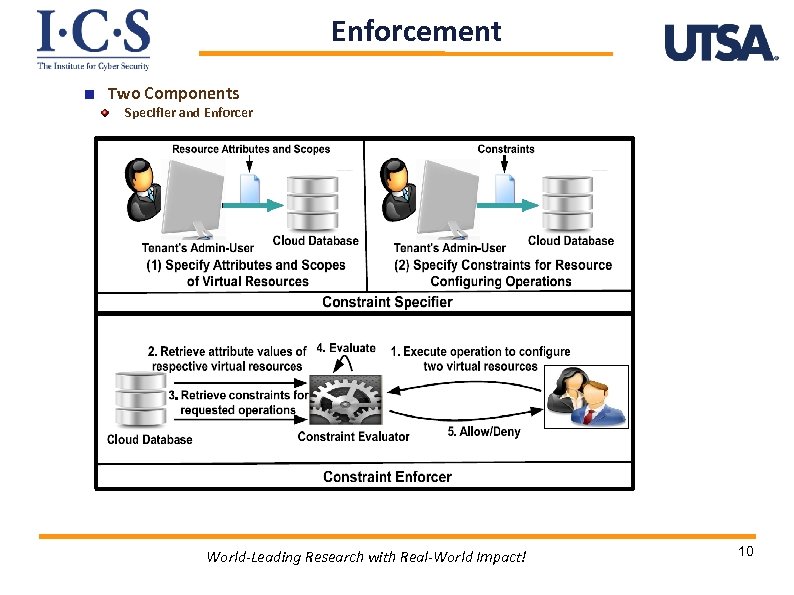
Enforcement Two Components Specifier and Enforcer World-Leading Research with Real-World Impact! 10
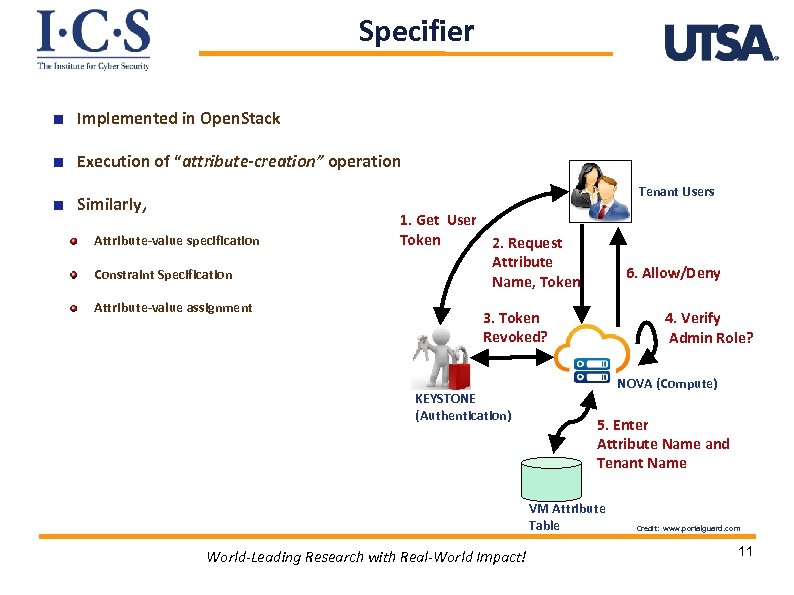
Specifier Implemented in Open. Stack Execution of “attribute-creation” operation Tenant Users Similarly, Attribute-value specification Constraint Specification Attribute-value assignment 1. Get User Token 2. Request Attribute Name, Token 6. Allow/Deny 3. Token Revoked? KEYSTONE (Authentication) 4. Verify Admin Role? NOVA (Compute) 5. Enter Attribute Name and Tenant Name VM Attribute Table World-Leading Research with Real-World Impact! Credit: www. portalguard. com 11
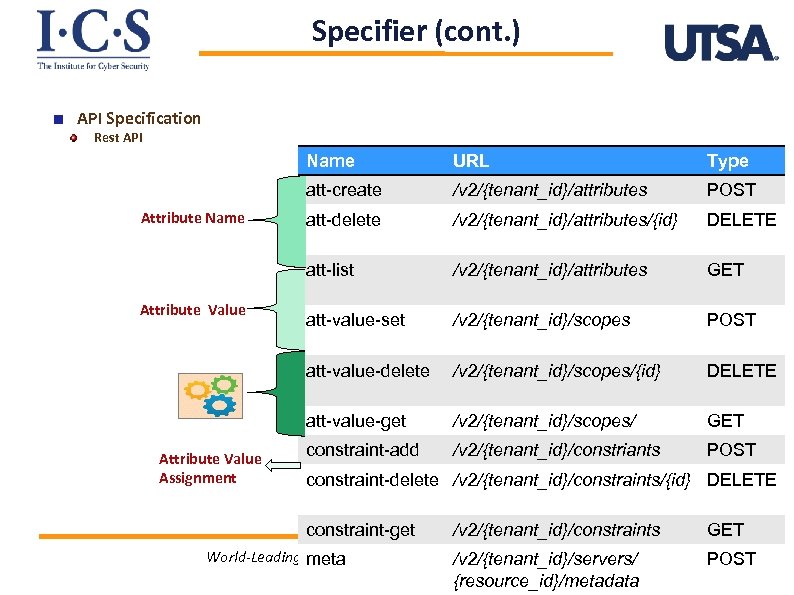
Specifier (cont. ) API Specification Rest API Name POST att-delete /v 2/{tenant_id}/attributes/{id} DELETE /v 2/{tenant_id}/attributes GET att-value-set /v 2/{tenant_id}/scopes POST att-value-delete /v 2/{tenant_id}/scopes/{id} DELETE att-value-get Attribute Value Assignment /v 2/{tenant_id}/attributes att-list Attribute Value Type att-create Attribute Name URL /v 2/{tenant_id}/scopes/ GET constraint-add /v 2/{tenant_id}/constriants POST constraint-delete /v 2/{tenant_id}/constraints/{id} DELETE constraint-get /v 2/{tenant_id}/constraints World-Leading Research with Real-World Impact! meta /v 2/{tenant_id}/servers/ {resource_id}/metadata GET 12 POST
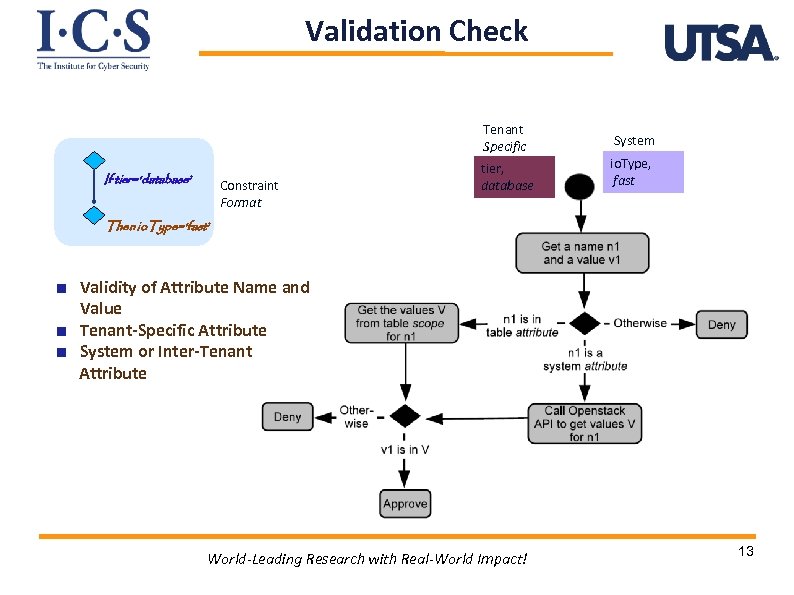
Validation Check Tenant Specific If tier=‘database’ Constraint Format tier, database System io. Type, fast Then io. Type=‘fast’ Validity of Attribute Name and Value Tenant-Specific Attribute System or Inter-Tenant Attribute World-Leading Research with Real-World Impact! 13
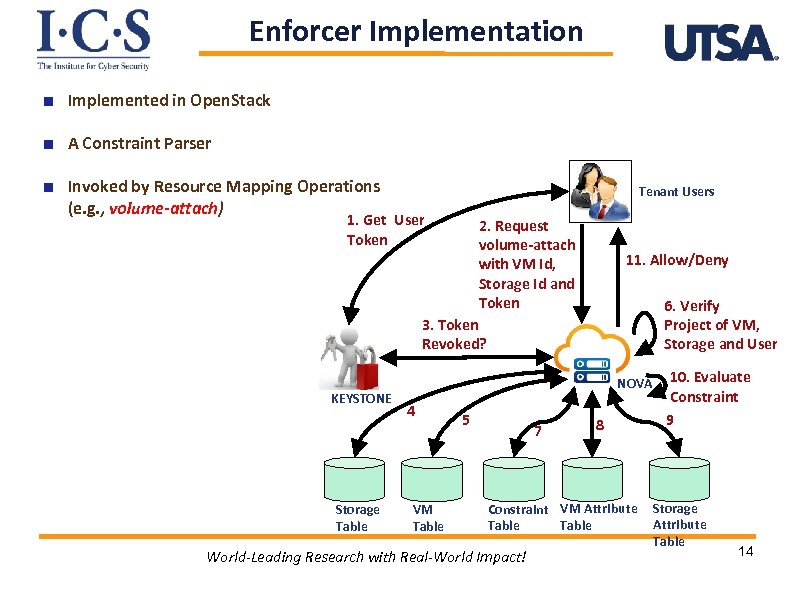
Enforcer Implementation Implemented in Open. Stack A Constraint Parser Invoked by Resource Mapping Operations (e. g. , volume-attach) Tenant Users 1. Get User Token 2. Request volume-attach with VM Id, Storage Id and Token 11. Allow/Deny 6. Verify Project of VM, Storage and User 3. Token Revoked? KEYSTONE Storage Table NOVA 4 VM Table 5 7 8 Constraint VM Attribute Table World-Leading Research with Real-World Impact! 10. Evaluate Constraint 9 Storage Attribute Table 14
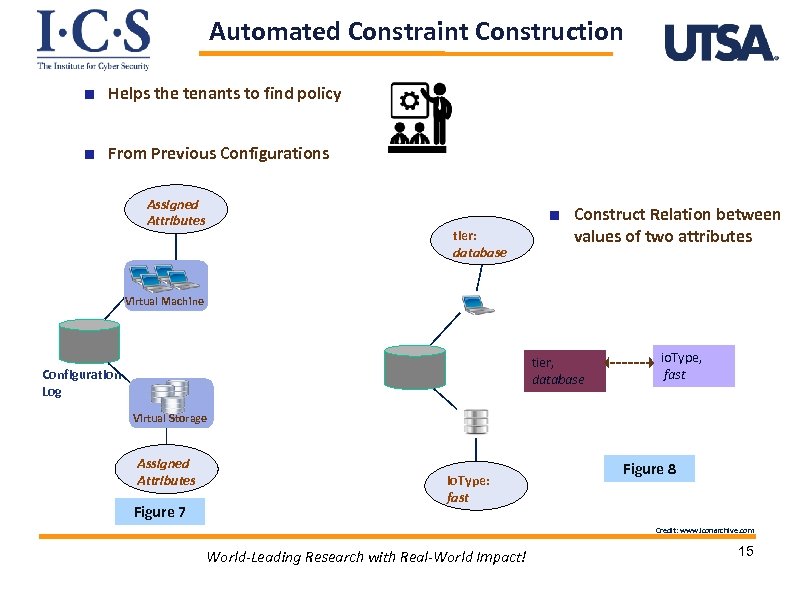
Automated Constraint Construction Helps the tenants to find policy From Previous Configurations Assigned Attributes tier: database Construct Relation between values of two attributes Virtual Machine tier, database Configuration Log io. Type, fast Virtual Storage Assigned Attributes Figure 7 io. Type: fast Figure 8 Credit: www. iconarchive. com World-Leading Research with Real-World Impact! 15
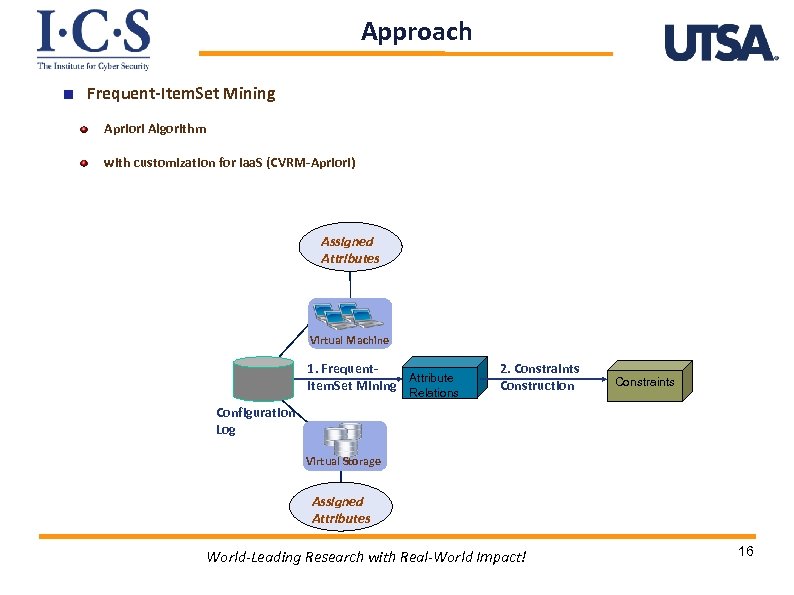
Approach Frequent-Item. Set Mining Apriori Algorithm with customization for Iaa. S (CVRM-Apriori) Assigned Attributes Virtual Machine 1. Frequent. Attribute Item. Set Mining Relations 2. Constraints Construction Constraints Configuration Log Virtual Storage Assigned Attributes World-Leading Research with Real-World Impact! 16
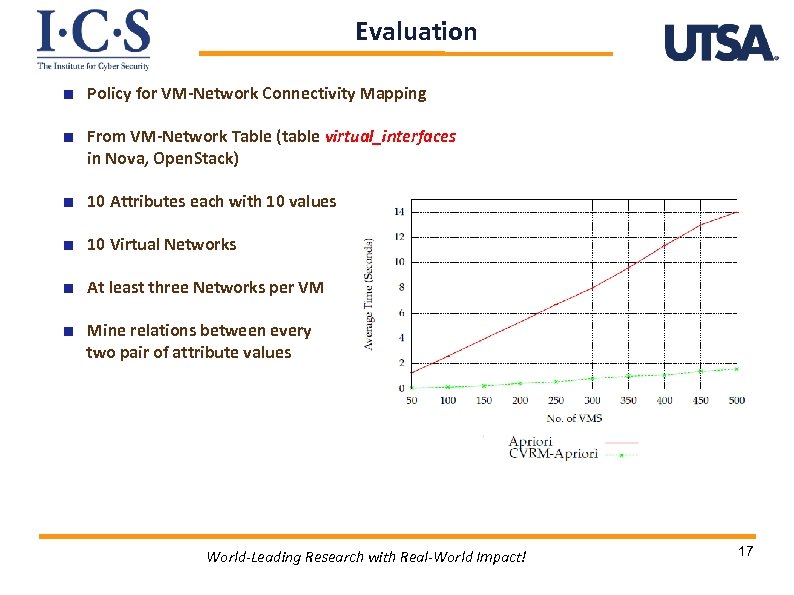
Evaluation Policy for VM-Network Connectivity Mapping From VM-Network Table (table virtual_interfaces in Nova, Open. Stack) 10 Attributes each with 10 values 10 Virtual Networks At least three Networks per VM Mine relations between every two pair of attribute values World-Leading Research with Real-World Impact! 17
Conclusion A Constraint Specification Framework Easily manageable and generic requirements Tenants Can be applied for Misconfiguration Prevention Future Work Also, for detection (flag-generator) Automatic Generation of Constraints Flag Generator System Semantic meaning of mined Attribute Relation Improve mining (incorporate noise) Credit: www. iconarchive. com World-Leading Research with Real-World Impact! 18
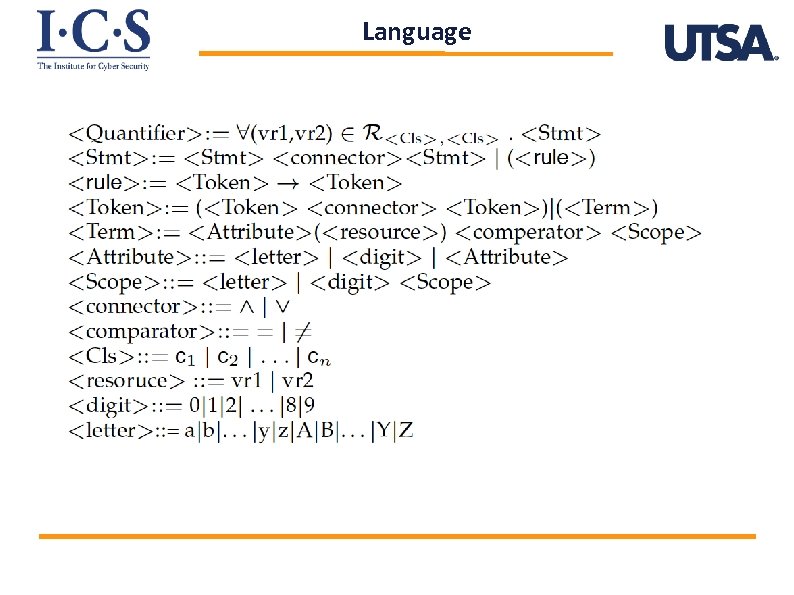
Language
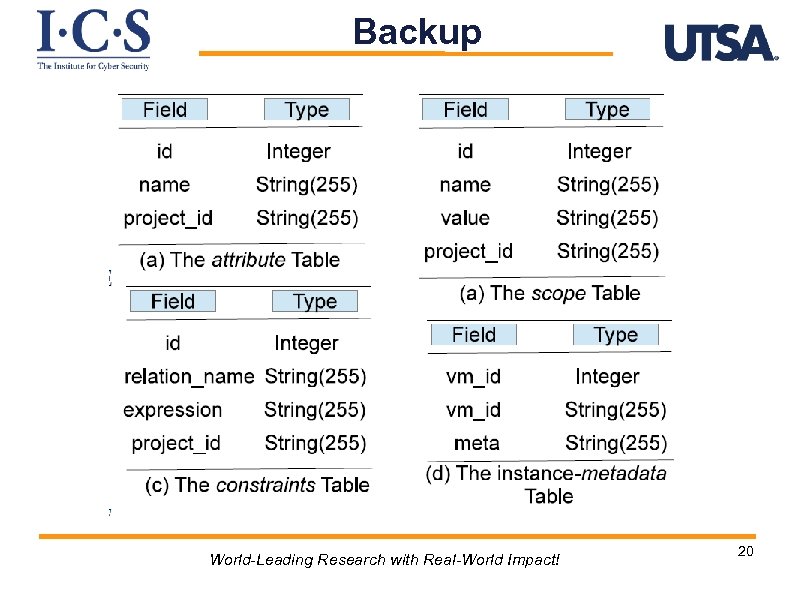
Backup World-Leading Research with Real-World Impact! 20
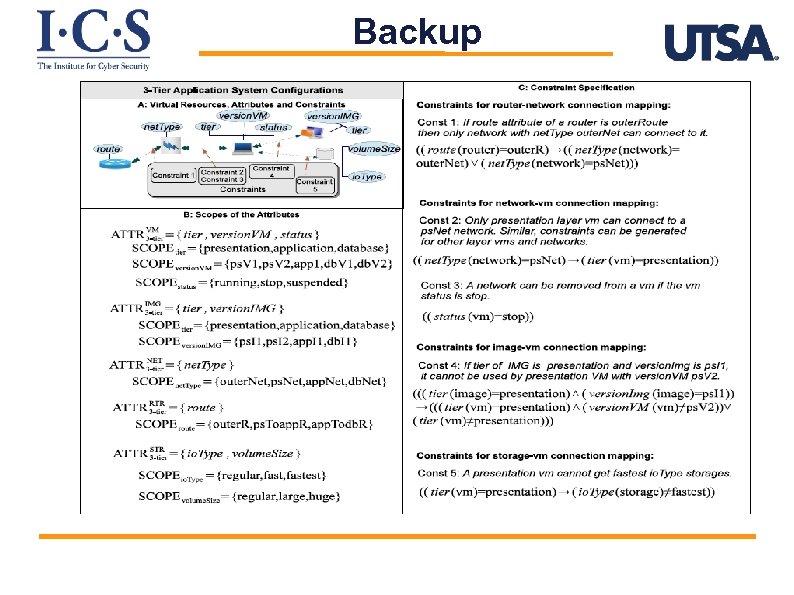
Backup
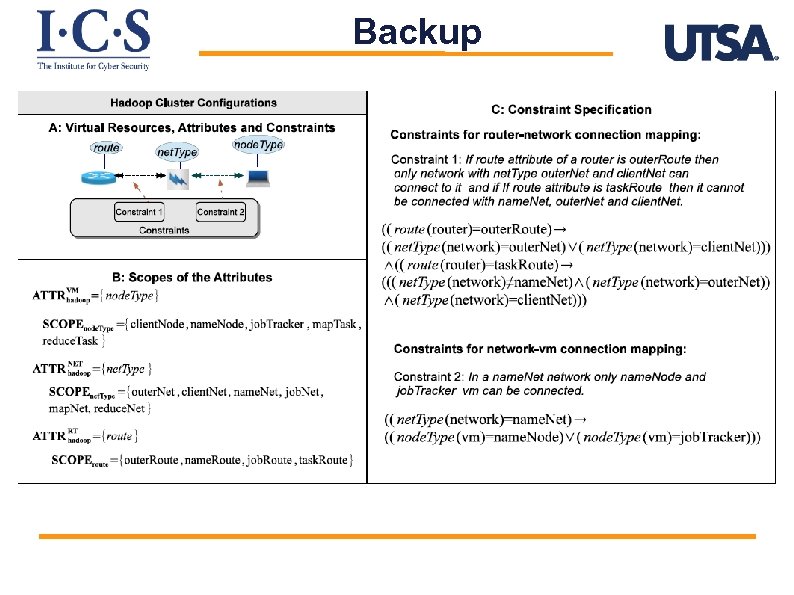
Backup
4cf825a02a57bcf0cfa25111d486d168.ppt