5417b299627f760d6bc6f3e7cbba5c3a.ppt
- Количество слайдов: 17

Information Security of Embedded Systems 3. 2. 2010: Algorithms and Measures Prof. Dr. Holger Schlingloff Institut für Informatik und Fraunhofer FIRST Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010

Structure 1. Introductory example 2. Embedded systems engineering 1. definitions and terms 2. design principles 3. Foundations of security 1. threats, attacks, measures 2. construction of safe systems 4. Design of secure systems 1. design challenges 2. safety modelling and assessment 3. cryptographic algorithms Embedded Security © Prof. Dr. H. Schlingloff 2010 5. Communication of embedded systems 1. 2. remote access sensor networks 6. Algorithms and measures 1. 2. 3. 4. digital signatures key management authentication authorization 7. Formal methods for security 1. 2. protocol verification logics and proof methods 3. 2. 2010 2

Digital Signatures • Public-key cryptography § A publishes his/her public key on his blog, mail and web site § If A encodes some text with the private key, anybody can decrypt it with this public key (or, vice versa, anybody encrypts with public key) § Hence, if we trust in A’s private key’s privacy, we know that A must have encrypted it (or, vice versa, only A can read it) § Or do we? • Public key cryptography – privacy § no unauthorized reading of content • Hash codes – integrity § no modification of messages • Digital signatures – authenticity § no faking of sender’s identity Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 3
Digital Certificates and Key Integrity • Problem in the above approach: attribution of private key to a • • person (attacker can generate a key and substitute it) Authenticity of public key? Solutions: § social processes (e. g. , ebay) § guaranteed by trust centre or other certification authority • Technique § § § TC generates public/private key pair KAE, KAD for A TC signs public key KAD by encoding it with its own private key KTCE A receives KAE and {KAD}KTCE B can check authenticity of {KAD}KTCE via KTCD problem: authenticity of KTCE ! Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 4
PKI (public key infrastructure) Functionality of a “real” signature: § § identification of signed originality of document contract, agreement to content emphasis of importance • Problems: forged signatures, fax • machines, signature machines Hierarchy of certification authorities (witnesses, notary etc) Digital equivalents: • Hierarchy of certification authorities (Trust centre, BSI) • Personalisation of private key (smart cards, picture ID) • Inhibit publication or transfer of private key by § black lists, white lists § penalties § legal measures Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 5

Key exchange and -management • Problem of authenticity of the communication partners: How do communication partners know their mutual identity? (the same problem appears in ordinary surface mail) • Solutions § Personalausweis, social security card § smart cards and trust centres: a trustworthy third party. User inserts card into machine, types in his PIN, the rest is automated • Which protocols/algorithms are used? Def. : A protocol is a distributed algorithm involving several parties, which is defined by a sequence of steps which fix the actions and messages between the parties to achieve the desired goal Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 6
Key Establishment • Def. : Key establishment (Schlüsselfestlegung) is the process or protocol • to establish a common secret between two or more parties for later cryptographic use Two variants of key establishment: § Key transport (Schlüsselaustausch) - One party creates the key and sends it to the other(s) - The key is calculated by all involved parties from information contributed by all parties. § Key agreement (Schlüsselvereinbarung) Keys by itself can be symmetric or asymmetric, and dynamic (for one session only) or static (a priori, for several sessions) Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 7

Prerequisites for key establishment • Trusted third party (Trusted server, authentication server) S § stepwise building of trust • Assumptions on A and S, e. g. , each communication partner A received from S a key which is only known to A and S § A must identify him/herself personally with S § S must keep the key secret (prevention against house braking, burglary, fraud, . . . ) § A must keep the key secret (e. g. by Smart. Card+PIN; legal consequences) • Assumptions on attackers § § recording, modification, deletion, detour, or replay of packets initiation of the protocol or interference with it no possibility for cryptanalysis known-key-attack: does a breaking of the key for one session lead to the possibility of calculating subsequent keys? Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 8

Protocols for key exchange Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 9
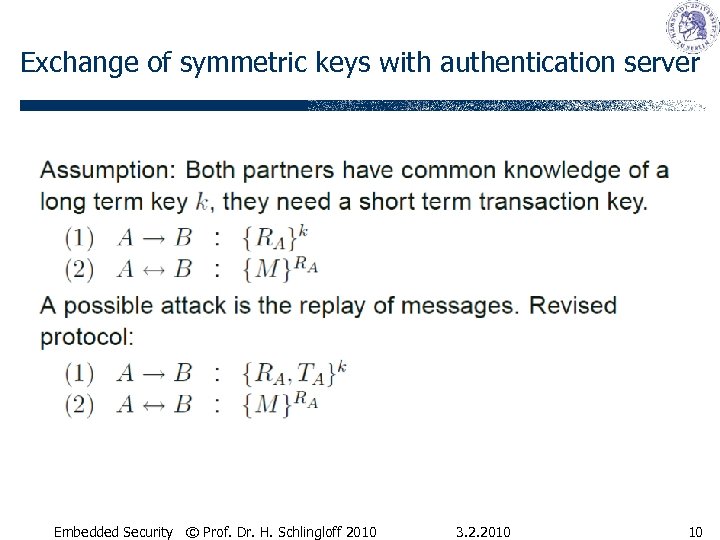
Exchange of symmetric keys with authentication server Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 10

Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 11
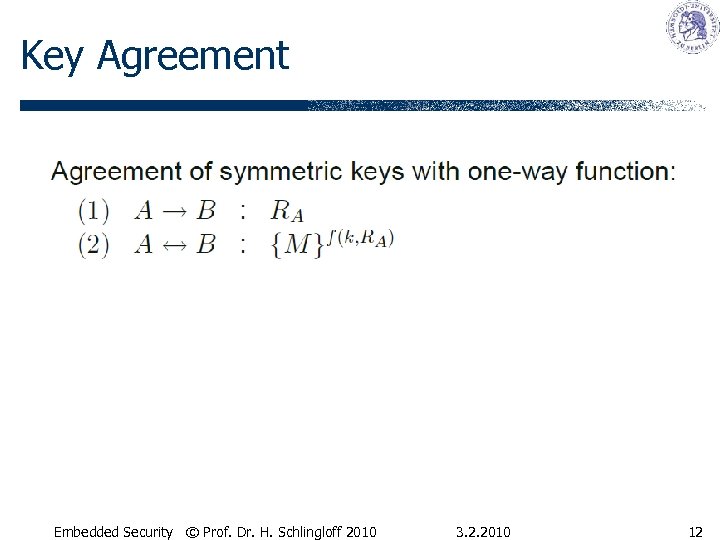
Key Agreement Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 12

Symmetric keys with authentication server Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 13
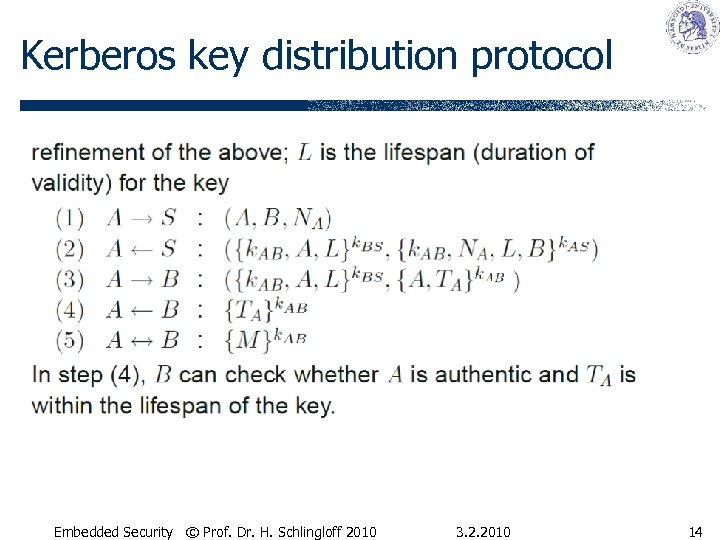
Kerberos key distribution protocol Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 14

Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 15
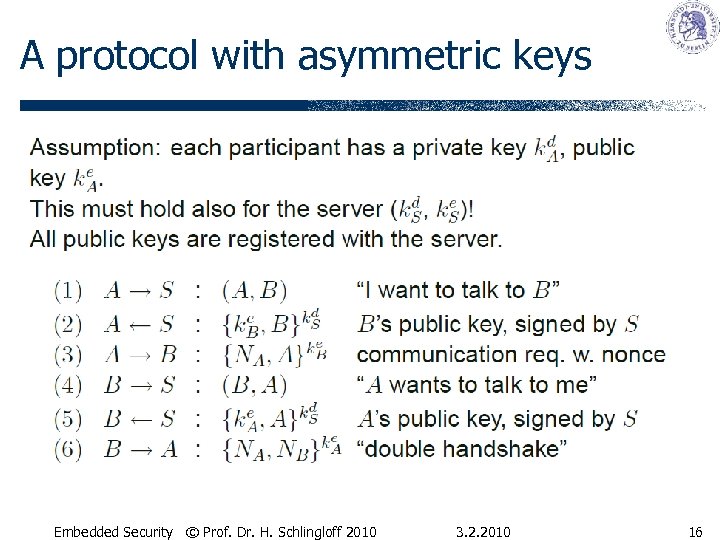
A protocol with asymmetric keys Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 16
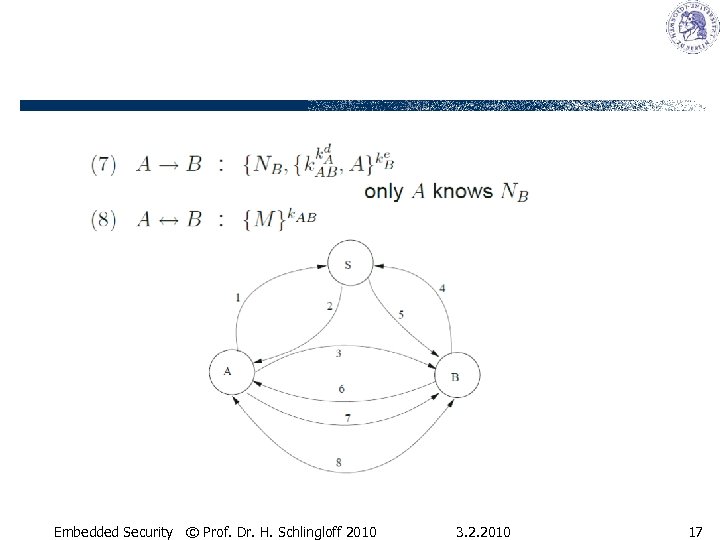
Embedded Security © Prof. Dr. H. Schlingloff 2010 3. 2. 2010 17
5417b299627f760d6bc6f3e7cbba5c3a.ppt