462e3b3d54111b4e932e33f3c7b5bcc6.ppt
- Количество слайдов: 35

Increasing IP Network Survivability: An Introduction to Protection Mechanisms 20 October 22, 2000 Jonathan Sadler Lead Engineer - ONG SE File Name

Motivation l There is increasing demand to carry mission critical traffic, real-time traffic, and other high priority traffic over the public internet l Any network that carries critical, high-priority traffic needs to be resilient to faults l As network technologies continue to improve and converge, protection and restoration schemes have become available at multiple layers File Name
Protection l What is it? l Automated mechanism for recovering traffic path l Invoked when the current working path fails l Requirements l Fast restoration time l Voice / video / data can tolerate small outages ( 50 ms) l Predictable l Protection path is pre-determined l Can be dedicated (1+1) or shared (M: N) l Can be preemptive File Name

Protection l How is protection different from dynamic rerouting? l Dynamic rerouting develops a new path utilizing current network state information l Delay incurred as state updates are flooded through network l Time to re-converge on new end-to-end path is long l Therefore time until destinations become re-reachable is long l Side Effect: State information will be received by nodes that are not involved in restoration causing unnecessary CPU usage l While best effort services may tolerate this behavior, new services will not l Vo. IP l Virtual leased line File Name
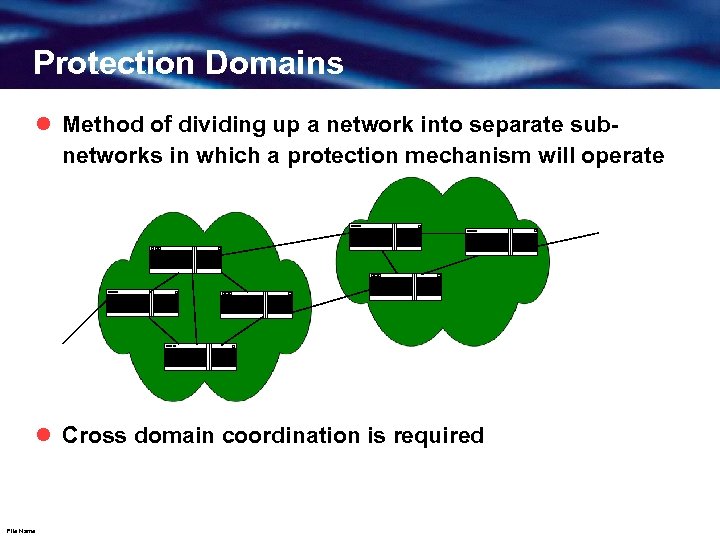
Protection Domains l Method of dividing up a network into separate subnetworks in which a protection mechanism will operate l Cross domain coordination is required File Name

Protection Topologies l Within a protection domain, a number of protection topologies may be used l Linear l Ring l Mesh l For any topology the following terminology applies: l Working: The path or span being used to carry live traffic l Protect: The path or span that will be used to recover live traffic File Name
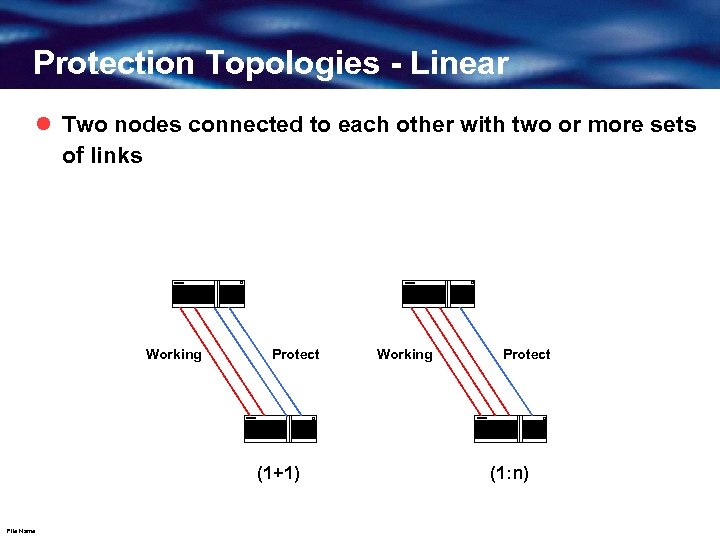
Protection Topologies - Linear l Two nodes connected to each other with two or more sets of links Working Protect (1+1) File Name Working Protect (1: n)
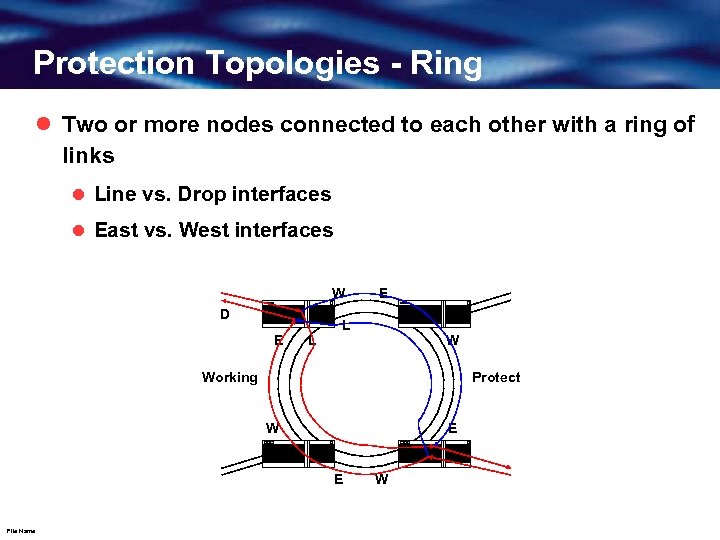
Protection Topologies - Ring l Two or more nodes connected to each other with a ring of links l Line vs. Drop interfaces l East vs. West interfaces W D E L W Working Protect W E E File Name W
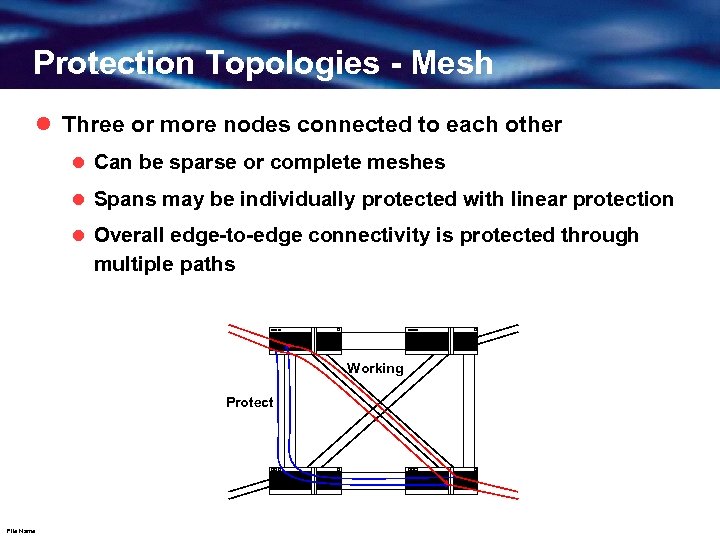
Protection Topologies - Mesh l Three or more nodes connected to each other l Can be sparse or complete meshes l Spans may be individually protected with linear protection l Overall edge-to-edge connectivity is protected through multiple paths Working Protect File Name
Protection Mechanisms l Protection mechanisms are the algorithms which will restore services carried by a specific network topology l Typically take advantage of topology characteristics l Two different approaches exist l Link oriented l Multiple links that support end-to-end connectivity can be individually switched to restore service l Path oriented l Two paths exist which can be “globally” switched to restore service File Name
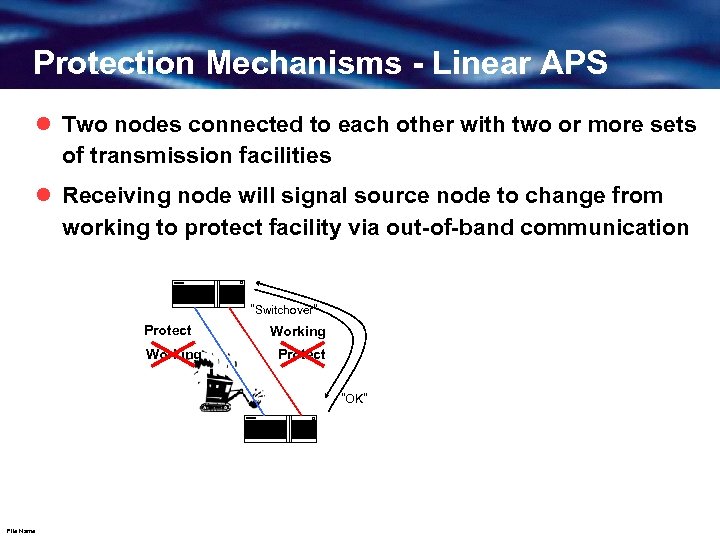
Protection Mechanisms - Linear APS l Two nodes connected to each other with two or more sets of transmission facilities l Receiving node will signal source node to change from working to protect facility via out-of-band communication “Switchover” Protect Working Protect “OK” File Name
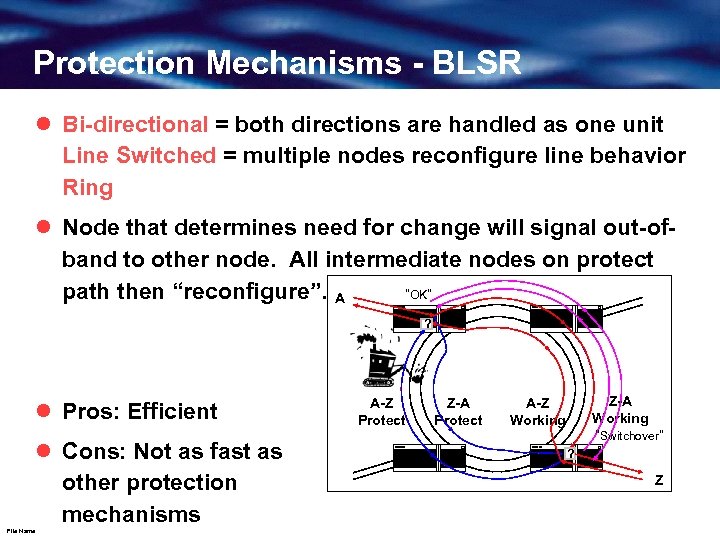
Protection Mechanisms - BLSR l Bi-directional = both directions are handled as one unit Line Switched = multiple nodes reconfigure line behavior Ring l Node that determines need for change will signal out-ofband to other node. All intermediate nodes on protect path then “reconfigure”. A “OK” ? l Pros: Efficient l Cons: Not as fast as other protection mechanisms File Name A-Z Working Protect Z-A Working Protect “Switchover” A-Z Working Protect ? Z
Protection Mechanisms - BLSR cont’d l How is this efficient? l Each node is involved in reconfiguring when a protection switch is necessary. Consequently, each node knows if the bandwidth reserved for a service is actually in use. l If a specific route is declared the “primary route” for the service, then the protect path will only be used when trying to restore a failure on the primary route. l As a result, it is possible to insert a second signal on the protect path. l When a protection switch is necessary to handle the higher priority traffic, then the “Extra Traffic” will be removed by the nodes as part of the switchover activity. File Name

Protection Mechanisms - BLSR cont’d l Why is more time needed for a protection switch? l Signaling latency l Traffic cross connect activation / deactivation in intermediate nodes l Definitely needed when Extra Traffic is in use File Name
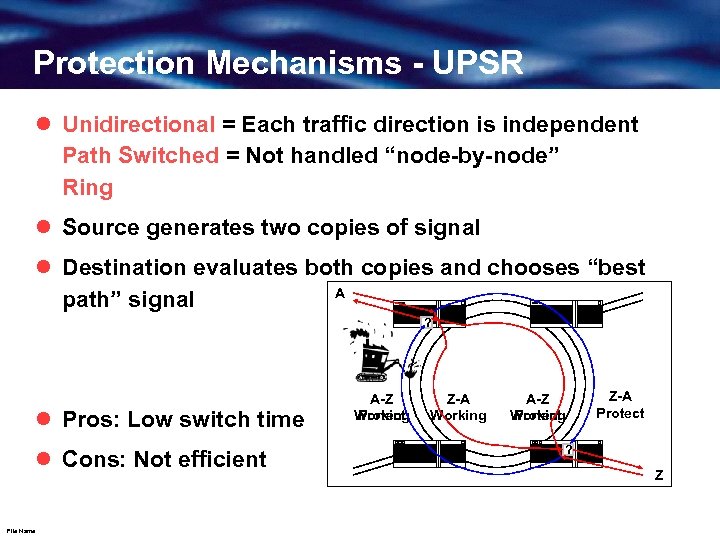
Protection Mechanisms - UPSR l Unidirectional = Each traffic direction is independent Path Switched = Not handled “node-by-node” Ring l Source generates two copies of signal l Destination evaluates both copies and chooses “best A path” signal ? l Pros: Low switch time l Cons: Not efficient File Name A-Z Working Protect Z-A Working A-Z Working Protect Z-A Protect ? Z
Protection Mechanisms - Mesh l End-to-End Path Oriented l Requires: l Topology Discovery l Constrained Route Selection (x 2) l Primary route l Protection route l Resource affinity (diversity) l Signaling Protocol l Service setup l Protection switchover l No standard solutions (yet) File Name
Protection Mech. - Revertive Switching l Once the failed path has been restored, should the traffic be moved back? l Non-revertive Switching l Done when failed path is no longer going to be used with service (i. e. service rolls) l Revertive Switching l Automatic System determines primary path is acceptable l Wait to Restore Time l l Manual Technician determines primary path is acceptable l Good in cases where the fault is experienced only under load l File Name

Protection Domain Consideration l What should be the scope of repair? l Global Repair l Traffic is restored using facilities within the global network l Local Repair l Traffic is restored using the minimum amount of facilities l Lacks network view, leading to potentially inefficient resource utilization File Name
Protection Hierarchy l Protection functionality is defined for: l Optical Layer l SONET l ATM / Frame Relay l MPLS / IP l How should all these layers interact? They shouldn’t File Name
Two Layer Recovery Model l Most providers are adopting a two-layer model, where: l Very-fast bulk restoration is done as close to the transport media as possible l Optical Switching l SONET where Optical Switching is not available l Service level restoration is done at the specific service layer l SONET -- VT 1. 5, STS-1, STS-3 c, STS-12 c, STS-48 c services l ATM / FR -- Switched Data Services l MPLS -- IP Services l Layers in between are not used for restoration l Service level restoration timers are set so that transport restoration can be attempted first File Name
Two Layer Recovery Model - Why? l Why have two layers instead of one? l Optical switching allows for the greatest number of services to be restored with the least amount of overhead l Optical switching will find out about physical failures first l Loss of light l Optical AIS l Optical protection domains are typically smaller than service -level protection domains, reducing signaling time l Service layers understand service specific performance requirements best, but may have a large number of services to restore File Name
Protection in SONET/SDH l Topologies / Mechanisms Available l 1+1 Linear APS l UPSR l BLSR l 2 -fiber l Restoration channels must be reserved, reducing protected capacity l 4 -fiber -- two sets of Tx/Rx fibers for each line interface Span Switch: Can restore by utilizing alternate Tx/Rx fibers l Ring Switch: Utilizes restoration channels located on a separate ring l l Extra Traffic possible l APS, BLSR signaling done in K 0 / K 1 bytes of overhead File Name
Protection in SONET/SDH (cont’d) l Failure Criteria l Loss of Signal (LOS) l Loss of Frame (LOF) l Threshold Crossing l Bit Error Rate (BER) l Coding Violations (CV) l Excessive SONET Pointer Justifications l Alarm Indication Signal (AIS) File Name

Applying Protection to MPLS l What does this do for me? l Provides fast restoration of MPLS services l Can be done on a service-by-service basis. For example: l Best effort could be biased to use Extra Traffic links l Bronze could be put on unprotected, but avoid Extra Traffic l Silver could be protected 1: n l Gold could be protected 1+1 File Name
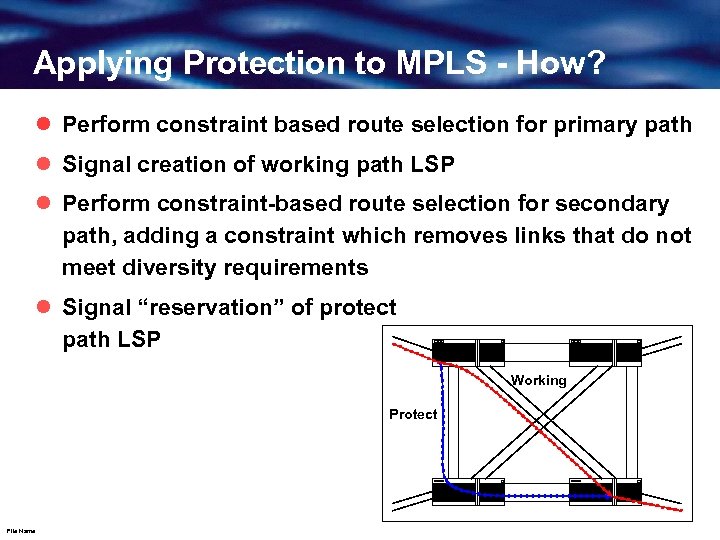
Applying Protection to MPLS - How? l Perform constraint based route selection for primary path l Signal creation of working path LSP l Perform constraint-based route selection for secondary path, adding a constraint which removes links that do not meet diversity requirements l Signal “reservation” of protect path LSP Working Protect File Name

Applying Protection to MPLS - How? l Extensions to IS-IS / OSPF l Utilizes the same Constraint Routing extensions as TE l New constraint: Shared Resource Link Group (SRLG) l Used for diversity determination l Extensions to CR-LDP / RSVP-TE l Add Protection LSP declaration to ERO l Add Reverse Notification Tree & Fault Notification Messages File Name
MPLS Protection - General Mesh Mech? l End-to-End Path Oriented l Requires: l Topology Discovery l Constrained Route Selection (x 2) l Primary route l Protection route l Resource affinity (diversity) l Signaling Protocol l Service setup l Protection switchover File Name OSPF w/ TE IS-IS w/ TE RSVP-TE CR-LDP
Benefits of a Generalized Control Plane l Extension of MPLS to non-IP technologies allows for: l Rapid provisioning of lower layer connections l Optical trails l SONET / SDH trails l Cut-through connections l Reduces traffic load on core routers l Extension of IP semantics (i. e. diff-serv) l Validates services that paid for protection are protected File Name
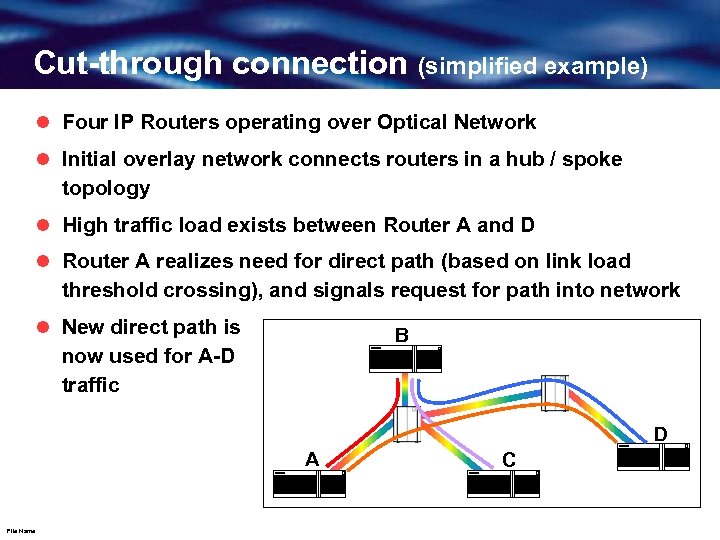
Cut-through connection (simplified example) l Four IP Routers operating over Optical Network l Initial overlay network connects routers in a hub / spoke topology l High traffic load exists between Router A and D l Router A realizes need for direct path (based on link load threshold crossing), and signals request for path into network l New direct path is now used for A-D traffic B D A File Name C

Summary l New services require mechanisms to recover working traffic as fast as possible l Optical Layer protection tools provide restoration with the least amount of overhead l Service Layer protection is also necessary l MPLS-TE with extensions can provide protection support for IP Networks l Can be extended to support any mesh network l Use of MPLS to integrate Optical and IP control planes allows IP service semantics to control protection mechanisms used at lower layers File Name
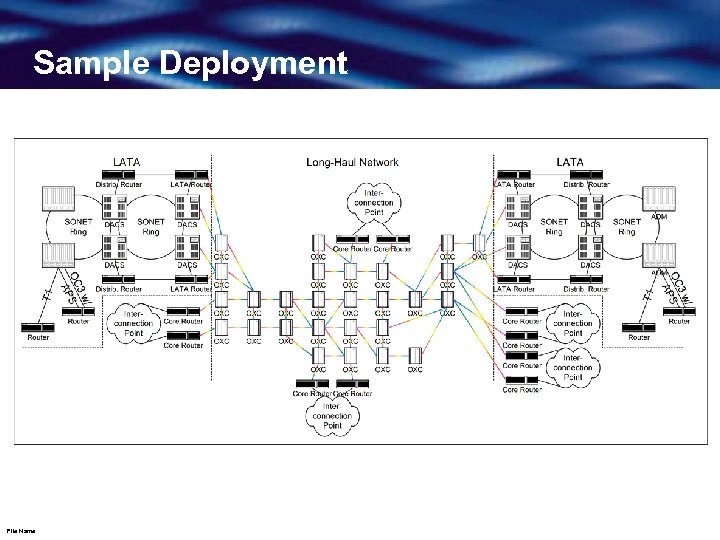
Sample Deployment File Name
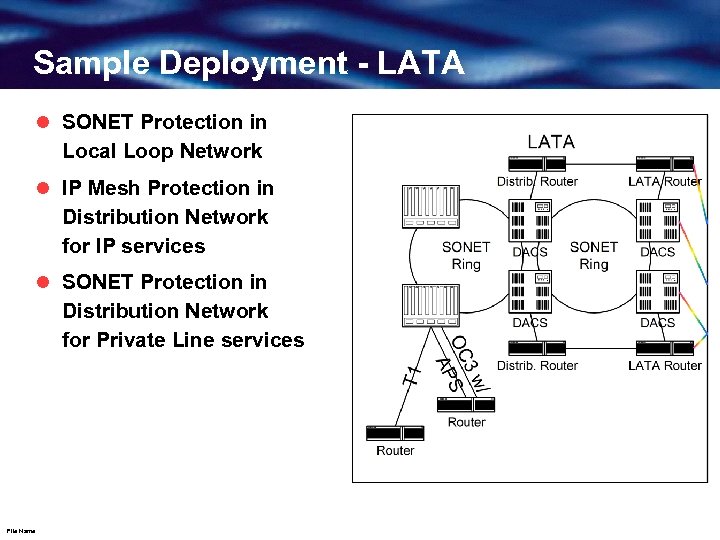
Sample Deployment - LATA l SONET Protection in Local Loop Network l IP Mesh Protection in Distribution Network for IP services l SONET Protection in Distribution Network for Private Line services File Name
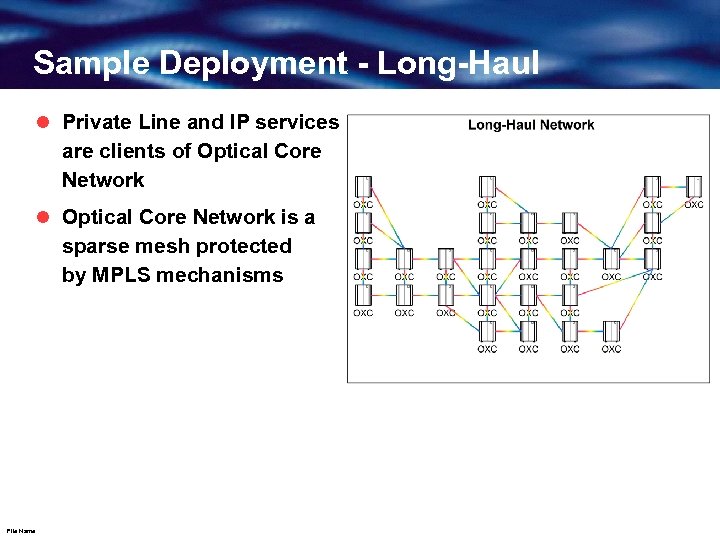
Sample Deployment - Long-Haul l Private Line and IP services are clients of Optical Core Network l Optical Core Network is a sparse mesh protected by MPLS mechanisms File Name
References l GR-253 -CORE, “Synchronous Optical NETwork (SONET) Transport Systems: Common Generic Criteria, ” Issue 2 rev 2, (Bellcore, January 1999) l GR-1230 -CORE, “SONET Bi-directional Line Switched Ring (BLSR) Equipment Generic Criteria, ” Issue 4, (Bellcore, December 1998) l GR-1400 -CORE, “SONET Dual-Fed Unidirectional Path Switched Ring (UPSR) Equipment Generic Criteria, ” Issue 2, (Bellcore, January 1999) l draft-owens-te-network-survivability-00. txt, “Network Survivability Considerations for Traffic Engineered IP Networks, ” (IETF, March 2000) l draft-ietf-mpls-recovery-frmwrk-00. txt, “Framework for MPLS-based Recovery, ” (IETF, September 2000) l draft-chang-mpls-path-protection-01. txt, “A Path Protection / Restoration Mechanism for MPLS Networks, ” (IETF, July 2000) l draft-chang-mpls-rsvpte-path-protection-ext-00. txt, “Extensions to RSVP-TE for MPLS Path Protection, ” (IETF, June 2000) File Name

File Name
462e3b3d54111b4e932e33f3c7b5bcc6.ppt