f689ebe70f4ee4e8d390841ead8b26f9.ppt
- Количество слайдов: 45

Infrastructure of Information Systems for BIS Part 2
PRIMARY STORAGE § Primary storage - The computer’s main memory, which consists of the random access memory (RAM), cache memory, and the read-only memory (ROM) that is directly accessible to the CPU
Random Access Memory (RAM) § Random access memory (RAM) - The computer’s primary working memory, in which program instructions and data are stored so that they can be accessed directly by the CPU via the processor’s high-speed external data bus § Volatility § Cache memory
Read-Only Memory (ROM) § Read-only memory (ROM) - The portion of a computer’s primary storage that does not lose its contents when one switches off the power § Flash memory § Memory card § Memory stick
Primary Storage RAM Register Cache
SECONDARY STORAGE § Secondary storage - Consists of equipment designed to store large volumes of data for long-term storage § Magnetic Media: Hard disks, jump-stick/ flash / USB drives § Optical Media : CD, DVD

Hard Drive
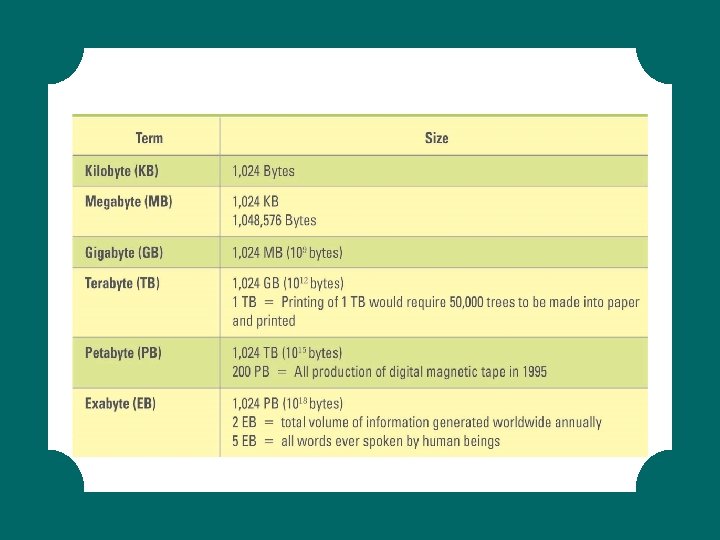
Secondary Storage Capacity
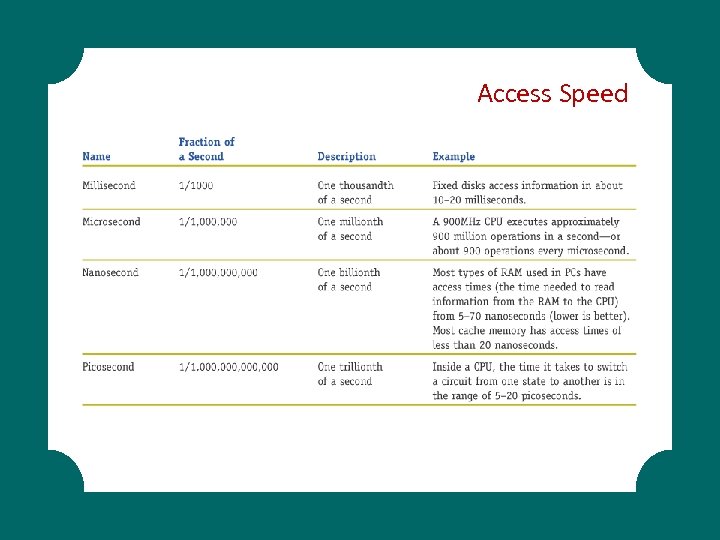
Access Speed
Magnetic Medium § Magnetic medium - A secondary storage medium that uses magnetic techniques to store and retrieve data on disks or tapes coated with magnetically sensitive materials § Magnetic tape - An older secondary storage medium that uses a strip of thin plastic coated with a magnetically sensitive recording medium § Hard drive - A secondary storage medium that uses several rigid disks coated with a magnetically sensitive material and housed together with the recording heads in a hermetically sealed mechanism
Optical Medium § Optical medium types include: § Compact disk-read-only memory (CDROM) § Compact disk-read-write (CD-RW) drive § Digital video disk (DVD) § DVD-ROM drive § Digital video disk-read/write (DVD-RW)

INPUT DEVICES § Input device - Equipment used to capture information and commands § Manual input devices - Joystick - Keyboard - Microphone § Automated input devices - Bar code scanner - Digital camera - Magnetic ink character reader
OUTPUT DEVICES § Output device Equipment used to see, hear, or otherwise accept the results of information processing requests § § § Cathode-ray tube (CRT) Liquid crystal display (LCD) Laser printer Ink-jet printer Plotter

§ Communication device - Equipment used to send information and receive it from one location to another § § § Dial-up access Cable Digital subscriber line Wireless Satellite COMMUNICATION DEVICES
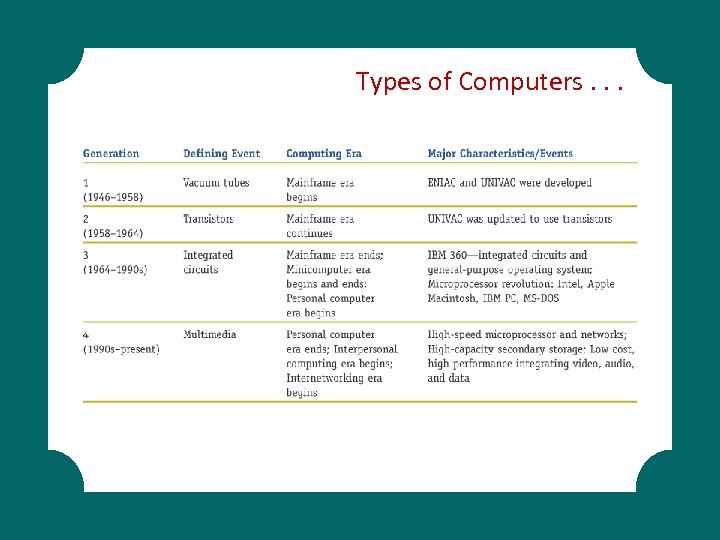
Types of Computers. . .
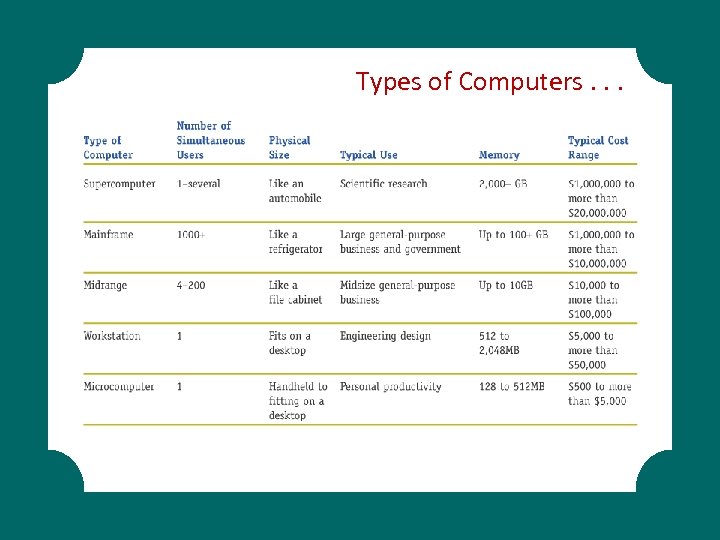
Types of Computers. . .

Strategic Hardware Issues § How do organizations keep up with the rapid price and performance advancements in hardware? § How often should an organization upgrade its computers and storage systems? § Will upgrades increase personal and organizational productivity? § How can organizations measure such increase? § How do organizations manage telecommuting?

SOFTWARE BASICS § System software controls how the various technology tools work together along with the application software § Operating system software § Utility software § Application software
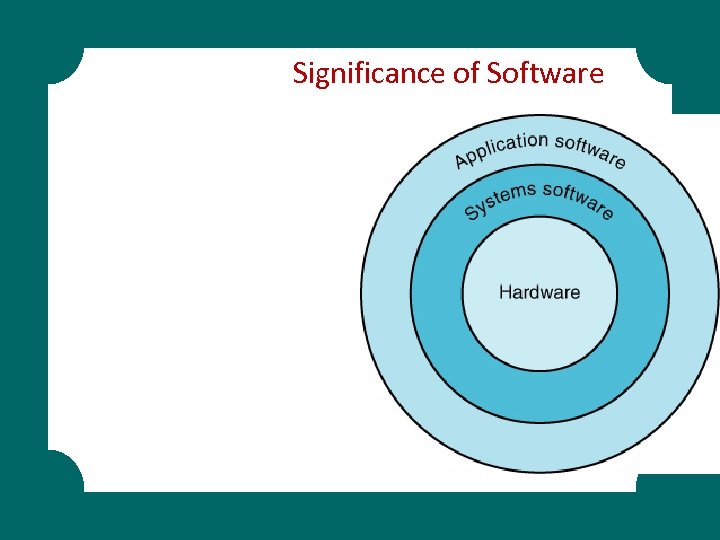
Significance of Software
Functions of the Operating System § § § Multitasking/multiprogramming (one CPU) Multithreading (many tasks in one program) Multiprocessing (multiple CPUs) Virtual Memory (extend primary to secondary storage) Graphical user interface (GUI)

System Support Programs System support programs System utilities System performance monitors System security monitors System support programs: Software that supports the operations management and users of a computer system by providing a variety of support services (e. g. system utility programs, performance monitors, and security monitors). § System utilities: Programs that accomplish common tasks such as sorting records, locating files, and managing memory usage. § System performance monitors: Programs that monitor the processing of jobs on a computer system and monitor system performance in areas such as processor time, memory space and application programs. § System security monitors: Programs that monitor a computer system to protect it and its resources from unauthorized use, fraud, or destruction. § § §
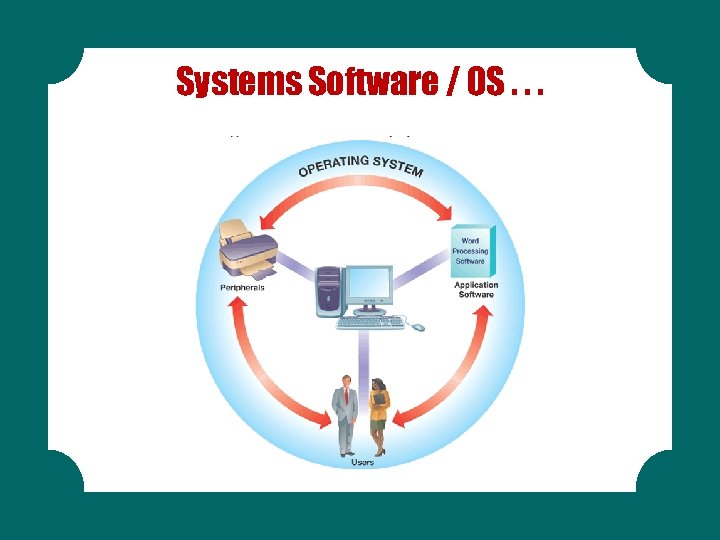
Systems Software / OS. . .
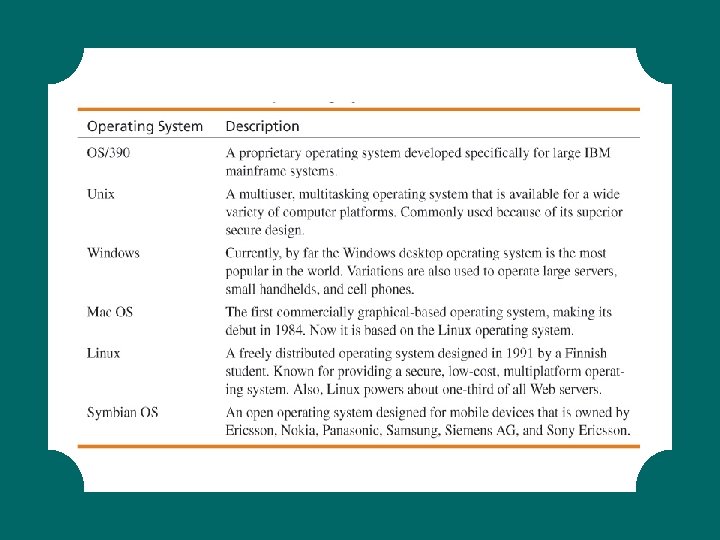
Common Operating Systems
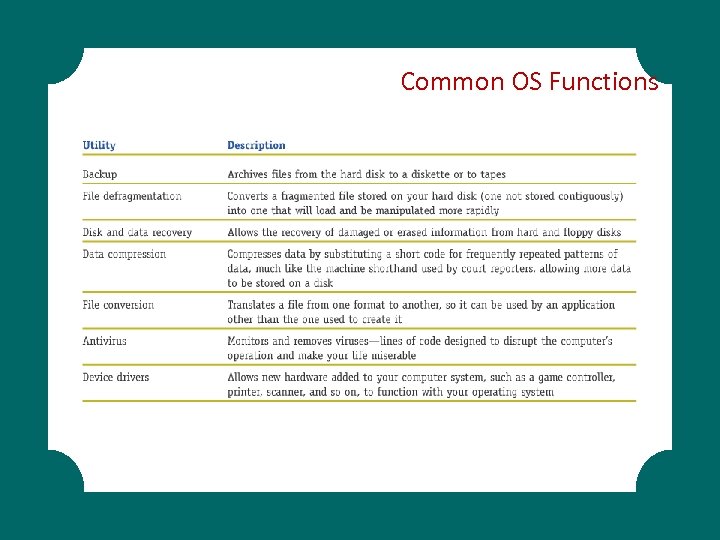
Common OS Functions

UTILITY SOFTWARE Types of utility software § Crash-proof § Disk image § Disk optimization § Encrypt data § File and data recovery § Text protect § Preventative security § Spyware § Uninstaller

Types of Utility Software Crash-proof - Helps save information if a computer crashes Disk image for data recovery - Relieves the burden of reinstalling and tweaking scores of applications if a hard drive crashes or becomes irretrievably corrupted Disk optimization - Organizes information on a hard disk in the most efficient way Encrypt data - Protects confidential information from unauthorized eyes. Programs such as Best. Crypt simply and effectively apply one of several powerful encryption schemes to hard drive information. Users unlock the information by entering a password in the Best. Crypt control panel. The program can also secure information on rewritable optical disks or any other storage media that is assigned a drive letter.

File and data recovery - Retrieves accidental deletion of photos or documents in Windows XP by utilities such as Free Undelete, which searches designated hard drive deletion areas for recognizable data. Text protect - In Microsoft Word, prevents users from typing over existing text after accidentally hitting the Insert key. Launch the Insert Toggle Key program, and the PC will beep whenever a user presses the Insert key.

Preventative security - Through programs such as Window Washer, erases file histories, browser cookies, cache contents, and other crumbs that applications and Windows leave on a hard drive. Spyware - Removes any software that employs a user’s Internet connection in the background without the user’s knowledge or explicit permission. Uninstaller - Can remove software that is no longer needed.
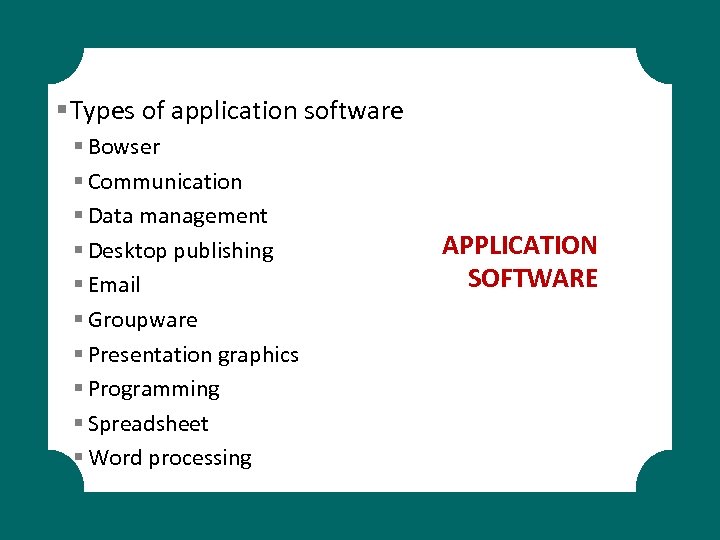
§ Types of application software § Bowser § Communication § Data management § Desktop publishing § Email § Groupware § Presentation graphics § Programming § Spreadsheet § Word processing APPLICATION SOFTWARE

Application Software § § Proprietary application software Contract / licensed software Off-the-shelf application software Package & personal productivity tools

Customized Application Software § Software developed “in-house” § Advantages: § Customizability § Problem specificity
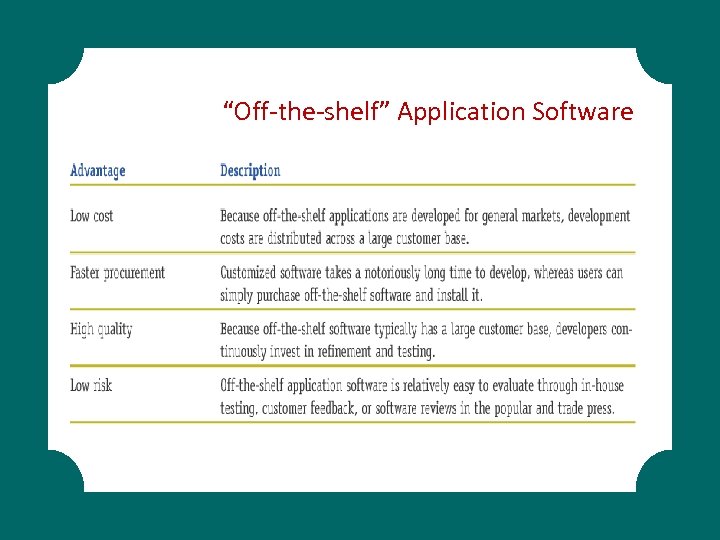
“Off-the-shelf” Application Software

§ A special class of software that includes operating systems, application software, and programming languages in which the source code (the actual program code) is freely available to the general public for use and/or modification § Popular Open Source Applications § Operating systems – Linux § Web browsers – Mozilla § Web servers – Apache § E-mail processing – Sendmail § Internet domain naming service – BIND § Secure connection standard - Open. SSL Open Source Software

Open Source Software Examples

Programming Languages § First-generation language: Machine Language § Second-generation language: Assembly language § Third-generation language: Procedural language § Fourth-generation language: Non-procedural language § Visual programming languages
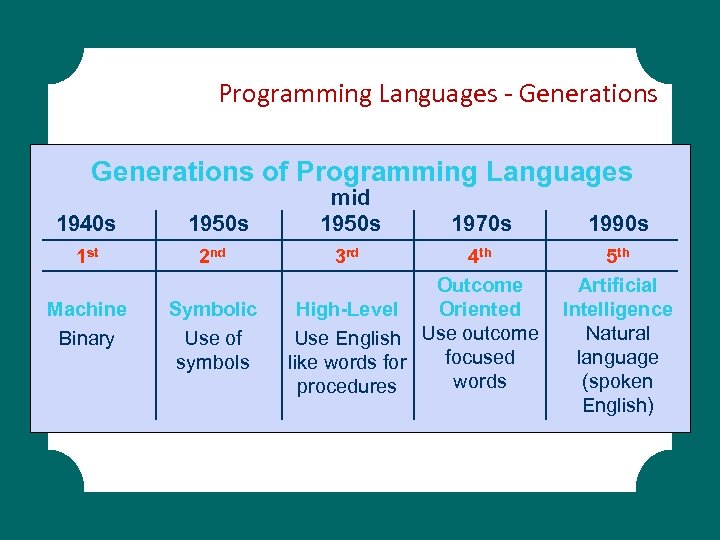
Programming Languages - Generations of Programming Languages 1940 s 1950 s mid 1950 s 1 st 2 nd 3 rd Machine Binary Symbolic Use of symbols 1970 s 4 th Outcome High-Level Oriented Use English Use outcome focused like words for words procedures 1990 s 5 th Artificial Intelligence Natural language (spoken English)
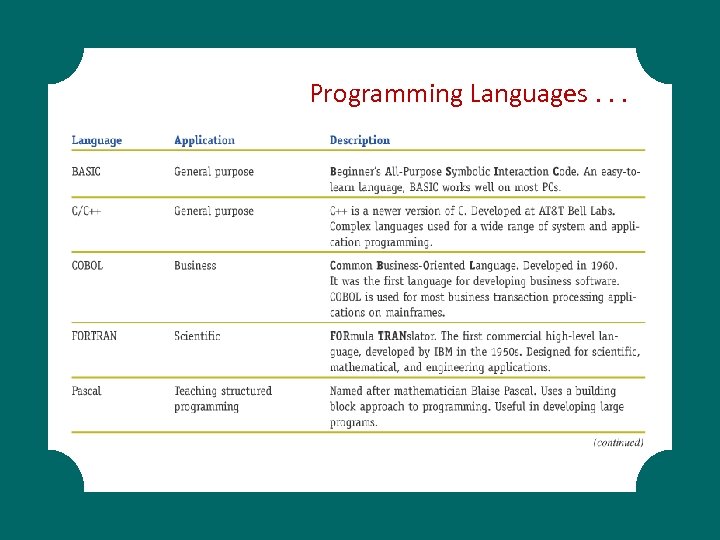
Programming Languages. . .

Programming Languages. . .

§ Compilers and Interpreters § Procedural Programming Languages: § Fortran, COBOL, BASIC, C § Object-oriented Programming Languages § C++, C# § Visual Languages § (with Toolbox, drag and drop objects) § Web Development Languages Programming Languages. . .
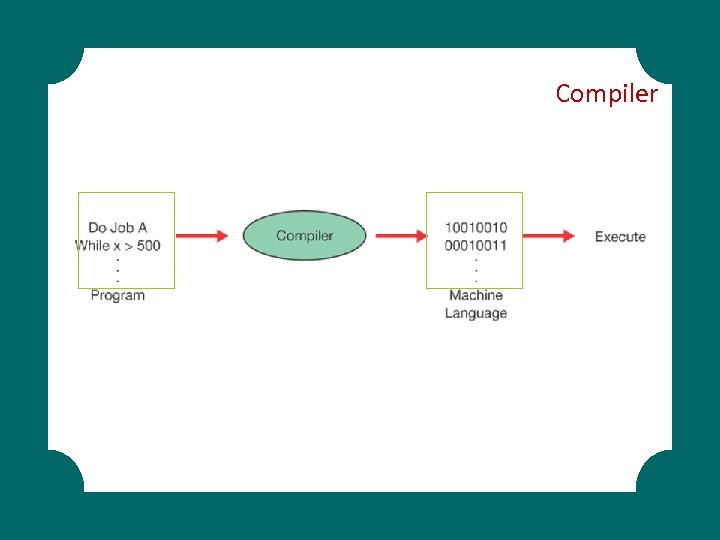
Compiler
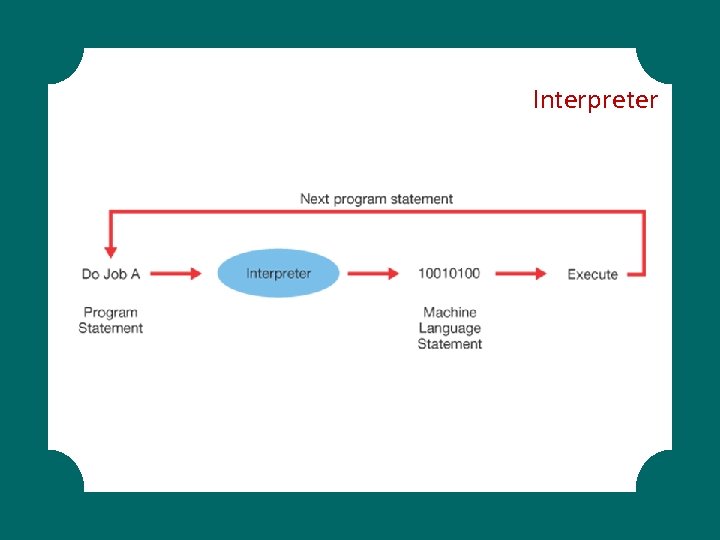
Interpreter

Hypertext Markup Language and Extensible Markup Language § § § Hypertext Hyperlinks Hypertext document Hypertext markup language (HTML) Extensible markup language (XML)
Interfaces: Command vs. GUI § Command-based interface § Menu interface (list of options) § Graphical user interface (GUI)

Strategic Software Issues § § § Software defects Software evaluation and selection Software licensing Open systems Open source software

f689ebe70f4ee4e8d390841ead8b26f9.ppt