f4431b72f9232318fb64b8bba134f402.ppt
- Количество слайдов: 19
 Information Systems Security Officer CS 996: Information Security Management Pavel Margolin 4/20/05
Information Systems Security Officer CS 996: Information Security Management Pavel Margolin 4/20/05
 Overview Who is an ISSO? l Duties and Responsibilities l Planning l Establishing the CIAPP l Info. Sec Functions l Info. Sec in the Government l
Overview Who is an ISSO? l Duties and Responsibilities l Planning l Establishing the CIAPP l Info. Sec Functions l Info. Sec in the Government l
 Who is an ISSO? l l ISSO – Information Systems Security Officer Reports to the Chief Information Officer (CIO), who reports to the CEO. Leader of the Information Security (Info. Sec) organization. Qualifications l l l Manage and organize people Communicate to upper management without much technical details Have enough technical expertise to understand systems and make decisions
Who is an ISSO? l l ISSO – Information Systems Security Officer Reports to the Chief Information Officer (CIO), who reports to the CEO. Leader of the Information Security (Info. Sec) organization. Qualifications l l l Manage and organize people Communicate to upper management without much technical details Have enough technical expertise to understand systems and make decisions
 Duties and Responsibilities Establishing and enforcing Corporate Information Assets Protection Program (CIAPP) l Managing people l Managing the business of CIAPP l Managing CIAPP processes l Hiring Info. Sec staff l Report to upper management l
Duties and Responsibilities Establishing and enforcing Corporate Information Assets Protection Program (CIAPP) l Managing people l Managing the business of CIAPP l Managing CIAPP processes l Hiring Info. Sec staff l Report to upper management l
 Planning l Strategic Plan (ISSSP) l l l Tactical Plan (ITP) l l l Compatible with Strategic Business Plan Long-term direction, goals, and objectives Short-range plan Supports CIAPP and Info. Sec functional goals and objectives Annual Plan (IAP) l l Identify and implement projects to accomplish the goals and objectives in the ISSSP and ITP Plan of projects for the year
Planning l Strategic Plan (ISSSP) l l l Tactical Plan (ITP) l l l Compatible with Strategic Business Plan Long-term direction, goals, and objectives Short-range plan Supports CIAPP and Info. Sec functional goals and objectives Annual Plan (IAP) l l Identify and implement projects to accomplish the goals and objectives in the ISSSP and ITP Plan of projects for the year
 Establishing the CIAPP l l l l l Reasons for the CIAPP Corporate vision, mission, and quality statements Corporate strategic, tactical, and annual business plans Info. Sec vision, mission and quality statements Info. Sec strategic, tactical and annual business plans Information and systems legal, ethical, and best business practices Overall information assets protection plans, policies, and procedures Current CIAPP-related and Info. Sec policies Current CIAPP-related and Info. Sec procedures Other topics as deemed appropriate by the ISSO
Establishing the CIAPP l l l l l Reasons for the CIAPP Corporate vision, mission, and quality statements Corporate strategic, tactical, and annual business plans Info. Sec vision, mission and quality statements Info. Sec strategic, tactical and annual business plans Information and systems legal, ethical, and best business practices Overall information assets protection plans, policies, and procedures Current CIAPP-related and Info. Sec policies Current CIAPP-related and Info. Sec procedures Other topics as deemed appropriate by the ISSO
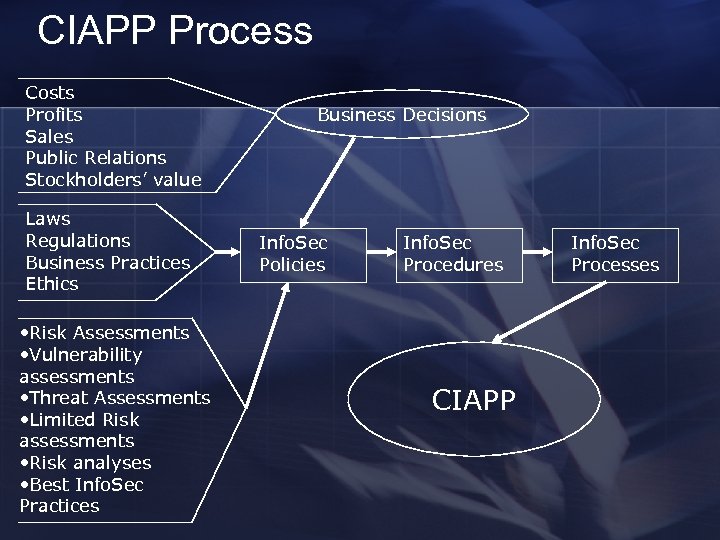 CIAPP Process Costs Profits Sales Public Relations Stockholders’ value Laws Regulations Business Practices Ethics • Risk Assessments • Vulnerability assessments • Threat Assessments • Limited Risk assessments • Risk analyses • Best Info. Sec Practices Business Decisions Info. Sec Policies Info. Sec Procedures CIAPP Info. Sec Processes
CIAPP Process Costs Profits Sales Public Relations Stockholders’ value Laws Regulations Business Practices Ethics • Risk Assessments • Vulnerability assessments • Threat Assessments • Limited Risk assessments • Risk analyses • Best Info. Sec Practices Business Decisions Info. Sec Policies Info. Sec Procedures CIAPP Info. Sec Processes
 Example CIAPP Requirements and Policy Directive 1. 2. 3. 4. 5. Introduction Section Purpose Section Scope Section Responsibilities Requirements Section A. B. C. D. E. F. G. 6. Identifying the value of the information Access to information systems Access to specific applications and files Audit trails and their review Reporting and response in the event of a violation Minimum protection requirements for the hardware, firmware and software Requirements for Info. Sec procedures at other departments and lower levels of the corporation Physical Security 1. Optional if Physical Security is handled by the Director of Security
Example CIAPP Requirements and Policy Directive 1. 2. 3. 4. 5. Introduction Section Purpose Section Scope Section Responsibilities Requirements Section A. B. C. D. E. F. G. 6. Identifying the value of the information Access to information systems Access to specific applications and files Audit trails and their review Reporting and response in the event of a violation Minimum protection requirements for the hardware, firmware and software Requirements for Info. Sec procedures at other departments and lower levels of the corporation Physical Security 1. Optional if Physical Security is handled by the Director of Security
 Info. Sec Functions l l l l l Processes Valuing Information Awareness Access Control Evaluation of all hardware, firmware and software Risk Management Security Tests and evaluations program Noncompliance Inquiries Contingency and emergency planning and disaster recovery program (CEP-DR)
Info. Sec Functions l l l l l Processes Valuing Information Awareness Access Control Evaluation of all hardware, firmware and software Risk Management Security Tests and evaluations program Noncompliance Inquiries Contingency and emergency planning and disaster recovery program (CEP-DR)
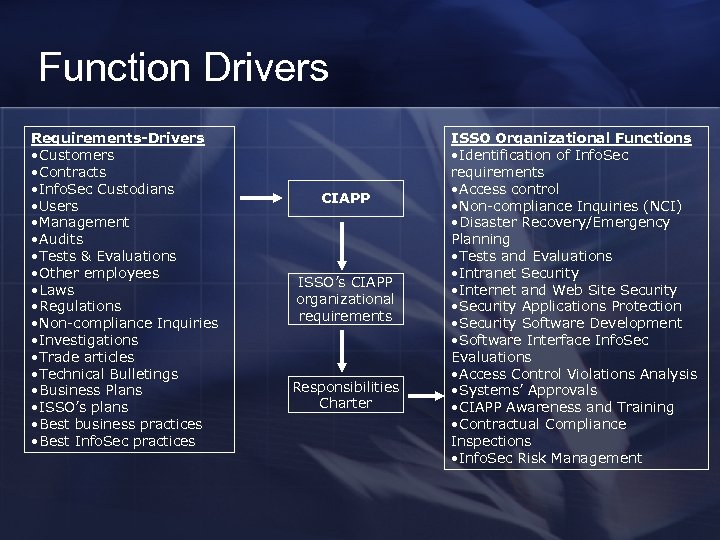 Function Drivers Requirements-Drivers • Customers • Contracts • Info. Sec Custodians • Users • Management • Audits • Tests & Evaluations • Other employees • Laws • Regulations • Non-compliance Inquiries • Investigations • Trade articles • Technical Bulletings • Business Plans • ISSO’s plans • Best business practices • Best Info. Sec practices CIAPP ISSO’s CIAPP organizational requirements Responsibilities Charter ISSO Organizational Functions • Identification of Info. Sec requirements • Access control • Non-compliance Inquiries (NCI) • Disaster Recovery/Emergency Planning • Tests and Evaluations • Intranet Security • Internet and Web Site Security • Security Applications Protection • Security Software Development • Software Interface Info. Sec Evaluations • Access Control Violations Analysis • Systems’ Approvals • CIAPP Awareness and Training • Contractual Compliance Inspections • Info. Sec Risk Management
Function Drivers Requirements-Drivers • Customers • Contracts • Info. Sec Custodians • Users • Management • Audits • Tests & Evaluations • Other employees • Laws • Regulations • Non-compliance Inquiries • Investigations • Trade articles • Technical Bulletings • Business Plans • ISSO’s plans • Best business practices • Best Info. Sec practices CIAPP ISSO’s CIAPP organizational requirements Responsibilities Charter ISSO Organizational Functions • Identification of Info. Sec requirements • Access control • Non-compliance Inquiries (NCI) • Disaster Recovery/Emergency Planning • Tests and Evaluations • Intranet Security • Internet and Web Site Security • Security Applications Protection • Security Software Development • Software Interface Info. Sec Evaluations • Access Control Violations Analysis • Systems’ Approvals • CIAPP Awareness and Training • Contractual Compliance Inspections • Info. Sec Risk Management
 Info. Sec in the Government l National Security Classified Information l l l Confidential – loss of this information cause damage to national security Secret – loss of this information cause serious damage to national security Top Secret – loss of this information cause grave damage to national security Black/Compartmented – Granted on a need to know (NTK) basis. Ex: Sensitive Compartmented Information (SCI). Unclassified l l l For Official Use Only Unclassified but Sensitive Information Unclassified
Info. Sec in the Government l National Security Classified Information l l l Confidential – loss of this information cause damage to national security Secret – loss of this information cause serious damage to national security Top Secret – loss of this information cause grave damage to national security Black/Compartmented – Granted on a need to know (NTK) basis. Ex: Sensitive Compartmented Information (SCI). Unclassified l l l For Official Use Only Unclassified but Sensitive Information Unclassified
 Info. Sec Requirements in the Government l l Info. Sec policy – laws, rules, practices that regulate how organizations handle national security data. Accountability – assigning responsibility and accountability to individuals or groups who deal with national security information Assurance – guarantees that the Info. Sec policy is implemented correctly and the Info. Sec elements accurately mediate and enforce the policy Documentation – records how a system is structured, its functions and how the system was designed
Info. Sec Requirements in the Government l l Info. Sec policy – laws, rules, practices that regulate how organizations handle national security data. Accountability – assigning responsibility and accountability to individuals or groups who deal with national security information Assurance – guarantees that the Info. Sec policy is implemented correctly and the Info. Sec elements accurately mediate and enforce the policy Documentation – records how a system is structured, its functions and how the system was designed
 Info. Sec Objectives in the Government l l l Protect and defend all information used by an AIS (automated information system) Prevent unauthorized access, modification, damage, destruction, or Do. S Provide assurances of: l l l Compliance with government and contractual obligations and agreements Confidentiality of all classified information Integrity of information and related processes Availability of information Usage by authorized personnel only of the information and AIS Identification and elimination of fraud, waste, and abuse
Info. Sec Objectives in the Government l l l Protect and defend all information used by an AIS (automated information system) Prevent unauthorized access, modification, damage, destruction, or Do. S Provide assurances of: l l l Compliance with government and contractual obligations and agreements Confidentiality of all classified information Integrity of information and related processes Availability of information Usage by authorized personnel only of the information and AIS Identification and elimination of fraud, waste, and abuse
 ISSO at Gov’t Agencies l l l l l Maintain a plan site security improvement Ensure IS systems are operated, used, maintained and disposed of properly Ensure IS systems are certified and accredited Ensure users and personnel have required security clearances, authorization, NTK, and are familiar with internal security practices Enforce security policies and safeguards on personnel having access to an IS Ensure audit trails are reviewed periodically Initiate protective and corrective measures Report security incidents in accordance with agency specific policy Report the security status of the IS Evaluate know vulnerabilities to determine if additional security is needed
ISSO at Gov’t Agencies l l l l l Maintain a plan site security improvement Ensure IS systems are operated, used, maintained and disposed of properly Ensure IS systems are certified and accredited Ensure users and personnel have required security clearances, authorization, NTK, and are familiar with internal security practices Enforce security policies and safeguards on personnel having access to an IS Ensure audit trails are reviewed periodically Initiate protective and corrective measures Report security incidents in accordance with agency specific policy Report the security status of the IS Evaluate know vulnerabilities to determine if additional security is needed
 Levels of Performance l Entry Level l l Intermediate Level l l Identify vulnerabilities and recommend security solutions required to return the system to an operational level of assurance. For a new system architecture, investigate and document system security technology, policies and training requirements to assure system operation at a specified level of assurance Advanced Level l For an accreditation action, analyze and evaluate system security technology, policy and training requirements in support of upper management. The analysis will include a description of the management/technology team required to successfully complete the accreditation process
Levels of Performance l Entry Level l l Intermediate Level l l Identify vulnerabilities and recommend security solutions required to return the system to an operational level of assurance. For a new system architecture, investigate and document system security technology, policies and training requirements to assure system operation at a specified level of assurance Advanced Level l For an accreditation action, analyze and evaluate system security technology, policy and training requirements in support of upper management. The analysis will include a description of the management/technology team required to successfully complete the accreditation process
 Duties of Gov’t ISSO l Develop Certification and Accreditation Posture l l l Plan for Certification and Accreditation Create CIA Policy Control Systems Policy Culture and Ethics Incidence Response Implement Site Security Policy l l Provide CIA Ensure Facility is approved Manage Operations of Information Systems Regulate General Principles l l l Security Management Access Controls l l l Access Control, Training, Awareness, Legal aspects, CC, etc Human Access Key Management Incident Response
Duties of Gov’t ISSO l Develop Certification and Accreditation Posture l l l Plan for Certification and Accreditation Create CIA Policy Control Systems Policy Culture and Ethics Incidence Response Implement Site Security Policy l l Provide CIA Ensure Facility is approved Manage Operations of Information Systems Regulate General Principles l l l Security Management Access Controls l l l Access Control, Training, Awareness, Legal aspects, CC, etc Human Access Key Management Incident Response
 Duties (continued) l Enforce and verify system security policy l l l l CIA and Accountability Security Management Access Controls Automated Security Tools Handling Media Incident Response Report on site security Status l l l Security Continuity Reporting Report Security Incidents Law Report Security Status of IS as required by upper management Report to Inspector General (IG)
Duties (continued) l Enforce and verify system security policy l l l l CIA and Accountability Security Management Access Controls Automated Security Tools Handling Media Incident Response Report on site security Status l l l Security Continuity Reporting Report Security Incidents Law Report Security Status of IS as required by upper management Report to Inspector General (IG)
 Duties (continued) l Support Certification and Accreditation Certification Functions l Accreditation Functions l Respond to upper management requests l
Duties (continued) l Support Certification and Accreditation Certification Functions l Accreditation Functions l Respond to upper management requests l
 References l l Kovacich, Dr. Gerald L. , “The Information Systems Security Officer’s Guide: Establishing and Managing an Information Protection Program” “Information Assurance Training Standard for Information Systems Security Officers” http: //www. cnss. gov/instructions. html
References l l Kovacich, Dr. Gerald L. , “The Information Systems Security Officer’s Guide: Establishing and Managing an Information Protection Program” “Information Assurance Training Standard for Information Systems Security Officers” http: //www. cnss. gov/instructions. html


