cbe2c383e11b8b61e12f8be8d72084ab.ppt
- Количество слайдов: 28
 Information Security and Research Data Management Data Security, Data Collection Options, and Data Analysis Plans: Thinking about the End from the Beginning Todd Ferris, MD Associate CIO, IT Services Director, Informatics Services Privacy and Security Officer Information Resources and Technology Stanford University School of Medicine © 2008. All rights reserved.
Information Security and Research Data Management Data Security, Data Collection Options, and Data Analysis Plans: Thinking about the End from the Beginning Todd Ferris, MD Associate CIO, IT Services Director, Informatics Services Privacy and Security Officer Information Resources and Technology Stanford University School of Medicine © 2008. All rights reserved.
 2 Overview Information Security Requirements § HIPAA § Stanford University Security Policies § FISMA & California SB 1386 & AB 1298 Conducting a Secure Research Study § Data security plans § Secure data collection § Data analysis and sharing Todd Ferris, MD, MS 5/22/2008
2 Overview Information Security Requirements § HIPAA § Stanford University Security Policies § FISMA & California SB 1386 & AB 1298 Conducting a Secure Research Study § Data security plans § Secure data collection § Data analysis and sharing Todd Ferris, MD, MS 5/22/2008
 3 HIPAA § Federal regulation covers privacy, security and much, much more! § HIPAA privacy & security regulations only apply to protected health information (PHI) § Security regs. only apply to electronic PHI (e. PHI) § It is very important to have a good, solid understanding of what is PHI and what is not. Todd Ferris, MD, MS 5/22/2008
3 HIPAA § Federal regulation covers privacy, security and much, much more! § HIPAA privacy & security regulations only apply to protected health information (PHI) § Security regs. only apply to electronic PHI (e. PHI) § It is very important to have a good, solid understanding of what is PHI and what is not. Todd Ferris, MD, MS 5/22/2008
 4 What the rule says Protected Health Information § Protected health information means individually identifiable health information, that is transmitted by electronic media, maintained in electronic media; or transmitted or maintained in any other form or medium. Todd Ferris, MD, MS 5/22/2008
4 What the rule says Protected Health Information § Protected health information means individually identifiable health information, that is transmitted by electronic media, maintained in electronic media; or transmitted or maintained in any other form or medium. Todd Ferris, MD, MS 5/22/2008
 5 What the rule says § Individually identifiable health information is information that is a subset of health information, including demographic information collected from an individual, and: Is created or received by a health care provider, health plan, employer, or health care clearinghouse; and relates to the past, present, or future physical or mental health or condition of an individual; the provision of health care to an individual; or the past, present, or future payment for the provision of health care to an individual; and that identifies the individual; or with respect to which there is a reasonable basis to believe the information can be used to identify the individual. Todd Ferris, MD, MS 5/22/2008
5 What the rule says § Individually identifiable health information is information that is a subset of health information, including demographic information collected from an individual, and: Is created or received by a health care provider, health plan, employer, or health care clearinghouse; and relates to the past, present, or future physical or mental health or condition of an individual; the provision of health care to an individual; or the past, present, or future payment for the provision of health care to an individual; and that identifies the individual; or with respect to which there is a reasonable basis to believe the information can be used to identify the individual. Todd Ferris, MD, MS 5/22/2008
 6 What we say (i. e. Stanford’s Policies) § Protected Health Information (PHI): Health information that is created or received by a covered entity and that is individually identifiable (i. e. , is not de-identified. ) Under HIPAA, protected health information does not include: … § De-identified Information: Health information that cannot be used to identify an individual. For information regarding how to determine that health information is deidentified or to generate de-identified information, refer to the HIPAA Use and Disclosure of Protected Health Information policy, Appendix A. Todd Ferris, MD, MS 5/22/2008
6 What we say (i. e. Stanford’s Policies) § Protected Health Information (PHI): Health information that is created or received by a covered entity and that is individually identifiable (i. e. , is not de-identified. ) Under HIPAA, protected health information does not include: … § De-identified Information: Health information that cannot be used to identify an individual. For information regarding how to determine that health information is deidentified or to generate de-identified information, refer to the HIPAA Use and Disclosure of Protected Health Information policy, Appendix A. Todd Ferris, MD, MS 5/22/2008
 7 What we say in Appendix A Health information is de-identified if it does not include any of the following identifiers of the individual or of relatives, employers, or household members of the individual: § § § § Names; Geographic subdivisions smaller than a state; Dates (except year) directly related to an individual, including birth date, health care service admission or discharge dates, date of death, and all ages over 89 and all elements of dates (including year) indicative of such age, unless aggregated into a single category of ages over 89; Telephone numbers; Fax numbers; E-mail addresses; Social security numbers; § § § § § Medical record numbers; Health plan beneficiary numbers, Account numbers; Certificate/Driver’s license numbers; Vehicle identifiers and serial numbers, including license plate numbers; Device identifiers and serial numbers; Web Universal Resource Locators (URLs); Internet Protocol (IP) address numbers; Biometric identifiers, including finger and voice prints; Full face photographic images and any comparable images; and Any other unique identifying number, characteristic or code Todd Ferris, MD, MS 5/22/2008
7 What we say in Appendix A Health information is de-identified if it does not include any of the following identifiers of the individual or of relatives, employers, or household members of the individual: § § § § Names; Geographic subdivisions smaller than a state; Dates (except year) directly related to an individual, including birth date, health care service admission or discharge dates, date of death, and all ages over 89 and all elements of dates (including year) indicative of such age, unless aggregated into a single category of ages over 89; Telephone numbers; Fax numbers; E-mail addresses; Social security numbers; § § § § § Medical record numbers; Health plan beneficiary numbers, Account numbers; Certificate/Driver’s license numbers; Vehicle identifiers and serial numbers, including license plate numbers; Device identifiers and serial numbers; Web Universal Resource Locators (URLs); Internet Protocol (IP) address numbers; Biometric identifiers, including finger and voice prints; Full face photographic images and any comparable images; and Any other unique identifying number, characteristic or code Todd Ferris, MD, MS 5/22/2008
 8 My brain is hurting! What must I know? § Will the study involve any PHI, if so which parts § Collection? Almost always § Analysis? May not be needed (think codebook) § Reporting? Never!? § If you have PHI, then you must follow HIPAA policies and procedures. § If any of this PHI is stored electronically, then HIPAA security policies apply. Todd Ferris, MD, MS 5/22/2008
8 My brain is hurting! What must I know? § Will the study involve any PHI, if so which parts § Collection? Almost always § Analysis? May not be needed (think codebook) § Reporting? Never!? § If you have PHI, then you must follow HIPAA policies and procedures. § If any of this PHI is stored electronically, then HIPAA security policies apply. Todd Ferris, MD, MS 5/22/2008
 9 HIPAA Security from A-Z: Stanford Policy Statements § Audit Controls: § Stanford will support security management activities designed to detect potential security incidents by implementing hardware, software, and/or procedural mechanisms that will record and examine information systems activity. § Business Associates: § When Stanford University enters into contracts on behalf of University HIPAA Components with certain persons or entities pursuant to which the contracting party will be provided with or have access to protected health information ("PHI"), Stanford University will enter into agreements with such persons ("business associate agreements") intended to protect the privacy of PHI transmitted in connection with such relationship. Todd Ferris, MD, MS 5/22/2008
9 HIPAA Security from A-Z: Stanford Policy Statements § Audit Controls: § Stanford will support security management activities designed to detect potential security incidents by implementing hardware, software, and/or procedural mechanisms that will record and examine information systems activity. § Business Associates: § When Stanford University enters into contracts on behalf of University HIPAA Components with certain persons or entities pursuant to which the contracting party will be provided with or have access to protected health information ("PHI"), Stanford University will enter into agreements with such persons ("business associate agreements") intended to protect the privacy of PHI transmitted in connection with such relationship. Todd Ferris, MD, MS 5/22/2008
 10 HIPAA Security: Stanford Policy Statements § Computing Devices and Electronic Storage Media: § SUHC will implement reasonable and appropriate measures designed to ensure that computing devices and electronic storage media covered by this policy will be installed, located and used in a way that minimizes the unauthorized or incidental disclosure of e. PHI. SUHC workforce and business associates will employ reasonable and appropriate safeguards when receiving, storing, using, transferring or disposing of computing devices or electronic storage media that store e. PHI. § Contingency Planning: § SUHC will develop and implement for each information system a contingency plan for responding to and recovering from system outages or other emergencies that may damage or make unavailable the system or e. PHI (e. g. , natural disaster, fire, vandalism, system failure, software corruption, virus, operator error). Todd Ferris, MD, MS 5/22/2008
10 HIPAA Security: Stanford Policy Statements § Computing Devices and Electronic Storage Media: § SUHC will implement reasonable and appropriate measures designed to ensure that computing devices and electronic storage media covered by this policy will be installed, located and used in a way that minimizes the unauthorized or incidental disclosure of e. PHI. SUHC workforce and business associates will employ reasonable and appropriate safeguards when receiving, storing, using, transferring or disposing of computing devices or electronic storage media that store e. PHI. § Contingency Planning: § SUHC will develop and implement for each information system a contingency plan for responding to and recovering from system outages or other emergencies that may damage or make unavailable the system or e. PHI (e. g. , natural disaster, fire, vandalism, system failure, software corruption, virus, operator error). Todd Ferris, MD, MS 5/22/2008
 11 HIPAA Security: Stanford Policy Statements § Data and System Integrity Policy: § SUHC will protect e. PHI from unauthorized alteration, destruction or disclosure by implementing reasonable and appropriate measures to facilitate the maintenance of reliable system components, workflows, and data. § Email and Other Electronic Messaging of e. PHI § SUHC will implement reasonable and appropriate measures to guard against unauthorized access to and protect the integrity and confidentiality of e. PHI that is being sent, received, or stored using an e-mail or other electronic messaging system ("electronic messaging"). Todd Ferris, MD, MS 5/22/2008
11 HIPAA Security: Stanford Policy Statements § Data and System Integrity Policy: § SUHC will protect e. PHI from unauthorized alteration, destruction or disclosure by implementing reasonable and appropriate measures to facilitate the maintenance of reliable system components, workflows, and data. § Email and Other Electronic Messaging of e. PHI § SUHC will implement reasonable and appropriate measures to guard against unauthorized access to and protect the integrity and confidentiality of e. PHI that is being sent, received, or stored using an e-mail or other electronic messaging system ("electronic messaging"). Todd Ferris, MD, MS 5/22/2008
 12 HIPAA Security: Stanford Policy Statements § Facilities Security: § SUHC will limit physical access to its information systems that contain e. PHI by implementing reasonable and appropriate measures to allow only authorized persons to access the facilities in which those information systems are housed. § Information Access Control: § SUHC will implement reasonable and appropriate measures to (i) limit access to e. PHI only to those persons or automated processes that have been granted access rights based on their required functions and (ii) prevent those who have not been granted those rights from obtaining access to e. PHI. Todd Ferris, MD, MS 5/22/2008
12 HIPAA Security: Stanford Policy Statements § Facilities Security: § SUHC will limit physical access to its information systems that contain e. PHI by implementing reasonable and appropriate measures to allow only authorized persons to access the facilities in which those information systems are housed. § Information Access Control: § SUHC will implement reasonable and appropriate measures to (i) limit access to e. PHI only to those persons or automated processes that have been granted access rights based on their required functions and (ii) prevent those who have not been granted those rights from obtaining access to e. PHI. Todd Ferris, MD, MS 5/22/2008
 13 HIPAA Security: Stanford Policy Statements § Security Management: § SUHC will take reasonable and appropriate precautions to prevent, detect, contain and correct security violations. § Transmission of e. PHI: § SUHC will implement reasonable and appropriate measures to guard against unauthorized access to and protect the integrity and confidentiality of e. PHI that is transmitted over an electronic communications network while the data is in transit when the transmission is initiated by SUHC. Todd Ferris, MD, MS 5/22/2008
13 HIPAA Security: Stanford Policy Statements § Security Management: § SUHC will take reasonable and appropriate precautions to prevent, detect, contain and correct security violations. § Transmission of e. PHI: § SUHC will implement reasonable and appropriate measures to guard against unauthorized access to and protect the integrity and confidentiality of e. PHI that is transmitted over an electronic communications network while the data is in transit when the transmission is initiated by SUHC. Todd Ferris, MD, MS 5/22/2008
 14 My brain hurts again, isn’t there an easier way? § Unfortunately, systems that hold e. PHI must comply with these policies. § However, next section will talk about some options that speed compliance. § The School of Medicine Information Security group is available to review any system. Todd Ferris, MD, MS 5/22/2008
14 My brain hurts again, isn’t there an easier way? § Unfortunately, systems that hold e. PHI must comply with these policies. § However, next section will talk about some options that speed compliance. § The School of Medicine Information Security group is available to review any system. Todd Ferris, MD, MS 5/22/2008
 15 Federal Information Security Management Act, aka FISMA § Signed into law December 2002 § Title III of the E-Government Act § “Requires each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other source. ” Todd Ferris, MD, MS 5/22/2008
15 Federal Information Security Management Act, aka FISMA § Signed into law December 2002 § Title III of the E-Government Act § “Requires each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other source. ” Todd Ferris, MD, MS 5/22/2008
 16 The VA and FISMA § As a federal agency, VA hospitals fall under FISMA. § All systems that hold VA data must be FISMA certified. § Problem – How to FISMA certify your system for a VA research project? § http: //en. wikipedia. org/wiki/Federal_Information_Security_Manageme nt_Act_of_2002 § http: //csrc. nist. gov/groups/SMA/fisma/overview. html Todd Ferris, MD, MS 5/22/2008
16 The VA and FISMA § As a federal agency, VA hospitals fall under FISMA. § All systems that hold VA data must be FISMA certified. § Problem – How to FISMA certify your system for a VA research project? § http: //en. wikipedia. org/wiki/Federal_Information_Security_Manageme nt_Act_of_2002 § http: //csrc. nist. gov/groups/SMA/fisma/overview. html Todd Ferris, MD, MS 5/22/2008
 17 Last but not least: California’s SB 1386 and AB 1298 § California leads the nation in laws protecting its residents against identity theft. § SB 1386 – September 2002 § Requires notification if “personal information” is potentially compromised § Personal information includes SS #, banking information… § AB 1298 – October 2007 § Adds medical information and health insurance information to definition of “personal information” Todd Ferris, MD, MS 5/22/2008
17 Last but not least: California’s SB 1386 and AB 1298 § California leads the nation in laws protecting its residents against identity theft. § SB 1386 – September 2002 § Requires notification if “personal information” is potentially compromised § Personal information includes SS #, banking information… § AB 1298 – October 2007 § Adds medical information and health insurance information to definition of “personal information” Todd Ferris, MD, MS 5/22/2008
 Conducting a Secure Research Study Thinking about the End from the Beginning © 2008. All rights reserved.
Conducting a Secure Research Study Thinking about the End from the Beginning © 2008. All rights reserved.
 19 Plan, then Do § Don’t leave the security of a research study until the last minute. § A good study will have contemplated how security will be handled even before submitting to the IRB. § Many granting agencies require a data security plan. A lack of planning on your part doesn’t constitute an emergency on my part. Todd Ferris, MD, MS 5/22/2008
19 Plan, then Do § Don’t leave the security of a research study until the last minute. § A good study will have contemplated how security will be handled even before submitting to the IRB. § Many granting agencies require a data security plan. A lack of planning on your part doesn’t constitute an emergency on my part. Todd Ferris, MD, MS 5/22/2008
 20 How to approach a data security plan § All good security programs start with a risk assessment! § § § How much data (# of patients, # of variables) How sensitive is the data (HIV, Ψ, SS#, etc. ) How many will have access How long will it be used Where will the data be stored Will the data be transferred § The risk assessment will drive the security techniques employed. Todd Ferris, MD, MS 5/22/2008
20 How to approach a data security plan § All good security programs start with a risk assessment! § § § How much data (# of patients, # of variables) How sensitive is the data (HIV, Ψ, SS#, etc. ) How many will have access How long will it be used Where will the data be stored Will the data be transferred § The risk assessment will drive the security techniques employed. Todd Ferris, MD, MS 5/22/2008
 21 How to write a data security plan § Start at the beginning - Go from data collection to final analysis and don’t forget the eventual close down. § Describe the security measures that will be put into place for each natural segment of the research. Use the HIPAA security policies to walk through each pertinent area. § Take your time and don’t forget about the So. M Information Security group. We love to proofread! Todd Ferris, MD, MS 5/22/2008
21 How to write a data security plan § Start at the beginning - Go from data collection to final analysis and don’t forget the eventual close down. § Describe the security measures that will be put into place for each natural segment of the research. Use the HIPAA security policies to walk through each pertinent area. § Take your time and don’t forget about the So. M Information Security group. We love to proofread! Todd Ferris, MD, MS 5/22/2008
 22 Secure Data Collection § Data collection poses many security threats § Many touch points § Poorly designed/implemented systems § Frequent movement of data § Requires significant attention of security solutions Todd Ferris, MD, MS 5/22/2008
22 Secure Data Collection § Data collection poses many security threats § Many touch points § Poorly designed/implemented systems § Frequent movement of data § Requires significant attention of security solutions Todd Ferris, MD, MS 5/22/2008
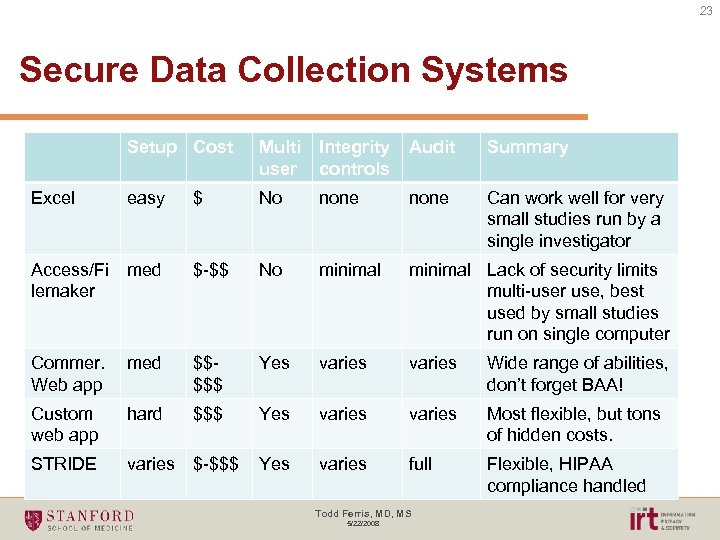 23 Secure Data Collection Systems Setup Cost Multi user Integrity controls Audit Summary Excel easy $ No none Can work well for very small studies run by a single investigator Access/Fi lemaker med $-$$ No minimal Lack of security limits multi-user use, best used by small studies run on single computer Commer. Web app med $$$$$ Yes varies Wide range of abilities, don’t forget BAA! Custom web app hard $$$ Yes varies Most flexible, but tons of hidden costs. STRIDE varies $-$$$ Yes varies full Flexible, HIPAA compliance handled Todd Ferris, MD, MS 5/22/2008
23 Secure Data Collection Systems Setup Cost Multi user Integrity controls Audit Summary Excel easy $ No none Can work well for very small studies run by a single investigator Access/Fi lemaker med $-$$ No minimal Lack of security limits multi-user use, best used by small studies run on single computer Commer. Web app med $$$$$ Yes varies Wide range of abilities, don’t forget BAA! Custom web app hard $$$ Yes varies Most flexible, but tons of hidden costs. STRIDE varies $-$$$ Yes varies full Flexible, HIPAA compliance handled Todd Ferris, MD, MS 5/22/2008
 24 A message from our sponsor § STRIDE § Run by the Center for Clinical Informatics § Houses clinical data from both LPCH and SHC that can be used for research § Also supports many research databases § Informatics Consultation Service § http: //clinicalinformatics. stanford. edu/consultation/ § Free!* § Will help with data dictionary design as well as database design Todd Ferris, MD, MS 5/22/2008
24 A message from our sponsor § STRIDE § Run by the Center for Clinical Informatics § Houses clinical data from both LPCH and SHC that can be used for research § Also supports many research databases § Informatics Consultation Service § http: //clinicalinformatics. stanford. edu/consultation/ § Free!* § Will help with data dictionary design as well as database design Todd Ferris, MD, MS 5/22/2008
 25 Data Analysis § From a security standpoint, it is best to use deidentified data in the analysis phase. § Dates can present an issue. Consider converting to day # and age. § If can’t be de-identified must be handled as PHI. § Ensure biostatistician or others doing analysis are aware and prepared to handle PHI. § Secure transmission of PHI. § Secure storage and processing of PHI. § Still remove any identifiers you can, this lowers the risk Todd Ferris, MD, MS 5/22/2008
25 Data Analysis § From a security standpoint, it is best to use deidentified data in the analysis phase. § Dates can present an issue. Consider converting to day # and age. § If can’t be de-identified must be handled as PHI. § Ensure biostatistician or others doing analysis are aware and prepared to handle PHI. § Secure transmission of PHI. § Secure storage and processing of PHI. § Still remove any identifiers you can, this lowers the risk Todd Ferris, MD, MS 5/22/2008
 26 Data Sharing § Increasing requirements to make data available for analysis by others. § Must carefully review the data before posting or releasing to ensure it is deidentified. § Information Privacy office can assist in the review. Todd Ferris, MD, MS 5/22/2008
26 Data Sharing § Increasing requirements to make data available for analysis by others. § Must carefully review the data before posting or releasing to ensure it is deidentified. § Information Privacy office can assist in the review. Todd Ferris, MD, MS 5/22/2008
 27 Closing out the Study § Don’t forget this step! § Once study is over, may need to comply with retention requirements. § Only keep what is required. § Securely destroy anything that is not required or planned to be maintained. § Shredding, secure erasing, etc. § Use a secure storage service for paper documents (e. g. , Iron Mountain) § If you will be storing e. PHI, you should have had a plan for secure long term electronic storage. Todd Ferris, MD, MS 5/22/2008
27 Closing out the Study § Don’t forget this step! § Once study is over, may need to comply with retention requirements. § Only keep what is required. § Securely destroy anything that is not required or planned to be maintained. § Shredding, secure erasing, etc. § Use a secure storage service for paper documents (e. g. , Iron Mountain) § If you will be storing e. PHI, you should have had a plan for secure long term electronic storage. Todd Ferris, MD, MS 5/22/2008
 28 Don’t Panic § There are many resources to help you create a secure research study. § So. M Information Security group § Ellen Amsel, eamsel@stanford. edu § So. M Information Privacy group § Todd Ferris, tferris@stanford. edu § Center for Clinical Informatics § http: //clinicalinformatics. stanford. edu Todd Ferris, MD, MS 5/22/2008
28 Don’t Panic § There are many resources to help you create a secure research study. § So. M Information Security group § Ellen Amsel, eamsel@stanford. edu § So. M Information Privacy group § Todd Ferris, tferris@stanford. edu § Center for Clinical Informatics § http: //clinicalinformatics. stanford. edu Todd Ferris, MD, MS 5/22/2008


