945699bc032c25e5d5dfd2f16dc54039.ppt
- Количество слайдов: 85
 Information Technology Audit & Forensic Techniques ACG 6936 Summer 2007 Grover Kearns, Ph. D, CPA 1
Information Technology Audit & Forensic Techniques ACG 6936 Summer 2007 Grover Kearns, Ph. D, CPA 1
 IT Forensic Techniques for Auditors Presentation Focus n n n Importance of IT Forensic Techniques to Organizations Importance of IT Forensic Techniques to Auditors Audit Goals of Forensic Investigation Digital Crime Scene Investigation Illustration of Forensic Tools A Forensic Protocol 2
IT Forensic Techniques for Auditors Presentation Focus n n n Importance of IT Forensic Techniques to Organizations Importance of IT Forensic Techniques to Auditors Audit Goals of Forensic Investigation Digital Crime Scene Investigation Illustration of Forensic Tools A Forensic Protocol 2
 Forensic Computing Defined Forensic Computing is the process of identifying, preserving, analyzing, and presenting digital evidence in a manner that is legally acceptable in a court of law Our interest is in … n Identifying and preserving evidence, n “post-mortem” system analysis to determine extent and nature of attack, and n the forensic framework 3
Forensic Computing Defined Forensic Computing is the process of identifying, preserving, analyzing, and presenting digital evidence in a manner that is legally acceptable in a court of law Our interest is in … n Identifying and preserving evidence, n “post-mortem” system analysis to determine extent and nature of attack, and n the forensic framework 3
 Importance of IT Forensic Techniques to Organizations Corporate Fraud Losses in 2004 n Cost companies an average loss of assets over $ 1. 7 million n A 50% increase over 2003 n Over one third of these frauds were discovered by accident, making "chance" the most common fraud detection tool. q Price. Waterhouse. Coopers, Global Economic Crime Survey 2005 4
Importance of IT Forensic Techniques to Organizations Corporate Fraud Losses in 2004 n Cost companies an average loss of assets over $ 1. 7 million n A 50% increase over 2003 n Over one third of these frauds were discovered by accident, making "chance" the most common fraud detection tool. q Price. Waterhouse. Coopers, Global Economic Crime Survey 2005 4
 Importance of IT Forensic Techniques to Organizations The New Corporate Environment Sarbanes-Oxley 2002 n COSO and COBIT n SAS 94 and SAS 99 n ISO 9000 and ISO 17799 n Gramm-Leach-Bliley Act n US Foreign Corrupt Practices Act …all of these have altered the corporate environment and made forensic techniques a necessity! n 5
Importance of IT Forensic Techniques to Organizations The New Corporate Environment Sarbanes-Oxley 2002 n COSO and COBIT n SAS 94 and SAS 99 n ISO 9000 and ISO 17799 n Gramm-Leach-Bliley Act n US Foreign Corrupt Practices Act …all of these have altered the corporate environment and made forensic techniques a necessity! n 5
 Importance of IT Forensic Techniques to Auditors SAS 99 SAS No. 99 - Consideration of Fraud in a Financial Statement Audit - requires auditors to … n Understand fraud n Gather evidence about the existence of fraud n Identify and respond to fraud risks n Document and communicate findings n Incorporate a technology focus 6
Importance of IT Forensic Techniques to Auditors SAS 99 SAS No. 99 - Consideration of Fraud in a Financial Statement Audit - requires auditors to … n Understand fraud n Gather evidence about the existence of fraud n Identify and respond to fraud risks n Document and communicate findings n Incorporate a technology focus 6
 Importance of IT Forensic Techniques to Organizations Intellectual Property Losses n n Rapid increase in theft of IP – 323% over five year period 1999 -2004 75% of estimated annual losses were to an employee, supplier or contractor Digital IP is more susceptible to theft Employees may not view it as theft 7
Importance of IT Forensic Techniques to Organizations Intellectual Property Losses n n Rapid increase in theft of IP – 323% over five year period 1999 -2004 75% of estimated annual losses were to an employee, supplier or contractor Digital IP is more susceptible to theft Employees may not view it as theft 7
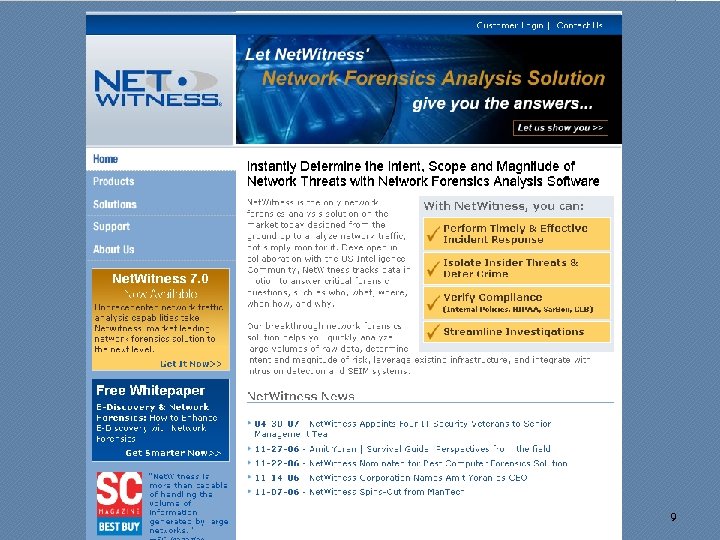
 Importance of IT Forensic Techniques to Organizations Network Fraud n n n Companies now highly reliant on networks Networks increasingly vulnerable to attacks Viruses, Trojans, Rootkits can add backdoors Social Engineering including Phishing and Pharming Confidential and proprietary information can be compromised Can create a corporate liability 8
Importance of IT Forensic Techniques to Organizations Network Fraud n n n Companies now highly reliant on networks Networks increasingly vulnerable to attacks Viruses, Trojans, Rootkits can add backdoors Social Engineering including Phishing and Pharming Confidential and proprietary information can be compromised Can create a corporate liability 8
 9
9
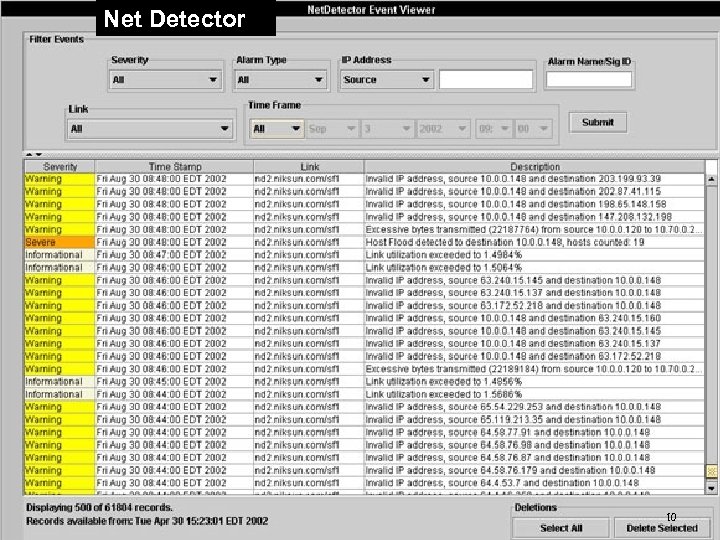 Net Detector 10
Net Detector 10
 Importance of IT Forensic Techniques to Organizations Security Challenges n n n Technology expanding and becoming more sophisticated Processes evolving and integrating with technologies People under trained Technology Policies outdated People Organizations at risk Policies Processes 11
Importance of IT Forensic Techniques to Organizations Security Challenges n n n Technology expanding and becoming more sophisticated Processes evolving and integrating with technologies People under trained Technology Policies outdated People Organizations at risk Policies Processes 11
 12
12
 13
13
 Importance of IT Forensic Techniques to Auditors Majority of fraud is uncovered by chance n Auditors often do not look for fraud n Prosecution requires evidence n Value of IT assets growing Treadway Commission Study … n Undetected fraud was a factor in one-half of the 450 lawsuits against independent auditors. n 14
Importance of IT Forensic Techniques to Auditors Majority of fraud is uncovered by chance n Auditors often do not look for fraud n Prosecution requires evidence n Value of IT assets growing Treadway Commission Study … n Undetected fraud was a factor in one-half of the 450 lawsuits against independent auditors. n 14
 Importance of IT Forensic Techniques to Auditors Auditor’s Knowledge, Skills, Abilities Accounting n Auditing n IT (weak) Needed … n Increased IT knowledge n Fraud and forensic accounting knowledge n Forensic investigative and analytical skills and abilities n 15
Importance of IT Forensic Techniques to Auditors Auditor’s Knowledge, Skills, Abilities Accounting n Auditing n IT (weak) Needed … n Increased IT knowledge n Fraud and forensic accounting knowledge n Forensic investigative and analytical skills and abilities n 15
 Importance of IT Forensic Techniques to Auditors Knowledge, Skills, Abilities: Needs Auditor’s need KSAs to … n Build a digital audit trail n Collect “usable” courtroom electronic evidence n Trace an unauthorized system user n Recommend or review security policies n Understand computer fraud techniques n Analyze and valuate incurred losses 16
Importance of IT Forensic Techniques to Auditors Knowledge, Skills, Abilities: Needs Auditor’s need KSAs to … n Build a digital audit trail n Collect “usable” courtroom electronic evidence n Trace an unauthorized system user n Recommend or review security policies n Understand computer fraud techniques n Analyze and valuate incurred losses 16
 Importance of IT Forensic Techniques to Auditors KSA Needs (cont. ) n n Understand information collected from various computer logs Be familiar with the Internet, web servers, firewalls, attack methodology, security procedures & penetration testing Understand organizational and legal protocols for incident handling Establish relationships with IT, risk management, security, law enforcement 17
Importance of IT Forensic Techniques to Auditors KSA Needs (cont. ) n n Understand information collected from various computer logs Be familiar with the Internet, web servers, firewalls, attack methodology, security procedures & penetration testing Understand organizational and legal protocols for incident handling Establish relationships with IT, risk management, security, law enforcement 17
 Audit Goals of a Forensic Investigation n n n Uncover fraudulent or criminal cyber activity Isolate evidentiary matter (freeze scene) Document the scene Create a chain-of-custody for evidence Analyze digital information Communicate results 18
Audit Goals of a Forensic Investigation n n n Uncover fraudulent or criminal cyber activity Isolate evidentiary matter (freeze scene) Document the scene Create a chain-of-custody for evidence Analyze digital information Communicate results 18
 Audit Goals of a Forensic Investigation Immediate Concerns n n What is level of certainty that a problem exists? Is this a criminal act? q q n n n Child porn, money laundering When should law enforcement be involved? Can the system be isolated? Is a subpoena necessary? Is the intrusion internal or external? Are suspects known? Is extent of loss/damage known? 19
Audit Goals of a Forensic Investigation Immediate Concerns n n What is level of certainty that a problem exists? Is this a criminal act? q q n n n Child porn, money laundering When should law enforcement be involved? Can the system be isolated? Is a subpoena necessary? Is the intrusion internal or external? Are suspects known? Is extent of loss/damage known? 19
 Audit Goals of a Forensic Investigation Immediate Response n n n n Shut down computer (pull plug) Bit-stream mirror-image of data Begin a traceback to identify possible log locations Contact system administrators on intermediate sites to request log preservation Contain damage Collect local logs Begin documentation 20
Audit Goals of a Forensic Investigation Immediate Response n n n n Shut down computer (pull plug) Bit-stream mirror-image of data Begin a traceback to identify possible log locations Contact system administrators on intermediate sites to request log preservation Contain damage Collect local logs Begin documentation 20
 Audit Goals of a Forensic Investigation Continuing Investigation n n n Implement measures to stop further loss Communicate to management and audit committee regularly Analyze copy of digital files Ascertain level and nature of loss Identify perpetrator(s) Develop theories about motives Maintain chain-of-custody 21
Audit Goals of a Forensic Investigation Continuing Investigation n n n Implement measures to stop further loss Communicate to management and audit committee regularly Analyze copy of digital files Ascertain level and nature of loss Identify perpetrator(s) Develop theories about motives Maintain chain-of-custody 21
 Digital Crime Scene Investigation Goal: Determine what fraud events occurred by using digital evidence Three Phases: q Preserve & Document Scene q Analyze/Search & Document Data q Reconstruct & Document Fraud Event 22
Digital Crime Scene Investigation Goal: Determine what fraud events occurred by using digital evidence Three Phases: q Preserve & Document Scene q Analyze/Search & Document Data q Reconstruct & Document Fraud Event 22
 Digital Crime Scene Investigation Scene Preservation & Documentation n n Goal: Preserve the state of as many digital objects as possible and document the crime scene. Methods: q q q n Shut system down Unplug (best) Do nothing Bag and tag 23
Digital Crime Scene Investigation Scene Preservation & Documentation n n Goal: Preserve the state of as many digital objects as possible and document the crime scene. Methods: q q q n Shut system down Unplug (best) Do nothing Bag and tag 23
 Digital Crime Scene Investigation Investigative Axiom Treat every incident as if it will end up in a criminal prosecution. 24
Digital Crime Scene Investigation Investigative Axiom Treat every incident as if it will end up in a criminal prosecution. 24
 Digital Crime Scene Investigation Incidents & Investigations n n Incident/Crime: An event that violates a policy or law Investigation: A process that develops and tests hypotheses to answer questions about events that occurred 25
Digital Crime Scene Investigation Incidents & Investigations n n Incident/Crime: An event that violates a policy or law Investigation: A process that develops and tests hypotheses to answer questions about events that occurred 25
 Audit Goals of a Forensic Investigation Rules of Evidence n n n Complete Authentic Admissible Reliable Believable 26
Audit Goals of a Forensic Investigation Rules of Evidence n n n Complete Authentic Admissible Reliable Believable 26
 Audit Goals of a Forensic Investigation Requirements for Evidence Computer logs … n Must not be modifiable n Must be complete n Appropriate retention rules 27
Audit Goals of a Forensic Investigation Requirements for Evidence Computer logs … n Must not be modifiable n Must be complete n Appropriate retention rules 27
 Digital Crime Scene Investigation Problems with Digital Investigation n n Timing essential – electronic evidence volatile Auditor may violate rules of evidence NEVER work directly on the evidence Skills needed to recover deleted data or encrypted data 28
Digital Crime Scene Investigation Problems with Digital Investigation n n Timing essential – electronic evidence volatile Auditor may violate rules of evidence NEVER work directly on the evidence Skills needed to recover deleted data or encrypted data 28
 Digital Crime Scene Investigation Extract, process, interpret n n n Work on the imaged data or “safe copy” Data extracted may be in binary form Process data to convert it to understandable form q q n Reverse-engineer to extract disk partition information, file systems, directories, files, etc Software available for this purpose Interpret the data – search for key words, phrases, etc. 29
Digital Crime Scene Investigation Extract, process, interpret n n n Work on the imaged data or “safe copy” Data extracted may be in binary form Process data to convert it to understandable form q q n Reverse-engineer to extract disk partition information, file systems, directories, files, etc Software available for this purpose Interpret the data – search for key words, phrases, etc. 29
 Digital Crime Scene Investigation Technology n n n Magnetic disks contain data after deletion Overwritten data may still be salvaged Memory still contains data after switch-off Swap files and temporary files store data Most OS’s perform extensive logging (so do network routers) 30
Digital Crime Scene Investigation Technology n n n Magnetic disks contain data after deletion Overwritten data may still be salvaged Memory still contains data after switch-off Swap files and temporary files store data Most OS’s perform extensive logging (so do network routers) 30
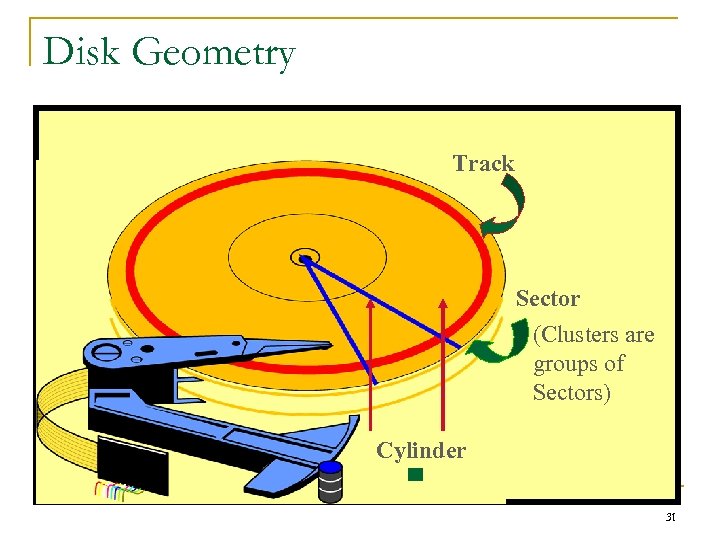 Disk Geometry Track Sector (Clusters are groups of Sectors) Cylinder 31
Disk Geometry Track Sector (Clusters are groups of Sectors) Cylinder 31
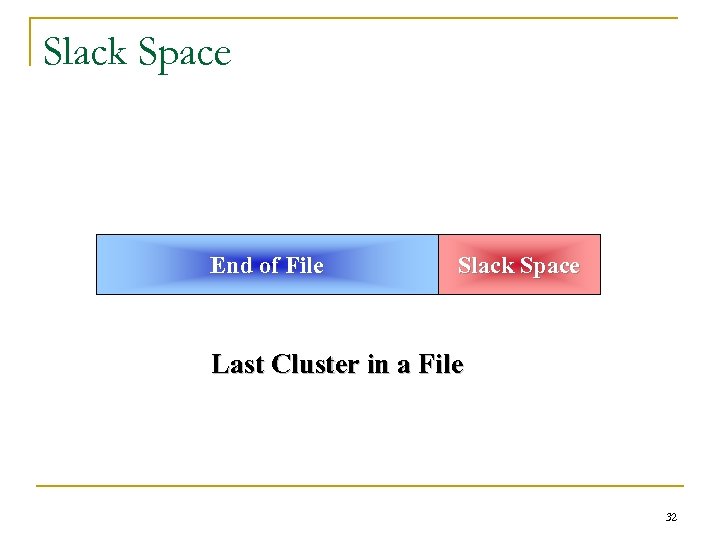 Slack Space End of File Slack Space Last Cluster in a File 32
Slack Space End of File Slack Space Last Cluster in a File 32
 Digital Crime Scene Investigation Order of Volatility n Preserve most volatile evidence first q Registers, caches, peripheral memory q Memory (kernel, physical) q Network state q Running processes q Disk q Floppies, backup media q CD-ROMs, printouts 33
Digital Crime Scene Investigation Order of Volatility n Preserve most volatile evidence first q Registers, caches, peripheral memory q Memory (kernel, physical) q Network state q Running processes q Disk q Floppies, backup media q CD-ROMs, printouts 33
 Digital Crime Scene Investigation Digital Forensic Investigation A process that uses science and technology to examine digital objects and that develops and tests theories, which can be entered into a court of law, to answer questions about events that occurred. IT Forensic Techniques are used to capture and analyze electronic data and develop theories. 34
Digital Crime Scene Investigation Digital Forensic Investigation A process that uses science and technology to examine digital objects and that develops and tests theories, which can be entered into a court of law, to answer questions about events that occurred. IT Forensic Techniques are used to capture and analyze electronic data and develop theories. 34
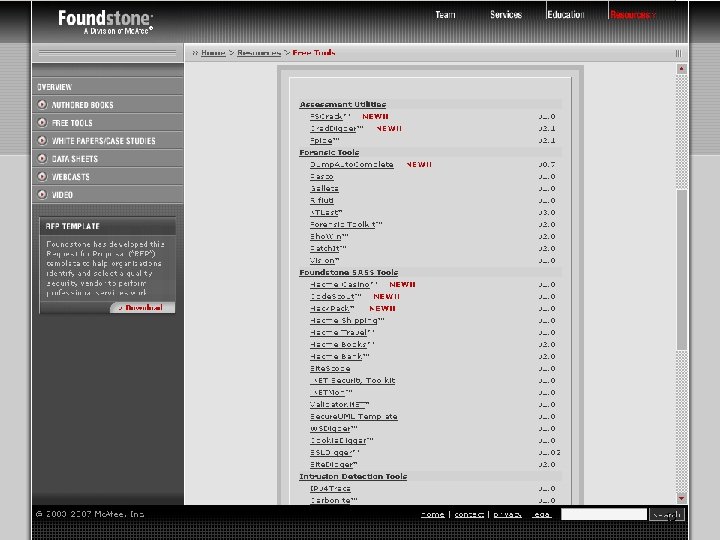
 Illustration of Forensic Tools Forensic Software Tools are used for … n Data imaging n Data recovery n Data integrity n Data extraction n Forensic Analysis n Monitoring 35
Illustration of Forensic Tools Forensic Software Tools are used for … n Data imaging n Data recovery n Data integrity n Data extraction n Forensic Analysis n Monitoring 35
 Data Imaging En. Case n n n Reduces internal investigation costs Platform independent Automated analysis saves time Supports electronic records audit Creates logical evidence files — eliminating need to capture entire hard drives 36
Data Imaging En. Case n n n Reduces internal investigation costs Platform independent Automated analysis saves time Supports electronic records audit Creates logical evidence files — eliminating need to capture entire hard drives 36
 Data Imaging En. Case n Previews computers over the network to determine whether relevant evidence exists: q q q q q Unallocated/allocated space Deleted files File slack Volume slack File system attributes CD ROMs/DVDs Mounted Fire. Wire and USB devices Mounted encrypted volumes Mounted thumb drives 37
Data Imaging En. Case n Previews computers over the network to determine whether relevant evidence exists: q q q q q Unallocated/allocated space Deleted files File slack Volume slack File system attributes CD ROMs/DVDs Mounted Fire. Wire and USB devices Mounted encrypted volumes Mounted thumb drives 37
 Data Recovery File Recovery with PC Inspector 38
Data Recovery File Recovery with PC Inspector 38
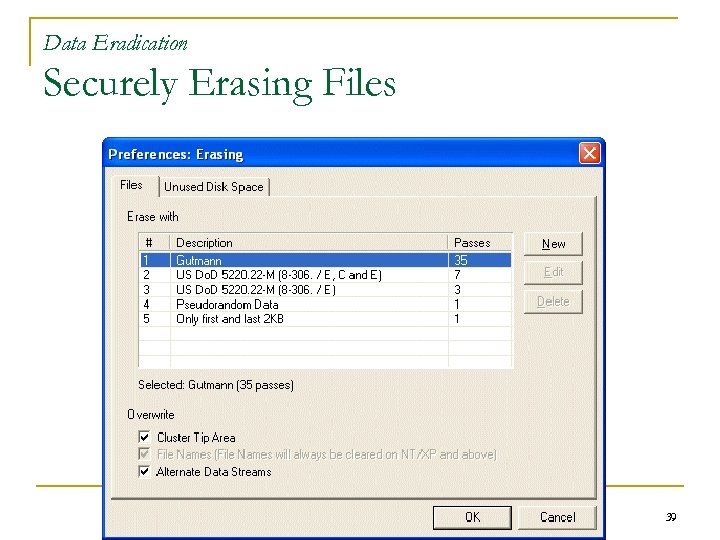 Data Eradication Securely Erasing Files 39
Data Eradication Securely Erasing Files 39
 Data Integrity MD 5 Message Digest – a hashing algorithm used to generate a checksum n Available online as freeware n Any changes to file will change the checksum Use: n Generate MD 5 of system or critical files regularly n Keep checksums in a secure place to compare against later if integrity is questioned n 40
Data Integrity MD 5 Message Digest – a hashing algorithm used to generate a checksum n Available online as freeware n Any changes to file will change the checksum Use: n Generate MD 5 of system or critical files regularly n Keep checksums in a secure place to compare against later if integrity is questioned n 40
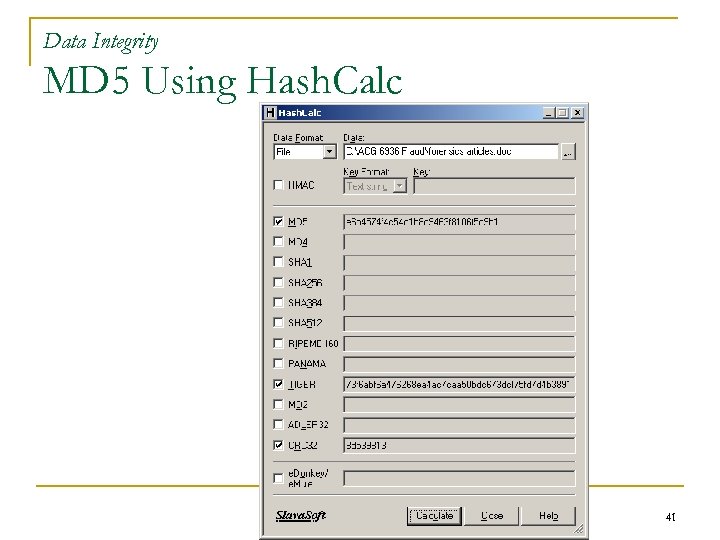 Data Integrity MD 5 Using Hash. Calc 41
Data Integrity MD 5 Using Hash. Calc 41
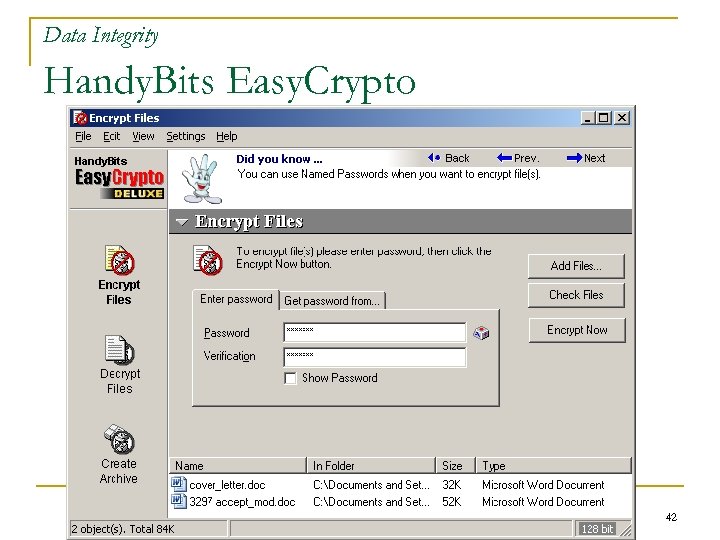 Data Integrity Handy. Bits Easy. Crypto 42
Data Integrity Handy. Bits Easy. Crypto 42
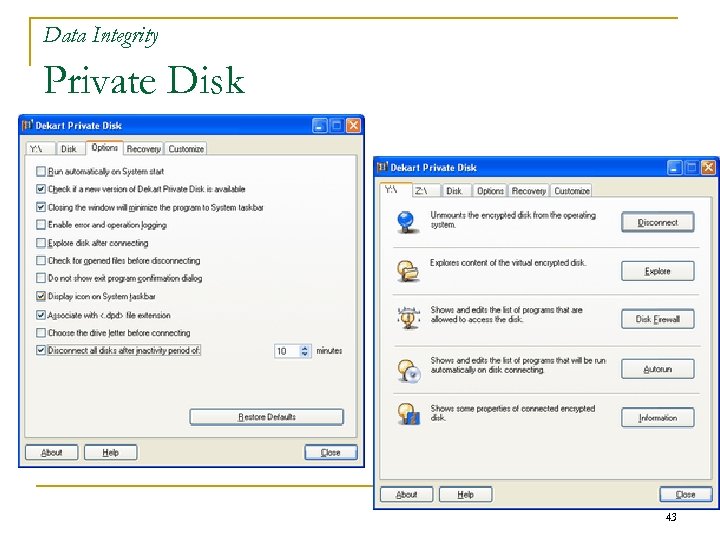 Data Integrity Private Disk 43
Data Integrity Private Disk 43
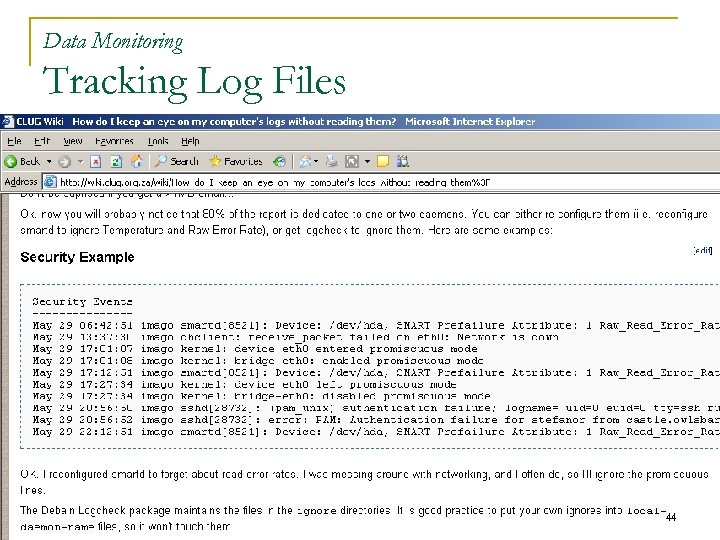 Data Monitoring Tracking Log Files 44
Data Monitoring Tracking Log Files 44
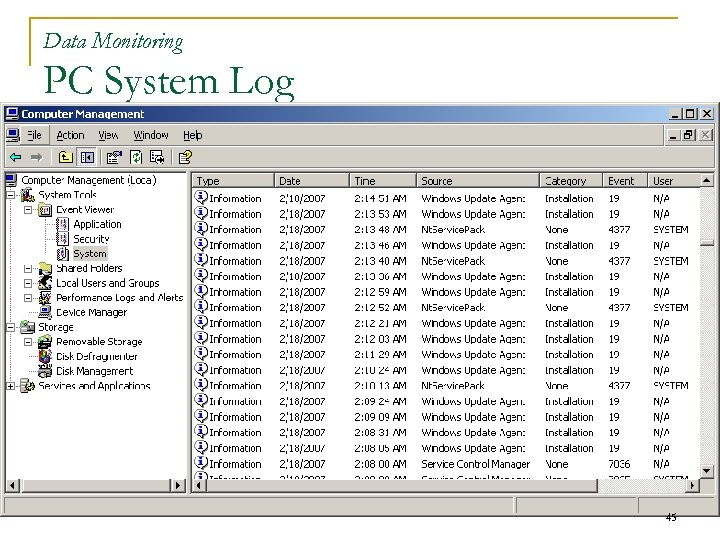 Data Monitoring PC System Log 45
Data Monitoring PC System Log 45
 Security Software Log Entries 46
Security Software Log Entries 46
 47
47
 Free Log Tools 48
Free Log Tools 48
 49
49
 Audit Command Language (ACL) ACL is the market leader in computerassisted audit technology and is an established forensics tool. Clientele includes … n 70 percent of the Fortune 500 companies n over two-thirds of the Global 500 n the Big Four public accounting firms n 50
Audit Command Language (ACL) ACL is the market leader in computerassisted audit technology and is an established forensics tool. Clientele includes … n 70 percent of the Fortune 500 companies n over two-thirds of the Global 500 n the Big Four public accounting firms n 50
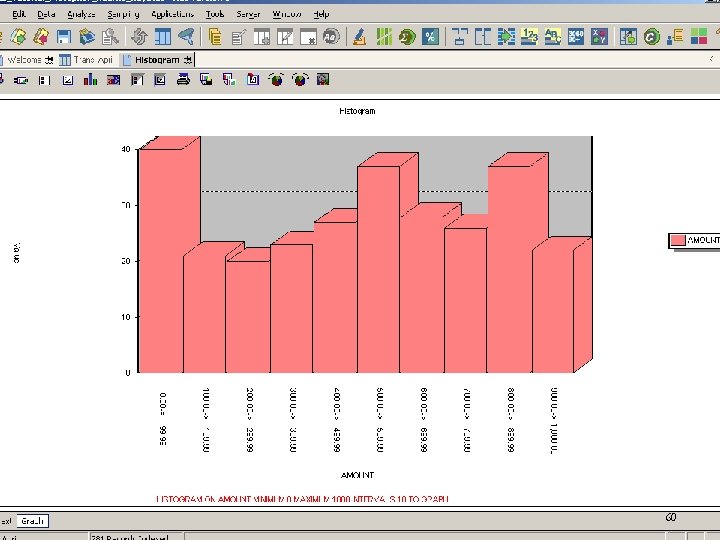
 Forensic Tools Audit Command Language ACL is a computer data extraction and analytical audit tool with audit capabilities … n. Statistics n. Duplicates and Gaps n. Stratify and Classify n. Sampling n. Benford Analysis 51
Forensic Tools Audit Command Language ACL is a computer data extraction and analytical audit tool with audit capabilities … n. Statistics n. Duplicates and Gaps n. Stratify and Classify n. Sampling n. Benford Analysis 51
 52
52
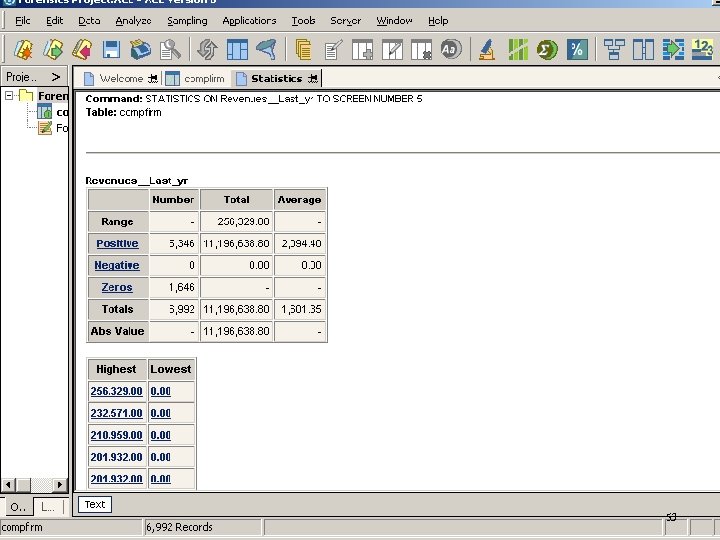 53
53
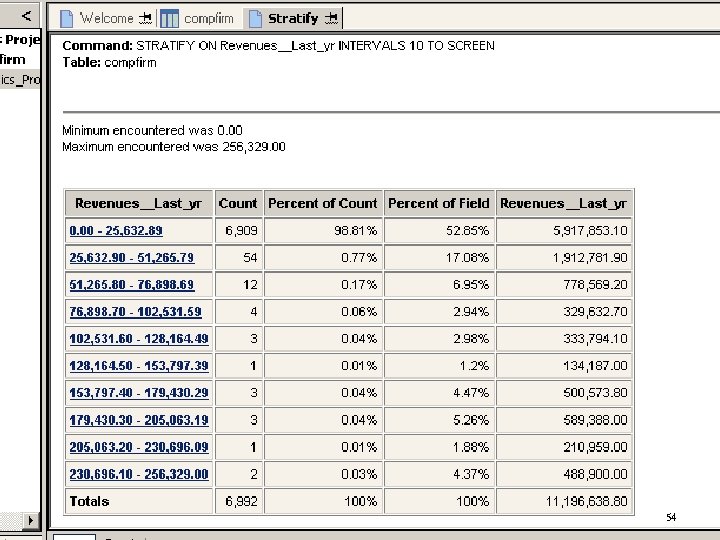 54
54
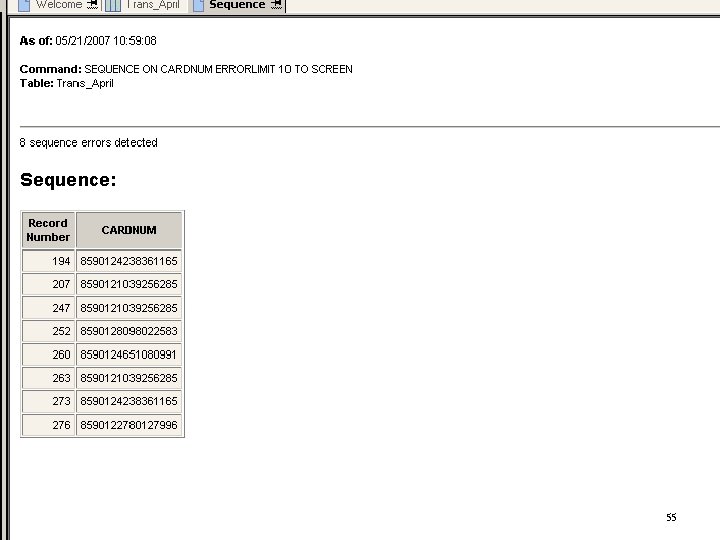 55
55
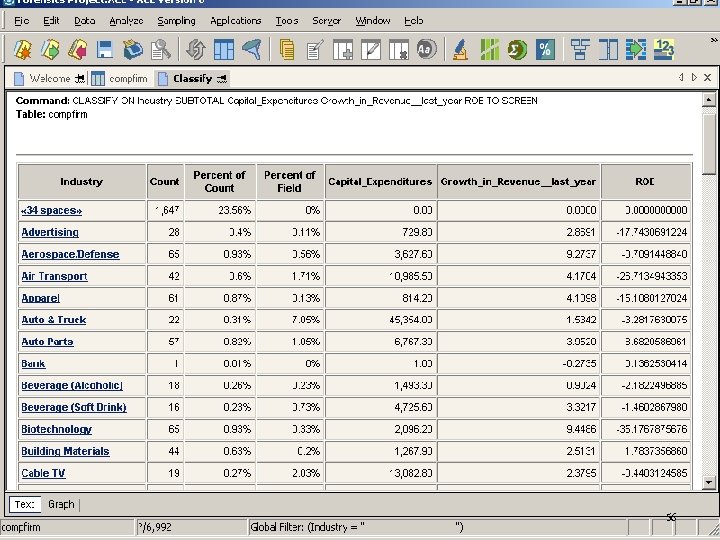 56
56
 Forensic Tools: ACL Benford Analysis n n States that the leading digit in some numerical series is follows an exponential rather than normal distribution Applies to a wide variety of figures: financial results, electricity bills, street addresses, stock prices, population numbers, death rates, lengths of rivers 57
Forensic Tools: ACL Benford Analysis n n States that the leading digit in some numerical series is follows an exponential rather than normal distribution Applies to a wide variety of figures: financial results, electricity bills, street addresses, stock prices, population numbers, death rates, lengths of rivers 57
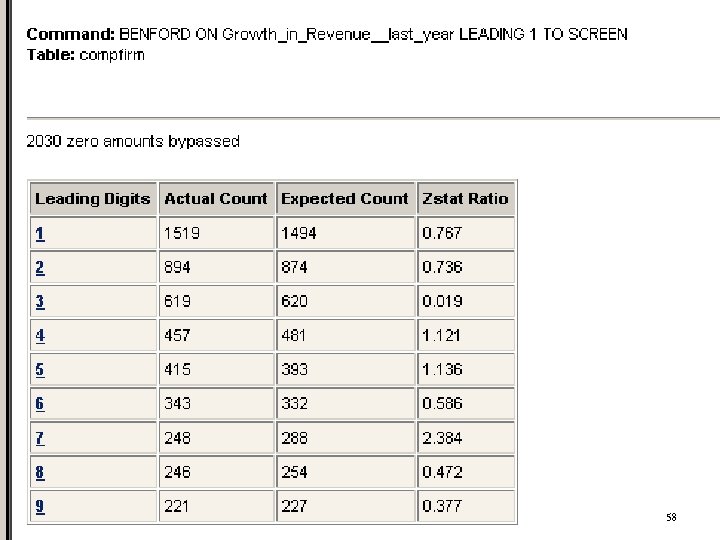 58
58
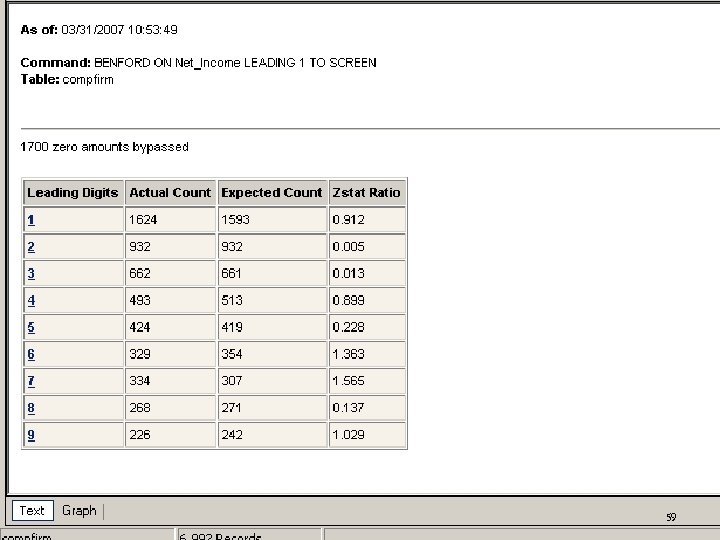 59
59
 60
60
 Data Monitoring Employee Internet Activity Spector captures employee web activity including keystrokes, email, and snapshots to answer questions like: n Which employees are spending the most time surfing web sites? n Which employees chat the most? n Who is sending the most emails with attachments? n Who is arriving to work late and leaving early? n What are my employees searching for on the Internet? 61
Data Monitoring Employee Internet Activity Spector captures employee web activity including keystrokes, email, and snapshots to answer questions like: n Which employees are spending the most time surfing web sites? n Which employees chat the most? n Who is sending the most emails with attachments? n Who is arriving to work late and leaving early? n What are my employees searching for on the Internet? 61
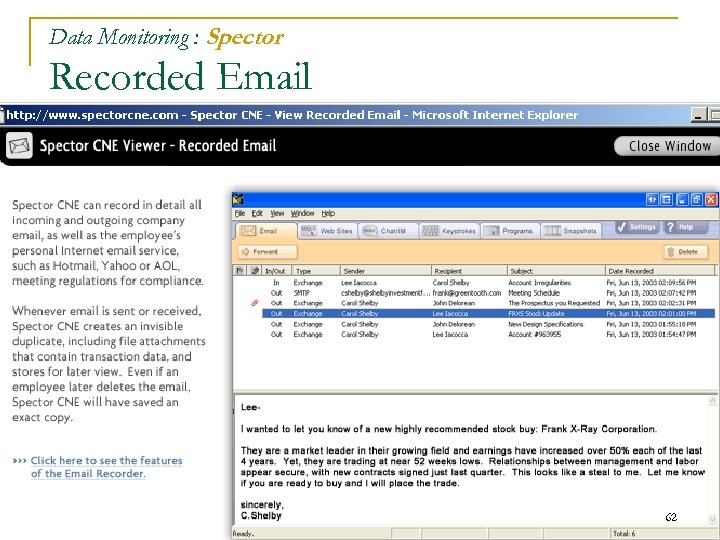 Data Monitoring : Spector Recorded Email 62
Data Monitoring : Spector Recorded Email 62
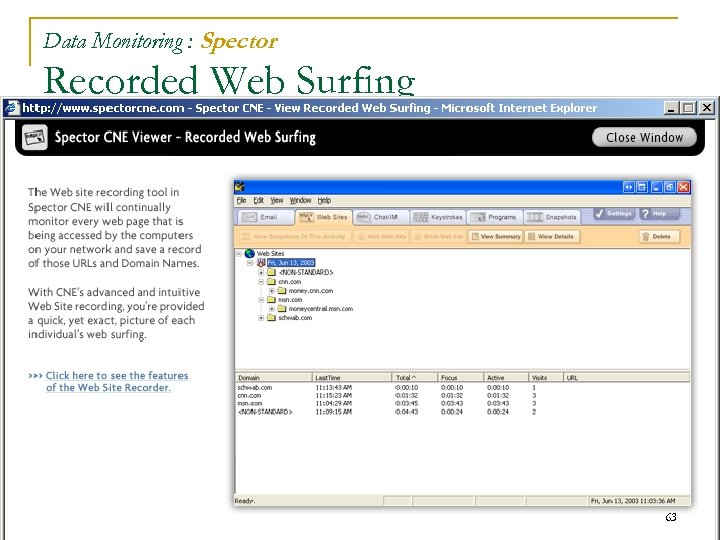 Data Monitoring : Spector Recorded Web Surfing 63
Data Monitoring : Spector Recorded Web Surfing 63
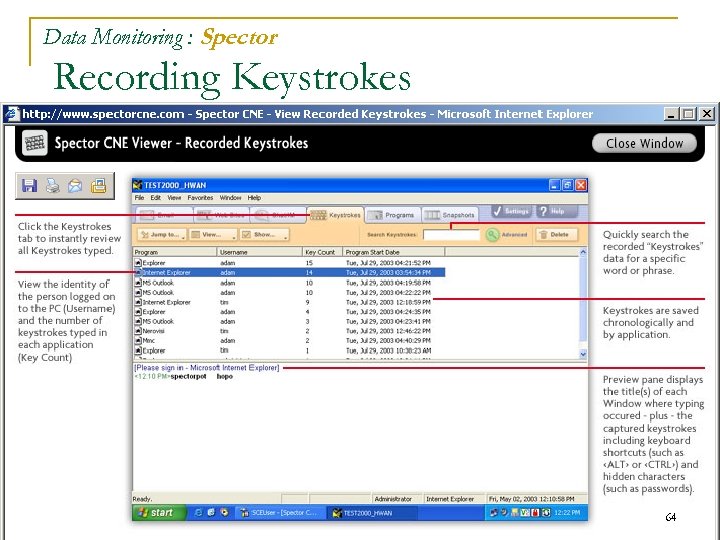 Data Monitoring : Spector Recording Keystrokes 64
Data Monitoring : Spector Recording Keystrokes 64
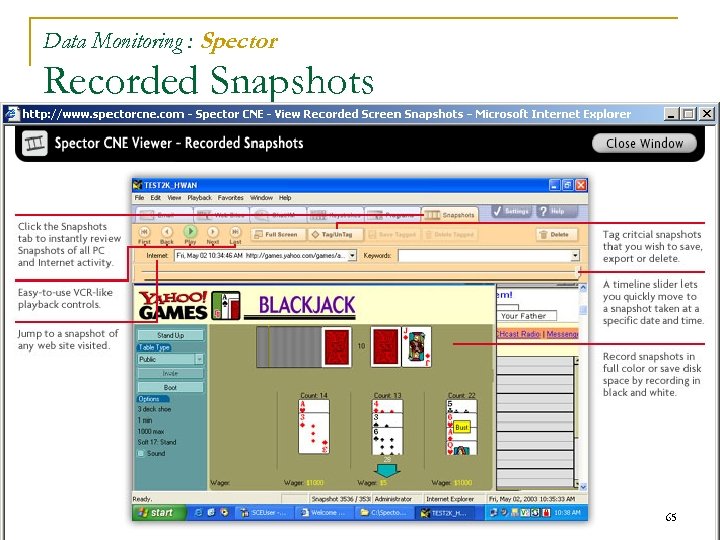 Data Monitoring : Spector Recorded Snapshots 65
Data Monitoring : Spector Recorded Snapshots 65
 66
66
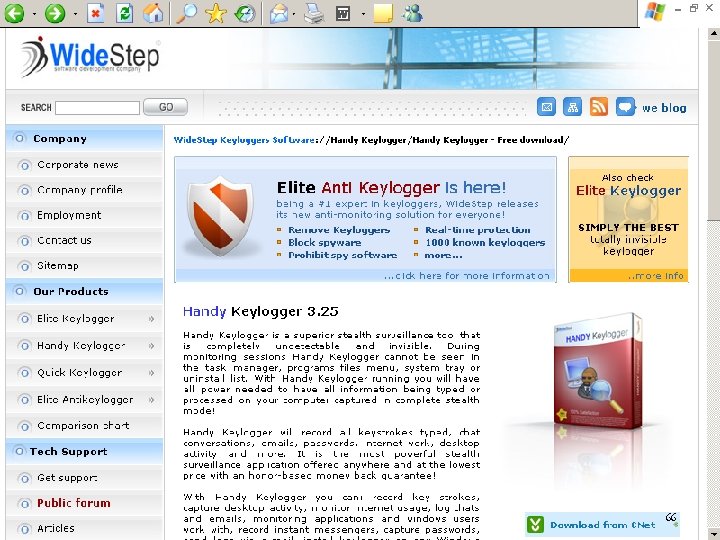
 Data Capture : Key Log Hardware Key. Katcher § Records chat, e-mail, internet & more § Is easier to use than parental control software § Identifies internet addresses § Uses no system resources § Works on all PC operating systems § Undetectable by software www. lakeshoretechnology. com 67
Data Capture : Key Log Hardware Key. Katcher § Records chat, e-mail, internet & more § Is easier to use than parental control software § Identifies internet addresses § Uses no system resources § Works on all PC operating systems § Undetectable by software www. lakeshoretechnology. com 67
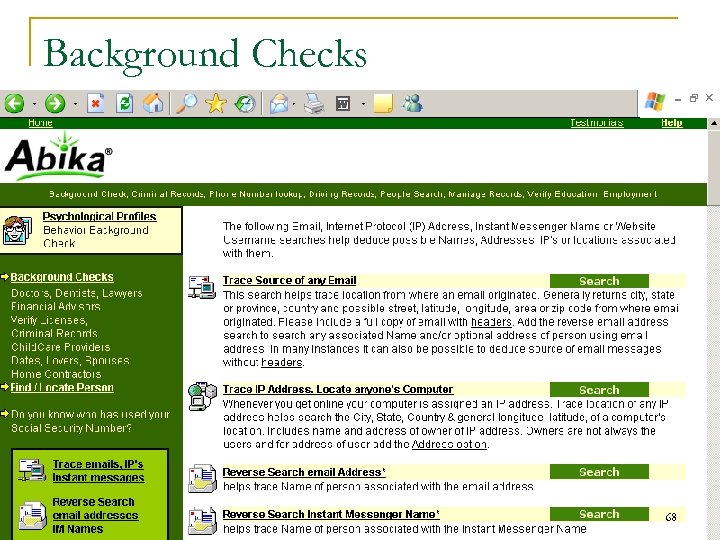 Background Checks 68
Background Checks 68
 http: //www. expressmetrix. com/solutions/ 69
http: //www. expressmetrix. com/solutions/ 69
 70
70
 71
71
 72
72
 73
73
 Developing a Forensic Protocol n n n The response plan must include a coordinated effort that integrates a number of organizational areas and possibly external areas Response to fraud events must have top priority Technology Key players must exist at all People major organizational Policies locations Processes 74
Developing a Forensic Protocol n n n The response plan must include a coordinated effort that integrates a number of organizational areas and possibly external areas Response to fraud events must have top priority Technology Key players must exist at all People major organizational Policies locations Processes 74
 Developing a Forensic Protocol End-to-End Forensic Analysis First rule of end-to-end forensic digital analysis q q Primary evidence must always be corroborated by at least one other piece of relevant primary evidence to be considered a valid part of the evidence chain. Evidence that does not fit this description, but does serve to corroborate some other piece of evidence without itself being corroborated, is considered to be secondary evidence. Exception: the first piece of evidence in the chain from the Identification layer 75
Developing a Forensic Protocol End-to-End Forensic Analysis First rule of end-to-end forensic digital analysis q q Primary evidence must always be corroborated by at least one other piece of relevant primary evidence to be considered a valid part of the evidence chain. Evidence that does not fit this description, but does serve to corroborate some other piece of evidence without itself being corroborated, is considered to be secondary evidence. Exception: the first piece of evidence in the chain from the Identification layer 75
 A Forensic Protocol Security Exposures Organizations may possess critical technology skills but … n Skills are locked in towers – IT, Security, Accounting, Auditing n Skills are centralized while fraud events can be decentralized n Skills are absent – vacations, illnesses, etc 76
A Forensic Protocol Security Exposures Organizations may possess critical technology skills but … n Skills are locked in towers – IT, Security, Accounting, Auditing n Skills are centralized while fraud events can be decentralized n Skills are absent – vacations, illnesses, etc 76
 A Forensic Protocol The Role of Policies n n They define the actions you can take They must be clear and simple to understand The employee must acknowledge that he or she read them, understands them and will comply with them They can’t violate law 77
A Forensic Protocol The Role of Policies n n They define the actions you can take They must be clear and simple to understand The employee must acknowledge that he or she read them, understands them and will comply with them They can’t violate law 77
 A Forensic Protocol Forensic Response Control Incident Response Planning … n Identify needs and objectives n Identify resources n Create policies, procedures n Create a forensic protocol n Acquire needed skills n Train n Monitor 78
A Forensic Protocol Forensic Response Control Incident Response Planning … n Identify needs and objectives n Identify resources n Create policies, procedures n Create a forensic protocol n Acquire needed skills n Train n Monitor 78
 A Forensic Protocol Documenting the Scene n n n Note time, date, persons present Photograph and video the scene Draw a layout of the scene Search for notes (passwords) that might be useful If possible freeze the system such that the current memory, swap files, and even CPU registers are saved or documented 79
A Forensic Protocol Documenting the Scene n n n Note time, date, persons present Photograph and video the scene Draw a layout of the scene Search for notes (passwords) that might be useful If possible freeze the system such that the current memory, swap files, and even CPU registers are saved or documented 79
 A Forensic Protocol n n First responder triggers alert Team response q q n Freeze scene Begin documentation Auditors begin analysis q q q Protect chain-of-custody Reconstruct events and develop theories Communicate results of analysis 80
A Forensic Protocol n n First responder triggers alert Team response q q n Freeze scene Begin documentation Auditors begin analysis q q q Protect chain-of-custody Reconstruct events and develop theories Communicate results of analysis 80
 A Forensic Protocol Summary Ensure appropriate policies n Preserve the crime scene (victim computer) n Act immediately to identify and preserve logs on intermediate systems n Conduct your investigation n Obtain subpoenas or contact law enforcement if necessary Key: Coordination between functional areas n 81
A Forensic Protocol Summary Ensure appropriate policies n Preserve the crime scene (victim computer) n Act immediately to identify and preserve logs on intermediate systems n Conduct your investigation n Obtain subpoenas or contact law enforcement if necessary Key: Coordination between functional areas n 81
 Conclusion IT Forensic Investigative Skills Can … n Decrease occurrence of fraud n Increase the difficulty of committing fraud n Improve fraud detection methods n Reduce total fraud losses Auditors trained in these skills are more valuable to the organization! 82
Conclusion IT Forensic Investigative Skills Can … n Decrease occurrence of fraud n Increase the difficulty of committing fraud n Improve fraud detection methods n Reduce total fraud losses Auditors trained in these skills are more valuable to the organization! 82
 Questions or Comments? Grover Kearns gkearns@stpt. usf. edu University of South Florida St. Petersburg 83
Questions or Comments? Grover Kearns gkearns@stpt. usf. edu University of South Florida St. Petersburg 83
 Web Resources n ACL q n Eraser q n http: //www. verisign. com Handy. Bits Encryption q n http: //www. download. com/3000 -2242 -10066144. html Veri. Sign q n http: //www. slavasoft. com/hashcalc/index. htm PC Inspector q n http: //www. private-disk. net/ Hash. Calc q n http: //www. heidi. ie/eraser/ Private Disk q n http: //www. acl. com/Default. aspx? bhcp=1 http: //www. handybits. com/ En. Case q http: //www. handybits. com/ 84
Web Resources n ACL q n Eraser q n http: //www. verisign. com Handy. Bits Encryption q n http: //www. download. com/3000 -2242 -10066144. html Veri. Sign q n http: //www. slavasoft. com/hashcalc/index. htm PC Inspector q n http: //www. private-disk. net/ Hash. Calc q n http: //www. heidi. ie/eraser/ Private Disk q n http: //www. acl. com/Default. aspx? bhcp=1 http: //www. handybits. com/ En. Case q http: //www. handybits. com/ 84
 Web Resources (cont. ) Spector http: //www. spectorsoft. com/ n Stolen ID Search https: //www. stolenidsearch. com/ n Abika Background Check http: //www. abika. com/ n Guide to Log Management http: //csrc. nist. gov/publications/nistpubs/800 -92/SP 800 -92. pdf n ACFE Fraud Prevention Checkup n http: //www. acfe. com/documents/Fraud_Prev_Checkup_IA. pdf Net. Witness http: //www. netwitness. com/ n GASP Std V 7. 0 Free Software http: //www. bsa. org/usa/antipiracy/Free-Software-Audit-Tools. cfm n Federal Guidelines for Searches http: //www. cybercrime. gov/searchmanual. htm n 85
Web Resources (cont. ) Spector http: //www. spectorsoft. com/ n Stolen ID Search https: //www. stolenidsearch. com/ n Abika Background Check http: //www. abika. com/ n Guide to Log Management http: //csrc. nist. gov/publications/nistpubs/800 -92/SP 800 -92. pdf n ACFE Fraud Prevention Checkup n http: //www. acfe. com/documents/Fraud_Prev_Checkup_IA. pdf Net. Witness http: //www. netwitness. com/ n GASP Std V 7. 0 Free Software http: //www. bsa. org/usa/antipiracy/Free-Software-Audit-Tools. cfm n Federal Guidelines for Searches http: //www. cybercrime. gov/searchmanual. htm n 85


