babe4f06054be905b1d0d0802f172a2b.ppt
- Количество слайдов: 46
 Incident Response
Incident Response
 Reading list Required: • Michael N. Schmitt, Computer Network Attack and the Use of Force in International Law. Thoughts on a Normative Framework. , 37 Colum. J. Transnat'l L. 885, 1999, http: //www. dtic. mil/cgi-bin/Get. TRDoc? AD=ADA 471993 Interesting: • Federal Communications Commission: Computer Security Incident Response Guide, 2001, http: //csrc. nist. gov/fasp/FASPDocs/incident-response/Incident. Response-Guide. pdf • Incident Response Team, R. Nellis, http: //www. rochissa. org/downloads/presentations/Incidence%20 R esponse%20 Teams. ppt • NIST special publications, http: //csrc. nist. gov/publications/nistpubs/index. html CSCE 727 - Farkas 2
Reading list Required: • Michael N. Schmitt, Computer Network Attack and the Use of Force in International Law. Thoughts on a Normative Framework. , 37 Colum. J. Transnat'l L. 885, 1999, http: //www. dtic. mil/cgi-bin/Get. TRDoc? AD=ADA 471993 Interesting: • Federal Communications Commission: Computer Security Incident Response Guide, 2001, http: //csrc. nist. gov/fasp/FASPDocs/incident-response/Incident. Response-Guide. pdf • Incident Response Team, R. Nellis, http: //www. rochissa. org/downloads/presentations/Incidence%20 R esponse%20 Teams. ppt • NIST special publications, http: //csrc. nist. gov/publications/nistpubs/index. html CSCE 727 - Farkas 2
 Due Care and Liability l Organizational liability for misuse – US Federal Sentencing Guidelines: chief executive officer and top management are responsible for fraud, theft, and antivirus violations committed by insiders or outsiders using the company’s resources. – Fines and penalties l l Base fine Culpability score (95%-400%) – Good faith efforts: written policies, procedures, security awareness program, disciplinary standards, monitoring and auditing, reporting, and cooperation with investigations CSCE 727 - Farkas 3
Due Care and Liability l Organizational liability for misuse – US Federal Sentencing Guidelines: chief executive officer and top management are responsible for fraud, theft, and antivirus violations committed by insiders or outsiders using the company’s resources. – Fines and penalties l l Base fine Culpability score (95%-400%) – Good faith efforts: written policies, procedures, security awareness program, disciplinary standards, monitoring and auditing, reporting, and cooperation with investigations CSCE 727 - Farkas 3
 How to Respond? CSCE 727 - Farkas 4
How to Respond? CSCE 727 - Farkas 4
 How to Respond? CSCE 727 - Farkas 5
How to Respond? CSCE 727 - Farkas 5
 How to Respond? CSCE 727 - Farkas 6
How to Respond? CSCE 727 - Farkas 6
 How to Response? l l l Actions to avoid further loss from intrusion Terminate intrusion and protect against reoccurrence Law enforcement – prosecute Enhance defensive security Reconstructive methods based on: – Time period of intrusion – Changes made by legitimate users during the effected period – Regular backups, audit trail based detection of effected components, semantic based recovery, minimal rollback for recovery. CSCE 727 - Farkas 7
How to Response? l l l Actions to avoid further loss from intrusion Terminate intrusion and protect against reoccurrence Law enforcement – prosecute Enhance defensive security Reconstructive methods based on: – Time period of intrusion – Changes made by legitimate users during the effected period – Regular backups, audit trail based detection of effected components, semantic based recovery, minimal rollback for recovery. CSCE 727 - Farkas 7
 Roles and Responsibilities l User: – Vigilant for unusual behavior – Report incidents l Manager: – Awareness training – Policies and procedures l System administration: – Install safeguards – Monitor system – Respond to incidents, including preservation of evidences CSCE 727 - Farkas 8
Roles and Responsibilities l User: – Vigilant for unusual behavior – Report incidents l Manager: – Awareness training – Policies and procedures l System administration: – Install safeguards – Monitor system – Respond to incidents, including preservation of evidences CSCE 727 - Farkas 8
 Computer Incident Response Team l Assist in handling security incidents – Formal – Informal Incident reporting and dissemination of incident information l Computer Security Officer l – Coordinate computer security efforts l Others: law enforcement coordinator, investigative support, media relations, etc. CSCE 727 - Farkas 9
Computer Incident Response Team l Assist in handling security incidents – Formal – Informal Incident reporting and dissemination of incident information l Computer Security Officer l – Coordinate computer security efforts l Others: law enforcement coordinator, investigative support, media relations, etc. CSCE 727 - Farkas 9
 Incident Response Process 1. Preparation – Baseline Protection – Planning and guidance – Roles and Responsibilities – Training – Incident response team CSCE 727 - Farkas 10
Incident Response Process 1. Preparation – Baseline Protection – Planning and guidance – Roles and Responsibilities – Training – Incident response team CSCE 727 - Farkas 10
 Incident Response Process 2. Identification and assessment – – Symptoms Nature of incident l l – Gather evidences l l – Identify perpetrator, origin and extent of attack Can be done during attack or after the attack Key stroke monitoring, honey nets, system logs, network traffic, etc. Legislations on Monitoring! Report on preliminary findings CSCE 727 - Farkas 11
Incident Response Process 2. Identification and assessment – – Symptoms Nature of incident l l – Gather evidences l l – Identify perpetrator, origin and extent of attack Can be done during attack or after the attack Key stroke monitoring, honey nets, system logs, network traffic, etc. Legislations on Monitoring! Report on preliminary findings CSCE 727 - Farkas 11
 Incident Response Process 3. Containment – Reduce the chance of spread of incident – Determine sensitive data – Terminate suspicious connections, personnel, applications, etc. – Move critical computing services – Handle human aspects, e. g. , perception management, panic, etc. CSCE 727 - Farkas 12
Incident Response Process 3. Containment – Reduce the chance of spread of incident – Determine sensitive data – Terminate suspicious connections, personnel, applications, etc. – Move critical computing services – Handle human aspects, e. g. , perception management, panic, etc. CSCE 727 - Farkas 12
 Incident Response Process 4. Eradication – – Determine and remove cause of incident if economically feasible Improve defenses, software, hardware, middleware, physical security, etc. Increase awareness and training Perform vulnerability analysis CSCE 727 - Farkas 13
Incident Response Process 4. Eradication – – Determine and remove cause of incident if economically feasible Improve defenses, software, hardware, middleware, physical security, etc. Increase awareness and training Perform vulnerability analysis CSCE 727 - Farkas 13
 Incident Response Process 5. Recovery – Determine course of action – Reestablish system functionality – Reporting and notifications – Documentation of incident handling and evidence preservation CSCE 727 - Farkas 14
Incident Response Process 5. Recovery – Determine course of action – Reestablish system functionality – Reporting and notifications – Documentation of incident handling and evidence preservation CSCE 727 - Farkas 14
 Follow Up Procedures l Incident evaluation: – Quality of incident (preparation, time to response, tools used, evaluation of response, etc. ) – Cost of incident (monetary cost, disruption, lost data, hardware damage, etc. ) l Preparing report l Revise policies and procedures CSCE 727 - Farkas 15
Follow Up Procedures l Incident evaluation: – Quality of incident (preparation, time to response, tools used, evaluation of response, etc. ) – Cost of incident (monetary cost, disruption, lost data, hardware damage, etc. ) l Preparing report l Revise policies and procedures CSCE 727 - Farkas 15
 What is “Survivability”? To decide whether a computer system is “survivable”, you must first decide what “survivable” means. CSCE 727 - Farkas 16
What is “Survivability”? To decide whether a computer system is “survivable”, you must first decide what “survivable” means. CSCE 727 - Farkas 16
 Vulnerable Components 1. Hardware 2. Software 3. Data 4. Communications 5. People CSCE 727 - Farkas 17
Vulnerable Components 1. Hardware 2. Software 3. Data 4. Communications 5. People CSCE 727 - Farkas 17
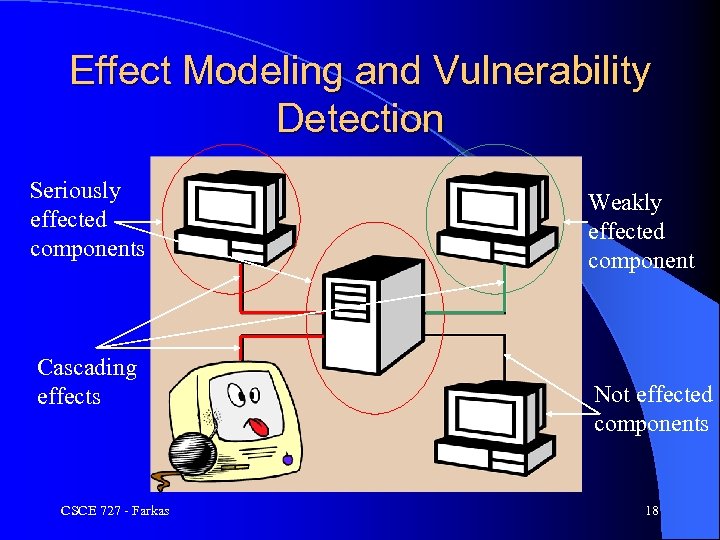 Effect Modeling and Vulnerability Detection Seriously effected components Cascading effects CSCE 727 - Farkas Weakly effected component Not effected components 18
Effect Modeling and Vulnerability Detection Seriously effected components Cascading effects CSCE 727 - Farkas Weakly effected component Not effected components 18
 Legal Aspects l l l National law International law Legal regime to apply Gray areas of law Legal response Evidence preservation CSCE 727 - Farkas 19
Legal Aspects l l l National law International law Legal regime to apply Gray areas of law Legal response Evidence preservation CSCE 727 - Farkas 19
 THEMIS: Threat Evaluation Metamodel for Information Systems Presented at the 2 nd Symposium on Intelligence and Security Informatics, 2004 Csilla Farkas, Thomas Wingfield, James B. Michael Duminda Wijesekera Themis, Goddess of Justice
THEMIS: Threat Evaluation Metamodel for Information Systems Presented at the 2 nd Symposium on Intelligence and Security Informatics, 2004 Csilla Farkas, Thomas Wingfield, James B. Michael Duminda Wijesekera Themis, Goddess of Justice
 Attacks Against Critical Infrastructures l l l Swedish hacker jammed 911 in central Florida in 1997 Juvenile hacker penetrated and disabled a telco computer servicing Worcester Airport in March 1997 Brisbane hacker used radio transmissions to create raw sewage overflows on Sunshine coast in 2000 Hackers broke into Gazprom’s system controlling gas flows in pipelines in 1999 Hackers got into California Independent Service Operator (ISO) development network for regional power grid in spring 2001 Numerous denial-of-service attacks against ISPs – some Source: D. Denning Information Warfare shut down CSCE 727 - Farkas 21
Attacks Against Critical Infrastructures l l l Swedish hacker jammed 911 in central Florida in 1997 Juvenile hacker penetrated and disabled a telco computer servicing Worcester Airport in March 1997 Brisbane hacker used radio transmissions to create raw sewage overflows on Sunshine coast in 2000 Hackers broke into Gazprom’s system controlling gas flows in pipelines in 1999 Hackers got into California Independent Service Operator (ISO) development network for regional power grid in spring 2001 Numerous denial-of-service attacks against ISPs – some Source: D. Denning Information Warfare shut down CSCE 727 - Farkas 21
 Rules Defining the Use of Force Schmitt Analysis Sources: Thomas Wingfield: The Law of Information Conflict: National Security Law in Cyberspace Michael N. Schmitt: Computer Network Attack and the Use of Force in International Law: Thoughts on a Normative Framework CSCE 727 - Farkas 22
Rules Defining the Use of Force Schmitt Analysis Sources: Thomas Wingfield: The Law of Information Conflict: National Security Law in Cyberspace Michael N. Schmitt: Computer Network Attack and the Use of Force in International Law: Thoughts on a Normative Framework CSCE 727 - Farkas 22
 CSCE 727 - Farkas 23
CSCE 727 - Farkas 23
 Spectrum of Conflict CSCE 727 - Farkas 24
Spectrum of Conflict CSCE 727 - Farkas 24
 Spectrum of Conflict CSCE 727 - Farkas 25
Spectrum of Conflict CSCE 727 - Farkas 25
 Spectrum of Conflict Art. 39 The Security Council shall determine the existence of any threat to the peace, breach of the peace, or act of aggression and shall make recommendations, or decide what measures shall be taken in accordance with Articles 41 and 42, to maintain or restore international peace and security. CSCE 727 - Farkas 26
Spectrum of Conflict Art. 39 The Security Council shall determine the existence of any threat to the peace, breach of the peace, or act of aggression and shall make recommendations, or decide what measures shall be taken in accordance with Articles 41 and 42, to maintain or restore international peace and security. CSCE 727 - Farkas 26
 Spectrum of Conflict Art. 2(4) All members shall refrain in their international relations from the threat or use of force against the territorial integrity or political independence of any state, or in any other manner inconsistent with the Purposes of the United Nations. CSCE 727 - Farkas 27
Spectrum of Conflict Art. 2(4) All members shall refrain in their international relations from the threat or use of force against the territorial integrity or political independence of any state, or in any other manner inconsistent with the Purposes of the United Nations. CSCE 727 - Farkas 27
 Spectrum of Conflict Art. 51 Nothing in the present Charter shall impair the inherent right of individual or collective self-defense if an armed attack occurs against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect the authority and responsibility of the Security Council under the present Charter to take at any time such action as it deems necessary in order to maintain or restore international peace and security. CSCE 727 - Farkas 28
Spectrum of Conflict Art. 51 Nothing in the present Charter shall impair the inherent right of individual or collective self-defense if an armed attack occurs against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect the authority and responsibility of the Security Council under the present Charter to take at any time such action as it deems necessary in order to maintain or restore international peace and security. CSCE 727 - Farkas 28
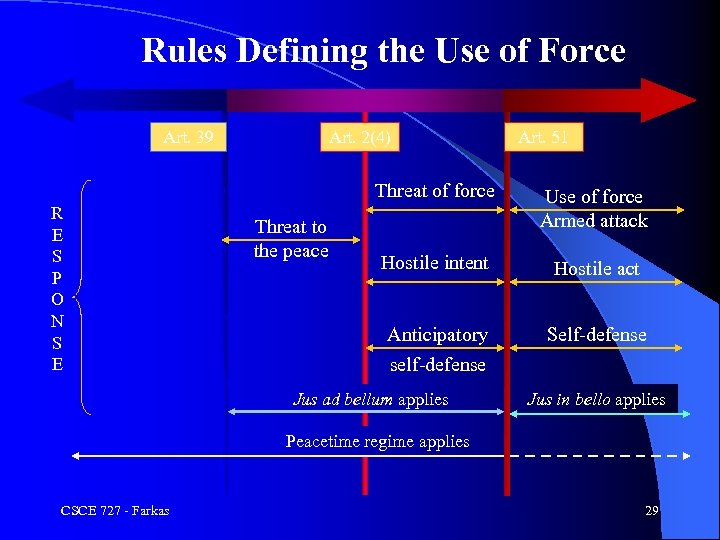 Rules Defining the Use of Force Art. 39 Art. 2(4) Art. 51 Threat of force R E S P O N S E Hostile intent Hostile act Anticipatory self-defense Threat to the peace Use of force Armed attack Self-defense Jus ad bellum applies Jus in bello applies Peacetime regime applies CSCE 727 - Farkas 29
Rules Defining the Use of Force Art. 39 Art. 2(4) Art. 51 Threat of force R E S P O N S E Hostile intent Hostile act Anticipatory self-defense Threat to the peace Use of force Armed attack Self-defense Jus ad bellum applies Jus in bello applies Peacetime regime applies CSCE 727 - Farkas 29
 Use of Force in Cyberspace Cyber vs. Kinetic Attack l Academic State-of-the-Art: Effects-Based Analysis l Problem: Charter Paradigm Means-Based l The Schmitt Reconciliation – Distinguishing Military from Diplomatic and Economic Coercion – Seven Factors l CSCE 727 - Farkas 30
Use of Force in Cyberspace Cyber vs. Kinetic Attack l Academic State-of-the-Art: Effects-Based Analysis l Problem: Charter Paradigm Means-Based l The Schmitt Reconciliation – Distinguishing Military from Diplomatic and Economic Coercion – Seven Factors l CSCE 727 - Farkas 30
 Schmitt Factors l Severity l Immediacy l Directness l Invasiveness l Measurability l Presumptive Legitimacy l Responsibility CSCE 727 - Farkas 31
Schmitt Factors l Severity l Immediacy l Directness l Invasiveness l Measurability l Presumptive Legitimacy l Responsibility CSCE 727 - Farkas 31
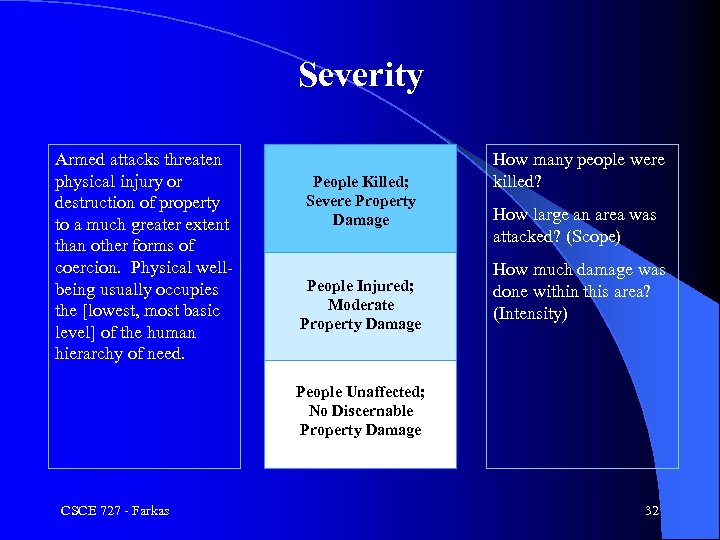 Severity Armed attacks threaten physical injury or destruction of property to a much greater extent than other forms of coercion. Physical wellbeing usually occupies the [lowest, most basic level] of the human hierarchy of need. People Killed; Severe Property Damage People Injured; Moderate Property Damage How many people were killed? How large an area was attacked? (Scope) How much damage was done within this area? (Intensity) People Unaffected; No Discernable Property Damage CSCE 727 - Farkas 32
Severity Armed attacks threaten physical injury or destruction of property to a much greater extent than other forms of coercion. Physical wellbeing usually occupies the [lowest, most basic level] of the human hierarchy of need. People Killed; Severe Property Damage People Injured; Moderate Property Damage How many people were killed? How large an area was attacked? (Scope) How much damage was done within this area? (Intensity) People Unaffected; No Discernable Property Damage CSCE 727 - Farkas 32
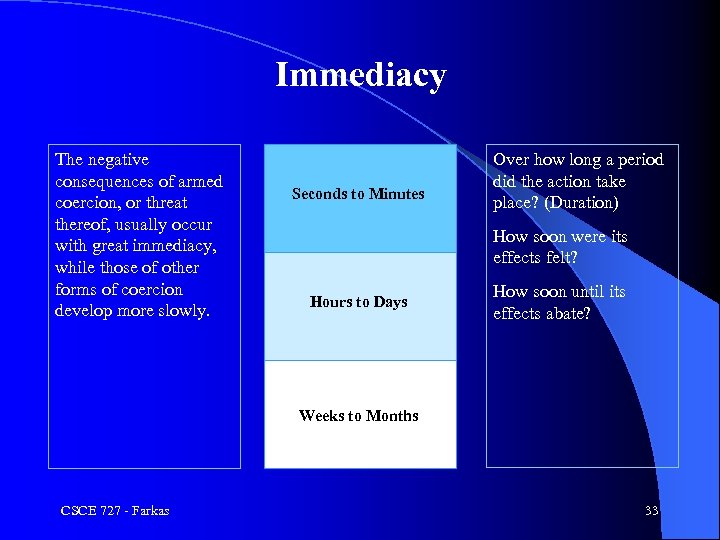 Immediacy The negative consequences of armed coercion, or threat thereof, usually occur with great immediacy, while those of other forms of coercion develop more slowly. People Seconds to. Killed; Minutes Severe Property Damage Over how long a period did the action take place? (Duration) How soon were its effects felt? Hours to Days How soon until its effects abate? Weeks to Months CSCE 727 - Farkas 33
Immediacy The negative consequences of armed coercion, or threat thereof, usually occur with great immediacy, while those of other forms of coercion develop more slowly. People Seconds to. Killed; Minutes Severe Property Damage Over how long a period did the action take place? (Duration) How soon were its effects felt? Hours to Days How soon until its effects abate? Weeks to Months CSCE 727 - Farkas 33
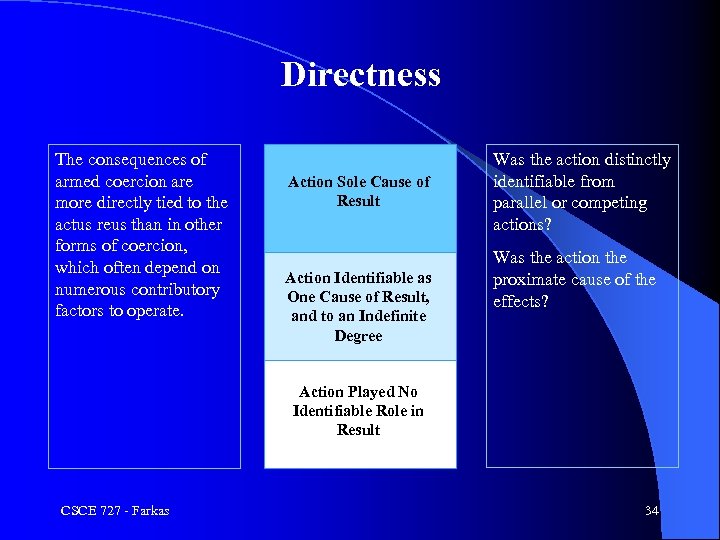 Directness The consequences of armed coercion are more directly tied to the actus reus than in other forms of coercion, which often depend on numerous contributory factors to operate. Action Sole. Killed; of People Cause Result Severe Property Damage Action Identifiable as One Cause of Result, and to an Indefinite Degree Was the action distinctly identifiable from parallel or competing actions? Was the action the proximate cause of the effects? Action Played No Identifiable Role in Result CSCE 727 - Farkas 34
Directness The consequences of armed coercion are more directly tied to the actus reus than in other forms of coercion, which often depend on numerous contributory factors to operate. Action Sole. Killed; of People Cause Result Severe Property Damage Action Identifiable as One Cause of Result, and to an Indefinite Degree Was the action distinctly identifiable from parallel or competing actions? Was the action the proximate cause of the effects? Action Played No Identifiable Role in Result CSCE 727 - Farkas 34
 Invasiveness In armed coercion, the act causing the harm usually crosses into the target state, whereas in economic warfare the acts generally occur beyond the target’s borders. As a result, even though armed and economic acts may have roughly similar consequences, the former represents a greater intrusion on the rights of the target state and, therefore, is more likely to disrupt international stability. CSCE 727 - Farkas Border Physically People Killed; Crossed; Action Has Severe Property Damage Point Locus Border Electronically Crossed; Action Occurs Over Diffuse Area Did the action involve physically crossing the target country’s borders? Was the locus of the action within the target country? Border Not Crossed; Action Has No Identifiable Locus in Target Country 35
Invasiveness In armed coercion, the act causing the harm usually crosses into the target state, whereas in economic warfare the acts generally occur beyond the target’s borders. As a result, even though armed and economic acts may have roughly similar consequences, the former represents a greater intrusion on the rights of the target state and, therefore, is more likely to disrupt international stability. CSCE 727 - Farkas Border Physically People Killed; Crossed; Action Has Severe Property Damage Point Locus Border Electronically Crossed; Action Occurs Over Diffuse Area Did the action involve physically crossing the target country’s borders? Was the locus of the action within the target country? Border Not Crossed; Action Has No Identifiable Locus in Target Country 35
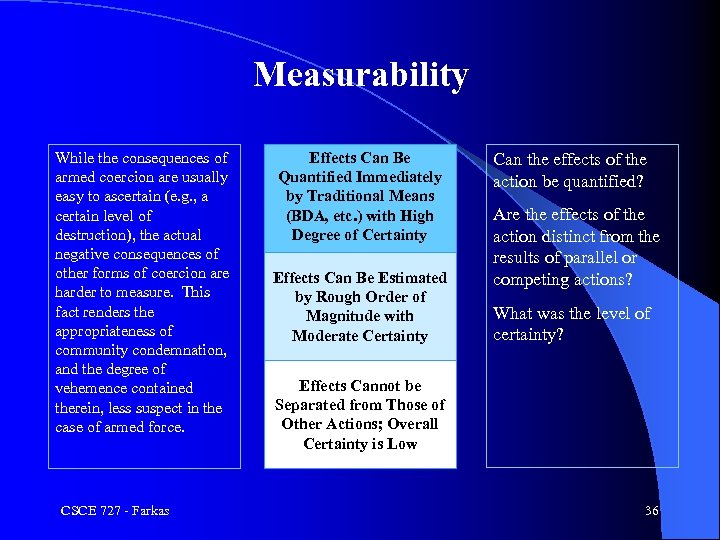 Measurability While the consequences of armed coercion are usually easy to ascertain (e. g. , a certain level of destruction), the actual negative consequences of other forms of coercion are harder to measure. This fact renders the appropriateness of community condemnation, and the degree of vehemence contained therein, less suspect in the case of armed force. CSCE 727 - Farkas Effects Can Be Quantified Immediately People Killed; by Traditional Damage Severe Property Means (BDA, etc. ) with High Degree of Certainty Effects Can Be Estimated by Rough Order of Magnitude with Moderate Certainty Can the effects of the action be quantified? Are the effects of the action distinct from the results of parallel or competing actions? What was the level of certainty? Effects Cannot be Separated from Those of Other Actions; Overall Certainty is Low 36
Measurability While the consequences of armed coercion are usually easy to ascertain (e. g. , a certain level of destruction), the actual negative consequences of other forms of coercion are harder to measure. This fact renders the appropriateness of community condemnation, and the degree of vehemence contained therein, less suspect in the case of armed force. CSCE 727 - Farkas Effects Can Be Quantified Immediately People Killed; by Traditional Damage Severe Property Means (BDA, etc. ) with High Degree of Certainty Effects Can Be Estimated by Rough Order of Magnitude with Moderate Certainty Can the effects of the action be quantified? Are the effects of the action distinct from the results of parallel or competing actions? What was the level of certainty? Effects Cannot be Separated from Those of Other Actions; Overall Certainty is Low 36
 Presumptive Legitimacy In most cases, whether under domestic or international law, the application of violence is deemed illegitimate absent some specific exception such as self-defense. The cognitive approach is prohibitory. By contrast, most other forms of coercion—again in the domestic and international sphere—are presumptively lawful, absent a prohibition to the contrary. The cognitive approach is permissive. CSCE 727 - Farkas Action Accomplished by People Killed; Means of Kinetic Attack Severe Property Damage Action Accomplished in Cyberspace but Manifested by a “Smoking Hole” in Physical Space Has this type of action achieved a customary acceptance within the international community? Is the means qualitatively similar to others presumed legitimate under international law? Action Accomplished in Cyberspace and Effects Not Apparent in Physical World 37
Presumptive Legitimacy In most cases, whether under domestic or international law, the application of violence is deemed illegitimate absent some specific exception such as self-defense. The cognitive approach is prohibitory. By contrast, most other forms of coercion—again in the domestic and international sphere—are presumptively lawful, absent a prohibition to the contrary. The cognitive approach is permissive. CSCE 727 - Farkas Action Accomplished by People Killed; Means of Kinetic Attack Severe Property Damage Action Accomplished in Cyberspace but Manifested by a “Smoking Hole” in Physical Space Has this type of action achieved a customary acceptance within the international community? Is the means qualitatively similar to others presumed legitimate under international law? Action Accomplished in Cyberspace and Effects Not Apparent in Physical World 37
 Responsibility Armed coercion is the exclusive province of states; only they may generally engage in uses of force across borders, and in most cases only they have the ability to do so with any meaningful impact. By contrast, non-governmental entities are often capable of engaging in other forms of coercion (propaganda, boycotts, etc. ). CSCE 727 - Farkas Responsibility for People Killed; Action Acknowledged Severe Property Degree by Acting State; Damage of Involvement Large Target State Government Aware of Acting State’s Responsibility; Public Role Unacknowledged; Degree of Involvement Moderate Is the action directly or indirectly attributable to the acting state? But for the acting state’s sake, would the action have occurred? Action Unattributable to Acting State; Degree of Involvement Low 38
Responsibility Armed coercion is the exclusive province of states; only they may generally engage in uses of force across borders, and in most cases only they have the ability to do so with any meaningful impact. By contrast, non-governmental entities are often capable of engaging in other forms of coercion (propaganda, boycotts, etc. ). CSCE 727 - Farkas Responsibility for People Killed; Action Acknowledged Severe Property Degree by Acting State; Damage of Involvement Large Target State Government Aware of Acting State’s Responsibility; Public Role Unacknowledged; Degree of Involvement Moderate Is the action directly or indirectly attributable to the acting state? But for the acting state’s sake, would the action have occurred? Action Unattributable to Acting State; Degree of Involvement Low 38
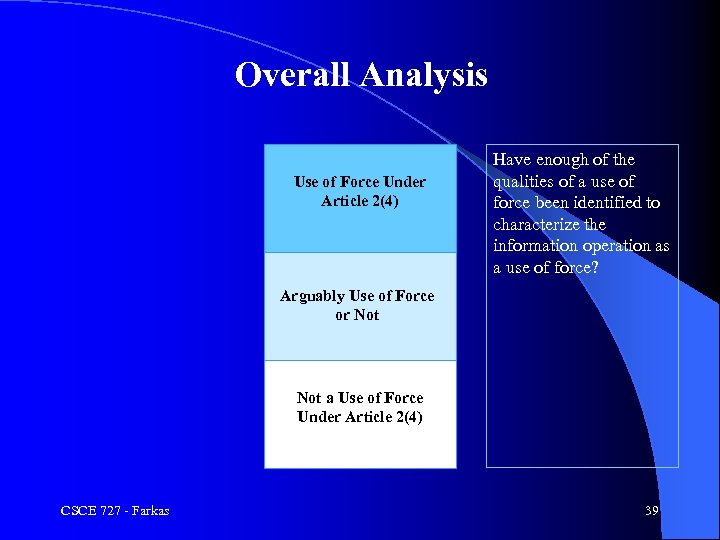 Overall Analysis Use People Killed; of Force Under Article 2(4) Severe Property Damage Have enough of the qualities of a use of force been identified to characterize the information operation as a use of force? Arguably Use of Force or Not a Use of Force Under Article 2(4) CSCE 727 - Farkas 39
Overall Analysis Use People Killed; of Force Under Article 2(4) Severe Property Damage Have enough of the qualities of a use of force been identified to characterize the information operation as a use of force? Arguably Use of Force or Not a Use of Force Under Article 2(4) CSCE 727 - Farkas 39
 THEMIS Threat Evaluation Metamodel for Information Systems CSCE 727 - Farkas 40
THEMIS Threat Evaluation Metamodel for Information Systems CSCE 727 - Farkas 40
 THEMIS l Attack Response Policy (ARP) language – ARP alphabet and predicates to represent attacks, consequences, and legal concepts l Interoperable legal ontologies l Attack evaluation and response rules l SWRL - A Semantic Web Rule Language combining OWL and Rule. ML CSCE 727 - Farkas 41
THEMIS l Attack Response Policy (ARP) language – ARP alphabet and predicates to represent attacks, consequences, and legal concepts l Interoperable legal ontologies l Attack evaluation and response rules l SWRL - A Semantic Web Rule Language combining OWL and Rule. ML CSCE 727 - Farkas 41
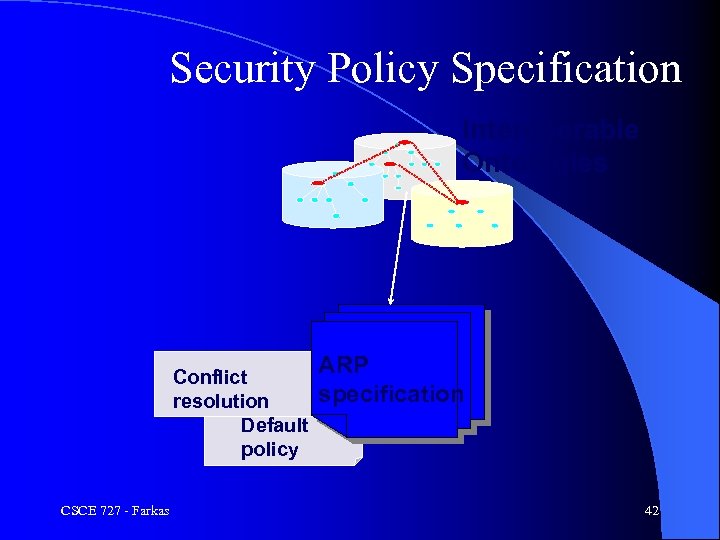 Security Policy Specification Interoperable Ontologies Conflict resolution Default policy CSCE 727 - Farkas ARP specification 42
Security Policy Specification Interoperable Ontologies Conflict resolution Default policy CSCE 727 - Farkas ARP specification 42
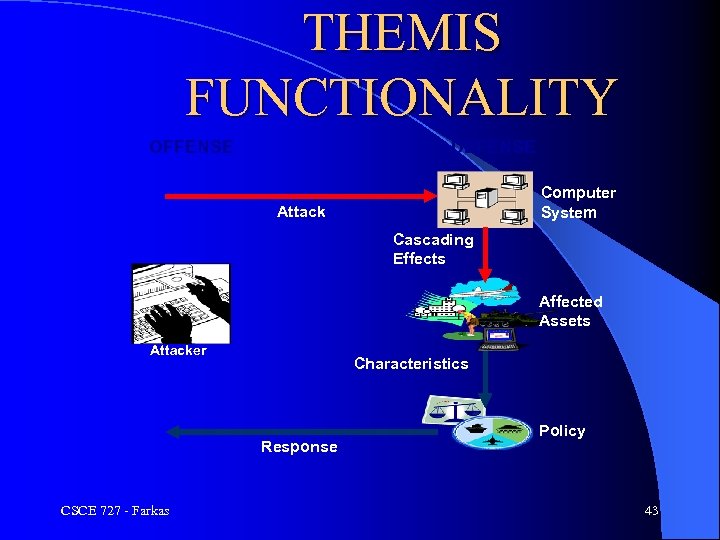 THEMIS FUNCTIONALITY OFFENSE DEFENSE Computer System Attack Cascading Effects Affected Assets Attacker Characteristics Response CSCE 727 - Farkas Policy 43
THEMIS FUNCTIONALITY OFFENSE DEFENSE Computer System Attack Cascading Effects Affected Assets Attacker Characteristics Response CSCE 727 - Farkas Policy 43
 Attack Response Policy (ARP) l ARP alphabet: constant symbols, variables, functions, and terms l ARP predicates: used to build rules l ARP rules: reason about the damages, express legal restrictions, and determine legitimacy of counter actions CSCE 727 - Farkas 44
Attack Response Policy (ARP) l ARP alphabet: constant symbols, variables, functions, and terms l ARP predicates: used to build rules l ARP rules: reason about the damages, express legal restrictions, and determine legitimacy of counter actions CSCE 727 - Farkas 44
 Example Predicates: – attack(a-id, a-name, orig, targ) – consequence(a-id, c-type, targ) – causes(c-type 1, targ 1, c-type 2, targ 2) l Rule: – attack(a-id, a-name, orig, targ 1) attack(a-id, a-name, orig, targ) consequence(a-id, c-type, targ) causes(c-type, targ, c-type 1, targ 1) l CSCE 727 - Farkas 45
Example Predicates: – attack(a-id, a-name, orig, targ) – consequence(a-id, c-type, targ) – causes(c-type 1, targ 1, c-type 2, targ 2) l Rule: – attack(a-id, a-name, orig, targ 1) attack(a-id, a-name, orig, targ) consequence(a-id, c-type, targ) causes(c-type, targ, c-type 1, targ 1) l CSCE 727 - Farkas 45
 Conclusions l Automated decision support system l Attack Response Policy Language – Alphabet – Predicates – Rules l Schmitt CSCE 727 - Farkas Analysis 46
Conclusions l Automated decision support system l Attack Response Policy Language – Alphabet – Predicates – Rules l Schmitt CSCE 727 - Farkas Analysis 46


