09a74857bd81bf94ddb1155e92c916c4.ppt
- Количество слайдов: 22
 Information Security Presentation April 2 nd, 2014 7: 30 am-9: 00 am Air Force Aerospace Science Class Major F. Larry Zentner, Jr.
Information Security Presentation April 2 nd, 2014 7: 30 am-9: 00 am Air Force Aerospace Science Class Major F. Larry Zentner, Jr.
 The Hub of Innovation • UNM is CAE/IAE and CAE/R • CAE/IAE - National Centers of Academic Excellence in Information Assurance Education • CAE/R - National Centers of Academic Excellence in Information Assurance Research
The Hub of Innovation • UNM is CAE/IAE and CAE/R • CAE/IAE - National Centers of Academic Excellence in Information Assurance Education • CAE/R - National Centers of Academic Excellence in Information Assurance Research
 Why is this relevant to you?
Why is this relevant to you?
 Demographics of Internet Users • U. S. Census Bureau reports that in 2012 74. 8% of all households in US carry some form of internet connection – The thing that everyone wants all the time Internet - 94. 8% of all US households with a computer use it to connect to the Internet
Demographics of Internet Users • U. S. Census Bureau reports that in 2012 74. 8% of all households in US carry some form of internet connection – The thing that everyone wants all the time Internet - 94. 8% of all US households with a computer use it to connect to the Internet
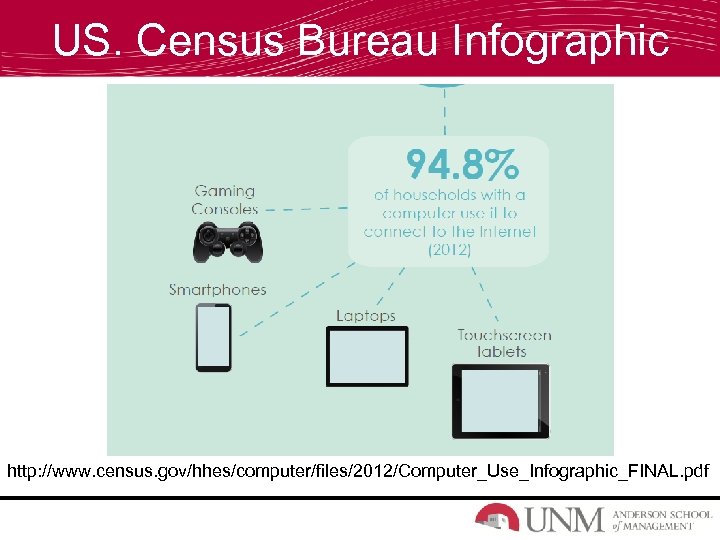 US. Census Bureau Infographic http: //www. census. gov/hhes/computer/files/2012/Computer_Use_Infographic_FINAL. pdf
US. Census Bureau Infographic http: //www. census. gov/hhes/computer/files/2012/Computer_Use_Infographic_FINAL. pdf
 The good, the bad and the ugly • The necessity of being connected via computers, tablets, smartphones, PDAs (Personal Digital Assistants- used as learning tools in classrooms, medical diagnosis/drug selection, GPS for cars, underwater divers who plan for breathing gas mixtures and decompression schedules and many more uses) …………
The good, the bad and the ugly • The necessity of being connected via computers, tablets, smartphones, PDAs (Personal Digital Assistants- used as learning tools in classrooms, medical diagnosis/drug selection, GPS for cars, underwater divers who plan for breathing gas mixtures and decompression schedules and many more uses) …………
 The good, the bad and the ugly • calls for increasing self-awareness when – roaming carefree in the Internet fields (browsing) – telling your friends where you will meet (text messaging via applications such as Cacao. Talk, Skype, Facebook messages, Whats. App) – shooting an email (via Comcast. net, AOL, Gmail)
The good, the bad and the ugly • calls for increasing self-awareness when – roaming carefree in the Internet fields (browsing) – telling your friends where you will meet (text messaging via applications such as Cacao. Talk, Skype, Facebook messages, Whats. App) – shooting an email (via Comcast. net, AOL, Gmail)
 The bad and the ugly – announcing where you are and what you are doing (Google+, Waze Social GPS Maps & Traffic, Life 360 – Family Locator) • What does it all mean for me? The more information you exchange on networks (intrawebs or Wi. Fi), the more vulnerable your information becomes The inevitable truth is that risks with your internet use will only increase in the future.
The bad and the ugly – announcing where you are and what you are doing (Google+, Waze Social GPS Maps & Traffic, Life 360 – Family Locator) • What does it all mean for me? The more information you exchange on networks (intrawebs or Wi. Fi), the more vulnerable your information becomes The inevitable truth is that risks with your internet use will only increase in the future.
 Hacked Companies • An undisclosed number of Yahoo’s e-mail accounts were hacked in January, 2014 • Username and passwords were compromised • Hackers were hunting for additional e-mail addresses to send spam and scam e-mails – phishing • Hacking banking and shopping sites is easier – email users use repeated passwords that are recovered/changed by e-mail
Hacked Companies • An undisclosed number of Yahoo’s e-mail accounts were hacked in January, 2014 • Username and passwords were compromised • Hackers were hunting for additional e-mail addresses to send spam and scam e-mails – phishing • Hacking banking and shopping sites is easier – email users use repeated passwords that are recovered/changed by e-mail
 The good and the bad • The Internet does not discriminate against intent – Hobbyist and professional hackers, even acquaintances who wish to do harm unto others – Law-abiding and with high personal and work ethic citizens – Employees in a company who inadvertently or intentionally send out company information to outsiders
The good and the bad • The Internet does not discriminate against intent – Hobbyist and professional hackers, even acquaintances who wish to do harm unto others – Law-abiding and with high personal and work ethic citizens – Employees in a company who inadvertently or intentionally send out company information to outsiders
 Fumbles on Twitter • Chelsea Handler on Oscar-winning movie: "Congratulations #12 yearsaslave Go to Africa or buy #ugandabekiddingme http: //amzn. to/1 de 1 ka 9 #aheadofthecurve #Oscars. “ And "#Angelina. Jolie just filed adoption papers #lupitanyongo #Oscars @chelseahandler. ” Always be self-aware when online and offline!
Fumbles on Twitter • Chelsea Handler on Oscar-winning movie: "Congratulations #12 yearsaslave Go to Africa or buy #ugandabekiddingme http: //amzn. to/1 de 1 ka 9 #aheadofthecurve #Oscars. “ And "#Angelina. Jolie just filed adoption papers #lupitanyongo #Oscars @chelseahandler. ” Always be self-aware when online and offline!
 Origin of risks • Where do risks come from? – Your Wifi and Bluetooth-enabled devices (smartphones, Xbox, printers, laptops) – Your online accounts (Gmail, Amazon) – You In the end, Computer and Internet Security is all about you.
Origin of risks • Where do risks come from? – Your Wifi and Bluetooth-enabled devices (smartphones, Xbox, printers, laptops) – Your online accounts (Gmail, Amazon) – You In the end, Computer and Internet Security is all about you.
![Review [1] • Computer security (ex: firewall hardware) VS • Internet security (ex: Antivirus, Review [1] • Computer security (ex: firewall hardware) VS • Internet security (ex: Antivirus,](https://present5.com/presentation/09a74857bd81bf94ddb1155e92c916c4/image-13.jpg) Review [1] • Computer security (ex: firewall hardware) VS • Internet security (ex: Antivirus, Internet Security Software Suites, spyware+adware protection, firewall software)
Review [1] • Computer security (ex: firewall hardware) VS • Internet security (ex: Antivirus, Internet Security Software Suites, spyware+adware protection, firewall software)
 Cybersecurity • Evolution from computer security in World War II through Internet security of 1960 s and cybersecurity of 1990 s and beyond
Cybersecurity • Evolution from computer security in World War II through Internet security of 1960 s and cybersecurity of 1990 s and beyond
 Firewall • How to turn on the Firewall on your home computer (XP/Windows Vista/7/8) http: //www. microsoft. com/enus/showcase/details. aspx? uuid=606771 cc -ac 77 -4 deb-af 3 b-185690 bd 57 ff
Firewall • How to turn on the Firewall on your home computer (XP/Windows Vista/7/8) http: //www. microsoft. com/enus/showcase/details. aspx? uuid=606771 cc -ac 77 -4 deb-af 3 b-185690 bd 57 ff
 Security News • A major cheating scandal erupted in a high school in Gallup - January, 2014 • A student looked over the shoulder of a teacher and got password to the grade book • A new academic fraud policy will be implemented in 2015 • What more should the high school administration do?
Security News • A major cheating scandal erupted in a high school in Gallup - January, 2014 • A student looked over the shoulder of a teacher and got password to the grade book • A new academic fraud policy will be implemented in 2015 • What more should the high school administration do?
![Security • First step to your computer security: – [Activity] Passwords 3 min – Security • First step to your computer security: – [Activity] Passwords 3 min –](https://present5.com/presentation/09a74857bd81bf94ddb1155e92c916c4/image-17.jpg) Security • First step to your computer security: – [Activity] Passwords 3 min – http: //www. google. com/goodtoknow/onlinesafety/passwords/ – Create a password that makes a sense to you and only you and is hard to guess – [Activity] Conclusion
Security • First step to your computer security: – [Activity] Passwords 3 min – http: //www. google. com/goodtoknow/onlinesafety/passwords/ – Create a password that makes a sense to you and only you and is hard to guess – [Activity] Conclusion
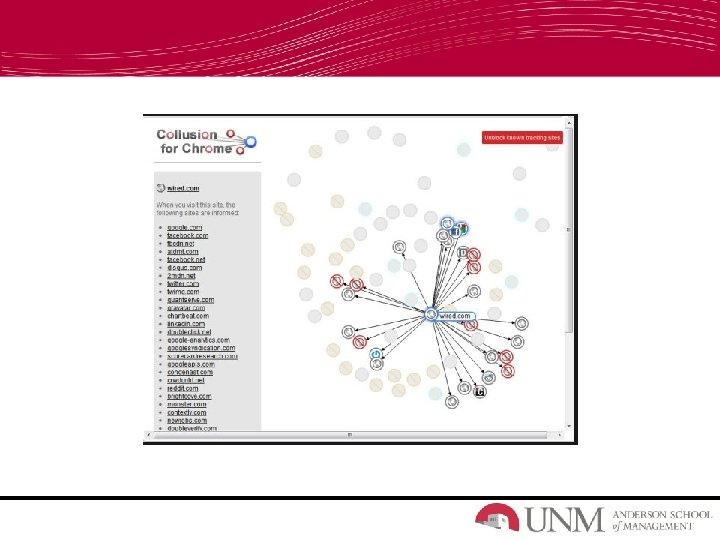
 Browser Security • Chrome Collusion - helps you visualize with graphs and block invisible websites that track you • Why are your steps tracked while you are browsing? Cookies – not as sweet as you may think http: //www. youtube. com/watch? v=z. P 79 Iwm 0 xb. A
Browser Security • Chrome Collusion - helps you visualize with graphs and block invisible websites that track you • Why are your steps tracked while you are browsing? Cookies – not as sweet as you may think http: //www. youtube. com/watch? v=z. P 79 Iwm 0 xb. A
 Pablos Holman, World Class Hacker and Inventor, TEDx. Youth@Midwest, 6: 00/17: 50 http: //www. youtube. com/watch? v=hq. Kaf. I 7 A md 8
Pablos Holman, World Class Hacker and Inventor, TEDx. Youth@Midwest, 6: 00/17: 50 http: //www. youtube. com/watch? v=hq. Kaf. I 7 A md 8
 “All your devices can be hacked” by Avi Rubin, TEDx. Mid. Atlantic, 16: 56 http: //www. youtube. com/watch? v=metk. Ee. Zv HTg
“All your devices can be hacked” by Avi Rubin, TEDx. Mid. Atlantic, 16: 56 http: //www. youtube. com/watch? v=metk. Ee. Zv HTg
 All about YOU • Questions? • Contact information: • Alex Seazzu, roma@unm. edu
All about YOU • Questions? • Contact information: • Alex Seazzu, roma@unm. edu


