0fc907190f8e14046aaa27a9b2cb0db9.ppt
- Количество слайдов: 18
 Improvements on Conventional PKI Wisdom Carl M. Ellison Sr. Security Architect Corporate Technology Group Intel Corporation 1 st PKI Workshop: April 24, 2002 Intel Labs
Improvements on Conventional PKI Wisdom Carl M. Ellison Sr. Security Architect Corporate Technology Group Intel Corporation 1 st PKI Workshop: April 24, 2002 Intel Labs
 Conventional PKI Wisdom 1. Get and use an acceptable ID certificate for digital signatures. 2. Each certificate should come from a CA with strong key security (a vault). 3. This allows you to know who your transaction partner is. 4. This process gives nonrepudiation. Slide 2 Intel Labs
Conventional PKI Wisdom 1. Get and use an acceptable ID certificate for digital signatures. 2. Each certificate should come from a CA with strong key security (a vault). 3. This allows you to know who your transaction partner is. 4. This process gives nonrepudiation. Slide 2 Intel Labs
 1. ID Certificates Which ID should I use and who should certify me? – 5 at work: carl. m. ellison; cme; amr/cellison; Ellison, Carl M;
1. ID Certificates Which ID should I use and who should certify me? – 5 at work: carl. m. ellison; cme; amr/cellison; Ellison, Carl M;
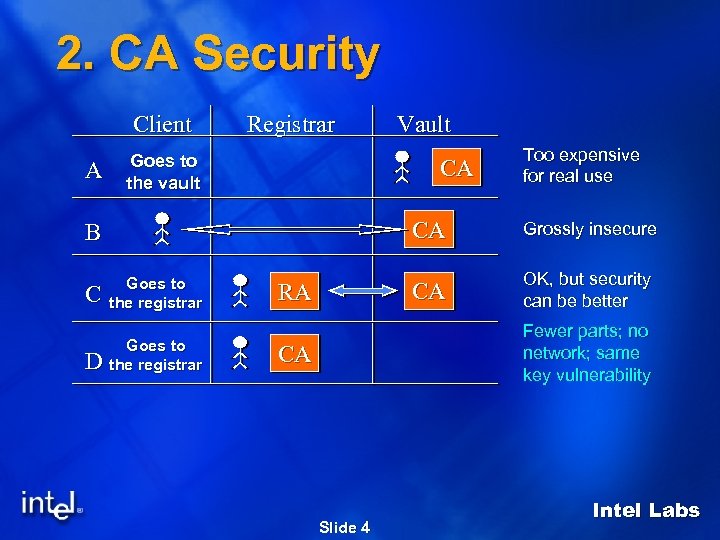 2. CA Security Client A Registrar Goes to the vault Vault CA Too expensive for real use CA C Goes to the registrar D Goes to the registrar RA Grossly insecure CA B OK, but security can be better Fewer parts; no network; same key vulnerability CA Slide 4 Intel Labs
2. CA Security Client A Registrar Goes to the vault Vault CA Too expensive for real use CA C Goes to the registrar D Goes to the registrar RA Grossly insecure CA B OK, but security can be better Fewer parts; no network; same key vulnerability CA Slide 4 Intel Labs
 3. Know the other person The John Wilson Problem – E-mail – Bay area trip, August 2001 – Ann Harrison Moral of the story: human beings do not use names the way we computer scientists would like them to. So … should we change all humans? Slide 5 Intel Labs
3. Know the other person The John Wilson Problem – E-mail – Bay area trip, August 2001 – Ann Harrison Moral of the story: human beings do not use names the way we computer scientists would like them to. So … should we change all humans? Slide 5 Intel Labs
 4. Non-repudiation (NR) Delayed enforcement: prosecute fraud Expensive to track & prosecute Valid only if victim can be made whole – not for secrets or high value content or lives Not possible to implement – – – inadequate protection of keys and S/W inadequate physical security no H/W to witness the signing That’s OK. If you need legal enforceability, you can use contractual commitment. Slide 6 Intel Labs
4. Non-repudiation (NR) Delayed enforcement: prosecute fraud Expensive to track & prosecute Valid only if victim can be made whole – not for secrets or high value content or lives Not possible to implement – – – inadequate protection of keys and S/W inadequate physical security no H/W to witness the signing That’s OK. If you need legal enforceability, you can use contractual commitment. Slide 6 Intel Labs
 New PKI Wisdom 1. There is no single ID, so a single ID certificate makes no sense. 2. Discard RAs and put CAs on RA desks. 3. Knowing a keyholder’s certified name does not tell you who that keyholder is. 4. Non-repudiation is neither adequate for serious problems nor achievable. 5. Do authorization (e. g. , access control) up front, instead. Slide 7 Intel Labs
New PKI Wisdom 1. There is no single ID, so a single ID certificate makes no sense. 2. Discard RAs and put CAs on RA desks. 3. Knowing a keyholder’s certified name does not tell you who that keyholder is. 4. Non-repudiation is neither adequate for serious problems nor achievable. 5. Do authorization (e. g. , access control) up front, instead. Slide 7 Intel Labs
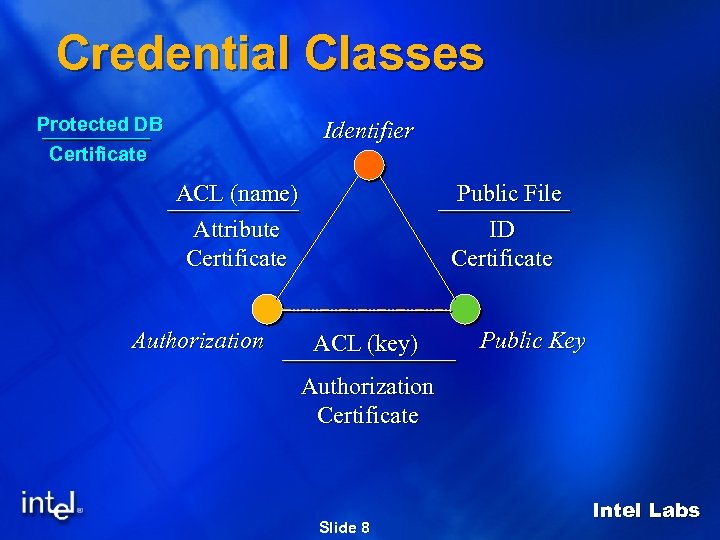 Credential Classes Protected DB Certificate Identifier ACL (name) Attribute Certificate Authorization Public File ID Certificate ACL (key) Public Key Authorization Certificate Slide 8 Intel Labs
Credential Classes Protected DB Certificate Identifier ACL (name) Attribute Certificate Authorization Public File ID Certificate ACL (key) Public Key Authorization Certificate Slide 8 Intel Labs
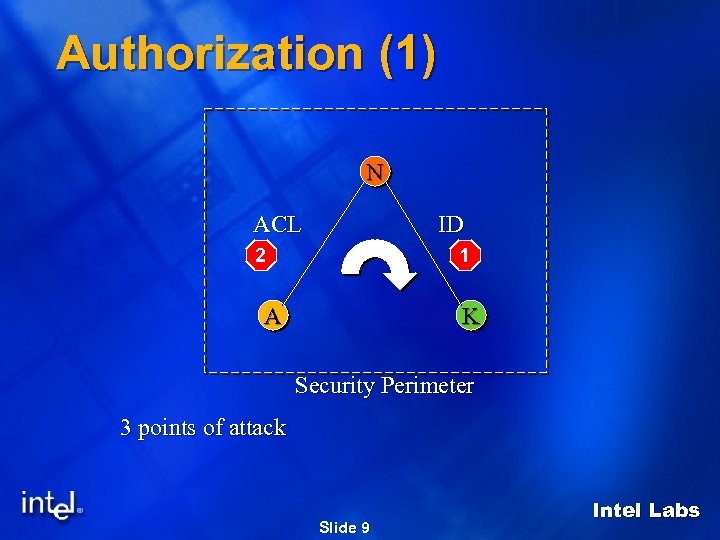 Authorization (1) N ACL ID 2 1 A K Security Perimeter 3 points of attack Slide 9 Intel Labs
Authorization (1) N ACL ID 2 1 A K Security Perimeter 3 points of attack Slide 9 Intel Labs
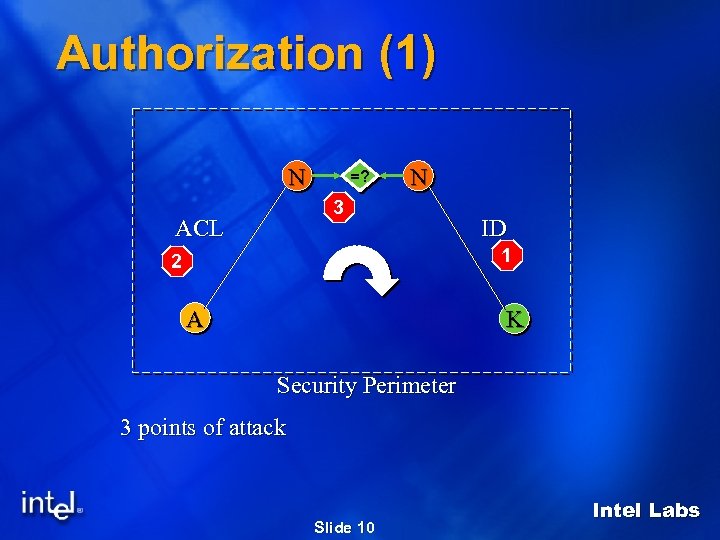 Authorization (1) N =? N 3 ACL ID 1 2 A K Security Perimeter 3 points of attack Slide 10 Intel Labs
Authorization (1) N =? N 3 ACL ID 1 2 A K Security Perimeter 3 points of attack Slide 10 Intel Labs
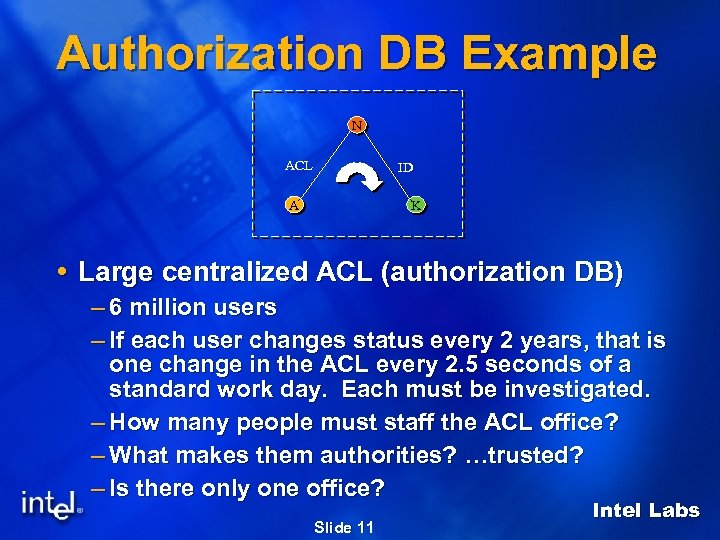 Authorization DB Example N ACL ID A K Large centralized ACL (authorization DB) – 6 million users – If each user changes status every 2 years, that is one change in the ACL every 2. 5 seconds of a standard work day. Each must be investigated. – How many people must staff the ACL office? – What makes them authorities? …trusted? – Is there only one office? Slide 11 Intel Labs
Authorization DB Example N ACL ID A K Large centralized ACL (authorization DB) – 6 million users – If each user changes status every 2 years, that is one change in the ACL every 2. 5 seconds of a standard work day. Each must be investigated. – How many people must staff the ACL office? – What makes them authorities? …trusted? – Is there only one office? Slide 11 Intel Labs
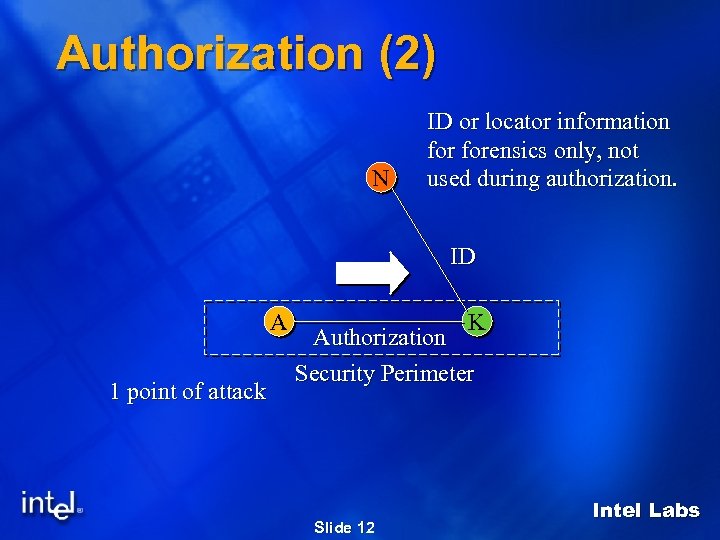 Authorization (2) N ID or locator information forensics only, not used during authorization. ID A 1 point of attack K Authorization Security Perimeter Slide 12 Intel Labs
Authorization (2) N ID or locator information forensics only, not used during authorization. ID A 1 point of attack K Authorization Security Perimeter Slide 12 Intel Labs
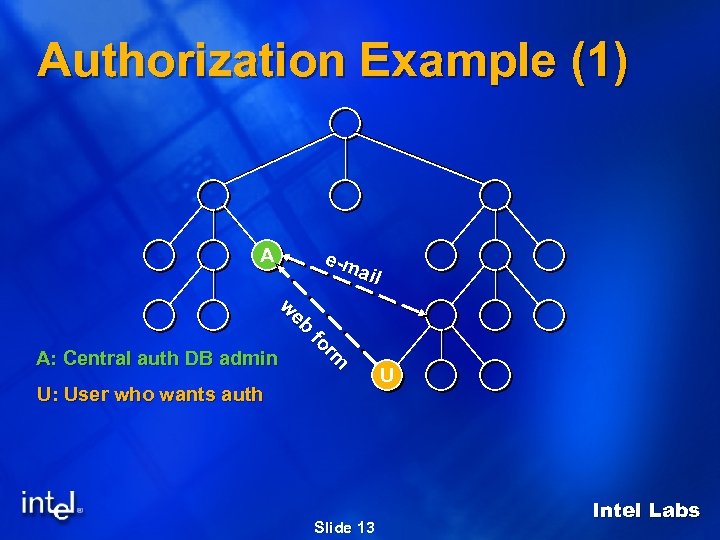 Authorization Example (1) A e-m ail eb eb w w m rm or ffo A: Central auth DB admin U: User who wants auth Slide 13 U Intel Labs
Authorization Example (1) A e-m ail eb eb w w m rm or ffo A: Central auth DB admin U: User who wants auth Slide 13 U Intel Labs
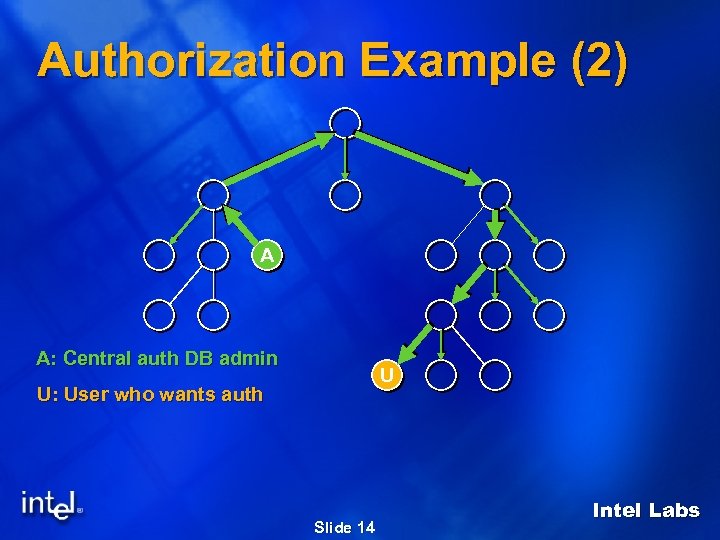 Authorization Example (2) A A: Central auth DB admin U U: User who wants auth Slide 14 Intel Labs
Authorization Example (2) A A: Central auth DB admin U U: User who wants auth Slide 14 Intel Labs
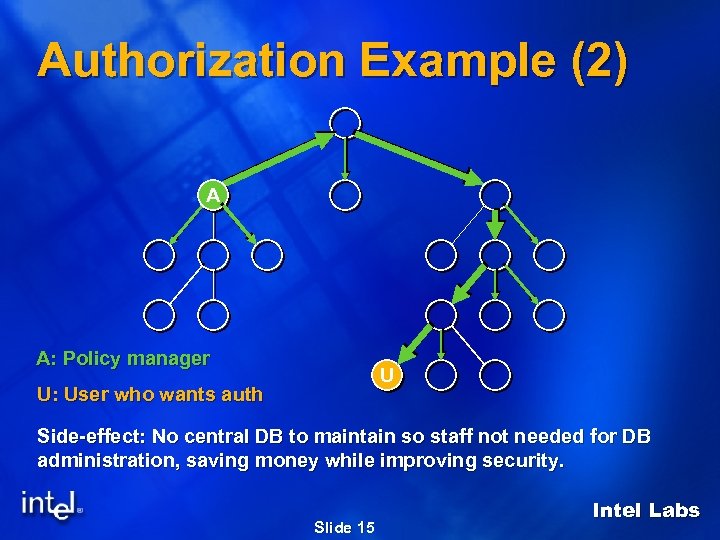 Authorization Example (2) A A: Policy manager U U: User who wants auth Side-effect: No central DB to maintain so staff not needed for DB administration, saving money while improving security. Slide 15 Intel Labs
Authorization Example (2) A A: Policy manager U U: User who wants auth Side-effect: No central DB to maintain so staff not needed for DB administration, saving money while improving security. Slide 15 Intel Labs
 Cross-company (1) Company A Company B appro val? req ues t Auth DB Staff Users who need auth Bridge two PKIs The John Wilson problem gets MUCH worse. – There are suddenly more John Wilsons than there were before. – There is no central naming authority with control over all PKIs. Access by A to B’s confidential information? (org chart; names) If A keeps a copy of a subset of B’s info, that’s dynamic & requires its own auth DB at A for updaters design recursion. If A accesses B data in place, that requires an auth DB at B. (ditto) Slide 16 Intel Labs
Cross-company (1) Company A Company B appro val? req ues t Auth DB Staff Users who need auth Bridge two PKIs The John Wilson problem gets MUCH worse. – There are suddenly more John Wilsons than there were before. – There is no central naming authority with control over all PKIs. Access by A to B’s confidential information? (org chart; names) If A keeps a copy of a subset of B’s info, that’s dynamic & requires its own auth DB at A for updaters design recursion. If A accesses B data in place, that requires an auth DB at B. (ditto) Slide 16 Intel Labs
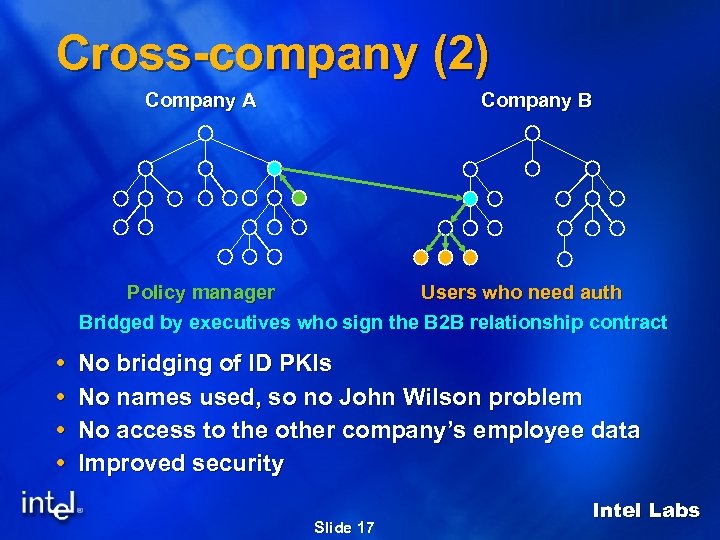 Cross-company (2) Company A Company B Policy manager Users who need auth Bridged by executives who sign the B 2 B relationship contract No bridging of ID PKIs No names used, so no John Wilson problem No access to the other company’s employee data Improved security Slide 17 Intel Labs
Cross-company (2) Company A Company B Policy manager Users who need auth Bridged by executives who sign the B 2 B relationship contract No bridging of ID PKIs No names used, so no John Wilson problem No access to the other company’s employee data Improved security Slide 17 Intel Labs
 References Dohrmann and Ellison, “Public Key Support for Collaborative Groups”, Internet 2 PKI Workshop, April 2002. Ellison, “Establishing Identity Without Certification Authorities”, 6 th USENIX Security Symposium, 1996. http: //developer. intel. com/ial/security/ http: //world. std. com/~cme/html/spki. html Slide 18 Intel Labs
References Dohrmann and Ellison, “Public Key Support for Collaborative Groups”, Internet 2 PKI Workshop, April 2002. Ellison, “Establishing Identity Without Certification Authorities”, 6 th USENIX Security Symposium, 1996. http: //developer. intel. com/ial/security/ http: //world. std. com/~cme/html/spki. html Slide 18 Intel Labs


