32f929e976f3bcfe9762f71e1beaca66.ppt
- Количество слайдов: 32
 Information Sharing and Security in Dynamic Coalitions Charles E. Phillips, Jr. Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 charlesp@engr. uconn. edu Profs. T. C. Ting and Steven A. Demurjian Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 http: //www. engr. uconn. edu/~steve@engr. uconn. edu SACMAT 02 -1
Information Sharing and Security in Dynamic Coalitions Charles E. Phillips, Jr. Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 charlesp@engr. uconn. edu Profs. T. C. Ting and Steven A. Demurjian Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 http: //www. engr. uconn. edu/~steve@engr. uconn. edu SACMAT 02 -1
 Overview of Presentation m m m Introduction The Dynamic Coalition Problem q Civilian Organizations q Military Involvement/GCCS Information Sharing and Security q Federating Resources q Data Integrity q Access Control (DAC and MAC) q Other Critical Security Issues Candidate Security Approach Conclusions and Future Work SACMAT 02 -2
Overview of Presentation m m m Introduction The Dynamic Coalition Problem q Civilian Organizations q Military Involvement/GCCS Information Sharing and Security q Federating Resources q Data Integrity q Access Control (DAC and MAC) q Other Critical Security Issues Candidate Security Approach Conclusions and Future Work SACMAT 02 -2
 Introduction Crisis and Coalitions m m A Crisis is Any Situation Requiring National or International Attention as Determined by the President of the United States or UN A Coalition is an Alliance of Organizations: Military, Civilian, International or any Combination A Dynamic Coalition is Formed in a Crisis and Changes as Crisis Develops, with the Key Concern Being the Most Effective way to Solve the Crisis Dynamic Coalition Problem (DCP) is the Inherent Security, Resource, and/or Information Sharing Risks that Occur as a Result of the Coalition Being Formed Quickly SACMAT 02 -3
Introduction Crisis and Coalitions m m A Crisis is Any Situation Requiring National or International Attention as Determined by the President of the United States or UN A Coalition is an Alliance of Organizations: Military, Civilian, International or any Combination A Dynamic Coalition is Formed in a Crisis and Changes as Crisis Develops, with the Key Concern Being the Most Effective way to Solve the Crisis Dynamic Coalition Problem (DCP) is the Inherent Security, Resource, and/or Information Sharing Risks that Occur as a Result of the Coalition Being Formed Quickly SACMAT 02 -3
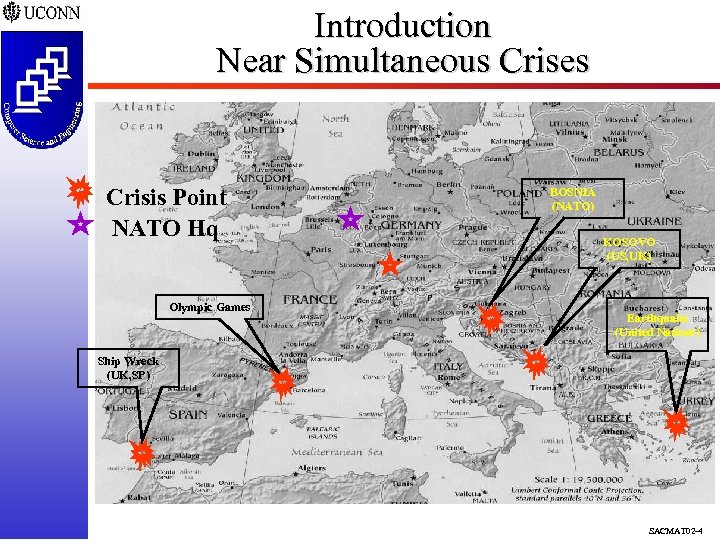 Introduction Near Simultaneous Crises Crisis Point NATO Hq Olympic Games BOSNIA (NATO) KOSOVO (US, UK) Earthquake (United Nations) Ship Wreck (UK, SP) SACMAT 02 -4
Introduction Near Simultaneous Crises Crisis Point NATO Hq Olympic Games BOSNIA (NATO) KOSOVO (US, UK) Earthquake (United Nations) Ship Wreck (UK, SP) SACMAT 02 -4
 Evaluation vs. DCP Emergent Need for Coalitions m “Coalitions must be flexible and no one coalition is or has the answer to all situations. ” » Secretary of Defense, Donald Rumsfeld m “Whenever possible we must seek to operate alongside alliance or coalition forces, integrating their capabilities and capitalizing on their strengths. ” » U. S. National Security Strategy m “Currently, there is no automated capability for passing command control information and situational awareness information between nations except by liaison officer, fax, telephone, or loaning equipment. ” » Undersecretary of Defense for Advanced Technology SACMAT 02 -5
Evaluation vs. DCP Emergent Need for Coalitions m “Coalitions must be flexible and no one coalition is or has the answer to all situations. ” » Secretary of Defense, Donald Rumsfeld m “Whenever possible we must seek to operate alongside alliance or coalition forces, integrating their capabilities and capitalizing on their strengths. ” » U. S. National Security Strategy m “Currently, there is no automated capability for passing command control information and situational awareness information between nations except by liaison officer, fax, telephone, or loaning equipment. ” » Undersecretary of Defense for Advanced Technology SACMAT 02 -5
 The Dynamic Coalition Problem m m Dynamic Coalition Problem (DCP) is the Inherent Security, Resource, and/or Information Sharing Risks that Occur as a Result of the Coalition Being Formed Quickly Private Organizations (PVO) q Doctors Without Boarders q Red Cross Non-Government Organizations (NGO) q NYPD Government Agencies q FBI q CIA q Military SACMAT 02 -6
The Dynamic Coalition Problem m m Dynamic Coalition Problem (DCP) is the Inherent Security, Resource, and/or Information Sharing Risks that Occur as a Result of the Coalition Being Formed Quickly Private Organizations (PVO) q Doctors Without Boarders q Red Cross Non-Government Organizations (NGO) q NYPD Government Agencies q FBI q CIA q Military SACMAT 02 -6
 Supporting Advanced Applications DCP Objectives for Crisis m m m m Federate Users Quickly and Dynamically Bring Together Resources (Legacy, COTs, GOTs, DBs, etc. ) Without Modification Dynamically Realize/Manage Simultaneous Crises Identify Users by Roles to Finely Tune Access Authorize, Authenticate, and Enforce a Scalable Security Policy that is Flexible in Response to Collation Needs Provide a Security Solution that is Portable, Extensible, and Redundant for Survivability Include Management/Introspection Capabilities to Track and Monitor System Behavior SACMAT 02 -7
Supporting Advanced Applications DCP Objectives for Crisis m m m m Federate Users Quickly and Dynamically Bring Together Resources (Legacy, COTs, GOTs, DBs, etc. ) Without Modification Dynamically Realize/Manage Simultaneous Crises Identify Users by Roles to Finely Tune Access Authorize, Authenticate, and Enforce a Scalable Security Policy that is Flexible in Response to Collation Needs Provide a Security Solution that is Portable, Extensible, and Redundant for Survivability Include Management/Introspection Capabilities to Track and Monitor System Behavior SACMAT 02 -7
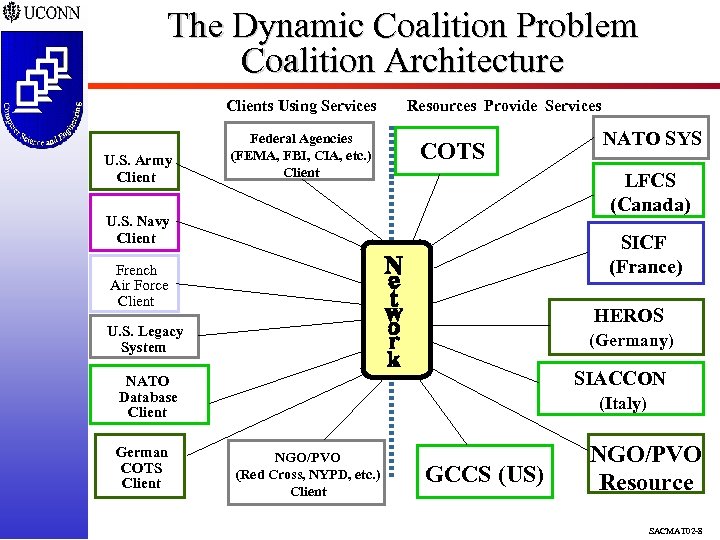 The Dynamic Coalition Problem Coalition Architecture Clients Using Services U. S. Army Client Federal Agencies (FEMA, FBI, CIA, etc. ) Client Resources Provide Services COTS LFCS (Canada) U. S. Navy Client SICF (France) French Air Force Client HEROS U. S. Legacy System (Germany) SIACCON NATO Database Client German COTS Client NATO SYS (Italy) NGO/PVO (Red Cross, NYPD, etc. ) Client GCCS (US) NGO/PVO Resource SACMAT 02 -8
The Dynamic Coalition Problem Coalition Architecture Clients Using Services U. S. Army Client Federal Agencies (FEMA, FBI, CIA, etc. ) Client Resources Provide Services COTS LFCS (Canada) U. S. Navy Client SICF (France) French Air Force Client HEROS U. S. Legacy System (Germany) SIACCON NATO Database Client German COTS Client NATO SYS (Italy) NGO/PVO (Red Cross, NYPD, etc. ) Client GCCS (US) NGO/PVO Resource SACMAT 02 -8
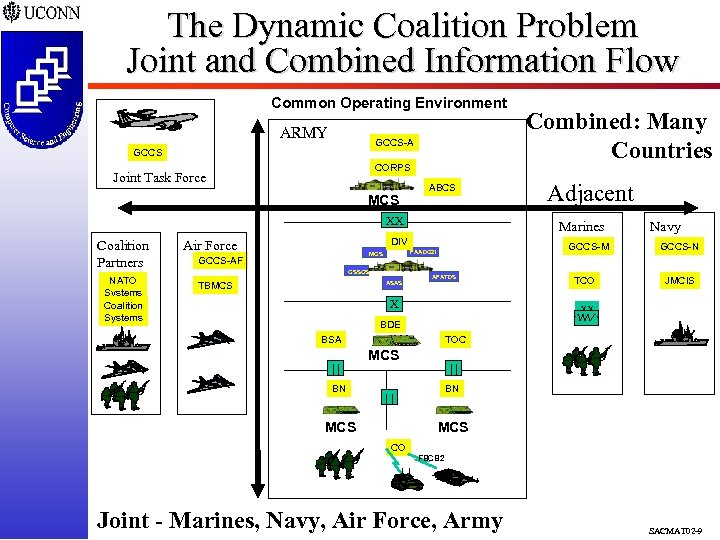 The Dynamic Coalition Problem Joint and Combined Information Flow Common Operating Environment ARMY GCCS-A GCCS CORPS Joint Task Force ABCS MCS XX Coalition Partners NATO Systems Coalition Systems GCCS-AF CSSCS ASAS TBMCS GCCS-M FAADC 2 I MCS Adjacent Marines DIV Air Force Combined: Many Countries AFATDS X TCO Navy GCCS-N JMCIS XX BDE BSA || BN TOC MCS || BN || MCS CO FBCB 2 Joint - Marines, Navy, Air Force, Army SACMAT 02 -9
The Dynamic Coalition Problem Joint and Combined Information Flow Common Operating Environment ARMY GCCS-A GCCS CORPS Joint Task Force ABCS MCS XX Coalition Partners NATO Systems Coalition Systems GCCS-AF CSSCS ASAS TBMCS GCCS-M FAADC 2 I MCS Adjacent Marines DIV Air Force Combined: Many Countries AFATDS X TCO Navy GCCS-N JMCIS XX BDE BSA || BN TOC MCS || BN || MCS CO FBCB 2 Joint - Marines, Navy, Air Force, Army SACMAT 02 -9
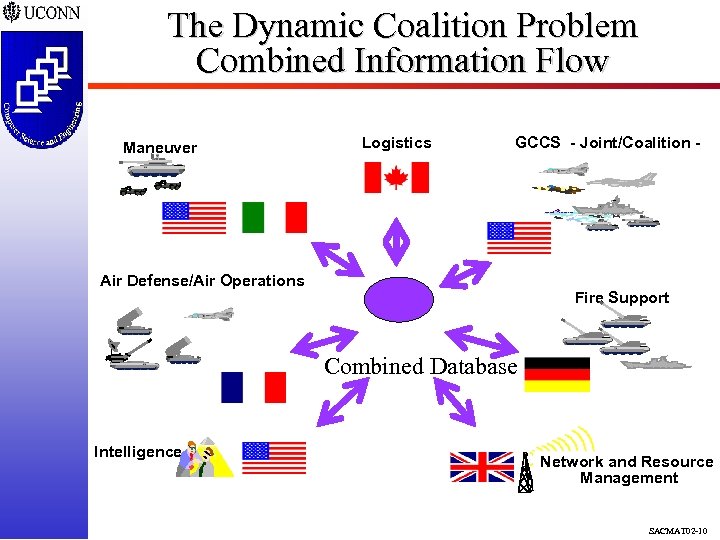 The Dynamic Coalition Problem Combined Information Flow Maneuver Logistics GCCS - Joint/Coalition - Air Defense/Air Operations Fire Support Combined Database Intelligence Network and Resource Management SACMAT 02 -10
The Dynamic Coalition Problem Combined Information Flow Maneuver Logistics GCCS - Joint/Coalition - Air Defense/Air Operations Fire Support Combined Database Intelligence Network and Resource Management SACMAT 02 -10
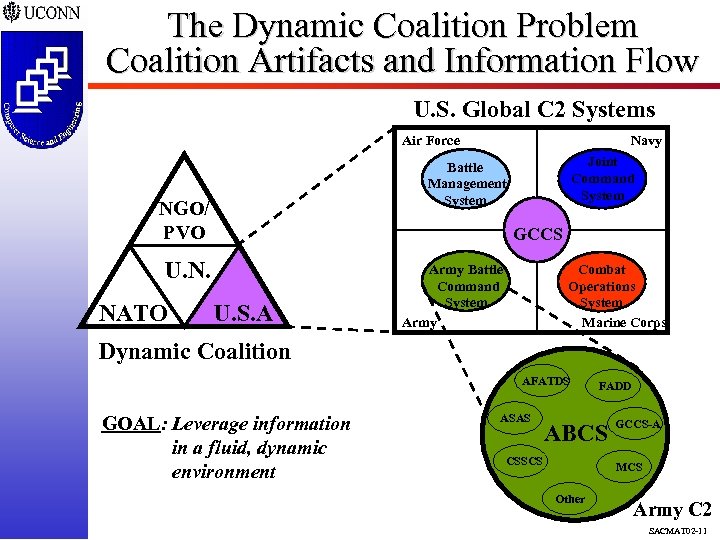 The Dynamic Coalition Problem Coalition Artifacts and Information Flow U. S. Global C 2 Systems Air Force Joint Command System Battle Management System NGO/ PVO GCCS U. N. NATO Navy U. S. A Army Battle Command System Army Combat Operations System Marine Corps Dynamic Coalition AFATDS GOAL: Leverage information in a fluid, dynamic environment ASAS FADD ABCS CSSCS GCCS-A MCS Other Army C 2 SACMAT 02 -11
The Dynamic Coalition Problem Coalition Artifacts and Information Flow U. S. Global C 2 Systems Air Force Joint Command System Battle Management System NGO/ PVO GCCS U. N. NATO Navy U. S. A Army Battle Command System Army Combat Operations System Marine Corps Dynamic Coalition AFATDS GOAL: Leverage information in a fluid, dynamic environment ASAS FADD ABCS CSSCS GCCS-A MCS Other Army C 2 SACMAT 02 -11
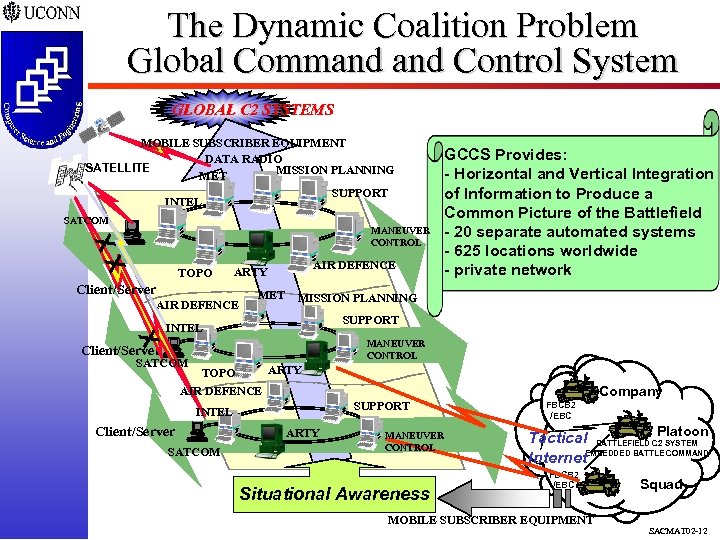 The Dynamic Coalition Problem Global Command Control System GLOBAL C 2 SYSTEMS MOBILE SUBSCRIBER EQUIPMENT DATA RADIO SATELLITE MISSION PLANNING MET SUPPORT INTEL SATCOM XX MANEUVER CONTROL TOPO AIR DEFENCE ARTY Client/Server AIR DEFENCE MET MISSION PLANNING SUPPORT INTEL X MANEUVER CONTROL Client/Server SATCOM GCCS Provides: - Horizontal and Vertical Integration of Information to Produce a Common Picture of the Battlefield - 20 separate automated systems - 625 locations worldwide - private network ARTY TOPO Company AIR DEFENCE SUPPORT INTEL Client/Server SATCOM ARTY MANEUVER CONTROL Situational Awareness FBCB 2 /EBC Platoon Tactical BATTLEFIELD C 2 SYSTEM Internet. EMBEDDED BATTLE COMMAND FBCB 2 /EBC MOBILE SUBSCRIBER EQUIPMENT Squad SACMAT 02 -12
The Dynamic Coalition Problem Global Command Control System GLOBAL C 2 SYSTEMS MOBILE SUBSCRIBER EQUIPMENT DATA RADIO SATELLITE MISSION PLANNING MET SUPPORT INTEL SATCOM XX MANEUVER CONTROL TOPO AIR DEFENCE ARTY Client/Server AIR DEFENCE MET MISSION PLANNING SUPPORT INTEL X MANEUVER CONTROL Client/Server SATCOM GCCS Provides: - Horizontal and Vertical Integration of Information to Produce a Common Picture of the Battlefield - 20 separate automated systems - 625 locations worldwide - private network ARTY TOPO Company AIR DEFENCE SUPPORT INTEL Client/Server SATCOM ARTY MANEUVER CONTROL Situational Awareness FBCB 2 /EBC Platoon Tactical BATTLEFIELD C 2 SYSTEM Internet. EMBEDDED BATTLE COMMAND FBCB 2 /EBC MOBILE SUBSCRIBER EQUIPMENT Squad SACMAT 02 -12
 The Dynamic Coalition Problem Global Command Control System Joint Services : Weather Video Teleconference Joint Operations Planning and Execution System Common Operational Picture Transportation Flow Analysis Logistics Planning Tool Defense Message System NATO Message System Component Services : Army Battle Command System Air Force Battle Management System Marine Combat Operations System Navy Command System a. k. a METOC TLCF JOPES COP JFAST LOGSAFE DMS CRONOS ABCS TBMCS TCO JMCIS SACMAT 02 -13
The Dynamic Coalition Problem Global Command Control System Joint Services : Weather Video Teleconference Joint Operations Planning and Execution System Common Operational Picture Transportation Flow Analysis Logistics Planning Tool Defense Message System NATO Message System Component Services : Army Battle Command System Air Force Battle Management System Marine Combat Operations System Navy Command System a. k. a METOC TLCF JOPES COP JFAST LOGSAFE DMS CRONOS ABCS TBMCS TCO JMCIS SACMAT 02 -13
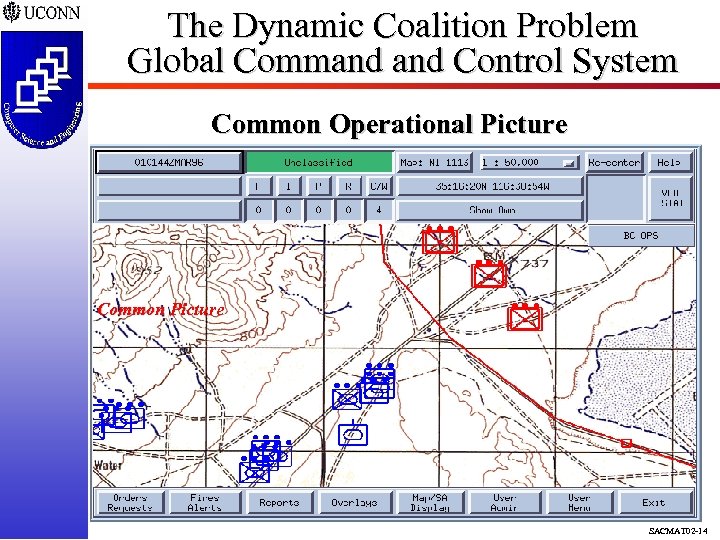 The Dynamic Coalition Problem Global Command Control System Common Operational Picture Common Picture SACMAT 02 -14
The Dynamic Coalition Problem Global Command Control System Common Operational Picture Common Picture SACMAT 02 -14
 The Dynamic Coalition Problem GCCS Shortfalls: User Roles m m Currently, GCCS Users have Static Profile Based on Position/Supervisor/Clearance Level Granularity Gives “Too Much Access” Profile Changes are Difficult to Make - Changes Done by System Admin. Not Security Officer What Can User Roles Offer to GCCS? q User Roles are Valuable Since They Allow Privileges to be Based on Responsibilities q Security Officer Controls Requirements q Support for Dynamic Changes in Privileges q Towards Least Privilege SACMAT 02 -15
The Dynamic Coalition Problem GCCS Shortfalls: User Roles m m Currently, GCCS Users have Static Profile Based on Position/Supervisor/Clearance Level Granularity Gives “Too Much Access” Profile Changes are Difficult to Make - Changes Done by System Admin. Not Security Officer What Can User Roles Offer to GCCS? q User Roles are Valuable Since They Allow Privileges to be Based on Responsibilities q Security Officer Controls Requirements q Support for Dynamic Changes in Privileges q Towards Least Privilege SACMAT 02 -15
 The Dynamic Coalition Problem GCCS Shortfalls: Time Controlled Access m m Currently, in GCCS, User Profiles are Indefinite with Respect to Time q Longer than a Single Crisis q Difficult to Distinguish in Multiple Crises q No Time Controllable Access on Users or GCCS Resources What can Time Constrained Access offer GCCS? q Junior Planners - Air Movements of Equipment Weeks before Deployment q Senior Planners - Adjustment in Air Movements Near and During Deployment q Similar Actions are Constrained by Time Based on Role SACMAT 02 -16
The Dynamic Coalition Problem GCCS Shortfalls: Time Controlled Access m m Currently, in GCCS, User Profiles are Indefinite with Respect to Time q Longer than a Single Crisis q Difficult to Distinguish in Multiple Crises q No Time Controllable Access on Users or GCCS Resources What can Time Constrained Access offer GCCS? q Junior Planners - Air Movements of Equipment Weeks before Deployment q Senior Planners - Adjustment in Air Movements Near and During Deployment q Similar Actions are Constrained by Time Based on Role SACMAT 02 -16
 The Dynamic Coalition Problem GCCS Shortfalls: Value Based Access m m Currently, in GCCS, Controlled Access Based on Information Values Difficult to Achieve q Unlimited Viewing of Common Operational Picture (COP) q Unlimited Access to Movement Information q Attempts to Constrain would have to be Programmatic - which is Problematic! What can Value-Based Access Offer to GCCS? q In COP Ø Constrain Display of Friendly and Enemy Positions Ø Limit Map Coordinates Displayed Ø Limit Tier of Display (Deployment, Weather, etc. ) SACMAT 02 -17
The Dynamic Coalition Problem GCCS Shortfalls: Value Based Access m m Currently, in GCCS, Controlled Access Based on Information Values Difficult to Achieve q Unlimited Viewing of Common Operational Picture (COP) q Unlimited Access to Movement Information q Attempts to Constrain would have to be Programmatic - which is Problematic! What can Value-Based Access Offer to GCCS? q In COP Ø Constrain Display of Friendly and Enemy Positions Ø Limit Map Coordinates Displayed Ø Limit Tier of Display (Deployment, Weather, etc. ) SACMAT 02 -17
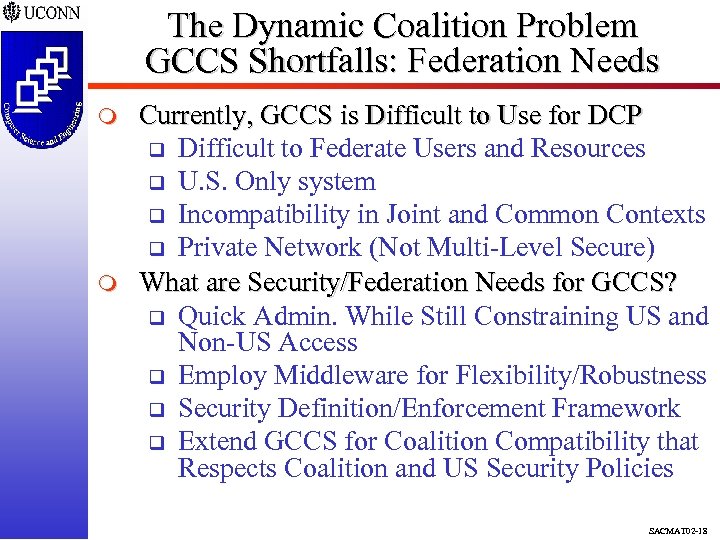 The Dynamic Coalition Problem GCCS Shortfalls: Federation Needs m m Currently, GCCS is Difficult to Use for DCP q Difficult to Federate Users and Resources q U. S. Only system q Incompatibility in Joint and Common Contexts q Private Network (Not Multi-Level Secure) What are Security/Federation Needs for GCCS? q Quick Admin. While Still Constraining US and Non-US Access q Employ Middleware for Flexibility/Robustness q Security Definition/Enforcement Framework q Extend GCCS for Coalition Compatibility that Respects Coalition and US Security Policies SACMAT 02 -18
The Dynamic Coalition Problem GCCS Shortfalls: Federation Needs m m Currently, GCCS is Difficult to Use for DCP q Difficult to Federate Users and Resources q U. S. Only system q Incompatibility in Joint and Common Contexts q Private Network (Not Multi-Level Secure) What are Security/Federation Needs for GCCS? q Quick Admin. While Still Constraining US and Non-US Access q Employ Middleware for Flexibility/Robustness q Security Definition/Enforcement Framework q Extend GCCS for Coalition Compatibility that Respects Coalition and US Security Policies SACMAT 02 -18
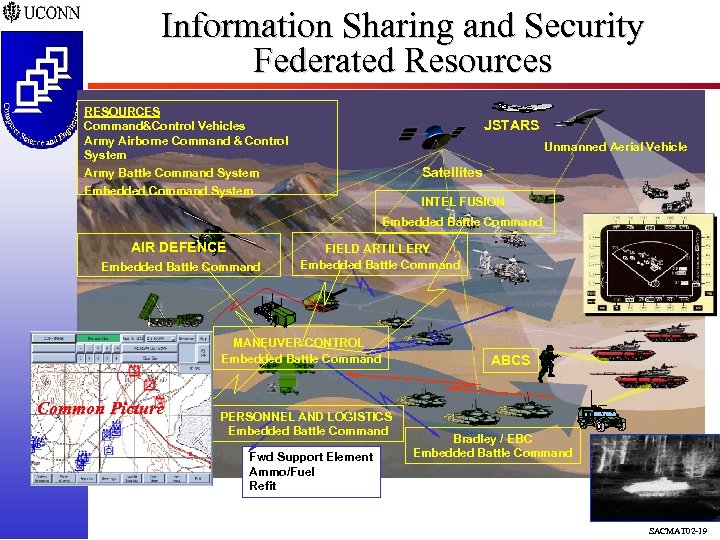 Information Sharing and Security Federated Resources RESOURCES Command&Control Vehicles Army Airborne Command & Control System JSTARS Unmanned Aerial Vehicle Satellites Army Battle Command System Embedded Command System INTEL FUSION Embedded Battle Command AIR DEFENCE Embedded Battle Command FIELD ARTILLERY Embedded Battle Command MANEUVER CONTROL Embedded Battle Command Common Picture PERSONNEL AND LOGISTICS Embedded Battle Command Fwd Support Element Ammo/Fuel Refit ABCS Bradley / EBC Embedded Battle Command SACMAT 02 -19
Information Sharing and Security Federated Resources RESOURCES Command&Control Vehicles Army Airborne Command & Control System JSTARS Unmanned Aerial Vehicle Satellites Army Battle Command System Embedded Command System INTEL FUSION Embedded Battle Command AIR DEFENCE Embedded Battle Command FIELD ARTILLERY Embedded Battle Command MANEUVER CONTROL Embedded Battle Command Common Picture PERSONNEL AND LOGISTICS Embedded Battle Command Fwd Support Element Ammo/Fuel Refit ABCS Bradley / EBC Embedded Battle Command SACMAT 02 -19
 Information Sharing and Security Syntactic Considerations m m Syntax is Structure and Format of the Information That is Needed to Support a Coalition Incorrect Structure or Format Could Result in Simple Error Message to Catastrophic Event For Sharing, Strict Formats Need to be Maintained In US Military, Message Formats Include q Heading and Ending Section Ø United States Message Text Formats (USMTF) Ø 128 Different Message Formats Text Body of Actual Message Problem: Formats Non-Standard Across Different Branches of Military and Countries q m SACMAT 02 -20
Information Sharing and Security Syntactic Considerations m m Syntax is Structure and Format of the Information That is Needed to Support a Coalition Incorrect Structure or Format Could Result in Simple Error Message to Catastrophic Event For Sharing, Strict Formats Need to be Maintained In US Military, Message Formats Include q Heading and Ending Section Ø United States Message Text Formats (USMTF) Ø 128 Different Message Formats Text Body of Actual Message Problem: Formats Non-Standard Across Different Branches of Military and Countries q m SACMAT 02 -20
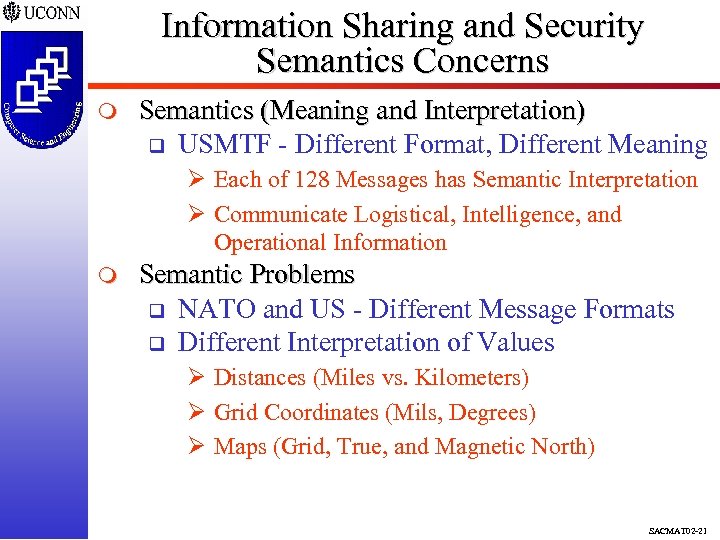 Information Sharing and Security Semantics Concerns m Semantics (Meaning and Interpretation) q USMTF - Different Format, Different Meaning Ø Each of 128 Messages has Semantic Interpretation Ø Communicate Logistical, Intelligence, and Operational Information m Semantic Problems q NATO and US - Different Message Formats q Different Interpretation of Values Ø Distances (Miles vs. Kilometers) Ø Grid Coordinates (Mils, Degrees) Ø Maps (Grid, True, and Magnetic North) SACMAT 02 -21
Information Sharing and Security Semantics Concerns m Semantics (Meaning and Interpretation) q USMTF - Different Format, Different Meaning Ø Each of 128 Messages has Semantic Interpretation Ø Communicate Logistical, Intelligence, and Operational Information m Semantic Problems q NATO and US - Different Message Formats q Different Interpretation of Values Ø Distances (Miles vs. Kilometers) Ø Grid Coordinates (Mils, Degrees) Ø Maps (Grid, True, and Magnetic North) SACMAT 02 -21
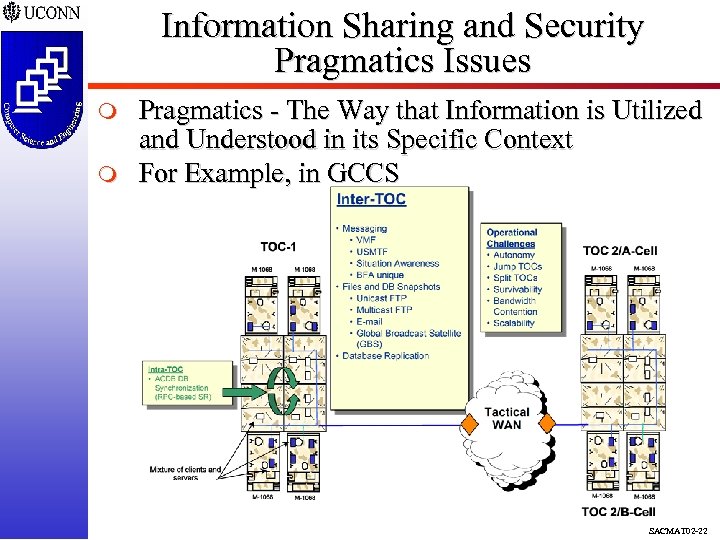 Information Sharing and Security Pragmatics Issues m m Pragmatics - The Way that Information is Utilized and Understood in its Specific Context For Example, in GCCS SACMAT 02 -22
Information Sharing and Security Pragmatics Issues m m Pragmatics - The Way that Information is Utilized and Understood in its Specific Context For Example, in GCCS SACMAT 02 -22
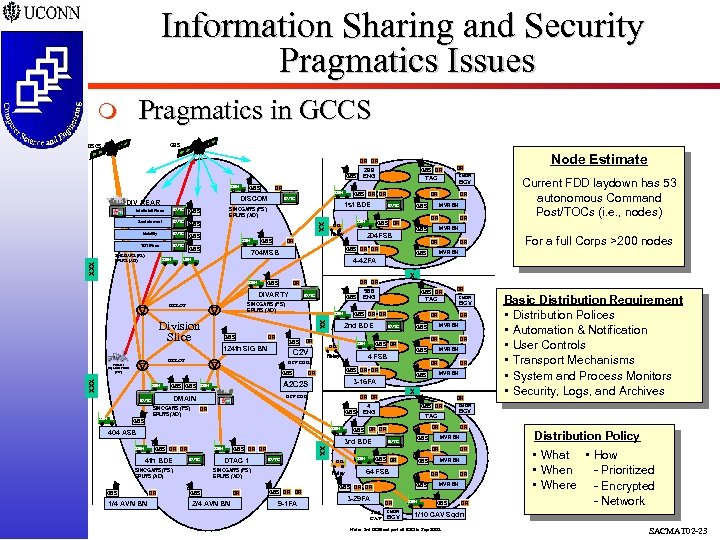 Information Sharing and Security Pragmatics Issues Pragmatics in GCCS m GBS DSCS DR DR GBS SEN VTel BVTC Info/Intel/Plans BVTC Mobility BVTC TGT/Fires BVTC SEN BVTC GBS BCV DR MVR BN GBS DR DR DR GBS DR DR 704 MSB Node Estimate Current FDD laydown has 53 autonomous Command Post/TOCs (i. e. , nodes) MVR BN GBS 204 FSB DR GBS CMDR DR BVTC SEN DR DR TAC GBS DR DR Relay SEN GBS DR 1 st BDE SINCGARS (FS) EPLRS (AD) GBS XX Sustainment XXX DR DISCOM DIV REAR SINCGARS (FS) EPLRS (AD) GBS 299 ENG DR For a full Corps >200 nodes MVR BN GBS 4 -42 FA LEN X SEN GBS DIVARTY BVTC SEN XX Division Slice GBS DR GBS 124 th SIG BN DR HCLOS XXX GBS SEN SINCGARS (FS) EPLRS (AD) SEN X DR 4 ENG GBS DR TAC BVTC SINCGARS (FS) EPLRS (AD) GBS 1/4 AVN BN DR DTAC 1 BVTC SINCGARS (FS) EPLRS (AD) GBS 2/4 AVN BN DR 9 -1 FA DR DR DR Relay GBS DR DR BCV MVR BN GBS XX 4 th BDE BVTC SEN GBS DR 64 FSB 3 -29 FA DR 1/10 CAV CMDR BCV DR DR GBS DR DR DR MVR BN GBS SEN MVR BN GBS Basic Distribution Requirement • Distribution Polices • Automation & Notification • User Controls • Transport Mechanisms • System and Process Monitors • Security, Logs, and Archives CMDR DR GBS DR DR 3 rd BDE DR MVR BN GBS DR DR 404 ASB GBS DR DR DR MVR BN GBS 3 -16 FA GBS SEN DR MVR BN DR DR DR GBS DR DR BCV DR GBS SEN CMDR DR GBS BVTC GBS DR DR DIV CDR DMAIN DR TAC 4 FSB Relay A 2 C 2 S VTel GBS DR 2 nd BDE DIV CDR GBS BVTC 588 ENG GBS DR DR DR C 2 V Theater Injection Point (TIP) SEN GBS SINCGARS (FS) EPLRS (AD) HCLOS SEN DR DR Distribution Policy • What • How • When - Prioritized • Where - Encrypted - Network 1/10 CAV Sqdn Note: 3 rd BDE not part of 1 DD in Sep 2000. SACMAT 02 -23
Information Sharing and Security Pragmatics Issues Pragmatics in GCCS m GBS DSCS DR DR GBS SEN VTel BVTC Info/Intel/Plans BVTC Mobility BVTC TGT/Fires BVTC SEN BVTC GBS BCV DR MVR BN GBS DR DR DR GBS DR DR 704 MSB Node Estimate Current FDD laydown has 53 autonomous Command Post/TOCs (i. e. , nodes) MVR BN GBS 204 FSB DR GBS CMDR DR BVTC SEN DR DR TAC GBS DR DR Relay SEN GBS DR 1 st BDE SINCGARS (FS) EPLRS (AD) GBS XX Sustainment XXX DR DISCOM DIV REAR SINCGARS (FS) EPLRS (AD) GBS 299 ENG DR For a full Corps >200 nodes MVR BN GBS 4 -42 FA LEN X SEN GBS DIVARTY BVTC SEN XX Division Slice GBS DR GBS 124 th SIG BN DR HCLOS XXX GBS SEN SINCGARS (FS) EPLRS (AD) SEN X DR 4 ENG GBS DR TAC BVTC SINCGARS (FS) EPLRS (AD) GBS 1/4 AVN BN DR DTAC 1 BVTC SINCGARS (FS) EPLRS (AD) GBS 2/4 AVN BN DR 9 -1 FA DR DR DR Relay GBS DR DR BCV MVR BN GBS XX 4 th BDE BVTC SEN GBS DR 64 FSB 3 -29 FA DR 1/10 CAV CMDR BCV DR DR GBS DR DR DR MVR BN GBS SEN MVR BN GBS Basic Distribution Requirement • Distribution Polices • Automation & Notification • User Controls • Transport Mechanisms • System and Process Monitors • Security, Logs, and Archives CMDR DR GBS DR DR 3 rd BDE DR MVR BN GBS DR DR 404 ASB GBS DR DR DR MVR BN GBS 3 -16 FA GBS SEN DR MVR BN DR DR DR GBS DR DR BCV DR GBS SEN CMDR DR GBS BVTC GBS DR DR DIV CDR DMAIN DR TAC 4 FSB Relay A 2 C 2 S VTel GBS DR 2 nd BDE DIV CDR GBS BVTC 588 ENG GBS DR DR DR C 2 V Theater Injection Point (TIP) SEN GBS SINCGARS (FS) EPLRS (AD) HCLOS SEN DR DR Distribution Policy • What • How • When - Prioritized • Where - Encrypted - Network 1/10 CAV Sqdn Note: 3 rd BDE not part of 1 DD in Sep 2000. SACMAT 02 -23
 Information Sharing and Security Data Integrity m m Concerns: Consistency, Accuracy, Reliability Accidental Errors q Crashes, Concurrent Access, Logical Errors q Actions: Ø Integrity Constraints Ø GUIs Ø Redundancy m Malicious Errors q Not Totally Preventable q Actions: Ø Authorization, Authentication, Enforcement Policy Ø Concurrent Updates to Backup DBs Ø Dual Homing SACMAT 02 -24
Information Sharing and Security Data Integrity m m Concerns: Consistency, Accuracy, Reliability Accidental Errors q Crashes, Concurrent Access, Logical Errors q Actions: Ø Integrity Constraints Ø GUIs Ø Redundancy m Malicious Errors q Not Totally Preventable q Actions: Ø Authorization, Authentication, Enforcement Policy Ø Concurrent Updates to Backup DBs Ø Dual Homing SACMAT 02 -24
 Information Sharing and Security Discretionary Access Control m m What is Discretionary Access Control (DAC)? q Restricts Access to Objects Based on the Identity of Group and /or Subject q Discretion with Access Permissions Supports the Ability to “Pass-on” Permissions DAC and DCP q Pass on from Subject to Subject is a Problem Ø Information Could be Passed from Subject (Owner) to Subject to Party Who Should be Restricted q For Example, Ø Local Commanders Can’t Release Information Ø Rely on Discretion by Foreign Disclosure Officer q Pass on of DAC Must be Carefully Controlled! SACMAT 02 -25
Information Sharing and Security Discretionary Access Control m m What is Discretionary Access Control (DAC)? q Restricts Access to Objects Based on the Identity of Group and /or Subject q Discretion with Access Permissions Supports the Ability to “Pass-on” Permissions DAC and DCP q Pass on from Subject to Subject is a Problem Ø Information Could be Passed from Subject (Owner) to Subject to Party Who Should be Restricted q For Example, Ø Local Commanders Can’t Release Information Ø Rely on Discretion by Foreign Disclosure Officer q Pass on of DAC Must be Carefully Controlled! SACMAT 02 -25
 Information Sharing and Security Role Based Access Control m m What is Role Based Access Control (RBAC)? q Roles Provide Means for Permissions to Objects, Resources, Based on Responsibilities q Users May have Multiple Roles Each with Different Set of Permissions q Role-Based Security Policy Flexible in both Management and Usage Issues for RBAC and DCP q Who Creates the Roles? q Who Determines Permissions (Access)? q Who Assigns Users to Roles? q Are there Constraints Placed on Users Within Those Roles? SACMAT 02 -26
Information Sharing and Security Role Based Access Control m m What is Role Based Access Control (RBAC)? q Roles Provide Means for Permissions to Objects, Resources, Based on Responsibilities q Users May have Multiple Roles Each with Different Set of Permissions q Role-Based Security Policy Flexible in both Management and Usage Issues for RBAC and DCP q Who Creates the Roles? q Who Determines Permissions (Access)? q Who Assigns Users to Roles? q Are there Constraints Placed on Users Within Those Roles? SACMAT 02 -26
 Information Sharing and Security Mandatory Access Control m m What is Mandatory Access Control (MAC)? q Restrict Access to Information, Resources, Based on Sensitivity Level (Classification) Classified Information - MAC Required q If Clearance (of User) Dominates Classification, Access is Allowed MAC and DCP q MAC will be Present in Coalition Assets q Need to Support MAC of US and Partners q Partners have Different Levels/Labels q Need to Reconcile Levels/Labels of Coalition Partners (which Include Past Adversaries!) SACMAT 02 -27
Information Sharing and Security Mandatory Access Control m m What is Mandatory Access Control (MAC)? q Restrict Access to Information, Resources, Based on Sensitivity Level (Classification) Classified Information - MAC Required q If Clearance (of User) Dominates Classification, Access is Allowed MAC and DCP q MAC will be Present in Coalition Assets q Need to Support MAC of US and Partners q Partners have Different Levels/Labels q Need to Reconcile Levels/Labels of Coalition Partners (which Include Past Adversaries!) SACMAT 02 -27
 Information Sharing and Security Other Issues m Intrusion Detection q Not Prevention q Intrusion Types: Ø Trojan Horse, Data Manipulation, Snooping q Defense: Ø Tracking and Accountability m Survivability q Reliability and Accessibility q Defense: Ø Redundancy m Cryptography q Fundamental to Security q Implementation Details (key distribution) SACMAT 02 -28
Information Sharing and Security Other Issues m Intrusion Detection q Not Prevention q Intrusion Types: Ø Trojan Horse, Data Manipulation, Snooping q Defense: Ø Tracking and Accountability m Survivability q Reliability and Accessibility q Defense: Ø Redundancy m Cryptography q Fundamental to Security q Implementation Details (key distribution) SACMAT 02 -28
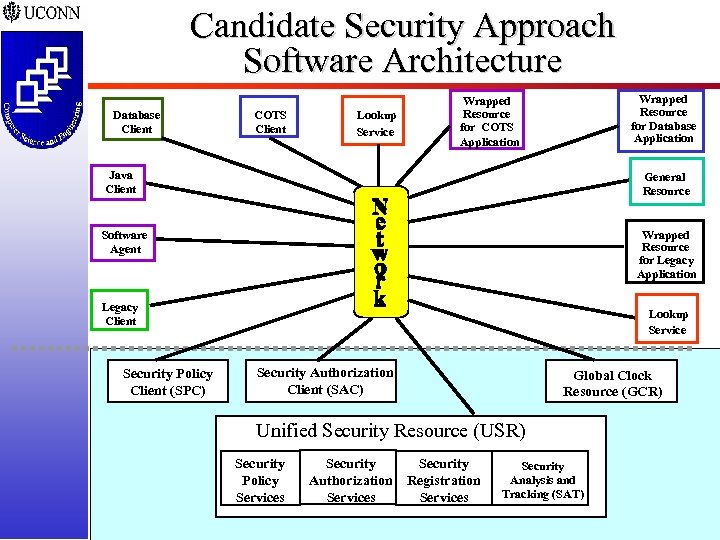 Candidate Security Approach Software Architecture Database Client COTS Client Lookup Service Wrapped Resource for Database Application Wrapped Resource for COTS Application Java Client General Resource Wrapped Resource for Legacy Application Software Agent Legacy Client Security Policy Client (SPC) Lookup Service Security Authorization Client (SAC) Global Clock Resource (GCR) Unified Security Resource (USR) Security Policy Services Security Authorization Services Security Registration Services Security Analysis and Tracking (SAT) SACMAT 02 -29
Candidate Security Approach Software Architecture Database Client COTS Client Lookup Service Wrapped Resource for Database Application Wrapped Resource for COTS Application Java Client General Resource Wrapped Resource for Legacy Application Software Agent Legacy Client Security Policy Client (SPC) Lookup Service Security Authorization Client (SAC) Global Clock Resource (GCR) Unified Security Resource (USR) Security Policy Services Security Authorization Services Security Registration Services Security Analysis and Tracking (SAT) SACMAT 02 -29
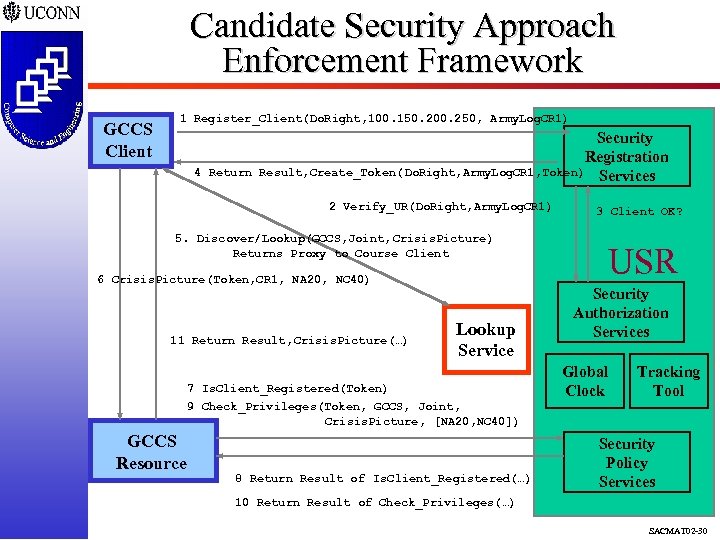 Candidate Security Approach Enforcement Framework GCCS Client 1 Register_Client(Do. Right, 100. 150. 200. 250, Army. Log. CR 1) 4 Return Security Registration Result, Create_Token( Do. Right, Army. Log. CR 1, Token) Services 2 Verify_UR(Do. Right, Army. Log. CR 1) 5. Discover/Lookup(GCCS, Joint, Crisis. Picture) Returns Proxy to Course Client 6 Crisis. Picture(Token, CR 1, NA 20, NC 40) 11 Return Result, Crisis. Picture(…) Lookup Service 7 Is. Client_Registered(Token) 9 Check_Privileges(Token, GCCS, Joint, Crisis. Picture, [NA 20, NC 40]) GCCS Resource 8 Return Result of Is. Client_Registered(…) 3 Client OK? USR Security Authorization Services Global Clock Tracking Tool Security Policy Services 10 Return Result of Check_Privileges(…) SACMAT 02 -30
Candidate Security Approach Enforcement Framework GCCS Client 1 Register_Client(Do. Right, 100. 150. 200. 250, Army. Log. CR 1) 4 Return Security Registration Result, Create_Token( Do. Right, Army. Log. CR 1, Token) Services 2 Verify_UR(Do. Right, Army. Log. CR 1) 5. Discover/Lookup(GCCS, Joint, Crisis. Picture) Returns Proxy to Course Client 6 Crisis. Picture(Token, CR 1, NA 20, NC 40) 11 Return Result, Crisis. Picture(…) Lookup Service 7 Is. Client_Registered(Token) 9 Check_Privileges(Token, GCCS, Joint, Crisis. Picture, [NA 20, NC 40]) GCCS Resource 8 Return Result of Is. Client_Registered(…) 3 Client OK? USR Security Authorization Services Global Clock Tracking Tool Security Policy Services 10 Return Result of Check_Privileges(…) SACMAT 02 -30
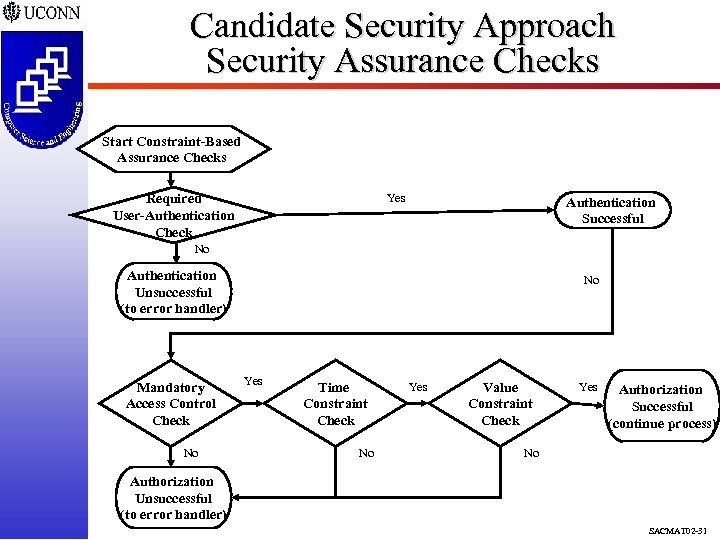 Candidate Security Approach Security Assurance Checks Start Constraint-Based Assurance Checks Required User-Authentication Check Yes Authentication Successful No Authentication Unsuccessful (to error handler) Mandatory Access Control Check No No Yes Time Constraint Check No Yes Value Constraint Check Yes Authorization Successful (continue process) No Authorization Unsuccessful (to error handler) SACMAT 02 -31
Candidate Security Approach Security Assurance Checks Start Constraint-Based Assurance Checks Required User-Authentication Check Yes Authentication Successful No Authentication Unsuccessful (to error handler) Mandatory Access Control Check No No Yes Time Constraint Check No Yes Value Constraint Check Yes Authorization Successful (continue process) No Authorization Unsuccessful (to error handler) SACMAT 02 -31
 Conclusions and Ongoing Work m m m Explored Information Sharing Issues Defined the Dynamic Coalition Problem Discussed Coalition Participants Examined GCCS and Needed Improvements Offered Candidate Security Approach Related/Ongoing Research Includes q Support for Mandatory Access Controls q Role Deconfliction and Mutual Exclusion q User Constraints q User Role Delegation Authority q www. engr. uconn. edu/~steve/DSEC/dsec. html SACMAT 02 -32
Conclusions and Ongoing Work m m m Explored Information Sharing Issues Defined the Dynamic Coalition Problem Discussed Coalition Participants Examined GCCS and Needed Improvements Offered Candidate Security Approach Related/Ongoing Research Includes q Support for Mandatory Access Controls q Role Deconfliction and Mutual Exclusion q User Constraints q User Role Delegation Authority q www. engr. uconn. edu/~steve/DSEC/dsec. html SACMAT 02 -32


