aa216581c922baa8985b9c30af292d8c.ppt
- Количество слайдов: 25

Injecting RBAC to Secure a Web-based Workflow System Gail-Joon Ahn and Ravi Sandhu George Mason University Myong Kang and Joon Park Naval Research Laboratory

WORKFLOW MANAGEMENT SYSTEMS ¨ Control and coordinate processes that may be processed by different processing entities ¨ Received much attention ¨ Marriage with Web technology ¨ Minimal security services © Gail J. Ahn 2000 2

RELATED WORKS ¨ D. Hollingsworth, 1995 ¨ Peter J. Denning, 1996 ¨ Johann Eder et el. , 1997 (Panta Rhei) ¨ J. Miller et al. , 1998 (METEOR) ¨ Myong H. Kang et al. , 1999 ¨ Wei-Kuang Huang and Vijay Atluri, 1999 © Gail J. Ahn 2000 3
OBJECTIVE ¨ Inject role-based access control (RBAC) into an existing web-based workflow system © Gail J. Ahn 2000 4
WHY RBAC? ¨A mechanism which allows and promotes an organization-specific access control policy based on roles ¨ Has become widely accepted as the proven technology © Gail J. Ahn 2000 5
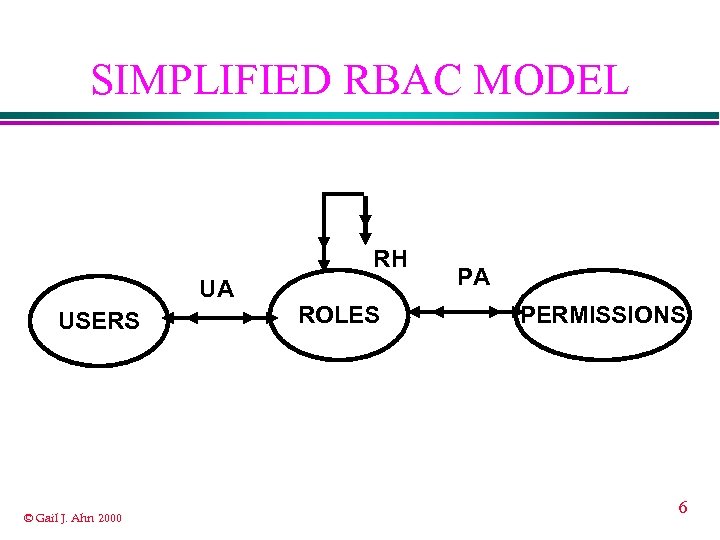
SIMPLIFIED RBAC MODEL RH UA USERS © Gail J. Ahn 2000 ROLES PA PERMISSIONS 6
ROLE-BASED SECURE WORKFLOW SYSTEM ¨ Workflow Design Tool ¨ Workflow (WF) System ¨ Role Server © Gail J. Ahn 2000 7
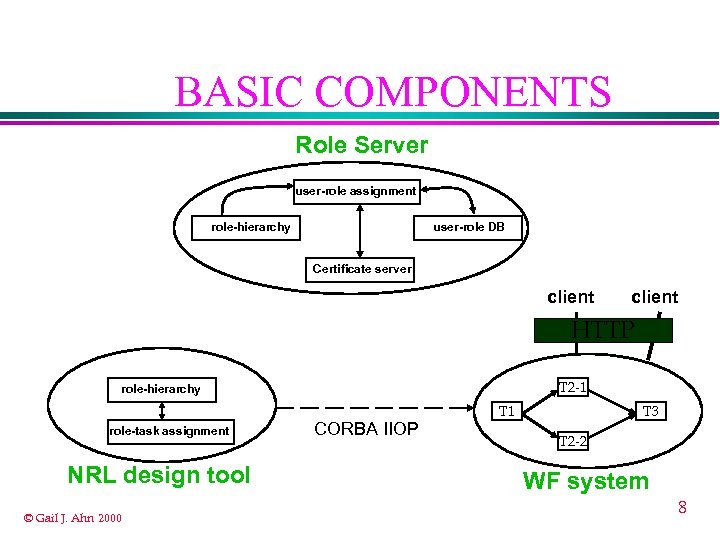
BASIC COMPONENTS Role Server user-role assignment role-hierarchy user-role DB Certificate server client HTTP T 2 -1 role-hierarchy role-task assignment NRL design tool © Gail J. Ahn 2000 CORBA IIOP T 1 T 3 T 2 -2 WF system 8
ARCHITECTURES ¨ USER-PULL STYLE ¨ SERVER-PULL STYLE © Gail J. Ahn 2000 9
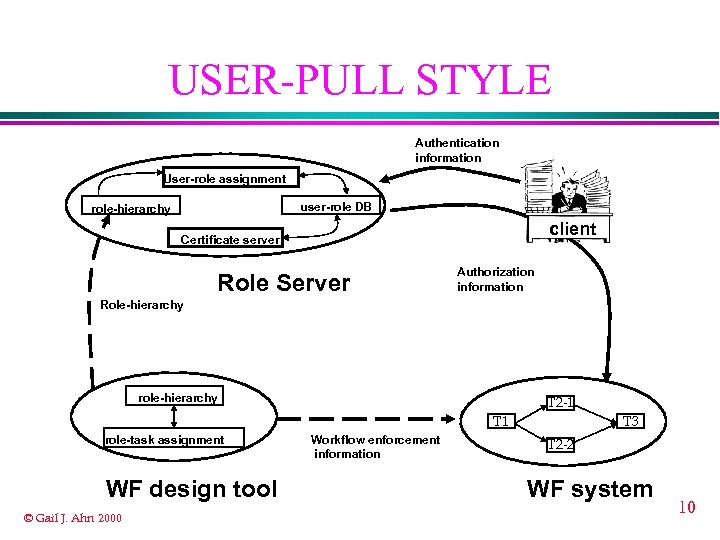
USER-PULL STYLE Authentication information User-role assignment user-role DB role-hierarchy client Certificate server Role Server Authorization information Role-hierarchy role-hierarchy T 2 -1 T 1 role-task assignment WF design tool © Gail J. Ahn 2000 Workflow enforcement information T 3 T 2 -2 WF system 10

SERVER-PULL STYLE User-role assignment role-hierarchy user-role DB client Certificate server Role Server Role-hierarchy Authentication information Authorization information role-hierarchy role-task assignment WF design tool © Gail J. Ahn 2000 T 2 -1 Workflow enforcement information T 1 T 3 T 2 -2 WF system 11

NRL (Naval Research Lab. ) DESIGN TOOL ¨ design workflow model ¨ create role and role hierarchies ¨ assign role to task ¨ exporting role hierarchies to role server © Gail J. Ahn 2000 12
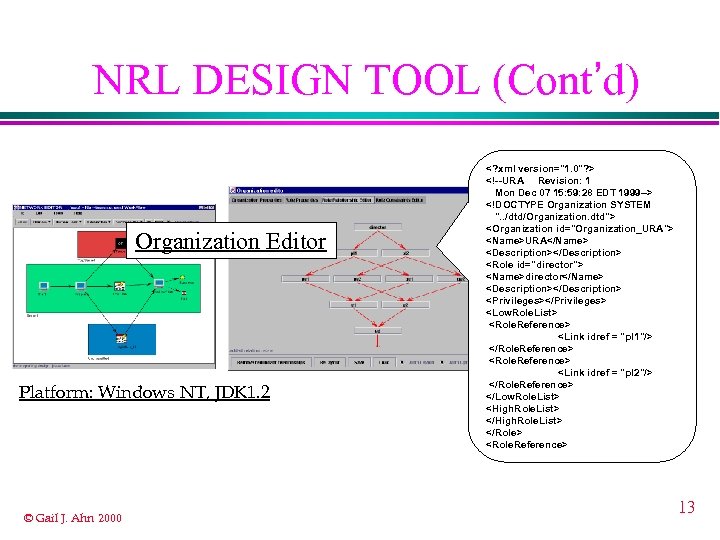
NRL DESIGN TOOL (Cont’d) Organization Editor Platform: Windows NT, JDK 1. 2 © Gail J. Ahn 2000 <? xml version="1. 0"? > <!--URA Revision: 1 Mon Dec 07 15: 59: 28 EDT 1999 --> <!DOCTYPE Organization SYSTEM ". . /dtd/Organization. dtd"> <Organization id="Organization_URA"> <Name>URA</Name> <Description></Description> <Role id="director"> <Name>director</Name> <Description></Description> <Privileges></Privileges> <Low. Role. List> <Role. Reference> <Link idref = "pl 1"/> </Role. Reference> <Link idref = "pl 2"/> </Role. Reference> </Low. Role. List> <High. Role. List> </Role> <Role. Reference> 13
WORKFLOW SYSTEM ¨ each task server is web server ¨ user should present client authentication certificate ¨ user’s privilege is authorized by content of certificate (specially client’s role information) © Gail J. Ahn 2000 14
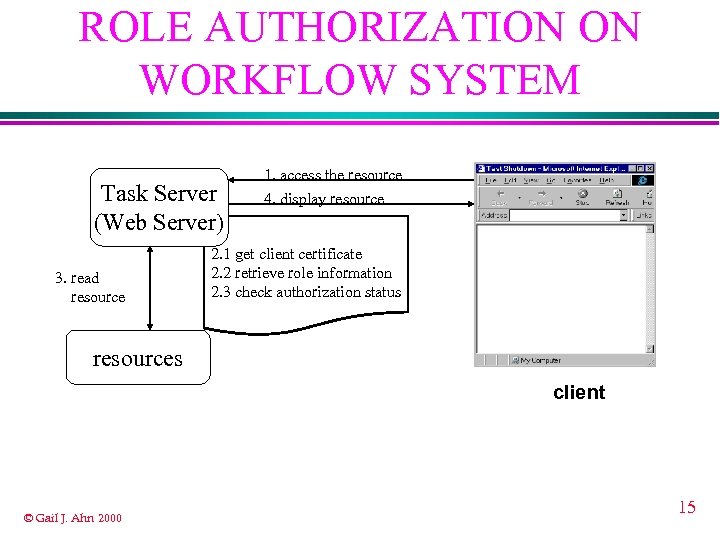
ROLE AUTHORIZATION ON WORKFLOW SYSTEM Task Server (Web Server) 3. read resource 1. access the resource 4. display resource 2. 1 get client certificate 2. 2 retrieve role information 2. 3 check authorization status resources client © Gail J. Ahn 2000 15
ROLE SERVER ¨ User Role Assignment ¨ Certificate Server © Gail J. Ahn 2000 16
USER ROLE ASSIGNMENT ¨ maintain role hierarchies and user database ¨ assign users to roles ¨ generate user-role database © Gail J. Ahn 2000 17
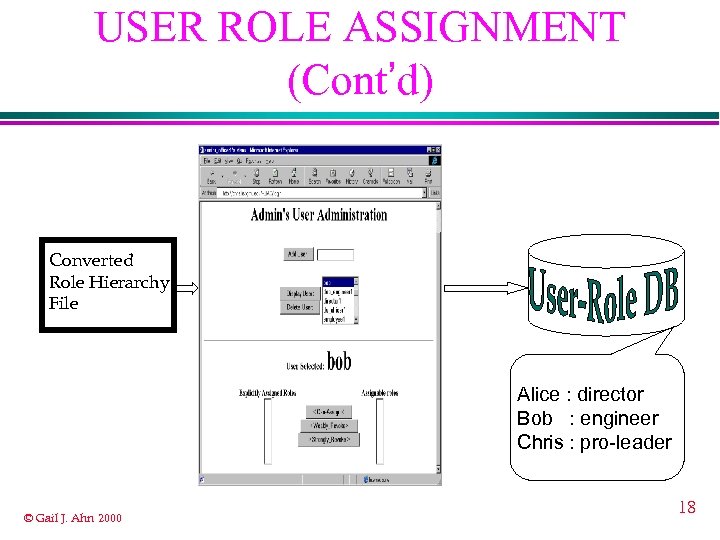
USER ROLE ASSIGNMENT (Cont’d) Converted Role Hierarchy File Alice : director Bob : engineer Chris : pro-leader © Gail J. Ahn 2000 18

CERTIFICATE SERVER ¨ authenticate client ¨ retrieve client’s role information from user-role database ¨ issue certificate with client’s role information © Gail J. Ahn 2000 19
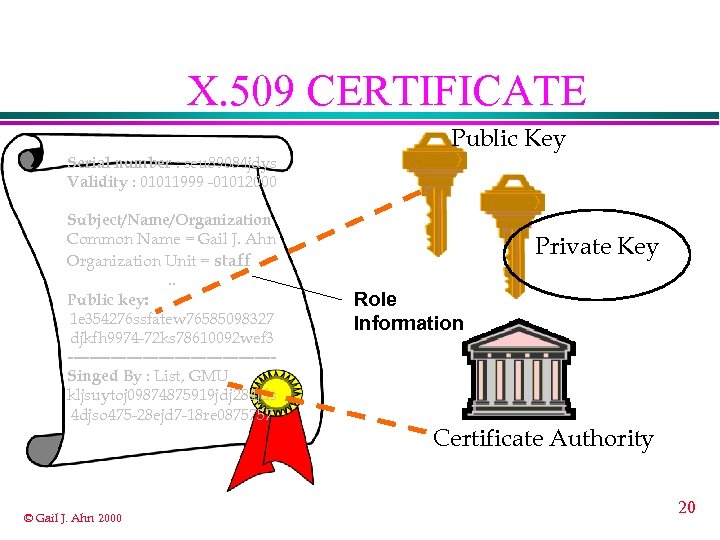
X. 509 CERTIFICATE Serial number : seu 89084 jdys Validity : 01011999 -01012000 Subject/Name/Organization Common Name = Gail J. Ahn Organization Unit = staff. . Public key: 1 e 354276 ssfatew 76585098327 djkfh 9974 -72 ks 78610092 wef 3 -------------------Singed By : List, GMU kljsuytoj 09874875919 jdj 284 jds 4 djso 475 -28 ejd 7 -18 re 0875757 © Gail J. Ahn 2000 Public Key Private Key Role Information Certificate Authority 20
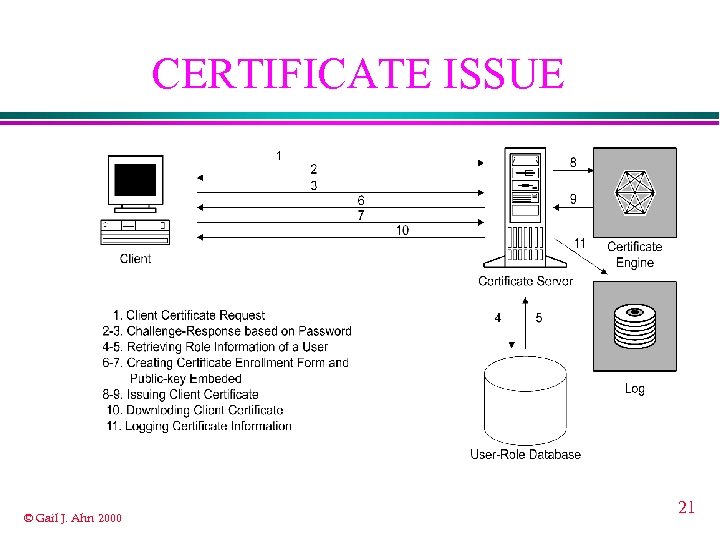
CERTIFICATE ISSUE © Gail J. Ahn 2000 21
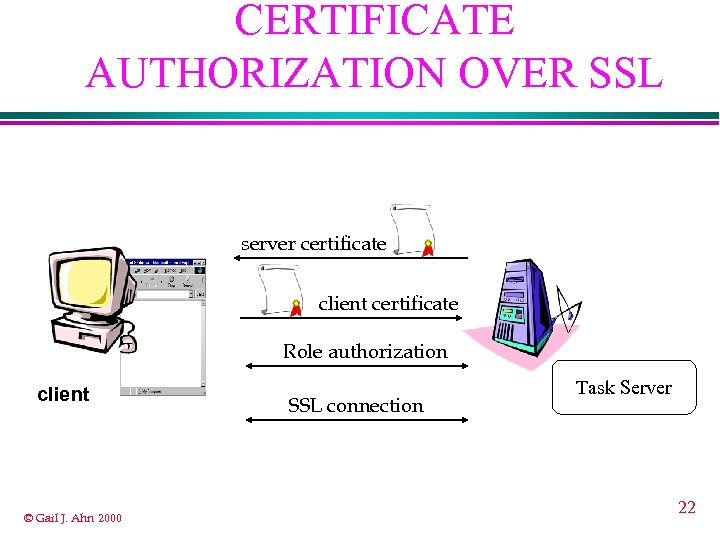
CERTIFICATE AUTHORIZATION OVER SSL server certificate client certificate Role authorization client © Gail J. Ahn 2000 SSL connection Task Server 22
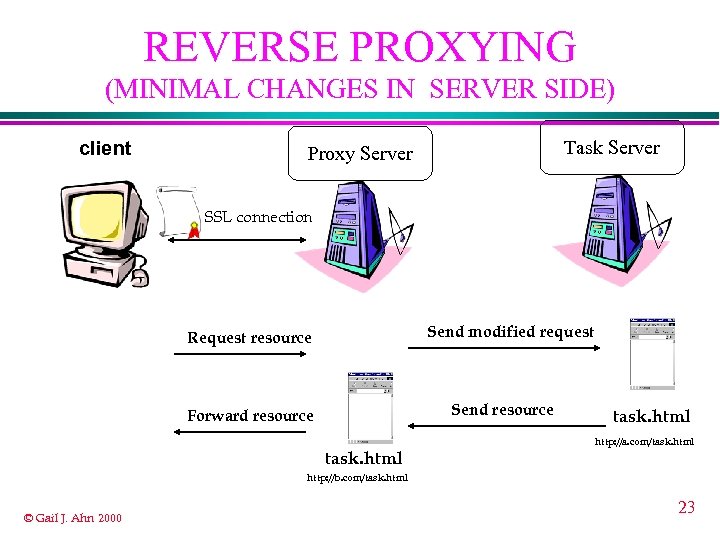
REVERSE PROXYING (MINIMAL CHANGES IN SERVER SIDE) client Task Server Proxy Server SSL connection Send modified request Request resource Send resource Forward resource task. html http: //a. com/task. html http: //b. com/task. html © Gail J. Ahn 2000 23
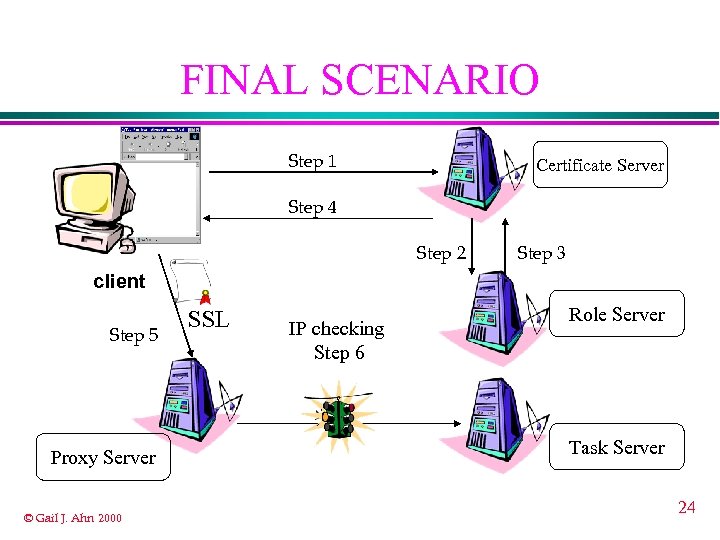
FINAL SCENARIO Step 1 Certificate Server Step 4 Step 2 Step 3 client Step 5 Proxy Server © Gail J. Ahn 2000 SSL IP checking Step 6 Role Server Task Server 24

CONCLUSION ¨ Model-driven experimental research ¨ Develop and motivate the model first ¨ Then implement on COTS platforms ¨ OM-AM Approach ¨ Objective ¨ Model ¨ Architecture ¨ Mechanism ¨ Funded © Gail J. Ahn 2000 by Naval Research Lab 25
aa216581c922baa8985b9c30af292d8c.ppt