5ef025708effd2a17cd0803b41a89c0a.ppt
- Количество слайдов: 27

<Insert Picture Here> Identity Management Best Practices Katerina Kalimeri, Senior Sales Consultant Oracle Hellas

Agenda • IDM Defined • Business Drivers for Complete Security • Key Elements of Identity Management • Oracle Approach to Identity Management • Oracle Id. M @ Work • Summary

Agenda • IDM Defined • Business Drivers for Complete Security • Key Elements of Identity Management • Oracle Approach to Identity Management • Oracle Id. M @ Work • Summary

What is Identity Management? Securing your IT assets from within • Management of digital identities through their complete lifecycle • IDENTITY LIFE CYCLE: JOIN / MOVE / LEAVE • Employee hire -> promotion -> departure • Securing access to applications and information • Authentication: proving you are who you say you are • Authorization: what you have access to, when, where • Scalable and available storage of identity information • Profile: roles and attributes about you

Agenda • IDM Defined • Business Drivers for Complete Security • Key Elements of Identity Management • Oracle Approach to Identity Management • Oracle Id. M @ Work • Summary
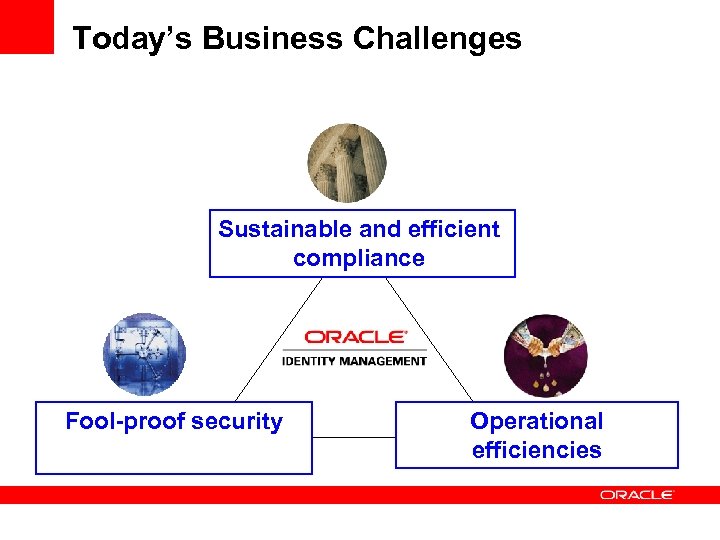
Today’s Business Challenges Sustainable and efficient compliance Fool-proof security Operational efficiencies
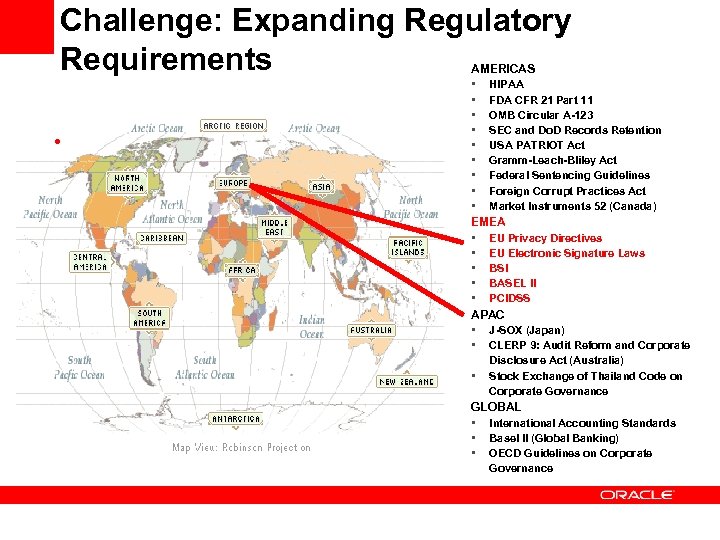
Challenge: Expanding Regulatory Requirements • AMERICAS • HIPAA • FDA CFR 21 Part 11 • OMB Circular A-123 • SEC and Do. D Records Retention • USA PATRIOT Act • Gramm-Leach-Bliley Act • Federal Sentencing Guidelines • Foreign Corrupt Practices Act • Market Instruments 52 (Canada) EMEA • EU Privacy Directives • EU Electronic Signature Laws • BSI • BASEL II • PCIDSS APAC • J-SOX (Japan) • CLERP 9: Audit Reform and Corporate • Disclosure Act (Australia) Stock Exchange of Thailand Code on Corporate Governance GLOBAL • International Accounting Standards • Basel II (Global Banking) • OECD Guidelines on Corporate Governance
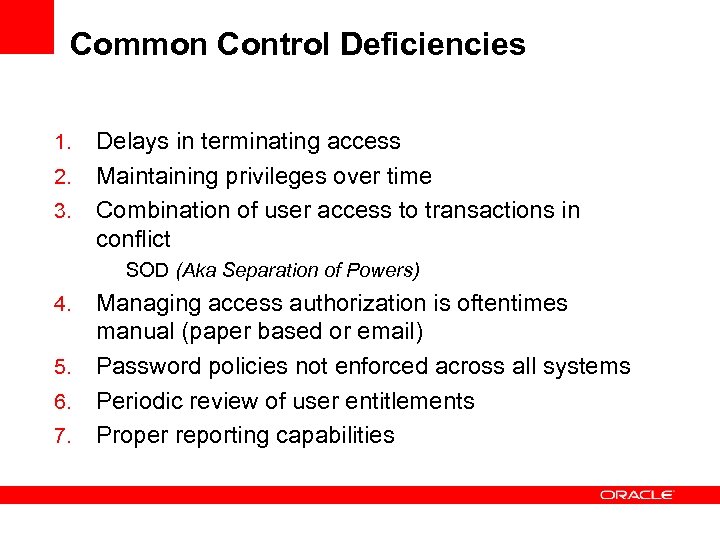
Common Control Deficiencies 1. 2. 3. Delays in terminating access Maintaining privileges over time Combination of user access to transactions in conflict SOD (Aka Separation of Powers) 4. 5. 6. 7. Managing access authorization is oftentimes manual (paper based or email) Password policies not enforced across all systems Periodic review of user entitlements Proper reporting capabilities
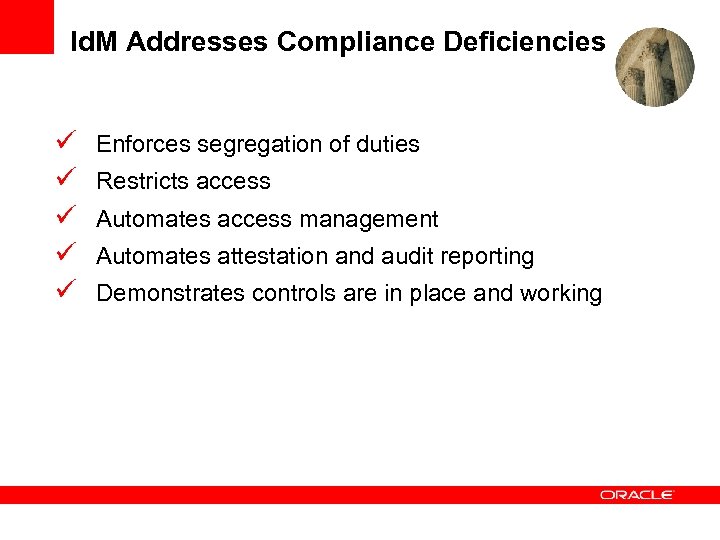
Id. M Addresses Compliance Deficiencies ü ü ü Enforces segregation of duties Restricts access Automates access management Automates attestation and audit reporting Demonstrates controls are in place and working

Challenge: Managing Security Risks • Majority of security breaches from within organization • Fragmented security policies • Orphaned accounts • Expired access rights • Lack of aggregated audit and accountability • Leaked passwords, social engineering • Manual provisioning requests prone to errors • Network administrators unaware of organizational and role changes

Id. M Strengthens Security üCentralized security and policy management • Consistent policies enforced across enterprise • Enterprise wide visibility of users, access rights, audit data üAutomated provisioning / de-provisioning • Role based user provisioning and de-provisioning • Automated updates triggered by user status change üSingle Sign-On, Delegated Administration • Reduce password compromises • Delegate policy administration to business owners

Challenge: Operational Efficiencies • Administrative costs • • Administering access for tens of thousands of users Overwhelming volume of help desk calls Manual provisioning of accounts for new hires Manual aggregation and cross checking of audit data • User Productivity • Long wait times acquiring access to requested systems • Forgotten passwords • No single password in use • IT Productivity • Developers reinventing security for each app they build
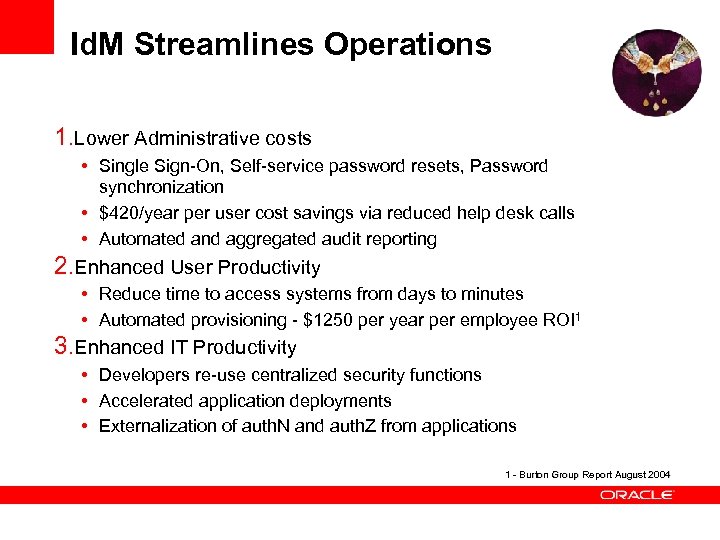
Id. M Streamlines Operations 1. Lower Administrative costs • Single Sign-On, Self-service password resets, Password synchronization • $420/year per user cost savings via reduced help desk calls • Automated and aggregated audit reporting 2. Enhanced User Productivity • Reduce time to access systems from days to minutes • Automated provisioning - $1250 per year per employee ROI 1 3. Enhanced IT Productivity • Developers re-use centralized security functions • Accelerated application deployments • Externalization of auth. N and auth. Z from applications 1 - Burton Group Report August 2004

Agenda • IDM Defined • Business Drivers for Complete Security • Key Elements of Identity Management • Oracle Approach to Identity Management • Oracle Id. M @ Work • Summary
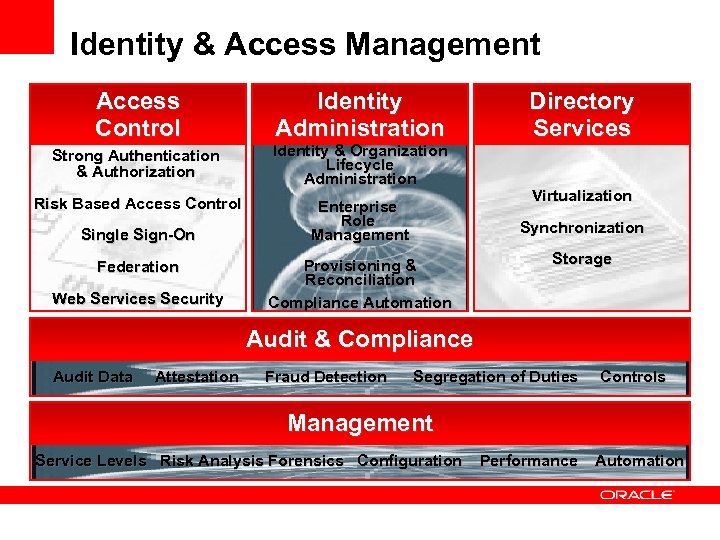
Identity & Access Management Access Control Identity Administration Strong Authentication & Authorization Identity & Organization Lifecycle Administration Risk Based Access Control Enterprise Role Management Single Sign-On Federation Web Services Security Directory Services Virtualization Synchronization Provisioning & Reconciliation Compliance Automation Storage Audit & Compliance Audit Data Attestation Fraud Detection Segregation of Duties Controls Management Service Levels Risk Analysis Forensics Configuration Performance Automation

Agenda • IDM Defined • Business Drivers for Complete Security • Key Elements of Identity Management • Oracle Approach to Identity Management • Oracle Id. M @ Work • Summary

30 Years of Security Leadership Bridgestream (Fall 2007 Id. M Acquisitions) Audit Vault (Spring 2007) Database Vault Content DB, Records DB Secure Enterprise Search Thor & Octet String (Id. M Acquisitions) Oracle Strategy: Acquisitions Phaos, Oblix, (Id. M Acquisitions) & Organic Growth Database CC Security Eval #18 (10 g R 1) Transparent Data Encryption VPD Column Sec Policies Fine Grained Auditing (9 i) st Database Common Criteria (EAL 4) 1 Oracle Label Security (2000 8. 1. 7) Virtual Private Database (1998) Enterprise User Security (8 i) Database Encryption API Kerberos Support (8 i) Support for PKI Radius Authentication Network Encryption (Oracle 7) Oracle Advanced Security introduced First Orange Book B 1 evaluation (1993) Trusted Oracle 7 MLS DB Government customer (CIA – Project Oracle) 1977 2007
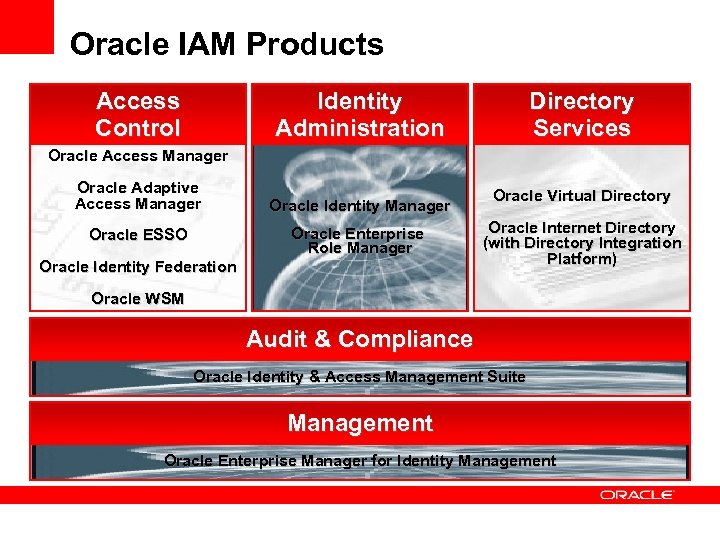
Oracle IAM Products Access Control Identity Administration Directory Services Oracle Access Manager Oracle Adaptive Access Manager Oracle Identity Manager Oracle Enterprise Role Manager Oracle ESSO Oracle Identity Federation Oracle Virtual Directory Oracle Internet Directory (with Directory Integration Platform) Oracle WSM Audit & Compliance Oracle Identity & Access Management Suite Management Oracle Enterprise Manager for Identity Management
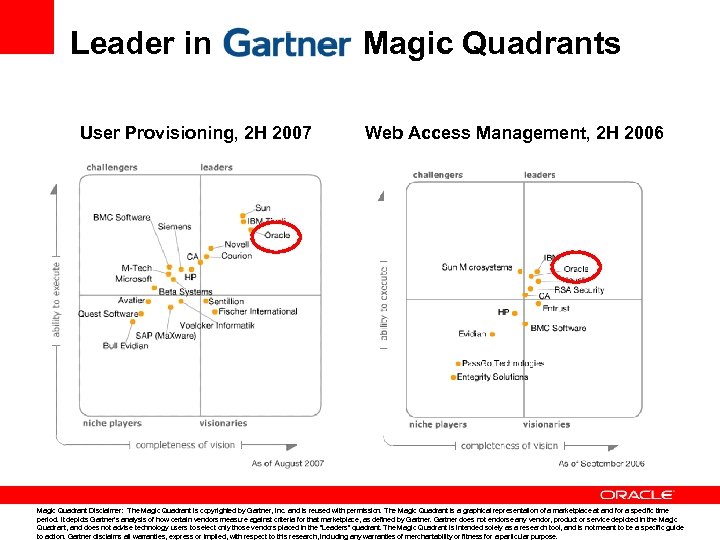
Leader in User Provisioning, 2 H 2007 Magic Quadrants Web Access Management, 2 H 2006 Magic Quadrant Disclaimer: The Magic Quadrant is copyrighted by Gartner, Inc. and is reused with permission. The Magic Quadrant is a graphical representation of a marketplace at and for a specific time period. It depicts Gartner's analysis of how certain vendors measure against criteria for that marketplace, as defined by Gartner does not endorse any vendor, product or service depicted in the Magic Quadrant, and does not advise technology users to select only those vendors placed in the "Leaders" quadrant. The Magic Quadrant is intended solely as a research tool, and is not meant to be a specific guide to action. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.

Agenda • IDM Defined • Business Drivers for Complete Security • Key Elements of Identity Management • Oracle Approach to Identity Management • Oracle Id. M @ Work • Summary
Case Study – Royal Bank of Scotland (RBS) BUSINESS CHALLENGE • Looking to automate provisioning & role management mapping Business Roles to IT Roles • Adding job-driven, position driven, team driven, and scoped roles to the role model • Meet compliance requirements and mitigate risk ORACLE SOLUTION • Oracle Identity Manager and Oracle Enterprise Role Manager chosen on May 2006 • 140, 000 Internal Users, plus 10 connectors • POC performance and reference meetings were key differentiators RESULTS • Expect to meet compliance and audit requirements – both regulatory and internal. • Dramatic improvement in accuracy via automation and workflow • Lower cost and improve security by enabling business units to manage role grants without compromising security policy
Case Study - Pfizer BUSINESS CHALLENGE • Wanted a portal which allows end users to determine what form of credential they would like to use to authenticate • Needed ability to enforce stronger authentication based on sensitivity of data being accessed • Needed a centralized security service • Needed zero downtime ORACLE SOLUTION • Oracle Access Manager and Oracle Virtual Directory are key components of Pfizer’s Identity and Access Management Infrastructure RESULTS • Built a security platform that allows new users to access the Pfizer applications based on their existing authentication factors – lowers cost of doing business with Pfizer. • SSO allows end users to have a stronger, unique authentication method to all applications – increases security by doing away with sticky-note syndrome.
Case Study – BAMF BUSINESS CHALLENGE ORACLE SOLUTION • Have a complex IT environment consisting of multiple data stores • Oracle Access Manager and Identity Manager for 10, 000 external & 2, 000 internal users • Need of Delegated administration and group management for their applications • Identity Manager allows for delegated management of identities, Password sync (e. g. with MS AD) • Need of Password Sync from Active Directory to several OID data stores • Governance compliance RESULTS • Reduced Administration costs and improved user experience around password management • Efficient Account creation and cancellation • Password sync between OID, AD (leading directory) and Oracle database • Web Single Sign-On with Application Express Apps and J 2 EE Apps

Agenda • IDM Defined • Business Drivers for Complete Security • Key Elements of Identity Management • Oracle Approach to Identity Management • Oracle Id. M @ Work • Summary
IDM the Oracle way… • “Holistic” approach with Oracle IAM Suite • Staged model for fast results • Externalized to be used across systems and applications • Value adding strategic partners • Evolve to remain ahead of pace • Support for life

Q & A

5ef025708effd2a17cd0803b41a89c0a.ppt