41aca867396a4416625f15447ec5f92a.ppt
- Количество слайдов: 44
 Information Assurance for the Enterprise: A Roadmap to Information Security, by Schou and Shoemaker Chapter 11 Law, Regulations, and Crime Mc. Graw-Hill/Irwin Copyright © 2007 by The Mc. Graw-Hill Companies, Inc. All rights reserved.
Information Assurance for the Enterprise: A Roadmap to Information Security, by Schou and Shoemaker Chapter 11 Law, Regulations, and Crime Mc. Graw-Hill/Irwin Copyright © 2007 by The Mc. Graw-Hill Companies, Inc. All rights reserved.
 Objectives Work with legal issues associated with computers and information ¢ Work with laws and regulations governing the security of information ¢ Consider the various aspects of cyber crime ¢ Work with the elements of ensuring contract compliance ¢ 11 -2
Objectives Work with legal issues associated with computers and information ¢ Work with laws and regulations governing the security of information ¢ Consider the various aspects of cyber crime ¢ Work with the elements of ensuring contract compliance ¢ 11 -2
 Compliance ¢ A formal process to ensure fulfillment of the terms of a law, regulation, contract, or standard Describes the overall approach to ensuring conformance with applicable laws, regulations, and contracts l Important part of day-to-day operation l ¢ Organizations have a duty to: Establish a formal identification process for legal problems associated with information l Ensure compliance l 11 -3
Compliance ¢ A formal process to ensure fulfillment of the terms of a law, regulation, contract, or standard Describes the overall approach to ensuring conformance with applicable laws, regulations, and contracts l Important part of day-to-day operation l ¢ Organizations have a duty to: Establish a formal identification process for legal problems associated with information l Ensure compliance l 11 -3
 Protecting Intellectual Property ¢ Intangible value l Intangible property has no actual form but it has value and is an asset • Can include everything from proprietary methods, programs, systems, procedures, and technical data, to business forecasts, industry estimates, survey data, and customer lists l Enforcement of intellectual property rights is possible because of the • Ability to document ownership • Ability to assign real value to intangible things 11 -4
Protecting Intellectual Property ¢ Intangible value l Intangible property has no actual form but it has value and is an asset • Can include everything from proprietary methods, programs, systems, procedures, and technical data, to business forecasts, industry estimates, survey data, and customer lists l Enforcement of intellectual property rights is possible because of the • Ability to document ownership • Ability to assign real value to intangible things 11 -4
 Protecting Intellectual Property ¢ International enforcement Make sure that all provisions for international regulation of intangible property are understood and obeyed l Enforcement agencies include: l • Business Software Alliance (BSA) • Recording Industry Association of America (RIAA) l 11 -5 Digital Millennium Copyright Act (DMCA) is considered as a tool for enforcement
Protecting Intellectual Property ¢ International enforcement Make sure that all provisions for international regulation of intangible property are understood and obeyed l Enforcement agencies include: l • Business Software Alliance (BSA) • Recording Industry Association of America (RIAA) l 11 -5 Digital Millennium Copyright Act (DMCA) is considered as a tool for enforcement
 Enforcing Protection Rights: The Digital Millennium Copyright Act (DMCA) ¢ DMCA Implements the World Intellectual Property Organization’s (WIPO) Copyright and Performances and Phonograms l Protects and criminalizes copyright infringement l Makes it criminal to circumvent software antipiracy measures or produce illegal copying l Although it strengthens legal protection internationally, enforcement of rights does not extend outside of the U. S. , Canada, and Western Europe l 11 -6
Enforcing Protection Rights: The Digital Millennium Copyright Act (DMCA) ¢ DMCA Implements the World Intellectual Property Organization’s (WIPO) Copyright and Performances and Phonograms l Protects and criminalizes copyright infringement l Makes it criminal to circumvent software antipiracy measures or produce illegal copying l Although it strengthens legal protection internationally, enforcement of rights does not extend outside of the U. S. , Canada, and Western Europe l 11 -6
 International Prevention and the Business Software Alliance (BSA) ¢ BSA is one of the most influential players in international piracy prevention Works with law enforcement agencies in over 30 countries l Identifies and prosecutes licensing agreement violators l Functions as a quasi-legal international entity l ¢ 11 -7 Work of the BSA is limited to countries where piracy is discouraged
International Prevention and the Business Software Alliance (BSA) ¢ BSA is one of the most influential players in international piracy prevention Works with law enforcement agencies in over 30 countries l Identifies and prosecutes licensing agreement violators l Functions as a quasi-legal international entity l ¢ 11 -7 Work of the BSA is limited to countries where piracy is discouraged
 Software Piracy ¢ Deliberate theft of software is piracy Computer programs are copyrighted works; therefore there is a need for a license or permission to use it l Valid proof called a software license is required to demonstrate that the use is with permission l Various types of permissions accompany these licenses: l • Some limit installation to a single computer • Others provide a site-wide authorization 11 -8
Software Piracy ¢ Deliberate theft of software is piracy Computer programs are copyrighted works; therefore there is a need for a license or permission to use it l Valid proof called a software license is required to demonstrate that the use is with permission l Various types of permissions accompany these licenses: l • Some limit installation to a single computer • Others provide a site-wide authorization 11 -8
 Software Piracy ¢ Consequences of piracy Organizations are liable for violating licensing agreement terms even if an individual worker actually caused the problem l To show due diligence: l • The organization must document a conscientious effort to enforce licensing restrictions in its operations • Proof of this is a comprehensive, formally documented control system that strictly monitors and enforces all contracts and agreements 11 -9
Software Piracy ¢ Consequences of piracy Organizations are liable for violating licensing agreement terms even if an individual worker actually caused the problem l To show due diligence: l • The organization must document a conscientious effort to enforce licensing restrictions in its operations • Proof of this is a comprehensive, formally documented control system that strictly monitors and enforces all contracts and agreements 11 -9
 Software Piracy ¢ Regulating piracy l Two federal regulations addressing software piracy: • Computer Software Rental Amendments Act of 1990 • Specifying that rental, lease, or lending of copyrighted software is forbidden without copyright owner authorization • Copyright law (Title 17 of the U. S. Code) • Interpreted to mean that the creation or distribution of copyrighted software without authorization is illegal even if there is no express copyright given to the owner 11 -10
Software Piracy ¢ Regulating piracy l Two federal regulations addressing software piracy: • Computer Software Rental Amendments Act of 1990 • Specifying that rental, lease, or lending of copyrighted software is forbidden without copyright owner authorization • Copyright law (Title 17 of the U. S. Code) • Interpreted to mean that the creation or distribution of copyrighted software without authorization is illegal even if there is no express copyright given to the owner 11 -10
 Laws Affecting Computer Use Most contemporary computer-use laws deal with protecting privacy and regulating commercial transactions ¢ There are four categories: ¢ Governmental regulations l Privacy regulations l Laws that define computer crime l Laws that regulate classified or sensitive information l 11 -11
Laws Affecting Computer Use Most contemporary computer-use laws deal with protecting privacy and regulating commercial transactions ¢ There are four categories: ¢ Governmental regulations l Privacy regulations l Laws that define computer crime l Laws that regulate classified or sensitive information l 11 -11
 Government Regulations ¢ First regulatory actions 18 U. S. C. 1005 (1948) prohibiting false entries in bank records and falsifying credit institution records l 18 U. S. C. 1362 (1948) prohibits malicious mischief to government property l 18 U. S. C. 2071 (1948) prohibits concealment, removal, or mutilation of public records l ¢ 11 -12 In 1952, 18 U. S. C. 1343, prohibited wire fraud using interstate communications systems
Government Regulations ¢ First regulatory actions 18 U. S. C. 1005 (1948) prohibiting false entries in bank records and falsifying credit institution records l 18 U. S. C. 1362 (1948) prohibits malicious mischief to government property l 18 U. S. C. 2071 (1948) prohibits concealment, removal, or mutilation of public records l ¢ 11 -12 In 1952, 18 U. S. C. 1343, prohibited wire fraud using interstate communications systems
 Government Regulations ¢ 1980 s – New laws to respond to legal problems developing around information processing and communication l l 11 -13 18 U. S. C. 1029 (1984) prohibited fraudulent use of credit cards, passwords, and telephone access codes 18 U. S. C. 2701 (1986) prohibited unauthorized access to electronically stored information 18 U. S. C. 2778 (1989) prohibited illegal export of software or data controlled by the Department of Defense (Do. D) 18 U. S. C. 2510 (1989) prohibited the illegal export of software or data controlled by the Department of Commerce
Government Regulations ¢ 1980 s – New laws to respond to legal problems developing around information processing and communication l l 11 -13 18 U. S. C. 1029 (1984) prohibited fraudulent use of credit cards, passwords, and telephone access codes 18 U. S. C. 2701 (1986) prohibited unauthorized access to electronically stored information 18 U. S. C. 2778 (1989) prohibited illegal export of software or data controlled by the Department of Defense (Do. D) 18 U. S. C. 2510 (1989) prohibited the illegal export of software or data controlled by the Department of Commerce
 Privacy Regulations ¢ Privacy centers on the acquisition and use of personal information as a commercial product l l l 11 -14 Institutions, both good and malicious, collect and maintain most vital personal information Accumulated information is harmless as long as it is not obtained or used with malicious intent Privacy is closely related to the information assurance principle of confidentiality Misappropriation of personal information may lead to more than privacy loss; it may lead to financial damages Notwithstanding possible criminal activity, privacy violations occur because of human error
Privacy Regulations ¢ Privacy centers on the acquisition and use of personal information as a commercial product l l l 11 -14 Institutions, both good and malicious, collect and maintain most vital personal information Accumulated information is harmless as long as it is not obtained or used with malicious intent Privacy is closely related to the information assurance principle of confidentiality Misappropriation of personal information may lead to more than privacy loss; it may lead to financial damages Notwithstanding possible criminal activity, privacy violations occur because of human error
 Privacy Regulations ¢ Legal consequences can be severe and apply even if the error was inadvertent Anticipate these threats by instituting routine assurance procedures and controls l Laws regarding privacy define the rights of individuals to know and control their personal information l 11 -15
Privacy Regulations ¢ Legal consequences can be severe and apply even if the error was inadvertent Anticipate these threats by instituting routine assurance procedures and controls l Laws regarding privacy define the rights of individuals to know and control their personal information l 11 -15
 Laws to Protect Privacy Individuals have the right to control some, but not all, of their information ¢ Bill of Rights to the U. S. Constitution (1791) ¢ l 11 -16 The Fourth Amendment guarantees individual protection against unreasonable search and seizure by the government
Laws to Protect Privacy Individuals have the right to control some, but not all, of their information ¢ Bill of Rights to the U. S. Constitution (1791) ¢ l 11 -16 The Fourth Amendment guarantees individual protection against unreasonable search and seizure by the government
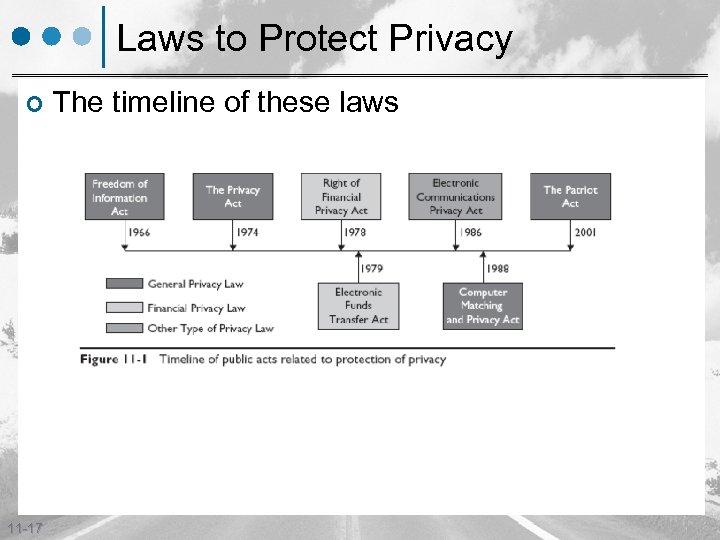 Laws to Protect Privacy ¢ 11 -17 The timeline of these laws
Laws to Protect Privacy ¢ 11 -17 The timeline of these laws
 The Freedom of Information Act ¢ Freedom of Information Act (FOIA) (5 U. S. C. 552 PL 890554) - 1966 l Offers the first electronic-age privacy protections • “Need to know” standard was replaced with a “right to know” l l Guarantees access to documents held by Executive Branch agencies and cabinet departments Does not apply to records held by • • • 11 -18 Elected federal officials The federal judiciary Private organizations Individuals who receive federal contracts or grants Tax-exempt organizations State and local government
The Freedom of Information Act ¢ Freedom of Information Act (FOIA) (5 U. S. C. 552 PL 890554) - 1966 l Offers the first electronic-age privacy protections • “Need to know” standard was replaced with a “right to know” l l Guarantees access to documents held by Executive Branch agencies and cabinet departments Does not apply to records held by • • • 11 -18 Elected federal officials The federal judiciary Private organizations Individuals who receive federal contracts or grants Tax-exempt organizations State and local government
 The Freedom of Information Act ¢ Requires federal agencies to provide full public disclosure of information Provides administrative and judicial remedies for those denied access l In 1986, amendments gave agencies some authority to deny access to a record or refuse to confirm its existence in specific instances: l • Records that might interfere with an active law enforcement investigation • Records from confidential informants • Records that pertain to foreign intelligence 11 -19
The Freedom of Information Act ¢ Requires federal agencies to provide full public disclosure of information Provides administrative and judicial remedies for those denied access l In 1986, amendments gave agencies some authority to deny access to a record or refuse to confirm its existence in specific instances: l • Records that might interfere with an active law enforcement investigation • Records from confidential informants • Records that pertain to foreign intelligence 11 -19
 The Privacy Act ¢ The Privacy Act (PL 93 -579) - 1974 l Defines the rights of individuals with respect to the computerized information kept about them • Requires the government to safeguard integrity, confidentiality, and availability • Agencies are to offer ways for individuals to determine what information is being recorded about them • Mandates a process to correct inaccuracies • Safeguards individuals from invasion of privacy by the federal government by: • Regulating the way the government collects, maintains, uses, and disseminates personal information 11 -20
The Privacy Act ¢ The Privacy Act (PL 93 -579) - 1974 l Defines the rights of individuals with respect to the computerized information kept about them • Requires the government to safeguard integrity, confidentiality, and availability • Agencies are to offer ways for individuals to determine what information is being recorded about them • Mandates a process to correct inaccuracies • Safeguards individuals from invasion of privacy by the federal government by: • Regulating the way the government collects, maintains, uses, and disseminates personal information 11 -20
 The Privacy Act l Federal agencies or specified organizations are subject to • Penalties for willful or intentional action that violates individual rights l Criminal penalties may be applied • If prohibited information is disclosed or • Where the maintenance of the record was in violation 11 -21
The Privacy Act l Federal agencies or specified organizations are subject to • Penalties for willful or intentional action that violates individual rights l Criminal penalties may be applied • If prohibited information is disclosed or • Where the maintenance of the record was in violation 11 -21
 Act Related to Financial Privacy ¢ The Right of Financial Privacy Act (1978) l ¢ The Electronic Funds Transfer Act (1979) l 11 -22 Establishes that a depositor’s bank accounts are private and can be accessed only by court order with due and proper notification Specifically safeguarded the privacy of transmissions related to funds using electronic funds transfer (EFT)
Act Related to Financial Privacy ¢ The Right of Financial Privacy Act (1978) l ¢ The Electronic Funds Transfer Act (1979) l 11 -22 Establishes that a depositor’s bank accounts are private and can be accessed only by court order with due and proper notification Specifically safeguarded the privacy of transmissions related to funds using electronic funds transfer (EFT)
 Act Related to Financial Privacy ¢ The Electronic Communications Privacy Act of 1986 (PL 99 -508, 18 U. S. C. 2510) Offered single clear statement of individual rights with respect to electronic information l Prohibits unauthorized interception of communications independent of how the transmission took place l • Includes transmissions over the following media: • • • 11 -23 Wire Radio Electromagnetic Photo-electrical Photo-optical
Act Related to Financial Privacy ¢ The Electronic Communications Privacy Act of 1986 (PL 99 -508, 18 U. S. C. 2510) Offered single clear statement of individual rights with respect to electronic information l Prohibits unauthorized interception of communications independent of how the transmission took place l • Includes transmissions over the following media: • • • 11 -23 Wire Radio Electromagnetic Photo-electrical Photo-optical
 Computer Matching and Privacy Protection Act ¢ The Computer Matching and Privacy Protection Act - 5 U. S. C. 552 a (1988) Amendment of The Privacy Act l If an individual proves that a federal agency intentionally or willfully violated provisions of this act, they can recover monetary damages l • Raised overall national awareness of potential for misuse of personal information collected on computers • Controversial because it institutionalizes data-mining activities conducted by federal agencies 11 -24
Computer Matching and Privacy Protection Act ¢ The Computer Matching and Privacy Protection Act - 5 U. S. C. 552 a (1988) Amendment of The Privacy Act l If an individual proves that a federal agency intentionally or willfully violated provisions of this act, they can recover monetary damages l • Raised overall national awareness of potential for misuse of personal information collected on computers • Controversial because it institutionalizes data-mining activities conducted by federal agencies 11 -24
 Computer Matching and Privacy Protection Act ¢ USA PATRIOT Act of 2001 l Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Act • Gives law enforcement and intelligence agencies • Authority to monitor private communications • Access to the personal information of individuals in order to safeguard against terrorism • Contravenes many federal government laws and common law legal precedents • It has been extremely divisive 11 -25
Computer Matching and Privacy Protection Act ¢ USA PATRIOT Act of 2001 l Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Act • Gives law enforcement and intelligence agencies • Authority to monitor private communications • Access to the personal information of individuals in order to safeguard against terrorism • Contravenes many federal government laws and common law legal precedents • It has been extremely divisive 11 -25
 Canning Spam: The CAN-SPAM Act of 2003 ¢ Deals with the rapid increase of Internet junk mail, called spam Based on the concept of affirmative consent l Under this law, it is illegal to: l • Send a commercial e-mail message with header information that is either false or misleading • Spoof the originating address or relay a message from another computer to disguise its point of origin • Failure to identify clearly that the message is an advertisement or solicitation l 11 -26 Requires that the message provides a conspicuous opportunity to decline further messages
Canning Spam: The CAN-SPAM Act of 2003 ¢ Deals with the rapid increase of Internet junk mail, called spam Based on the concept of affirmative consent l Under this law, it is illegal to: l • Send a commercial e-mail message with header information that is either false or misleading • Spoof the originating address or relay a message from another computer to disguise its point of origin • Failure to identify clearly that the message is an advertisement or solicitation l 11 -26 Requires that the message provides a conspicuous opportunity to decline further messages
 Canning Spam: The CAN-SPAM Act of 2003 Aggravated violations can bring a substantial fine and imprisonment of one to five years ¢ Federal enforcement of CAN-SPAM is vested in the Federal Trade Commission (FTC) ¢ l ¢ 11 -27 Prosecutes in the same way as other unfair or criminal trade practice States enforce this law through their respective attorneys general
Canning Spam: The CAN-SPAM Act of 2003 Aggravated violations can bring a substantial fine and imprisonment of one to five years ¢ Federal enforcement of CAN-SPAM is vested in the Federal Trade Commission (FTC) ¢ l ¢ 11 -27 Prosecutes in the same way as other unfair or criminal trade practice States enforce this law through their respective attorneys general
 Cyber Crime ¢ “Hacker” – Any person who violates a computer or its information Hackers seek unauthorized access to computer systems l Motivated for different reasons: l • • • 11 -28 Curiosity or recreational attacks Business or financial attacks Grudge attacks Intelligence attacks Military or terrorist attacks
Cyber Crime ¢ “Hacker” – Any person who violates a computer or its information Hackers seek unauthorized access to computer systems l Motivated for different reasons: l • • • 11 -28 Curiosity or recreational attacks Business or financial attacks Grudge attacks Intelligence attacks Military or terrorist attacks
 Cyber Crime ¢ Types of hackers are differentiated based on four factors: Motivation – Why was the crime committed and how, where, when, and why was a particular victim selected? l Method – Sequence of events and behavior of victims and offenders have to be considered l Outcome – What was the result of the criminal behavior? What was the degree of harm and was it intentional? l Post-offense behavior – How does the offender act after committing the crime? Do they seek publicity or anonymity? l 11 -29
Cyber Crime ¢ Types of hackers are differentiated based on four factors: Motivation – Why was the crime committed and how, where, when, and why was a particular victim selected? l Method – Sequence of events and behavior of victims and offenders have to be considered l Outcome – What was the result of the criminal behavior? What was the degree of harm and was it intentional? l Post-offense behavior – How does the offender act after committing the crime? Do they seek publicity or anonymity? l 11 -29
 Motivation and Method ¢ Classified into eight behavioral signatures or methods of operation (MOs): Ego l Exposure l Deviance l Monetary gain l Extortion l Sabotage l Disinformation l Infowar l 11 -30
Motivation and Method ¢ Classified into eight behavioral signatures or methods of operation (MOs): Ego l Exposure l Deviance l Monetary gain l Extortion l Sabotage l Disinformation l Infowar l 11 -30
 Outcome ¢ The outcome is a good way of classifying intent l Six factors describe intent: • Trespass • Invasion – three categories: • Appropriation (of personal information) • Publication of private facts (confidentiality) • False light • • 11 -31 Theft Harm Commercialization Strategic
Outcome ¢ The outcome is a good way of classifying intent l Six factors describe intent: • Trespass • Invasion – three categories: • Appropriation (of personal information) • Publication of private facts (confidentiality) • False light • • 11 -31 Theft Harm Commercialization Strategic
 Behavior ¢ There at least 12 distinct behavioral types: l l l 11 -32 Kiddies Cyber-punks Old-timers Code warriors Cyber thief Cyber hucksters Unhappy insiders Ex–insiders Cyber–stalkers Conman The Soldier Warfighter
Behavior ¢ There at least 12 distinct behavioral types: l l l 11 -32 Kiddies Cyber-punks Old-timers Code warriors Cyber thief Cyber hucksters Unhappy insiders Ex–insiders Cyber–stalkers Conman The Soldier Warfighter
 Types of Hacker Tools ¢ Password cracking – relies on: l Password sharing • The simple disclosure of a password to others l Password guessing • Hackers use software to automate this attack l Password capture • Hacker obtains the password using malware or Trojan code 11 -33
Types of Hacker Tools ¢ Password cracking – relies on: l Password sharing • The simple disclosure of a password to others l Password guessing • Hackers use software to automate this attack l Password capture • Hacker obtains the password using malware or Trojan code 11 -33
 Technological Approaches of Attackers ¢ Approaches of attackers Spoofing l Probe tools l • Port scanners • Keyloggers and their password capture variants Remote Administration Tool (RAT) l Social engineering - “running a con game” l • “Phone survey” and the “emergency situation” • Defense: know or verify the identity of the person you are talking to • Low-tech approach – “dumpster diving” • Countermeasure: a good shredder 11 -34
Technological Approaches of Attackers ¢ Approaches of attackers Spoofing l Probe tools l • Port scanners • Keyloggers and their password capture variants Remote Administration Tool (RAT) l Social engineering - “running a con game” l • “Phone survey” and the “emergency situation” • Defense: know or verify the identity of the person you are talking to • Low-tech approach – “dumpster diving” • Countermeasure: a good shredder 11 -34
 Computer Crime ¢ Crimes against property Not always technical in origin l Do not directly involve the use of the hacking tools l ¢ Criminal acts include: Phishing scams to steal account information from unsuspecting customers l Auction fraud, and non-delivery of merchandise l 11 -35
Computer Crime ¢ Crimes against property Not always technical in origin l Do not directly involve the use of the hacking tools l ¢ Criminal acts include: Phishing scams to steal account information from unsuspecting customers l Auction fraud, and non-delivery of merchandise l 11 -35
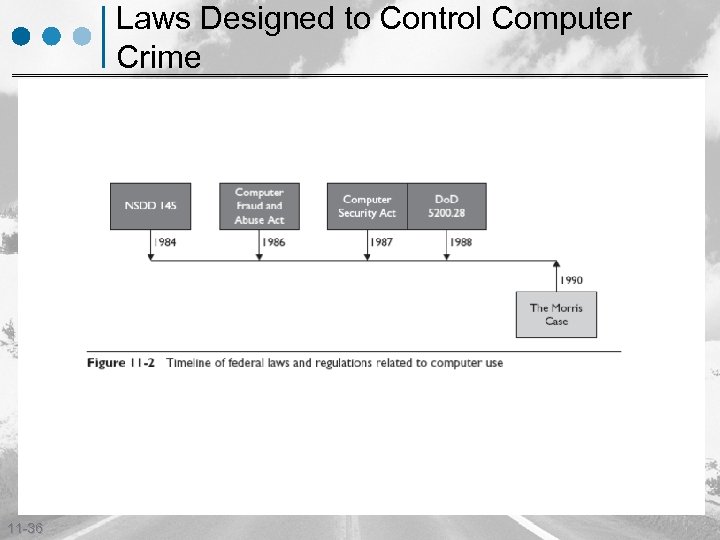 Laws Designed to Control Computer Crime 11 -36
Laws Designed to Control Computer Crime 11 -36
 Computer Fraud and Abuse Act ¢ Public Law 99 -474, the Computer Fraud and Abuse Act (1986) – establishes that a person is in criminal violation of the law if they: Knowingly access a federal interest computer without proper authorization l Exceed their permitted access privileges and subsequently use that access to: l • Cause a loss greater than $1, 000 • Obtain sensitive governmental information • Perform an act that prevents other authorized users from using a computer 11 -37
Computer Fraud and Abuse Act ¢ Public Law 99 -474, the Computer Fraud and Abuse Act (1986) – establishes that a person is in criminal violation of the law if they: Knowingly access a federal interest computer without proper authorization l Exceed their permitted access privileges and subsequently use that access to: l • Cause a loss greater than $1, 000 • Obtain sensitive governmental information • Perform an act that prevents other authorized users from using a computer 11 -37
 Computer Fraud and Abuse Act ¢ First application of the fraud and abuse act: The Morris case l 11 -38 In 1990, Robert T. Morris, Jr. , the legendary implementer of the first Internet “worm, ” was convicted and sentenced under this law
Computer Fraud and Abuse Act ¢ First application of the fraud and abuse act: The Morris case l 11 -38 In 1990, Robert T. Morris, Jr. , the legendary implementer of the first Internet “worm, ” was convicted and sentenced under this law
 Federal Regulations for Classified and Sensitive Information ¢ National Security Decision Directive 145– 1984 (NSDD-145) – covers such items as: Census Bureau statistics l Air traffic control information l Health and financial records l ¢ PL 107 -347 - Federal Information Security Management Act of 2002 Currently governs sensitive and classified information l Agencies must demonstrate due diligence in compliance l 11 -39
Federal Regulations for Classified and Sensitive Information ¢ National Security Decision Directive 145– 1984 (NSDD-145) – covers such items as: Census Bureau statistics l Air traffic control information l Health and financial records l ¢ PL 107 -347 - Federal Information Security Management Act of 2002 Currently governs sensitive and classified information l Agencies must demonstrate due diligence in compliance l 11 -39
 Federal Regulations for Classified and Sensitive Information l FISMA applies where the function, operation, or issuance of that system involves any of the following: • • Intelligence activities Cryptologic activities related to national security Command control of military forces Equipment that is an integral part of a weapon or weapons system • Equipment critical to fulfillment of military or intelligence missions • Information specifically authorized under executive order, or an act of Congress as classified in the interest of national defense or foreign policy 11 -40
Federal Regulations for Classified and Sensitive Information l FISMA applies where the function, operation, or issuance of that system involves any of the following: • • Intelligence activities Cryptologic activities related to national security Command control of military forces Equipment that is an integral part of a weapon or weapons system • Equipment critical to fulfillment of military or intelligence missions • Information specifically authorized under executive order, or an act of Congress as classified in the interest of national defense or foreign policy 11 -40
 National Computer Security Center ¢ National Computer Security Center (NCSC) Evaluates and recommends computing equipment for high-security applications l Trusted Product Evaluation Program (TPEP) – carries out NCSC’s computer evaluation directives l • Tests commercial products against a comprehensive set of security-related criteria l NCSC issued the first Department of Defense (Do. D) Trusted Computer System Evaluation Criteria (TCSEC) in August 1983 • “Orange book” 11 -41
National Computer Security Center ¢ National Computer Security Center (NCSC) Evaluates and recommends computing equipment for high-security applications l Trusted Product Evaluation Program (TPEP) – carries out NCSC’s computer evaluation directives l • Tests commercial products against a comprehensive set of security-related criteria l NCSC issued the first Department of Defense (Do. D) Trusted Computer System Evaluation Criteria (TCSEC) in August 1983 • “Orange book” 11 -41
 The Common criteria ¢ Common criteria l Standard model for certifying trustworthiness of commercial-off-the-shelf products under TPEP • Vendors request an evaluation of their commercial-offthe-shelf (COTS) products from the TPEP to get a specific level of trust rating • Evaluators working under TPEP use the Common Criteria to assess how well the product meets the requirements for the targeted rating • Evaluation Assurance Level (EAL) defines where the product falls on a scale of assurance 11 -42
The Common criteria ¢ Common criteria l Standard model for certifying trustworthiness of commercial-off-the-shelf products under TPEP • Vendors request an evaluation of their commercial-offthe-shelf (COTS) products from the TPEP to get a specific level of trust rating • Evaluators working under TPEP use the Common Criteria to assess how well the product meets the requirements for the targeted rating • Evaluation Assurance Level (EAL) defines where the product falls on a scale of assurance 11 -42
 Ensuring Contract Compliance ¢ Compliance ensures that the terms have been met l The body of law regulating contracts • Contract law: the principle for defining compliance, rights, and obligations of parties • Contract agreements: monitored through systematic reviews or audits of the results • Formal reviews and inspections assure legal and regulatory compliance 11 -43
Ensuring Contract Compliance ¢ Compliance ensures that the terms have been met l The body of law regulating contracts • Contract law: the principle for defining compliance, rights, and obligations of parties • Contract agreements: monitored through systematic reviews or audits of the results • Formal reviews and inspections assure legal and regulatory compliance 11 -43
 Ensuring Contract Compliance l Formal contract reviews – scheduled based on the level of assurance desired • Reviews have to be formally planned and scheduled as part of the overall information assurance process • Planning has to be based on the level of integrity required l Compliance audits – ensure the strict conformance to a contract condition, law, or regulation • Audit process requires a complete definition of the requirements of a given compliance situation 11 -44
Ensuring Contract Compliance l Formal contract reviews – scheduled based on the level of assurance desired • Reviews have to be formally planned and scheduled as part of the overall information assurance process • Planning has to be based on the level of integrity required l Compliance audits – ensure the strict conformance to a contract condition, law, or regulation • Audit process requires a complete definition of the requirements of a given compliance situation 11 -44


