dd85da383d1172f620553c0beba7fbbc.ppt
- Количество слайдов: 63
 Individual Identification Shurong Zhong (Ph. D, Associate Pf. ) Department of Forensic Biology, KMMU Cell Phone: 18213823198 E-mail: zhongshurong@hotmail. com
Individual Identification Shurong Zhong (Ph. D, Associate Pf. ) Department of Forensic Biology, KMMU Cell Phone: 18213823198 E-mail: zhongshurong@hotmail. com
 Graduated from Kunming Institute of Zoology, Chinese Academy of Sciences , July 2005
Graduated from Kunming Institute of Zoology, Chinese Academy of Sciences , July 2005
 Got Ph. D degree, March 2006 Joined School of Forensic Medicine, KMMU, 2006
Got Ph. D degree, March 2006 Joined School of Forensic Medicine, KMMU, 2006
 Studied at Cornell University Jan. 2010 -Jan. 2011 Weill Institute for Cell and Molecular Biology
Studied at Cornell University Jan. 2010 -Jan. 2011 Weill Institute for Cell and Molecular Biology
 Teaching
Teaching
 Scientific Research Alcohol Dependence Syndrome Candidate Genes
Scientific Research Alcohol Dependence Syndrome Candidate Genes
 Scientific Projects • Chinese National Natural Science Foundation (81000577) (Principal Investigator) Title: Study of pharmacodynamic gene and treatment for alcohol dependence in Yunnan Yi and Miao populations. • Yunnan Natural Science Foundation (2009 CD 080) (Principal Investigator) Title: Association analyses of genetic polymorphisms of alcohol metabolism related genes with alcohol dependence syndrome in Yi and Miao minority populations in Yunnan province. • Yunnan Natural Science Foundation (2007 C 223 M) (Principal Investigator) Title: Association analyses of genetic polymorphisms of DRD 2, DRD 4 and COMT with alcohol dependence syndrome in Yunnan Han population. • Yunnan Natural Science Foundation (2009 CD 211) (Co-Investigator) Title: Association analyses of genetic polymorphisms of pharmacodynamics genes with alcohol dependence syndrome and Personalized Medicines. • Chinese National Natural Science Foundation (30960115) (Co-Investigator) Title: The selection of sensitive genotype for drinking behaviour and alcohol abuse and research of genetic features. • Yunnan Educational Scientific Research Foundation (07 Z 10336) (Co-Investigator) Title: Association analyses of genetic polymorphisms of COMT and CYP 2 E 1 with alcohol dependence syndrome in Yunnan Han population.
Scientific Projects • Chinese National Natural Science Foundation (81000577) (Principal Investigator) Title: Study of pharmacodynamic gene and treatment for alcohol dependence in Yunnan Yi and Miao populations. • Yunnan Natural Science Foundation (2009 CD 080) (Principal Investigator) Title: Association analyses of genetic polymorphisms of alcohol metabolism related genes with alcohol dependence syndrome in Yi and Miao minority populations in Yunnan province. • Yunnan Natural Science Foundation (2007 C 223 M) (Principal Investigator) Title: Association analyses of genetic polymorphisms of DRD 2, DRD 4 and COMT with alcohol dependence syndrome in Yunnan Han population. • Yunnan Natural Science Foundation (2009 CD 211) (Co-Investigator) Title: Association analyses of genetic polymorphisms of pharmacodynamics genes with alcohol dependence syndrome and Personalized Medicines. • Chinese National Natural Science Foundation (30960115) (Co-Investigator) Title: The selection of sensitive genotype for drinking behaviour and alcohol abuse and research of genetic features. • Yunnan Educational Scientific Research Foundation (07 Z 10336) (Co-Investigator) Title: Association analyses of genetic polymorphisms of COMT and CYP 2 E 1 with alcohol dependence syndrome in Yunnan Han population.
 Judicial Identification Individual Identification Paternity Testing
Judicial Identification Individual Identification Paternity Testing
 On 21 November 1983, a 15 -year-old girl named Lynda Mann left her home to visit a friend's house. She did not return. The next morning, she was found raped and strangled on a deserted footpath known locally as the Black Pad. Narborough, Leicestershire, England, United Kingdom
On 21 November 1983, a 15 -year-old girl named Lynda Mann left her home to visit a friend's house. She did not return. The next morning, she was found raped and strangled on a deserted footpath known locally as the Black Pad. Narborough, Leicestershire, England, United Kingdom
 Narborough, Leicestershire, England, United Kingdom Only semen was taken from the murder scene. The semen sample revealed to a person with type A blood an enzyme profile that matched only 10 percent of males With no other leads or evidence, the case was left open.
Narborough, Leicestershire, England, United Kingdom Only semen was taken from the murder scene. The semen sample revealed to a person with type A blood an enzyme profile that matched only 10 percent of males With no other leads or evidence, the case was left open.
 On 31 July 1986, another 15 -year-old girl, Dawn Ashworth, took a shortcut instead of taking her normal route home. Two days later, her body was found in a wooded area near a footpath called Ten Pound Lane. She had been beaten, savagely raped, and strangled to death. Enderby, Leicestershire, England, United Kingdom
On 31 July 1986, another 15 -year-old girl, Dawn Ashworth, took a shortcut instead of taking her normal route home. Two days later, her body was found in a wooded area near a footpath called Ten Pound Lane. She had been beaten, savagely raped, and strangled to death. Enderby, Leicestershire, England, United Kingdom
 Enderby, Leicestershire, England, United Kingdom Only semen was taken from the murder scene. The method of operation matched that of the first attack. And semen sample revealed the same blood type.
Enderby, Leicestershire, England, United Kingdom Only semen was taken from the murder scene. The method of operation matched that of the first attack. And semen sample revealed the same blood type.
 Is he the real murderer? • The prime suspect was Richard Buckland. • He was a local 17 -year-old youth, who revealed knowledge of Ashworth's body, and admitted the crime under questioning, but denied the first murder.
Is he the real murderer? • The prime suspect was Richard Buckland. • He was a local 17 -year-old youth, who revealed knowledge of Ashworth's body, and admitted the crime under questioning, but denied the first murder.
 Alec Jeffreys Professor University of Leicester 1984,Jeffreys developed a new technique, which is called RFLP.
Alec Jeffreys Professor University of Leicester 1984,Jeffreys developed a new technique, which is called RFLP.
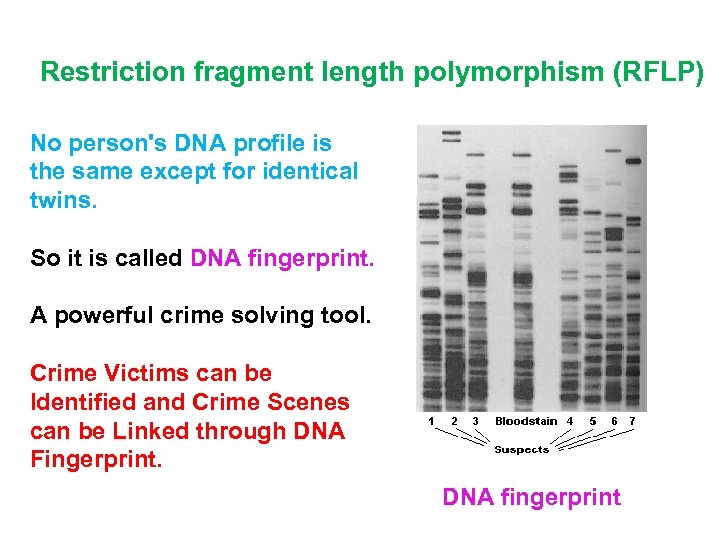 Restriction fragment length polymorphism (RFLP) No person's DNA profile is the same except for identical twins. So it is called DNA fingerprint. A powerful crime solving tool. Crime Victims can be Identified and Crime Scenes can be Linked through DNA Fingerprint. DNA fingerprint
Restriction fragment length polymorphism (RFLP) No person's DNA profile is the same except for identical twins. So it is called DNA fingerprint. A powerful crime solving tool. Crime Victims can be Identified and Crime Scenes can be Linked through DNA Fingerprint. DNA fingerprint
 Using DNA Fingerprint • November 1986, 17 -year-old Richard John Buckland was innocent of both murders. • The tests did prove conclusively that the crimes were committed by the same person.
Using DNA Fingerprint • November 1986, 17 -year-old Richard John Buckland was innocent of both murders. • The tests did prove conclusively that the crimes were committed by the same person.
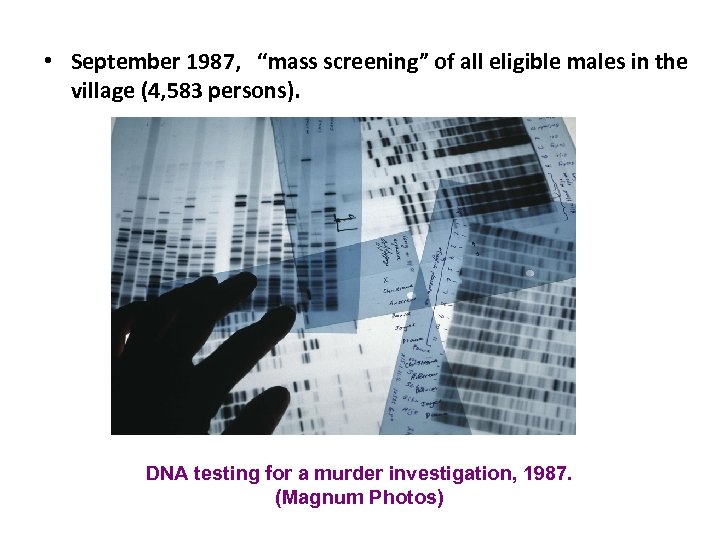 • September 1987, “mass screening” of all eligible males in the village (4, 583 persons). DNA testing for a murder investigation, 1987. (Magnum Photos)
• September 1987, “mass screening” of all eligible males in the village (4, 583 persons). DNA testing for a murder investigation, 1987. (Magnum Photos)
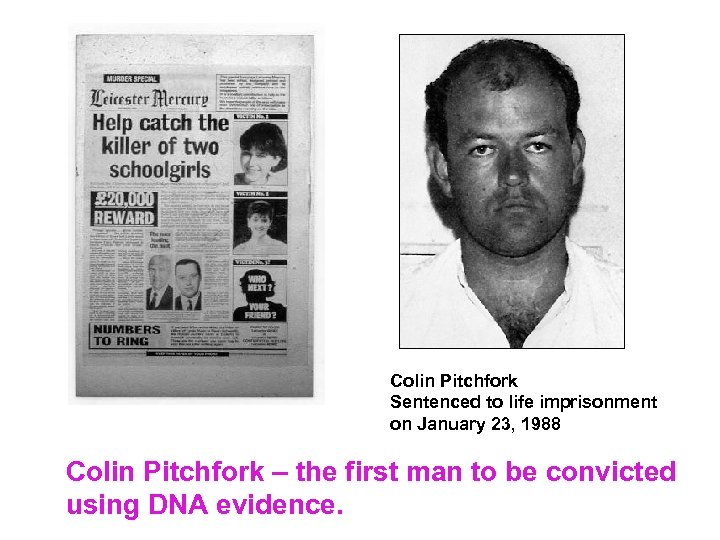 Colin Pitchfork Sentenced to life imprisonment on January 23, 1988 Colin Pitchfork – the first man to be convicted using DNA evidence.
Colin Pitchfork Sentenced to life imprisonment on January 23, 1988 Colin Pitchfork – the first man to be convicted using DNA evidence.
 Individual Identification Using DNA Typing
Individual Identification Using DNA Typing
 Content 1. What is Individual Identification? 2. How to conduct Individual Identification? 3. Typical cases 4. New Technique
Content 1. What is Individual Identification? 2. How to conduct Individual Identification? 3. Typical cases 4. New Technique
 1. What is Individual Identification? Individual/Personal Identification Theory To analyze genetic markers of biological samples collected from individual or crime scene to determine whether biological samples were identical or not.
1. What is Individual Identification? Individual/Personal Identification Theory To analyze genetic markers of biological samples collected from individual or crime scene to determine whether biological samples were identical or not.
 Biological samples from crime scenes Samples of suspects / Victims Suspicious Semen RFLP "Samples" and "sample" to compare Suspect
Biological samples from crime scenes Samples of suspects / Victims Suspicious Semen RFLP "Samples" and "sample" to compare Suspect
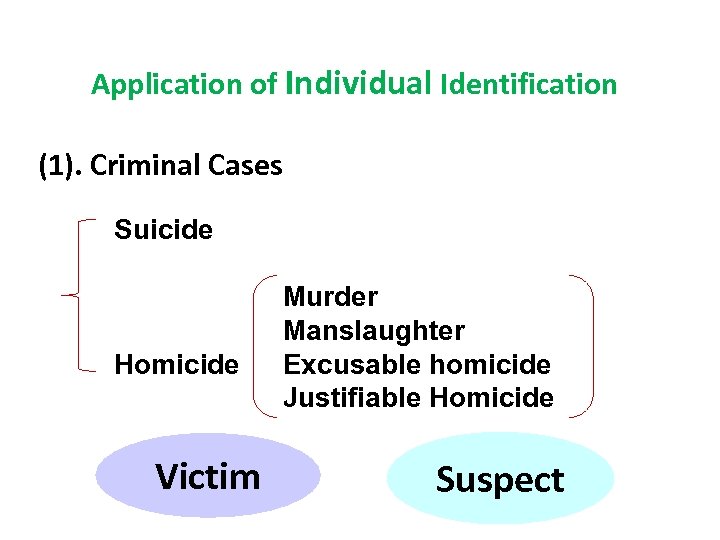 Application of Individual Identification (1). Criminal Cases Suicide Homicide Victim Murder Manslaughter Excusable homicide Justifiable Homicide Suspect
Application of Individual Identification (1). Criminal Cases Suicide Homicide Victim Murder Manslaughter Excusable homicide Justifiable Homicide Suspect
 ? Putting pieces back together
? Putting pieces back together
 (2). Traffic Accident Scene Investigation
(2). Traffic Accident Scene Investigation
 Victim Driver
Victim Driver
 (3). Mass Disaster Investigations 2004 Indian Ocean Tsunami 2001 “ 911”, New York 2008 Wenchuan Earthquake
(3). Mass Disaster Investigations 2004 Indian Ocean Tsunami 2001 “ 911”, New York 2008 Wenchuan Earthquake
 Bombing Case
Bombing Case
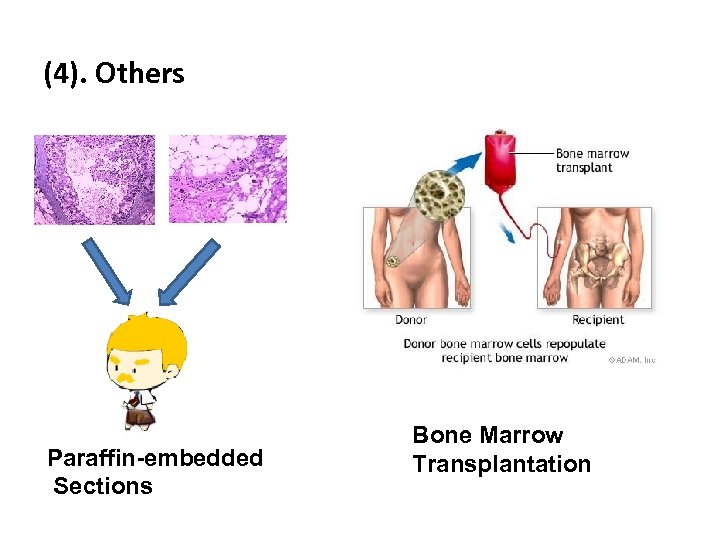 (4). Others Paraffin-embedded Sections Bone Marrow Transplantation
(4). Others Paraffin-embedded Sections Bone Marrow Transplantation
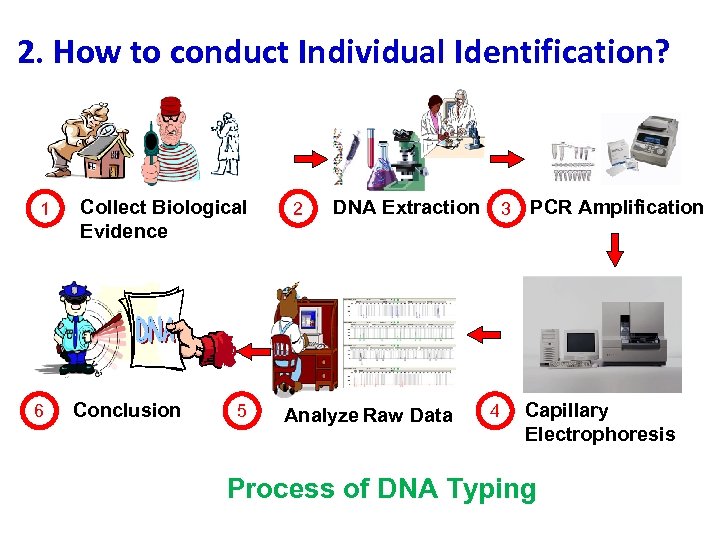 2. How to conduct Individual Identification? 1 6 Collect Biological Evidence Conclusion 5 2 DNA Extraction Analyze Raw Data 3 4 PCR Amplification Capillary Electrophoresis Process of DNA Typing
2. How to conduct Individual Identification? 1 6 Collect Biological Evidence Conclusion 5 2 DNA Extraction Analyze Raw Data 3 4 PCR Amplification Capillary Electrophoresis Process of DNA Typing
 1 What are Biological Evidence? Blood Semen Saliva Teeth Bone Urine Soft Tissue Hair (w/Root &Shaft)
1 What are Biological Evidence? Blood Semen Saliva Teeth Bone Urine Soft Tissue Hair (w/Root &Shaft)
 1 What are Biological Evidence? Cigarette Butts Envelope & Stamps Fingerprint residues Fingernail Clippings Chewing Gum Bite Marks Sweat/Tears Feces Trace Biological Evidence Touching DNA
1 What are Biological Evidence? Cigarette Butts Envelope & Stamps Fingerprint residues Fingernail Clippings Chewing Gum Bite Marks Sweat/Tears Feces Trace Biological Evidence Touching DNA
 1 What are Biological Evidence? Animal Material Plant Material Bacterial/Fungal Material Non-human Biological Evidence
1 What are Biological Evidence? Animal Material Plant Material Bacterial/Fungal Material Non-human Biological Evidence
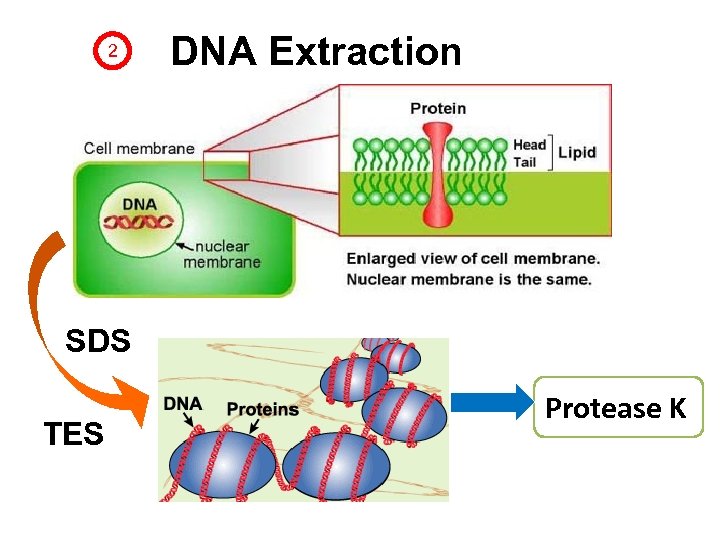 2 DNA Extraction SDS TES Protease K
2 DNA Extraction SDS TES Protease K
 3 PCR amplification RFLP Limitations • needs g amounts of DNA • DNA needs to be pure • assay time: several days to > week Multiplex PCR
3 PCR amplification RFLP Limitations • needs g amounts of DNA • DNA needs to be pure • assay time: several days to > week Multiplex PCR
 4 Capillary Electrophoresis
4 Capillary Electrophoresis
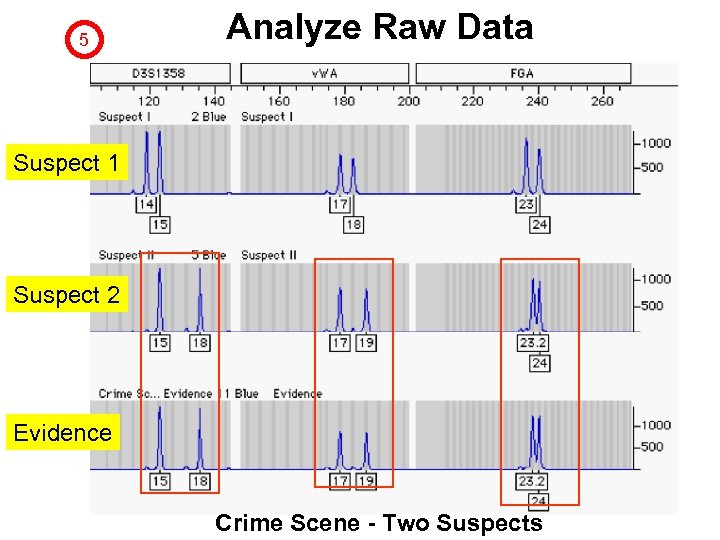 5 Analyze Raw Data Suspect 1 Suspect 2 Evidence Crime Scene - Two Suspects
5 Analyze Raw Data Suspect 1 Suspect 2 Evidence Crime Scene - Two Suspects
 6 Conclusion Suspicious Semen Colin Pitchfork The semen taken from both murder scenes were from Colin Pitchfork.
6 Conclusion Suspicious Semen Colin Pitchfork The semen taken from both murder scenes were from Colin Pitchfork.
 3. Typical cases Case 1: Sexual scandal between Monica Lewinsky and Bill Clinton 1998, Recorded phone calls (between Lewinsky and a close friend)
3. Typical cases Case 1: Sexual scandal between Monica Lewinsky and Bill Clinton 1998, Recorded phone calls (between Lewinsky and a close friend)
 李昌钰 Henry Chang-Yu Lee The world's foremost forensic scientists.
李昌钰 Henry Chang-Yu Lee The world's foremost forensic scientists.
 DNA analyses of semen stains on a dress worn by Monica Lewinsky match DNA from a blood sample taken from ex-president Bill Clinton.
DNA analyses of semen stains on a dress worn by Monica Lewinsky match DNA from a blood sample taken from ex-president Bill Clinton.
 Clinton confessed his affair with miss Monica at last. Bill Clinton – the worst victim of DNA evidence.
Clinton confessed his affair with miss Monica at last. Bill Clinton – the worst victim of DNA evidence.
 Case 2 Suspect A and his blood sample
Case 2 Suspect A and his blood sample
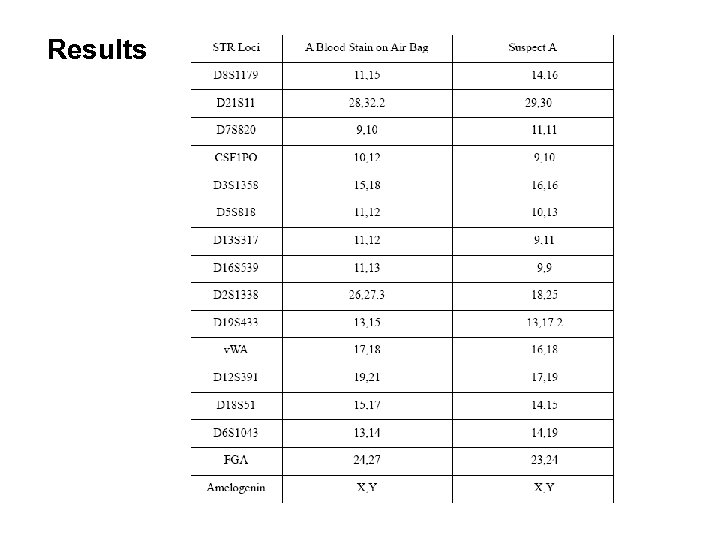 Results
Results
 Conclusion • DNA analyses of a blood stain on the air bag did not match DNA from a blood sample taken from suspect A. • The blood stain on the air bag was not from suspect A.
Conclusion • DNA analyses of a blood stain on the air bag did not match DNA from a blood sample taken from suspect A. • The blood stain on the air bag was not from suspect A.
 Case 3
Case 3
 Li XX and his blood sample
Li XX and his blood sample
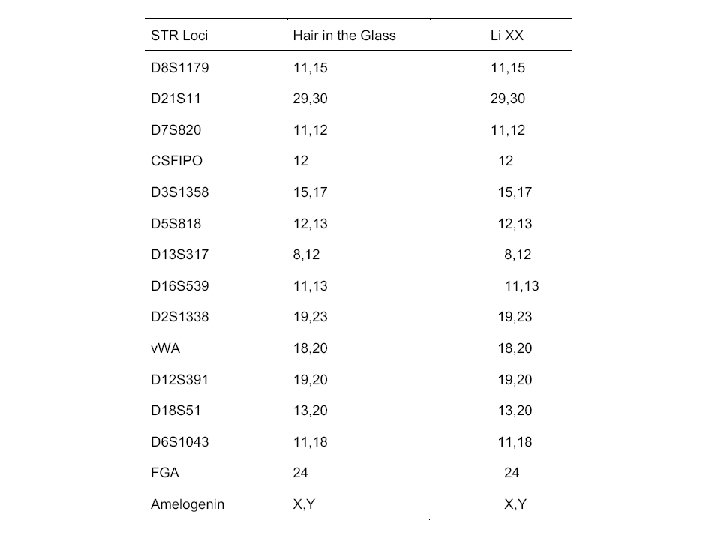
 • DNA analyses of hair in the glass did match DNA from a blood sample taken from Li XX. • Was the hair in the glass from Li XX? We can not answer it yet.
• DNA analyses of hair in the glass did match DNA from a blood sample taken from Li XX. • Was the hair in the glass from Li XX? We can not answer it yet.
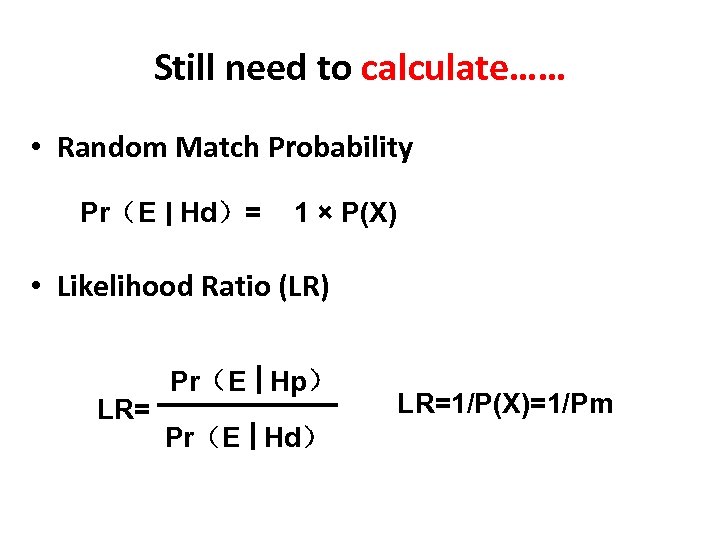 Still need to calculate…… • Random Match Probability Pr(E Hd)= 1 × P(X) • Likelihood Ratio (LR) LR= Pr(E Hp) Pr(E Hd) LR=1/P(X)=1/Pm
Still need to calculate…… • Random Match Probability Pr(E Hd)= 1 × P(X) • Likelihood Ratio (LR) LR= Pr(E Hp) Pr(E Hd) LR=1/P(X)=1/Pm
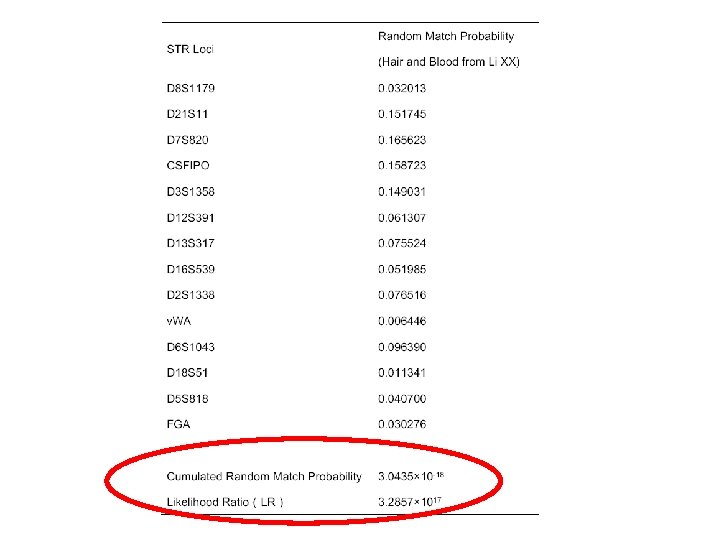
 Conclusion • DNA analyses of hair on the glass did match DNA from a blood sample taken from Li XX. • The hair in the glass was from Li XX.
Conclusion • DNA analyses of hair on the glass did match DNA from a blood sample taken from Li XX. • The hair in the glass was from Li XX.
 4. New Technique Interpol – General Secretariat
4. New Technique Interpol – General Secretariat
 Interpol’s Databases and Services Child Pornography Images Cocaine Logos Counterfeit Currencies Criminal Names DNA Fingerprints Payment Cards Stolen Travel Documents Stolen Vehicles Stolen Works of Art Weapons and Explosives Command & Coordination Criminal Analysis Disaster Victim Identification Financial & High-tech Crime Fugitive Investigations Organized Crime & Drugs Public Safety & Terrorism Regional Support Trafficking in Human Beings
Interpol’s Databases and Services Child Pornography Images Cocaine Logos Counterfeit Currencies Criminal Names DNA Fingerprints Payment Cards Stolen Travel Documents Stolen Vehicles Stolen Works of Art Weapons and Explosives Command & Coordination Criminal Analysis Disaster Victim Identification Financial & High-tech Crime Fugitive Investigations Organized Crime & Drugs Public Safety & Terrorism Regional Support Trafficking in Human Beings
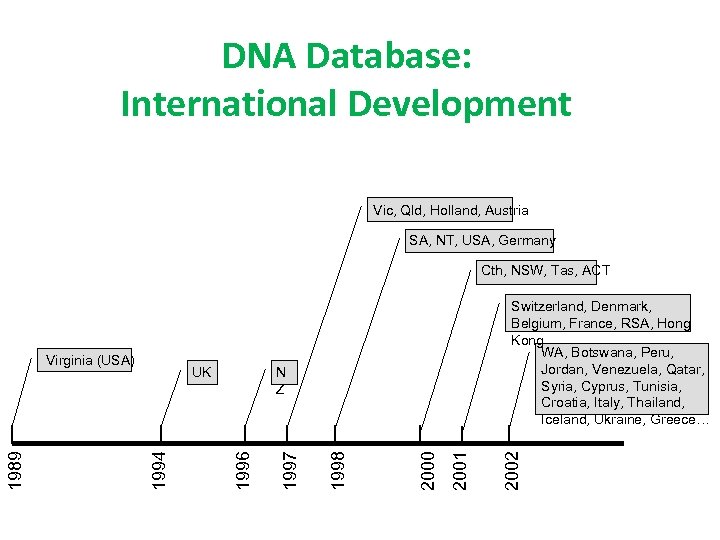 DNA Database: International Development Vic, Qld, Holland, Austria SA, NT, USA, Germany Cth, NSW, Tas, ACT 2002 2001 2000 1998 1997 N Z 1996 UK 1994 1989 Virginia (USA) Switzerland, Denmark, Belgium, France, RSA, Hong Kong WA, Botswana, Peru, Jordan, Venezuela, Qatar, Syria, Cyprus, Tunisia, Croatia, Italy, Thailand, Iceland, Ukraine, Greece…
DNA Database: International Development Vic, Qld, Holland, Austria SA, NT, USA, Germany Cth, NSW, Tas, ACT 2002 2001 2000 1998 1997 N Z 1996 UK 1994 1989 Virginia (USA) Switzerland, Denmark, Belgium, France, RSA, Hong Kong WA, Botswana, Peru, Jordan, Venezuela, Qatar, Syria, Cyprus, Tunisia, Croatia, Italy, Thailand, Iceland, Ukraine, Greece…
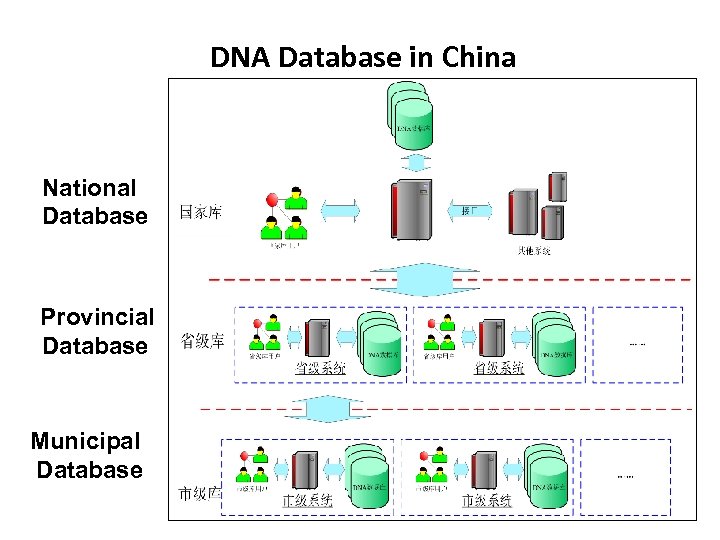 DNA Database in China National Database Provincial Database Municipal Database
DNA Database in China National Database Provincial Database Municipal Database
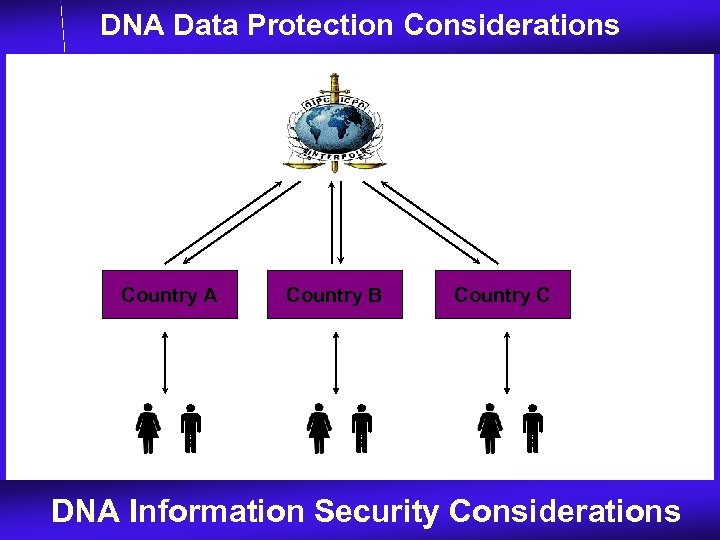 DNA Data Protection Considerations Country A Country B Country C DNA Information Security Considerations
DNA Data Protection Considerations Country A Country B Country C DNA Information Security Considerations
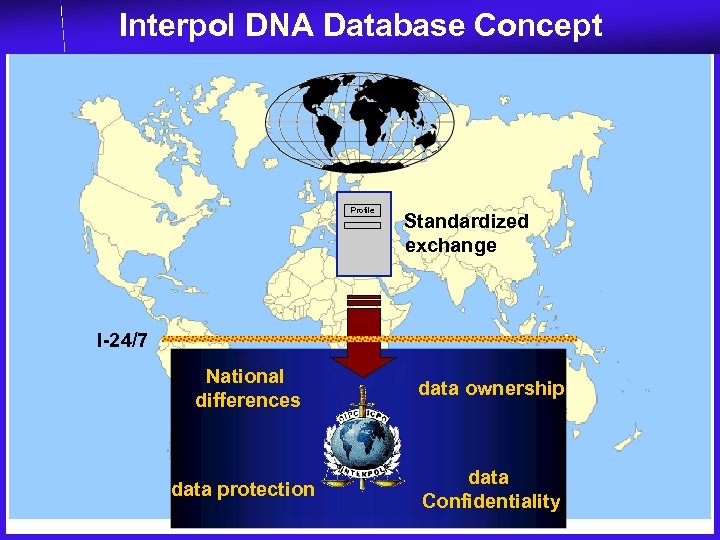 Interpol DNA Database Concept Profile Standardized exchange I-24/7 National differences data ownership data protection data Confidentiality
Interpol DNA Database Concept Profile Standardized exchange I-24/7 National differences data ownership data protection data Confidentiality
 China and Interpol China provides information to Interpol’s databases: Criminal Names and Investigations Stolen Travel Documents Stolen Motor Vehicles Stolen Works of Art Fingerprints DNA
China and Interpol China provides information to Interpol’s databases: Criminal Names and Investigations Stolen Travel Documents Stolen Motor Vehicles Stolen Works of Art Fingerprints DNA
 Miniaturisation: Rapid, Portable Analysis • Example: Agilent Technologies BA 2100 instrument – 12 -channel micro-CE device • Challenge: Is it able to type standard forensic DNA markers? • Obvious advantages: – Significantly reduced run times than current CE techniques • Potential screening technique for multiple-stain cases, decrease DNA backlogs – Potential for portability – DNA typing at the scene • Notable disadvantage: – Poor separation capacity at present
Miniaturisation: Rapid, Portable Analysis • Example: Agilent Technologies BA 2100 instrument – 12 -channel micro-CE device • Challenge: Is it able to type standard forensic DNA markers? • Obvious advantages: – Significantly reduced run times than current CE techniques • Potential screening technique for multiple-stain cases, decrease DNA backlogs – Potential for portability – DNA typing at the scene • Notable disadvantage: – Poor separation capacity at present
 SNP Technique Using HIris. Plex Tech to predict looks
SNP Technique Using HIris. Plex Tech to predict looks
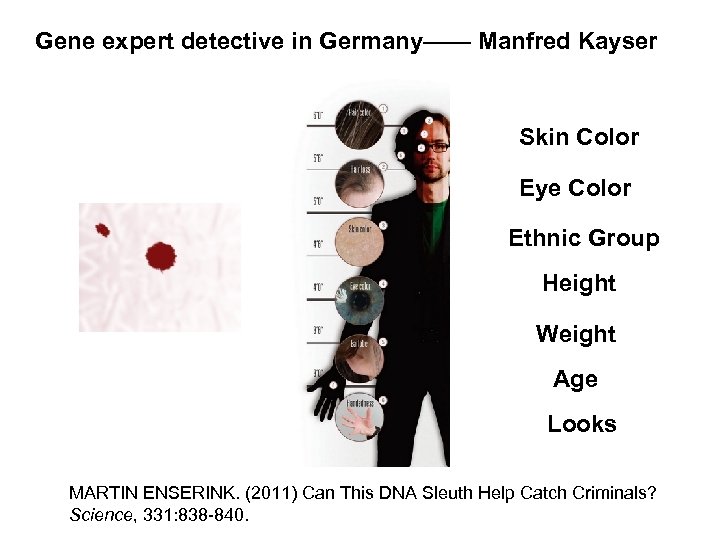 Gene expert detective in Germany—— Manfred Kayser Skin Color Eye Color Ethnic Group Height Weight Age Looks MARTIN ENSERINK. (2011) Can This DNA Sleuth Help Catch Criminals? Science, 331: 838 -840.
Gene expert detective in Germany—— Manfred Kayser Skin Color Eye Color Ethnic Group Height Weight Age Looks MARTIN ENSERINK. (2011) Can This DNA Sleuth Help Catch Criminals? Science, 331: 838 -840.
 Questions: 1. What is Individual Identification? 2. How to conduct Individual Identification?
Questions: 1. What is Individual Identification? 2. How to conduct Individual Identification?


