41bb83371d997ca09a8e87351fcbcb9c.ppt
- Количество слайдов: 47
 Information Assurance for the Enterprise: A Roadmap to Information Security, by Schou and Shoemaker Chapter 6 Ensuring Controlled Access Mc. Graw-Hill/Irwin Copyright © 2007 by The Mc. Graw-Hill Companies, Inc. All rights reserved.
Information Assurance for the Enterprise: A Roadmap to Information Security, by Schou and Shoemaker Chapter 6 Ensuring Controlled Access Mc. Graw-Hill/Irwin Copyright © 2007 by The Mc. Graw-Hill Companies, Inc. All rights reserved.
 Objectives The fundamental principles of access control ¢ How to structure and conduct the authorization process ¢ Common access control models ¢ 6 -2
Objectives The fundamental principles of access control ¢ How to structure and conduct the authorization process ¢ Common access control models ¢ 6 -2
 Access Control ¢ Access control – describes the regulation of interaction between subjects and objects within a given environment l ¢ Degree of regulation will determine how comprehensive and robust the overall protection scheme will be With information assurance: Subjects are people or processes l Processes can be either managerial or technical l Objects can be anything appropriately accessed by a valid subject l 6 -3
Access Control ¢ Access control – describes the regulation of interaction between subjects and objects within a given environment l ¢ Degree of regulation will determine how comprehensive and robust the overall protection scheme will be With information assurance: Subjects are people or processes l Processes can be either managerial or technical l Objects can be anything appropriately accessed by a valid subject l 6 -3
 Principles of Access Control Implementing and managing the access control process can be a very complex activity ¢ Access control process centers around three principles: ¢ Identity – asserts and verifies the user’s identity l Authority – authorizes user access privileges l Accountability – tracks user actions, analyzes and reports l 6 -4
Principles of Access Control Implementing and managing the access control process can be a very complex activity ¢ Access control process centers around three principles: ¢ Identity – asserts and verifies the user’s identity l Authority – authorizes user access privileges l Accountability – tracks user actions, analyzes and reports l 6 -4
 Establishing Identity ¢ The principle of identity is composed of two functions: Identification function establishes the identity of every person or process that seeks access l Authentication function confirms that it is valid l 6 -5
Establishing Identity ¢ The principle of identity is composed of two functions: Identification function establishes the identity of every person or process that seeks access l Authentication function confirms that it is valid l 6 -5
 Passwords: Something You Know ¢ The simplest and most economical means of identifying an individual l Password management system will consistently: • Allow legitimate users to directly register for access • Allow forgotten passwords to be authenticated and reset by user • Allow IT support staff to authenticate callers for password management • Synchronize users across a range of platforms • Provide for immediate cancellation of passwords 6 -6
Passwords: Something You Know ¢ The simplest and most economical means of identifying an individual l Password management system will consistently: • Allow legitimate users to directly register for access • Allow forgotten passwords to be authenticated and reset by user • Allow IT support staff to authenticate callers for password management • Synchronize users across a range of platforms • Provide for immediate cancellation of passwords 6 -6
 Passwords: Something You Know ¢ Problem with passwords l Memory • Limitation of human memory to remember multiple passwords • Writing them down is a serious violation of information assurance or security protocol l Usage vulnerabilities • Short passwords – easily compromised by brute force, guessed or obtained through surreptitious means 6 -7
Passwords: Something You Know ¢ Problem with passwords l Memory • Limitation of human memory to remember multiple passwords • Writing them down is a serious violation of information assurance or security protocol l Usage vulnerabilities • Short passwords – easily compromised by brute force, guessed or obtained through surreptitious means 6 -7
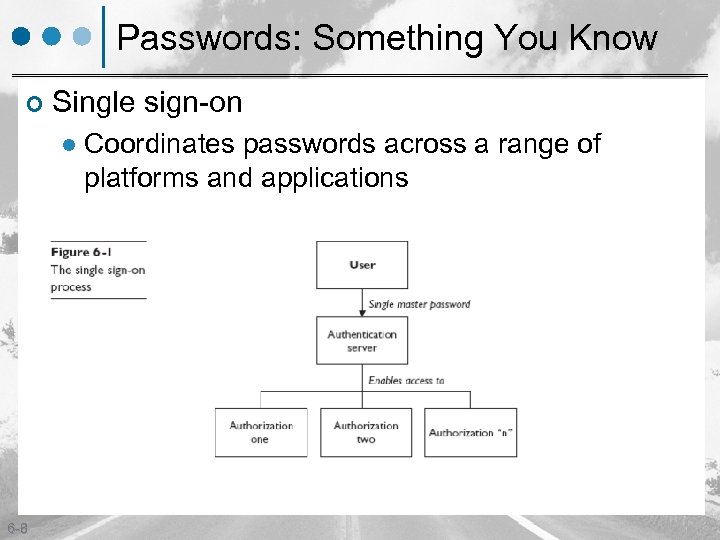 Passwords: Something You Know ¢ Single sign-on l 6 -8 Coordinates passwords across a range of platforms and applications
Passwords: Something You Know ¢ Single sign-on l 6 -8 Coordinates passwords across a range of platforms and applications
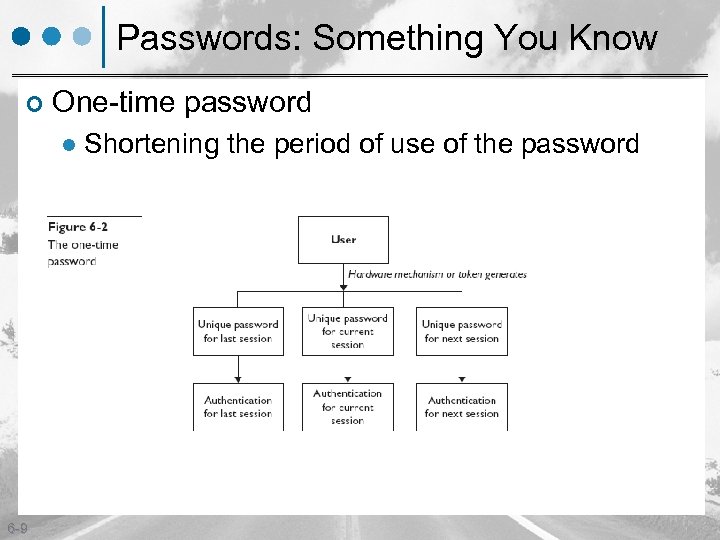 Passwords: Something You Know ¢ One-time password l 6 -9 Shortening the period of use of the password
Passwords: Something You Know ¢ One-time password l 6 -9 Shortening the period of use of the password
 Token-Based Security: Something You Have ¢ Tokens – identification and authorization devices presented at the time of access l ¢ Function similar to a key and lock Most frequently used authentication device is the smart card, or swipe card Embedded semiconductor chip accepts, stores, and sends information l Keeps personal information with a high degree of security and portability l Provides secure enterprise-wide access control l 6 -10
Token-Based Security: Something You Have ¢ Tokens – identification and authorization devices presented at the time of access l ¢ Function similar to a key and lock Most frequently used authentication device is the smart card, or swipe card Embedded semiconductor chip accepts, stores, and sends information l Keeps personal information with a high degree of security and portability l Provides secure enterprise-wide access control l 6 -10
 Token-Based Security: Something You Have Provides tamper-resistant storage and transport for critical data l Used in encryption systems, to store digital keys, and to create one-time passwords l ¢ Vulnerabilities associated with using smart cards: l Theft and loss of tokens • Unauthorized finder will be able to gain access under the legitimate user’s authorizations 6 -11
Token-Based Security: Something You Have Provides tamper-resistant storage and transport for critical data l Used in encryption systems, to store digital keys, and to create one-time passwords l ¢ Vulnerabilities associated with using smart cards: l Theft and loss of tokens • Unauthorized finder will be able to gain access under the legitimate user’s authorizations 6 -11
 Biometrics: Something You Are Biometrics – authentication using physical characteristics ¢ Subject asserts identity by presenting a unique personal characteristic such as a fingerprint ¢ Highly secure because they confirm identity by means of physical characteristics that cannot be duplicated l Very effective, since physical characteristics might change slowly over time but they are impossible to lose l 6 -12
Biometrics: Something You Are Biometrics – authentication using physical characteristics ¢ Subject asserts identity by presenting a unique personal characteristic such as a fingerprint ¢ Highly secure because they confirm identity by means of physical characteristics that cannot be duplicated l Very effective, since physical characteristics might change slowly over time but they are impossible to lose l 6 -12
 Biometrics: Something You Are ¢ Problem with biometric technology: Still in its infancy l Can fail due to its dependency on advanced processing capabilities l When it comes to the identity process, possible failures include: l • False positives allow unauthorized individuals to access system resources • False negatives deny authorized people access 6 -13
Biometrics: Something You Are ¢ Problem with biometric technology: Still in its infancy l Can fail due to its dependency on advanced processing capabilities l When it comes to the identity process, possible failures include: l • False positives allow unauthorized individuals to access system resources • False negatives deny authorized people access 6 -13
 Combining Approaches: Multifactor Authentication ¢ Multifactor authentication – combination of two or three different approaches to create a single access control function l It increases the level of security • Example: automatic teller machine (ATM) 6 -14
Combining Approaches: Multifactor Authentication ¢ Multifactor authentication – combination of two or three different approaches to create a single access control function l It increases the level of security • Example: automatic teller machine (ATM) 6 -14
 Approaches for Establishing Identity in Cyberspace ¢ Digital signatures: asserting identity using cryptography l Signatures generated from the message itself by mathematical means • MD-5 algorithm • Message digests ¢ Digital certificates: utilizing trust infrastructures l l Third party confirmation that verifies that the message did indeed come from the entity it claims to have come from Certification supported by Public Key Infrastructures (PKIs) • PKIs verify, enroll, and certify users • PKIs serve as the trusted third party 6 -15
Approaches for Establishing Identity in Cyberspace ¢ Digital signatures: asserting identity using cryptography l Signatures generated from the message itself by mathematical means • MD-5 algorithm • Message digests ¢ Digital certificates: utilizing trust infrastructures l l Third party confirmation that verifies that the message did indeed come from the entity it claims to have come from Certification supported by Public Key Infrastructures (PKIs) • PKIs verify, enroll, and certify users • PKIs serve as the trusted third party 6 -15
 Approaches for Establishing Identity in Cyberspace ¢ Digital certificate is a public document that contains: Information that identifies a user l User’s encryption key l Validity period for the certificate and other information l 6 -16
Approaches for Establishing Identity in Cyberspace ¢ Digital certificate is a public document that contains: Information that identifies a user l User’s encryption key l Validity period for the certificate and other information l 6 -16
 Mutual Authentication: Ensuring Identity During Transmission ¢ A process in which each side of an electronic communication verifies the authenticity of the other during message transmission Ensures the integrity of the transmission process as well as the message sent l Especially important when remote clients are attempting to assert their identity to servers l 6 -17
Mutual Authentication: Ensuring Identity During Transmission ¢ A process in which each side of an electronic communication verifies the authenticity of the other during message transmission Ensures the integrity of the transmission process as well as the message sent l Especially important when remote clients are attempting to assert their identity to servers l 6 -17
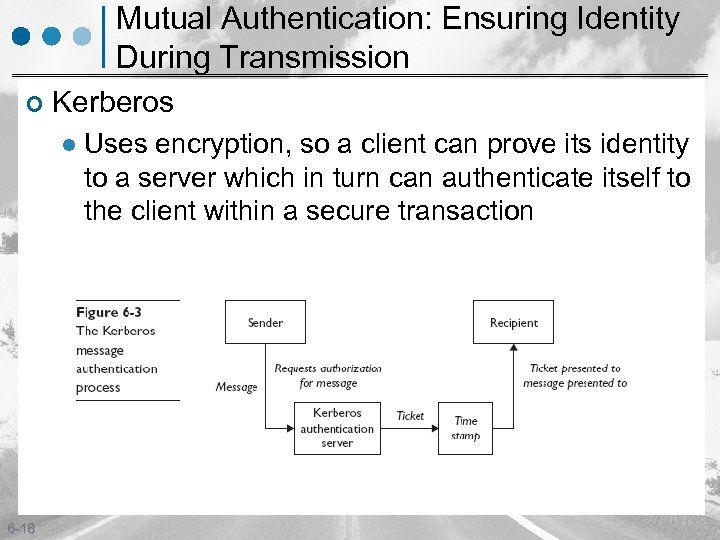 Mutual Authentication: Ensuring Identity During Transmission ¢ Kerberos l 6 -18 Uses encryption, so a client can prove its identity to a server which in turn can authenticate itself to the client within a secure transaction
Mutual Authentication: Ensuring Identity During Transmission ¢ Kerberos l 6 -18 Uses encryption, so a client can prove its identity to a server which in turn can authenticate itself to the client within a secure transaction
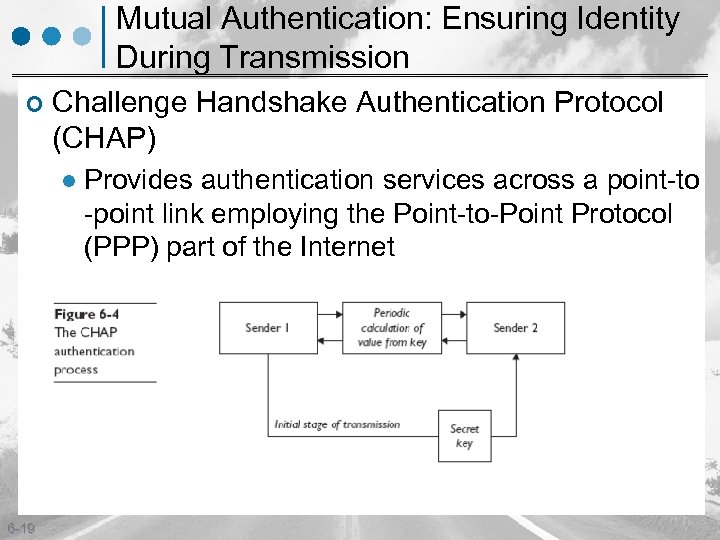 Mutual Authentication: Ensuring Identity During Transmission ¢ Challenge Handshake Authentication Protocol (CHAP) l 6 -19 Provides authentication services across a point-to -point link employing the Point-to-Point Protocol (PPP) part of the Internet
Mutual Authentication: Ensuring Identity During Transmission ¢ Challenge Handshake Authentication Protocol (CHAP) l 6 -19 Provides authentication services across a point-to -point link employing the Point-to-Point Protocol (PPP) part of the Internet
 Authorization: Controlling Access ¢ Authorization asserts specific rights to use the system, which have been granted to a subject Rights are referred to as permissions or privileges – based on the concept of “trust” l Trusted subjects are allowed access to specified objects l Security domain – A systematic point of reference on which determination, assignment, and monitoring of access is based l • Incorporates all related objects, with common protection needs, into a single manageable entity 6 -20
Authorization: Controlling Access ¢ Authorization asserts specific rights to use the system, which have been granted to a subject Rights are referred to as permissions or privileges – based on the concept of “trust” l Trusted subjects are allowed access to specified objects l Security domain – A systematic point of reference on which determination, assignment, and monitoring of access is based l • Incorporates all related objects, with common protection needs, into a single manageable entity 6 -20
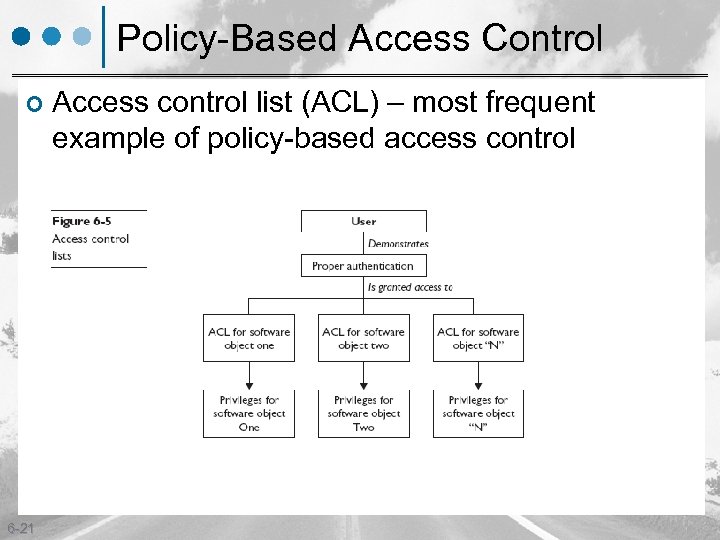 Policy-Based Access Control ¢ 6 -21 Access control list (ACL) – most frequent example of policy-based access control
Policy-Based Access Control ¢ 6 -21 Access control list (ACL) – most frequent example of policy-based access control
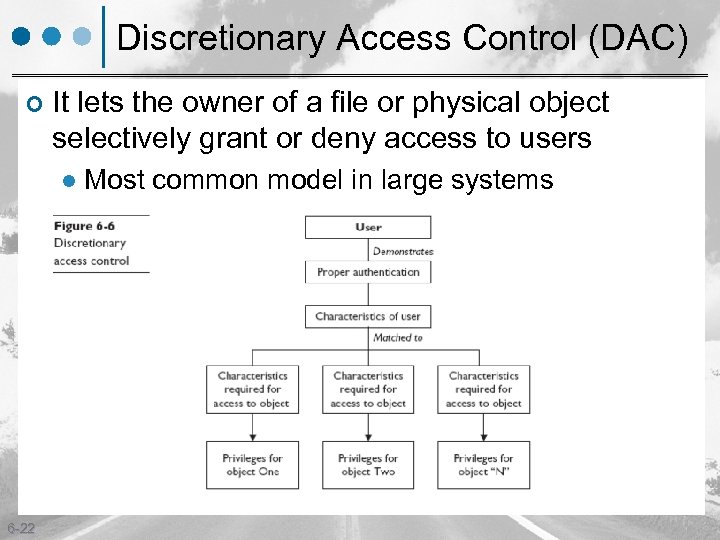 Discretionary Access Control (DAC) ¢ It lets the owner of a file or physical object selectively grant or deny access to users l 6 -22 Most common model in large systems
Discretionary Access Control (DAC) ¢ It lets the owner of a file or physical object selectively grant or deny access to users l 6 -22 Most common model in large systems
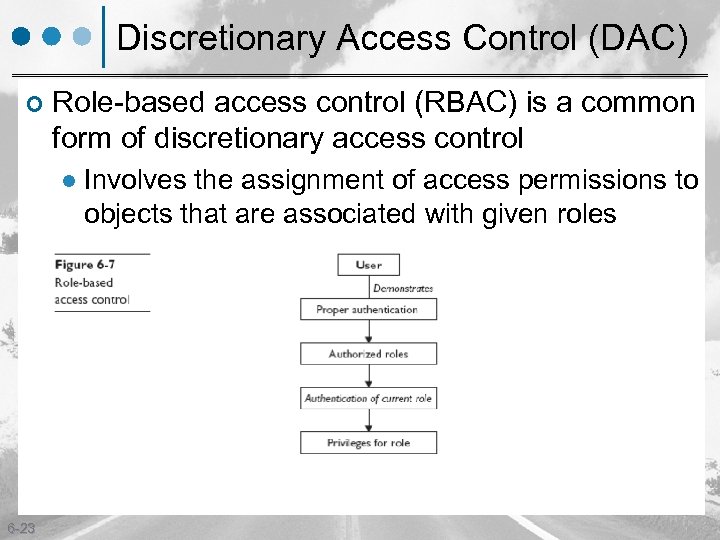 Discretionary Access Control (DAC) ¢ Role-based access control (RBAC) is a common form of discretionary access control l 6 -23 Involves the assignment of access permissions to objects that are associated with given roles
Discretionary Access Control (DAC) ¢ Role-based access control (RBAC) is a common form of discretionary access control l 6 -23 Involves the assignment of access permissions to objects that are associated with given roles
 Discretionary Access Control (DAC) ¢ Content-dependent access control Used to control access to record-intensive applications such as databases l Capability-based system – access is granted if the user possesses a capability (ticket) l • Authorization Table Matrix (ATM) manages the assignment of access privileges Advantage: achieves a greater level of granularity in the process and it is both simple and intuitive l Disadvantage: Machine-intensive; requires a very high level of computer performance l 6 -24
Discretionary Access Control (DAC) ¢ Content-dependent access control Used to control access to record-intensive applications such as databases l Capability-based system – access is granted if the user possesses a capability (ticket) l • Authorization Table Matrix (ATM) manages the assignment of access privileges Advantage: achieves a greater level of granularity in the process and it is both simple and intuitive l Disadvantage: Machine-intensive; requires a very high level of computer performance l 6 -24
 Discretionary Access Control (DAC) ¢ Temporal access control – Event driven and dynamic l Whether access is granted, and the type of access given is determined by: • The time of day • The point of origin • How many times the individual identity attempted to access the system • The number of password attempts Advantage: allows anticipation and protection from undesirable events l Disadvantage: chain of events that lead to a given decision is not always predictable l 6 -25
Discretionary Access Control (DAC) ¢ Temporal access control – Event driven and dynamic l Whether access is granted, and the type of access given is determined by: • The time of day • The point of origin • How many times the individual identity attempted to access the system • The number of password attempts Advantage: allows anticipation and protection from undesirable events l Disadvantage: chain of events that lead to a given decision is not always predictable l 6 -25
 Mandatory Access Control (MAC) ¢ MAC restricts a subject’s access to objects based on a set of security attributes l Used when policy dictates that: • Protection decisions must not be decided by the object owner • The system must enforce the protection decisions over the wishes or intentions of the object owner Prevents arbitrary object sharing l Uses a specific set of policies or security rules to define the sharing of data within the organization l 6 -26
Mandatory Access Control (MAC) ¢ MAC restricts a subject’s access to objects based on a set of security attributes l Used when policy dictates that: • Protection decisions must not be decided by the object owner • The system must enforce the protection decisions over the wishes or intentions of the object owner Prevents arbitrary object sharing l Uses a specific set of policies or security rules to define the sharing of data within the organization l 6 -26
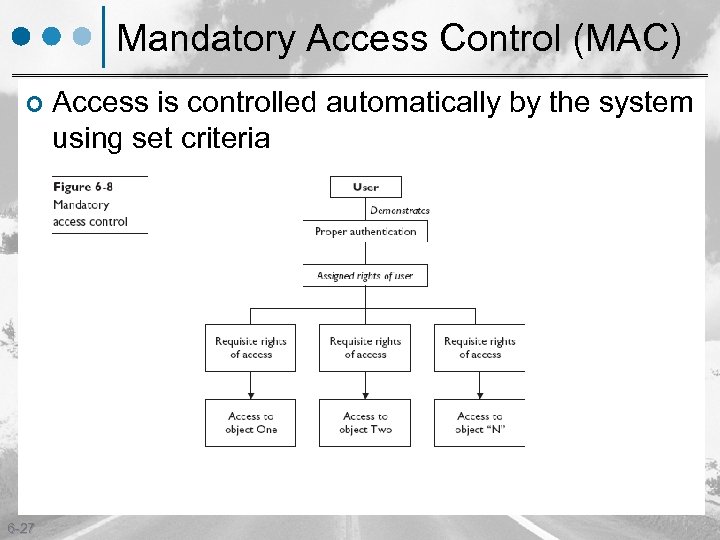 Mandatory Access Control (MAC) ¢ 6 -27 Access is controlled automatically by the system using set criteria
Mandatory Access Control (MAC) ¢ 6 -27 Access is controlled automatically by the system using set criteria
 Real-World Access Control: Automating the Process A reference monitor implemented either operationally or within the operating system ¢ Real-time and dynamic allocation of access privileges ¢ Situation can involve internal and external processes and applications l Accesses must be managed securely in real time for the system to meet its required objectives l System must be able to distinguish instantly and correctly assign the rights for each individual identity l • As well as determine what each can and cannot access 6 -28
Real-World Access Control: Automating the Process A reference monitor implemented either operationally or within the operating system ¢ Real-time and dynamic allocation of access privileges ¢ Situation can involve internal and external processes and applications l Accesses must be managed securely in real time for the system to meet its required objectives l System must be able to distinguish instantly and correctly assign the rights for each individual identity l • As well as determine what each can and cannot access 6 -28
 Real-World Access Control: Automating the Process ¢ Automated identity management system requires five basic conditions: Identity architecture – establishing the identity infrastructure l Privilege setting – establishing the rights of each identity l Identity reference – automating the process l • Reference monitor involves three factors: completeness, and isolation, verifiability Enforcement of privileges – guarding the door l Continuous maintenance – keeping the system current l 6 -29
Real-World Access Control: Automating the Process ¢ Automated identity management system requires five basic conditions: Identity architecture – establishing the identity infrastructure l Privilege setting – establishing the rights of each identity l Identity reference – automating the process l • Reference monitor involves three factors: completeness, and isolation, verifiability Enforcement of privileges – guarding the door l Continuous maintenance – keeping the system current l 6 -29
 Setting Up the System: Account Management ¢ Account management is the day-to-day face of any automated access control system Ensures that identity data are accurate and up to date l Ensures that the monitoring and enforcement system is operating as intended l Links user identities to specific applications, databases, and services l Built around three related processes: l • Creation of new system access • Modification to system access • Termination of system access 6 -30
Setting Up the System: Account Management ¢ Account management is the day-to-day face of any automated access control system Ensures that identity data are accurate and up to date l Ensures that the monitoring and enforcement system is operating as intended l Links user identities to specific applications, databases, and services l Built around three related processes: l • Creation of new system access • Modification to system access • Termination of system access 6 -30
 Intrusion Detection: Backstopping Access Control Access control is backstopped by intrusion detection ¢ Information assurance has four general goals: ¢ Preventive – avoid the occurrence l Detective – identify characterize the occurrence l Corrective – remedy the circumstance l Compensating – provide alternative control l ¢ 6 -31 Intrusion detection is a purely detective activity
Intrusion Detection: Backstopping Access Control Access control is backstopped by intrusion detection ¢ Information assurance has four general goals: ¢ Preventive – avoid the occurrence l Detective – identify characterize the occurrence l Corrective – remedy the circumstance l Compensating – provide alternative control l ¢ 6 -31 Intrusion detection is a purely detective activity
 Intrusion Detection Systems: Keeping the Perimeter Secure ¢ Designed to sit on the perimeter and detect, characterize, and report on any suspicious attempts to access a protected space l Built around boundary sensors - a software utility that is located at the perimeter of the protected space and monitors traffic • Term commonly used to describe this utility is intrusion detection system (IDS) • Intrusion prevention systems (IPSs) 6 -32
Intrusion Detection Systems: Keeping the Perimeter Secure ¢ Designed to sit on the perimeter and detect, characterize, and report on any suspicious attempts to access a protected space l Built around boundary sensors - a software utility that is located at the perimeter of the protected space and monitors traffic • Term commonly used to describe this utility is intrusion detection system (IDS) • Intrusion prevention systems (IPSs) 6 -32
 Types of Intrusion Detection: Automated versus Human Centered Automated: when instantaneous response is needed ¢ Human-centered: if time will allow for a more considered response ¢ Two types of IDS: ¢ Network-Based IDS (NIDS) – detect attacks by capturing and analyzing network packets l Host-Based IDS (HIDS) – Operate on information collected analyzed by an individual computer system l 6 -33
Types of Intrusion Detection: Automated versus Human Centered Automated: when instantaneous response is needed ¢ Human-centered: if time will allow for a more considered response ¢ Two types of IDS: ¢ Network-Based IDS (NIDS) – detect attacks by capturing and analyzing network packets l Host-Based IDS (HIDS) – Operate on information collected analyzed by an individual computer system l 6 -33
 Common Network-Based IDS (NIDS) ¢ Pattern-matching IDS l ¢ State-matching IDS l ¢ Scans incoming network packets for specific byte sequence signatures stored in a database of known attacks Scans for attack behaviors in the traffic stream itself rather than the presence of an individual packet signature Analysis engine methods l Use anomalous behavior as the basis for their response • Example: Statistical anomaly-based IDS 6 -34
Common Network-Based IDS (NIDS) ¢ Pattern-matching IDS l ¢ State-matching IDS l ¢ Scans incoming network packets for specific byte sequence signatures stored in a database of known attacks Scans for attack behaviors in the traffic stream itself rather than the presence of an individual packet signature Analysis engine methods l Use anomalous behavior as the basis for their response • Example: Statistical anomaly-based IDS 6 -34
 Common Network-Based IDS (NIDS) ¢ Protocol anomaly-based methods l ¢ Traffic anomaly-based methods l 6 -35 Capable of using feedback from prior attempts to refine their approach Watch for unusual traffic activities, suddenly appearing on the network
Common Network-Based IDS (NIDS) ¢ Protocol anomaly-based methods l ¢ Traffic anomaly-based methods l 6 -35 Capable of using feedback from prior attempts to refine their approach Watch for unusual traffic activities, suddenly appearing on the network
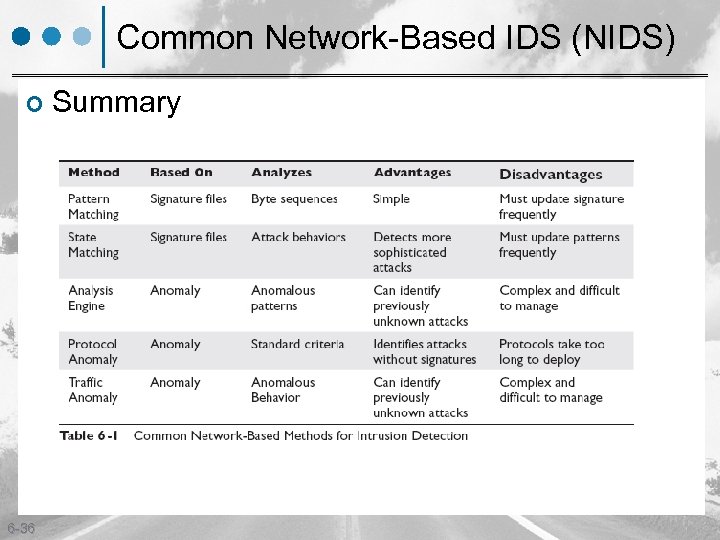 Common Network-Based IDS (NIDS) ¢ 6 -36 Summary
Common Network-Based IDS (NIDS) ¢ 6 -36 Summary
 Host-Based IDS (HIDS) ¢ Work through the audit function and monitoring audit trails A record of system activities usually generated by the system l Types of events captured in an audit trail include: l • • • l 6 -37 Network connection event data System-level event data Application-level event data User-level event data Keystroke activity Primary issue is the volume of data that must be examined for this understanding to be adequate
Host-Based IDS (HIDS) ¢ Work through the audit function and monitoring audit trails A record of system activities usually generated by the system l Types of events captured in an audit trail include: l • • • l 6 -37 Network connection event data System-level event data Application-level event data User-level event data Keystroke activity Primary issue is the volume of data that must be examined for this understanding to be adequate
 Security Assessments: Penetration Testing ¢ “Pen” testing denotes activities undertaken to identify and exploit security vulnerabilities Evaluates system security by attacking it l Aimed at the security conditions that are the most common targets of intruders l Types of pen tests include: l • Zero-knowledge – where the tester has no relevant information about the target • Partial-knowledge – where the tester may have some information about the target • Full-knowledge – the tester has intimate knowledge of the target environment 6 -38
Security Assessments: Penetration Testing ¢ “Pen” testing denotes activities undertaken to identify and exploit security vulnerabilities Evaluates system security by attacking it l Aimed at the security conditions that are the most common targets of intruders l Types of pen tests include: l • Zero-knowledge – where the tester has no relevant information about the target • Partial-knowledge – where the tester may have some information about the target • Full-knowledge – the tester has intimate knowledge of the target environment 6 -38
 Security Assessments: Penetration Testing l Pen-testing methods are based on four activities: • • l Resultant report can help to identify: • • • 6 -39 Discovery Enumeration Vulnerability mapping User and privilege access Vulnerabilities of the system Gaps in security measures IDS and intrusion response capability Whether anyone is monitoring audit logs How suspicious activity is reported Potential countermeasures
Security Assessments: Penetration Testing l Pen-testing methods are based on four activities: • • l Resultant report can help to identify: • • • 6 -39 Discovery Enumeration Vulnerability mapping User and privilege access Vulnerabilities of the system Gaps in security measures IDS and intrusion response capability Whether anyone is monitoring audit logs How suspicious activity is reported Potential countermeasures
 Security Assessments: Penetration Testing l Various types of penetration-testing strategies include: • • • l Application security testing Denial of Service (Do. S) testing War dialing Wireless network penetration testing Social engineering Internal procedures focus on identifying anomalies in the internal IT environment and include: • Blind tests • Double-blind test • Targeted tests 6 -40
Security Assessments: Penetration Testing l Various types of penetration-testing strategies include: • • • l Application security testing Denial of Service (Do. S) testing War dialing Wireless network penetration testing Social engineering Internal procedures focus on identifying anomalies in the internal IT environment and include: • Blind tests • Double-blind test • Targeted tests 6 -40
 Common Access Control Models ¢ Access control models enforce policies Must be specifically designed to embody the organization’s overall approach to security l Three types of models in common use in the industry today: l • Confidentiality/Classification-based models – Bell. La. Padula • Integrity-based models – Biba • Transaction-based models – Clark-Wilson 6 -41
Common Access Control Models ¢ Access control models enforce policies Must be specifically designed to embody the organization’s overall approach to security l Three types of models in common use in the industry today: l • Confidentiality/Classification-based models – Bell. La. Padula • Integrity-based models – Biba • Transaction-based models – Clark-Wilson 6 -41
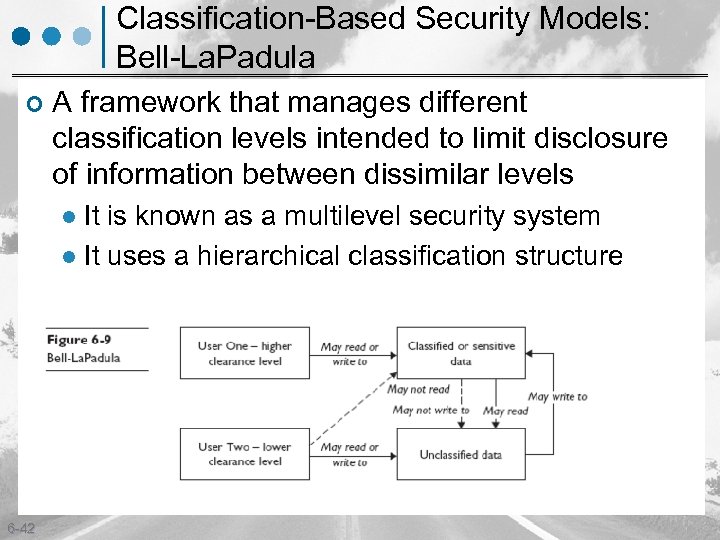 Classification-Based Security Models: Bell-La. Padula ¢ A framework that manages different classification levels intended to limit disclosure of information between dissimilar levels It is known as a multilevel security system l It uses a hierarchical classification structure l 6 -42
Classification-Based Security Models: Bell-La. Padula ¢ A framework that manages different classification levels intended to limit disclosure of information between dissimilar levels It is known as a multilevel security system l It uses a hierarchical classification structure l 6 -42
 Classification-Based Security Models: Bell-La. Padula ¢ Bell-La. Padula l Employs both mandatory and discretionary access control mechanisms • Implements two security rules - “no-read-up” and “nowrite-down. ” Centers on a set of subjects along with data objects and their relative security levels l Classification level of the object and the access rights of the subject determine: l • What data the subject is authorized to access • What they may legitimately do with it 6 -43
Classification-Based Security Models: Bell-La. Padula ¢ Bell-La. Padula l Employs both mandatory and discretionary access control mechanisms • Implements two security rules - “no-read-up” and “nowrite-down. ” Centers on a set of subjects along with data objects and their relative security levels l Classification level of the object and the access rights of the subject determine: l • What data the subject is authorized to access • What they may legitimately do with it 6 -43
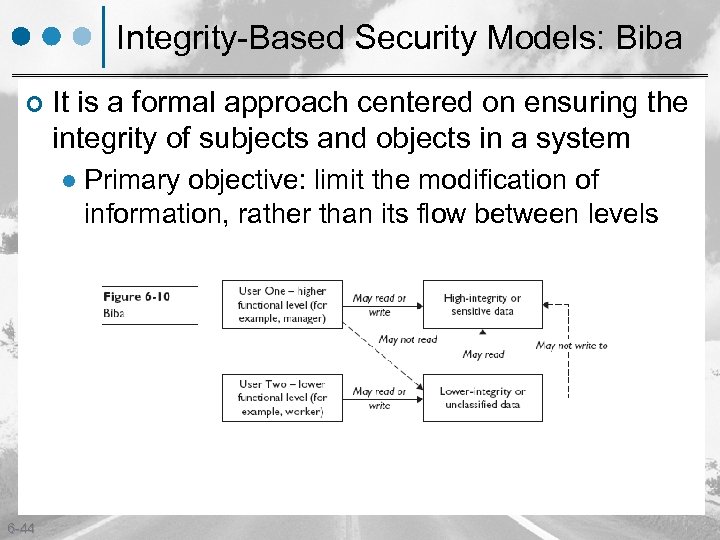 Integrity-Based Security Models: Biba ¢ It is a formal approach centered on ensuring the integrity of subjects and objects in a system l 6 -44 Primary objective: limit the modification of information, rather than its flow between levels
Integrity-Based Security Models: Biba ¢ It is a formal approach centered on ensuring the integrity of subjects and objects in a system l 6 -44 Primary objective: limit the modification of information, rather than its flow between levels
 Integrity-Based Security Models: Biba ¢ Biba operates on two simple rules: A subject with a lower classification cannot write data to a higher classification l A subject with a higher classification cannot read data from a lower classification l ¢ 6 -45 Biba model is called an information flow model
Integrity-Based Security Models: Biba ¢ Biba operates on two simple rules: A subject with a lower classification cannot write data to a higher classification l A subject with a higher classification cannot read data from a lower classification l ¢ 6 -45 Biba model is called an information flow model
 Transaction-Based Security Models: Clark-Wilson ¢ This model uses transactions as the basis for its access control decision making l Defines two levels of integrity: • Constrained data items (CDI) – the controlled assets • Unconstrained data items (UDI) – not deemed valuable enough to control l Defines two types of processes to control CDIs: • Integrity verification processes (IVP) – ensure that the CDI meets specified integrity constraints • Transformation processes (TP) – change the state of data from one valid state to another 6 -46
Transaction-Based Security Models: Clark-Wilson ¢ This model uses transactions as the basis for its access control decision making l Defines two levels of integrity: • Constrained data items (CDI) – the controlled assets • Unconstrained data items (UDI) – not deemed valuable enough to control l Defines two types of processes to control CDIs: • Integrity verification processes (IVP) – ensure that the CDI meets specified integrity constraints • Transformation processes (TP) – change the state of data from one valid state to another 6 -46
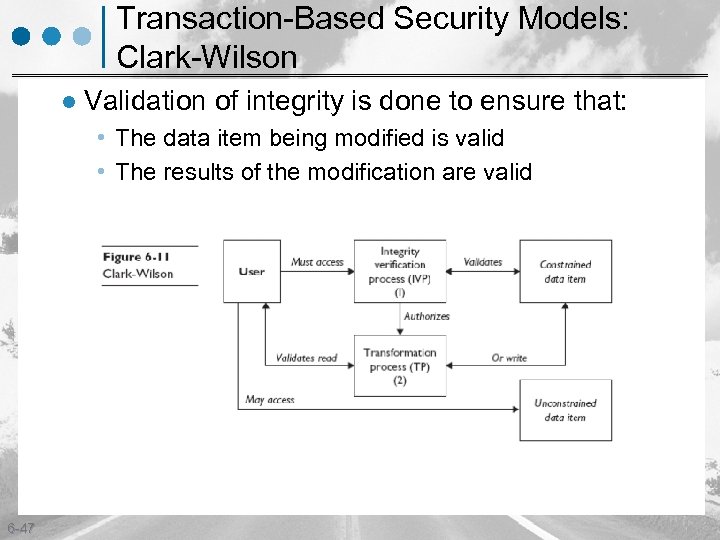 Transaction-Based Security Models: Clark-Wilson l Validation of integrity is done to ensure that: • The data item being modified is valid • The results of the modification are valid 6 -47
Transaction-Based Security Models: Clark-Wilson l Validation of integrity is done to ensure that: • The data item being modified is valid • The results of the modification are valid 6 -47


