908cc240cad4fc00b9cf84f5b94b98bb.ppt
- Количество слайдов: 84

Information Security and Its Impact on Business Prof. Chi-Chun Lo National Chiao-Tung University Oct. 5, 2006

INTRODUCTION

What if someone asks your CEO “How Secure is Your Corporation? " • One foot in ice water and one foot in boiling water does not mean that on average you are at room temperature. – Corporations are not monolithic, and all parts of the business don’t have (or necessarily need) the same level of security – Security is not an end state, nor can it be judged by measuring any single variable at any single point in time

Selling Security is Still a Challenge • Is the glass half empty, or is it half full? • Security is like the brakes on your car. – Their function is to slow you down – But their purpose is to allow you to go fast. Bill Malick, Gartner

Scope of Security • System Security - Mostly Technical Issues - Hardware & Software Solutions, e. g. ; Cryptography, Protocol, Security System etc. • Information Security - Mostly Managerial Issues - Business Solutions, e. g. ; Organization, Culture (Behavior), Policy, Risk Management, Standards, Legal Rights etc.
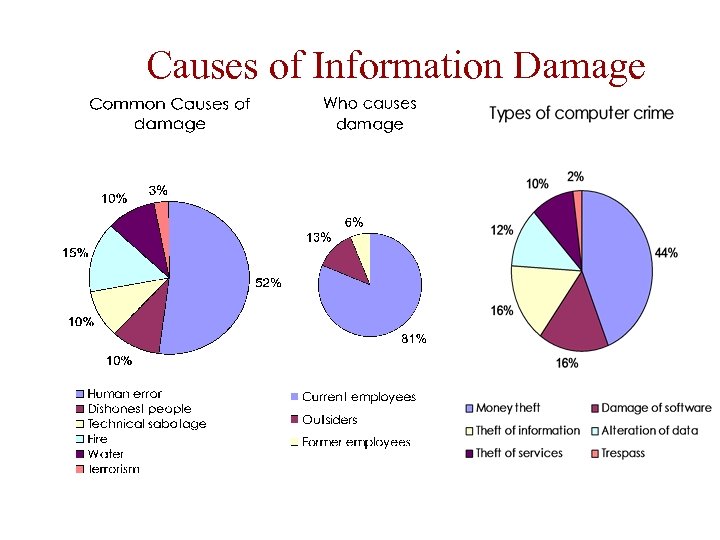
Causes of Information Damage
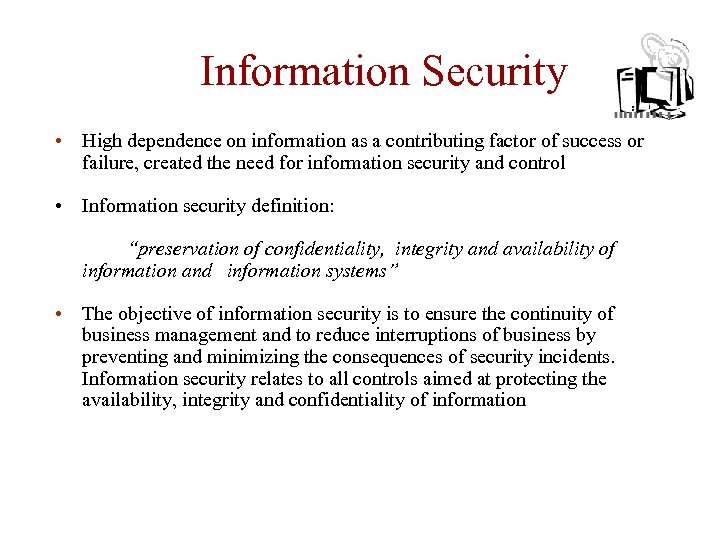
Information Security • High dependence on information as a contributing factor of success or failure, created the need for information security and control • Information security definition: “preservation of confidentiality, integrity and availability of information and information systems” • The objective of information security is to ensure the continuity of business management and to reduce interruptions of business by preventing and minimizing the consequences of security incidents. Information security relates to all controls aimed at protecting the availability, integrity and confidentiality of information
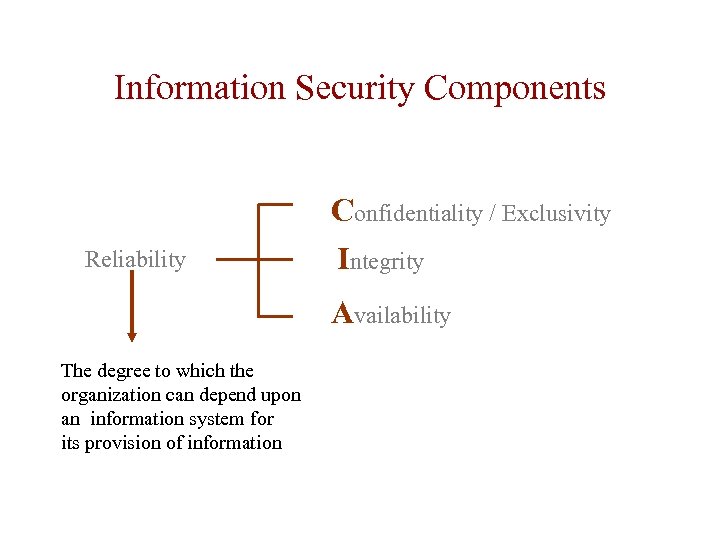
Information Security Components Reliability Confidentiality / Exclusivity Integrity Availability The degree to which the organization can depend upon an information system for its provision of information
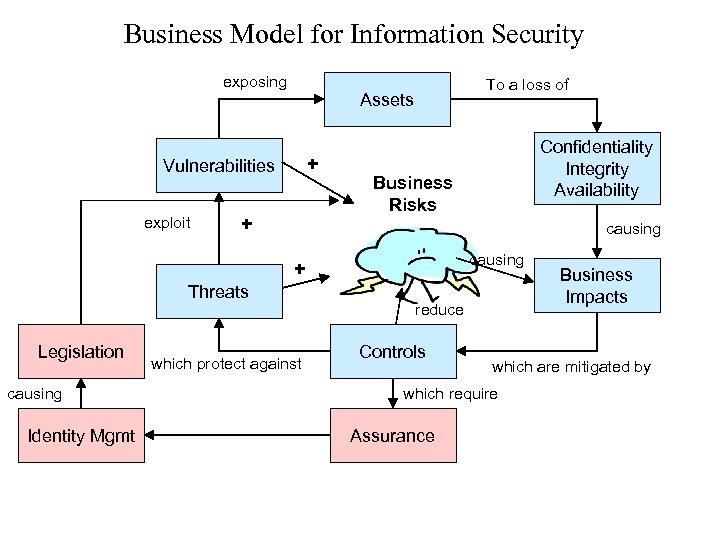
Business Model for Information Security exposing Assets + Vulnerabilities exploit To a loss of + Business Risks causing + Threats Legislation causing Identity Mgmt Confidentiality Integrity Availability which protect against reduce Controls which are mitigated by which require Assurance Business Impacts

Security Systems Development Life Cycle(SSDLC) • A systematic way of providing information security • Phases: -Phase 1: Investigation, including policy and procedure etc. -Phase 2: Analysis, including risk management etc. -Phase 3: Logical Design, including standards etc. -Phase 4: Physical Design, including technology selection etc. -Phase 5: Implementation -Phase 6: Maintenance and Change

POLICY and PROCEDURE

Policy and Procedure • • • A policy is typically a document that outlines specific requirements or rules that must be met. In the information/network security realm, policies are usually point-specific, covering a single area. For example, an “Acceptable Use” policy would cover the rules and regulations for appropriate use of the computing facilities. A standard is typically a collections or system-specific or procedural-specific requirements that must be meet by everyone. – For example, you might have a standard that describes to how to harden a Windows NT workstation for placement on an external (DMZ) network. – People must follow this standard exactly if they wish to install a Windows NT workstation on an external network segment. A guideline is typically a collection of system specific or procedural specific “suggestions” for best practice. – They are not requirements to be met, but are strongly recommended. Effective security policies make frequent references to standards and guidelines that exist within an organization.

A Security Policy Framework • Policies define appropriate behavior. • Policies set the stage in terms of what tools and procedures are needed. • Policies communicate a consensus. • Policies provide a foundation for HR action in response to inappropriate behavior. • Policies may help prosecute cases.

Importance of Security Policies • Security policies are an absolute must for any organization. • They provide the virtual glue to hold it all together. • Policies lay the ground-work. • Imagine a small city that did not have any rules? What would life be like? The same applies to your organization.

Who and What to Trust • Trust is a major principle underlying the development of security policies. • Initial step is to determine who gets access. • Deciding on level of trust is a delicate balancing act. • Too much trust may lead to eventual security problems • Too little trust may make it difficult to find and keep employees or get jobs done • How much should you trust people regarding to their access or usage of computer and network resources?

Possible Trust Models • Trust everyone all of the time: – easiest to enforce, but impractical – one bad apple can ruin the whole barrel • Trust no one at no time: – most restrictive, but also impractical – difficult to staff positions • Trust some people some of the time: – exercise caution in amount of trust given – access is given out as needed – technical controls are needed to ensure trust is not violated

Why the Political Turmoil? • People view policies as: – an impediment to productivity – measures to control behavior • People have different views about the need for security controls. • People fear policies will be difficult to follow and implement. • Policies affect everyone within the organization.

Who Should Be Concerned? • Users - policies will affect them the most. • System support personnel - they will be required to implement, comply with and support the policies. • Managers - they are concerned about protection of data and the associated cost of the policy. • Company lawyers and auditors - they are concerned about company reputation, responsibility to clients/customers.

The Policy Design Process • Choose the policy development team. • Designate a person or a group to serve as the official policy interpreter. • Decide on the scope and goals of the policy. – Scope should be a statement about who is covered by the policy. • Decide on how specific to make the policy – not meant to be a detailed implementation plan – don’t include facts which change frequently

The Policy Design Process • A sample of people affected by the policy should be provided an opportunity to review and comment • A sampling of the support staff effected by policy should have an opportunity to review it. • Incorporate policy awareness as a part of awareness employee orientation. • Provide a refresher overview course on course policies once or twice a year.

Basic Policy Requirements • Policies must: – be implementable and enforceable – be concise and easy to understand – balance protection with productivity • Policies should: – state reasons why policy is needed – describe what is covered by the policies – define contacts and responsibilities – discuss how violations will be handled

Level of Control • Security needs and culture play major role. • Security policies MUST balance level of control with level of productivity. • If policies are too restrictive, people will find ways to circumvent controls. • Technical controls are not always possible. • You must have management commitment on the level of control.

Policy Structure • Dependent on company size and goals. • One large document or several small ones? – smaller documents are easier to maintain/update • Some policies appropriate for every site, others are specific to certain environments. • Some key policies: – acceptable use – remote access – information protection – perimeter security – baseline host/device security

The Acceptable Use Policy • Discusses and defines the appropriate use of the computing resources. • Users should be required to read and sign account usage policy as part of the account policy request process. • A key policy that all sites should have.

Remote Access Policy • Outlines and defines acceptable methods of remotely connecting to the internal network. • Essential in large organization where networks are geographically dispersed and even extend into the homes. • Should cover all available methods to remotely access internal resources: – dial-in (SLIP, PPP) – ISDN/frame relay – telnet/ssh access from internet – cable modem/VPN/DSL

Information Protection Policy • Provides guidelines to users on the processing, storage and transmission of sensitive information. • Main goal is to ensure information is appropriately protected from modification or disclosure. • May be appropriate to have new employees sign policy as part of their initial orientation. • Should define sensitivity levels of information.

The Perimeter Security Policy • Describes, in general, how perimeter security is maintained. • Describes who is responsible for maintaining it. • Describes how hardware and software changes to perimeter security devices are managed and how changes are requested and approved.

Virus Protection and Prevention Policy • Provides baseline requirements for the use of virus protection software. • Provides guidelines for reporting and containing virus infections. • Provides guidelines for several levels of virus risk. • Should discuss requirements for scanning email attachments. • Should discuss policy for the download and installation of public domain software.

Virus Protection and Prevention Policy • Should discuss frequency of virus data file updates. • Should discuss testing procedures for installation of new software.

Password Policy • Provides guidelines for how user level and system level passwords are managed and changed. • Discusses password construction rules. • Provides guidelines for how passwords are protected from disclosure. • Discusses application development guidelines for when passwords are needed. • Discusses the use of SNMP community strings and pass-phrases.

Other Important Policies • A policy which addresses forwarding of email to offsite addresses. • A policy which addresses wireless networks. • A policy which addresses baseline lab security standards. • A policy which addresses baseline router configuration parameters. • A policy which addresses requirements for installing devices on a dirty network.

Security Procedures • Policies only define "what" is to be protected. • Procedures define "how" to protect resources and are the mechanisms to enforce policy. • Procedures define detailed actions to take for specific incidents. • Procedures provide a quick reference in times of crisis. • Procedures help eliminate the problem of a single point of failure (e. g. , an employee suddenly leaves or is unavailable in a time of crisis).

Configuration Management Procedure • Defines how new hardware/software is tested and installed. • Defines how hardware/software changes are documented. • Defines who must be informed when hardware and software changes occur. • Defines who has authority to make hardware and software configuration changes.
Data Backup and Off-site Storage Procedures • • • Defines which file systems are backed up. Defines how often backups are performed. Defines how often storage media is rotated. Defines how often backups are stored off-site. Defines how storage media is labeled and documented.

Incident Handling Procedure • Defines how to handle anomaly investigation and intruder attacks. • Defines areas of responsibilities for members of the response team. • Defines what information to record and track. • Defines who to notify and when. • Defines who can release information and the procedure for releasing the information. • Defines how a follow-up analysis should be performed and who will participate.

RISK MANAGEMENT

Risk is the likelihood of the occurrence of a vulnerability multiplied by the value of the information asset minus the percentage of risk mitigated by current controls plus the uncertainty of current knowledge of the vulnerability

What is Risk • • • A definable event Probability of occurrence Impact of occurrence A risk occurs when the problem happens Loss expectancy that a threat might exploit a vulnerability.
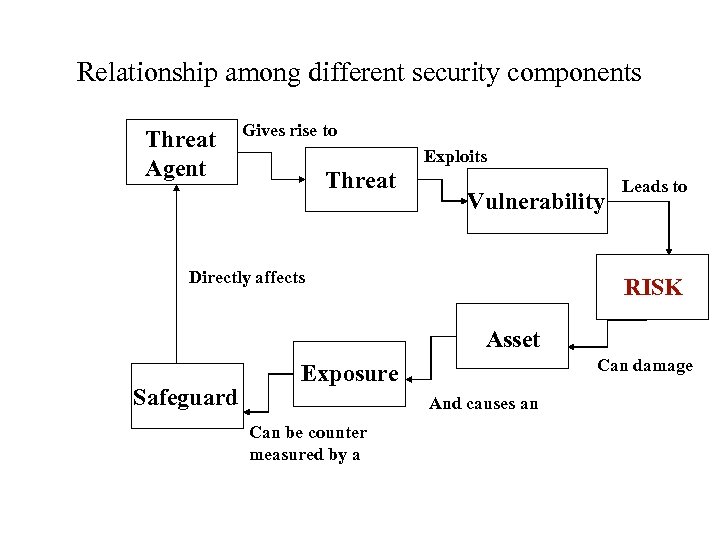
Relationship among different security components Threat Agent Gives rise to Threat Exploits Vulnerability Directly affects Leads to RISK Asset Safeguard Can damage Exposure And causes an Can be counter measured by a
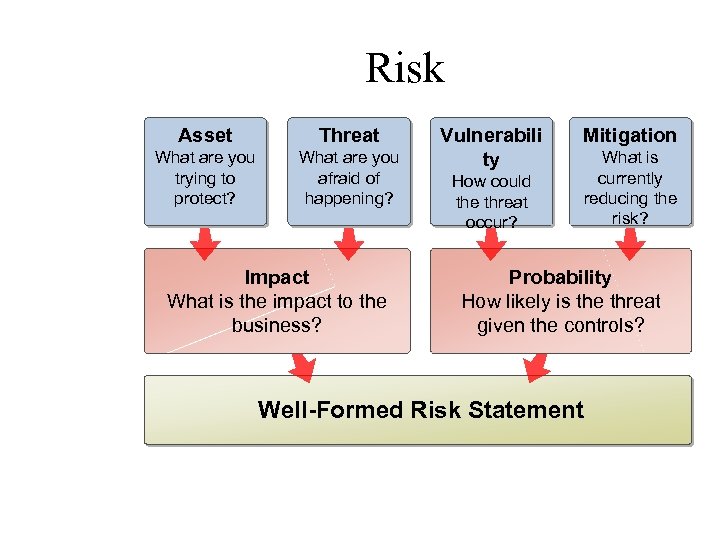
Risk Asset Threat What are you trying to protect? What are you afraid of happening? Impact What is the impact to the business? Vulnerabili ty Mitigation How could the threat occur? What is currently reducing the risk? Probability How likely is the threat given the controls? Well-Formed Risk Statement

Vulnerability Identification • Vulnerability – is a software, hardware, or procedural weakness that may provide an attacker the open door to enter a system. • Specific avenues threat agents can exploit to attack an information asset are called vulnerabilities • Examine how each threat could be perpetrated and list organization’s assets and vulnerabilities • Process works best when people with diverse backgrounds within organization work iteratively in a series of brainstorming sessions • At the end of risk identification process, list of assets and their vulnerabilities is achieved

Risk Mitigation • Understand security risk • Understand technology • Accept Risk – Documentation of risk acceptance is a form of mitigation. • Defer or transfer risk – Insurance • Mitigate risk – Technology can mitigate risk

Risk Management Process

How to Develop a Security Risk Management Process? • Security risk management process: – A process for identifying, prioritizing, and managing risk to an acceptable level within the organization • Developing a formal security risk management process must address the following: – Threat response time – Regulatory compliance – Infrastructure management costs – Risk identification and assessment (prioritization)

Successful Factors for Security Risk Management Process Key factors to implementing a successful security risk management process include: – Executive sponsorship – Well-defined list of risk management stakeholders – Organizational maturity in terms of risk management – An atmosphere of open communications and teamwork – A holistic view of the organization – Security risk management team’s authority
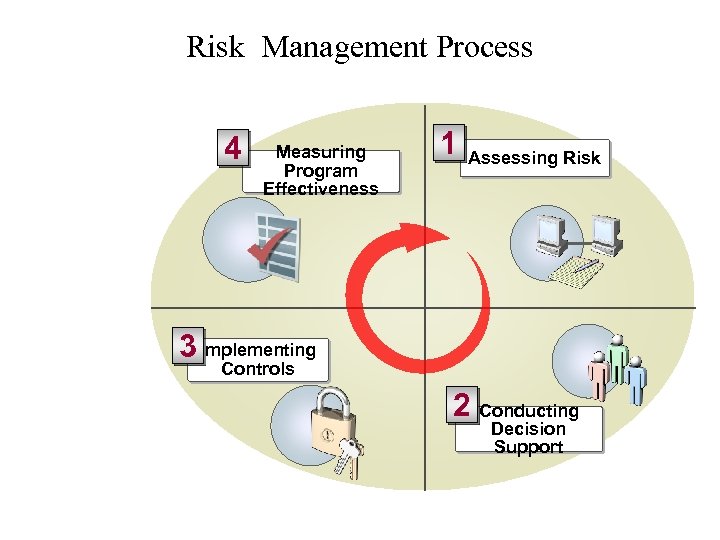
Risk Management Process 4 Measuring Program Effectiveness 1 Assessing Risk 3 Implementing Controls 2 Conducting Decision Support
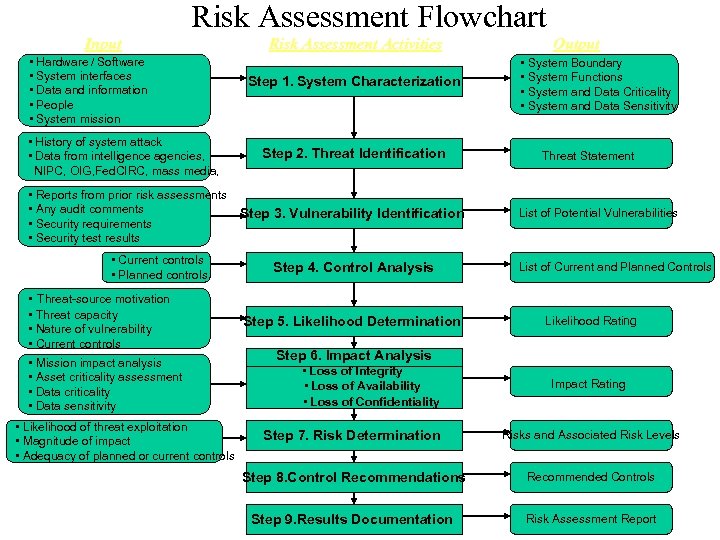
Risk Assessment Flowchart Input • Hardware / Software • System interfaces • Data and information • People • System mission • History of system attack • Data from intelligence agencies, NIPC, OIG, Fed. CIRC, mass media, • Reports from prior risk assessments • Any audit comments • Security requirements • Security test results • Current controls • Planned controls • Threat-source motivation • Threat capacity • Nature of vulnerability • Current controls • Mission impact analysis • Asset criticality assessment • Data criticality • Data sensitivity • Likelihood of threat exploitation • Magnitude of impact • Adequacy of planned or current controls Risk Assessment Activities Step 1. System Characterization Step 2. Threat Identification Step 3. Vulnerability Identification Step 4. Control Analysis Step 5. Likelihood Determination Output • System Boundary • System Functions • System and Data Criticality • System and Data Sensitivity Threat Statement List of Potential Vulnerabilities List of Current and Planned Controls Likelihood Rating Step 6. Impact Analysis • Loss of Integrity • Loss of Availability • Loss of Confidentiality Impact Rating Step 7. Risk Determination Risks and Associated Risk Levels Step 8. Control Recommendations Recommended Controls Step 9. Results Documentation Risk Assessment Report
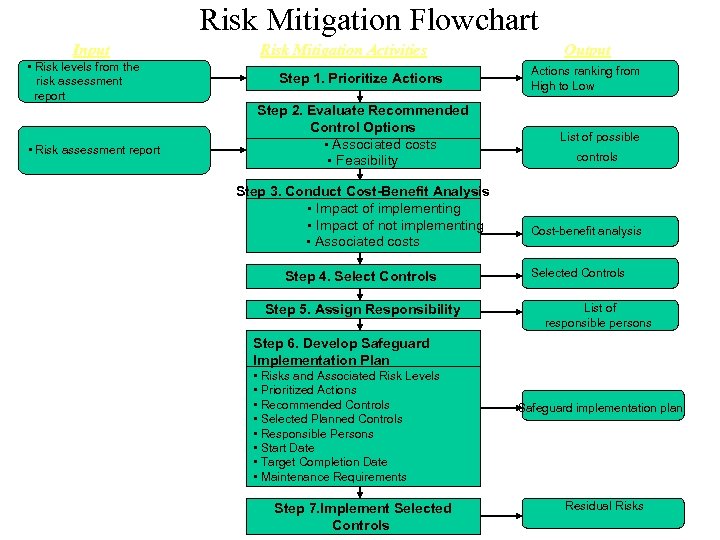
Risk Mitigation Flowchart Input • Risk levels from the risk assessment report • Risk assessment report Risk Mitigation Activities Step 1. Prioritize Actions Step 2. Evaluate Recommended Control Options • Associated costs • Feasibility Step 3. Conduct Cost-Benefit Analysis • Impact of implementing • Impact of not implementing • Associated costs Step 4. Select Controls Step 5. Assign Responsibility Output Actions ranking from High to Low List of possible controls Cost-benefit analysis Selected Controls List of responsible persons Step 6. Develop Safeguard Implementation Plan • Risks and Associated Risk Levels • Prioritized Actions • Recommended Controls • Selected Planned Controls • Responsible Persons • Start Date • Target Completion Date • Maintenance Requirements Step 7. Implement Selected Controls Safeguard implementation plan Residual Risks

Risk Analysis Method
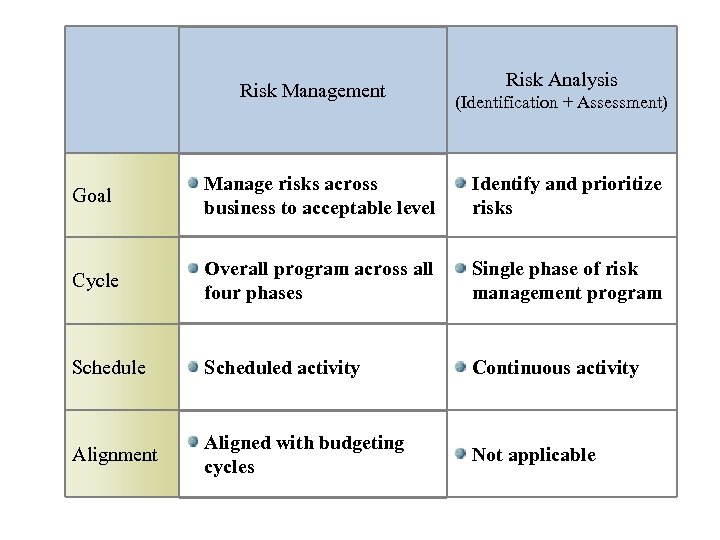
Risk Management Risk Analysis (Identification + Assessment) Goal Manage risks across business to acceptable level Identify and prioritize risks Cycle Overall program across all four phases Single phase of risk management program Scheduled activity Continuous activity Alignment Aligned with budgeting cycles Not applicable

Risk Analysis Method Two types of risk analysis: – Quantitative – attempts to assign real numbers to the costs of safeguards and the amount of damage that can take place – Qualitative – An analysis that judges an organization’s risk to threats, which is based on judgment, intuition, and the experience versus assigning real numbers to this possible risks and their potential loss; e. g. , Analytical Hierarchy Process (AHP)

Steps of Quantitative Risk Analysis • Assign value to information assets (tangible and intangible) • Estimate potential loss per risk • Perform a threat analysis • Derive the overall loss potential per risk • Choose safeguards / countermeasure for each risk • Determine risk response (e. g. mitigation, avoidance, acceptance)

Quantitative Risk Analysis • Exposure Factor (EF) = Percentage of asset loss caused by identified threat; ranges from 0 to 100% • Single Loss Expectancy (SLE) = Asset Value x Exposure Factor; 1, 000 @ 10% likelihood = $100, 000 • Annualized Rate of Occurrence (ARO) = Estimated frequency a threat will occur with in a year and is characterized on an annual basis. A threat occurring once in 10 years has an ARO of 0. 1; a threat occurring 50 times in a year has an ARO of 50 • Annualized Loss Expectancy (ALE) = Single Loss Expectancy x Annualized Rate of Occurrence • Safeguard cost/benefit analysis = (ALE before implementing safeguard) – (ALE after implementing safeguard) – (annual cost of safeguard) == value of safeguard to the company

Quantitative Risk Analysis - Summary • Pros – Uses probability concepts – the likelihood that an risk will occur or will not occur – The value of information is expressed in monetary terms with supporting rationale – Risk assessment results are derived and expressed in management speak • Cons – Purely quantitative risk analysis not possible because quantitative measures must be applied to qualitative elements – Can be less ambiguous but using numbers can give appearance of specificity that does not really exist – Huge amount of data must be gathered and managed

Qualitative Risk Analysis • Does not assign numbers and monetary value to components and losses. • Walks through different scenarios of risk possibilities and rank the seriousness of the threats for the sensitivity of the assets.

Identifying Qualitative Risks • • • Expert Interviews Brainstorming Nominal Group Technique Affinity Diagram Analogy Techniques
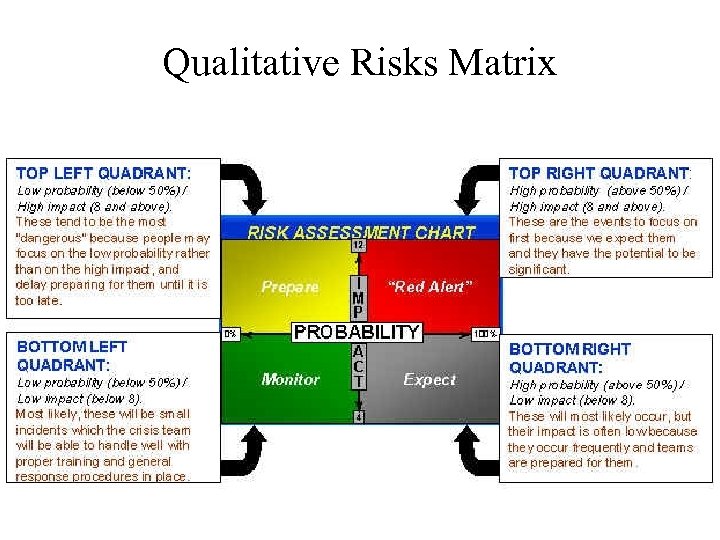
Qualitative Risks Matrix
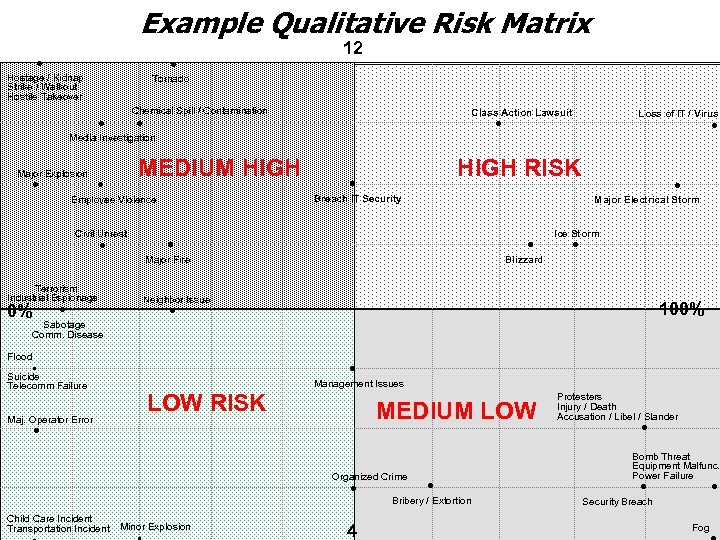
Example Qualitative Risk Matrix Hostage / Kidnap Strike / Walkout Hostile Takeover 12 Tornado Chemical Spill / Contamination Class Action Lawsuit Media Investigation Major Explosion MEDIUM HIGH Terrorism Industrial Espionage 0% Sabotage Comm. Disease Blizzard Ice Storm Neighbor Issue 100% Management Issues LOW RISK MEDIUM LOW Organized Crime Child Care Incident Transportation Incident Major Electrical Storm Major Fire Maj. Operator Error HIGH RISK Flood Suicide Telecomm Failure. Breach IT Security Employee Violence Civil Unrest Loss of IT / Virus Minor Explosion 4 Bribery / Extortion Protesters Injury / Death Accusation / Libel / Slander Bomb Threat Equipment Malfunc. Power Failure Security Breach Fog
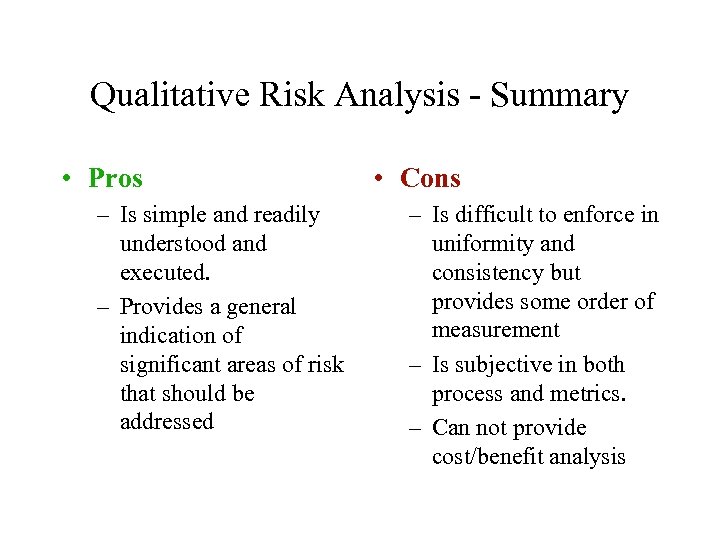
Qualitative Risk Analysis - Summary • Pros – Is simple and readily understood and executed. – Provides a general indication of significant areas of risk that should be addressed • Cons – Is difficult to enforce in uniformity and consistency but provides some order of measurement – Is subjective in both process and metrics. – Can not provide cost/benefit analysis
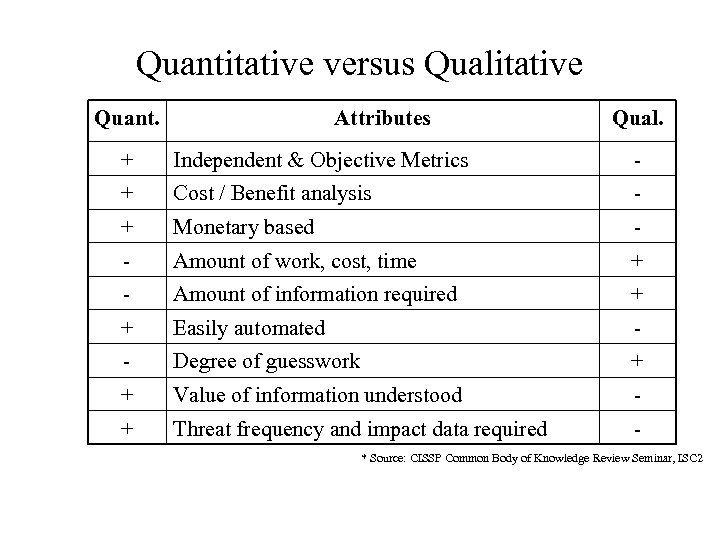
Quantitative versus Qualitative Quant. Attributes Qual. + Independent & Objective Metrics - + Cost / Benefit analysis - + Monetary based - - Amount of work, cost, time + - Amount of information required + + Easily automated - - Degree of guesswork + + Value of information understood - + Threat frequency and impact data required - * Source: CISSP Common Body of Knowledge Review Seminar, ISC 2

Corporate Risk Analysis Strategy
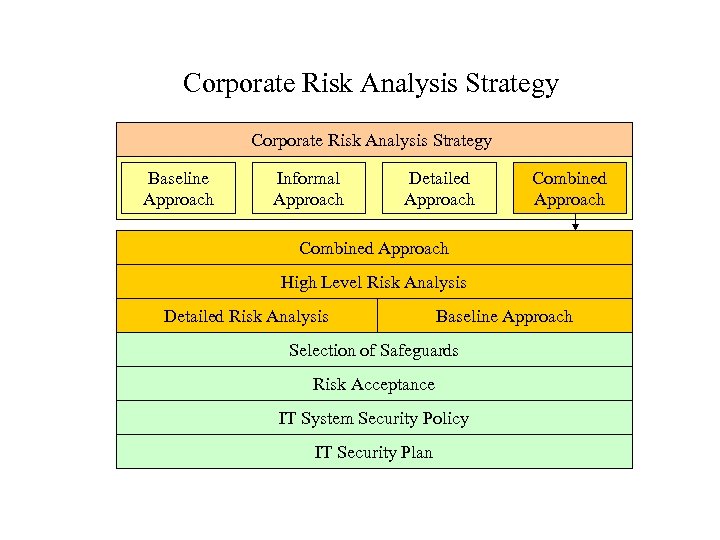
Corporate Risk Analysis Strategy Baseline Approach Informal Approach Detailed Approach Combined Approach High Level Risk Analysis Detailed Risk Analysis Baseline Approach Selection of Safeguards Risk Acceptance IT System Security Policy IT Security Plan

Baseline Approach • Establish a minimum set of safeguards to protect all or some IT systems of an organization • Achieved through the use of safeguard catalogues which suggest a set of safeguards to protect an IT system against the most common threats • The level of baseline security can be adjusted to the needs of the organization Advantages 1. Minimum amount of resources 2. Cost-effective Disadvantages 1. Excessive level of security 2. A lack of security 3. Security relevant changes
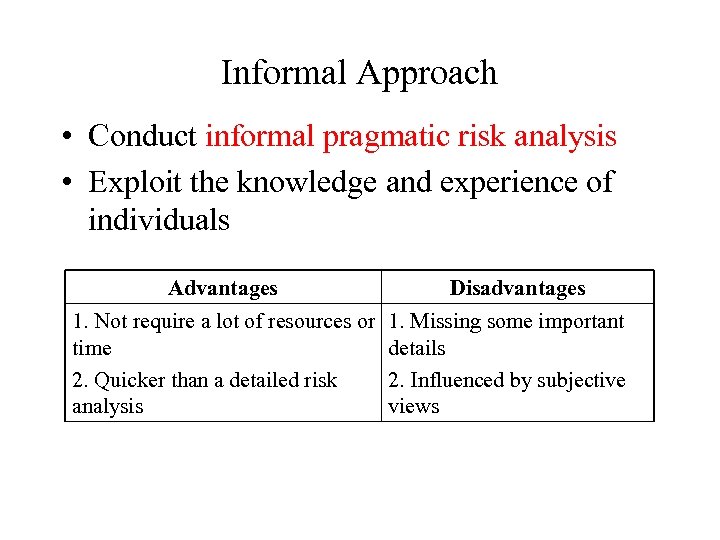
Informal Approach • Conduct informal pragmatic risk analysis • Exploit the knowledge and experience of individuals Advantages 1. Not require a lot of resources or time 2. Quicker than a detailed risk analysis Disadvantages 1. Missing some important details 2. Influenced by subjective views
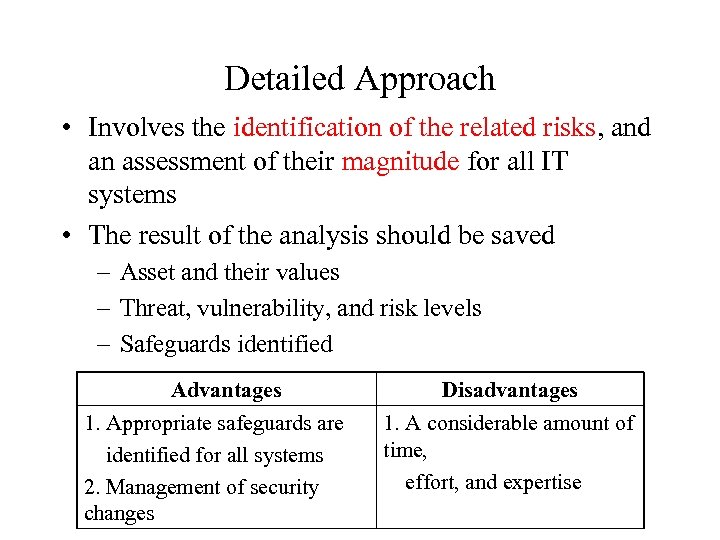
Detailed Approach • Involves the identification of the related risks, and an assessment of their magnitude for all IT systems • The result of the analysis should be saved – Asset and their values – Threat, vulnerability, and risk levels – Safeguards identified Advantages 1. Appropriate safeguards are identified for all systems 2. Management of security changes Disadvantages 1. A considerable amount of time, effort, and expertise
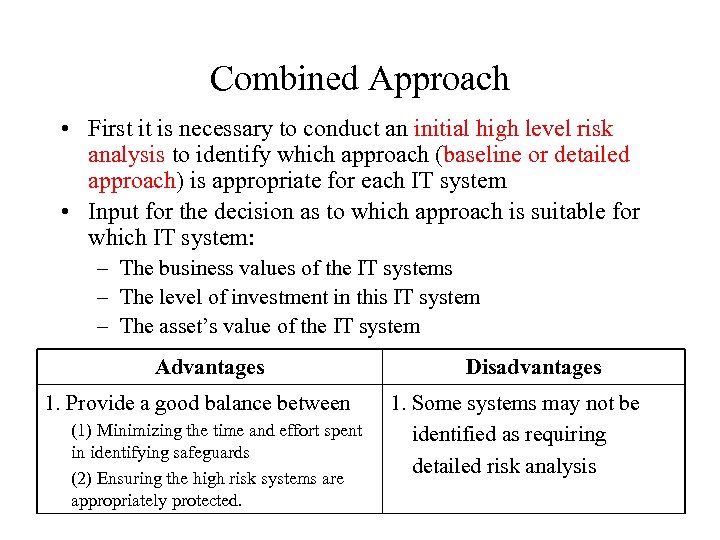
Combined Approach • First it is necessary to conduct an initial high level risk analysis to identify which approach (baseline or detailed approach) is appropriate for each IT system • Input for the decision as to which approach is suitable for which IT system: – The business values of the IT systems – The level of investment in this IT system – The asset’s value of the IT system Advantages 1. Provide a good balance between (1) Minimizing the time and effort spent in identifying safeguards (2) Ensuring the high risk systems are appropriately protected. Disadvantages 1. Some systems may not be identified as requiring detailed risk analysis
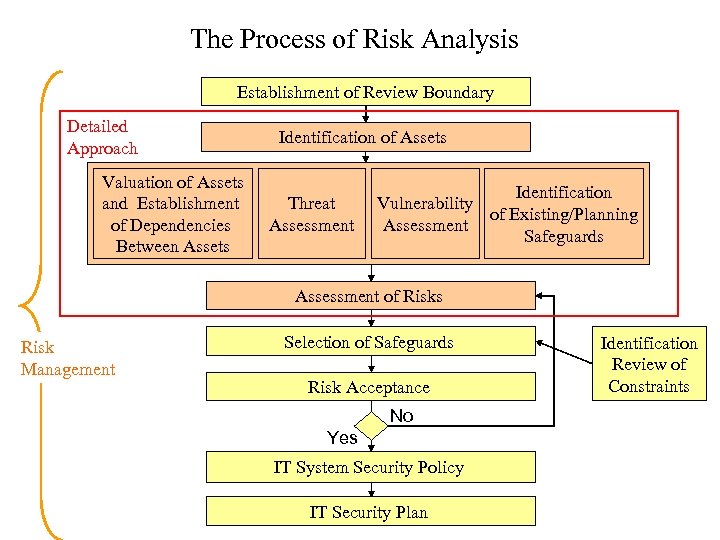
The Process of Risk Analysis Establishment of Review Boundary Detailed Approach Valuation of Assets and Establishment of Dependencies Between Assets Identification of Assets Threat Assessment Identification Vulnerability of Existing/Planning Assessment Safeguards Assessment of Risks Risk Management Selection of Safeguards Risk Acceptance No Yes IT System Security Policy IT Security Plan Identification Review of Constraints

INFORMATION SECURITY STANDARD

Introduction • ISO 17799/BS 7799 -1 is an international standard that sets out the requirements of good practice for Information Security Management. • ISO 27001/BS 7799 -2 defines the specification for an Information Security Management System (ISMS). - The scope of an ISMS includes: processes people IT Systems Policies
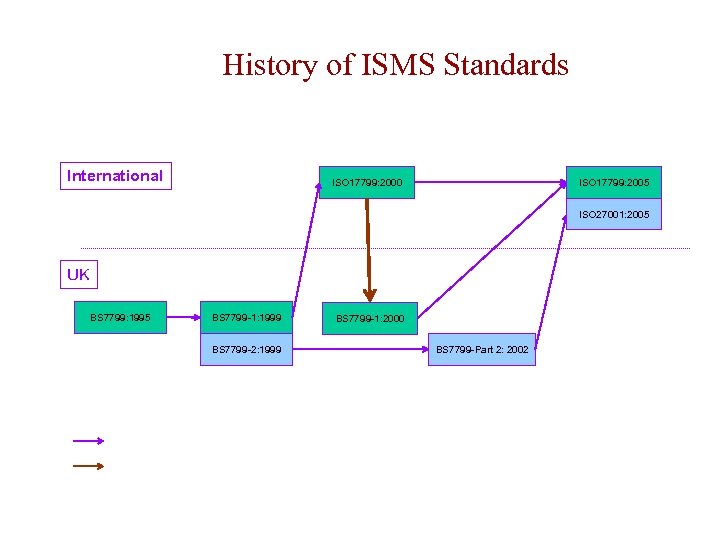
History of ISMS Standards International ISO 17799: 2000 ISO 17799: 2005 ISO 27001: 2005 UK BS 7799: 1995 BS 7799 -1: 1999 BS 7799 -2: 1999 = copy/translation = revision BS 7799 -1: 2000 BS 7799 -Part 2: 2002

What is BS 7799 -1 / ISO 17799? • The goal of BS 7799 -1 / ISO 17799 is to “provide a common base for developing organizational security standards and effective security management practice and to provide confidence in inter-organizational dealings. ”

Who is BS 7799 -1/ISO 17799 for? • BS 7799 -1 / ISO 17799 meets the needs of organizations and companies of all types, both private and public. • For any organization that stores confidential information on internal or external systems, depends on such systems to run its operations, or indeed wishes to demonstrate its information security by conforming to a known standard, BS 7799 -1 / ISO 17799 would be of very great interest.

The Eleven Key Context of ISO 17799 • Security policy - This provides management direction and support for information security • Organization of information security - To help you manage information security within the organization • Asset management - To help you identify your assets and appropriately protect them • Human resources security - To reduce the risks of human error, theft, fraud or misuse of facilities • Physical and environmental security - To prevent unauthorized access, damage and interference to business premises and information • Communications and operations management - To ensure the correct and secure operation of information processing facilities

The Eleven Key Context of ISO 17799 (cont’d) • Access control - To control access to information • Information systems acquisition, development and maintenance - To ensure that security is built into information systems • Information security incident management-To make sure that all information security events and weaknesses can be reported and solve effectively. • Business continuity management - To counteract interruptions to business activities and to protect critical business processes from the effects of major failures or disasters • Compliance - To avoid breaches of any criminal and civil law, statutory, regulatory or contractual obligations, and any security requirement
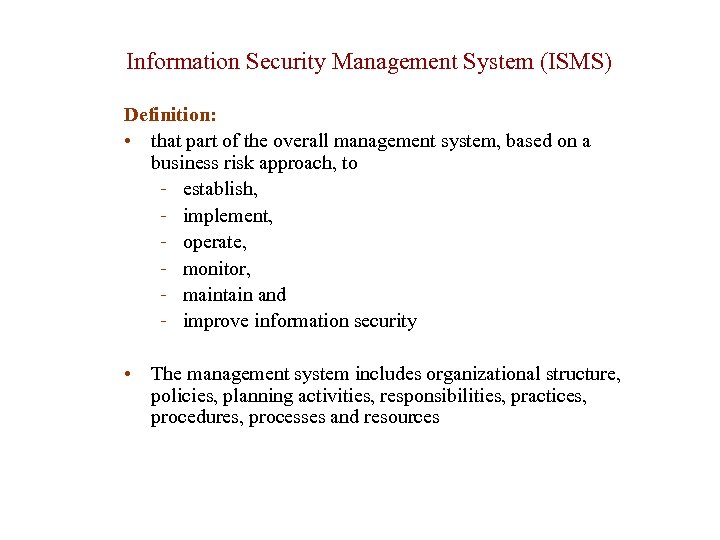
Information Security Management System (ISMS) Definition: • that part of the overall management system, based on a business risk approach, to - establish, - implement, - operate, - monitor, - maintain and - improve information security • The management system includes organizational structure, policies, planning activities, responsibilities, practices, procedures, processes and resources
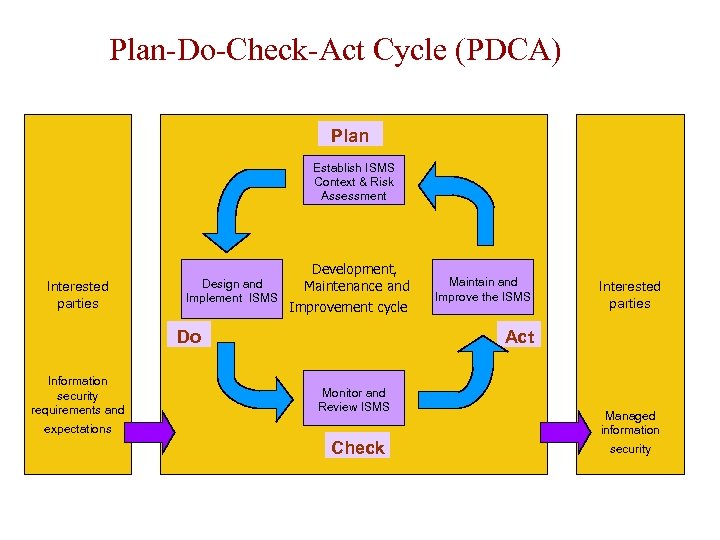
Plan-Do-Check-Act Cycle (PDCA) Plan Establish ISMS Context & Risk Assessment Interested parties Design and Implement ISMS Development, Maintenance and Improvement cycle Do Information security requirements and Maintain and Improve the ISMS Interested parties Act Monitor and Review ISMS expectations Check Managed information security
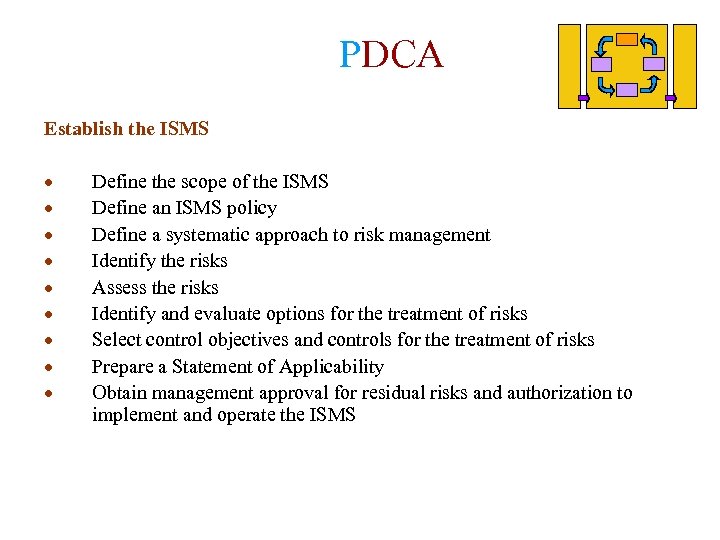
PDCA Establish the ISMS · · · · · Define the scope of the ISMS Define an ISMS policy Define a systematic approach to risk management Identify the risks Assess the risks Identify and evaluate options for the treatment of risks Select control objectives and controls for the treatment of risks Prepare a Statement of Applicability Obtain management approval for residual risks and authorization to implement and operate the ISMS

PDCA Implement and operate the ISMS • • • Formulate a risk treatment plan and its documentation, including planned process and detailed procedures Implement the risk treatment planned controls Implement training and awareness programs Manage operations and resources Implement procedures and controls to detect and response to security incidents

PDCA Monitor and review the ISMS • • • Execute monitoring procedures Undertake regular reviews Review level of residual risk Conduct internal audits Undertake a management review Record actions and events

PDCA Maintain and improve the ISMS • • Implement the identified improvements Take appropriate corrective and preventive actions Communicate results Ensure effectiveness
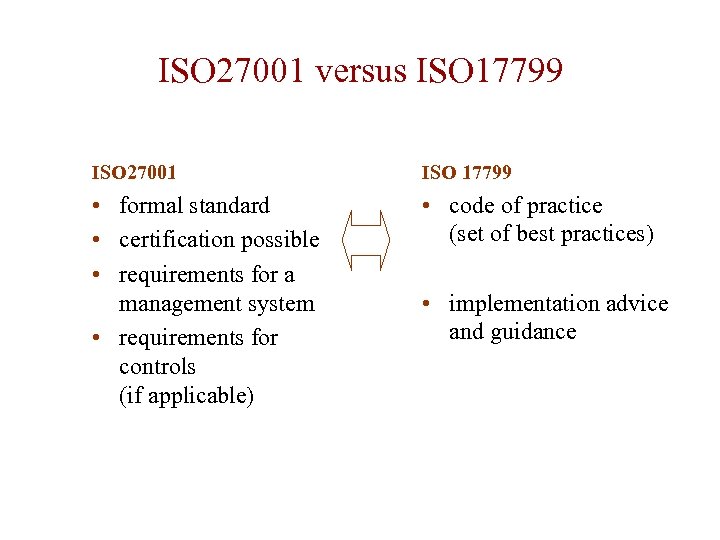
ISO 27001 versus ISO 17799 ISO 27001 ISO 17799 • formal standard • certification possible • requirements for a management system • requirements for controls (if applicable) • code of practice (set of best practices) • implementation advice and guidance

What are ISO 17799 and ISO 27001 not • limited to information technology • a security checklist • an insurance policy against security breaches • an audit method • a risk analysis method

POSSIBLE RESEARCH DIRECTION

• Assessment of factors influencing the effectiveness of information security management • Risk assessment using fuzzy consensus measures • Online privacy: Issues and Concerns • Organizational changes pertaining to information security • Culture impact on the success of information security management • Information security disaster recovery planning: crisis management • Conforming information security standards
908cc240cad4fc00b9cf84f5b94b98bb.ppt