018b2a893447a67555db904495c79c01.ppt
- Количество слайдов: 89
 In the Name of the Most High Networking Review By Behzad Akbari Spring 2011 These power point slides have been adapted from slides prepared by Prof. Jim Kurose (U Mass) 1
In the Name of the Most High Networking Review By Behzad Akbari Spring 2011 These power point slides have been adapted from slides prepared by Prof. Jim Kurose (U Mass) 1
 Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control v equalize backgrounds q flow control v identify remedial work q congestion control v ease into course q routing q LANs q addressing 2
Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control v equalize backgrounds q flow control v identify remedial work q congestion control v ease into course q routing q LANs q addressing 2
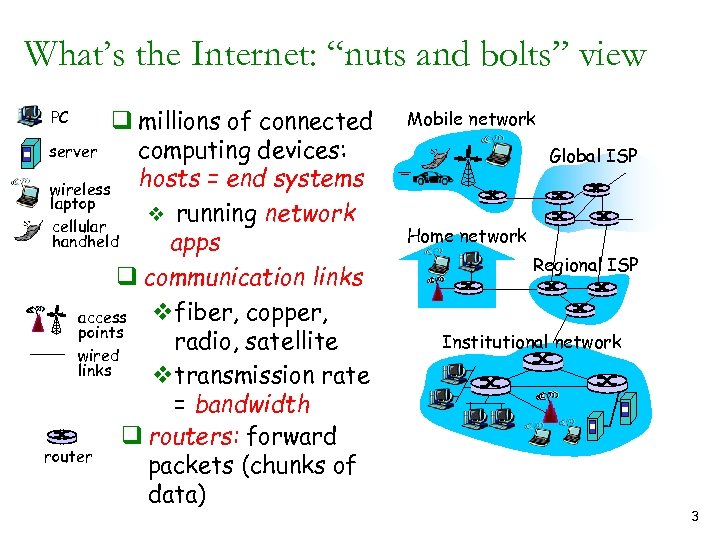 What’s the Internet: “nuts and bolts” view q millions of connected server computing devices: hosts = end systems wireless laptop v running network cellular handheld apps q communication links vfiber, copper, access points radio, satellite wired links vtransmission rate = bandwidth q routers: forward router packets (chunks of data) PC Mobile network Global ISP Home network Regional ISP Institutional network 3
What’s the Internet: “nuts and bolts” view q millions of connected server computing devices: hosts = end systems wireless laptop v running network cellular handheld apps q communication links vfiber, copper, access points radio, satellite wired links vtransmission rate = bandwidth q routers: forward router packets (chunks of data) PC Mobile network Global ISP Home network Regional ISP Institutional network 3
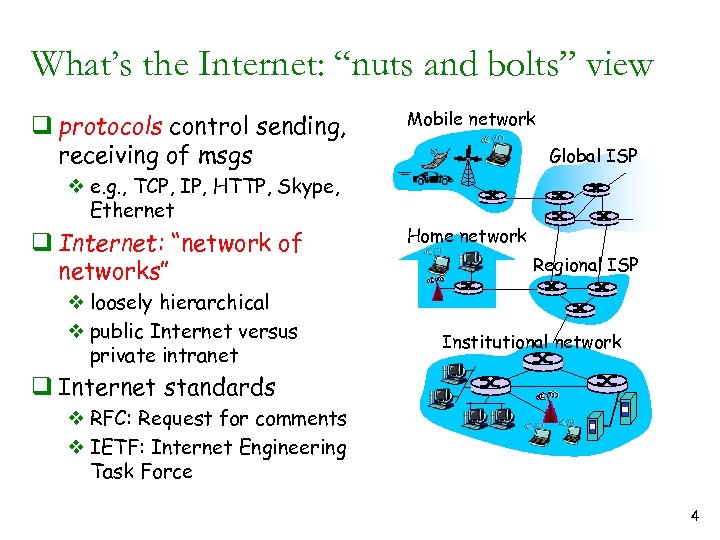 What’s the Internet: “nuts and bolts” view q protocols control sending, receiving of msgs v e. g. , TCP, IP, HTTP, Skype, Ethernet q Internet: “network of networks” v loosely hierarchical v public Internet versus private intranet Mobile network Global ISP Home network Regional ISP Institutional network q Internet standards v RFC: Request for comments v IETF: Internet Engineering Task Force 4
What’s the Internet: “nuts and bolts” view q protocols control sending, receiving of msgs v e. g. , TCP, IP, HTTP, Skype, Ethernet q Internet: “network of networks” v loosely hierarchical v public Internet versus private intranet Mobile network Global ISP Home network Regional ISP Institutional network q Internet standards v RFC: Request for comments v IETF: Internet Engineering Task Force 4
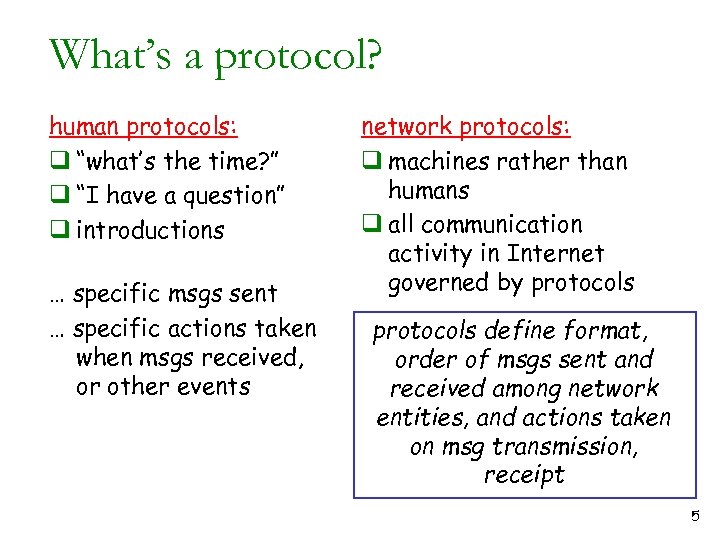 What’s a protocol? human protocols: q “what’s the time? ” q “I have a question” q introductions … specific msgs sent … specific actions taken when msgs received, or other events network protocols: q machines rather than humans q all communication activity in Internet governed by protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt 5
What’s a protocol? human protocols: q “what’s the time? ” q “I have a question” q introductions … specific msgs sent … specific actions taken when msgs received, or other events network protocols: q machines rather than humans q all communication activity in Internet governed by protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt 5
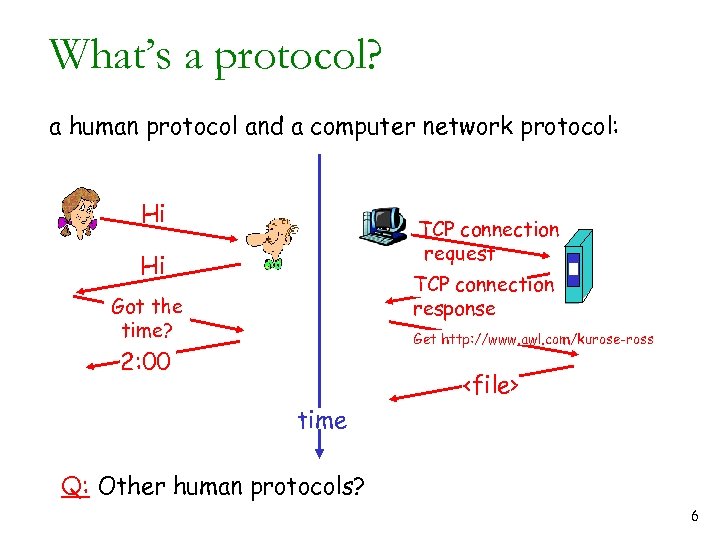 What’s a protocol? a human protocol and a computer network protocol: Hi TCP connection request Hi TCP connection response Got the time? Get http: //www. awl. com/kurose-ross 2: 00
What’s a protocol? a human protocol and a computer network protocol: Hi TCP connection request Hi TCP connection response Got the time? Get http: //www. awl. com/kurose-ross 2: 00
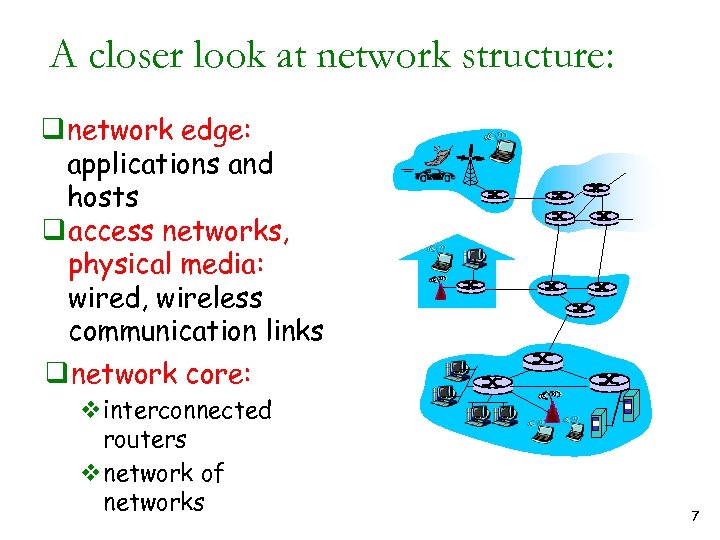 A closer look at network structure: q network edge: applications and hosts q access networks, physical media: wired, wireless communication links q network core: vinterconnected routers vnetwork of networks 7
A closer look at network structure: q network edge: applications and hosts q access networks, physical media: wired, wireless communication links q network core: vinterconnected routers vnetwork of networks 7
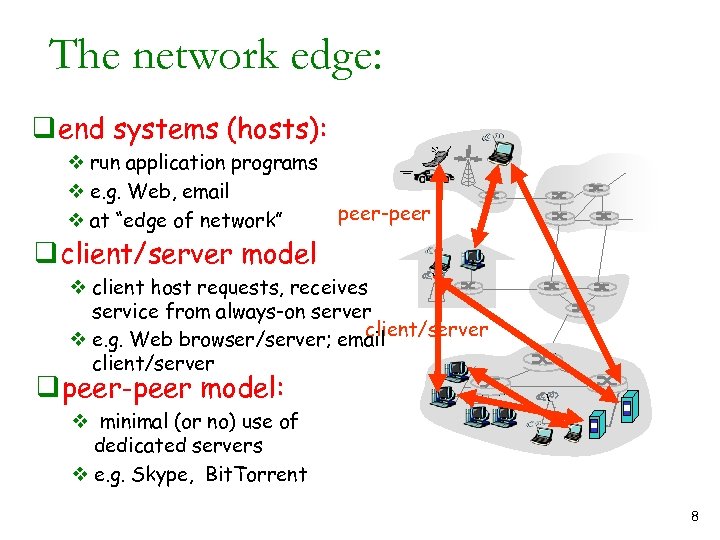 The network edge: q end systems (hosts): v run application programs v e. g. Web, email v at “edge of network” peer-peer q client/server model v client host requests, receives service from always-on server client/server v e. g. Web browser/server; email client/server q peer-peer model: v minimal (or no) use of dedicated servers v e. g. Skype, Bit. Torrent 8
The network edge: q end systems (hosts): v run application programs v e. g. Web, email v at “edge of network” peer-peer q client/server model v client host requests, receives service from always-on server client/server v e. g. Web browser/server; email client/server q peer-peer model: v minimal (or no) use of dedicated servers v e. g. Skype, Bit. Torrent 8
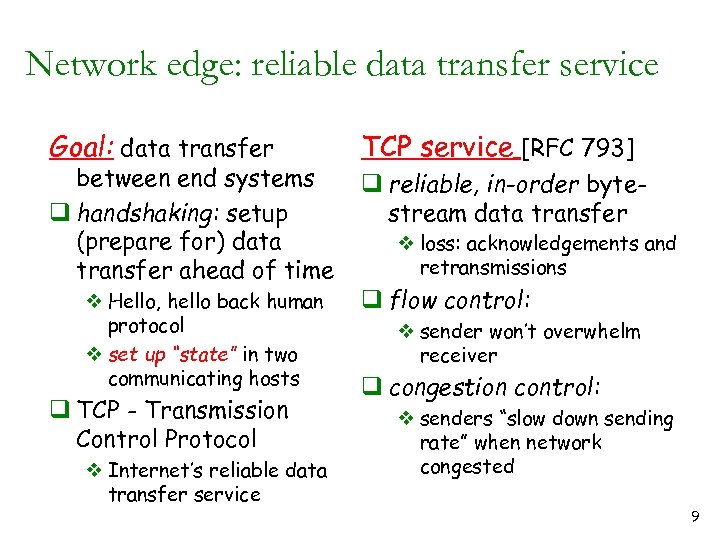 Network edge: reliable data transfer service Goal: data transfer between end systems q handshaking: setup (prepare for) data transfer ahead of time v Hello, hello back human protocol v set up “state” in two communicating hosts q TCP - Transmission Control Protocol v Internet’s reliable data transfer service TCP service [RFC 793] q reliable, in-order bytestream data transfer v loss: acknowledgements and retransmissions q flow control: v sender won’t overwhelm receiver q congestion control: v senders “slow down sending rate” when network congested 9
Network edge: reliable data transfer service Goal: data transfer between end systems q handshaking: setup (prepare for) data transfer ahead of time v Hello, hello back human protocol v set up “state” in two communicating hosts q TCP - Transmission Control Protocol v Internet’s reliable data transfer service TCP service [RFC 793] q reliable, in-order bytestream data transfer v loss: acknowledgements and retransmissions q flow control: v sender won’t overwhelm receiver q congestion control: v senders “slow down sending rate” when network congested 9
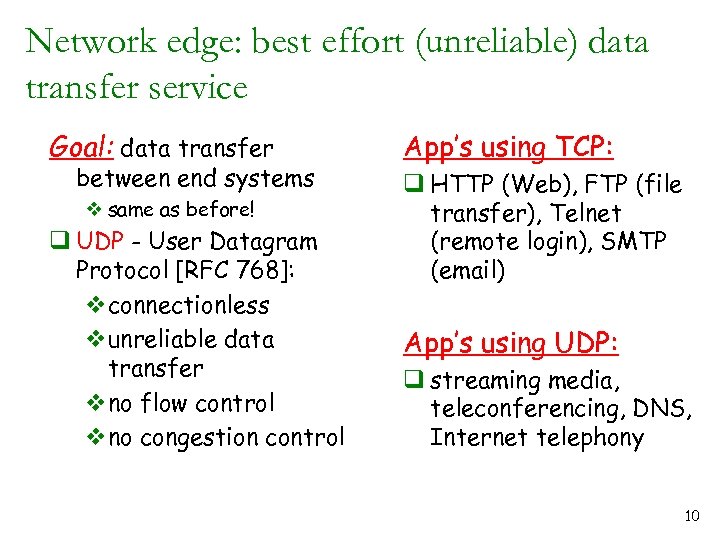 Network edge: best effort (unreliable) data transfer service Goal: data transfer between end systems v same as before! q UDP - User Datagram Protocol [RFC 768]: vconnectionless vunreliable data transfer vno flow control vno congestion control App’s using TCP: q HTTP (Web), FTP (file transfer), Telnet (remote login), SMTP (email) App’s using UDP: q streaming media, teleconferencing, DNS, Internet telephony 10
Network edge: best effort (unreliable) data transfer service Goal: data transfer between end systems v same as before! q UDP - User Datagram Protocol [RFC 768]: vconnectionless vunreliable data transfer vno flow control vno congestion control App’s using TCP: q HTTP (Web), FTP (file transfer), Telnet (remote login), SMTP (email) App’s using UDP: q streaming media, teleconferencing, DNS, Internet telephony 10
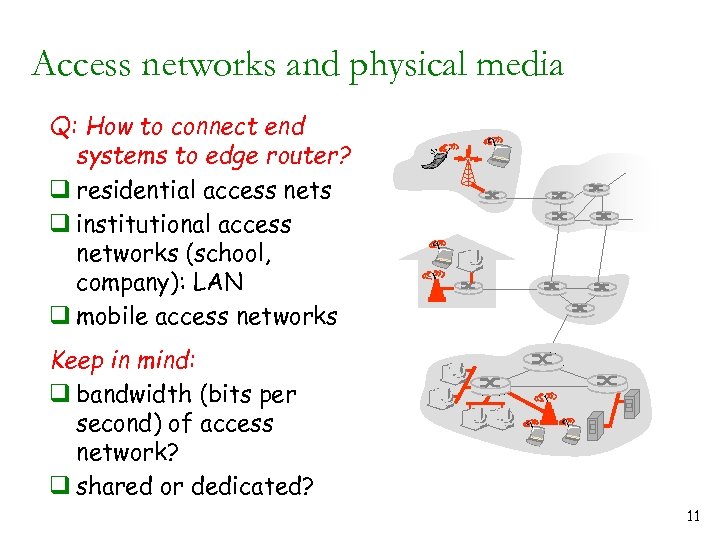 Access networks and physical media Q: How to connect end systems to edge router? q residential access nets q institutional access networks (school, company): LAN q mobile access networks Keep in mind: q bandwidth (bits per second) of access network? q shared or dedicated? 11
Access networks and physical media Q: How to connect end systems to edge router? q residential access nets q institutional access networks (school, company): LAN q mobile access networks Keep in mind: q bandwidth (bits per second) of access network? q shared or dedicated? 11
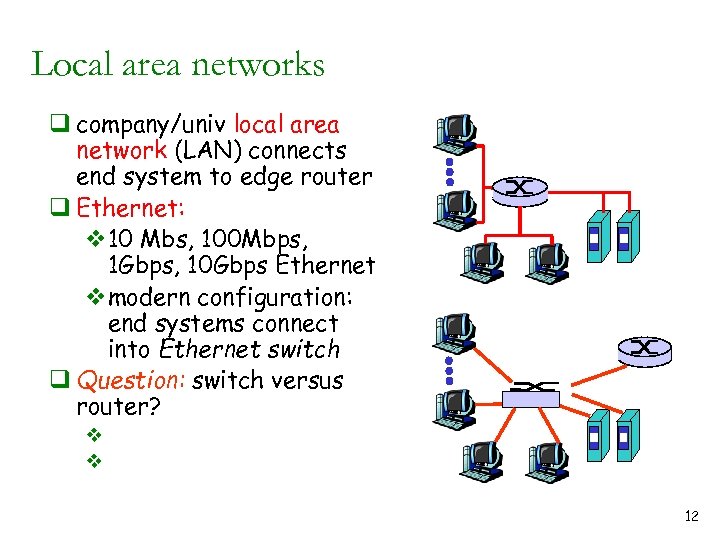 Local area networks q company/univ local area network (LAN) connects end system to edge router q Ethernet: v 10 Mbs, 100 Mbps, 1 Gbps, 10 Gbps Ethernet vmodern configuration: end systems connect into Ethernet switch q Question: switch versus router? v v 12
Local area networks q company/univ local area network (LAN) connects end system to edge router q Ethernet: v 10 Mbs, 100 Mbps, 1 Gbps, 10 Gbps Ethernet vmodern configuration: end systems connect into Ethernet switch q Question: switch versus router? v v 12
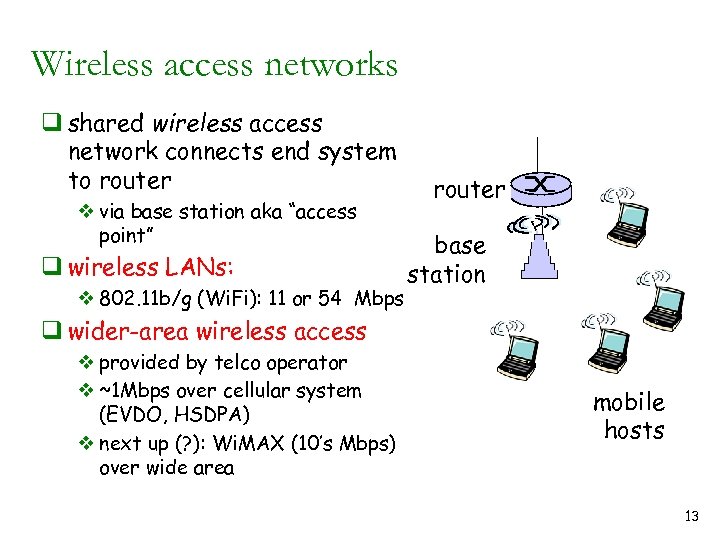 Wireless access networks q shared wireless access network connects end system to router v via base station aka “access point” q wireless LANs: v 802. 11 b/g (Wi. Fi): 11 or 54 Mbps router base station q wider-area wireless access v provided by telco operator v ~1 Mbps over cellular system (EVDO, HSDPA) v next up (? ): Wi. MAX (10’s Mbps) over wide area mobile hosts 13
Wireless access networks q shared wireless access network connects end system to router v via base station aka “access point” q wireless LANs: v 802. 11 b/g (Wi. Fi): 11 or 54 Mbps router base station q wider-area wireless access v provided by telco operator v ~1 Mbps over cellular system (EVDO, HSDPA) v next up (? ): Wi. MAX (10’s Mbps) over wide area mobile hosts 13
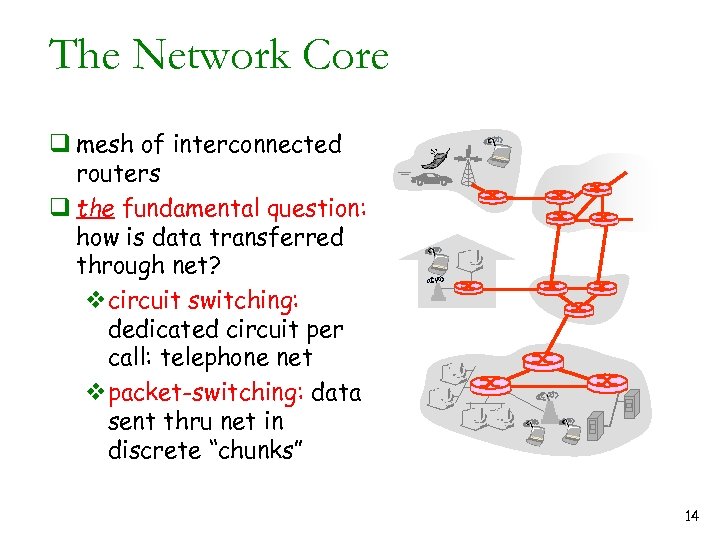 The Network Core q mesh of interconnected routers q the fundamental question: how is data transferred through net? vcircuit switching: dedicated circuit per call: telephone net vpacket-switching: data sent thru net in discrete “chunks” 14
The Network Core q mesh of interconnected routers q the fundamental question: how is data transferred through net? vcircuit switching: dedicated circuit per call: telephone net vpacket-switching: data sent thru net in discrete “chunks” 14
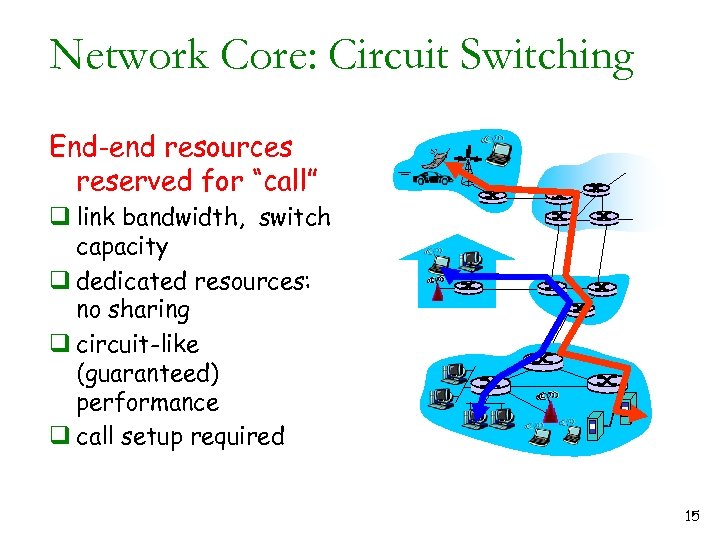 Network Core: Circuit Switching End-end resources reserved for “call” q link bandwidth, switch capacity q dedicated resources: no sharing q circuit-like (guaranteed) performance q call setup required 15
Network Core: Circuit Switching End-end resources reserved for “call” q link bandwidth, switch capacity q dedicated resources: no sharing q circuit-like (guaranteed) performance q call setup required 15
 Network Core: Circuit Switching network resources (e. g. , bandwidth) divided into “pieces” q pieces allocated to calls q resource piece idle if not used by owning call (no sharing) q Qiestion: how is bandwidth divided into “pieces” v v 16
Network Core: Circuit Switching network resources (e. g. , bandwidth) divided into “pieces” q pieces allocated to calls q resource piece idle if not used by owning call (no sharing) q Qiestion: how is bandwidth divided into “pieces” v v 16
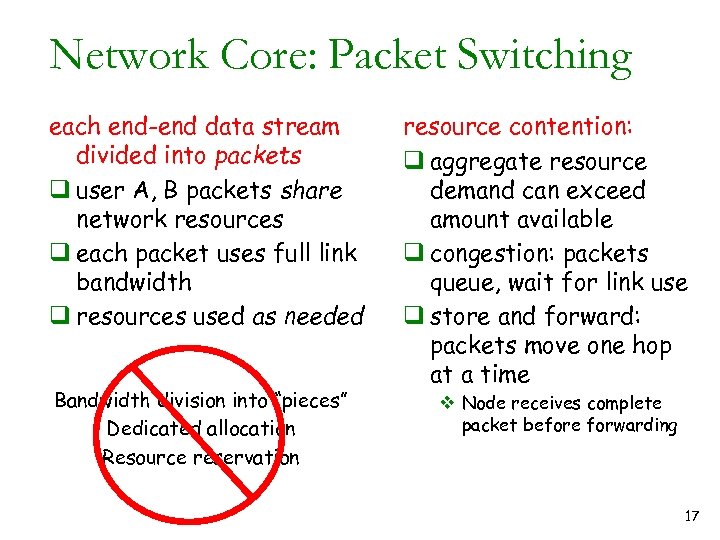 Network Core: Packet Switching each end-end data stream divided into packets q user A, B packets share network resources q each packet uses full link bandwidth q resources used as needed Bandwidth division into “pieces” Dedicated allocation Resource reservation resource contention: q aggregate resource demand can exceed amount available q congestion: packets queue, wait for link use q store and forward: packets move one hop at a time v Node receives complete packet before forwarding 17
Network Core: Packet Switching each end-end data stream divided into packets q user A, B packets share network resources q each packet uses full link bandwidth q resources used as needed Bandwidth division into “pieces” Dedicated allocation Resource reservation resource contention: q aggregate resource demand can exceed amount available q congestion: packets queue, wait for link use q store and forward: packets move one hop at a time v Node receives complete packet before forwarding 17
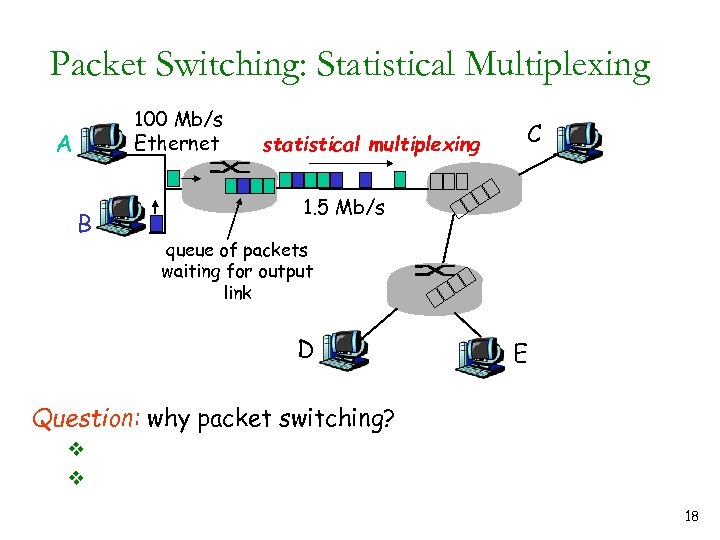 Packet Switching: Statistical Multiplexing 100 Mb/s Ethernet A B statistical multiplexing C 1. 5 Mb/s queue of packets waiting for output link D E Question: why packet switching? v v 18
Packet Switching: Statistical Multiplexing 100 Mb/s Ethernet A B statistical multiplexing C 1. 5 Mb/s queue of packets waiting for output link D E Question: why packet switching? v v 18
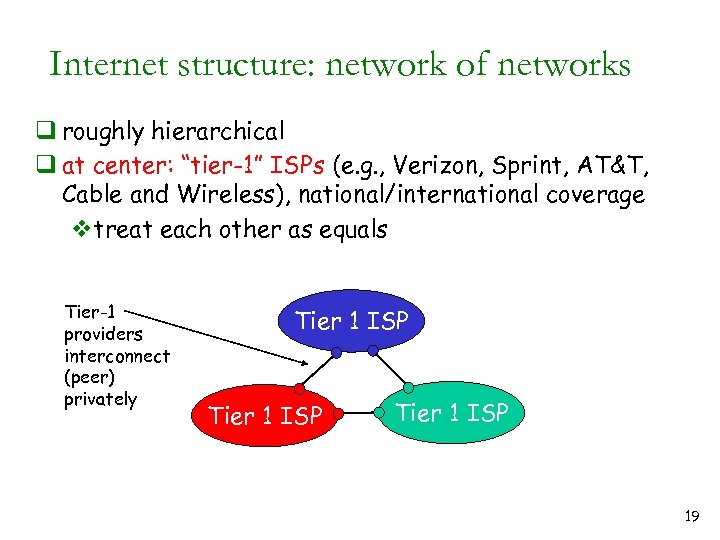 Internet structure: network of networks q roughly hierarchical q at center: “tier-1” ISPs (e. g. , Verizon, Sprint, AT&T, Cable and Wireless), national/international coverage vtreat each other as equals Tier-1 providers interconnect (peer) privately Tier 1 ISP 19
Internet structure: network of networks q roughly hierarchical q at center: “tier-1” ISPs (e. g. , Verizon, Sprint, AT&T, Cable and Wireless), national/international coverage vtreat each other as equals Tier-1 providers interconnect (peer) privately Tier 1 ISP 19
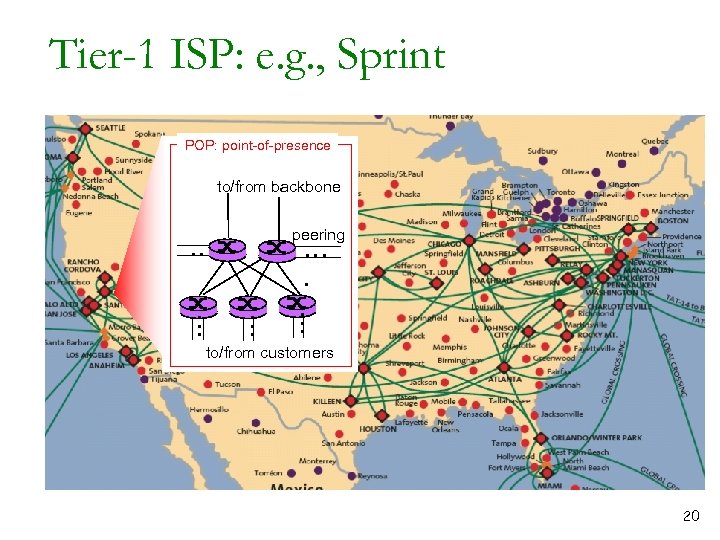 Tier-1 ISP: e. g. , Sprint POP: point-of-presence to/from backbone peering … … … to/from customers 20
Tier-1 ISP: e. g. , Sprint POP: point-of-presence to/from backbone peering … … … to/from customers 20
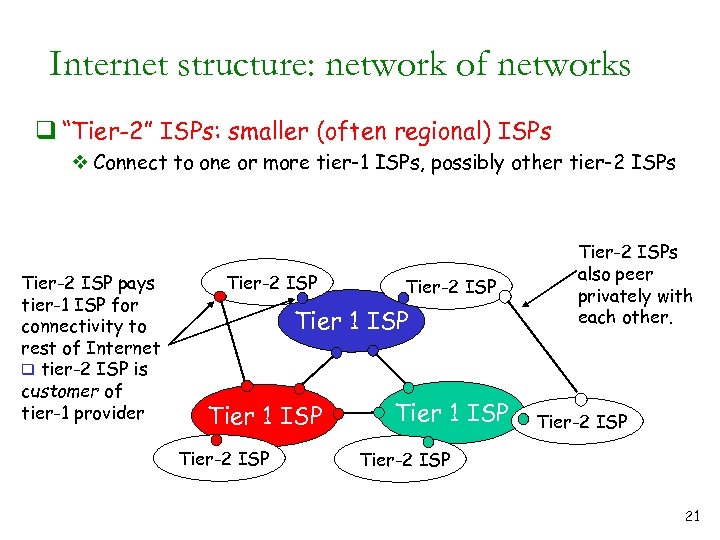 Internet structure: network of networks q “Tier-2” ISPs: smaller (often regional) ISPs v Connect to one or more tier-1 ISPs, possibly other tier-2 ISPs Tier-2 ISP pays tier-1 ISP for connectivity to rest of Internet q tier-2 ISP is customer of tier-1 provider Tier-2 ISP Tier 1 ISP Tier-2 ISPs also peer privately with each other. Tier-2 ISP 21
Internet structure: network of networks q “Tier-2” ISPs: smaller (often regional) ISPs v Connect to one or more tier-1 ISPs, possibly other tier-2 ISPs Tier-2 ISP pays tier-1 ISP for connectivity to rest of Internet q tier-2 ISP is customer of tier-1 provider Tier-2 ISP Tier 1 ISP Tier-2 ISPs also peer privately with each other. Tier-2 ISP 21
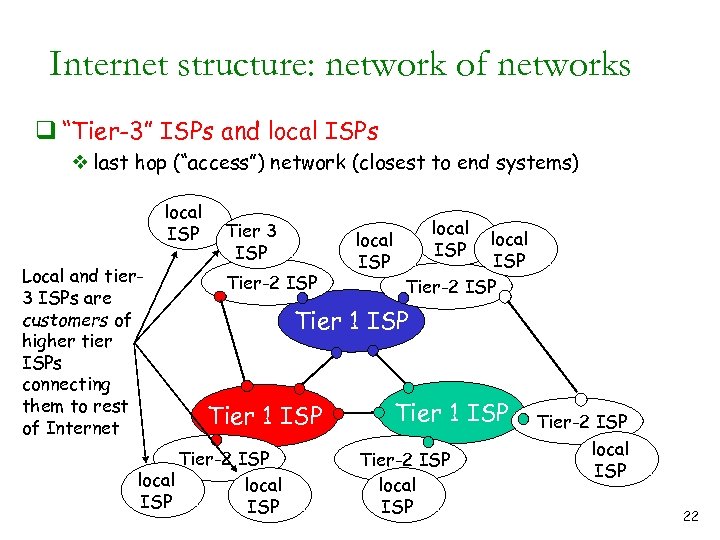 Internet structure: network of networks q “Tier-3” ISPs and local ISPs v last hop (“access”) network (closest to end systems) local ISP Local and tier 3 ISPs are customers of higher tier ISPs connecting them to rest of Internet Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local ISP 22
Internet structure: network of networks q “Tier-3” ISPs and local ISPs v last hop (“access”) network (closest to end systems) local ISP Local and tier 3 ISPs are customers of higher tier ISPs connecting them to rest of Internet Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local ISP 22
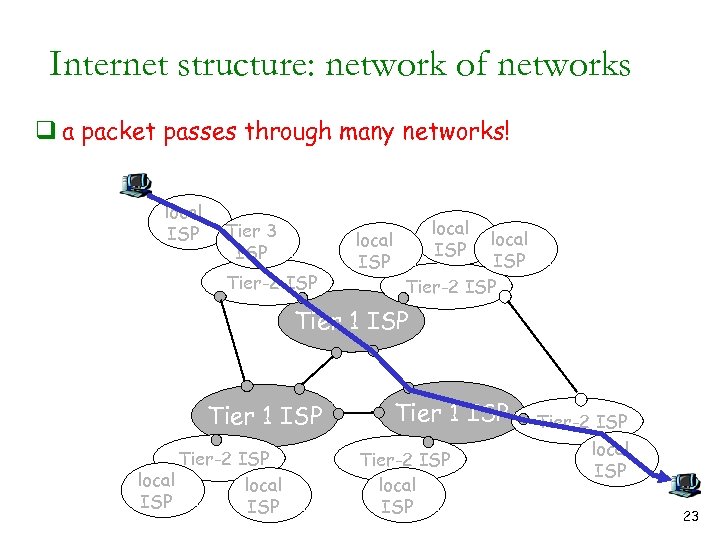 Internet structure: network of networks q a packet passes through many networks! local ISP Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local ISP 23
Internet structure: network of networks q a packet passes through many networks! local ISP Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local ISP 23
 Protocol “Layers” Networks are complex! q many “pieces”: vhosts vrouters vlinks of various media vapplications vprotocols vhardware, software 24
Protocol “Layers” Networks are complex! q many “pieces”: vhosts vrouters vlinks of various media vapplications vprotocols vhardware, software 24
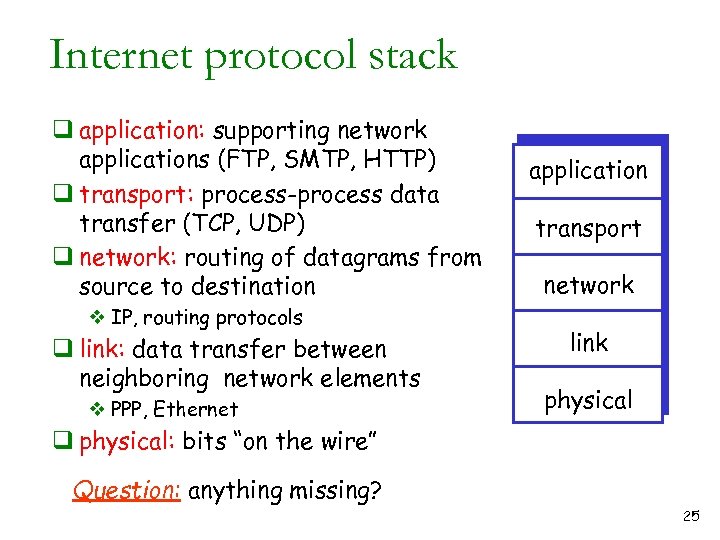 Internet protocol stack q application: supporting network applications (FTP, SMTP, HTTP) q transport: process-process data transfer (TCP, UDP) q network: routing of datagrams from source to destination v IP, routing protocols q link: data transfer between neighboring network elements v PPP, Ethernet application transport network link physical q physical: bits “on the wire” Question: anything missing? 25
Internet protocol stack q application: supporting network applications (FTP, SMTP, HTTP) q transport: process-process data transfer (TCP, UDP) q network: routing of datagrams from source to destination v IP, routing protocols q link: data transfer between neighboring network elements v PPP, Ethernet application transport network link physical q physical: bits “on the wire” Question: anything missing? 25
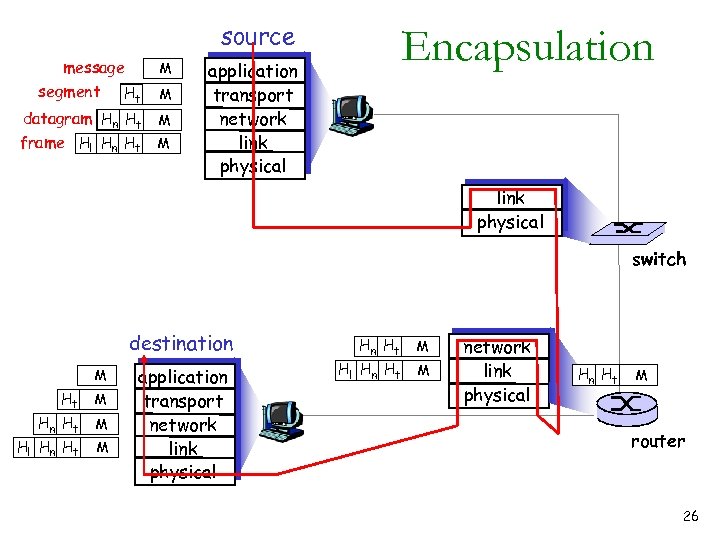 source message segment Ht M datagram Hn Ht M frame Hl Hn Ht M M Encapsulation application transport network link physical switch destination M Ht M Hn Ht Hl Hn Ht M M application transport network link physical Hn Ht Hl Hn Ht M M network link physical Hn Ht M router 26
source message segment Ht M datagram Hn Ht M frame Hl Hn Ht M M Encapsulation application transport network link physical switch destination M Ht M Hn Ht Hl Hn Ht M M application transport network link physical Hn Ht Hl Hn Ht M M network link physical Hn Ht M router 26
 Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing q synthesis: v control timescales 27
Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing q synthesis: v control timescales 27
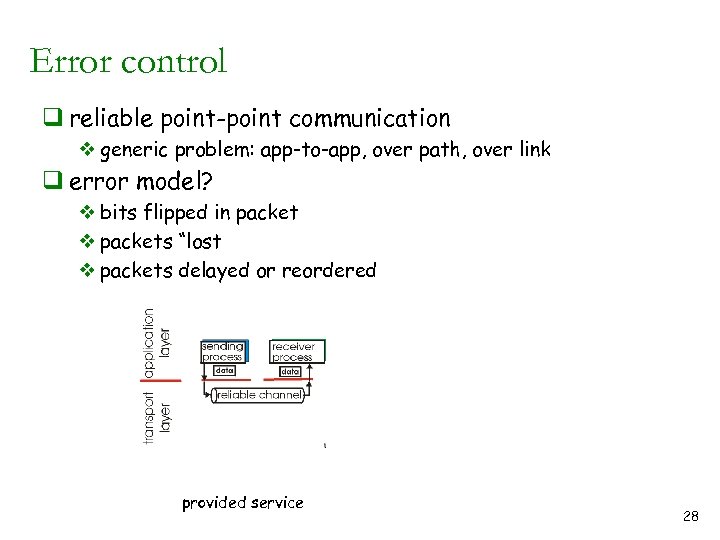 Error control q reliable point-point communication v generic problem: app-to-app, over path, over link q error model? v bits flipped in packet v packets “lost v packets delayed or reordered provided service implementation 28
Error control q reliable point-point communication v generic problem: app-to-app, over path, over link q error model? v bits flipped in packet v packets “lost v packets delayed or reordered provided service implementation 28
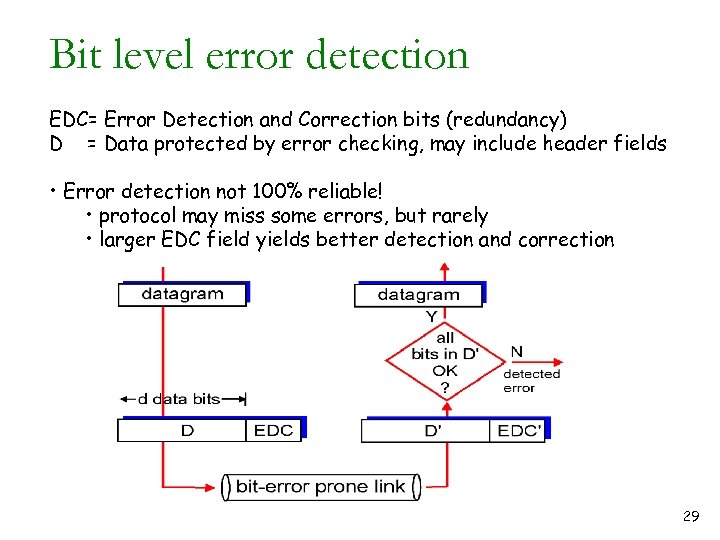 Bit level error detection EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction 29
Bit level error detection EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction 29
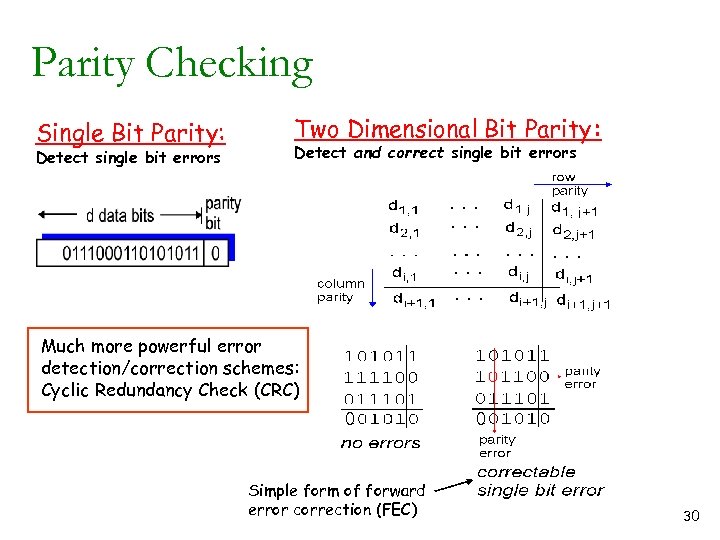 Parity Checking Single Bit Parity: Detect single bit errors Two Dimensional Bit Parity: Detect and correct single bit errors Much more powerful error detection/correction schemes: Cyclic Redundancy Check (CRC) 0 Simple form of forward error correction (FEC) 0 30
Parity Checking Single Bit Parity: Detect single bit errors Two Dimensional Bit Parity: Detect and correct single bit errors Much more powerful error detection/correction schemes: Cyclic Redundancy Check (CRC) 0 Simple form of forward error correction (FEC) 0 30
 Internet checksum Goal: detect “errors” (e. g. , flipped bits) in transmitted segment (note: used at transport layer only) Sender: q treat segment contents as sequence of 16 -bit integers q checksum: addition (1’s complement sum) of segment contents q sender puts checksum value into segment checksum field Receiver: q compute checksum of received segment q check if computed checksum equals checksum field value: v NO - error detected v YES - no error detected. But maybe errors nonetheless? 31
Internet checksum Goal: detect “errors” (e. g. , flipped bits) in transmitted segment (note: used at transport layer only) Sender: q treat segment contents as sequence of 16 -bit integers q checksum: addition (1’s complement sum) of segment contents q sender puts checksum value into segment checksum field Receiver: q compute checksum of received segment q check if computed checksum equals checksum field value: v NO - error detected v YES - no error detected. But maybe errors nonetheless? 31
 Recovering from lost packets q why are packets lost? vlimited storage, discarded in congestion voutages: eventually reroute around failure (~sec recovery times hopefully) vdropped at end system e. g. , on NIC q ARQ: automatic request repeat vsender puts sequence numbers on packets (why) vreceiver positively or negatively acknowledges correct receipt of packet vsender starts (logical) timer for each packet, timeout and retransmits 32
Recovering from lost packets q why are packets lost? vlimited storage, discarded in congestion voutages: eventually reroute around failure (~sec recovery times hopefully) vdropped at end system e. g. , on NIC q ARQ: automatic request repeat vsender puts sequence numbers on packets (why) vreceiver positively or negatively acknowledges correct receipt of packet vsender starts (logical) timer for each packet, timeout and retransmits 32
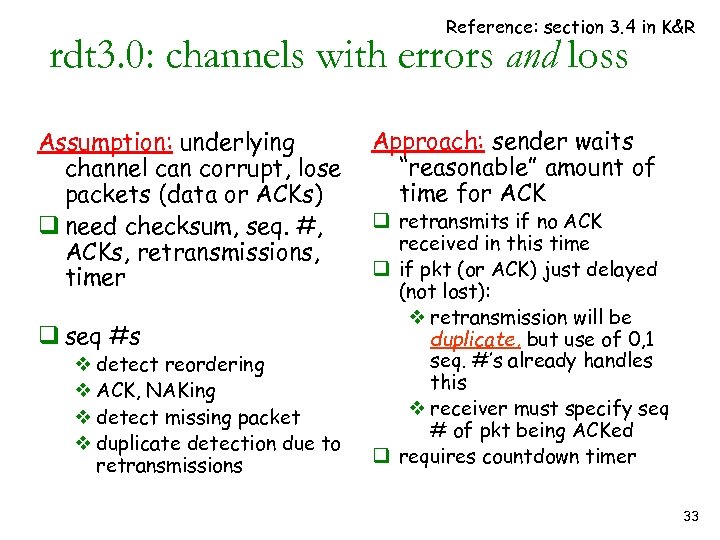 Reference: section 3. 4 in K&R rdt 3. 0: channels with errors and loss Assumption: underlying channel can corrupt, lose packets (data or ACKs) q need checksum, seq. #, ACKs, retransmissions, timer q seq #s v detect reordering v ACK, NAKing v detect missing packet v duplicate detection due to retransmissions Approach: sender waits “reasonable” amount of time for ACK q retransmits if no ACK received in this time q if pkt (or ACK) just delayed (not lost): v retransmission will be duplicate, but use of 0, 1 seq. #’s already handles this v receiver must specify seq # of pkt being ACKed q requires countdown timer 33
Reference: section 3. 4 in K&R rdt 3. 0: channels with errors and loss Assumption: underlying channel can corrupt, lose packets (data or ACKs) q need checksum, seq. #, ACKs, retransmissions, timer q seq #s v detect reordering v ACK, NAKing v detect missing packet v duplicate detection due to retransmissions Approach: sender waits “reasonable” amount of time for ACK q retransmits if no ACK received in this time q if pkt (or ACK) just delayed (not lost): v retransmission will be duplicate, but use of 0, 1 seq. #’s already handles this v receiver must specify seq # of pkt being ACKed q requires countdown timer 33
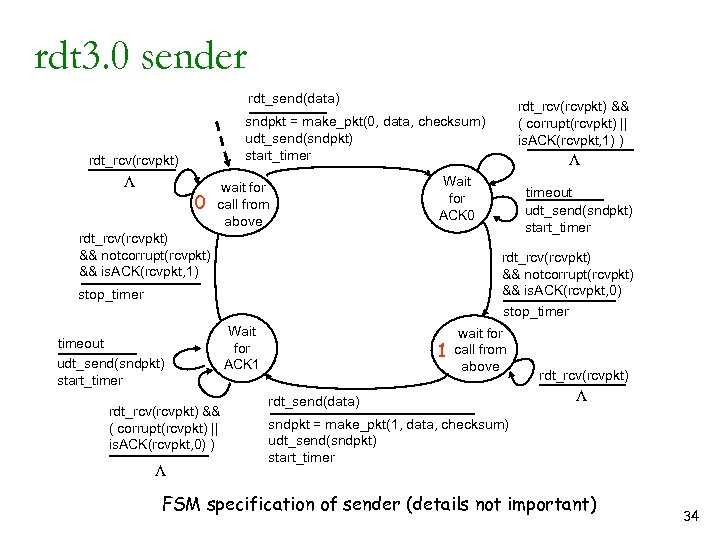 rdt 3. 0 sender rdt_send(data) sndpkt = make_pkt(0, data, checksum) udt_send(sndpkt) start_timer rdt_rcv(rcvpkt) L 0 wait for call from above rdt_rcv(rcvpkt) && ( corrupt(rcvpkt) || is. ACK(rcvpkt, 0) ) timeout udt_send(sndpkt) start_timer rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) && is. ACK(rcvpkt, 0) stop_timer timeout udt_send(sndpkt) start_timer L Wait for ACK 0 rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) && is. ACK(rcvpkt, 1) L rdt_rcv(rcvpkt) && ( corrupt(rcvpkt) || is. ACK(rcvpkt, 1) ) Wait for ACK 1 1 wait for call from above rdt_send(data) rdt_rcv(rcvpkt) L sndpkt = make_pkt(1, data, checksum) udt_send(sndpkt) start_timer FSM specification of sender (details not important) 34
rdt 3. 0 sender rdt_send(data) sndpkt = make_pkt(0, data, checksum) udt_send(sndpkt) start_timer rdt_rcv(rcvpkt) L 0 wait for call from above rdt_rcv(rcvpkt) && ( corrupt(rcvpkt) || is. ACK(rcvpkt, 0) ) timeout udt_send(sndpkt) start_timer rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) && is. ACK(rcvpkt, 0) stop_timer timeout udt_send(sndpkt) start_timer L Wait for ACK 0 rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) && is. ACK(rcvpkt, 1) L rdt_rcv(rcvpkt) && ( corrupt(rcvpkt) || is. ACK(rcvpkt, 1) ) Wait for ACK 1 1 wait for call from above rdt_send(data) rdt_rcv(rcvpkt) L sndpkt = make_pkt(1, data, checksum) udt_send(sndpkt) start_timer FSM specification of sender (details not important) 34
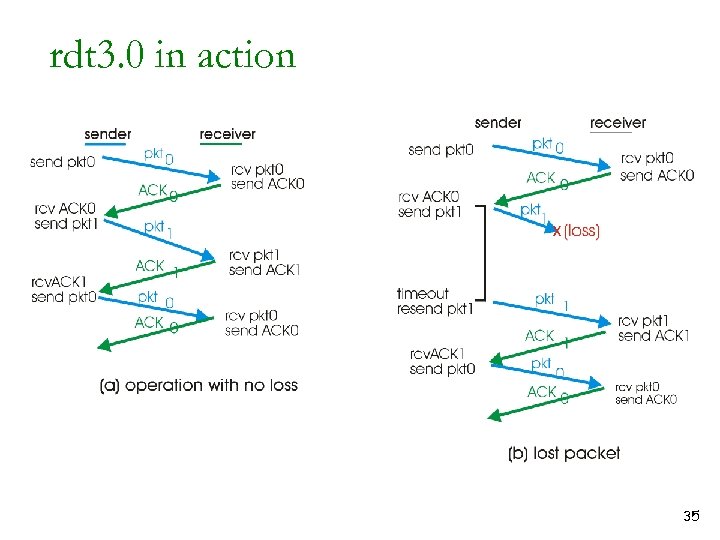 rdt 3. 0 in action 35
rdt 3. 0 in action 35
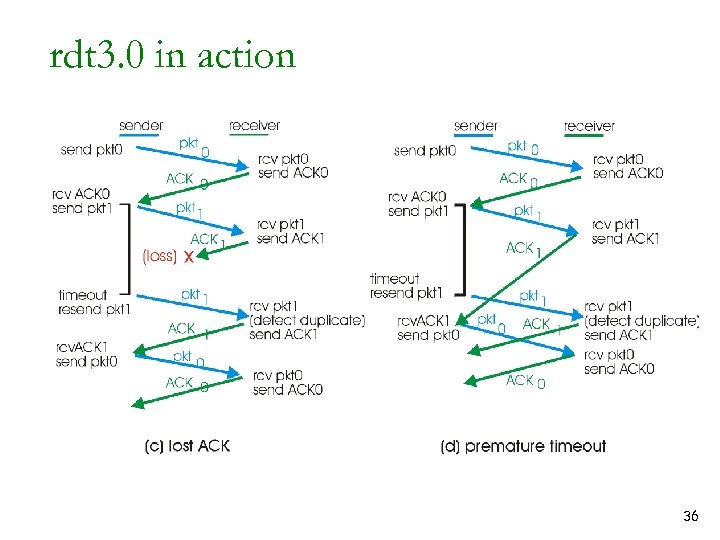 rdt 3. 0 in action 36
rdt 3. 0 in action 36
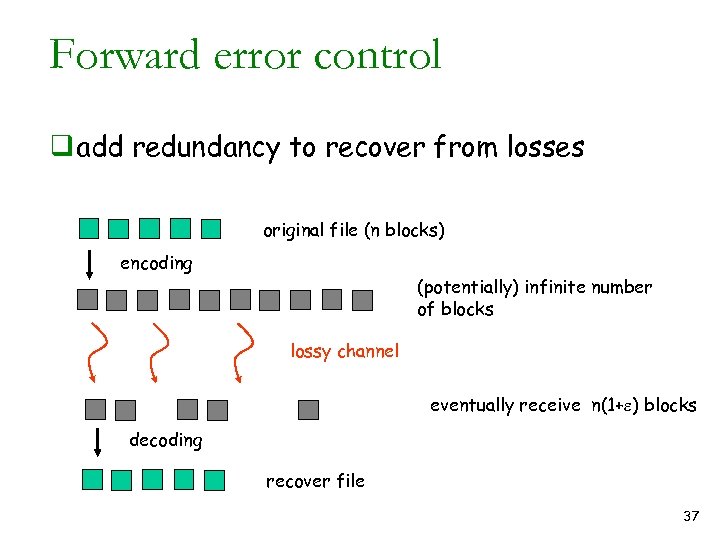 Forward error control q add redundancy to recover from losses original file (n blocks) encoding (potentially) infinite number of blocks lossy channel eventually receive n(1+e) blocks decoding recover file 37
Forward error control q add redundancy to recover from losses original file (n blocks) encoding (potentially) infinite number of blocks lossy channel eventually receive n(1+e) blocks decoding recover file 37
 Forward error control q e controls computation cost, BW usage q used for video delivery; large file transfers 38
Forward error control q e controls computation cost, BW usage q used for video delivery; large file transfers 38
 Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing q synthesis: v “a day in the life” v control timescales 39
Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing q synthesis: v “a day in the life” v control timescales 39
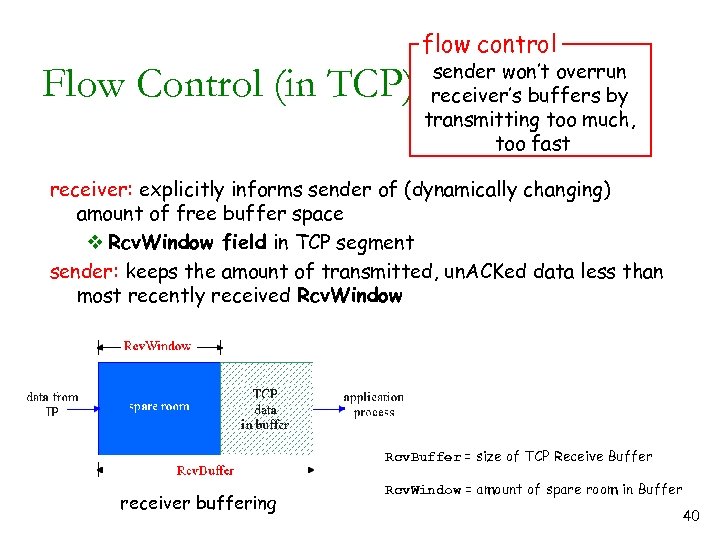 flow control Flow Control (in TCP) sender won’t overrun receiver’s buffers by transmitting too much, too fast receiver: explicitly informs sender of (dynamically changing) amount of free buffer space v Rcv. Window field in TCP segment sender: keeps the amount of transmitted, un. ACKed data less than most recently received Rcv. Window Rcv. Buffer = size of TCP Receive Buffer receiver buffering Rcv. Window = amount of spare room in Buffer 40
flow control Flow Control (in TCP) sender won’t overrun receiver’s buffers by transmitting too much, too fast receiver: explicitly informs sender of (dynamically changing) amount of free buffer space v Rcv. Window field in TCP segment sender: keeps the amount of transmitted, un. ACKed data less than most recently received Rcv. Window Rcv. Buffer = size of TCP Receive Buffer receiver buffering Rcv. Window = amount of spare room in Buffer 40
 Principles of Congestion Control Congestion: q informally: “too many sources sending too much data too fast for network to handle” q different from flow control! q manifestations: vlost packets (buffer overflow at routers) vlong delays (queueing in router buffers) 41
Principles of Congestion Control Congestion: q informally: “too many sources sending too much data too fast for network to handle” q different from flow control! q manifestations: vlost packets (buffer overflow at routers) vlong delays (queueing in router buffers) 41
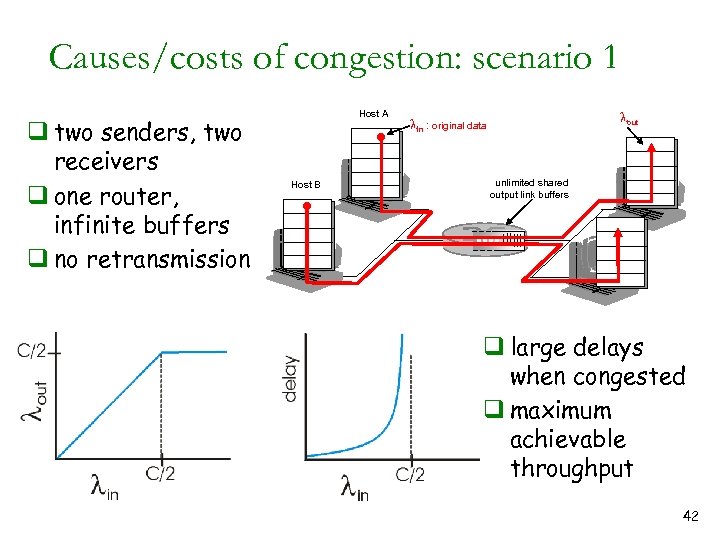 Causes/costs of congestion: scenario 1 q two senders, two receivers q one router, infinite buffers q no retransmission Host A Host B lout lin : original data unlimited shared output link buffers q large delays when congested q maximum achievable throughput 42
Causes/costs of congestion: scenario 1 q two senders, two receivers q one router, infinite buffers q no retransmission Host A Host B lout lin : original data unlimited shared output link buffers q large delays when congested q maximum achievable throughput 42
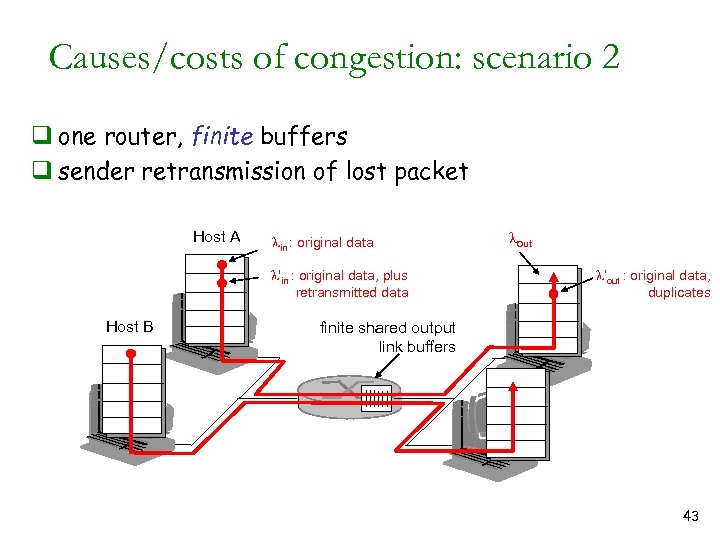 Causes/costs of congestion: scenario 2 q one router, finite buffers q sender retransmission of lost packet Host A lin : original data l'in : original data, plus retransmitted data Host B lout l‘out : original data, duplicates finite shared output link buffers 43
Causes/costs of congestion: scenario 2 q one router, finite buffers q sender retransmission of lost packet Host A lin : original data l'in : original data, plus retransmitted data Host B lout l‘out : original data, duplicates finite shared output link buffers 43
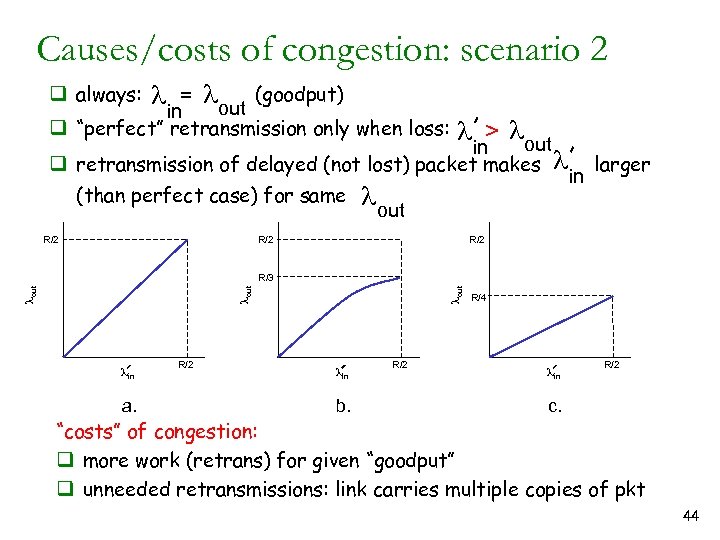 Causes/costs of congestion: scenario 2 (goodput) = l out in q “perfect” retransmission only when loss: q always: l l > lout in q retransmission of delayed (not lost) packet makes (than perfect case) for same R/2 l lout R/2 in larger R/2 lin a. R/2 lout R/3 lin b. R/2 R/4 lin R/2 c. “costs” of congestion: q more work (retrans) for given “goodput” q unneeded retransmissions: link carries multiple copies of pkt 44
Causes/costs of congestion: scenario 2 (goodput) = l out in q “perfect” retransmission only when loss: q always: l l > lout in q retransmission of delayed (not lost) packet makes (than perfect case) for same R/2 l lout R/2 in larger R/2 lin a. R/2 lout R/3 lin b. R/2 R/4 lin R/2 c. “costs” of congestion: q more work (retrans) for given “goodput” q unneeded retransmissions: link carries multiple copies of pkt 44
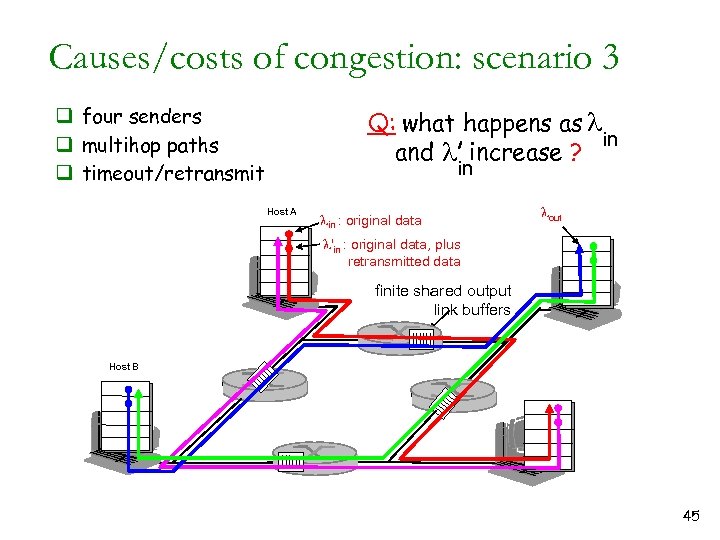 Causes/costs of congestion: scenario 3 q four senders q multihop paths q timeout/retransmit Q: what happens as l in and l increase ? in Host A lin : original data lout l'in : original data, plus retransmitted data finite shared output link buffers Host B 45
Causes/costs of congestion: scenario 3 q four senders q multihop paths q timeout/retransmit Q: what happens as l in and l increase ? in Host A lin : original data lout l'in : original data, plus retransmitted data finite shared output link buffers Host B 45
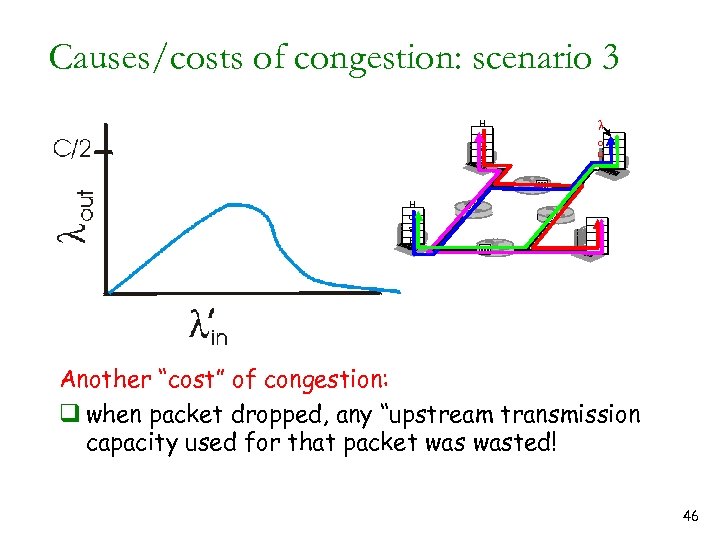 Causes/costs of congestion: scenario 3 H o st A l o u t H o st B Another “cost” of congestion: q when packet dropped, any “upstream transmission capacity used for that packet wasted! 46
Causes/costs of congestion: scenario 3 H o st A l o u t H o st B Another “cost” of congestion: q when packet dropped, any “upstream transmission capacity used for that packet wasted! 46
 Approaches towards congestion control Two broad approaches towards congestion control: End-end congestion control: q no explicit feedback from network q congestion inferred from end-system observed loss, delay q approach taken by TCP Network-assisted congestion control: q routers provide feedback to end systems v single bit indicating congestion (SNA, DECbit, TCP/IP ECN, ATM) v explicit rate sender should send at 47
Approaches towards congestion control Two broad approaches towards congestion control: End-end congestion control: q no explicit feedback from network q congestion inferred from end-system observed loss, delay q approach taken by TCP Network-assisted congestion control: q routers provide feedback to end systems v single bit indicating congestion (SNA, DECbit, TCP/IP ECN, ATM) v explicit rate sender should send at 47
 Case study: ATM ABR congestion control ABR: available bit rate: q “elastic service” q if sender’s path “underloaded”: v sender should use available bandwidth q if sender’s path congested: v sender throttled to minimum guaranteed rate RM (resource management) cells: q sent by sender, interspersed with data cells q bits in RM cell set by switches (“network-assisted”) v NI bit: no increase in rate (mild congestion) v CI bit: congestion indication q RM cells returned to sender by receiver, with bits intact 48
Case study: ATM ABR congestion control ABR: available bit rate: q “elastic service” q if sender’s path “underloaded”: v sender should use available bandwidth q if sender’s path congested: v sender throttled to minimum guaranteed rate RM (resource management) cells: q sent by sender, interspersed with data cells q bits in RM cell set by switches (“network-assisted”) v NI bit: no increase in rate (mild congestion) v CI bit: congestion indication q RM cells returned to sender by receiver, with bits intact 48
 Case study: ATM ABR congestion control q two-byte ER (explicit rate) field in RM cell v congested switch may lower ER value in cell v sender’ send rate thus minimum supportable rate on path q EFCI bit in data cells: set to 1 in congested switch v if data cell preceding RM cell has EFCI set, sender sets CI bit in returned RM cell 49
Case study: ATM ABR congestion control q two-byte ER (explicit rate) field in RM cell v congested switch may lower ER value in cell v sender’ send rate thus minimum supportable rate on path q EFCI bit in data cells: set to 1 in congested switch v if data cell preceding RM cell has EFCI set, sender sets CI bit in returned RM cell 49
 TCP Congestion Control q end-end control (no network assistance) q transmission rate limited by congestion window size, Congwin, over segments: Congwin 50
TCP Congestion Control q end-end control (no network assistance) q transmission rate limited by congestion window size, Congwin, over segments: Congwin 50
 TCP congestion control: q “probing” for usable bandwidth: v ideally: transmit as fast as possible (Congwin as large as possible) without loss v increase Congwin until loss (congestion) v loss: decrease Congwin, then begin probing (increasing) again q two “phases” v slow start v congestion avoidance q important variables: v Congwin v threshold: defines threshold between two slow start phase, congestion control phase 51
TCP congestion control: q “probing” for usable bandwidth: v ideally: transmit as fast as possible (Congwin as large as possible) without loss v increase Congwin until loss (congestion) v loss: decrease Congwin, then begin probing (increasing) again q two “phases” v slow start v congestion avoidance q important variables: v Congwin v threshold: defines threshold between two slow start phase, congestion control phase 51
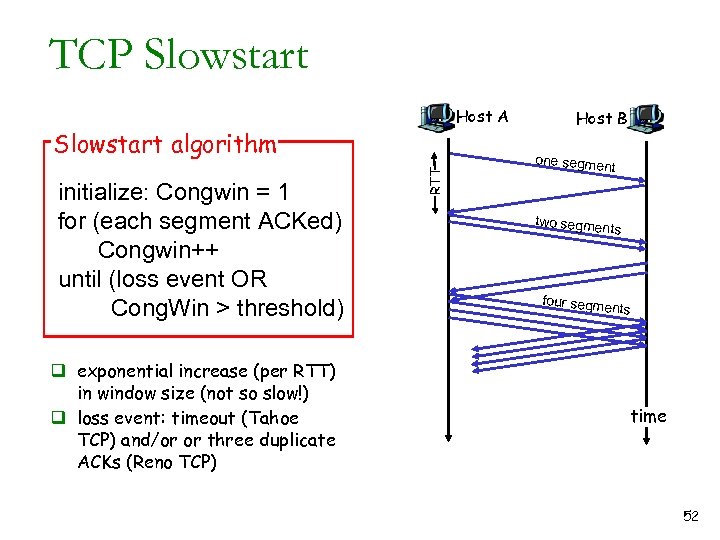 TCP Slowstart Host A initialize: Congwin = 1 for (each segment ACKed) Congwin++ until (loss event OR Cong. Win > threshold) q exponential increase (per RTT) in window size (not so slow!) q loss event: timeout (Tahoe TCP) and/or or three duplicate ACKs (Reno TCP) RTT Slowstart algorithm Host B one segme nt two segme nts four segme nts time 52
TCP Slowstart Host A initialize: Congwin = 1 for (each segment ACKed) Congwin++ until (loss event OR Cong. Win > threshold) q exponential increase (per RTT) in window size (not so slow!) q loss event: timeout (Tahoe TCP) and/or or three duplicate ACKs (Reno TCP) RTT Slowstart algorithm Host B one segme nt two segme nts four segme nts time 52
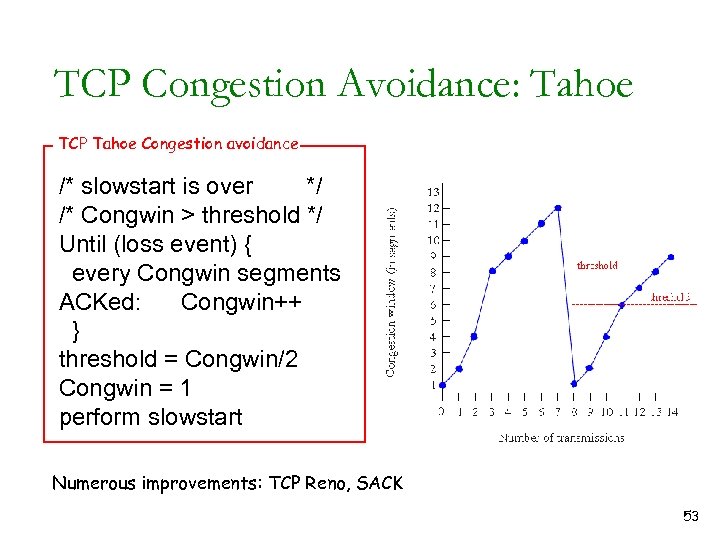 TCP Congestion Avoidance: Tahoe TCP Tahoe Congestion avoidance /* slowstart is over */ /* Congwin > threshold */ Until (loss event) { every Congwin segments ACKed: Congwin++ } threshold = Congwin/2 Congwin = 1 perform slowstart Numerous improvements: TCP Reno, SACK 53
TCP Congestion Avoidance: Tahoe TCP Tahoe Congestion avoidance /* slowstart is over */ /* Congwin > threshold */ Until (loss event) { every Congwin segments ACKed: Congwin++ } threshold = Congwin/2 Congwin = 1 perform slowstart Numerous improvements: TCP Reno, SACK 53
 Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing (and network layer v ease into course services) q LANs q addressing q synthesis: v control timescales 54
Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing (and network layer v ease into course services) q LANs q addressing q synthesis: v control timescales 54
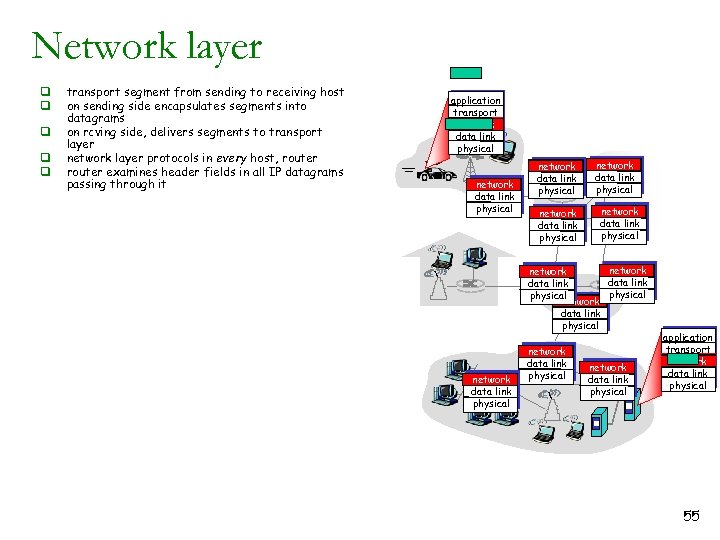 Network layer q q q transport segment from sending to receiving host on sending side encapsulates segments into datagrams on rcving side, delivers segments to transport layer network layer protocols in every host, router examines header fields in all IP datagrams passing through it application transport network data link physical network data link physical network data link physical application transport network data link physical 55
Network layer q q q transport segment from sending to receiving host on sending side encapsulates segments into datagrams on rcving side, delivers segments to transport layer network layer protocols in every host, router examines header fields in all IP datagrams passing through it application transport network data link physical network data link physical network data link physical application transport network data link physical 55
 Two Key Network-Layer Functions q forwarding: move packets from router’s input to appropriate router output q routing: determine route taken by packets from source to dest. analogy: q routing: process of planning trip from source to dest q forwarding: process of getting through single interchange vrouting algorithms 56
Two Key Network-Layer Functions q forwarding: move packets from router’s input to appropriate router output q routing: determine route taken by packets from source to dest. analogy: q routing: process of planning trip from source to dest q forwarding: process of getting through single interchange vrouting algorithms 56
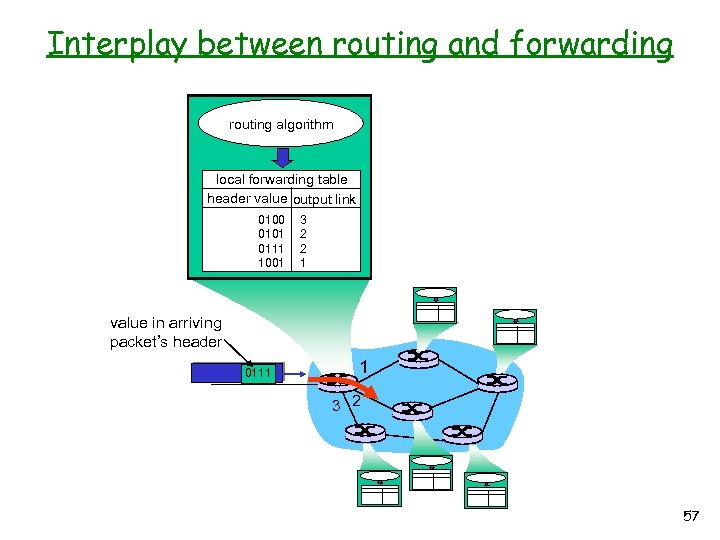 Interplay between routing and forwarding routing algorithm local forwarding table header value output link 0100 0101 0111 1001 3 2 2 1 value in arriving packet’s header 0111 1 3 2 57
Interplay between routing and forwarding routing algorithm local forwarding table header value output link 0100 0101 0111 1001 3 2 2 1 value in arriving packet’s header 0111 1 3 2 57
 Network service model service abstraction Q: What service model for “channel” transporting packets from sender to receiver? q guaranteed bandwidth? q preservation of inter-packet timing (no jitter)? q loss-free delivery? q in-order delivery? q congestion feedback to sender? CRUCIAL question! The most important abstraction provided by network layer: ? ? ? virtual circuit or datagram? 58
Network service model service abstraction Q: What service model for “channel” transporting packets from sender to receiver? q guaranteed bandwidth? q preservation of inter-packet timing (no jitter)? q loss-free delivery? q in-order delivery? q congestion feedback to sender? CRUCIAL question! The most important abstraction provided by network layer: ? ? ? virtual circuit or datagram? 58
 Virtual circuits “source-to-dest path behaves much like telephone circuit” v performance-wise v network actions along source-to-dest path q call setup, teardown for each call before data can flow q each packet carries VC identifier (not destination host ID) q every router on source-dest path maintains “state” for each passing connection v transport-layer connection only involved two end systems q link, router resources (bandwidth, buffers) may be allocated to VC v to get circuit-like perf. 59
Virtual circuits “source-to-dest path behaves much like telephone circuit” v performance-wise v network actions along source-to-dest path q call setup, teardown for each call before data can flow q each packet carries VC identifier (not destination host ID) q every router on source-dest path maintains “state” for each passing connection v transport-layer connection only involved two end systems q link, router resources (bandwidth, buffers) may be allocated to VC v to get circuit-like perf. 59
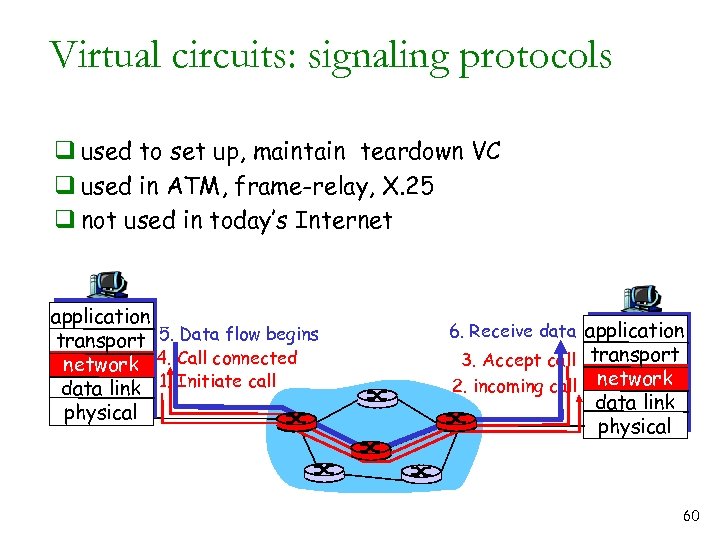 Virtual circuits: signaling protocols q used to set up, maintain teardown VC q used in ATM, frame-relay, X. 25 q not used in today’s Internet application transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical 6. Receive data application 3. Accept call transport 2. incoming call network data link physical 60
Virtual circuits: signaling protocols q used to set up, maintain teardown VC q used in ATM, frame-relay, X. 25 q not used in today’s Internet application transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical 6. Receive data application 3. Accept call transport 2. incoming call network data link physical 60
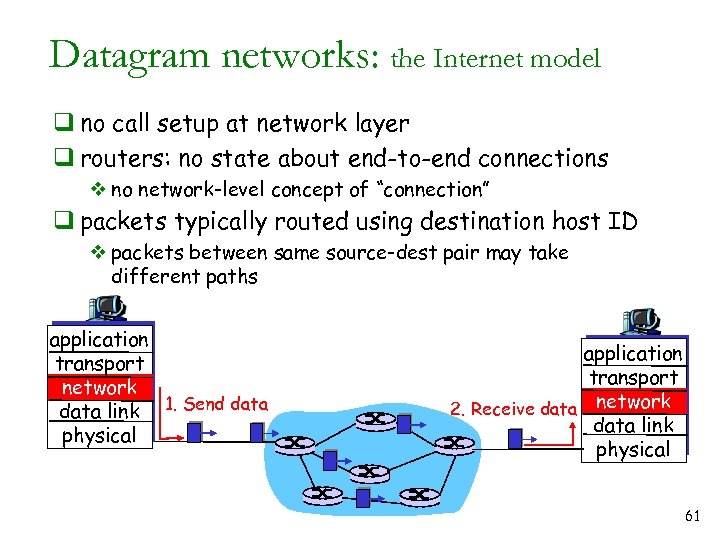 Datagram networks: the Internet model q no call setup at network layer q routers: no state about end-to-end connections v no network-level concept of “connection” q packets typically routed using destination host ID v packets between same source-dest pair may take different paths application transport network data link 1. Send data physical application transport 2. Receive data network data link physical 61
Datagram networks: the Internet model q no call setup at network layer q routers: no state about end-to-end connections v no network-level concept of “connection” q packets typically routed using destination host ID v packets between same source-dest pair may take different paths application transport network data link 1. Send data physical application transport 2. Receive data network data link physical 61
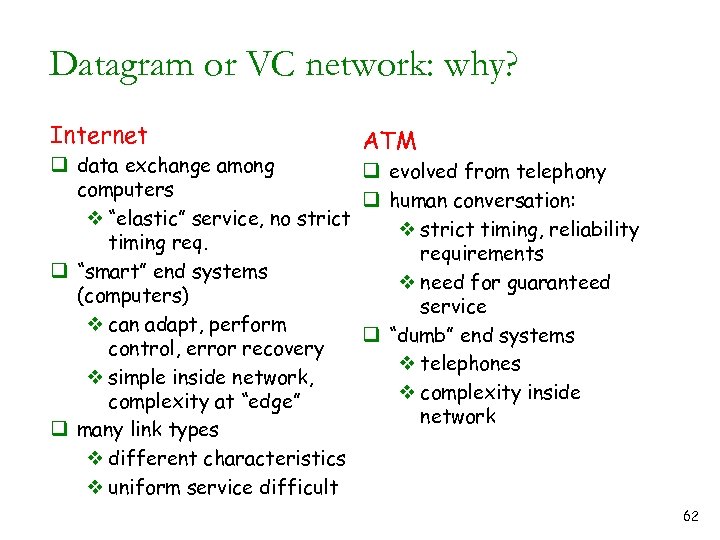 Datagram or VC network: why? Internet ATM q data exchange among q evolved from telephony computers q human conversation: v “elastic” service, no strict v strict timing, reliability timing requirements q “smart” end systems v need for guaranteed (computers) service v can adapt, perform q “dumb” end systems control, error recovery v telephones v simple inside network, v complexity inside complexity at “edge” network q many link types v different characteristics v uniform service difficult 62
Datagram or VC network: why? Internet ATM q data exchange among q evolved from telephony computers q human conversation: v “elastic” service, no strict v strict timing, reliability timing requirements q “smart” end systems v need for guaranteed (computers) service v can adapt, perform q “dumb” end systems control, error recovery v telephones v simple inside network, v complexity inside complexity at “edge” network q many link types v different characteristics v uniform service difficult 62
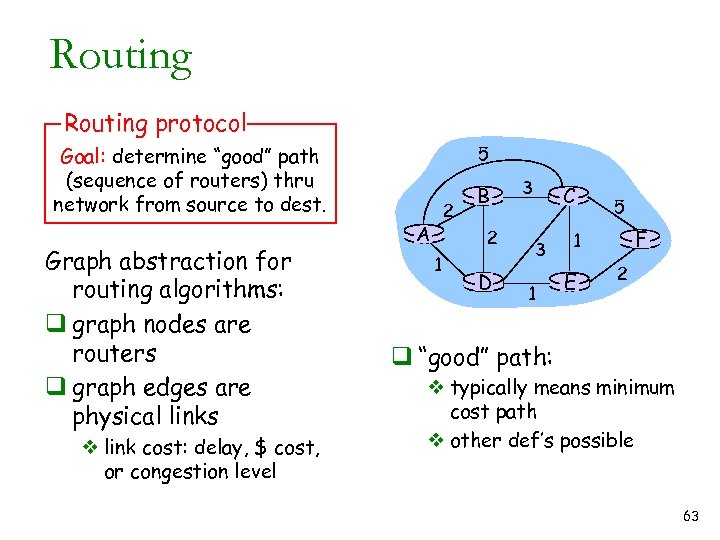 Routing protocol 5 Goal: determine “good” path (sequence of routers) thru network from source to dest. Graph abstraction for routing algorithms: q graph nodes are routers q graph edges are physical links v link cost: delay, $ cost, or congestion level 2 A B 2 1 D 3 C 3 1 5 F 1 E 2 q “good” path: v typically means minimum cost path v other def’s possible 63
Routing protocol 5 Goal: determine “good” path (sequence of routers) thru network from source to dest. Graph abstraction for routing algorithms: q graph nodes are routers q graph edges are physical links v link cost: delay, $ cost, or congestion level 2 A B 2 1 D 3 C 3 1 5 F 1 E 2 q “good” path: v typically means minimum cost path v other def’s possible 63
 Routing: only two approaches used in practice Global: q all routers have complete topology, link cost info q “link state” algorithms: use Dijkstra’s algorithm to find shortest path from given router to all destinations Decentralized: q router knows physically-connected neighbors, link costs to neighbors q iterative process of computation, exchange of info with neighbors q “distance vector” algorithms q a ‘self-stabilizing algorithm’ (we’ll see these later) 64
Routing: only two approaches used in practice Global: q all routers have complete topology, link cost info q “link state” algorithms: use Dijkstra’s algorithm to find shortest path from given router to all destinations Decentralized: q router knows physically-connected neighbors, link costs to neighbors q iterative process of computation, exchange of info with neighbors q “distance vector” algorithms q a ‘self-stabilizing algorithm’ (we’ll see these later) 64
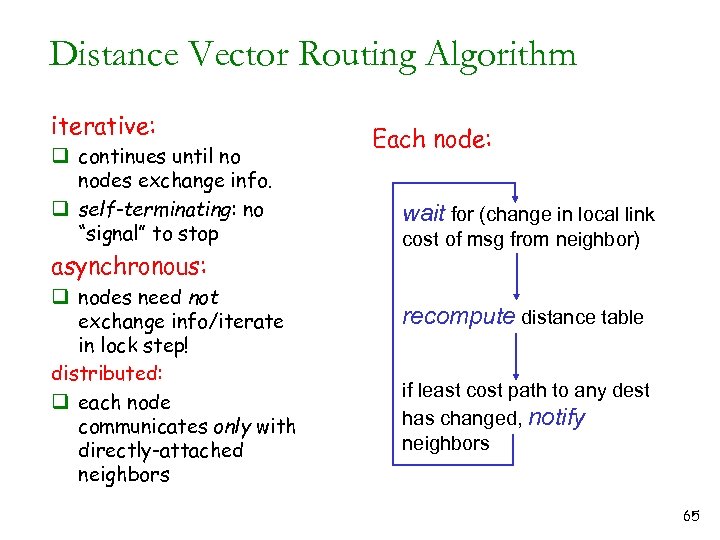 Distance Vector Routing Algorithm iterative: q continues until no nodes exchange info. q self-terminating: no “signal” to stop asynchronous: q nodes need not exchange info/iterate in lock step! distributed: q each node communicates only with directly-attached neighbors Each node: wait for (change in local link cost of msg from neighbor) recompute distance table if least cost path to any dest has changed, notify neighbors 65
Distance Vector Routing Algorithm iterative: q continues until no nodes exchange info. q self-terminating: no “signal” to stop asynchronous: q nodes need not exchange info/iterate in lock step! distributed: q each node communicates only with directly-attached neighbors Each node: wait for (change in local link cost of msg from neighbor) recompute distance table if least cost path to any dest has changed, notify neighbors 65
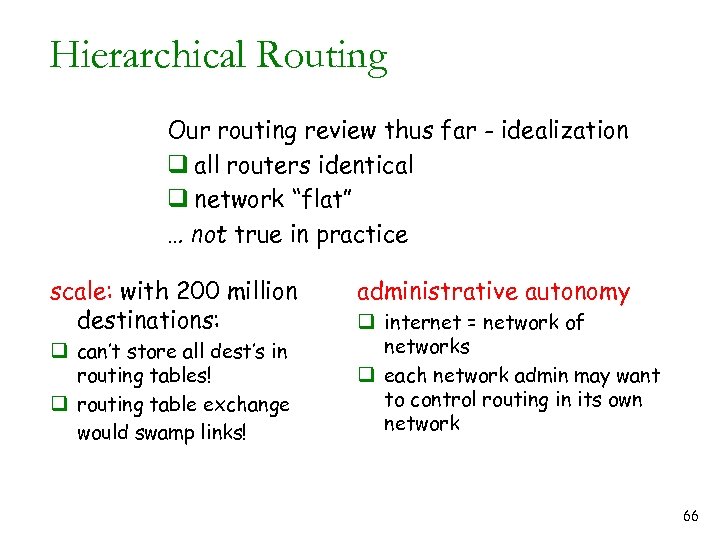 Hierarchical Routing Our routing review thus far - idealization q all routers identical q network “flat” … not true in practice scale: with 200 million destinations: q can’t store all dest’s in routing tables! q routing table exchange would swamp links! administrative autonomy q internet = network of networks q each network admin may want to control routing in its own network 66
Hierarchical Routing Our routing review thus far - idealization q all routers identical q network “flat” … not true in practice scale: with 200 million destinations: q can’t store all dest’s in routing tables! q routing table exchange would swamp links! administrative autonomy q internet = network of networks q each network admin may want to control routing in its own network 66
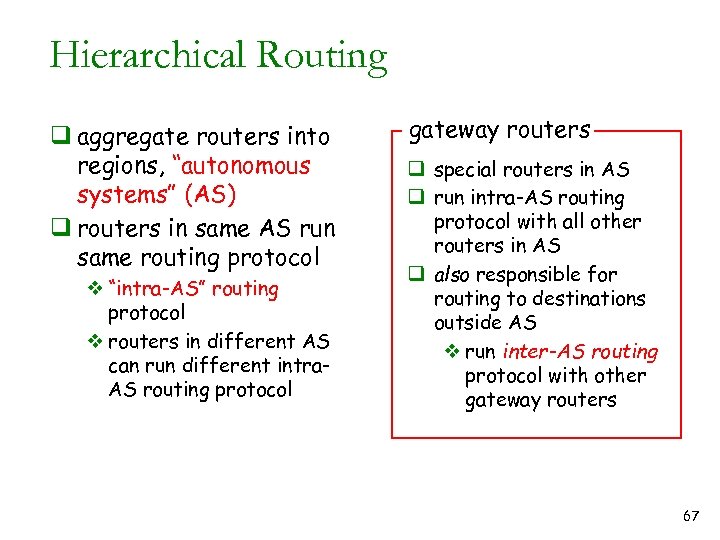 Hierarchical Routing q aggregate routers into regions, “autonomous systems” (AS) q routers in same AS run same routing protocol v “intra-AS” routing protocol v routers in different AS can run different intra. AS routing protocol gateway routers q special routers in AS q run intra-AS routing protocol with all other routers in AS q also responsible for routing to destinations outside AS v run inter-AS routing protocol with other gateway routers 67
Hierarchical Routing q aggregate routers into regions, “autonomous systems” (AS) q routers in same AS run same routing protocol v “intra-AS” routing protocol v routers in different AS can run different intra. AS routing protocol gateway routers q special routers in AS q run intra-AS routing protocol with all other routers in AS q also responsible for routing to destinations outside AS v run inter-AS routing protocol with other gateway routers 67
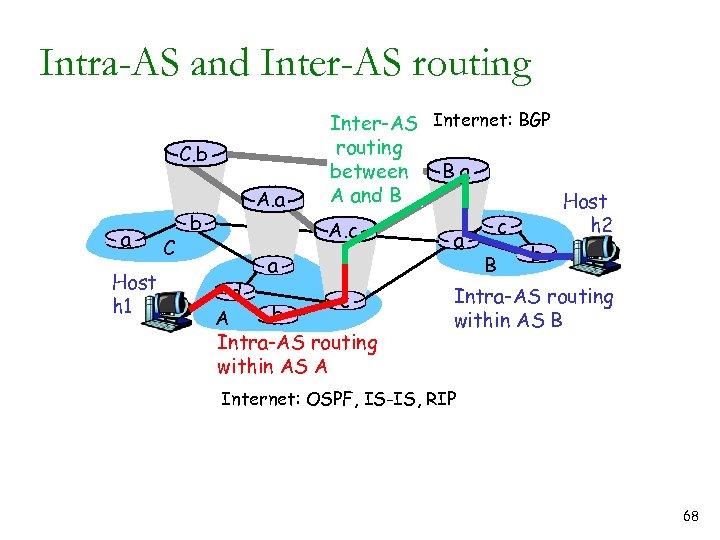 Intra-AS and Inter-AS routing C. b a Host h 1 C b A. a a Inter-AS Internet: BGP routing B. a between A and B Host h 2 c A. c a b B d c b A Intra-AS routing within AS B Internet: OSPF, IS-IS, RIP 68
Intra-AS and Inter-AS routing C. b a Host h 1 C b A. a a Inter-AS Internet: BGP routing B. a between A and B Host h 2 c A. c a b B d c b A Intra-AS routing within AS B Internet: OSPF, IS-IS, RIP 68
 Addressing q what’s an address? videntifier that differentiates between me and someone else, and also helps route data to/from me q real world examples of addressing? v mailing address voffice #, floor, etc vphone 69
Addressing q what’s an address? videntifier that differentiates between me and someone else, and also helps route data to/from me q real world examples of addressing? v mailing address voffice #, floor, etc vphone 69
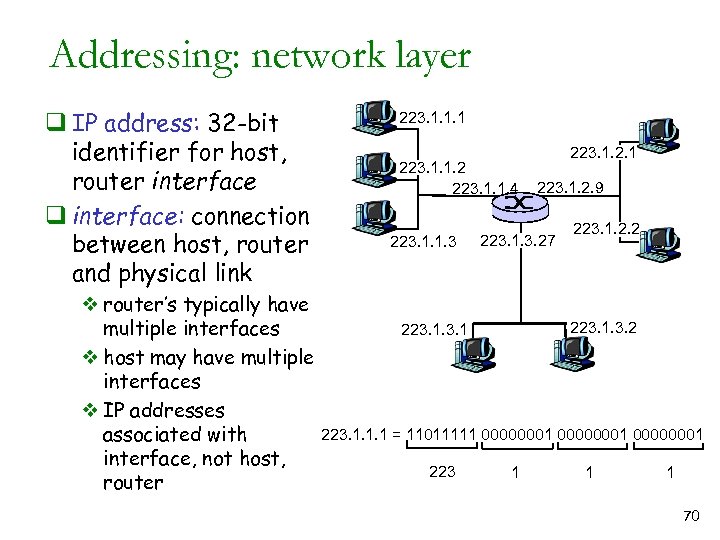 Addressing: network layer q IP address: 32 -bit identifier for host, router interface q interface: connection between host, router and physical link v router’s typically have multiple interfaces v host may have multiple interfaces v IP addresses associated with interface, not host, router 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 223. 1. 1. 1 = 11011111 00000001 223 1 1 1 70
Addressing: network layer q IP address: 32 -bit identifier for host, router interface q interface: connection between host, router and physical link v router’s typically have multiple interfaces v host may have multiple interfaces v IP addresses associated with interface, not host, router 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 223. 1. 1. 1 = 11011111 00000001 223 1 1 1 70
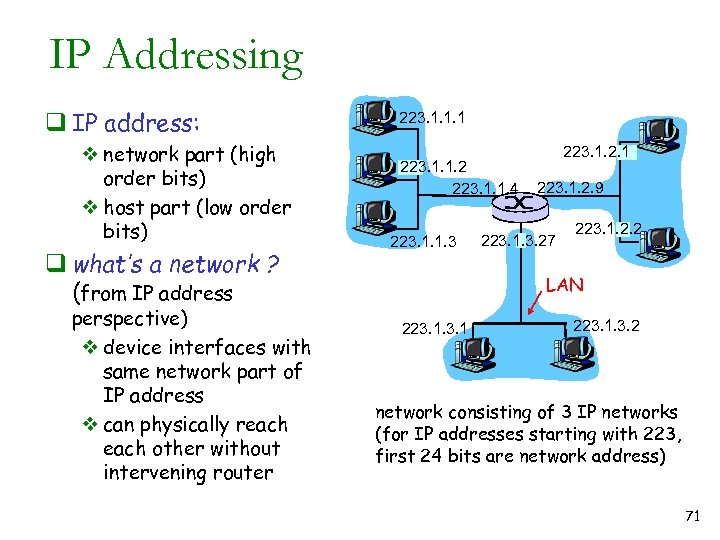 IP Addressing q IP address: v network part (high order bits) v host part (low order bits) q what’s a network ? (from IP address perspective) v device interfaces with same network part of IP address v can physically reach other without intervening router 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 network consisting of 3 IP networks (for IP addresses starting with 223, first 24 bits are network address) 71
IP Addressing q IP address: v network part (high order bits) v host part (low order bits) q what’s a network ? (from IP address perspective) v device interfaces with same network part of IP address v can physically reach other without intervening router 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 network consisting of 3 IP networks (for IP addresses starting with 223, first 24 bits are network address) 71
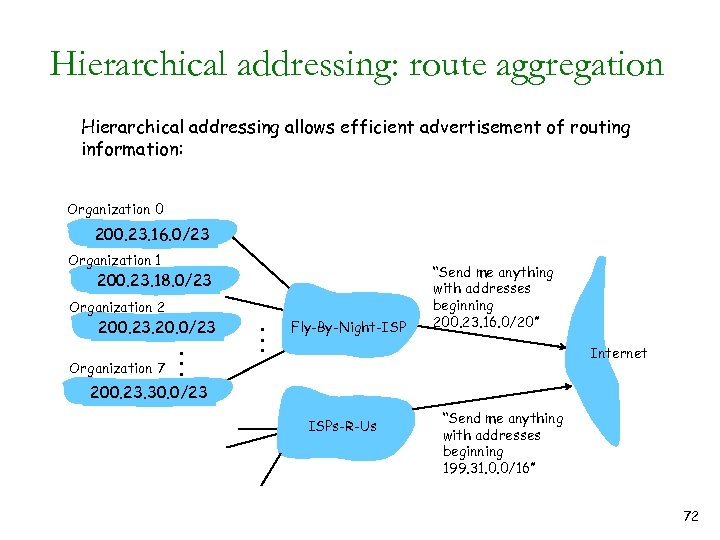 Hierarchical addressing: route aggregation Hierarchical addressing allows efficient advertisement of routing information: Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us “Send me anything with addresses beginning 199. 31. 0. 0/16” 72
Hierarchical addressing: route aggregation Hierarchical addressing allows efficient advertisement of routing information: Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us “Send me anything with addresses beginning 199. 31. 0. 0/16” 72
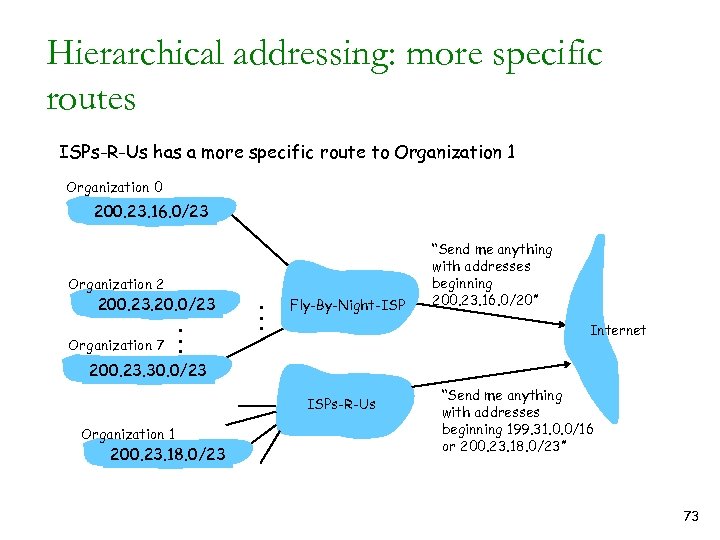 Hierarchical addressing: more specific routes ISPs-R-Us has a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us Organization 1 200. 23. 18. 0/23 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” 73
Hierarchical addressing: more specific routes ISPs-R-Us has a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us Organization 1 200. 23. 18. 0/23 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” 73
 IP addresses: how to get one? Q: How does host get IP address? q hard-coded by system admin in a file v. Wintel: control-panel->network->configuration->tcp/ip->properties v. UNIX: /etc/rc. config q DHCP: Dynamic Host Configuration Protocol: dynamically get address: “plug-and-play” vhost broadcasts “DHCP discover” msg v. DHCP server responds with “DHCP offer” msg vhost requests IP address: “DHCP request” msg v. DHCP server sends address: “DHCP ack” msg 74
IP addresses: how to get one? Q: How does host get IP address? q hard-coded by system admin in a file v. Wintel: control-panel->network->configuration->tcp/ip->properties v. UNIX: /etc/rc. config q DHCP: Dynamic Host Configuration Protocol: dynamically get address: “plug-and-play” vhost broadcasts “DHCP discover” msg v. DHCP server responds with “DHCP offer” msg vhost requests IP address: “DHCP request” msg v. DHCP server sends address: “DHCP ack” msg 74
 Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing (cont. ) q synthesis: v control timescales 75
Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing (cont. ) q synthesis: v control timescales 75
 Link Layer: Introduction Some terminology: q hosts and routers are nodes q communication channels that connect adjacent nodes along communication path are links v wired links v wireless links v LANs q layer-2 packet is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link 76
Link Layer: Introduction Some terminology: q hosts and routers are nodes q communication channels that connect adjacent nodes along communication path are links v wired links v wireless links v LANs q layer-2 packet is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link 76
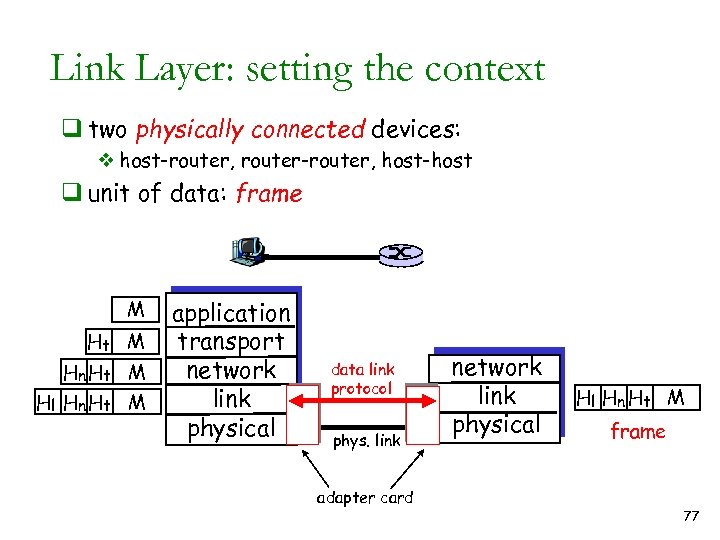 Link Layer: setting the context q two physically connected devices: v host-router, router-router, host-host q unit of data: frame M Ht M Hn Ht M Hl Hn Ht M application transport network link physical data link protocol phys. link adapter card network link physical Hl Hn Ht M frame 77
Link Layer: setting the context q two physically connected devices: v host-router, router-router, host-host q unit of data: frame M Ht M Hn Ht M Hl Hn Ht M application transport network link physical data link protocol phys. link adapter card network link physical Hl Hn Ht M frame 77
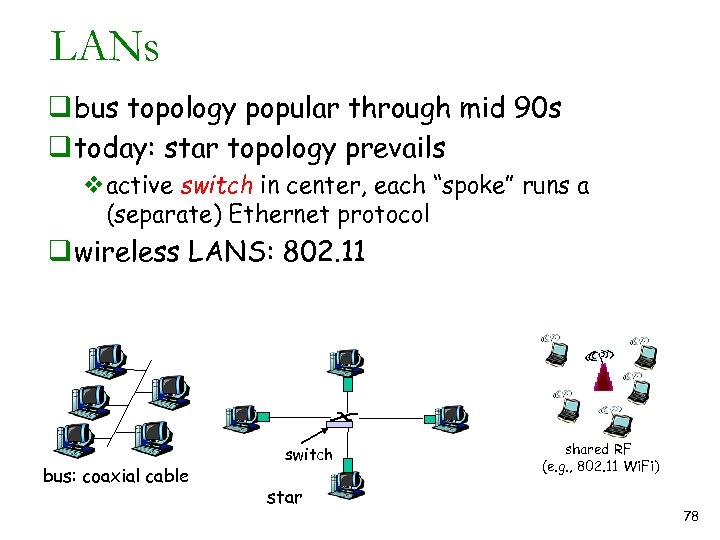 LANs q bus topology popular through mid 90 s q today: star topology prevails vactive switch in center, each “spoke” runs a (separate) Ethernet protocol q wireless LANS: 802. 11 bus: coaxial cable switch star shared RF (e. g. , 802. 11 Wi. Fi) 78
LANs q bus topology popular through mid 90 s q today: star topology prevails vactive switch in center, each “spoke” runs a (separate) Ethernet protocol q wireless LANS: 802. 11 bus: coaxial cable switch star shared RF (e. g. , 802. 11 Wi. Fi) 78
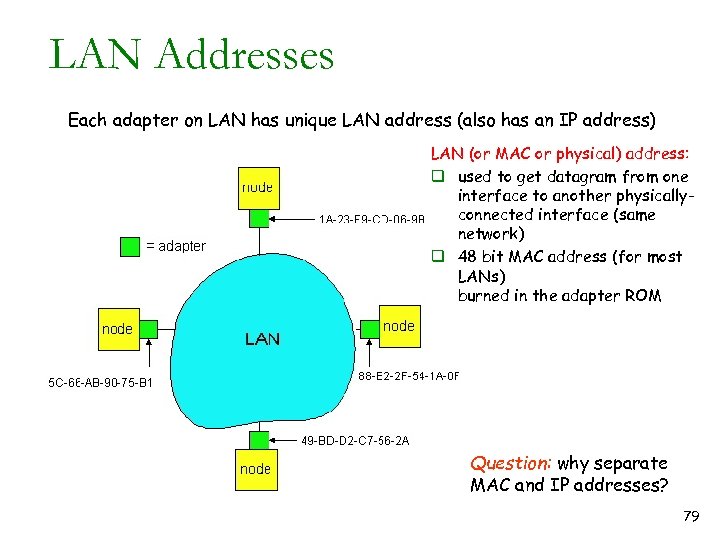 LAN Addresses Each adapter on LAN has unique LAN address (also has an IP address) LAN (or MAC or physical) address: q used to get datagram from one interface to another physicallyconnected interface (same network) q 48 bit MAC address (for most LANs) burned in the adapter ROM Question: why separate MAC and IP addresses? 79
LAN Addresses Each adapter on LAN has unique LAN address (also has an IP address) LAN (or MAC or physical) address: q used to get datagram from one interface to another physicallyconnected interface (same network) q 48 bit MAC address (for most LANs) burned in the adapter ROM Question: why separate MAC and IP addresses? 79
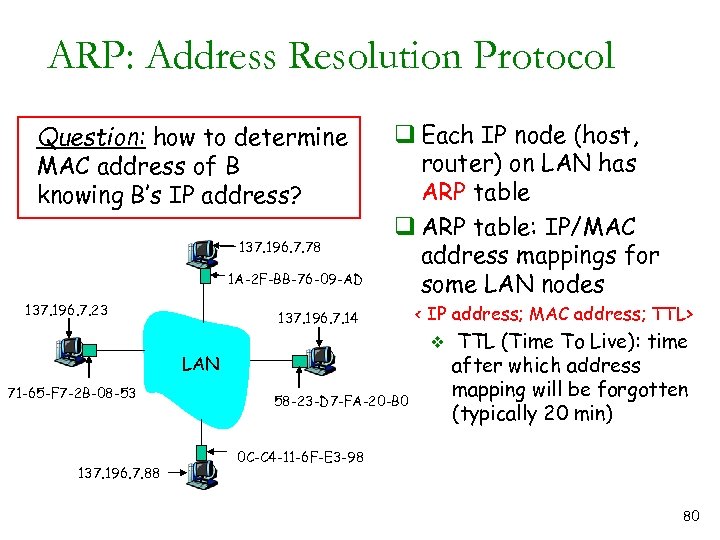 ARP: Address Resolution Protocol Question: how to determine MAC address of B knowing B’s IP address? 137. 196. 7. 78 1 A-2 F-BB-76 -09 -AD 137. 196. 7. 23 q Each IP node (host, router) on LAN has ARP table q ARP table: IP/MAC address mappings for some LAN nodes 137. 196. 7. 14 v LAN 71 -65 -F 7 -2 B-08 -53 137. 196. 7. 88 < IP address; MAC address; TTL> 58 -23 -D 7 -FA-20 -B 0 TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) 0 C-C 4 -11 -6 F-E 3 -98 80
ARP: Address Resolution Protocol Question: how to determine MAC address of B knowing B’s IP address? 137. 196. 7. 78 1 A-2 F-BB-76 -09 -AD 137. 196. 7. 23 q Each IP node (host, router) on LAN has ARP table q ARP table: IP/MAC address mappings for some LAN nodes 137. 196. 7. 14 v LAN 71 -65 -F 7 -2 B-08 -53 137. 196. 7. 88 < IP address; MAC address; TTL> 58 -23 -D 7 -FA-20 -B 0 TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) 0 C-C 4 -11 -6 F-E 3 -98 80
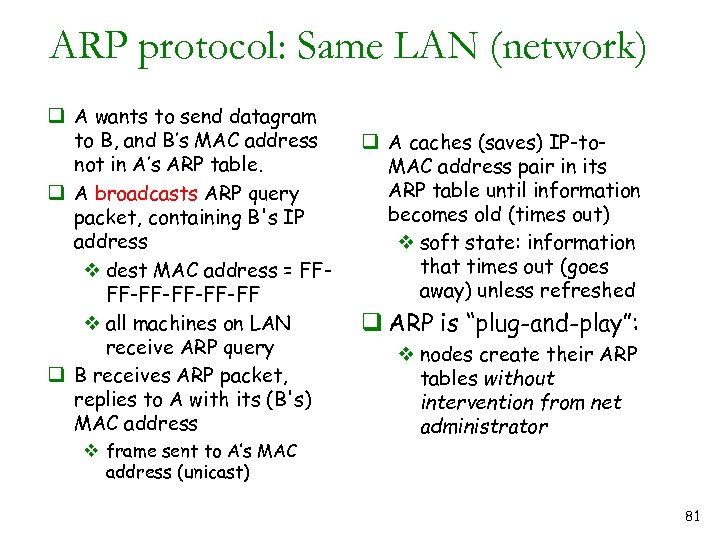 ARP protocol: Same LAN (network) q A wants to send datagram to B, and B’s MAC address not in A’s ARP table. q A broadcasts ARP query packet, containing B's IP address v dest MAC address = FFFF-FF-FF v all machines on LAN receive ARP query q B receives ARP packet, replies to A with its (B's) MAC address v frame sent to A’s MAC address (unicast) q A caches (saves) IP-to. MAC address pair in its ARP table until information becomes old (times out) v soft state: information that times out (goes away) unless refreshed q ARP is “plug-and-play”: v nodes create their ARP tables without intervention from net administrator 81
ARP protocol: Same LAN (network) q A wants to send datagram to B, and B’s MAC address not in A’s ARP table. q A broadcasts ARP query packet, containing B's IP address v dest MAC address = FFFF-FF-FF v all machines on LAN receive ARP query q B receives ARP packet, replies to A with its (B's) MAC address v frame sent to A’s MAC address (unicast) q A caches (saves) IP-to. MAC address pair in its ARP table until information becomes old (times out) v soft state: information that times out (goes away) unless refreshed q ARP is “plug-and-play”: v nodes create their ARP tables without intervention from net administrator 81
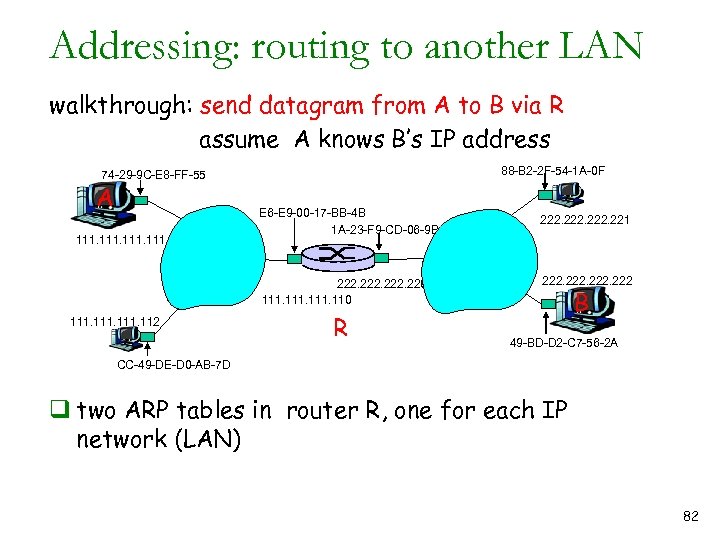 Addressing: routing to another LAN walkthrough: send datagram from A to B via R assume A knows B’s IP address 88 -B 2 -2 F-54 -1 A-0 F 74 -29 -9 C-E 8 -FF-55 A 111 E 6 -E 9 -00 -17 -BB-4 B 1 A-23 -F 9 -CD-06 -9 B 222. 220 111. 112 R 222. 221 222 B 49 -BD-D 2 -C 7 -56 -2 A CC-49 -DE-D 0 -AB-7 D q two ARP tables in router R, one for each IP network (LAN) 82
Addressing: routing to another LAN walkthrough: send datagram from A to B via R assume A knows B’s IP address 88 -B 2 -2 F-54 -1 A-0 F 74 -29 -9 C-E 8 -FF-55 A 111 E 6 -E 9 -00 -17 -BB-4 B 1 A-23 -F 9 -CD-06 -9 B 222. 220 111. 112 R 222. 221 222 B 49 -BD-D 2 -C 7 -56 -2 A CC-49 -DE-D 0 -AB-7 D q two ARP tables in router R, one for each IP network (LAN) 82
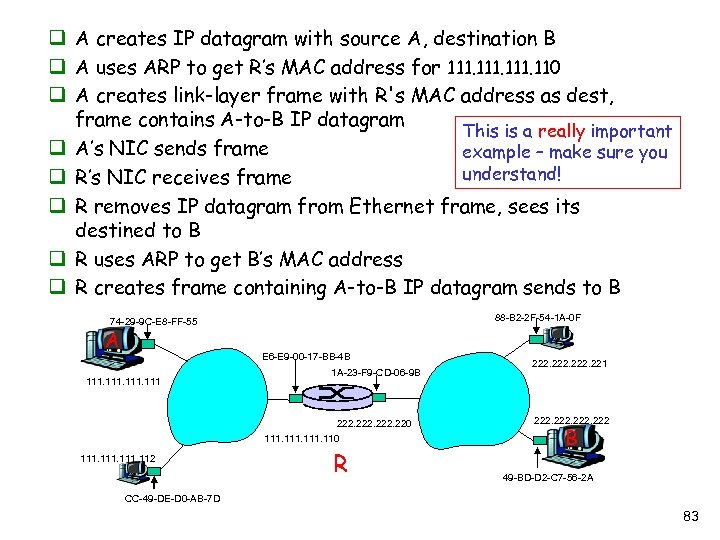 q A creates IP datagram with source A, destination B q A uses ARP to get R’s MAC address for 111. 110 q A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram This is a really important q A’s NIC sends frame example – make sure you understand! q R’s NIC receives frame q R removes IP datagram from Ethernet frame, sees its destined to B q R uses ARP to get B’s MAC address q R creates frame containing A-to-B IP datagram sends to B 88 -B 2 -2 F-54 -1 A-0 F 74 -29 -9 C-E 8 -FF-55 A E 6 -E 9 -00 -17 -BB-4 B 111 1 A-23 -F 9 -CD-06 -9 B 222. 220 111. 112 R 222. 221 222 B 49 -BD-D 2 -C 7 -56 -2 A CC-49 -DE-D 0 -AB-7 D 83
q A creates IP datagram with source A, destination B q A uses ARP to get R’s MAC address for 111. 110 q A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram This is a really important q A’s NIC sends frame example – make sure you understand! q R’s NIC receives frame q R removes IP datagram from Ethernet frame, sees its destined to B q R uses ARP to get B’s MAC address q R creates frame containing A-to-B IP datagram sends to B 88 -B 2 -2 F-54 -1 A-0 F 74 -29 -9 C-E 8 -FF-55 A E 6 -E 9 -00 -17 -BB-4 B 111 1 A-23 -F 9 -CD-06 -9 B 222. 220 111. 112 R 222. 221 222 B 49 -BD-D 2 -C 7 -56 -2 A CC-49 -DE-D 0 -AB-7 D 83
 Part 0: Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing (cont. ) q synthesis: v control timescales 84
Part 0: Networking Review Goals: q review key topics from intro networks course Overview: q overview q error control q flow control v equalize backgrounds q congestion control v identify remedial work q routing v ease into course q LANs q addressing (cont. ) q synthesis: v control timescales 84
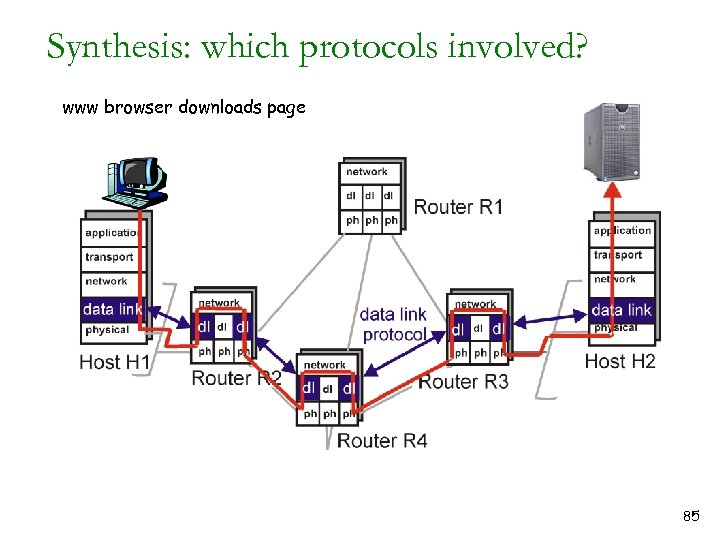 Synthesis: which protocols involved? www browser downloads page 85
Synthesis: which protocols involved? www browser downloads page 85
 Protocols involved in http GET q user types in a URL, what happens? q DNS: translate hostname to IP address v via DHCP, source has IP address of DNS server (suppose DNS server on same network segment) v create DNS query, pass to UDP, create UDP segment containing DNS query, pass to IP on host v look in routing table (DHCP gave me default router), recognize that DNS server on same network. v use ARP to determine MAC address of DNS server v Ethernet used to send frame to DNS server on physically connected “wire” (network segment, ethernet “cable”) v on DNS machine ethernet->IP->UDP. UDP looks at dest port #, sees it is DNS, passes DNS query to DNS application. (assume DNS knows IP addresses of hostname in original URL - address found!) v DNS server sends UDP reply back to orginating machine 86
Protocols involved in http GET q user types in a URL, what happens? q DNS: translate hostname to IP address v via DHCP, source has IP address of DNS server (suppose DNS server on same network segment) v create DNS query, pass to UDP, create UDP segment containing DNS query, pass to IP on host v look in routing table (DHCP gave me default router), recognize that DNS server on same network. v use ARP to determine MAC address of DNS server v Ethernet used to send frame to DNS server on physically connected “wire” (network segment, ethernet “cable”) v on DNS machine ethernet->IP->UDP. UDP looks at dest port #, sees it is DNS, passes DNS query to DNS application. (assume DNS knows IP addresses of hostname in original URL - address found!) v DNS server sends UDP reply back to orginating machine 86
 Protocols involved in http GET q browser now has IP address of GET destination server q need to establish TCP connection to server, send SYN packet (will get an SYNACK back, eventuallly…. ) q SYN packet down to network layer, with IP address of server. Since server destined “off my network”, SYN packet goes through router. q look in routing table, see that destination off network, need to send to “default gateway” (to get off my net) q use ARP to get MAC address of default gateway, create Ethernet frame with gateway MAC address, containing IP packet containing TCP segment, containing SYN q IMPORTANT to realize that while the Ethernet frame containing the IP datagram that contains the TCP SYN has as its destination address the MAC address of the router, the IP datagram (still) has as destination address the IP address of the remote www server 87
Protocols involved in http GET q browser now has IP address of GET destination server q need to establish TCP connection to server, send SYN packet (will get an SYNACK back, eventuallly…. ) q SYN packet down to network layer, with IP address of server. Since server destined “off my network”, SYN packet goes through router. q look in routing table, see that destination off network, need to send to “default gateway” (to get off my net) q use ARP to get MAC address of default gateway, create Ethernet frame with gateway MAC address, containing IP packet containing TCP segment, containing SYN q IMPORTANT to realize that while the Ethernet frame containing the IP datagram that contains the TCP SYN has as its destination address the MAC address of the router, the IP datagram (still) has as destination address the IP address of the remote www server 87
 Protocols involved in http GET q Router receives Ethernet frame (frame addressed to router), looks at IP datagram, sees that IP datagram not addressed to itself (IP datagram addressed to server). Router knows it must forward IP datagram to next hop router along path to eventual destination. q Router checks routing tables (table values populated using intra, possibly inter-, domain routing protocols like OSPF, RIP, IS-IS, BGP (inter). Get IP address of next hop router. q Router puts IP packets in Ethernet frame, Ethernet frame addressed to next hop router. MAC address of next hop router determined by ARP. Frame sent to next hop router. q Network management shoehorn: arriving packets at interface cause SNMP MIB variable for # arriving IP datagrams to be incremented q Forwarding continues until IP datagram containing TCP SYN eventually arrives at destination, gaia. cs. umass. edu (128. 119. 30) q Up to IP, demultiplex from Ethernet to IP using Ethernet TYPE field to identify IP as upper layer protocol q From IP to TCP using protocol field of IP datagram, q SYN packet arrives at gaia TCP (FINALLY) 88
Protocols involved in http GET q Router receives Ethernet frame (frame addressed to router), looks at IP datagram, sees that IP datagram not addressed to itself (IP datagram addressed to server). Router knows it must forward IP datagram to next hop router along path to eventual destination. q Router checks routing tables (table values populated using intra, possibly inter-, domain routing protocols like OSPF, RIP, IS-IS, BGP (inter). Get IP address of next hop router. q Router puts IP packets in Ethernet frame, Ethernet frame addressed to next hop router. MAC address of next hop router determined by ARP. Frame sent to next hop router. q Network management shoehorn: arriving packets at interface cause SNMP MIB variable for # arriving IP datagrams to be incremented q Forwarding continues until IP datagram containing TCP SYN eventually arrives at destination, gaia. cs. umass. edu (128. 119. 30) q Up to IP, demultiplex from Ethernet to IP using Ethernet TYPE field to identify IP as upper layer protocol q From IP to TCP using protocol field of IP datagram, q SYN packet arrives at gaia TCP (FINALLY) 88
 Protocols involved in http GET q So …. SYN has arrived at gaia. Gaia returns SYNACK to initial sender q Gaia gets synack, ready to send data. q HTTP GET message now sent to gaia. cs. umass. edu in TCP segment, in IP datagram, in Ethernet frame, along hops to gaia. cs. umass. edu q GET arrives! REPLY formulated by http server … and sent 89
Protocols involved in http GET q So …. SYN has arrived at gaia. Gaia returns SYNACK to initial sender q Gaia gets synack, ready to send data. q HTTP GET message now sent to gaia. cs. umass. edu in TCP segment, in IP datagram, in Ethernet frame, along hops to gaia. cs. umass. edu q GET arrives! REPLY formulated by http server … and sent 89


