e704d91fdc255a78c1cbeb3692a4d951.ppt
- Количество слайдов: 21
 Implementing User Authentication for a State-wide Initiative Mary-Elise Haug INSPIRE System Administrato mehaug@incolsa. net
Implementing User Authentication for a State-wide Initiative Mary-Elise Haug INSPIRE System Administrato mehaug@incolsa. net
 Outline ¨ Overview of INSPIRE ¨ INSPIRE user authentication issues ¨ Using proxy servers for ISPs in Indiana ¨ Using digital certificates for national ISPs ¨ Interaction with sitesearch authentication
Outline ¨ Overview of INSPIRE ¨ INSPIRE user authentication issues ¨ Using proxy servers for ISPs in Indiana ¨ Using digital certificates for national ISPs ¨ Interaction with sitesearch authentication
 Overview: What is INSPIRE ¨ Indiana’s Virtual Library on the Internet Þ primarily collection of commercial databases that have contractual restrictions on use ¨ Part of the mission is “to ensure access to these information resources for all residents of all ages, in all walks of life … through Internet connected computers in homes, businesses, schools, and libraries.
Overview: What is INSPIRE ¨ Indiana’s Virtual Library on the Internet Þ primarily collection of commercial databases that have contractual restrictions on use ¨ Part of the mission is “to ensure access to these information resources for all residents of all ages, in all walks of life … through Internet connected computers in homes, businesses, schools, and libraries.
 Overview: Who are INSPIRE’s users ¨ All residents of Indiana ¨ Residents are not required to have a library card or any other institutional affiliation ¨ What separates INSPIRE from other statewide projects is having a user population based on geography rather than affiliation or pc location Þ we do not require libraries to authenticate their own patrons
Overview: Who are INSPIRE’s users ¨ All residents of Indiana ¨ Residents are not required to have a library card or any other institutional affiliation ¨ What separates INSPIRE from other statewide projects is having a user population based on geography rather than affiliation or pc location Þ we do not require libraries to authenticate their own patrons
 Authentication definitions ¨ Access -- the ability to use licensed databases ¨ Authorization -- providing a user access to restricted databases ¨ Authentication -- verifying that user is really who you think the user is
Authentication definitions ¨ Access -- the ability to use licensed databases ¨ Authorization -- providing a user access to restricted databases ¨ Authentication -- verifying that user is really who you think the user is
 Authentication issues ¨ Existing authentication methods assume that you know who your users are and may already have a database of users Þcomputers in library or school buildings Þdatabase of library users or students
Authentication issues ¨ Existing authentication methods assume that you know who your users are and may already have a database of users Þcomputers in library or school buildings Þdatabase of library users or students
 Authentication issues II ¨ Internet commerce solutions (ie users register themselves) Þmethods for registering users/creating maintaining db • easy to verify email address • accept users’ data for address – anyone that can figure out a valid zipcode for Indiana could gain access
Authentication issues II ¨ Internet commerce solutions (ie users register themselves) Þmethods for registering users/creating maintaining db • easy to verify email address • accept users’ data for address – anyone that can figure out a valid zipcode for Indiana could gain access
 Authentication issues III ¨ Two issues involved 1 how to verify residency 2 how to maintain information about authorized users ¨ Two different approaches 1 machine (pc) oriented 2 user oriented
Authentication issues III ¨ Two issues involved 1 how to verify residency 2 how to maintain information about authorized users ¨ Two different approaches 1 machine (pc) oriented 2 user oriented
 Authentication: pcs in Indiana ¨ Access Control (ACL) Þlist of ip addresses or domains used by Indiana institutions • . in. us ÞSurveyed libraries for initial list Þcommercial ISPs verified in ARIN when possible
Authentication: pcs in Indiana ¨ Access Control (ACL) Þlist of ip addresses or domains used by Indiana institutions • . in. us ÞSurveyed libraries for initial list Þcommercial ISPs verified in ARIN when possible
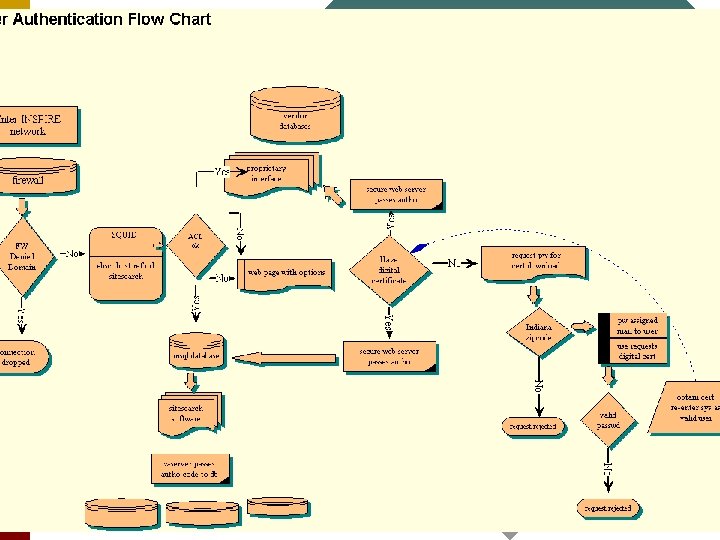
 Squid ¨ Use the squid proxy server as an http accelerator Þlistens on port 80 Þwill get db interface pages for ip/domains list in acl list Þredirects others to secure web server/access denied page
Squid ¨ Use the squid proxy server as an http accelerator Þlistens on port 80 Þwill get db interface pages for ip/domains list in acl list Þredirects others to secure web server/access denied page
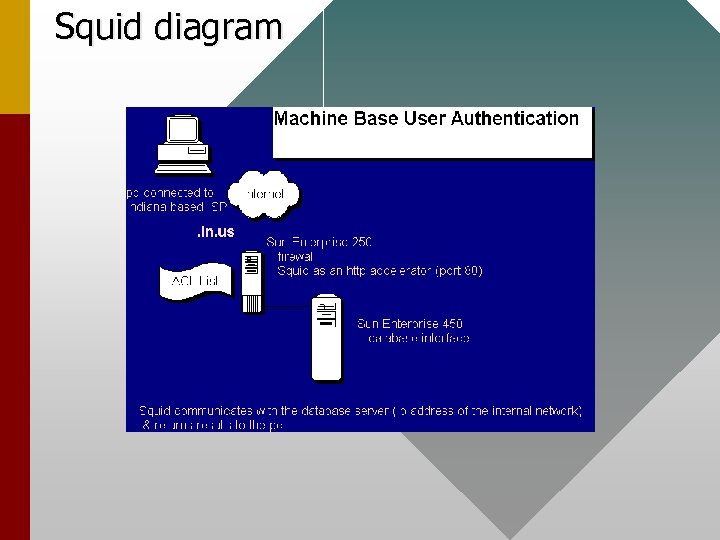 Squid diagram
Squid diagram
 Authentication: user based ¨ Evaluated alternatives Þ username/password vs. digital certificates ¨ Digital certificates chosen Þ new, innovative technology Þ easier to maintain then traditional db Þ possibility that certificates could deal with address verification
Authentication: user based ¨ Evaluated alternatives Þ username/password vs. digital certificates ¨ Digital certificates chosen Þ new, innovative technology Þ easier to maintain then traditional db Þ possibility that certificates could deal with address verification
 Authentication: user based Digital Certificate Implementation ¨ certs with address verification too costly ($10 each) & represented overkill for security needs ¨ using a CA (Verisign/Thawte) also involved considerable cost/potential for user to have to pay for a base certificate ¨ decided to become a CA and issue our own certificates • selected Netscape Certificate Server
Authentication: user based Digital Certificate Implementation ¨ certs with address verification too costly ($10 each) & represented overkill for security needs ¨ using a CA (Verisign/Thawte) also involved considerable cost/potential for user to have to pay for a base certificate ¨ decided to become a CA and issue our own certificates • selected Netscape Certificate Server
 Authentication: user based Verify residency ¨ no high tech solutions seemed to meet our needs or fit in within budget parameters ¨ decided to mail a one time use password ¨ the password would allow users to request a digital certificate ¨ digital certificates would expire, forcing user to have address re-checked
Authentication: user based Verify residency ¨ no high tech solutions seemed to meet our needs or fit in within budget parameters ¨ decided to mail a one time use password ¨ the password would allow users to request a digital certificate ¨ digital certificates would expire, forcing user to have address re-checked
 Authentication: user based How it works ¨ User fills out registration form ¨ password is assigned ¨ mailed to user in a secure self mailer ¨ user enters valid password ¨ access to digital certificate server granted ¨ user requests & downloads certificate ¨ links to database interfaces available through secure web server which requires a valid certificate
Authentication: user based How it works ¨ User fills out registration form ¨ password is assigned ¨ mailed to user in a secure self mailer ¨ user enters valid password ¨ access to digital certificate server granted ¨ user requests & downloads certificate ¨ links to database interfaces available through secure web server which requires a valid certificate
 Authentication: Secure Web Server ¨ Use Stronghold -- chose this option to avoid dealing with encryption law ¨ Set up to check for a digital certificate issued by INSPIRE CA ¨ As digital certs gain in popularity could check state=IN for Indiana residents ¨ Using as a proxy yields a lot of overhead, so current pass an autho/pw
Authentication: Secure Web Server ¨ Use Stronghold -- chose this option to avoid dealing with encryption law ¨ Set up to check for a digital certificate issued by INSPIRE CA ¨ As digital certs gain in popularity could check state=IN for Indiana residents ¨ Using as a proxy yields a lot of overhead, so current pass an autho/pw
 Downside of Digital Certificates ¨ Difficulty downloading certificates Þ AOL users Þ process intimidating Þ implemented differently in Netscape and IE ¨ Free toolkits underdeveloped Þ examples only work with Netscape ¨ Prices for commercial products increased dramatically in the last 18 months ¨ When act as a CA the server certificate isn’t built in to the browser
Downside of Digital Certificates ¨ Difficulty downloading certificates Þ AOL users Þ process intimidating Þ implemented differently in Netscape and IE ¨ Free toolkits underdeveloped Þ examples only work with Netscape ¨ Prices for commercial products increased dramatically in the last 18 months ¨ When act as a CA the server certificate isn’t built in to the browser
 Interaction with Site. Search Authentication ¨ With Squid all users appear to come from an internal ip address, which is in msql db ¨ With the secure web server have used it as a proxy or have passed a username/pw embedded in a php script
Interaction with Site. Search Authentication ¨ With Squid all users appear to come from an internal ip address, which is in msql db ¨ With the secure web server have used it as a proxy or have passed a username/pw embedded in a php script
 Interaction with Site. Search Authentication ¨ Downside is that cannot track users based on an individual library ¨ Authentication scheme will need modification which will involve entering library ip addresses in msql db and use squid to redirect users to sitesearch port ¨ Potential to include an institutional field in the digital certificate exists
Interaction with Site. Search Authentication ¨ Downside is that cannot track users based on an individual library ¨ Authentication scheme will need modification which will involve entering library ip addresses in msql db and use squid to redirect users to sitesearch port ¨ Potential to include an institutional field in the digital certificate exists
 Summary ¨ Authentication most challenging aspect of setting up INSPIRE system ¨ Requires continuous staff attention Þinstitutions change ISPs/set up firewalls or proxies that change authentication Þhelping users with digital certificates ¨ Still have not developed the optimum solution ÞDoes that magic solution exist ?
Summary ¨ Authentication most challenging aspect of setting up INSPIRE system ¨ Requires continuous staff attention Þinstitutions change ISPs/set up firewalls or proxies that change authentication Þhelping users with digital certificates ¨ Still have not developed the optimum solution ÞDoes that magic solution exist ?


