e0679a8b45b74e1c6128b78585e01695.ppt
- Количество слайдов: 163
 INFORMATION WARFARE Part 2: Cases Advanced Course in Engineering 2005 Cyber Security Boot Camp Air Force Research Laboratory Information Directorate, Rome, NY M. E. Kabay, Ph. D, CISSP Assoc. Prof. Information Assurance Program Direction, MSIA Division of Business & Management, Norwich University Northfield, Vermont mailto: mkabay@norwich. edu V: 802. 479. 7937 1 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
INFORMATION WARFARE Part 2: Cases Advanced Course in Engineering 2005 Cyber Security Boot Camp Air Force Research Laboratory Information Directorate, Rome, NY M. E. Kabay, Ph. D, CISSP Assoc. Prof. Information Assurance Program Direction, MSIA Division of Business & Management, Norwich University Northfield, Vermont mailto: mkabay@norwich. edu V: 802. 479. 7937 1 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Topics Ø 08: 00 -08: 15 Introductions & Overview Ø 08: 30 -09: 00 Fundamental Concepts Ø 09: 05 -11: 55 Case Histories Ø 13: 15 -15: 15 INFOWAR Theory Ø 15: 30 -16: 00 Project Assignments 2 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Topics Ø 08: 00 -08: 15 Introductions & Overview Ø 08: 30 -09: 00 Fundamental Concepts Ø 09: 05 -11: 55 Case Histories Ø 13: 15 -15: 15 INFOWAR Theory Ø 15: 30 -16: 00 Project Assignments 2 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Examples of INFOSEC Breaches and Failures Ø Electronic infrastructure growing in importance Ø Must expand conception of warfare in the age of ubiquitous computing Ø Cases intended to stimulate your imagination Ø Spans last decade of developments to provide wide range of examples Ø Provide ideas for your INFOWAR attack/defense projects 3 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Examples of INFOSEC Breaches and Failures Ø Electronic infrastructure growing in importance Ø Must expand conception of warfare in the age of ubiquitous computing Ø Cases intended to stimulate your imagination Ø Spans last decade of developments to provide wide range of examples Ø Provide ideas for your INFOWAR attack/defense projects 3 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 4 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 4 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud q. Psyops Ø Denial of Service (Do. S) 5 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud q. Psyops Ø Denial of Service (Do. S) 5 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Breaches of Confidentiality: GAO vs IRS GAO blasts IRS (1997. 04) Ø IRS “misplaced” 6, 400 computer records Ø 1, 515 cases unauthorized browsing in 1994 -5 Ø Only 23 employees fired for browsing Ø Sen. John Glenn introduced bill qestablish criminal penalties qagainst unauthorized access qby employees 6 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Breaches of Confidentiality: GAO vs IRS GAO blasts IRS (1997. 04) Ø IRS “misplaced” 6, 400 computer records Ø 1, 515 cases unauthorized browsing in 1994 -5 Ø Only 23 employees fired for browsing Ø Sen. John Glenn introduced bill qestablish criminal penalties qagainst unauthorized access qby employees 6 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Eavesdropping: Gingrich Ø 1997. 01 -- Newt Gingrich cellular call monitored q. FL couple using police scanner qsent tapes to Democrats Ø 1997. 04 -- Gingrich wiretappers charged q. John & Alice Martin qfederal charges qfines up to $10, 000 Ø MORAL qdon’t talk about sensitive stuff on cell phones without activating encryption 7 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Eavesdropping: Gingrich Ø 1997. 01 -- Newt Gingrich cellular call monitored q. FL couple using police scanner qsent tapes to Democrats Ø 1997. 04 -- Gingrich wiretappers charged q. John & Alice Martin qfederal charges qfines up to $10, 000 Ø MORAL qdon’t talk about sensitive stuff on cell phones without activating encryption 7 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Eavesdropping: Easy Ø 1997. 02 -- Billy Tauzin (R, LA) demonstrated scanner modifications to Subcommittee qmodified off-the-shelf scanner in 2 minutes qeavesdropped on cell-phone call Ø 1997. 02 -- French high court examined unauthorized wire-tapping by government anti -terrorism unit 8 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Eavesdropping: Easy Ø 1997. 02 -- Billy Tauzin (R, LA) demonstrated scanner modifications to Subcommittee qmodified off-the-shelf scanner in 2 minutes qeavesdropped on cell-phone call Ø 1997. 02 -- French high court examined unauthorized wire-tapping by government anti -terrorism unit 8 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Eavesdropping: AT&T Insider Job AT&T World. Net Sniffer Scandal (1997. 05) Ø Reports that World. Net subject to packet sniffing from external site qcaptured user IDs and passwords qmuch fuss and bother Ø Hoax qdiscovered misrepresentation qpacket sniffer was on internal LANs, not on TCP/IP circuits 9 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Eavesdropping: AT&T Insider Job AT&T World. Net Sniffer Scandal (1997. 05) Ø Reports that World. Net subject to packet sniffing from external site qcaptured user IDs and passwords qmuch fuss and bother Ø Hoax qdiscovered misrepresentation qpacket sniffer was on internal LANs, not on TCP/IP circuits 9 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Eavesdropping: NJ Pagers Ø Pager eavedropping in NJ (1997. 08) Ø Content sold to news organizations Ø Senior New York City officials qmayor's office qtop police and fire department officers Ø Authorities used pagers believing them more secure than phones Ø Nov: Steven Gessman, Vinnie Martin and Robert Gessman qadmitted illegal eavesdropping qscheduled for sentencing on March 3, 1998 10 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Eavesdropping: NJ Pagers Ø Pager eavedropping in NJ (1997. 08) Ø Content sold to news organizations Ø Senior New York City officials qmayor's office qtop police and fire department officers Ø Authorities used pagers believing them more secure than phones Ø Nov: Steven Gessman, Vinnie Martin and Robert Gessman qadmitted illegal eavesdropping qscheduled for sentencing on March 3, 1998 10 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Eavesdropping: White House pagers (1997. 09) Ø Hacker posted transcripts of WH pager messages on Net Ø Include sensitive information about First Family movements Ø Traffic analysis dangerous qflurry of messages before President (etc. ) move from one site to another qproblem even if message encrypted 11 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Eavesdropping: White House pagers (1997. 09) Ø Hacker posted transcripts of WH pager messages on Net Ø Include sensitive information about First Family movements Ø Traffic analysis dangerous qflurry of messages before President (etc. ) move from one site to another qproblem even if message encrypted 11 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Eavesdropping: Wireless Phone Blabbermouth criminals arrested (1998. 06) Ø Saratoga County, NY woman qoverhead crooks on wireless phone qplanned to beat and rob old woman qreported to police Ø Police arrested three men and charged them with conspiracy Ø Woman refused to reveal her identity qillegal to intercept wireless communications qillegal to communicate content 12 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Eavesdropping: Wireless Phone Blabbermouth criminals arrested (1998. 06) Ø Saratoga County, NY woman qoverhead crooks on wireless phone qplanned to beat and rob old woman qreported to police Ø Police arrested three men and charged them with conspiracy Ø Woman refused to reveal her identity qillegal to intercept wireless communications qillegal to communicate content 12 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Man-in-the-Middle: Pager Teenager intercepts doctor’s pages (2001. 01) Ø Inova Fairfax Hospital, VA Ø Teenager forwarded physician’s number to his own pager Ø Responded to nurses’ requests with fake medical instructions q. Blood tests q. Administer oxygen q. About a dozen orders in all 13 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Man-in-the-Middle: Pager Teenager intercepts doctor’s pages (2001. 01) Ø Inova Fairfax Hospital, VA Ø Teenager forwarded physician’s number to his own pager Ø Responded to nurses’ requests with fake medical instructions q. Blood tests q. Administer oxygen q. About a dozen orders in all 13 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Potential Connectivity: Health. South Digital Hospital? (2001. 03) Ø Health. South hospitals to have Internet connections at each bed Ø Doctors and nurses can access and update patient records 14 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Potential Connectivity: Health. South Digital Hospital? (2001. 03) Ø Health. South hospitals to have Internet connections at each bed Ø Doctors and nurses can access and update patient records 14 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Leakage: Spy Data on TV Live broadcasts from spy satellites on TV (2002. 06) Ø European satellite TV viewers can watch live broadcasts of peacekeeping and anti-terrorist operations q. US spyplanes over the Balkans Ø Broadcast through a Telstar 11 satellite over Brazil Ø US spyplane broadcasts not encrypted Ø Anyone in Europe with satellite TV receiver can watch surveillance operations Ø Satellite feeds connected to the Internet 15 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Leakage: Spy Data on TV Live broadcasts from spy satellites on TV (2002. 06) Ø European satellite TV viewers can watch live broadcasts of peacekeeping and anti-terrorist operations q. US spyplanes over the Balkans Ø Broadcast through a Telstar 11 satellite over Brazil Ø US spyplane broadcasts not encrypted Ø Anyone in Europe with satellite TV receiver can watch surveillance operations Ø Satellite feeds connected to the Internet 15 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 16 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 16 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Davy Intl vs VA Technologie AG Dow Jones News Service (1996. 06) Ø UK Davy Intl q. Lost lucrative Saudi-Arabian contract qalleged industrial espionage Ø Sued Voest-Alpine Industrial Services q. UK branch of Austrian firm VA Tecnologie AG Ø Obtained court order for seizure of evidence q. Received 2, 000 pages & disks with info belonging to Davy Intl from VA Technologie 17 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Davy Intl vs VA Technologie AG Dow Jones News Service (1996. 06) Ø UK Davy Intl q. Lost lucrative Saudi-Arabian contract qalleged industrial espionage Ø Sued Voest-Alpine Industrial Services q. UK branch of Austrian firm VA Tecnologie AG Ø Obtained court order for seizure of evidence q. Received 2, 000 pages & disks with info belonging to Davy Intl from VA Technologie 17 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Boehringer Mannheim Corp vs. Lifescan 1996. 06 Ø US subsidiary of Boehringer Mannheim Corp (pharmaceuticals) vs Johnson & Johnson unit Ø Accused Lifescan Inc of encouraging industrial espionage for 18 months q. Supposedly stole prototype blood sugar monitor q. Allegedly presented "Inspector Clouseau" and "Columbo" awards to employees for stealing secret info from BMC Ø Lifescan countersued with equivalent accusations q. BMC had Lifescan Competitive Kill Team q. Hired private detectives to spy on Lifescan 18 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Boehringer Mannheim Corp vs. Lifescan 1996. 06 Ø US subsidiary of Boehringer Mannheim Corp (pharmaceuticals) vs Johnson & Johnson unit Ø Accused Lifescan Inc of encouraging industrial espionage for 18 months q. Supposedly stole prototype blood sugar monitor q. Allegedly presented "Inspector Clouseau" and "Columbo" awards to employees for stealing secret info from BMC Ø Lifescan countersued with equivalent accusations q. BMC had Lifescan Competitive Kill Team q. Hired private detectives to spy on Lifescan 18 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Intel & AMD 1996. 06 -- Reuters Ø Argentinian national Guillermo Gaede Ø Admitted he sent videotapes about Intel chipmanufacturing to AMD Ø AMD immediately notified police Ø Industrial spy sentenced to 33 months in federal prison 19 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Intel & AMD 1996. 06 -- Reuters Ø Argentinian national Guillermo Gaede Ø Admitted he sent videotapes about Intel chipmanufacturing to AMD Ø AMD immediately notified police Ø Industrial spy sentenced to 33 months in federal prison 19 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Espionage: CIA vs Europe 1996. 08 -- Sunday Times, RISKS 18. 30 Ø US CIA allegedly hacking into European Parliament & European Commission computers Ø Stealing economic and political secrets Ø Supposedly used info in GATT 20 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Espionage: CIA vs Europe 1996. 08 -- Sunday Times, RISKS 18. 30 Ø US CIA allegedly hacking into European Parliament & European Commission computers Ø Stealing economic and political secrets Ø Supposedly used info in GATT 20 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Interactive Television Technologies 1996. 08 -- PR Newswire Ø 4 yr R&D project for TV interface to Net Ø Top secret -- moving to high-security facility Ø Before move, thieves stole computers and storage media Ø Estimated $250 M value Ø Looks like industrial espionage Ø Reconstructed data from backups Ø But patenting prematurely to protect property 21 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Interactive Television Technologies 1996. 08 -- PR Newswire Ø 4 yr R&D project for TV interface to Net Ø Top secret -- moving to high-security facility Ø Before move, thieves stole computers and storage media Ø Estimated $250 M value Ø Looks like industrial espionage Ø Reconstructed data from backups Ø But patenting prematurely to protect property 21 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Owens Corning & PPG & Owens Corning (1996. 12) Ø Major manufacturers & competitors Ø Cleaning contractor stole operational documents at night from PPG Ø Offered to Owens Corning for $1, 000 Ø Some years ago PPG had informed OC of similar scam — also resulted in arrests Ø Owens Corning notified PPG Ø Informed FBI, worked with LEOs to build case Ø Perpetrator arrested by FBI 22 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Owens Corning & PPG & Owens Corning (1996. 12) Ø Major manufacturers & competitors Ø Cleaning contractor stole operational documents at night from PPG Ø Offered to Owens Corning for $1, 000 Ø Some years ago PPG had informed OC of similar scam — also resulted in arrests Ø Owens Corning notified PPG Ø Informed FBI, worked with LEOs to build case Ø Perpetrator arrested by FBI 22 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: GM Opel vs VW 1997. 01 — news wires Ø GM alleged industrial espionage (Oct 96) qformer purchasing chief, Jose Ignacio Lopez de Arriortua qleft GM to join VW in 1993 qallegedly stole 3 crates confidential documents Ø GM claimed stolen documents included highly confidential info qfuture product plans, parts prices & manufacturing techniques qunfairly allowed VW to reduce costs qcaused unspecified financial damage Ø Settled out of court (1997. 01) 23 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: GM Opel vs VW 1997. 01 — news wires Ø GM alleged industrial espionage (Oct 96) qformer purchasing chief, Jose Ignacio Lopez de Arriortua qleft GM to join VW in 1993 qallegedly stole 3 crates confidential documents Ø GM claimed stolen documents included highly confidential info qfuture product plans, parts prices & manufacturing techniques qunfairly allowed VW to reduce costs qcaused unspecified financial damage Ø Settled out of court (1997. 01) 23 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Bristol-Myers-Squibb Taiwanese arrested for espionage (1997. 06) Ø Attempted to bribe Bristol-Myers Squibb scientist Ø Wanted production details for Taxol qovarian cancer drug qworth $B Ø Employee reported to employer; then FBI arranged sting Ø Both agents arrested Ø Face 35 years and 10 years in jail, respectively 25 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Bristol-Myers-Squibb Taiwanese arrested for espionage (1997. 06) Ø Attempted to bribe Bristol-Myers Squibb scientist Ø Wanted production details for Taxol qovarian cancer drug qworth $B Ø Employee reported to employer; then FBI arranged sting Ø Both agents arrested Ø Face 35 years and 10 years in jail, respectively 25 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: DEC/INTEL Battle of the Giants: DEC vs Intel Ø 1997. 05 — DEC sues Intel, claiming theft of chip designs Ø 1997. 05 — Intel sues DEC, demanding return of proprietary information Ø 1997. 06 — DEC demands former employee now at Intel remain silent about proprietary DEC information Ø 1997. 07 — DEC accuses Intel of anti-trust Ø 1997. 10 — out of court settlement 26 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: DEC/INTEL Battle of the Giants: DEC vs Intel Ø 1997. 05 — DEC sues Intel, claiming theft of chip designs Ø 1997. 05 — Intel sues DEC, demanding return of proprietary information Ø 1997. 06 — DEC demands former employee now at Intel remain silent about proprietary DEC information Ø 1997. 07 — DEC accuses Intel of anti-trust Ø 1997. 10 — out of court settlement 26 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Law Firm Legal firm accused of espionage (1999. 11) Ø 1 st lawsuit involving industrial espionage by lawyers Ø Moore Publishing (Wilmington DE) sued Steptoe & Johnson (Washington DC) qallegedly breaking into computer systems 750 X qstolen user-ID & password Ø Systematic cyberwar qmisinformation posted on newsgroups q. Hot. Mail account traced to defendants Ø Damages at least $10 M 28 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Law Firm Legal firm accused of espionage (1999. 11) Ø 1 st lawsuit involving industrial espionage by lawyers Ø Moore Publishing (Wilmington DE) sued Steptoe & Johnson (Washington DC) qallegedly breaking into computer systems 750 X qstolen user-ID & password Ø Systematic cyberwar qmisinformation posted on newsgroups q. Hot. Mail account traced to defendants Ø Damages at least $10 M 28 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: France vs UK French Intelligence Service Targets UK Businesses (2000. 01) Ø James Clark writing in Sunday Times of London Ø Spent $M on satellite technology for listening stations & upgraded SIGINT Ø Aimed at British defense firms, petroleum companies and other commercial targets Ø Surveillance includes GSM phones Ø UK officials warned not to discuss sensitive issues on mobile phones 29 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: France vs UK French Intelligence Service Targets UK Businesses (2000. 01) Ø James Clark writing in Sunday Times of London Ø Spent $M on satellite technology for listening stations & upgraded SIGINT Ø Aimed at British defense firms, petroleum companies and other commercial targets Ø Surveillance includes GSM phones Ø UK officials warned not to discuss sensitive issues on mobile phones 29 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Oracle vs Microsoft Oracle Dumpster®-Dives vs MS (2000. 06) Ø Bill Gates complained about Dumpster® Diving of trash of organizations supporting MS in antitrust case Ø CEO Larry Ellison of Oracle admitted using private detectives to go through trash of q. Association for Competitive Technology q. Independent Institute q. Citizens for a Sound Economy Ø Suggested he would happily ship Oracle trash to MS in spirit of full disclosure. 30 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Oracle vs Microsoft Oracle Dumpster®-Dives vs MS (2000. 06) Ø Bill Gates complained about Dumpster® Diving of trash of organizations supporting MS in antitrust case Ø CEO Larry Ellison of Oracle admitted using private detectives to go through trash of q. Association for Competitive Technology q. Independent Institute q. Citizens for a Sound Economy Ø Suggested he would happily ship Oracle trash to MS in spirit of full disclosure. 30 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Echelon EU Parliament attacks Echelon (2000. 07) Ø Formed temporary committee to investigate spy network Ø Suspicions that Echelon used to intercept conversations of European businesses Ø Information might be given to competitors from Echelon operators q. US, Canada, Australia, New Zealand Ø In 2001. 05, report recommend more use of encryption to defeat Echelon 31 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Echelon EU Parliament attacks Echelon (2000. 07) Ø Formed temporary committee to investigate spy network Ø Suspicions that Echelon used to intercept conversations of European businesses Ø Information might be given to competitors from Echelon operators q. US, Canada, Australia, New Zealand Ø In 2001. 05, report recommend more use of encryption to defeat Echelon 31 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Datang vs Lucent et al. Chinese nationals arrested (2001. 05) Ø Two citizens of PRC worked at Lucent q. Highly respected scientists q. Worked with a Chinese business partner Ø Sent proprietary information to Beijing’s Datang Telecom Technology Co. q. Pathstar Access Server -- “Crown jewel” Ø Arrested by FBI q. Conspiracy to commit wire fraud q. Max penalty 5 years in prison & $250 K fine Ø In 2002. 04, charged with additional espionage q. Theft from Telenetworks, Net. Plane Systems, Hughes Software Systems, and Ziatech 32 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Datang vs Lucent et al. Chinese nationals arrested (2001. 05) Ø Two citizens of PRC worked at Lucent q. Highly respected scientists q. Worked with a Chinese business partner Ø Sent proprietary information to Beijing’s Datang Telecom Technology Co. q. Pathstar Access Server -- “Crown jewel” Ø Arrested by FBI q. Conspiracy to commit wire fraud q. Max penalty 5 years in prison & $250 K fine Ø In 2002. 04, charged with additional espionage q. Theft from Telenetworks, Net. Plane Systems, Hughes Software Systems, and Ziatech 32 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Short Notes Ø 2001. 07: EMC sues former employees for data theft to help competitor Network Appliance Ø 2002. 09: 32 -year old Chinese national working for (PRC) China National Petroleum Corp arrested for trying to steal seismic-imaging software from 3 DGeo of Mountain View, CA Ø 2003. 05: 3 charged in Ericsson spy case in Sweden. Sold secrets to Russian intelligence agent. Ø 2005. 01: IBM selling PC business to PRC Lenovo Group for $1. 75 B – US Ctee on Foreign Investments investigating implications. 33 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Short Notes Ø 2001. 07: EMC sues former employees for data theft to help competitor Network Appliance Ø 2002. 09: 32 -year old Chinese national working for (PRC) China National Petroleum Corp arrested for trying to steal seismic-imaging software from 3 DGeo of Mountain View, CA Ø 2003. 05: 3 charged in Ericsson spy case in Sweden. Sold secrets to Russian intelligence agent. Ø 2005. 01: IBM selling PC business to PRC Lenovo Group for $1. 75 B – US Ctee on Foreign Investments investigating implications. 33 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Scandal in Israel Trojan Horse scandal rocks Israel (2005. 06) Ø Author Amon Jackont target of attacks q. Parts of current novel MS posted on Web q. Attempted theft from bank account Ø Police found keystroke logger on Jackont’s computer q. Suspicion fell on stepdaughter’s ex-husband, Michael Haephrati Ø Discovered Haephrati apparently installed Trojan programs on big industrial firms’ computers (HP, Ace Hardware…) q. Confidential info sent to server in London q. Allegedly selling secrets to other companies q. Dozens of arrests at highest levels (CEOs) 34 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Scandal in Israel Trojan Horse scandal rocks Israel (2005. 06) Ø Author Amon Jackont target of attacks q. Parts of current novel MS posted on Web q. Attempted theft from bank account Ø Police found keystroke logger on Jackont’s computer q. Suspicion fell on stepdaughter’s ex-husband, Michael Haephrati Ø Discovered Haephrati apparently installed Trojan programs on big industrial firms’ computers (HP, Ace Hardware…) q. Confidential info sent to server in London q. Allegedly selling secrets to other companies q. Dozens of arrests at highest levels (CEOs) 34 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Industrial Espionage: Interloc vs Amazon Lawsuit over intercepted e-mail (1999. 11) Ø Interloc admitted intercepting & copying 4, 000 e-mail messages sent to Amazon. com q. Went through own ISP Valinet q. To gain competitive advantage against Amazon? Ø Interloc's business managers denied any wrongful intention qfailed to explain why they copied e-mail Ø Alibris company bought Interloc & paid $250 K fine on behalf of their new acquisition q. This is called a failure of due diligence in mergers and acquisitions practice 35 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Industrial Espionage: Interloc vs Amazon Lawsuit over intercepted e-mail (1999. 11) Ø Interloc admitted intercepting & copying 4, 000 e-mail messages sent to Amazon. com q. Went through own ISP Valinet q. To gain competitive advantage against Amazon? Ø Interloc's business managers denied any wrongful intention qfailed to explain why they copied e-mail Ø Alibris company bought Interloc & paid $250 K fine on behalf of their new acquisition q. This is called a failure of due diligence in mergers and acquisitions practice 35 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 36 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 36 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Library Systems June 96 — NCSA IS/Recon Ø Public and corporate library systems being used to train apprentice criminal hackers Ø May also be used by more experienced criminal hackers Ø Isolate library network from rest of network 37 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Library Systems June 96 — NCSA IS/Recon Ø Public and corporate library systems being used to train apprentice criminal hackers Ø May also be used by more experienced criminal hackers Ø Isolate library network from rest of network 37 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: San Francisco High Schoolersvs PBX July 96 — RISKS 18. 26 Ø High-school students in the San Francisco area q. Broke into local manufacturing firm PBX Ø Attacked voice-mail qerased information qchanged passwords qcreated new accounts for own use qcrashed system through overuse Ø Company spent $40, 000 on tech support 38 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: San Francisco High Schoolersvs PBX July 96 — RISKS 18. 26 Ø High-school students in the San Francisco area q. Broke into local manufacturing firm PBX Ø Attacked voice-mail qerased information qchanged passwords qcreated new accounts for own use qcrashed system through overuse Ø Company spent $40, 000 on tech support 38 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Scotland Yard PBX Aug 96 — Reuters Ø Scotland Yard's PBX hacked by phone phreaks Ø U$1. 5 M of fraudulent calls Ø Used direct inward services access (DISA) Ø Moral qdisable DISA qno limit on liability when using DISA quse phone service cards instead qlimit on liability if card stolen or account abused 39 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Scotland Yard PBX Aug 96 — Reuters Ø Scotland Yard's PBX hacked by phone phreaks Ø U$1. 5 M of fraudulent calls Ø Used direct inward services access (DISA) Ø Moral qdisable DISA qno limit on liability when using DISA quse phone service cards instead qlimit on liability if card stolen or account abused 39 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Mitnick Sept 96 — AP Ø Kevin Mitnick indicted in Los Angeles Ø 25 count indictment q stealing software q damaging computers at University of Southern California q using passwords without authorization q using stolen cellular phone codes Ø Readings about the Mitnick case q Goodell, J. (1996). The Cyberthief and the Samurai: The True Story of Kevin Mitnick—and the Man Who Hunted Him Down. Dell (New York). ISBN 0 -440 -22205 -2. xix + 328. q Hafner, K. & J. Markoff (1991). Cyberpunk: Outlaws and Hackers on the Computer Frontier. Touchstone Books, Simon & Schuster (New York). ISBN 0 -671 -77879 -X. 368. Index. q Littman, J. (1996). The Fugitive Game: Online with Kevin Mitnick—The Inside Story of the Great Cyberchase. Little, Brown and Company (Boston). ISBN 0 -316 -5258 -7. x + 383. q Shimomura, T. & J. Markoff (1996). Takedown: The Pursuit and Capture of Kevin Mitnick, America's Most Wanted Computer Outlaw—by the Man Who Did It. Hyperion (New York). ISBN 0 -7868 -6210 -6. xii + 324. Index. 40 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Mitnick Sept 96 — AP Ø Kevin Mitnick indicted in Los Angeles Ø 25 count indictment q stealing software q damaging computers at University of Southern California q using passwords without authorization q using stolen cellular phone codes Ø Readings about the Mitnick case q Goodell, J. (1996). The Cyberthief and the Samurai: The True Story of Kevin Mitnick—and the Man Who Hunted Him Down. Dell (New York). ISBN 0 -440 -22205 -2. xix + 328. q Hafner, K. & J. Markoff (1991). Cyberpunk: Outlaws and Hackers on the Computer Frontier. Touchstone Books, Simon & Schuster (New York). ISBN 0 -671 -77879 -X. 368. Index. q Littman, J. (1996). The Fugitive Game: Online with Kevin Mitnick—The Inside Story of the Great Cyberchase. Little, Brown and Company (Boston). ISBN 0 -316 -5258 -7. x + 383. q Shimomura, T. & J. Markoff (1996). Takedown: The Pursuit and Capture of Kevin Mitnick, America's Most Wanted Computer Outlaw—by the Man Who Did It. Hyperion (New York). ISBN 0 -7868 -6210 -6. xii + 324. Index. 40 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Danish Criminal Hackers Dec 96 — AP Ø 6 criminal hackers from Denmark Ø Attacked Pentagon & business computers Ø Sentenced to minor jail terms Ø Ordered to pay fines, perform community service Ø One sentenced to 90 days in jail, second to 40 days Ø Defense lawyers: criminals had “done the hacking victims a favor by exposing the vulnerability of their computer systems. ” 41 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Danish Criminal Hackers Dec 96 — AP Ø 6 criminal hackers from Denmark Ø Attacked Pentagon & business computers Ø Sentenced to minor jail terms Ø Ordered to pay fines, perform community service Ø One sentenced to 90 days in jail, second to 40 days Ø Defense lawyers: criminals had “done the hacking victims a favor by exposing the vulnerability of their computer systems. ” 41 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Ex-Employees 1997. 02 -- Computer Sciences Corporation Ø Warn that many organizations attacked by exemployees Ø Ex-employees of outsourcing firms a threat Ø Cited example of Big Six firm where exemployee used e-mail and voice-mail for one year after termination Ø Recommend use of single-logon system Ø Token-based authentication also useful in centralizing control of I&A 42 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Ex-Employees 1997. 02 -- Computer Sciences Corporation Ø Warn that many organizations attacked by exemployees Ø Ex-employees of outsourcing firms a threat Ø Cited example of Big Six firm where exemployee used e-mail and voice-mail for one year after termination Ø Recommend use of single-logon system Ø Token-based authentication also useful in centralizing control of I&A 42 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Croatian Hackers Attack Pentagon 1997. 02 -- RISKS, Reuters Ø Teenagers in Croatia broke into US military systems Ø Pentagon asked Croatian police for cooperation Ø Arrested kids, searched homes Ø Confiscated computer equipment Ø Preliminary estimates of losses running in $500 K range 43 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Croatian Hackers Attack Pentagon 1997. 02 -- RISKS, Reuters Ø Teenagers in Croatia broke into US military systems Ø Pentagon asked Croatian police for cooperation Ø Arrested kids, searched homes Ø Confiscated computer equipment Ø Preliminary estimates of losses running in $500 K range 43 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: DISA Report 1997. 03 — EDUPAGE Ø Info. War Division of Defense Information Systems Agency of US Ø Retested 15, 000 Pentagon computers qhad warned system managers of vulnerabilities in previous audit Ø 90% of systems were still vulnerable Ø Recommended emphasizing response (immediate shutdown) instead of focusing solely on preventing penetrations 44 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: DISA Report 1997. 03 — EDUPAGE Ø Info. War Division of Defense Information Systems Agency of US Ø Retested 15, 000 Pentagon computers qhad warned system managers of vulnerabilities in previous audit Ø 90% of systems were still vulnerable Ø Recommended emphasizing response (immediate shutdown) instead of focusing solely on preventing penetrations 44 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Cloverdale Two Ø Multiple assaults on military & research sites — 1998. 01 q. Attacks on 11 military computer systems qseveral universities qfederal laboratories Ø “Most organized and systematic [attack] the Pentagon has seen to date. . ” BUT. . . Ø. . . Actually teenaged criminal hackers q. Suburbs north of San Francisco q. Caught with cooperation of ISP — 1998. 02 qprovided facilities for FBI monitoring Ø Punished by 3 -year exclusion from computing by themselves 45 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Cloverdale Two Ø Multiple assaults on military & research sites — 1998. 01 q. Attacks on 11 military computer systems qseveral universities qfederal laboratories Ø “Most organized and systematic [attack] the Pentagon has seen to date. . ” BUT. . . Ø. . . Actually teenaged criminal hackers q. Suburbs north of San Francisco q. Caught with cooperation of ISP — 1998. 02 qprovided facilities for FBI monitoring Ø Punished by 3 -year exclusion from computing by themselves 45 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Hungarian ISP 1997. 03 -- RISKS Ø Hungary's main ISP, MATAV Ø Assigned 1, 200 IDs whose passwords were the billing ID itself Ø Published list of these IDs -- as a warning to change the passwords Ø USENET postings announced the breach of security 46 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Hungarian ISP 1997. 03 -- RISKS Ø Hungary's main ISP, MATAV Ø Assigned 1, 200 IDs whose passwords were the billing ID itself Ø Published list of these IDs -- as a warning to change the passwords Ø USENET postings announced the breach of security 46 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Netherlands Hackers vs Pentagon? 1997. 03 -- EDUPAGE Ø Criminal hackers penetrated Pentagon systems during Gulf War Ø Claimed that hackers approached Iraqi intelligence with stolen information Ø Iraqis said to have rejected info, fearing a disinformation campaign Ø Rop Gongrijp of Hac. Tic qextremely skeptical of whole story qtraces what he thinks is an urban myth to an article that never claimed anything about Iraqis at all 47 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Netherlands Hackers vs Pentagon? 1997. 03 -- EDUPAGE Ø Criminal hackers penetrated Pentagon systems during Gulf War Ø Claimed that hackers approached Iraqi intelligence with stolen information Ø Iraqis said to have rejected info, fearing a disinformation campaign Ø Rop Gongrijp of Hac. Tic qextremely skeptical of whole story qtraces what he thinks is an urban myth to an article that never claimed anything about Iraqis at all 47 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Datastream Cowboy Fined UK teenager cracked military computers (1994; trial 1997. 03) Ø Richard Pryce attacked US Air Defense System in 1994 (was 16 years old) Ø Broke into Griffiss AFB, NY Ø Cracked Lockheed network in CA Ø Was described as “#1 threat to US security” in Senate Armed Forces Committee hearings Ø Fined equivalent of $1, 915 Ø Pryce now working hard on getting to play bass fiddle in a London orchestra 48 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Datastream Cowboy Fined UK teenager cracked military computers (1994; trial 1997. 03) Ø Richard Pryce attacked US Air Defense System in 1994 (was 16 years old) Ø Broke into Griffiss AFB, NY Ø Cracked Lockheed network in CA Ø Was described as “#1 threat to US security” in Senate Armed Forces Committee hearings Ø Fined equivalent of $1, 915 Ø Pryce now working hard on getting to play bass fiddle in a London orchestra 48 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Swedish “Demon. Freaker ” Fined a Pittance Phreak placed 60, 000 calls at US telco expense (1996; trial 1997. 05) Ø Racked up $250 K of charges Ø Repeatedly linked US emergency lines to each other, causing havoc Ø Caught by rapid trace while claiming his penis was glued to a wall Ø History of alcohol abuse and glue-sniffing Ø Fined equivalent of $350 Ø Interned in psychiatric institution 49 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Swedish “Demon. Freaker ” Fined a Pittance Phreak placed 60, 000 calls at US telco expense (1996; trial 1997. 05) Ø Racked up $250 K of charges Ø Repeatedly linked US emergency lines to each other, causing havoc Ø Caught by rapid trace while claiming his penis was glued to a wall Ø History of alcohol abuse and glue-sniffing Ø Fined equivalent of $350 Ø Interned in psychiatric institution 49 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Private-School Naughty Boys Brockville teens crack Rip. Net (1997. 06) Ø 16 -year-old A+ student + 4 accomplices Ø Broke into Rip. Net ISP in Brockville, ON Ø Stole 1300 user IDs + passwords Ø Distributed for free access Ø Quickly discovered Ø Rip. Net and police agreed to let posh school handle punishment qringleader out of computer class for 1 year qall have to write essays on what bad boys they were 50 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Private-School Naughty Boys Brockville teens crack Rip. Net (1997. 06) Ø 16 -year-old A+ student + 4 accomplices Ø Broke into Rip. Net ISP in Brockville, ON Ø Stole 1300 user IDs + passwords Ø Distributed for free access Ø Quickly discovered Ø Rip. Net and police agreed to let posh school handle punishment qringleader out of computer class for 1 year qall have to write essays on what bad boys they were 50 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: “Mr Nobody” Cracks Netcom 15 -year-old boasts of exploits to Interactive Week (1997. 06) Ø Cracked PBX in 1995 (age 13) Ø Listened to voice-mail messages qboxes had “Joe” passwords -- same as extension itself (stupid default) Ø Phreak and friends placed long-distance calls at Netcom expense 51 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: “Mr Nobody” Cracks Netcom 15 -year-old boasts of exploits to Interactive Week (1997. 06) Ø Cracked PBX in 1995 (age 13) Ø Listened to voice-mail messages qboxes had “Joe” passwords -- same as extension itself (stupid default) Ø Phreak and friends placed long-distance calls at Netcom expense 51 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: ON 14 -year-old 1997. 09 -- Burlington, ON Ø >500 attempts to penetrate systems qall over North America qevidence of malicious hacking Ø Attacked US military computers qcaused downfall qmilitary tracked him down qcooperated with local police 52 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: ON 14 -year-old 1997. 09 -- Burlington, ON Ø >500 attempts to penetrate systems qall over North America qevidence of malicious hacking Ø Attacked US military computers qcaused downfall qmilitary tracked him down qcooperated with local police 52 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: NTT Hacked Ø Nippon Telephone & Telegraph -- 1997. 10 Ø Stole proprietary programs for software development Ø Used internal ID -- possibly social engineering Ø Had or found number of modem qdid it bypass the firewall? 53 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: NTT Hacked Ø Nippon Telephone & Telegraph -- 1997. 10 Ø Stole proprietary programs for software development Ø Used internal ID -- possibly social engineering Ø Had or found number of modem qdid it bypass the firewall? 53 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Pentration Citibank Hack : 1998. 02 (events started 1994. 07) Ø Vladimir Levin of St Petersburg hacked Citibank computers Ø Conspirator Alexei Lachmanov transferred U$2. 8 M to five Tel Aviv banks Ø Admitted to attempting to withdraw US$940, 000 from those accounts Ø Three other members of the gang pleaded guilty Ø Levin extradited 1997. 09 54 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Pentration Citibank Hack : 1998. 02 (events started 1994. 07) Ø Vladimir Levin of St Petersburg hacked Citibank computers Ø Conspirator Alexei Lachmanov transferred U$2. 8 M to five Tel Aviv banks Ø Admitted to attempting to withdraw US$940, 000 from those accounts Ø Three other members of the gang pleaded guilty Ø Levin extradited 1997. 09 54 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Citibank -- Conclusion 1998. 02 -- Levin sentenced to 3 years, fined Ø Vladimir Levin convicted by NYC court Ø Transferred $12 M in assets from Citibank Ø Crime spotted after first $400 K theft Ø Citibank cooperated with FBI Ø MORAL: report computer crime & help prosecute the criminals 55 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Citibank -- Conclusion 1998. 02 -- Levin sentenced to 3 years, fined Ø Vladimir Levin convicted by NYC court Ø Transferred $12 M in assets from Citibank Ø Crime spotted after first $400 K theft Ø Citibank cooperated with FBI Ø MORAL: report computer crime & help prosecute the criminals 55 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: Voice Mail 1998. 05: Cincinnati Enquirer reporter breaks law Ø Michael Gallagher broke into voice mail of Chiquita Fruits Ø Stories in paper accused Chiquita of illegal activities Ø Reporter fired Ø Enquirer paid q$10 M to Chiquita in damages qpublished front-page apologies 3 days in a row 56 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: Voice Mail 1998. 05: Cincinnati Enquirer reporter breaks law Ø Michael Gallagher broke into voice mail of Chiquita Fruits Ø Stories in paper accused Chiquita of illegal activities Ø Reporter fired Ø Enquirer paid q$10 M to Chiquita in damages qpublished front-page apologies 3 days in a row 56 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: U Colorado U. Colorado student arrested -- 1998. 03 Ø Joshua Gregory Pearson, 18 qcomputer science major Ø Allegedly provided stolen passwords and access codes to Israeli hacker “Heavy Metal” qmay have used packet sniffer qintercepted passwords and access codes Ø Israeli broke into U. CO computer system qalso denial of service qunauthorized programs flooded U. CO email accounts with error messages 58 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: U Colorado U. Colorado student arrested -- 1998. 03 Ø Joshua Gregory Pearson, 18 qcomputer science major Ø Allegedly provided stolen passwords and access codes to Israeli hacker “Heavy Metal” qmay have used packet sniffer qintercepted passwords and access codes Ø Israeli broke into U. CO computer system qalso denial of service qunauthorized programs flooded U. CO email accounts with error messages 58 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: MOD redux New MOD crows about exploits -- 1998. 04 Ø Masters of Downloading instead of Masters of Deception Ø Claimed penetration of US military networks q. DISN (Defense Information Systems Network) q. DEM (DISN Equipment Manager) ücontrols military Global Positioning Satellites (GPS) 59 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: MOD redux New MOD crows about exploits -- 1998. 04 Ø Masters of Downloading instead of Masters of Deception Ø Claimed penetration of US military networks q. DISN (Defense Information Systems Network) q. DEM (DISN Equipment Manager) ücontrols military Global Positioning Satellites (GPS) 59 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: AOL Techs ACLU site on AOL vandalized -- 1998. 05 Ø Intruder simply asked AOL help-desk staffers for a “new” password for Web site control Ø Success may be function of size q 1000 s of staffers qmany new and poorly trained Ø Birthday problem: P{at least one failure} = 1 - (1 -p)n p=probability of one failure and n=number of independent units 60 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: AOL Techs ACLU site on AOL vandalized -- 1998. 05 Ø Intruder simply asked AOL help-desk staffers for a “new” password for Web site control Ø Success may be function of size q 1000 s of staffers qmany new and poorly trained Ø Birthday problem: P{at least one failure} = 1 - (1 -p)n p=probability of one failure and n=number of independent units 60 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: SLAC Attacked Stanford Linear Accelerator Center -- 1998. 06 Ø Intruder logged in with a password qguessed? sniffed? borrowed? qlater posting indicated LAN sniffers qimplies inside job Ø Evidence qnew zero-length file q 50 files accessed Ø Results: SLAC off the Net entire week q 30 people worked overtime qpossible interdiction of foreign logins 61 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: SLAC Attacked Stanford Linear Accelerator Center -- 1998. 06 Ø Intruder logged in with a password qguessed? sniffed? borrowed? qlater posting indicated LAN sniffers qimplies inside job Ø Evidence qnew zero-length file q 50 files accessed Ø Results: SLAC off the Net entire week q 30 people worked overtime qpossible interdiction of foreign logins 61 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: John the Ripper Decryption of password files -- 1998. 08 Ø UC Berkeley Sys Admin qdiscovered someone cracked his password qrunning “John the Ripper” decryption prog qsuccessfully cracked about 48, 000 pws from a list of 186, 126 encrypted passwords Ø Cracker broke into systems at qnoted Silicon Valley company q. Indiana ISP qother UC Berkeley systems, q. Caltech, MIT, and Harvard Ø Used Swedish ISP Telenordia then went through England, Denmark, South Korea 62 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: John the Ripper Decryption of password files -- 1998. 08 Ø UC Berkeley Sys Admin qdiscovered someone cracked his password qrunning “John the Ripper” decryption prog qsuccessfully cracked about 48, 000 pws from a list of 186, 126 encrypted passwords Ø Cracker broke into systems at qnoted Silicon Valley company q. Indiana ISP qother UC Berkeley systems, q. Caltech, MIT, and Harvard Ø Used Swedish ISP Telenordia then went through England, Denmark, South Korea 62 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Automated Shoulder-Surfing (1) Newmarket, ON customers surfed -- 1998. 04 Ø Thieves in cahoots with a gas-station employee qinstalled minicam for debit-card PIN pad Ø Make fake debit cards to pillage accounts qused ATMs at midnight to steal 2 days’ max Ø Total thefts > $100 K Ø Arrested just before a planned expansion to five more gas stations 63 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Automated Shoulder-Surfing (1) Newmarket, ON customers surfed -- 1998. 04 Ø Thieves in cahoots with a gas-station employee qinstalled minicam for debit-card PIN pad Ø Make fake debit cards to pillage accounts qused ATMs at midnight to steal 2 days’ max Ø Total thefts > $100 K Ø Arrested just before a planned expansion to five more gas stations 63 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Automated Shoulder-Surfing (2) Finland: extra card-reader on ATM -- 1998. 10 Ø Small black card reader glued onto regular card slot q. Collected debit- and credit-card codes Ø Standard shoulder-surfing to garner PINs Ø Made 60 counterfeit cards Ø Stole 180 000 FIM (~U$36, 600) 64 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Automated Shoulder-Surfing (2) Finland: extra card-reader on ATM -- 1998. 10 Ø Small black card reader glued onto regular card slot q. Collected debit- and credit-card codes Ø Standard shoulder-surfing to garner PINs Ø Made 60 counterfeit cards Ø Stole 180 000 FIM (~U$36, 600) 64 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2000 Ø 2000. 01: Global Hell member, 16 yrs old, arrested in Eldorado, CA for stealing user. IDs and passwords for 200, 000 accounts on Pacific Bell ISP. Cracked 63, 000 & boasted about it in chat room. Ø 2000. 03: Max Ray “Max Vision” Butler, 27, of Berkeley, CA indicted on charges of penetrating systems as NASA, Argonne Natl Labs, Brookhaven Natl Lab, Marshall Space Center, and Do. D facilities. Ø 2000. 07: Raymond Torricelli, 20, of New Rochelle, NY arrested and charged with breaking into NASA, Georgia Southern U, San Jose State U computers & stealing credit card #s used for $10 K of theft 65 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2000 Ø 2000. 01: Global Hell member, 16 yrs old, arrested in Eldorado, CA for stealing user. IDs and passwords for 200, 000 accounts on Pacific Bell ISP. Cracked 63, 000 & boasted about it in chat room. Ø 2000. 03: Max Ray “Max Vision” Butler, 27, of Berkeley, CA indicted on charges of penetrating systems as NASA, Argonne Natl Labs, Brookhaven Natl Lab, Marshall Space Center, and Do. D facilities. Ø 2000. 07: Raymond Torricelli, 20, of New Rochelle, NY arrested and charged with breaking into NASA, Georgia Southern U, San Jose State U computers & stealing credit card #s used for $10 K of theft 65 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2000 Ø 2000. 09: 16 -yr-old Florida boy “c. Omrade” sentenced to 6 mo detention in federal prison for penetrating NASA & Pentagon computers Ø 2000. 10: 21 cyberthieves arrested in Sicily in process of stealing $500 M from Banco de Sicilia. Included members of the Mafia, computer specialists and bank employees. Ø 2000. 12: Netherlands hacker penetrated U Washington Medical Center in Seattle. Stole admissions records for 4, 000 cardiac patients. No firewalls or encryption. 66 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2000 Ø 2000. 09: 16 -yr-old Florida boy “c. Omrade” sentenced to 6 mo detention in federal prison for penetrating NASA & Pentagon computers Ø 2000. 10: 21 cyberthieves arrested in Sicily in process of stealing $500 M from Banco de Sicilia. Included members of the Mafia, computer specialists and bank employees. Ø 2000. 12: Netherlands hacker penetrated U Washington Medical Center in Seattle. Stole admissions records for 4, 000 cardiac patients. No firewalls or encryption. 66 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2001 Ø 2001. 01: Jerome Heckenkamp, 21, indicted for allegedly hacking computers at e. Bay, Exodus, Juniper, e. Trade, Lycos, and Cygnus and causing a total of more than $900, 000 in damage in 1999. Ø 2001. 05: Chinese hackers in Guandong penetrated California Independent System Operator’s flow-control computers during an electrical-power crisis. Ø 2001. 07: Lee Ashurst, 22, of Manchester, England, hacked into UAE only ISP and crashed entire country’s access to Internet. Fined £ 2000 and faced civil tort for £ 500 K 67 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2001 Ø 2001. 01: Jerome Heckenkamp, 21, indicted for allegedly hacking computers at e. Bay, Exodus, Juniper, e. Trade, Lycos, and Cygnus and causing a total of more than $900, 000 in damage in 1999. Ø 2001. 05: Chinese hackers in Guandong penetrated California Independent System Operator’s flow-control computers during an electrical-power crisis. Ø 2001. 07: Lee Ashurst, 22, of Manchester, England, hacked into UAE only ISP and crashed entire country’s access to Internet. Fined £ 2000 and faced civil tort for £ 500 K 67 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
![Penetration: 2002 Ø 2002. 02: Adrian Lamo [sic] claimed he hacked NY Times computers Penetration: 2002 Ø 2002. 02: Adrian Lamo [sic] claimed he hacked NY Times computers](https://present5.com/presentation/e0679a8b45b74e1c6128b78585e01695/image-65.jpg) Penetration: 2002 Ø 2002. 02: Adrian Lamo [sic] claimed he hacked NY Times computers and demonstrated how to alter news stories on Yahoo. Ø 2002. 05: Experian loses 13, 000 credit reports to hackers. Ø 2002. 05: Criminal hackers steal financial information about 265, 000 CA state personnel Ø 2002. 08: Princeton admissions personnel hack into Yale University admission records Ø 2002. 08: Forensic. Tec Solutions of San Diego brags about breaking into Army, Navy, NASA computers – gets raided by FBI 68 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2002 Ø 2002. 02: Adrian Lamo [sic] claimed he hacked NY Times computers and demonstrated how to alter news stories on Yahoo. Ø 2002. 05: Experian loses 13, 000 credit reports to hackers. Ø 2002. 05: Criminal hackers steal financial information about 265, 000 CA state personnel Ø 2002. 08: Princeton admissions personnel hack into Yale University admission records Ø 2002. 08: Forensic. Tec Solutions of San Diego brags about breaking into Army, Navy, NASA computers – gets raided by FBI 68 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2003 2002. 02: Contractor for VISA and MASTERCARD penetrated by hackers 2003. 03: Hackers gain full access to AOL customer database with 3. 5 million users. q. Access requires a user ID, two passwords and a Secur. ID code; q. Hackers obtained all of these by spamming the AOL employee database with phony security updates, through online password trades, or by "social engineering" attacks over AOL's Instant Messenger (AIM) or the telephone. 69 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2003 2002. 02: Contractor for VISA and MASTERCARD penetrated by hackers 2003. 03: Hackers gain full access to AOL customer database with 3. 5 million users. q. Access requires a user ID, two passwords and a Secur. ID code; q. Hackers obtained all of these by spamming the AOL employee database with phony security updates, through online password trades, or by "social engineering" attacks over AOL's Instant Messenger (AIM) or the telephone. 69 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2003 Ø 2003. 03: U Texas Austin loses control to hackers over 59, 000 records about students, alumni, faculty, staff. Police charge 20 -yr-old student Christopher Andrew Phillips. Ø 2003. 04: GA Tech computers 0 wn 3 d by hackers from Feb 4 to Mar 14; 57, 000 database records copied included credit-card data for about 40, 000 people Ø 2003. 04: “Blaster Ball” Trojan allows hacker in former Soviet Union to penetrate William Bee Ririe Hospital in Ely, NV Ø 2003. 07: French hackers break into KY govt computers, gain root 70 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2003 Ø 2003. 03: U Texas Austin loses control to hackers over 59, 000 records about students, alumni, faculty, staff. Police charge 20 -yr-old student Christopher Andrew Phillips. Ø 2003. 04: GA Tech computers 0 wn 3 d by hackers from Feb 4 to Mar 14; 57, 000 database records copied included credit-card data for about 40, 000 people Ø 2003. 04: “Blaster Ball” Trojan allows hacker in former Soviet Union to penetrate William Bee Ririe Hospital in Ely, NV Ø 2003. 07: French hackers break into KY govt computers, gain root 70 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2003 Ø 2003. 08: Diebold e-voting company’s Web servers cracked Ø 2003. 11: Hackers access top-secret files at Australian Do. D. Ø 2003. 12: Hackers attack Vote. Here systems 71 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2003 Ø 2003. 08: Diebold e-voting company’s Web servers cracked Ø 2003. 11: Hackers access top-secret files at Australian Do. D. Ø 2003. 12: Hackers attack Vote. Here systems 71 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2004 Ø 2004. 03: Allegiance Telecom notifies 4, 000 users of hack attack that released their user. IDs and passwords [what? Not encrypted? ? ] Ø 2004. 04: Tera. Grid supercomputer network funded by NSF disrupted by hackers Ø 2004. 09: Do. E auditors report 199 hacks penetrating 3, 541 systems in 2003 Ø 2004. 10: Purdue University systems hacked 72 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2004 Ø 2004. 03: Allegiance Telecom notifies 4, 000 users of hack attack that released their user. IDs and passwords [what? Not encrypted? ? ] Ø 2004. 04: Tera. Grid supercomputer network funded by NSF disrupted by hackers Ø 2004. 09: Do. E auditors report 199 hacks penetrating 3, 541 systems in 2003 Ø 2004. 10: Purdue University systems hacked 72 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Penetration: 2005 Ø 2005. 01: Nicolas Lee Jacobsen, 21, charged with breaking into T-Mobile computers for more than 1 year q. Access to 16. 3 M customer files q. Obtain voicemail PINs, passwords for Web access to e-mail q. Read e-mail of FBI agent investigating his own case! Ø 2005. 01: Hackers break into George Mason University computers Ø 2005. 03: 150 applicants to business schools break into their own records illegally on Apply. Yourself Web site 73 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Penetration: 2005 Ø 2005. 01: Nicolas Lee Jacobsen, 21, charged with breaking into T-Mobile computers for more than 1 year q. Access to 16. 3 M customer files q. Obtain voicemail PINs, passwords for Web access to e-mail q. Read e-mail of FBI agent investigating his own case! Ø 2005. 01: Hackers break into George Mason University computers Ø 2005. 03: 150 applicants to business schools break into their own records illegally on Apply. Yourself Web site 73 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 BREAK 5’ 12” 74 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
BREAK 5’ 12” 74 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: NYC Tax Fraud Nov 96 -- AP Ø 3 NYC tax department employees Ø Bribed by property owners from 1992 onward Ø Removed records of taxes owing Ø Fraudulently entered legitimate payments from innocent victims to wrong tax accounts Ø Used bugs in software to cover tracks Ø Stole $13 M in taxes owing + $7 M in interest Ø Over 200 arrests expected Ø Face 10 years prison per count 75 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: NYC Tax Fraud Nov 96 -- AP Ø 3 NYC tax department employees Ø Bribed by property owners from 1992 onward Ø Removed records of taxes owing Ø Fraudulently entered legitimate payments from innocent victims to wrong tax accounts Ø Used bugs in software to cover tracks Ø Stole $13 M in taxes owing + $7 M in interest Ø Over 200 arrests expected Ø Face 10 years prison per count 75 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: Thick Salami at Taco Bell 1997. 01 -- RISKS Ø Willis Robinson (22 years old) reprogrammed Taco Bell cash register qregistered each $2. 99 item as costing $0. 01 qpocketed $2. 98 cash per transaction qstole $3, 600 Ø Management assumed error was hardware or software Ø Idiot was caught because he bragged about his theft to co-workers Ø Sentenced to 10 years in prison 76 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: Thick Salami at Taco Bell 1997. 01 -- RISKS Ø Willis Robinson (22 years old) reprogrammed Taco Bell cash register qregistered each $2. 99 item as costing $0. 01 qpocketed $2. 98 cash per transaction qstole $3, 600 Ø Management assumed error was hardware or software Ø Idiot was caught because he bragged about his theft to co-workers Ø Sentenced to 10 years in prison 76 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: Embezzlement London & Manchester Assurance (1997. 01) Ø Jamie Griffin q 21 years old qclerk qaltered records to steal £ 44, 000 qgambled it all away qclaimed extortion by IRA Ø Sentenced to 7 months imprisonment 77 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: Embezzlement London & Manchester Assurance (1997. 01) Ø Jamie Griffin q 21 years old qclerk qaltered records to steal £ 44, 000 qgambled it all away qclaimed extortion by IRA Ø Sentenced to 7 months imprisonment 77 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling? or QA? Brisbane, Australia (1997. 09) Ø Three men charged with hacking Ø Transferred A$1. 76 M qfrom Commonwealth Bank qto Metway Bank Ø Claimed they were victims of QA error qblame Commonwealth Bank qallege CB placed A$50 M into practice account qfor learning how to use online system for direct payments 78 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling? or QA? Brisbane, Australia (1997. 09) Ø Three men charged with hacking Ø Transferred A$1. 76 M qfrom Commonwealth Bank qto Metway Bank Ø Claimed they were victims of QA error qblame Commonwealth Bank qallege CB placed A$50 M into practice account qfor learning how to use online system for direct payments 78 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: SANS Security Digest hacked (1997. 10) Ø Satirical, misspelled, vulgar nonsense Ø Acutely embarrassing 79 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: SANS Security Digest hacked (1997. 10) Ø Satirical, misspelled, vulgar nonsense Ø Acutely embarrassing 79 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: Québec Tax evasion by computer (1997. 12) Ø Québec, Canada restaurateurs Ø U. S. -made computer program ("zapper") Ø Skimmed off up to 30% of the receipts Ø Evaded Revenue Canada and provincial tax Ø $M/year 80 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: Québec Tax evasion by computer (1997. 12) Ø Québec, Canada restaurateurs Ø U. S. -made computer program ("zapper") Ø Skimmed off up to 30% of the receipts Ø Evaded Revenue Canada and provincial tax Ø $M/year 80 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: SSA Social Security Administration -- 1998. 10 Ø Employee become angry with woman qargued in an Internet chatroom Ø Used fellow-employee's terminal Ø Filled in death date for woman in SSA records Ø Victim applied for loan at bank qshe was "cyberdead” Ø Jorge Yong admitted culpability qresigned qpaid $800 in fines and damages 81 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: SSA Social Security Administration -- 1998. 10 Ø Employee become angry with woman qargued in an Internet chatroom Ø Used fellow-employee's terminal Ø Filled in death date for woman in SSA records Ø Victim applied for loan at bank qshe was "cyberdead” Ø Jorge Yong admitted culpability qresigned qpaid $800 in fines and damages 81 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: LA Gas Los Angeles gasoline-pump fraud -- 1998. 10 Ø DA charged 4 men with fraud Ø Allegedly installed new computer chips in gasoline pumps qcheated consumers qoverstated amounts 7%-25% Ø Complaints about buying more gasoline than capacity of fuel tank Ø Difficult to prove initially qprogrammed chips to spot 5 & 10 gallon tests by inspectors qdelivered exactly right amount for them 82 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: LA Gas Los Angeles gasoline-pump fraud -- 1998. 10 Ø DA charged 4 men with fraud Ø Allegedly installed new computer chips in gasoline pumps qcheated consumers qoverstated amounts 7%-25% Ø Complaints about buying more gasoline than capacity of fuel tank Ø Difficult to prove initially qprogrammed chips to spot 5 & 10 gallon tests by inspectors qdelivered exactly right amount for them 82 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: X. COM Free money (2000. 01) Ø X. COM online bank Ø Transfer funds from the account of any person at any U. S. bank Ø Needed only target’s account number and bank routing information 83 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: X. COM Free money (2000. 01) Ø X. COM online bank Ø Transfer funds from the account of any person at any U. S. bank Ø Needed only target’s account number and bank routing information 83 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: BOOM! New security measures at UK nuclear plants (2001. 09) Ø Employee tried to sabotage nuclear plant (1999. 06) Ø Security guard! Ø Tried to alter sensitive information Ø New measures put into place 18 months later 84 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: BOOM! New security measures at UK nuclear plants (2001. 09) Ø Employee tried to sabotage nuclear plant (1999. 06) Ø Security guard! Ø Tried to alter sensitive information Ø New measures put into place 18 months later 84 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: Cisco accountants stole stock (2001. 11) Ø Oct 2000 -Mar 2001: schemed to issue stock q. Abused access to computer systems q. Created forged stock-disbursal records q. Total theft: $7, 868, 637 Ø Sentences q 34 months in federal prison q. Complete restitution of theft q 3 years supervised release 85 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: Cisco accountants stole stock (2001. 11) Ø Oct 2000 -Mar 2001: schemed to issue stock q. Abused access to computer systems q. Created forged stock-disbursal records q. Total theft: $7, 868, 637 Ø Sentences q 34 months in federal prison q. Complete restitution of theft q 3 years supervised release 85 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling? GOOGLE Bombs Ø GOOGLE used as political ploy (2004. 01) Ø Pranksters engineer Web sites to alter GOOGLE links and statistics Ø Linked George W. Bush to bad words q“unelectable” q“miserable failure” Ø Supporters retaliated with similar ploys against Kerry 86 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling? GOOGLE Bombs Ø GOOGLE used as political ploy (2004. 01) Ø Pranksters engineer Web sites to alter GOOGLE links and statistics Ø Linked George W. Bush to bad words q“unelectable” q“miserable failure” Ø Supporters retaliated with similar ploys against Kerry 86 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Data Diddling: Making the Grade California high school student arrested (2004. 05) Ø Corona del Mar High School, Newport-Mesa Unified School District Ø 17 years old Ø Accused of felony Ø Allegedly hacked school system to change grades Ø Altered grades of 6 juniors and 1 senior Ø Faces up to 3 years in prison 87 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Data Diddling: Making the Grade California high school student arrested (2004. 05) Ø Corona del Mar High School, Newport-Mesa Unified School District Ø 17 years old Ø Accused of felony Ø Allegedly hacked school system to change grades Ø Altered grades of 6 juniors and 1 senior Ø Faces up to 3 years in prison 87 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 88 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 88 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Sabotage? IEvs Navigator 89 Internet Explorer 4. 0 vs Netscape Navigator (1997. 10) Ø IE 4. 0 includes features from Plus! for Windows 95 qanti-aliasing function qsmoothes large fonts on screen Ø Reportedly does not smooth fonts in Netscape Navigator Ø Allegedly not found to fail in any other program tested -- but updated Occam’s Razor states: Never attribute to malice what stupidity can adequately explain. 09: 05 -11: 55 Copyright © 2005 M. E. Kabay. All rights reserved.
Sabotage? IEvs Navigator 89 Internet Explorer 4. 0 vs Netscape Navigator (1997. 10) Ø IE 4. 0 includes features from Plus! for Windows 95 qanti-aliasing function qsmoothes large fonts on screen Ø Reportedly does not smooth fonts in Netscape Navigator Ø Allegedly not found to fail in any other program tested -- but updated Occam’s Razor states: Never attribute to malice what stupidity can adequately explain. 09: 05 -11: 55 Copyright © 2005 M. E. Kabay. All rights reserved.
 Sabotage? MS- edia. Playervs M Real. Audio Several reports of software conflicts — 1998. 10 Ø Installation of MS-Media. Player causes problems with other media players Ø MS product takes over file associations Ø Prevents usability of Real. Audio Ø De-installation switches file associations to other MS products Ø MS denied deliberate attack, accuses other programs of quality problems [Attila the Hun no doubt accused Europeans of quality problems, too. ] 90 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Sabotage? MS- edia. Playervs M Real. Audio Several reports of software conflicts — 1998. 10 Ø Installation of MS-Media. Player causes problems with other media players Ø MS product takes over file associations Ø Prevents usability of Real. Audio Ø De-installation switches file associations to other MS products Ø MS denied deliberate attack, accuses other programs of quality problems [Attila the Hun no doubt accused Europeans of quality problems, too. ] 90 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Hactivists Pentagon Meets : Monty Python “Electronic Disruption Theater” hacker group whine about unfair tactics — 1998. 10 Ø Criminal hackers attacke Do. D Defense. Link 1998. 09 Ø Do. D allegedly used offensive information warfare techniques qallegedly posted hostile Java applet qcriminals downloaded it qsupposedly crashed their systems Ø Criminals complained about illegal response Ø Some legal minds agreed (!) 91 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Hactivists Pentagon Meets : Monty Python “Electronic Disruption Theater” hacker group whine about unfair tactics — 1998. 10 Ø Criminal hackers attacke Do. D Defense. Link 1998. 09 Ø Do. D allegedly used offensive information warfare techniques qallegedly posted hostile Java applet qcriminals downloaded it qsupposedly crashed their systems Ø Criminals complained about illegal response Ø Some legal minds agreed (!) 91 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 “Hactivism on the Rise ” Ø Political action by criminal hackers — or criminal hacking by political activists? Ø “HACKING BHABA” article in FORBES qattack on Bhaba nuclear research facility in India (1998. 05) qinterviews with teenaged perpetrators Ø Attacks on Chinese censorship (1998. 11) q. WIRED qgraduate student disabled Chinese content filters qvandalized pro-censorship site in China 92 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
“Hactivism on the Rise ” Ø Political action by criminal hackers — or criminal hacking by political activists? Ø “HACKING BHABA” article in FORBES qattack on Bhaba nuclear research facility in India (1998. 05) qinterviews with teenaged perpetrators Ø Attacks on Chinese censorship (1998. 11) q. WIRED qgraduate student disabled Chinese content filters qvandalized pro-censorship site in China 92 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Sabotage: Reuters Hong Kong Nov 96 -- RISKS 18. 65 Ø Reuters in Hong Kong qmarket information crucial for trading qlogic bombs at 5 investment-bank clients q 36 hours downtime in networks qno significant effects on their work qembarrassed by the incident Ø Caused by disgruntled computer technician Ø Costs q 1, 700 person-hours for recovery q. HK$1. 3 M (~$168 K) 93 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Sabotage: Reuters Hong Kong Nov 96 -- RISKS 18. 65 Ø Reuters in Hong Kong qmarket information crucial for trading qlogic bombs at 5 investment-bank clients q 36 hours downtime in networks qno significant effects on their work qembarrassed by the incident Ø Caused by disgruntled computer technician Ø Costs q 1, 700 person-hours for recovery q. HK$1. 3 M (~$168 K) 93 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Sabotage: CA Dept Info Tech 1997. 01 -- San Francisco Chronicle, RISKS Ø Fired subcontractor arrested qaccused of trying to cause damage the California Department of Information Technology q. Spent six hours online before being detected q. Crashed system Ø Data restored from backups Ø System management did not know the accused had been fired Ø Did not alter security after his dismissal 94 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Sabotage: CA Dept Info Tech 1997. 01 -- San Francisco Chronicle, RISKS Ø Fired subcontractor arrested qaccused of trying to cause damage the California Department of Information Technology q. Spent six hours online before being detected q. Crashed system Ø Data restored from backups Ø System management did not know the accused had been fired Ø Did not alter security after his dismissal 94 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Sabotage: Gateway 2000 1997. 01 -- EDUPAGE Ø 20, 000 copies of promotional video Ø 30 seconds of pornography in mid-video Ø Investigators thinking focusing on likelihood of disgruntled employee of Gateway 2000 or at video production company 95 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Sabotage: Gateway 2000 1997. 01 -- EDUPAGE Ø 20, 000 copies of promotional video Ø 30 seconds of pornography in mid-video Ø Investigators thinking focusing on likelihood of disgruntled employee of Gateway 2000 or at video production company 95 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Sabotage: US Coast Guard DP worker goes ballistic -- 1998. 06 Ø Shakuntla Devi Singla qcivilian data processing worker qreported possible crime by contractor Ø Warnings disregarded q. Wiped out personnel database q. Crashed system Ø Recovery (where were their backups? ) q 115 Coast Guard employees q 1, 800 hours to restore data Ø Sentenced to 5 months jail then 5 months home detention Ø Fined $35, 000 restitution 96 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Sabotage: US Coast Guard DP worker goes ballistic -- 1998. 06 Ø Shakuntla Devi Singla qcivilian data processing worker qreported possible crime by contractor Ø Warnings disregarded q. Wiped out personnel database q. Crashed system Ø Recovery (where were their backups? ) q 115 Coast Guard employees q 1, 800 hours to restore data Ø Sentenced to 5 months jail then 5 months home detention Ø Fined $35, 000 restitution 96 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Sabotage: Telecast Fiber Ø Former Employee Destroys Files (2003. 08) Ø John Corrado broke into Telecast Fiber Systems Inc, Worcester MA q. Used modem q. Destroyed R&D files and demos used by sales reps Ø Pleaded guilty, agreed to pay $10, 360 restitution Ø Possible penalties: qmax 1 year prison q$100 K fine 97 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Sabotage: Telecast Fiber Ø Former Employee Destroys Files (2003. 08) Ø John Corrado broke into Telecast Fiber Systems Inc, Worcester MA q. Used modem q. Destroyed R&D files and demos used by sales reps Ø Pleaded guilty, agreed to pay $10, 360 restitution Ø Possible penalties: qmax 1 year prison q$100 K fine 97 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Web Vandalism Ø CIA (1996. 09) Ø USAF (1996. 12) Ø NASA (1997. 03) Ø Air. Tran (1997. 09) Ø UNICEF (1998. 01) Ø US Dept Commerce (1998. 02) Ø New York Times (1998. 09) Ø SETI site (1999) Ø Fort Monmouth (1999) Ø Senate of the USA (twice)(1999) 98 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Web Vandalism Ø CIA (1996. 09) Ø USAF (1996. 12) Ø NASA (1997. 03) Ø Air. Tran (1997. 09) Ø UNICEF (1998. 01) Ø US Dept Commerce (1998. 02) Ø New York Times (1998. 09) Ø SETI site (1999) Ø Fort Monmouth (1999) Ø Senate of the USA (twice)(1999) 98 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
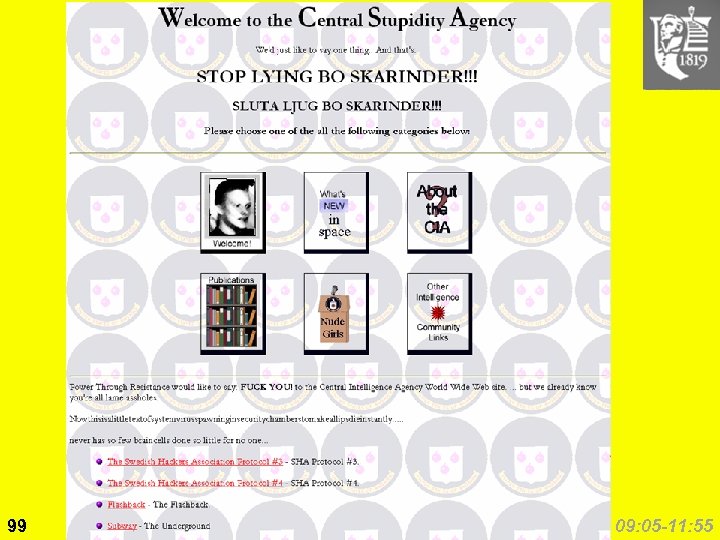 CIA (1996. 09) 99 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
CIA (1996. 09) 99 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
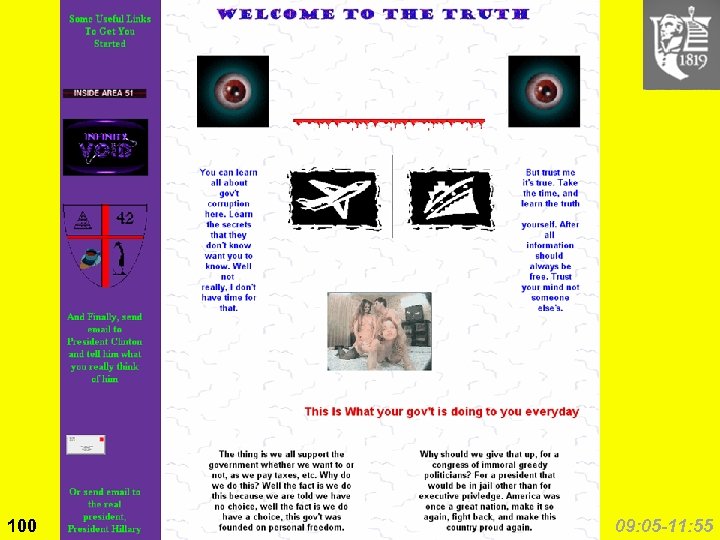 USAF (1996. 12) 100 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
USAF (1996. 12) 100 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 NASA (1997. 03) 101 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
NASA (1997. 03) 101 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
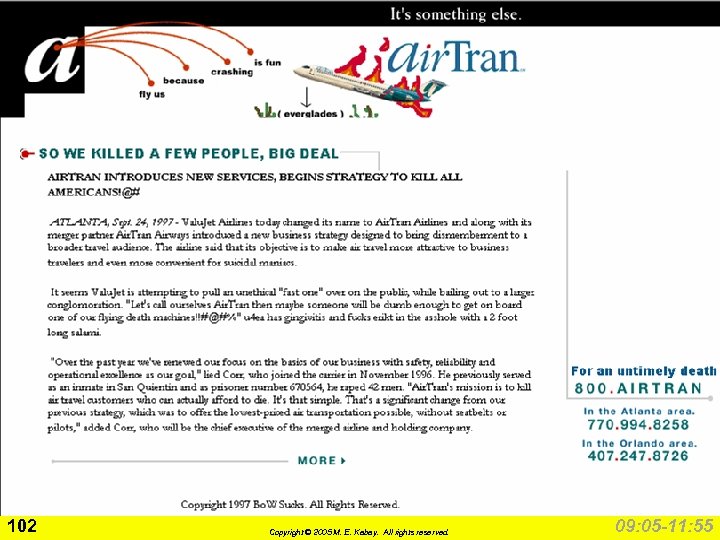 Air. Tran (1997. 09) 102 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Air. Tran (1997. 09) 102 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 UNICEF (1998. 01) 103 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
UNICEF (1998. 01) 103 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 US Dept Commerce (1998. 02) 104 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
US Dept Commerce (1998. 02) 104 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 New York Times (1998. 0 9) 105 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
New York Times (1998. 0 9) 105 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 SETI (1999) 106 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
SETI (1999) 106 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Fort Monmouth (1999) 107 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Fort Monmouth (1999) 107 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Senate of the USA (1) (1999) 108 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Senate of the USA (1) (1999) 108 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Senate of the USA (2) (1999. 06) 109 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Senate of the USA (2) (1999. 06) 109 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 DEFCON (1999. 07) 110 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
DEFCON (1999. 07) 110 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Vandalism: 2000 Ø 2001. 01: “Lamers Team” deface Library of Congress Web site Ø 2000. 03: Gallup site defaced with misleading pointers to Anti. Online Ø 2000. 04: 16 -year-old in Sweden arrested for defacing Web side of Swedish National Board of Health and Welfare Ø 2000. 09: “fluxnyne” defaces OPEC Web site 111 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Vandalism: 2000 Ø 2001. 01: “Lamers Team” deface Library of Congress Web site Ø 2000. 03: Gallup site defaced with misleading pointers to Anti. Online Ø 2000. 04: 16 -year-old in Sweden arrested for defacing Web side of Swedish National Board of Health and Welfare Ø 2000. 09: “fluxnyne” defaces OPEC Web site 111 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Vandalism: 2001 & 2003 Ø 2001. 01: MS Web pages defaced by “Prime Suspectz” hacker group Ø 2001. 05: Chinese security experts report 14% of worldwide hacker attacks aimed at PRC Web sites Ø 2003. 05: Hackers attack Denver Internet radio station hosting security conference Ø 2003. 06: Hijacker switched registration of LA County Web site by calling ARIN and then stole 65, 000 Web site addresses for use in sending pornographic spam 112 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Vandalism: 2001 & 2003 Ø 2001. 01: MS Web pages defaced by “Prime Suspectz” hacker group Ø 2001. 05: Chinese security experts report 14% of worldwide hacker attacks aimed at PRC Web sites Ø 2003. 05: Hackers attack Denver Internet radio station hosting security conference Ø 2003. 06: Hijacker switched registration of LA County Web site by calling ARIN and then stole 65, 000 Web site addresses for use in sending pornographic spam 112 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Vandalism: 2003 & 2004 Ø 2003. 07: Sudanese hacker destroys Websites of Sudan Airlines, Khartoum University, Aptec Computers, Sudanese Internet Company. Ø 2003. 12: 13 NASA Websites defaced by Brazilian hackers “drwxr” with antiwar sentiments Ø 2004. 06: Silicon Valley Land Survey Web site used to post videos of Paul Johnson (victim of Al Qaeda terrorists) Ø 2004. 06: Hackers infest 60 computers at South Korean research institutes and government agencies with Peep Trojan RAT 113 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Vandalism: 2003 & 2004 Ø 2003. 07: Sudanese hacker destroys Websites of Sudan Airlines, Khartoum University, Aptec Computers, Sudanese Internet Company. Ø 2003. 12: 13 NASA Websites defaced by Brazilian hackers “drwxr” with antiwar sentiments Ø 2004. 06: Silicon Valley Land Survey Web site used to post videos of Paul Johnson (victim of Al Qaeda terrorists) Ø 2004. 06: Hackers infest 60 computers at South Korean research institutes and government agencies with Peep Trojan RAT 113 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 BREAK 5’ 02” 114 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
BREAK 5’ 02” 114 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 115 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 115 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Moldovan Scam 1997. 11 — news wires, EDUPAGE, RISKS Ø Pornography seekers logged into http: //www. sexygirls. com (Nov 96 -1997. 02) Ø Special viewer program to decode pictures Ø Trojan program qsecretly disconnected modem connection qturned modem sound off qdialed ISP in Moldavia — long distance Ø Long-distance charges in $K/victim Ø Court ordered refund of $M to consumers 116 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Moldovan Scam 1997. 11 — news wires, EDUPAGE, RISKS Ø Pornography seekers logged into http: //www. sexygirls. com (Nov 96 -1997. 02) Ø Special viewer program to decode pictures Ø Trojan program qsecretly disconnected modem connection qturned modem sound off qdialed ISP in Moldavia — long distance Ø Long-distance charges in $K/victim Ø Court ordered refund of $M to consumers 116 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Back Orifice c. Dc (Cult of the Dead Cow) — 1998. 07 Ø Back Orifice for analyzing and compromising MS-Windows security Ø Sir Dystic — hacker with L 0 PHT Ø “Main legitimate purposes for BO: ” qremote tech support aid qemployee monitoring qremote administering [of a Windows network]. Ø "Wink. ” 118 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Back Orifice c. Dc (Cult of the Dead Cow) — 1998. 07 Ø Back Orifice for analyzing and compromising MS-Windows security Ø Sir Dystic — hacker with L 0 PHT Ø “Main legitimate purposes for BO: ” qremote tech support aid qemployee monitoring qremote administering [of a Windows network]. Ø "Wink. ” 118 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Back Orifice — cont’d Ø Features qimage and data capture from any Windows system on a compromised network q. HTTP server allowing unrestricted I/O to and from workstation qpacket sniffer qkeystroke monitor qsoftware for easy manipulations of the victims' Internet connections Ø Trojan allows infection of other applications Ø Stealth techniques Ø 15, 000 copies distributed to IRC users in infected file “nfo. zip” 119 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Back Orifice — cont’d Ø Features qimage and data capture from any Windows system on a compromised network q. HTTP server allowing unrestricted I/O to and from workstation qpacket sniffer qkeystroke monitor qsoftware for easy manipulations of the victims' Internet connections Ø Trojan allows infection of other applications Ø Stealth techniques Ø 15, 000 copies distributed to IRC users in infected file “nfo. zip” 119 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Open Source Contaminated TCP wrapper infected with Trojan (1999. 01) Ø Early on 21 Jan 1999 someone inserted Trojan code into distribution site Ø Trapdoor access to contaminated systems Ø Sent e-mail indicating which sites contaminated 120 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Open Source Contaminated TCP wrapper infected with Trojan (1999. 01) Ø Early on 21 Jan 1999 someone inserted Trojan code into distribution site Ø Trapdoor access to contaminated systems Ø Sent e-mail indicating which sites contaminated 120 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Palm PDA “Pirated” Gameboy software infects PDAs (2000. 08) Ø Deletes applications on Palm Pilot Ø Proof of concept? 121 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Palm PDA “Pirated” Gameboy software infects PDAs (2000. 08) Ø Deletes applications on Palm Pilot Ø Proof of concept? 121 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: MS a Victim QAZ Trojan invaders Microsoft (2000. 10) Ø Company passwords sent to e-mail address in St Petersburg, Russia Ø “Deplorable act of industrial espionage” Ø Investigation suggested little damage Ø Source files very large – probably not transferred 122 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: MS a Victim QAZ Trojan invaders Microsoft (2000. 10) Ø Company passwords sent to e-mail address in St Petersburg, Russia Ø “Deplorable act of industrial espionage” Ø Investigation suggested little damage Ø Source files very large – probably not transferred 122 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: MS “Cumulative Patch” MS Cumulative Patch a trick (2002. 03) Ø E-mail with 160 KB attachment Ø Subject: “Internet Security Update” Ø “Eliminates MS Outlook/Express… vulnerabilities” Ø Vague link to MS security site Ø Actually contained “Gibe” worm 123 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: MS “Cumulative Patch” MS Cumulative Patch a trick (2002. 03) Ø E-mail with 160 KB attachment Ø Subject: “Internet Security Update” Ø “Eliminates MS Outlook/Express… vulnerabilities” Ø Vague link to MS security site Ø Actually contained “Gibe” worm 123 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Reverse-Proxy Spam Trojan Migmaf trojan commandeers PCs (2003. 07) Ø “Migrant mafia” takes over PCs by stealth q. Not certain how it spreads q. Programmer may be changing code constantly to elude anti-malware products Ø Relays requests for porn sites through infected systems q. Web page passed through zombie q. Impossible to locate master server q. Porn sites may be traps for credit-card data Ø Zombies also serve as spam relay sites 124 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Reverse-Proxy Spam Trojan Migmaf trojan commandeers PCs (2003. 07) Ø “Migrant mafia” takes over PCs by stealth q. Not certain how it spreads q. Programmer may be changing code constantly to elude anti-malware products Ø Relays requests for porn sites through infected systems q. Web page passed through zombie q. Impossible to locate master server q. Porn sites may be traps for credit-card data Ø Zombies also serve as spam relay sites 124 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Linux Backdoor Linux kernel attacked (2003. 11) Ø Hacker tried to enter backdoor code into sys_wait 4() function Ø Would have granted root Ø Noticed by experienced Linux programmers 125 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Linux Backdoor Linux kernel attacked (2003. 11) Ø Hacker tried to enter backdoor code into sys_wait 4() function Ø Would have granted root Ø Noticed by experienced Linux programmers 125 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Phatbot uses P 2 P Ø Phatbot attacks security (2004. 03) Ø Extensive feature set q. Controlled through P 2 P networks q. Provides complete remote control over system (open files, reboot, send files…. ) q. Snoops for passwords & tries to send them q. Tries to disable firewalls and AV products Ø Author arrested 2004 -05 q. Baden-Württemberg, Germany 126 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Phatbot uses P 2 P Ø Phatbot attacks security (2004. 03) Ø Extensive feature set q. Controlled through P 2 P networks q. Provides complete remote control over system (open files, reboot, send files…. ) q. Snoops for passwords & tries to send them q. Tries to disable firewalls and AV products Ø Author arrested 2004 -05 q. Baden-Württemberg, Germany 126 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Mac Attack MS-Office Installer icon is Trojan (2004. 05) Ø AS. MW 2004. Trojan has icon like that of MS Installaer for MS-Office for Mac Ø Actually Trojan that deletes all files in user’s home folder 127 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Mac Attack MS-Office Installer icon is Trojan (2004. 05) Ø AS. MW 2004. Trojan has icon like that of MS Installaer for MS-Office for Mac Ø Actually Trojan that deletes all files in user’s home folder 127 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Cell Phones “Skulls” targets Nokia 7610 (2004. 11) Ø Appears as a “theme manager” utility Ø Exploits Symbian OS Ø Actually disables all programs on phone q. Calendar, phonebook, camera, Web browser, SMS applications, etc. q. Leaves only outbound and inbound phone calls functional Ø By 2005. 04, researchers had found >100 Trojans affecting Symbian OS 128 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Cell Phones “Skulls” targets Nokia 7610 (2004. 11) Ø Appears as a “theme manager” utility Ø Exploits Symbian OS Ø Actually disables all programs on phone q. Calendar, phonebook, camera, Web browser, SMS applications, etc. q. Leaves only outbound and inbound phone calls functional Ø By 2005. 04, researchers had found >100 Trojans affecting Symbian OS 128 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Cellery Worm Clogs Networks (2005. 01) Ø Infected “Tetris” game contains worm Ø Reproduces throughout network Ø Can cause serious bandwidth saturation Ø Users who perceive playing games at work as normal may not realize that the program is a threat 129 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Cellery Worm Clogs Networks (2005. 01) Ø Infected “Tetris” game contains worm Ø Reproduces throughout network Ø Can cause serious bandwidth saturation Ø Users who perceive playing games at work as normal may not realize that the program is a threat 129 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Trojan: Bankash-A Trojan attacks antispyware tool, logs keystrokes (2005. 02) Ø Arrives in e-mail attachment Ø Tries to disable MS antispyware and antivirus software Ø Logs user keystrokes, tries to send creditcard & banking info to receiving site Ø May delete files Ø Attempts to install yet more malware Ø Downloads additional code from the Internet 130 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Trojan: Bankash-A Trojan attacks antispyware tool, logs keystrokes (2005. 02) Ø Arrives in e-mail attachment Ø Tries to disable MS antispyware and antivirus software Ø Logs user keystrokes, tries to send creditcard & banking info to receiving site Ø May delete files Ø Attempts to install yet more malware Ø Downloads additional code from the Internet 130 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinfo q. Psyops Ø Denial of Service (Do. S) 131 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinfo q. Psyops Ø Denial of Service (Do. S) 131 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Deception: Holiday Inns Call vs Management 1997. 01 -- AP Ø Holiday Inns uses 1 -800 -HOLIDAY for reservations (note the O) Ø Call Management uses 1 -800 -H 0 LIDAY (note the ZERO Ø Holiday Inns sued and lost Ø Other firms have used phone numbers adjacent to important commercial numbers in order to capture calls from misdealing customers Ø Old porn site whitehouse. com (now a respectable site) used confusion with whitehouse. gov to trick kids into visit 132 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Deception: Holiday Inns Call vs Management 1997. 01 -- AP Ø Holiday Inns uses 1 -800 -HOLIDAY for reservations (note the O) Ø Call Management uses 1 -800 -H 0 LIDAY (note the ZERO Ø Holiday Inns sued and lost Ø Other firms have used phone numbers adjacent to important commercial numbers in order to capture calls from misdealing customers Ø Old porn site whitehouse. com (now a respectable site) used confusion with whitehouse. gov to trick kids into visit 132 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Disinfo Belgian ATC Fraud : 1997. 01 — Reuters Ø Belgian lunatic broadcasting false information to pilots Ø Air-Traffic Control have caught the false information in time to prevent tragedy Ø Serious problem for air safety Ø Police so far unable to locate pirate transmitter Ø Lunatic thought to be former ATC employee 133 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Disinfo Belgian ATC Fraud : 1997. 01 — Reuters Ø Belgian lunatic broadcasting false information to pilots Ø Air-Traffic Control have caught the false information in time to prevent tragedy Ø Serious problem for air safety Ø Police so far unable to locate pirate transmitter Ø Lunatic thought to be former ATC employee 133 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Disinfo Negotiations with : Kidnappers Spoofed 1997. 02 — RISKS Ø Colombian terrorists kidnapped soldiers Government of Colombia decided to negotiate through e-mail Ø Right-wing terrorists sent fraudulent e-mail claiming to represent government position 134 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Disinfo Negotiations with : Kidnappers Spoofed 1997. 02 — RISKS Ø Colombian terrorists kidnapped soldiers Government of Colombia decided to negotiate through e-mail Ø Right-wing terrorists sent fraudulent e-mail claiming to represent government position 134 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Disinfo Cronkite Smeared : 1997. 01 — AP Ø Tim Hughes created Web libeling Walter Cronkite qsaid WC had shrieked imprecations qspat at Hughes and wife in FL restaurant Ø Included falsified digital images purporting to show Cronkite posing with KKK members Ø Cronkite threatened lawsuit Ø Hughes took down page, said it was a satire 135 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Disinfo Cronkite Smeared : 1997. 01 — AP Ø Tim Hughes created Web libeling Walter Cronkite qsaid WC had shrieked imprecations qspat at Hughes and wife in FL restaurant Ø Included falsified digital images purporting to show Cronkite posing with KKK members Ø Cronkite threatened lawsuit Ø Hughes took down page, said it was a satire 135 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Psyops: Motley Fool Mar 96 -- Wall Street Journal; EDUPAGE; RISKS Ø Iomega high-capacity removable disk drives Ø America Online's Motley Fool bulletin board q. False information q. Flaming and physical threats Ø Caused volatility of stock prices 136 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Psyops: Motley Fool Mar 96 -- Wall Street Journal; EDUPAGE; RISKS Ø Iomega high-capacity removable disk drives Ø America Online's Motley Fool bulletin board q. False information q. Flaming and physical threats Ø Caused volatility of stock prices 136 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Psyops: Pairgain Ø 1999. 04: Gary Dale Hoke arrested by FBI q. Employee of Pairgain Ø Created bogus Web page q. Simulated Bloomberg information service q. Touted Pair. Gain stock üundervalued – impending takeover Ø Pointed to fake page using Yahoo message boards q. Investors bid up price of Pairgain stock from $8. 50 to $11. 12 (130%) q 13. 7 M shares traded – 700% normal volume 137 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Psyops: Pairgain Ø 1999. 04: Gary Dale Hoke arrested by FBI q. Employee of Pairgain Ø Created bogus Web page q. Simulated Bloomberg information service q. Touted Pair. Gain stock üundervalued – impending takeover Ø Pointed to fake page using Yahoo message boards q. Investors bid up price of Pairgain stock from $8. 50 to $11. 12 (130%) q 13. 7 M shares traded – 700% normal volume 137 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Pairgain – cont’d Ø Windfall gains & losses by investors Ø Hoke did not in fact trade any of the stock himself q. Pleaded guilty to charges of stock manipulation q. Sentenced to home detention, probation, restitution 138 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Pairgain – cont’d Ø Windfall gains & losses by investors Ø Hoke did not in fact trade any of the stock himself q. Pleaded guilty to charges of stock manipulation q. Sentenced to home detention, probation, restitution 138 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Psyops: Emulex 2000. 98: Emulex lost 60% of total share value Ø Mark Jakob, 23 years old Ø Fabricated news release Ø Sent from community college computer Ø Circulated by Dow Jones, Bloomberg Ø Claimed profit warning, SEC investigators, loss of CEO Ø Jackob profited by $240, 000 in minutes 139 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Psyops: Emulex 2000. 98: Emulex lost 60% of total share value Ø Mark Jakob, 23 years old Ø Fabricated news release Ø Sent from community college computer Ø Circulated by Dow Jones, Bloomberg Ø Claimed profit warning, SEC investigators, loss of CEO Ø Jackob profited by $240, 000 in minutes 139 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Psyops: Ponzi EE-Biz Ventures steals $50 M (2001. 07) Ø Donald A. English claimed huge profits Ø Paid early investors with money from later ones Ø Classic “Ponzi” scheme Ø Arrested by FBI Ø Most victims were sick or elderly 140 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Psyops: Ponzi EE-Biz Ventures steals $50 M (2001. 07) Ø Donald A. English claimed huge profits Ø Paid early investors with money from later ones Ø Classic “Ponzi” scheme Ø Arrested by FBI Ø Most victims were sick or elderly 140 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Psyops: 4 -1 -9 Brides Ø Prospective Brides Needed Money (2004. 11) Ø Russian Yury Lazarev hired women to write flowery letters to possible partners Ø Included sexy photographs Ø 3, 000 men responded from around world Ø Attempts to meet met with requests for money q. Visas q. Airline tickets Ø Net profits: $300, 000 Ø One year suspended sentence in Moscow 141 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Psyops: 4 -1 -9 Brides Ø Prospective Brides Needed Money (2004. 11) Ø Russian Yury Lazarev hired women to write flowery letters to possible partners Ø Included sexy photographs Ø 3, 000 men responded from around world Ø Attempts to meet met with requests for money q. Visas q. Airline tickets Ø Net profits: $300, 000 Ø One year suspended sentence in Moscow 141 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 BREAK 4’ 56” 142 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
BREAK 4’ 56” 142 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 143 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Cases Ø Breaches of confidentiality Ø Industrial Espionage Ø Unauthorized Access (Penetration) Ø Unauthorized Modification q. Data Diddling q. Sabotage, vandalism q. Trojan Horses Ø Deception q. Fraud, disinformation q. Psyops Ø Denial of Service (Do. S) 143 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 History of Do. S Ø 1987 -12: Christmas-Tree Worm q. IBM internal networks q. Grew explosively q. Self-mailing graphic q. Escaped into BITNET Ø 1988 -11: Morris Worm q. Probably launched by mistake q. Demonstration program q. Replicated through Internet q~9, 000 systems crashed or were deliberately taken off-line 144 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
History of Do. S Ø 1987 -12: Christmas-Tree Worm q. IBM internal networks q. Grew explosively q. Self-mailing graphic q. Escaped into BITNET Ø 1988 -11: Morris Worm q. Probably launched by mistake q. Demonstration program q. Replicated through Internet q~9, 000 systems crashed or were deliberately taken off-line 144 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
![Do. S: Mail-Bombing Via Lists 1996. 08/12 Ø 1996. 08 — “Johnny [x]chaotic” q Do. S: Mail-Bombing Via Lists 1996. 08/12 Ø 1996. 08 — “Johnny [x]chaotic” q](https://present5.com/presentation/e0679a8b45b74e1c6128b78585e01695/image-141.jpg) Do. S: Mail-Bombing Via Lists 1996. 08/12 Ø 1996. 08 — “Johnny [x]chaotic” q subscribed dozens of people to hundreds of lists q victims received up to 20, 000 e-mail msg/day q published rambling, incoherent manifesto q became known as “UNAMAILER” Ø 1996. 12 — UNAMAILER struck again Ø Root problem q some list managers automatically subscribe people q should verifying authenticity of request q send request for confirmation 145 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Mail-Bombing Via Lists 1996. 08/12 Ø 1996. 08 — “Johnny [x]chaotic” q subscribed dozens of people to hundreds of lists q victims received up to 20, 000 e-mail msg/day q published rambling, incoherent manifesto q became known as “UNAMAILER” Ø 1996. 12 — UNAMAILER struck again Ø Root problem q some list managers automatically subscribe people q should verifying authenticity of request q send request for confirmation 145 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Spam / Junk E-mail 1996. 09 Ø AOL began blocking all inbound mail from junk e-mailers Ø Court challenges on both sides Ø Other ISPs beginning to revolt against onslaught of automated spam generators Ø Courts have ruled that junk e-mail does not have to be transmitted by ISPs 146 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Spam / Junk E-mail 1996. 09 Ø AOL began blocking all inbound mail from junk e-mailers Ø Court challenges on both sides Ø Other ISPs beginning to revolt against onslaught of automated spam generators Ø Courts have ruled that junk e-mail does not have to be transmitted by ISPs 146 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Spam / Junk E-mail 1996. 09 Ø Paul Engel, San Francisco stock broker Ø Disagreement with an employee of the SRI Ø Allegedly resulted in mail-bombing run on 23 September Ø 25, 000 messages consisting of the word “Idiot” Ø Originated from SRI account Ø Prevented him from using his computer Ø 1996. 12: Sued SRI for $25, 000 of damages 147 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Spam / Junk E-mail 1996. 09 Ø Paul Engel, San Francisco stock broker Ø Disagreement with an employee of the SRI Ø Allegedly resulted in mail-bombing run on 23 September Ø 25, 000 messages consisting of the word “Idiot” Ø Originated from SRI account Ø Prevented him from using his computer Ø 1996. 12: Sued SRI for $25, 000 of damages 147 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Vineyard. NET vs Spam 1997. 01 Ø Vineyard. NET hijacked by CV Communications Ø Connected directly to the ISP's SMTP server Ø Sent out 66, 000 advertisements for spamming services Ø Most victims: Compu. Serve and AOL Ø Tuned firewall to reject further input from rogue Ø Adjusted two-stage mail delivery software qscan and delete all junk e-mail 148 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Vineyard. NET vs Spam 1997. 01 Ø Vineyard. NET hijacked by CV Communications Ø Connected directly to the ISP's SMTP server Ø Sent out 66, 000 advertisements for spamming services Ø Most victims: Compu. Serve and AOL Ø Tuned firewall to reject further input from rogue Ø Adjusted two-stage mail delivery software qscan and delete all junk e-mail 148 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Miscellany 1997. 01/03 Ø 1997. 01 — “Rev. White” spams IRC Undernet q racist, homophobic, misogynist q threatening messages Ø 1997. 01 — Cleveland resident receives 100 calls/night because his phone # is 1 -off AOL’s Ø 1997. 03 — Inter. NIC loses papers for unnamed company q cut off its DNS entry q down for 20 hours Ø 1997. 03 — Sprynet suddenly terminates service to anyone not using
Do. S: Miscellany 1997. 01/03 Ø 1997. 01 — “Rev. White” spams IRC Undernet q racist, homophobic, misogynist q threatening messages Ø 1997. 01 — Cleveland resident receives 100 calls/night because his phone # is 1 -off AOL’s Ø 1997. 03 — Inter. NIC loses papers for unnamed company q cut off its DNS entry q down for 20 hours Ø 1997. 03 — Sprynet suddenly terminates service to anyone not using
 Do. S: Wasting Time On-Line 1997. 06 Ø 1997. 06 — employee use of Web for fun during working hours qconsumes average 2 hours of productivity/week qother estimates range from 5% to 40% lost qalso consume bandwidth Ø 1997. 06 — Pitney Bowes study from Gallup and San Jose State University q 972 top-level staff from Fortune 1000 qsevere damage to productivity from interrupts q 50% said interruptions every 10 minutes qoverwhelmed by flood of messages 150 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Wasting Time On-Line 1997. 06 Ø 1997. 06 — employee use of Web for fun during working hours qconsumes average 2 hours of productivity/week qother estimates range from 5% to 40% lost qalso consume bandwidth Ø 1997. 06 — Pitney Bowes study from Gallup and San Jose State University q 972 top-level staff from Fortune 1000 qsevere damage to productivity from interrupts q 50% said interruptions every 10 minutes qoverwhelmed by flood of messages 150 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Bluelister Attacks Antispammers 1997. 06: Forged headers from Antispam sites Ø 1 or more persons Ø Send large amounts junk e-mail from antispammers home sites Ø Resulting floods of angry responses crashes systems Ø Net. Home Web-hosting service severely compromised 151 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Bluelister Attacks Antispammers 1997. 06: Forged headers from Antispam sites Ø 1 or more persons Ø Send large amounts junk e-mail from antispammers home sites Ø Resulting floods of angry responses crashes systems Ø Net. Home Web-hosting service severely compromised 151 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S News 1998 Ø 1998. 01: Sanford “Spamford” Wallace found new spam-friendly ISP qoffices swamped with phone calls, e-mails and threats Ø 1998. 03: Windows NT servers crash under hack attacks q. Carnegie Mellon, MIT, NASA sites, man U. Cal. Campuses, US Navy Ø 1998. 03: Mailstorm by National Association of Broadcasters qinstructions on how to unsubscribe actually sent messages to list itself 152 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S News 1998 Ø 1998. 01: Sanford “Spamford” Wallace found new spam-friendly ISP qoffices swamped with phone calls, e-mails and threats Ø 1998. 03: Windows NT servers crash under hack attacks q. Carnegie Mellon, MIT, NASA sites, man U. Cal. Campuses, US Navy Ø 1998. 03: Mailstorm by National Association of Broadcasters qinstructions on how to unsubscribe actually sent messages to list itself 152 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S News 1998 (Cont’d) Ø 1998. 05: Panamsat Galaxy 4 satellite malfunctions q 10 M pagers silenced qalso some public radio networks qtwo days of disruption Ø 1998. 09: Misappropriation of resources q. Aaron Blosser accused of using 2585 computers at US West qlooking for prime numbers qused 10 years of processing cycles qsent response time from 3 -5 seconds to 5 minutes 153 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S News 1998 (Cont’d) Ø 1998. 05: Panamsat Galaxy 4 satellite malfunctions q 10 M pagers silenced qalso some public radio networks qtwo days of disruption Ø 1998. 09: Misappropriation of resources q. Aaron Blosser accused of using 2585 computers at US West qlooking for prime numbers qused 10 years of processing cycles qsent response time from 3 -5 seconds to 5 minutes 153 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Worcester Hacker Convicted Teenager punished for hack — 1998. 03 Ø Kid broke into Bell Atlantic switch in suburb of Boston, MA in 1997. 03 qcrashed switch q 6 hours down Ø Disrupted service for 600 customers & local airport control tower Ø Severely sentenced as example to others q 2 years probation qloss of computer q 250 hours community service q$5, 000 restitution 154 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Worcester Hacker Convicted Teenager punished for hack — 1998. 03 Ø Kid broke into Bell Atlantic switch in suburb of Boston, MA in 1997. 03 qcrashed switch q 6 hours down Ø Disrupted service for 600 customers & local airport control tower Ø Severely sentenced as example to others q 2 years probation qloss of computer q 250 hours community service q$5, 000 restitution 154 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: MS & CERT-CC Down Network vandal attacks MS (2001. 01) Ø Flooded MS sites w/ packets Ø Down for a day Ø Due to putting DNS servers in single network CERT-CC down 30 hours (2001. 05) Ø Do. S packet flood Ø Viewed as “just another attack” by staff 155 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: MS & CERT-CC Down Network vandal attacks MS (2001. 01) Ø Flooded MS sites w/ packets Ø Down for a day Ø Due to putting DNS servers in single network CERT-CC down 30 hours (2001. 05) Ø Do. S packet flood Ø Viewed as “just another attack” by staff 155 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Cloud Nine ISP out of business (2002. 01) Ø Massive Do. S q. E-mail q. DNS servers Ø Shut down operations Ø Insurance insufficient to pay for rebuilding systems Ø Decided to sell business to competitors 156 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Cloud Nine ISP out of business (2002. 01) Ø Massive Do. S q. E-mail q. DNS servers Ø Shut down operations Ø Insurance insufficient to pay for rebuilding systems Ø Decided to sell business to competitors 156 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: White House site offline (2002. 05) Ø Do. S 09: 00 -11: 15 4 May 2002 Ø Suspect Chinese and pro-Chinese hackers 157 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: White House site offline (2002. 05) Ø Do. S 09: 00 -11: 15 4 May 2002 Ø Suspect Chinese and pro-Chinese hackers 157 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Root Servers Do. S cripples 9 of 13 root servers (2002. 10) Ø Most sophisticated and large-scale assault on root servers to date q. Started 16: 45 EDT Monday 21 Oct 2002 q 30 -40 x normal traffic from South Korea and US origins q 7 servers failed completely; 2 intermittently q. Remaining 4 servers continued to service ‘Net requests – no significant degradation of service Ø Verisign upgraded protection on its servers as a result 158 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Root Servers Do. S cripples 9 of 13 root servers (2002. 10) Ø Most sophisticated and large-scale assault on root servers to date q. Started 16: 45 EDT Monday 21 Oct 2002 q 30 -40 x normal traffic from South Korea and US origins q 7 servers failed completely; 2 intermittently q. Remaining 4 servers continued to service ‘Net requests – no significant degradation of service Ø Verisign upgraded protection on its servers as a result 158 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Al-Jazeera swamped (2003. 03) Ø Arab satellite TV network Web site unavailable Ø Swamped by bogus traffic aimed at US servers for its site 159 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Al-Jazeera swamped (2003. 03) Ø Arab satellite TV network Web site unavailable Ø Swamped by bogus traffic aimed at US servers for its site 159 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Akamai (E-Commerce) Akamai Technologies goes down (2004. 06) Ø Network vandals attacked Akamai servers Ø Manages 15% of total traffic on Internet Ø Down for 45 minutes Ø Serve major players in e-commerce q. Microsoft q. Yahoo q. Fed. Ex q. Xero. X, . . . many others q. Also FBI Ø Care to estimate the costs of downtime? ? 160 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Akamai (E-Commerce) Akamai Technologies goes down (2004. 06) Ø Network vandals attacked Akamai servers Ø Manages 15% of total traffic on Internet Ø Down for 45 minutes Ø Serve major players in e-commerce q. Microsoft q. Yahoo q. Fed. Ex q. Xero. X, . . . many others q. Also FBI Ø Care to estimate the costs of downtime? ? 160 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: GOOGLE &. com Disappear Briefly GOOGLE disappears from Web (2005. 05) Ø Gone for 15 minutes 7 May 2005 Ø Glitch in DNS Ø Drew attention to concerns over DNS stability Ø National Research Council issued report criticizing state of DNS infrastructure http: //www 7. nationalacademies. org/cstb/pub_d ns. html Historical note: 2000. 08. 23: 4 of 13 root DNS servers failed Ø All access (http, ftp, smtp) to entire. com domain blocked for 1 hour worldwide 161 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: GOOGLE &. com Disappear Briefly GOOGLE disappears from Web (2005. 05) Ø Gone for 15 minutes 7 May 2005 Ø Glitch in DNS Ø Drew attention to concerns over DNS stability Ø National Research Council issued report criticizing state of DNS infrastructure http: //www 7. nationalacademies. org/cstb/pub_d ns. html Historical note: 2000. 08. 23: 4 of 13 root DNS servers failed Ø All access (http, ftp, smtp) to entire. com domain blocked for 1 hour worldwide 161 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Backhoe Attacks Ø 1997. 06 -- Republic of Buryatiya q. Thief removed 60 m copper cable q. Shut down all external communications 5 hours q. Estimated cost ~$135, 000 Ø 1997. 06 -- Khazakhstan q 2 thieves began stealing copper from highvoltage electrical power line -- while it was live qsoon they weren’t Ø 1997. 06 -- Florence, NJ qconstruction crew sliced through major UUNet backbone 162 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Backhoe Attacks Ø 1997. 06 -- Republic of Buryatiya q. Thief removed 60 m copper cable q. Shut down all external communications 5 hours q. Estimated cost ~$135, 000 Ø 1997. 06 -- Khazakhstan q 2 thieves began stealing copper from highvoltage electrical power line -- while it was live qsoon they weren’t Ø 1997. 06 -- Florence, NJ qconstruction crew sliced through major UUNet backbone 162 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: More Backhoe Attacks Ø 1997. 10: Dump-truck driver leaves truck bed up, rips telephone cables – 119, 000 Sprint users out of service for 4 hours Ø 1998. 02: Illuminet cables severed in Illinois – phone/ISP service out all over eastern seaboard for AT&T, Teleport, Bell Atlantic mobile Ø 2001. 03: Thieves attempted to steal copper cable in Ontario Canada. They actually cut a fiberoptic cable and wiped out Internet service for 300, 000 users. Then while workers were repairing the damage, rodents attacked the exposed cable and eliminated service once more. 163 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: More Backhoe Attacks Ø 1997. 10: Dump-truck driver leaves truck bed up, rips telephone cables – 119, 000 Sprint users out of service for 4 hours Ø 1998. 02: Illuminet cables severed in Illinois – phone/ISP service out all over eastern seaboard for AT&T, Teleport, Bell Atlantic mobile Ø 2001. 03: Thieves attempted to steal copper cable in Ontario Canada. They actually cut a fiberoptic cable and wiped out Internet service for 300, 000 users. Then while workers were repairing the damage, rodents attacked the exposed cable and eliminated service once more. 163 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: Tunnel Fire Derails Internet Service Ø Train derailed in Baltimore tunnel (2001. 07) Ø Damaged fiber-optic cables Ø Affected Internet service, telephony across USA q. World. Com, PSINet, Above. Net q. Delays on eastern seaboard q. Problems even in Seattle, Los Angeles 164 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: Tunnel Fire Derails Internet Service Ø Train derailed in Baltimore tunnel (2001. 07) Ø Damaged fiber-optic cables Ø Affected Internet service, telephony across USA q. World. Com, PSINet, Above. Net q. Delays on eastern seaboard q. Problems even in Seattle, Los Angeles 164 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Do. S: What if GPS Fails? Ø As if 2003. 04: 18 of 28 GPS satellites q. Operating beyond intended lifespan or q. Have equipment failure Ø GPS failure would affect q. Civil aviation q. Trucking q. Shipping q. Telecommunications Ø Internet backbone operators use GPS time stamps 165 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Do. S: What if GPS Fails? Ø As if 2003. 04: 18 of 28 GPS satellites q. Operating beyond intended lifespan or q. Have equipment failure Ø GPS failure would affect q. Civil aviation q. Trucking q. Shipping q. Telecommunications Ø Internet backbone operators use GPS time stamps 165 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 DISCUSSION 166 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
DISCUSSION 166 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
 Resume at 13: 14: 54 167 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55
Resume at 13: 14: 54 167 Copyright © 2005 M. E. Kabay. All rights reserved. 09: 05 -11: 55


