20670c057c39ba1e628b263c8adfc140.ppt
- Количество слайдов: 47


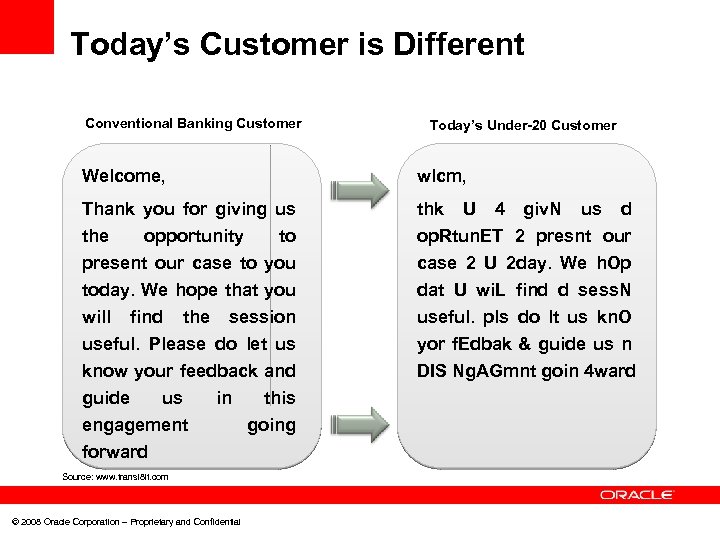 Today’s Customer is Different Conventional Banking Customer Today’s Under-20 Customer Welcome, wlcm, Thank you for giving us thk the opportunity to present our case to you op. Rtun. ET 2 presnt our case 2 U 2 day. We h. Op dat U wi. L find d sess. N useful. pls do lt us kn. O yor f. Edbak & guide us n DIS Ng. AGmnt goin 4 ward today. We hope that you will find the session useful. Please do let us know your feedback and guide us in this engagement forward Source: www. transl 8 it. com © 2008 Oracle Corporation – Proprietary and Confidential going U 4 giv. N us d
Today’s Customer is Different Conventional Banking Customer Today’s Under-20 Customer Welcome, wlcm, Thank you for giving us thk the opportunity to present our case to you op. Rtun. ET 2 presnt our case 2 U 2 day. We h. Op dat U wi. L find d sess. N useful. pls do lt us kn. O yor f. Edbak & guide us n DIS Ng. AGmnt goin 4 ward today. We hope that you will find the session useful. Please do let us know your feedback and guide us in this engagement forward Source: www. transl 8 it. com © 2008 Oracle Corporation – Proprietary and Confidential going U 4 giv. N us d
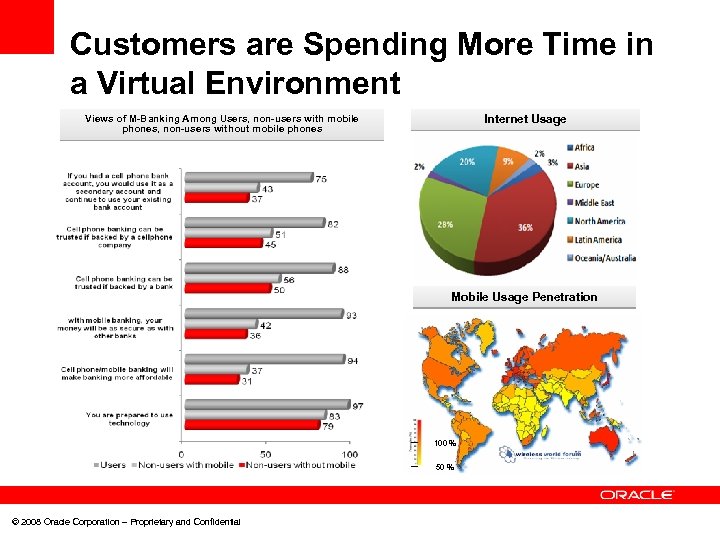 Customers are Spending More Time in a Virtual Environment Internet Usage Views of M-Banking Among Users, non-users with mobile phones, non-users without mobile phones Mobile Usage Penetration 100 % 50 % © 2008 Oracle Corporation – Proprietary and Confidential
Customers are Spending More Time in a Virtual Environment Internet Usage Views of M-Banking Among Users, non-users with mobile phones, non-users without mobile phones Mobile Usage Penetration 100 % 50 % © 2008 Oracle Corporation – Proprietary and Confidential
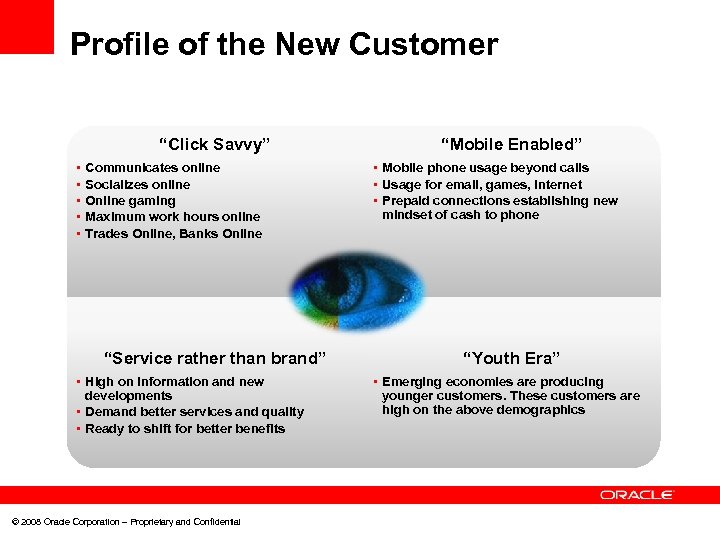 Profile of the New Customer “Click Savvy” • • • Communicates online Socializes online Online gaming Maximum work hours online Trades Online, Banks Online “Service rather than brand” • High on information and new developments • Demand better services and quality • Ready to shift for better benefits © 2008 Oracle Corporation – Proprietary and Confidential “Mobile Enabled” • Mobile phone usage beyond calls • Usage for email, games, internet • Prepaid connections establishing new mindset of cash to phone “Youth Era” • Emerging economies are producing younger customers. These customers are high on the above demographics
Profile of the New Customer “Click Savvy” • • • Communicates online Socializes online Online gaming Maximum work hours online Trades Online, Banks Online “Service rather than brand” • High on information and new developments • Demand better services and quality • Ready to shift for better benefits © 2008 Oracle Corporation – Proprietary and Confidential “Mobile Enabled” • Mobile phone usage beyond calls • Usage for email, games, internet • Prepaid connections establishing new mindset of cash to phone “Youth Era” • Emerging economies are producing younger customers. These customers are high on the above demographics
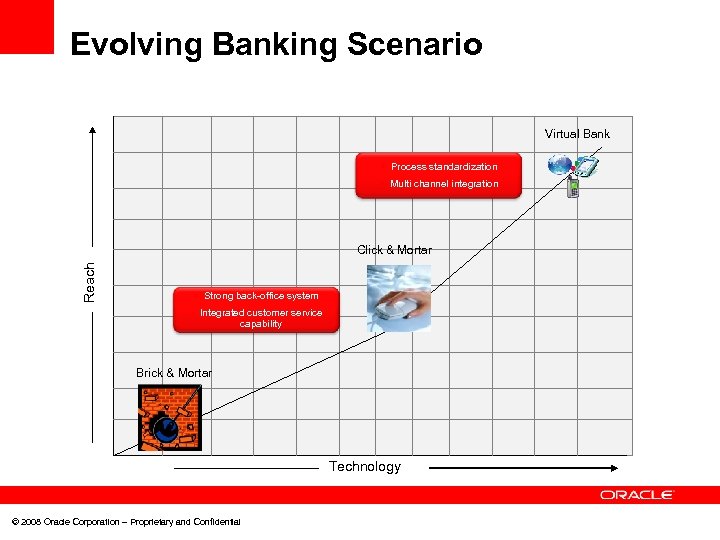 Evolving Banking Scenario Virtual Bank • Process standardization • Multi channel integration Reach Click & Mortar • Strong back-office system • Integrated customer service capability Brick & Mortar Technology © 2008 Oracle Corporation – Proprietary and Confidential
Evolving Banking Scenario Virtual Bank • Process standardization • Multi channel integration Reach Click & Mortar • Strong back-office system • Integrated customer service capability Brick & Mortar Technology © 2008 Oracle Corporation – Proprietary and Confidential
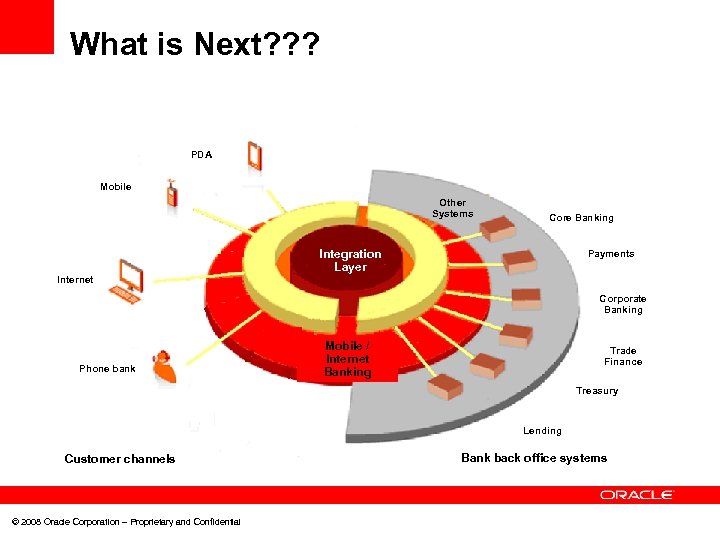 What is Next? ? ? PDA Mobile Other Systems Core Banking Integration Layer Payments Internet Corporate Banking Phone bank Mobile / Internet Banking Trade Finance Treasury Lending Customer channels © 2008 Oracle Corporation – Proprietary and Confidential Bank back office systems
What is Next? ? ? PDA Mobile Other Systems Core Banking Integration Layer Payments Internet Corporate Banking Phone bank Mobile / Internet Banking Trade Finance Treasury Lending Customer channels © 2008 Oracle Corporation – Proprietary and Confidential Bank back office systems
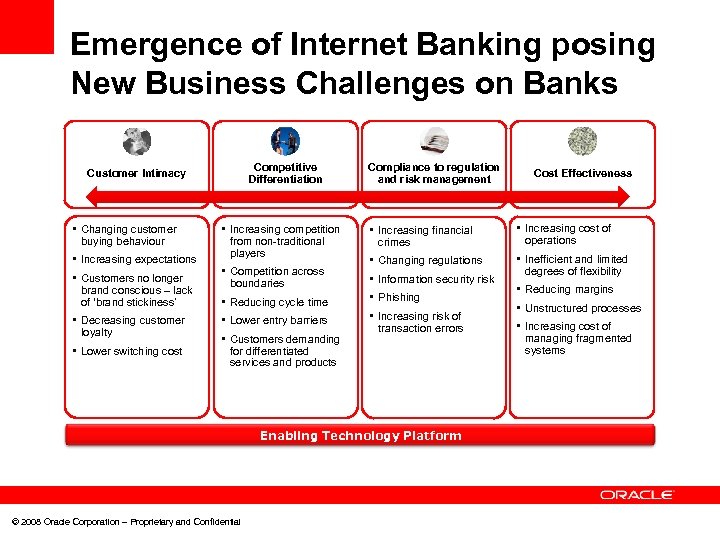 Emergence of Internet Banking posing New Business Challenges on Banks Competitive Differentiation Customer Intimacy • Changing customer • Increasing competition • Increasing expectations • Customers no longer • Competition across • Decreasing customer • Reducing cycle time • Lower entry barriers • Customers demanding buying behaviour brand conscious – lack of ‘brand stickiness’ loyalty • Lower switching cost from non-traditional players boundaries Compliance to regulation and risk management • Increasing financial • Increasing cost of • • • Inefficient and limited crimes Changing regulations Information security risk Phishing Increasing risk of transaction errors for differentiated services and products Enabling Technology Platform © 2008 Oracle Corporation – Proprietary and Confidential Cost Effectiveness operations degrees of flexibility • Reducing margins • Unstructured processes • Increasing cost of managing fragmented systems
Emergence of Internet Banking posing New Business Challenges on Banks Competitive Differentiation Customer Intimacy • Changing customer • Increasing competition • Increasing expectations • Customers no longer • Competition across • Decreasing customer • Reducing cycle time • Lower entry barriers • Customers demanding buying behaviour brand conscious – lack of ‘brand stickiness’ loyalty • Lower switching cost from non-traditional players boundaries Compliance to regulation and risk management • Increasing financial • Increasing cost of • • • Inefficient and limited crimes Changing regulations Information security risk Phishing Increasing risk of transaction errors for differentiated services and products Enabling Technology Platform © 2008 Oracle Corporation – Proprietary and Confidential Cost Effectiveness operations degrees of flexibility • Reducing margins • Unstructured processes • Increasing cost of managing fragmented systems
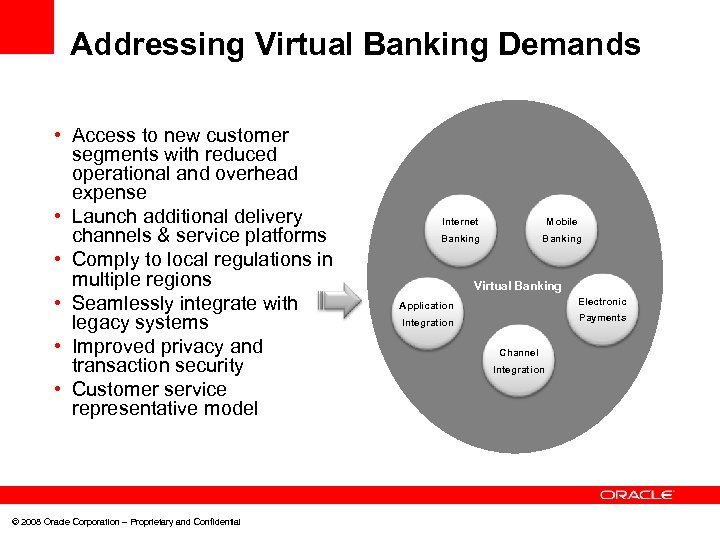 Addressing Virtual Banking Demands • Access to new customer segments with reduced operational and overhead expense • Launch additional delivery channels & service platforms • Comply to local regulations in multiple regions • Seamlessly integrate with legacy systems • Improved privacy and transaction security • Customer service representative model © 2008 Oracle Corporation – Proprietary and Confidential Internet Mobile Banking Virtual Banking Application Electronic Integration Payments Channel Integration
Addressing Virtual Banking Demands • Access to new customer segments with reduced operational and overhead expense • Launch additional delivery channels & service platforms • Comply to local regulations in multiple regions • Seamlessly integrate with legacy systems • Improved privacy and transaction security • Customer service representative model © 2008 Oracle Corporation – Proprietary and Confidential Internet Mobile Banking Virtual Banking Application Electronic Integration Payments Channel Integration
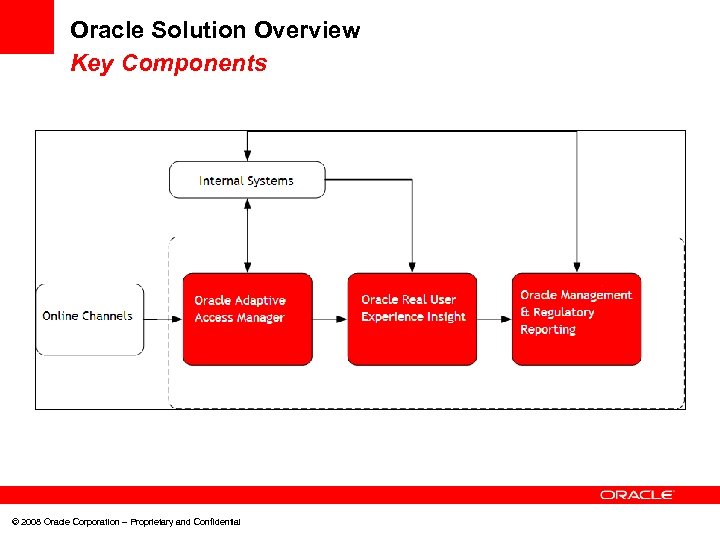 Oracle Solution Overview Key Components © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Solution Overview Key Components © 2008 Oracle Corporation – Proprietary and Confidential
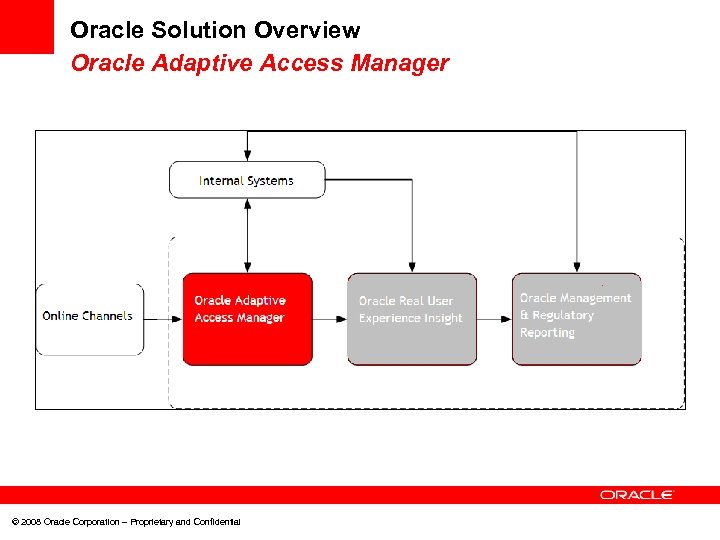 Oracle Solution Overview Oracle Adaptive Access Manager © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Solution Overview Oracle Adaptive Access Manager © 2008 Oracle Corporation – Proprietary and Confidential
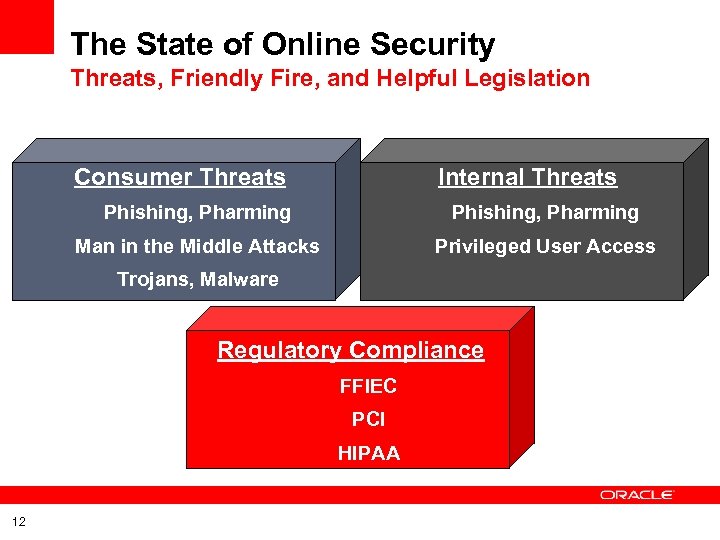 The State of Online Security Threats, Friendly Fire, and Helpful Legislation Consumer Threats Internal Threats Phishing, Pharming Man in the Middle Attacks Privileged User Access Trojans, Malware Regulatory Compliance FFIEC PCI HIPAA 12
The State of Online Security Threats, Friendly Fire, and Helpful Legislation Consumer Threats Internal Threats Phishing, Pharming Man in the Middle Attacks Privileged User Access Trojans, Malware Regulatory Compliance FFIEC PCI HIPAA 12
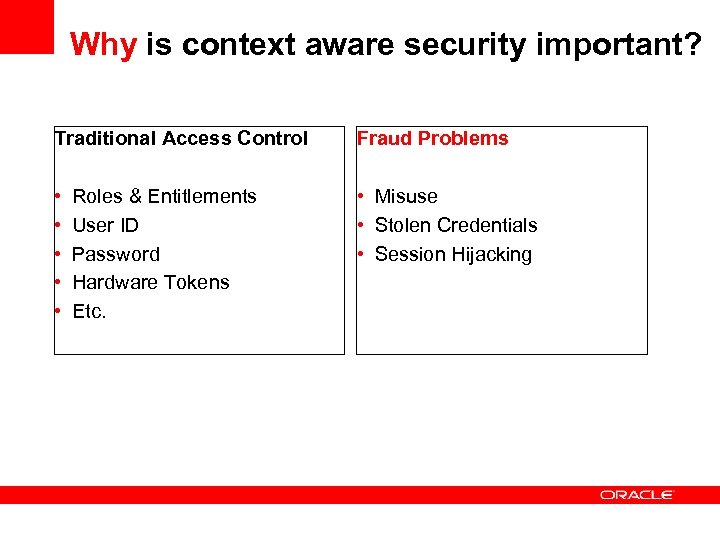 Why is context aware security important? Traditional Access Control Fraud Problems • • • Misuse • Stolen Credentials • Session Hijacking Roles & Entitlements User ID Password Hardware Tokens Etc.
Why is context aware security important? Traditional Access Control Fraud Problems • • • Misuse • Stolen Credentials • Session Hijacking Roles & Entitlements User ID Password Hardware Tokens Etc.
 Real-Time Prevention of Identity Theft and Online Fraud 1. “Simplify and Strengthen” User and Device Authentication • Lower Help Desk costs by simplifying end user authentication experience • Strengthen the process with Device, Behavior and Location Fingerprinting 2. “Prevent and Detect” Fraud against your online systems • Hundreds of Out-of-the-Box Anti-Fraud scenarios provide immediate return • Ease-to-Understand Admin interface allows for Real-Time adjustments • Quickly bolt-on to existing Web Access Management to strengthen security 3. “Record, Analyze and Report” online activity for audit/forensic purposes • Review and drill-down into session and transaction details based on the User, the Application, IP Address, Location, Alert-Type, etc • Leverage the powerful Adaptive Reporting and BI Engine with over 50 Outof-the-Box reports and the ability to create Ad-Hoc queries © 2008 Oracle Corporation – Proprietary and Confidential
Real-Time Prevention of Identity Theft and Online Fraud 1. “Simplify and Strengthen” User and Device Authentication • Lower Help Desk costs by simplifying end user authentication experience • Strengthen the process with Device, Behavior and Location Fingerprinting 2. “Prevent and Detect” Fraud against your online systems • Hundreds of Out-of-the-Box Anti-Fraud scenarios provide immediate return • Ease-to-Understand Admin interface allows for Real-Time adjustments • Quickly bolt-on to existing Web Access Management to strengthen security 3. “Record, Analyze and Report” online activity for audit/forensic purposes • Review and drill-down into session and transaction details based on the User, the Application, IP Address, Location, Alert-Type, etc • Leverage the powerful Adaptive Reporting and BI Engine with over 50 Outof-the-Box reports and the ability to create Ad-Hoc queries © 2008 Oracle Corporation – Proprietary and Confidential
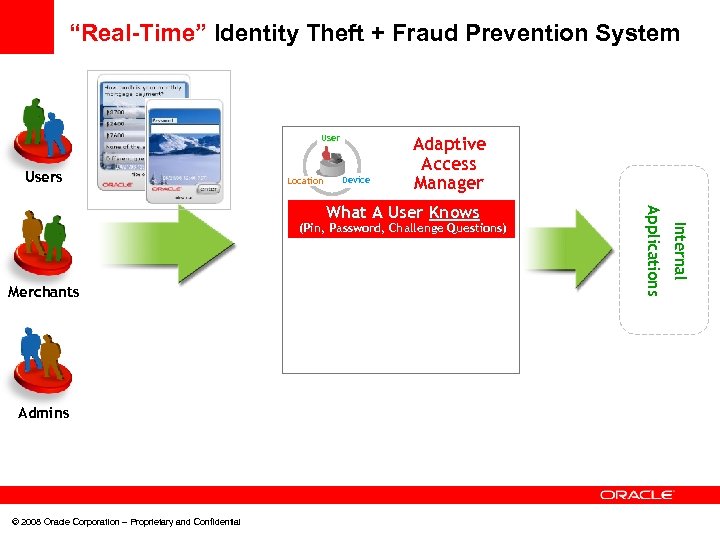 “Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager Merchants Admins © 2008 Oracle Corporation – Proprietary and Confidential Internal (Pin, Password, Challenge Questions) Applications What A User Knows
“Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager Merchants Admins © 2008 Oracle Corporation – Proprietary and Confidential Internal (Pin, Password, Challenge Questions) Applications What A User Knows
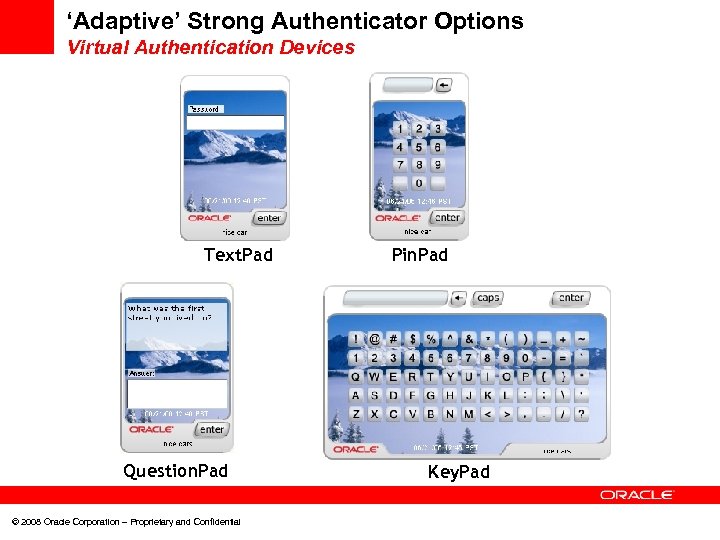 ‘Adaptive’ Strong Authenticator Options Virtual Authentication Devices Text. Pad Question. Pad © 2008 Oracle Corporation – Proprietary and Confidential Pin. Pad Key. Pad
‘Adaptive’ Strong Authenticator Options Virtual Authentication Devices Text. Pad Question. Pad © 2008 Oracle Corporation – Proprietary and Confidential Pin. Pad Key. Pad
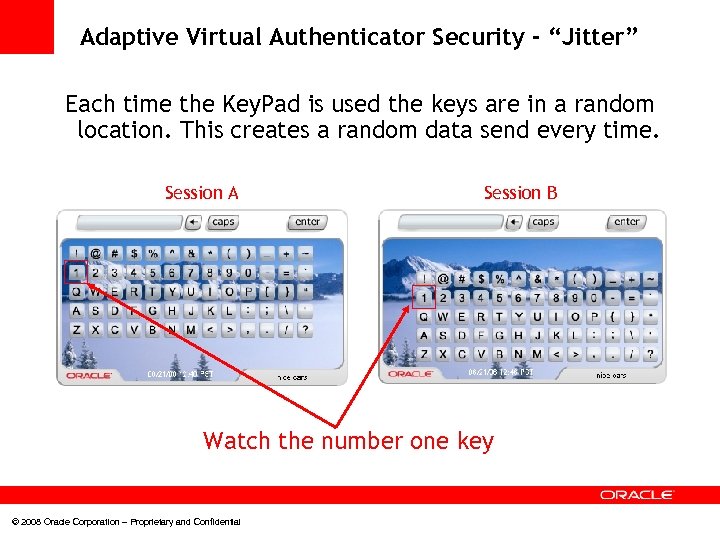 Adaptive Virtual Authenticator Security - “Jitter” Each time the Key. Pad is used the keys are in a random location. This creates a random data send every time. Session A Session B Watch the number one key © 2008 Oracle Corporation – Proprietary and Confidential
Adaptive Virtual Authenticator Security - “Jitter” Each time the Key. Pad is used the keys are in a random location. This creates a random data send every time. Session A Session B Watch the number one key © 2008 Oracle Corporation – Proprietary and Confidential
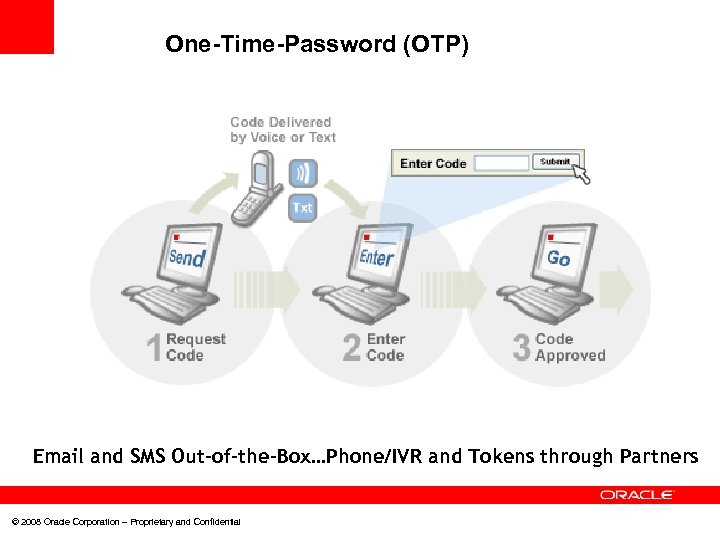 One-Time-Password (OTP) Email and SMS Out-of-the-Box…Phone/IVR and Tokens through Partners © 2008 Oracle Corporation – Proprietary and Confidential
One-Time-Password (OTP) Email and SMS Out-of-the-Box…Phone/IVR and Tokens through Partners © 2008 Oracle Corporation – Proprietary and Confidential
 “Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager What A User Has (Device Fingerprinting) Merchants Admins © 2008 Oracle Corporation – Proprietary and Confidential Internal (Pin, Password, Challenge Questions) Applications What A User Knows
“Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager What A User Has (Device Fingerprinting) Merchants Admins © 2008 Oracle Corporation – Proprietary and Confidential Internal (Pin, Password, Challenge Questions) Applications What A User Knows
 What Is Being Captured – Under the Covers? Used for Risk Scoring and Forensics © 2008 Oracle Corporation – Proprietary and Confidential
What Is Being Captured – Under the Covers? Used for Risk Scoring and Forensics © 2008 Oracle Corporation – Proprietary and Confidential
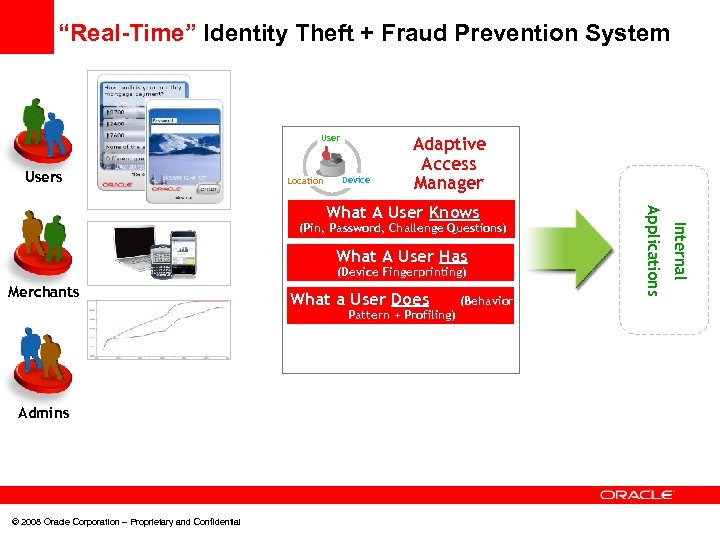 “Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager What A User Has (Device Fingerprinting) Merchants What a User Does Pattern + Profiling) Admins © 2008 Oracle Corporation – Proprietary and Confidential (Behavior Internal (Pin, Password, Challenge Questions) Applications What A User Knows
“Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager What A User Has (Device Fingerprinting) Merchants What a User Does Pattern + Profiling) Admins © 2008 Oracle Corporation – Proprietary and Confidential (Behavior Internal (Pin, Password, Challenge Questions) Applications What A User Knows
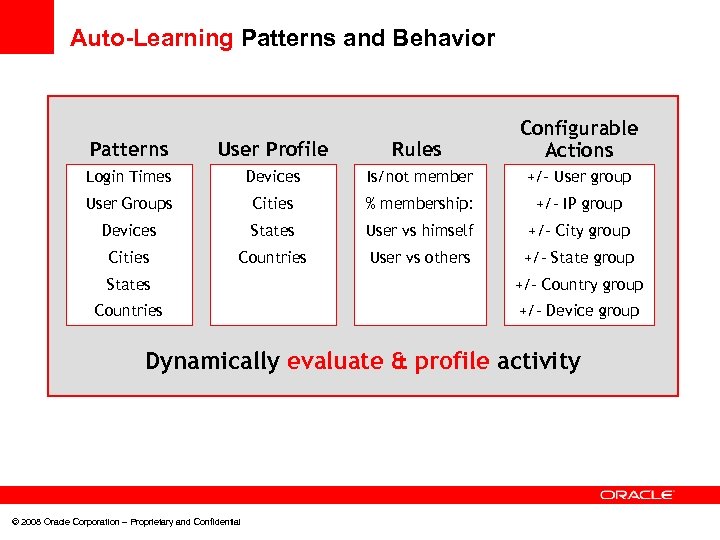 Auto-Learning Patterns and Behavior Patterns User Profile Rules Configurable Actions Login Times Devices Is/not member +/- User group User Groups Cities % membership: +/- IP group Devices States User vs himself +/- City group Cities Countries User vs others +/- State group States +/- Country group Countries +/- Device group Dynamically evaluate & profile activity © 2008 Oracle Corporation – Proprietary and Confidential
Auto-Learning Patterns and Behavior Patterns User Profile Rules Configurable Actions Login Times Devices Is/not member +/- User group User Groups Cities % membership: +/- IP group Devices States User vs himself +/- City group Cities Countries User vs others +/- State group States +/- Country group Countries +/- Device group Dynamically evaluate & profile activity © 2008 Oracle Corporation – Proprietary and Confidential
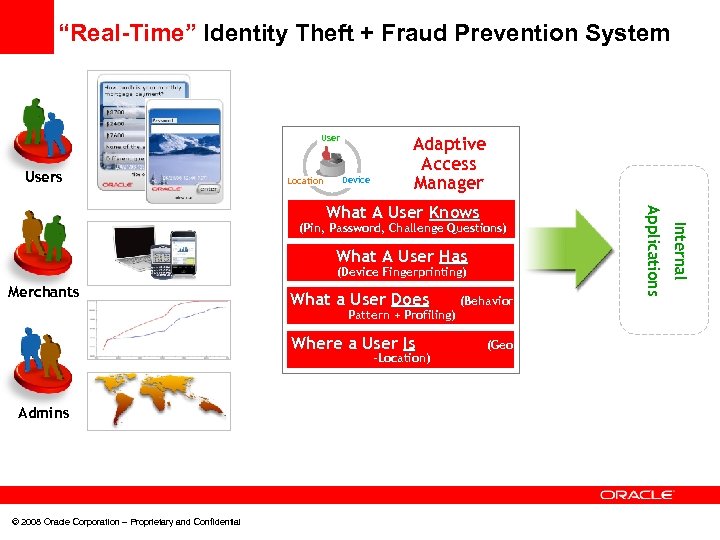 “Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager What A User Has (Device Fingerprinting) Merchants What a User Does Pattern + Profiling) Where a User Is -Location) Admins © 2008 Oracle Corporation – Proprietary and Confidential (Behavior (Geo Internal (Pin, Password, Challenge Questions) Applications What A User Knows
“Real-Time” Identity Theft + Fraud Prevention System Users Location Device Adaptive Access Manager What A User Has (Device Fingerprinting) Merchants What a User Does Pattern + Profiling) Where a User Is -Location) Admins © 2008 Oracle Corporation – Proprietary and Confidential (Behavior (Geo Internal (Pin, Password, Challenge Questions) Applications What A User Knows
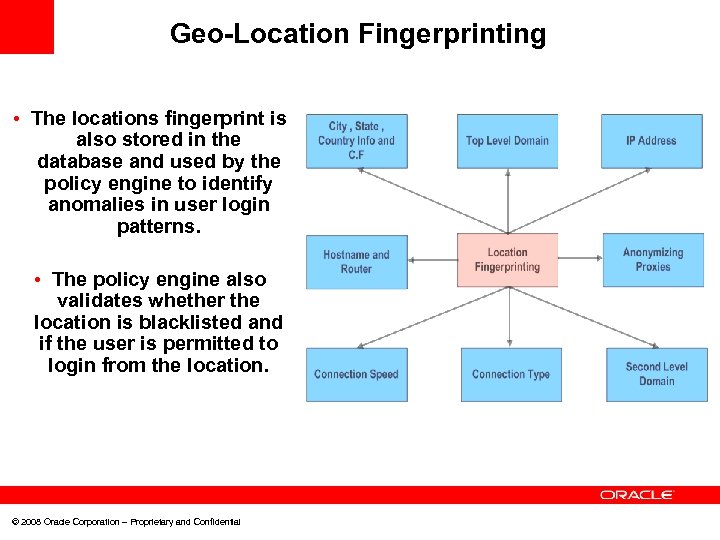 Geo-Location Fingerprinting • The locations fingerprint is also stored in the database and used by the policy engine to identify anomalies in user login patterns. • The policy engine also validates whether the location is blacklisted and if the user is permitted to login from the location. © 2008 Oracle Corporation – Proprietary and Confidential
Geo-Location Fingerprinting • The locations fingerprint is also stored in the database and used by the policy engine to identify anomalies in user login patterns. • The policy engine also validates whether the location is blacklisted and if the user is permitted to login from the location. © 2008 Oracle Corporation – Proprietary and Confidential
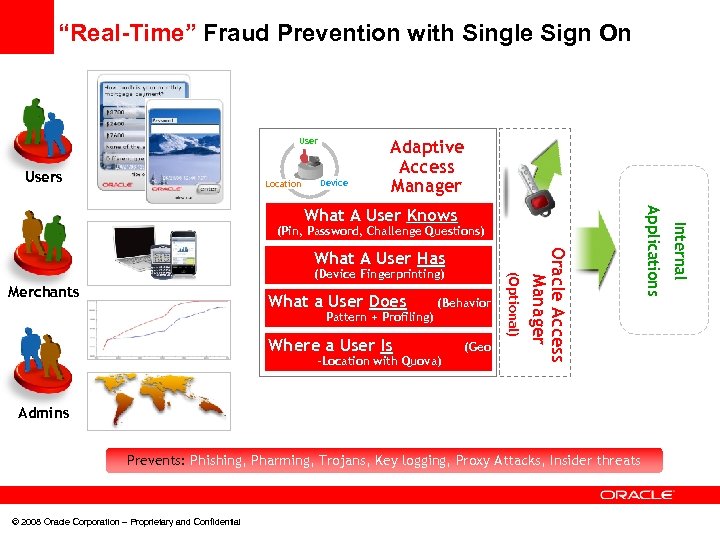 “Real-Time” Fraud Prevention with Single Sign On Users Location Device Adaptive Access Manager What a User Does Pattern + Profiling) Where a User Is (Behavior -Location with Quova) (Geo Admins Prevents: Phishing, Pharming, Trojans, Key logging, Proxy Attacks, Insider threats © 2008 Oracle Corporation – Proprietary and Confidential Internal Merchants (Optional) (Device Fingerprinting) Oracle Access Manager What A User Has Applications What A User Knows (Pin, Password, Challenge Questions)
“Real-Time” Fraud Prevention with Single Sign On Users Location Device Adaptive Access Manager What a User Does Pattern + Profiling) Where a User Is (Behavior -Location with Quova) (Geo Admins Prevents: Phishing, Pharming, Trojans, Key logging, Proxy Attacks, Insider threats © 2008 Oracle Corporation – Proprietary and Confidential Internal Merchants (Optional) (Device Fingerprinting) Oracle Access Manager What A User Has Applications What A User Knows (Pin, Password, Challenge Questions)
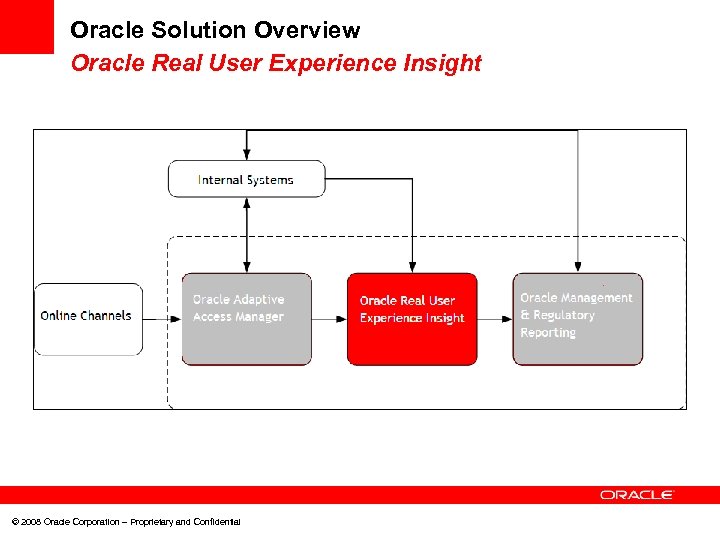 Oracle Solution Overview Oracle Real User Experience Insight © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Solution Overview Oracle Real User Experience Insight © 2008 Oracle Corporation – Proprietary and Confidential
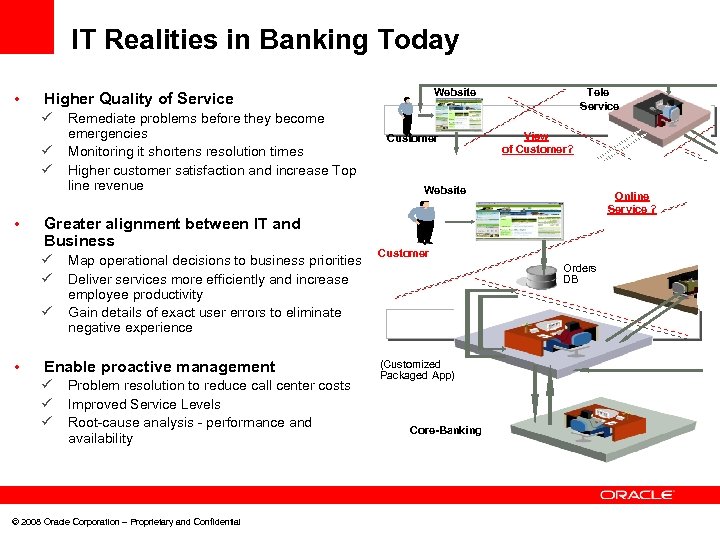 IT Realities in Banking Today • ü ü ü • Remediate problems before they become emergencies Monitoring it shortens resolution times Higher customer satisfaction and increase Top line revenue Greater alignment between IT and Business ü ü ü • Website Higher Quality of Service Map operational decisions to business priorities Deliver services more efficiently and increase employee productivity Gain details of exact user errors to eliminate negative experience Enable proactive management ü ü ü Problem resolution to reduce call center costs Improved Service Levels Root-cause analysis - performance and availability © 2008 Oracle Corporation – Proprietary and Confidential Customer Tele Service View of Customer? Website Online Service ? Customer Orders DB (Customized Packaged App) Core-Banking
IT Realities in Banking Today • ü ü ü • Remediate problems before they become emergencies Monitoring it shortens resolution times Higher customer satisfaction and increase Top line revenue Greater alignment between IT and Business ü ü ü • Website Higher Quality of Service Map operational decisions to business priorities Deliver services more efficiently and increase employee productivity Gain details of exact user errors to eliminate negative experience Enable proactive management ü ü ü Problem resolution to reduce call center costs Improved Service Levels Root-cause analysis - performance and availability © 2008 Oracle Corporation – Proprietary and Confidential Customer Tele Service View of Customer? Website Online Service ? Customer Orders DB (Customized Packaged App) Core-Banking
 What you do not want happening… © 2008 Oracle Corporation – Proprietary and Confidential
What you do not want happening… © 2008 Oracle Corporation – Proprietary and Confidential
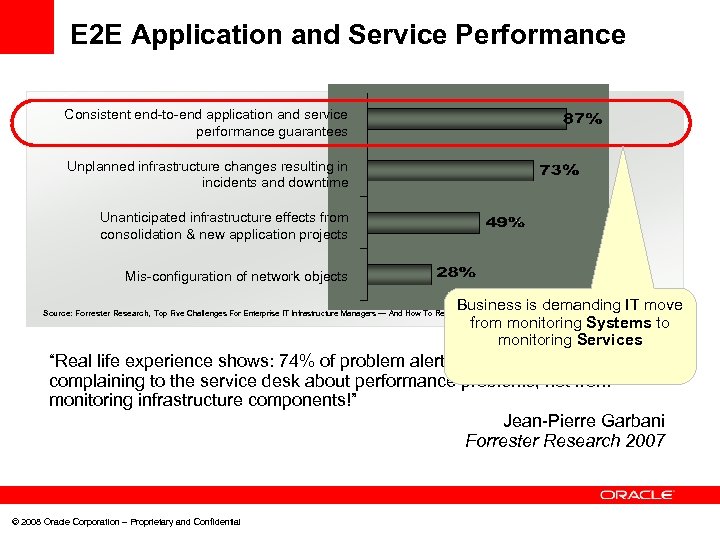 E 2 E Application and Service Performance Consistent end-to-end application and service performance guarantees Unplanned infrastructure changes resulting in incidents and downtime Unanticipated infrastructure effects from consolidation & new application projects Mis-configuration of network objects Business is demanding IT move from monitoring Systems to monitoring Services Source: Forrester Research, Top Five Challenges For Enterprise IT Infrastructure Managers — And How To Resolve Them, Thomas Mendel, March 2005 “Real life experience shows: 74% of problem alerts come from end users complaining to the service desk about performance problems, not from monitoring infrastructure components!” Jean-Pierre Garbani Forrester Research 2007 © 2008 Oracle Corporation – Proprietary and Confidential
E 2 E Application and Service Performance Consistent end-to-end application and service performance guarantees Unplanned infrastructure changes resulting in incidents and downtime Unanticipated infrastructure effects from consolidation & new application projects Mis-configuration of network objects Business is demanding IT move from monitoring Systems to monitoring Services Source: Forrester Research, Top Five Challenges For Enterprise IT Infrastructure Managers — And How To Resolve Them, Thomas Mendel, March 2005 “Real life experience shows: 74% of problem alerts come from end users complaining to the service desk about performance problems, not from monitoring infrastructure components!” Jean-Pierre Garbani Forrester Research 2007 © 2008 Oracle Corporation – Proprietary and Confidential
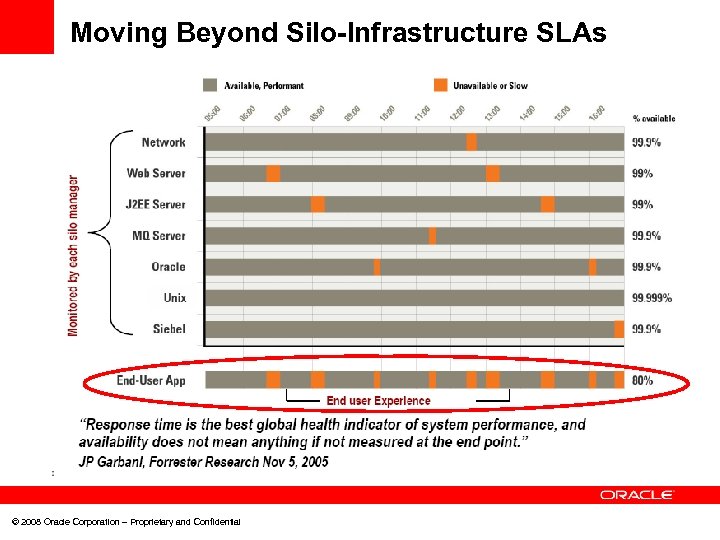 Moving Beyond Silo-Infrastructure SLAs © 2008 Oracle Corporation – Proprietary and Confidential
Moving Beyond Silo-Infrastructure SLAs © 2008 Oracle Corporation – Proprietary and Confidential
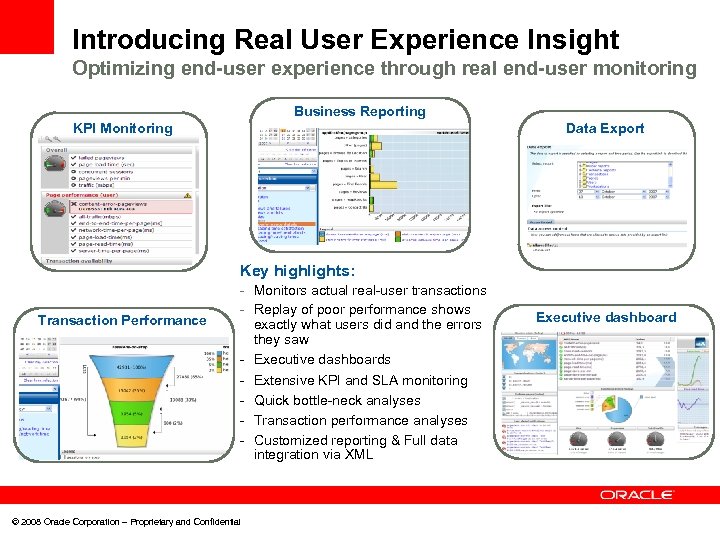 Introducing Real User Experience Insight Optimizing end-user experience through real end-user monitoring Business Reporting Data Export KPI Monitoring Key highlights: Transaction Performance - Monitors actual real-user transactions - Replay of poor performance shows exactly what users did and the errors they saw - Executive dashboards - Extensive KPI and SLA monitoring - Quick bottle-neck analyses - Transaction performance analyses - Customized reporting & Full data integration via XML © 2008 Oracle Corporation – Proprietary and Confidential Executive dashboard
Introducing Real User Experience Insight Optimizing end-user experience through real end-user monitoring Business Reporting Data Export KPI Monitoring Key highlights: Transaction Performance - Monitors actual real-user transactions - Replay of poor performance shows exactly what users did and the errors they saw - Executive dashboards - Extensive KPI and SLA monitoring - Quick bottle-neck analyses - Transaction performance analyses - Customized reporting & Full data integration via XML © 2008 Oracle Corporation – Proprietary and Confidential Executive dashboard
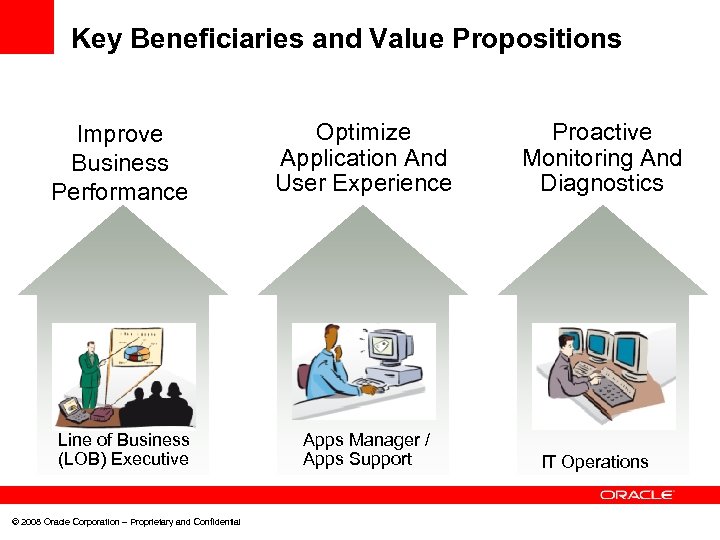 Key Beneficiaries and Value Propositions Improve Business Performance Optimize Application And User Experience Line of Business (LOB) Executive Apps Manager / Apps Support © 2008 Oracle Corporation – Proprietary and Confidential Proactive Monitoring And Diagnostics IT Operations
Key Beneficiaries and Value Propositions Improve Business Performance Optimize Application And User Experience Line of Business (LOB) Executive Apps Manager / Apps Support © 2008 Oracle Corporation – Proprietary and Confidential Proactive Monitoring And Diagnostics IT Operations
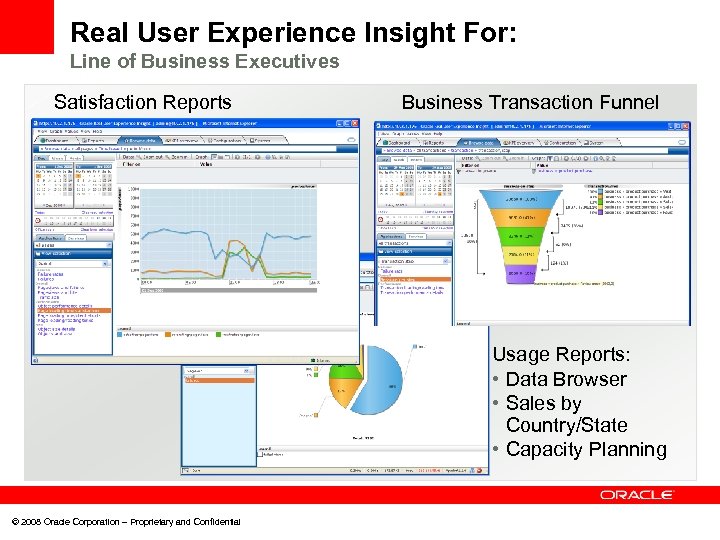 Real User Experience Insight For: Line of Business Executives Satisfaction Reports Business Transaction Funnel Usage Reports: • Data Browser • Sales by Country/State • Capacity Planning © 2008 Oracle Corporation – Proprietary and Confidential
Real User Experience Insight For: Line of Business Executives Satisfaction Reports Business Transaction Funnel Usage Reports: • Data Browser • Sales by Country/State • Capacity Planning © 2008 Oracle Corporation – Proprietary and Confidential
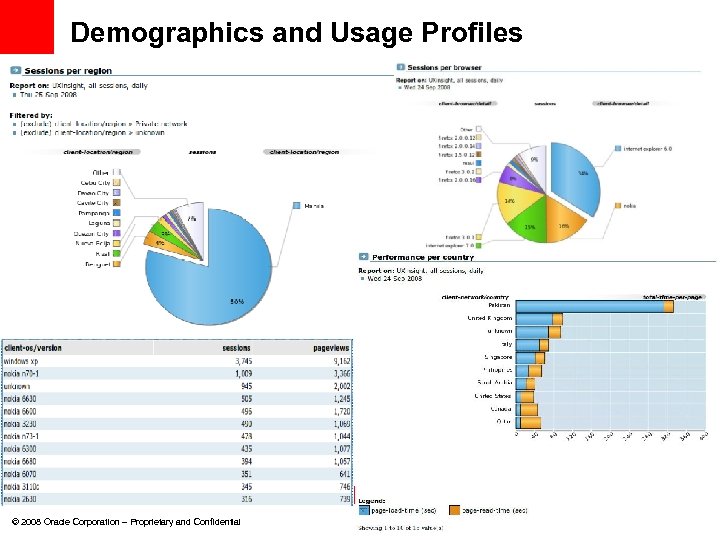 Demographics and Usage Profiles © 2008 Oracle Corporation – Proprietary and Confidential
Demographics and Usage Profiles © 2008 Oracle Corporation – Proprietary and Confidential
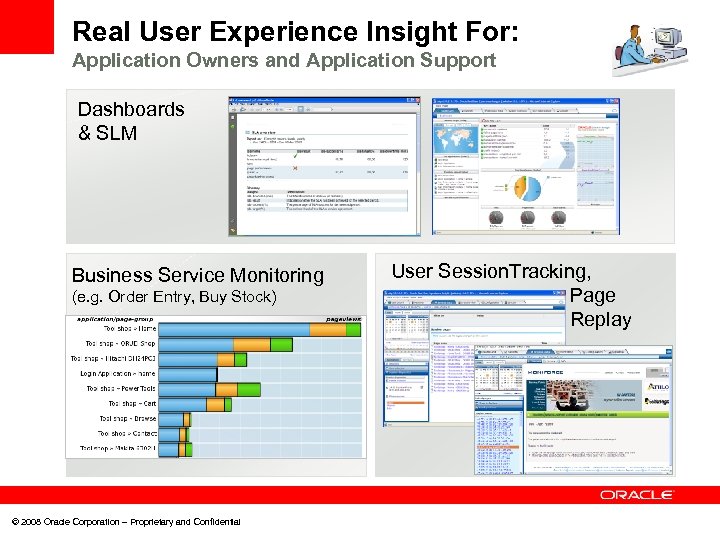 Real User Experience Insight For: Application Owners and Application Support Dashboards & SLM Business Service Monitoring (e. g. Order Entry, Buy Stock) © 2008 Oracle Corporation – Proprietary and Confidential User Session. Tracking, Page Replay
Real User Experience Insight For: Application Owners and Application Support Dashboards & SLM Business Service Monitoring (e. g. Order Entry, Buy Stock) © 2008 Oracle Corporation – Proprietary and Confidential User Session. Tracking, Page Replay
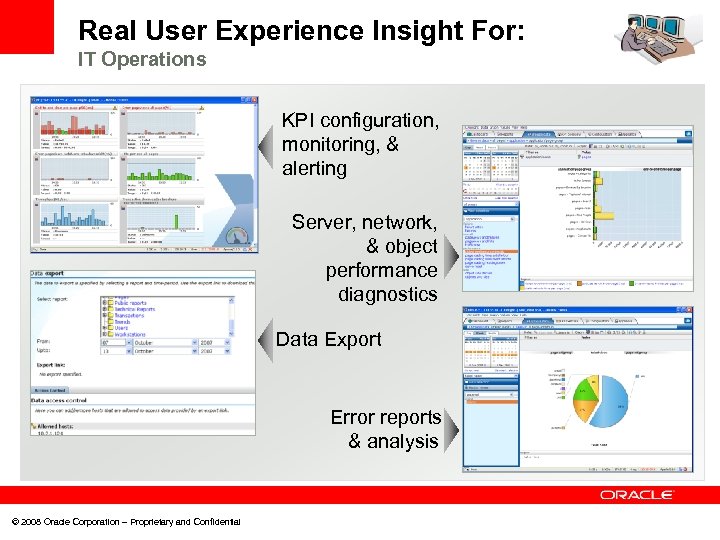 Real User Experience Insight For: IT Operations KPI configuration, monitoring, & alerting Server, network, & object performance diagnostics Data Export Error reports & analysis © 2008 Oracle Corporation – Proprietary and Confidential
Real User Experience Insight For: IT Operations KPI configuration, monitoring, & alerting Server, network, & object performance diagnostics Data Export Error reports & analysis © 2008 Oracle Corporation – Proprietary and Confidential
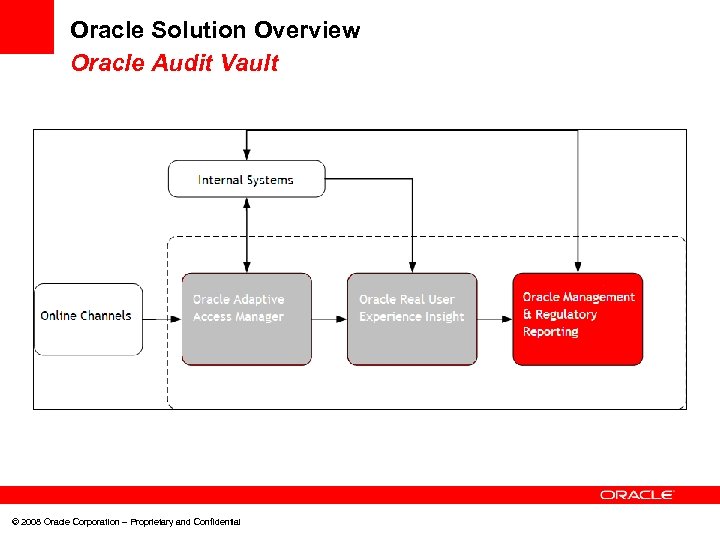 Oracle Solution Overview Oracle Audit Vault © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Solution Overview Oracle Audit Vault © 2008 Oracle Corporation – Proprietary and Confidential
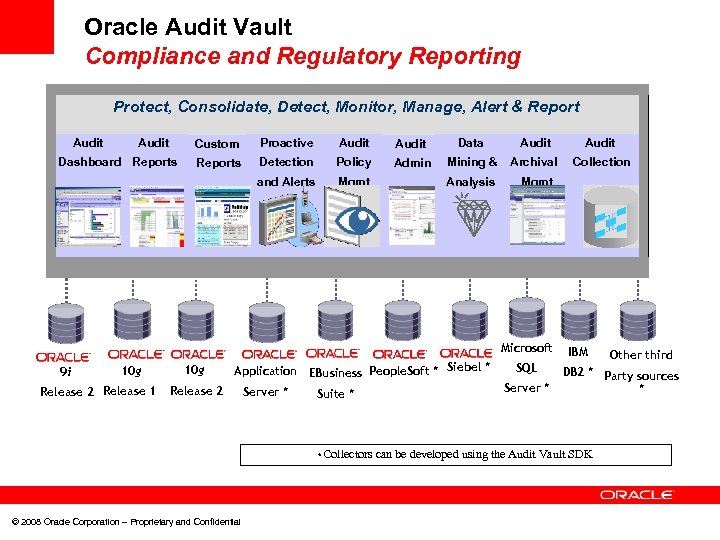 Oracle Audit Vault Compliance and Regulatory Reporting Protect, Consolidate, Detect, Monitor, Manage, Alert & Report Audit Custom Audit Data Audit Reports Detection Policy Admin Mining & Archival Collection and Alerts Dashboard Reports Proactive Mgmt Analysis Mgmt Microsoft 9 i 10 g Release 2 Release 1 10 g Application EBusiness People. Soft * Siebel * Release 2 Server * Suite * * © 2008 Oracle Corporation – Proprietary and Confidential SQL Server * IBM Other third DB 2 * Party sources * Collectors can be developed using the Audit Vault SDK
Oracle Audit Vault Compliance and Regulatory Reporting Protect, Consolidate, Detect, Monitor, Manage, Alert & Report Audit Custom Audit Data Audit Reports Detection Policy Admin Mining & Archival Collection and Alerts Dashboard Reports Proactive Mgmt Analysis Mgmt Microsoft 9 i 10 g Release 2 Release 1 10 g Application EBusiness People. Soft * Siebel * Release 2 Server * Suite * * © 2008 Oracle Corporation – Proprietary and Confidential SQL Server * IBM Other third DB 2 * Party sources * Collectors can be developed using the Audit Vault SDK
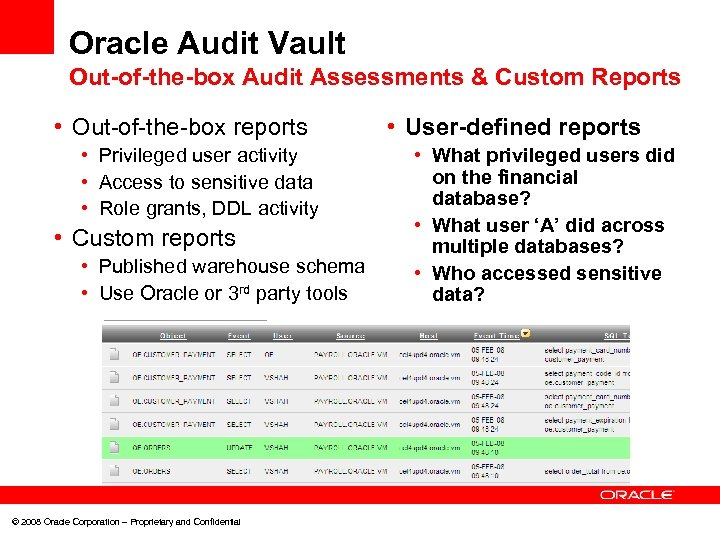 Oracle Audit Vault Out-of-the-box Audit Assessments & Custom Reports • Out-of-the-box reports • Privileged user activity • Access to sensitive data • Role grants, DDL activity • Custom reports • Published warehouse schema • Use Oracle or 3 rd party tools © 2008 Oracle Corporation – Proprietary and Confidential • User-defined reports • What privileged users did on the financial database? • What user ‘A’ did across multiple databases? • Who accessed sensitive data?
Oracle Audit Vault Out-of-the-box Audit Assessments & Custom Reports • Out-of-the-box reports • Privileged user activity • Access to sensitive data • Role grants, DDL activity • Custom reports • Published warehouse schema • Use Oracle or 3 rd party tools © 2008 Oracle Corporation – Proprietary and Confidential • User-defined reports • What privileged users did on the financial database? • What user ‘A’ did across multiple databases? • Who accessed sensitive data?
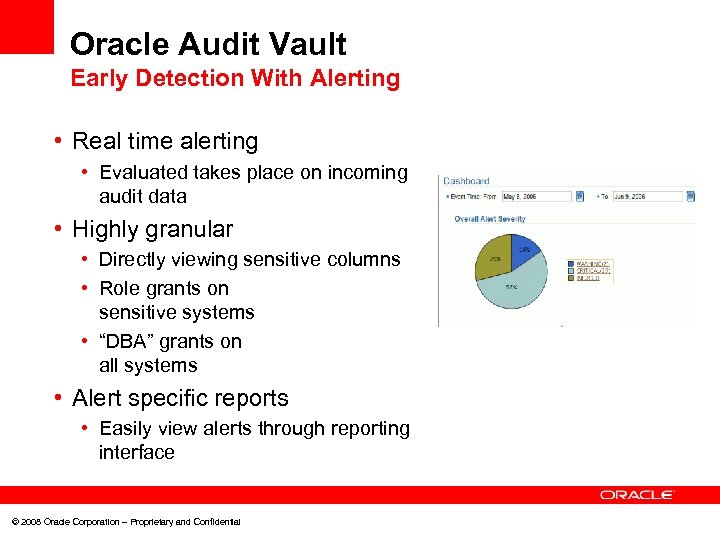 Oracle Audit Vault Early Detection With Alerting • Real time alerting • Evaluated takes place on incoming audit data • Highly granular • Directly viewing sensitive columns • Role grants on sensitive systems • “DBA” grants on all systems • Alert specific reports • Easily view alerts through reporting interface © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Audit Vault Early Detection With Alerting • Real time alerting • Evaluated takes place on incoming audit data • Highly granular • Directly viewing sensitive columns • Role grants on sensitive systems • “DBA” grants on all systems • Alert specific reports • Easily view alerts through reporting interface © 2008 Oracle Corporation – Proprietary and Confidential
 Oracle Audit Vault Scalable, Flexible & Secure • Performance and Scalability • Scale to Terabytes with partitioning • Data warehouse enables business intelligence and analysis • Security • Separation of duty • Privileged users can't modify audit data • Data protected in transit from source to Audit Vault © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Audit Vault Scalable, Flexible & Secure • Performance and Scalability • Scale to Terabytes with partitioning • Data warehouse enables business intelligence and analysis • Security • Separation of duty • Privileged users can't modify audit data • Data protected in transit from source to Audit Vault © 2008 Oracle Corporation – Proprietary and Confidential
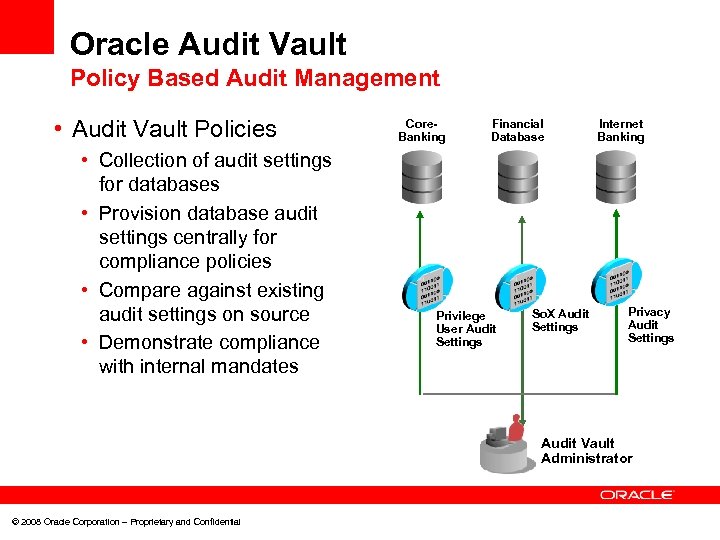 Oracle Audit Vault Policy Based Audit Management • Audit Vault Policies • Collection of audit settings for databases • Provision database audit settings centrally for compliance policies • Compare against existing audit settings on source • Demonstrate compliance with internal mandates Core. Banking Financial Database Privilege User Audit Settings So. X Audit Settings Internet Banking Privacy Audit Settings Audit Vault Administrator © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Audit Vault Policy Based Audit Management • Audit Vault Policies • Collection of audit settings for databases • Provision database audit settings centrally for compliance policies • Compare against existing audit settings on source • Demonstrate compliance with internal mandates Core. Banking Financial Database Privilege User Audit Settings So. X Audit Settings Internet Banking Privacy Audit Settings Audit Vault Administrator © 2008 Oracle Corporation – Proprietary and Confidential
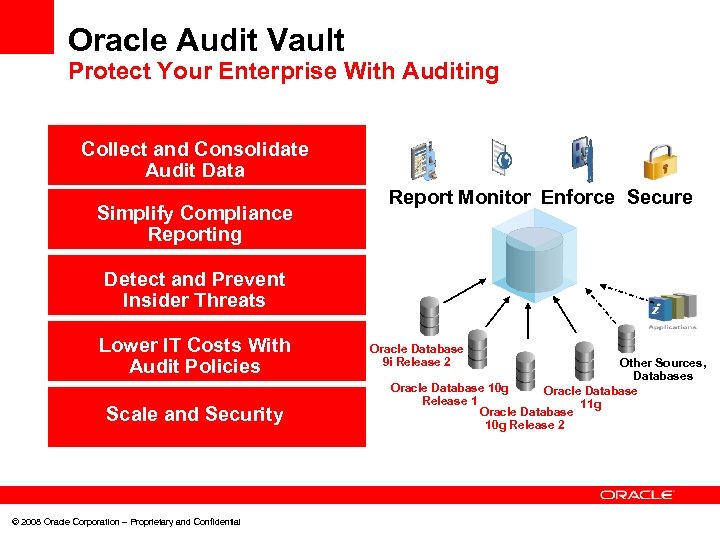 Oracle Audit Vault Protect Your Enterprise With Auditing Collect and Consolidate Audit Data Simplify Compliance Reporting Report Monitor Enforce Secure Detect and Prevent Insider Threats Lower IT Costs With Audit Policies Scale and Security © 2008 Oracle Corporation – Proprietary and Confidential Oracle Database 9 i Release 2 Other Sources, Databases Oracle Database 10 g Oracle Database Release 1 11 g Oracle Database 10 g Release 2
Oracle Audit Vault Protect Your Enterprise With Auditing Collect and Consolidate Audit Data Simplify Compliance Reporting Report Monitor Enforce Secure Detect and Prevent Insider Threats Lower IT Costs With Audit Policies Scale and Security © 2008 Oracle Corporation – Proprietary and Confidential Oracle Database 9 i Release 2 Other Sources, Databases Oracle Database 10 g Oracle Database Release 1 11 g Oracle Database 10 g Release 2
 Oracle Solution Overview Enterprise Risk/Security & Experience Monitoring System Key Differentiators Real Time Detection & Prevention Software-based multi-factor Strong Authentication Sophisticated Transaction Monitoring with out-of-thebox capability Unified Reporting End to End integrated solution with industry proven modules. © 2008 Oracle Corporation – Proprietary and Confidential
Oracle Solution Overview Enterprise Risk/Security & Experience Monitoring System Key Differentiators Real Time Detection & Prevention Software-based multi-factor Strong Authentication Sophisticated Transaction Monitoring with out-of-thebox capability Unified Reporting End to End integrated solution with industry proven modules. © 2008 Oracle Corporation – Proprietary and Confidential
 © 2008 Oracle Corporation – Proprietary and Confidential
© 2008 Oracle Corporation – Proprietary and Confidential




