71f1f5e6368e541d0babc5d9540223d7.ppt
- Количество слайдов: 28
 Implementing Network Security Level 250 Sandeep Modhvadia Security Technical Specialist http: //blogs. msdn. com/sandeepm deep@microsoft. com
Implementing Network Security Level 250 Sandeep Modhvadia Security Technical Specialist http: //blogs. msdn. com/sandeepm deep@microsoft. com
 Agenda PKI Overview Secure Remote Access Secure Wireless Segmentation via IPsec Application Layer Firewalling
Agenda PKI Overview Secure Remote Access Secure Wireless Segmentation via IPsec Application Layer Firewalling
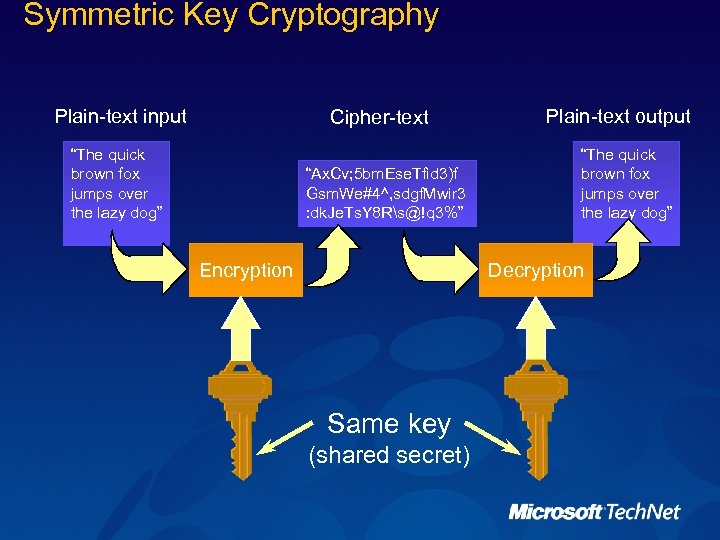 Symmetric Key Cryptography Plain-text input Cipher-text “The quick brown fox jumps over the lazy dog” “Ax. Cv; 5 bm. Ese. Tfid 3)f Gsm. We#4^, sdgf. Mwir 3 : dk. Je. Ts. Y 8 Rs@!q 3%” Encryption Plain-text output “The quick brown fox jumps over the lazy dog” Decryption Same key (shared secret)
Symmetric Key Cryptography Plain-text input Cipher-text “The quick brown fox jumps over the lazy dog” “Ax. Cv; 5 bm. Ese. Tfid 3)f Gsm. We#4^, sdgf. Mwir 3 : dk. Je. Ts. Y 8 Rs@!q 3%” Encryption Plain-text output “The quick brown fox jumps over the lazy dog” Decryption Same key (shared secret)
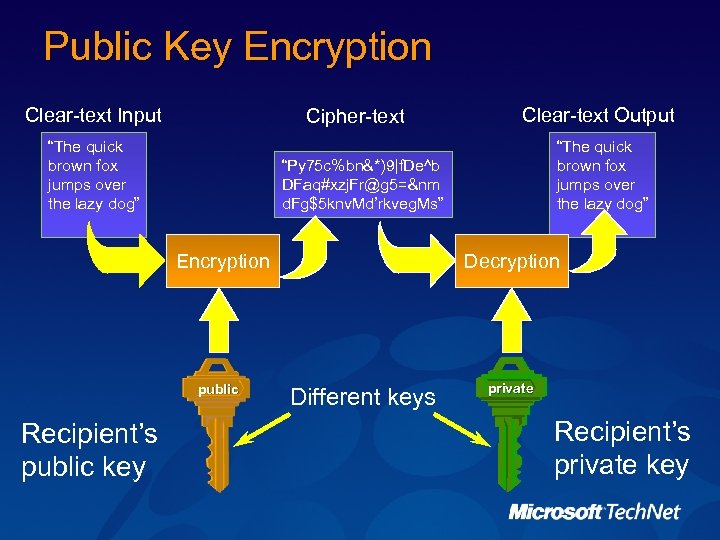 Public Key Encryption Clear-text Input Cipher-text “The quick brown fox jumps over the lazy dog” “Py 75 c%bn&*)9|f. De^b DFaq#xzj. Fr@g 5=&nm d. Fg$5 knv. Md’rkveg. Ms” Encryption public Recipient’s public key Clear-text Output Decryption Different keys private Recipient’s private key
Public Key Encryption Clear-text Input Cipher-text “The quick brown fox jumps over the lazy dog” “Py 75 c%bn&*)9|f. De^b DFaq#xzj. Fr@g 5=&nm d. Fg$5 knv. Md’rkveg. Ms” Encryption public Recipient’s public key Clear-text Output Decryption Different keys private Recipient’s private key
 Public Key Pros and Cons Weakness: Extremely slow Susceptible to “known ciphertext” attack Problem of trusting public key (see later on PKI) Strength Solves problem of passing the key Allows establishment of trust context between parties
Public Key Pros and Cons Weakness: Extremely slow Susceptible to “known ciphertext” attack Problem of trusting public key (see later on PKI) Strength Solves problem of passing the key Allows establishment of trust context between parties
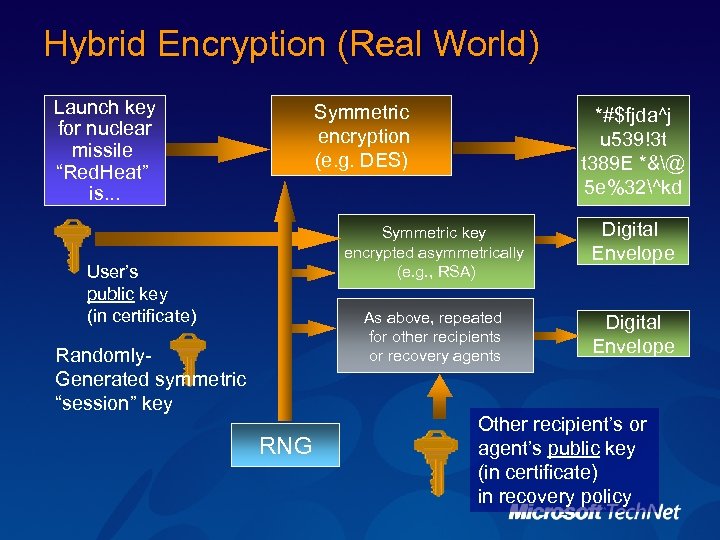 Hybrid Encryption (Real World) Launch key for nuclear missile “Red. Heat” is. . . Symmetric encryption (e. g. DES) *#$fjda^j u 539!3 t t 389 E *&@ 5 e%32^kd Symmetric key encrypted asymmetrically (e. g. , RSA) As above, repeated for other recipients or recovery agents User’s public key (in certificate) Randomly. Generated symmetric “session” key RNG Digital Envelope Other recipient’s or agent’s public key (in certificate) in recovery policy
Hybrid Encryption (Real World) Launch key for nuclear missile “Red. Heat” is. . . Symmetric encryption (e. g. DES) *#$fjda^j u 539!3 t t 389 E *&@ 5 e%32^kd Symmetric key encrypted asymmetrically (e. g. , RSA) As above, repeated for other recipients or recovery agents User’s public key (in certificate) Randomly. Generated symmetric “session” key RNG Digital Envelope Other recipient’s or agent’s public key (in certificate) in recovery policy
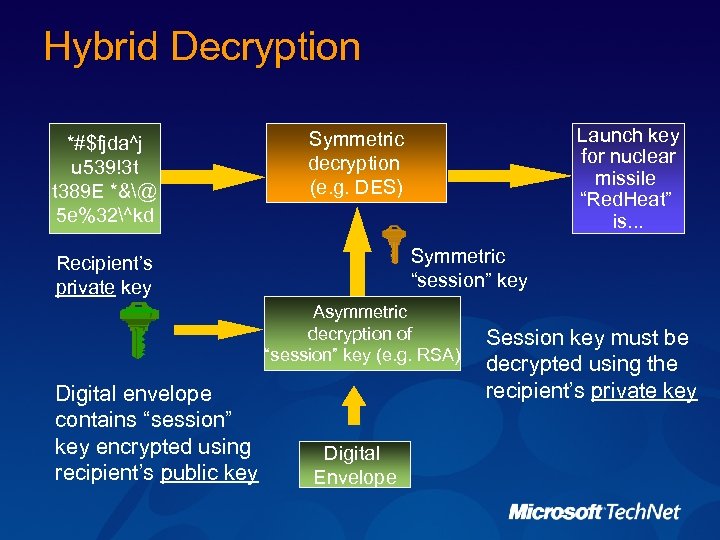 Hybrid Decryption *#$fjda^j u 539!3 t t 389 E *&@ 5 e%32^kd Launch key for nuclear missile “Red. Heat” is. . . Symmetric decryption (e. g. DES) Symmetric “session” key Recipient’s private key Asymmetric decryption of “session” key (e. g. RSA) Digital envelope contains “session” key encrypted using recipient’s public key Digital Envelope Session key must be decrypted using the recipient’s private key
Hybrid Decryption *#$fjda^j u 539!3 t t 389 E *&@ 5 e%32^kd Launch key for nuclear missile “Red. Heat” is. . . Symmetric decryption (e. g. DES) Symmetric “session” key Recipient’s private key Asymmetric decryption of “session” key (e. g. RSA) Digital envelope contains “session” key encrypted using recipient’s public key Digital Envelope Session key must be decrypted using the recipient’s private key
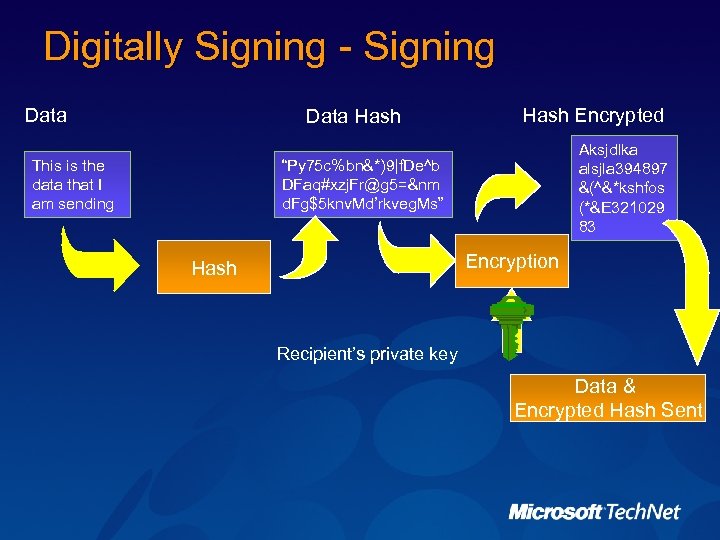 Digitally Signing - Signing Data Hash This is the data that I am sending Hash Encrypted Aksjdlka alsjla 394897 &(^&*kshfos (*&E 321029 83 “Py 75 c%bn&*)9|f. De^b DFaq#xzj. Fr@g 5=&nm d. Fg$5 knv. Md’rkveg. Ms” Encryption Hash Recipient’s private key Data & Encrypted Hash Sent
Digitally Signing - Signing Data Hash This is the data that I am sending Hash Encrypted Aksjdlka alsjla 394897 &(^&*kshfos (*&E 321029 83 “Py 75 c%bn&*)9|f. De^b DFaq#xzj. Fr@g 5=&nm d. Fg$5 knv. Md’rkveg. Ms” Encryption Hash Recipient’s private key Data & Encrypted Hash Sent
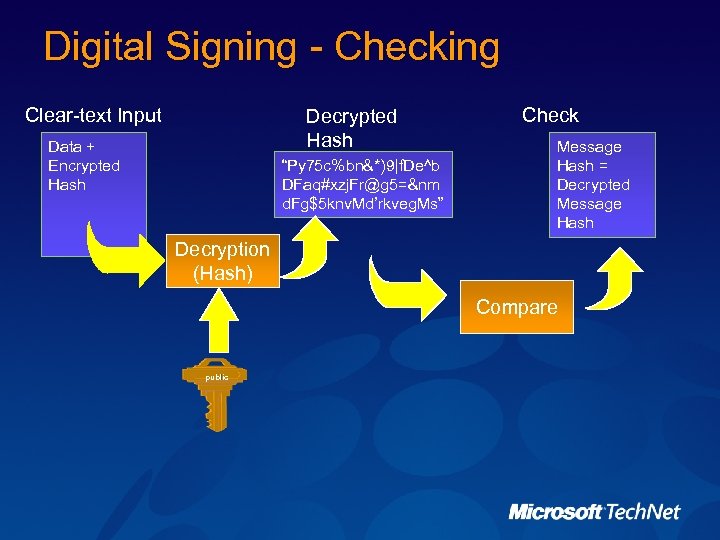 Digital Signing - Checking Clear-text Input Decrypted Hash Data + Encrypted Hash “Py 75 c%bn&*)9|f. De^b DFaq#xzj. Fr@g 5=&nm d. Fg$5 knv. Md’rkveg. Ms” Check Message Hash = Decrypted Message Hash Decryption (Hash) Compare public
Digital Signing - Checking Clear-text Input Decrypted Hash Data + Encrypted Hash “Py 75 c%bn&*)9|f. De^b DFaq#xzj. Fr@g 5=&nm d. Fg$5 knv. Md’rkveg. Ms” Check Message Hash = Decrypted Message Hash Decryption (Hash) Compare public
 Key Thoughts How do you design a PKI? By Geography? By PK Function? By Administration Internal or External? How Many Certificates Usage Times
Key Thoughts How do you design a PKI? By Geography? By PK Function? By Administration Internal or External? How Many Certificates Usage Times
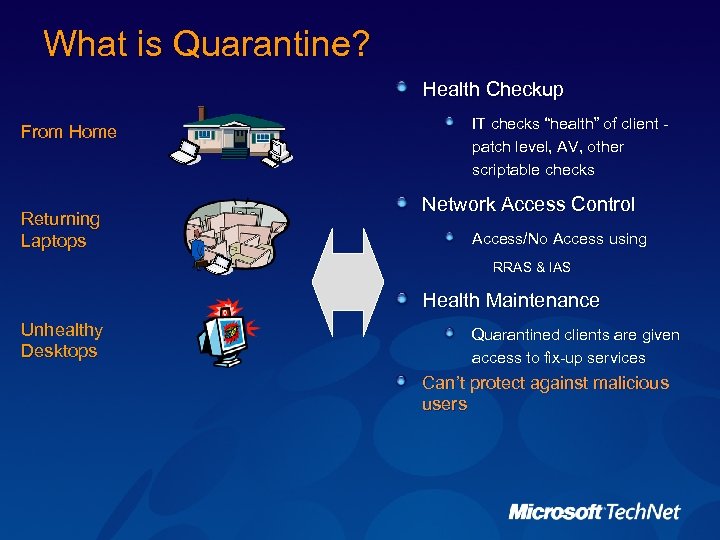 What is Quarantine? Health Checkup From Home Returning Laptops IT checks “health” of client patch level, AV, other scriptable checks Network Access Control Access/No Access using RRAS & IAS Health Maintenance Unhealthy Desktops Quarantined clients are given access to fix-up services Can’t protect against malicious users
What is Quarantine? Health Checkup From Home Returning Laptops IT checks “health” of client patch level, AV, other scriptable checks Network Access Control Access/No Access using RRAS & IAS Health Maintenance Unhealthy Desktops Quarantined clients are given access to fix-up services Can’t protect against malicious users
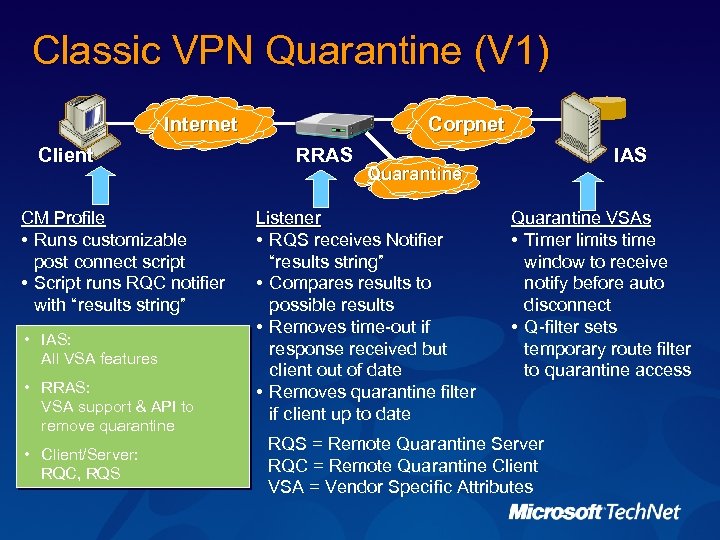 Classic VPN Quarantine (V 1) Internet Client CM Profile • Runs customizable post connect script • Script runs RQC notifier with “results string” • IAS: All VSA features • RRAS: VSA support & API to remove quarantine • Client/Server: RQC, RQS Corpnet RRAS IAS Quarantine Listener • RQS receives Notifier “results string” • Compares results to possible results • Removes time-out if response received but client out of date • Removes quarantine filter if client up to date Quarantine VSAs • Timer limits time window to receive notify before auto disconnect • Q-filter sets temporary route filter to quarantine access RQS = Remote Quarantine Server RQC = Remote Quarantine Client VSA = Vendor Specific Attributes
Classic VPN Quarantine (V 1) Internet Client CM Profile • Runs customizable post connect script • Script runs RQC notifier with “results string” • IAS: All VSA features • RRAS: VSA support & API to remove quarantine • Client/Server: RQC, RQS Corpnet RRAS IAS Quarantine Listener • RQS receives Notifier “results string” • Compares results to possible results • Removes time-out if response received but client out of date • Removes quarantine filter if client up to date Quarantine VSAs • Timer limits time window to receive notify before auto disconnect • Q-filter sets temporary route filter to quarantine access RQS = Remote Quarantine Server RQC = Remote Quarantine Client VSA = Vendor Specific Attributes
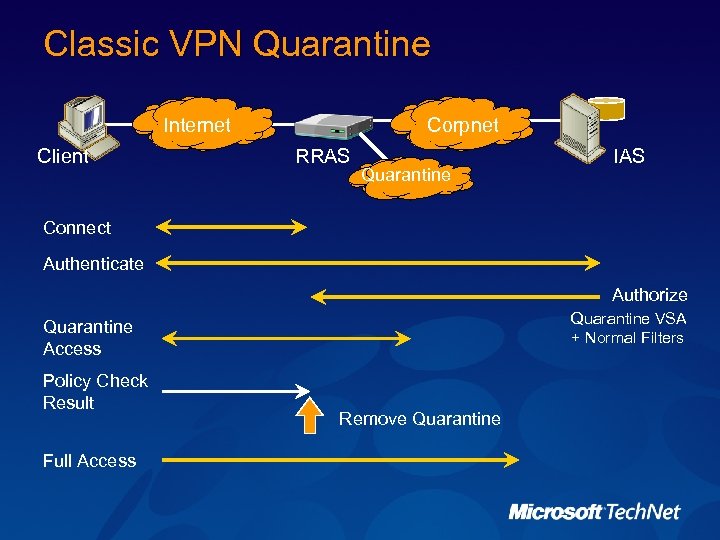 Classic VPN Quarantine Internet Client Corpnet RRAS Quarantine IAS Connect Authenticate Authorize Quarantine VSA + Normal Filters Quarantine Access Policy Check Result Full Access Remove Quarantine
Classic VPN Quarantine Internet Client Corpnet RRAS Quarantine IAS Connect Authenticate Authorize Quarantine VSA + Normal Filters Quarantine Access Policy Check Result Full Access Remove Quarantine
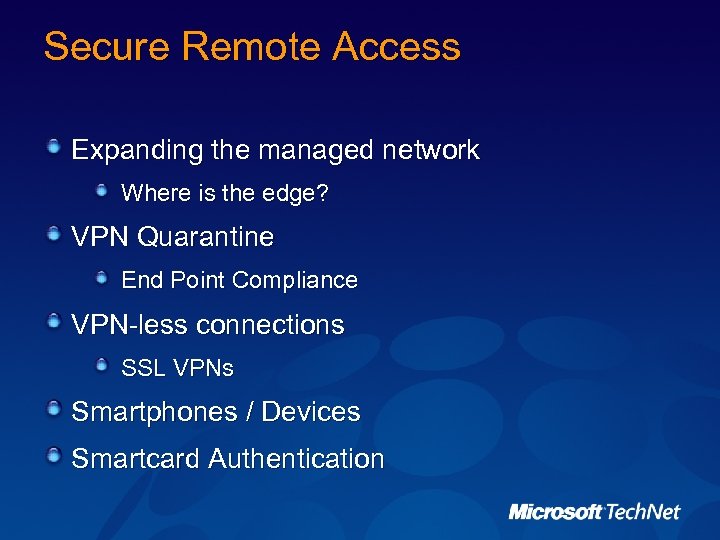 Secure Remote Access Expanding the managed network Where is the edge? VPN Quarantine End Point Compliance VPN-less connections SSL VPNs Smartphones / Devices Smartcard Authentication
Secure Remote Access Expanding the managed network Where is the edge? VPN Quarantine End Point Compliance VPN-less connections SSL VPNs Smartphones / Devices Smartcard Authentication
 Secure Wireless Basics Shifting the entry barrier Key themes Security Management Usability
Secure Wireless Basics Shifting the entry barrier Key themes Security Management Usability
 Security Best Practices What NOT to do Hidden SSID Does not provide any real security Easily discoverable in well-used environments Windows client experience is impacted MAC Filtering Does not scale NIC management issue MAC is spoofable “Shared” mode Sounds like more security but is actually worse Not to be confused with Pre-Shared Key (PSK) which is more secure Open networks and VPN’s Grants everyone access to the wireless segment Great for hotspots, not for your business
Security Best Practices What NOT to do Hidden SSID Does not provide any real security Easily discoverable in well-used environments Windows client experience is impacted MAC Filtering Does not scale NIC management issue MAC is spoofable “Shared” mode Sounds like more security but is actually worse Not to be confused with Pre-Shared Key (PSK) which is more secure Open networks and VPN’s Grants everyone access to the wireless segment Great for hotspots, not for your business
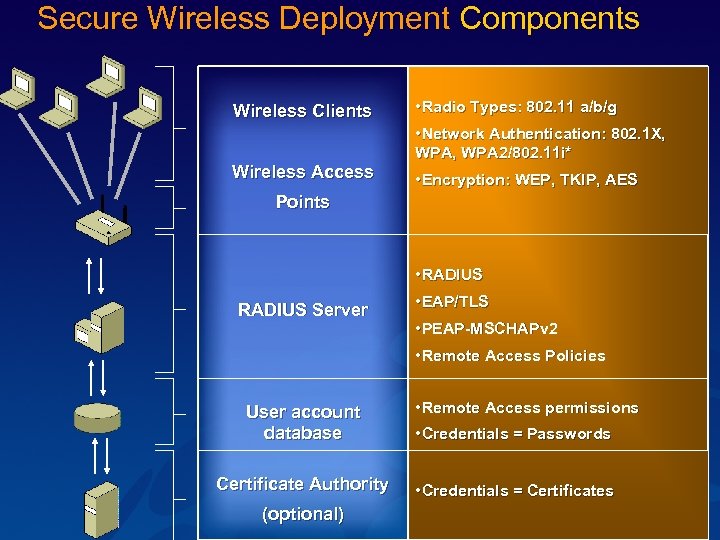 Secure Wireless Deployment Components Wireless Clients Wireless Access • Radio Types: 802. 11 a/b/g • Network Authentication: 802. 1 X, WPA 2/802. 11 i* • Encryption: WEP, TKIP, AES Points RADIUS Server User account database Certificate Authority (optional) • RADIUS • EAP/TLS • PEAP-MSCHAPv 2 • Remote Access Policies • Remote Access permissions • Credentials = Passwords • Credentials = Certificates
Secure Wireless Deployment Components Wireless Clients Wireless Access • Radio Types: 802. 11 a/b/g • Network Authentication: 802. 1 X, WPA 2/802. 11 i* • Encryption: WEP, TKIP, AES Points RADIUS Server User account database Certificate Authority (optional) • RADIUS • EAP/TLS • PEAP-MSCHAPv 2 • Remote Access Policies • Remote Access permissions • Credentials = Passwords • Credentials = Certificates
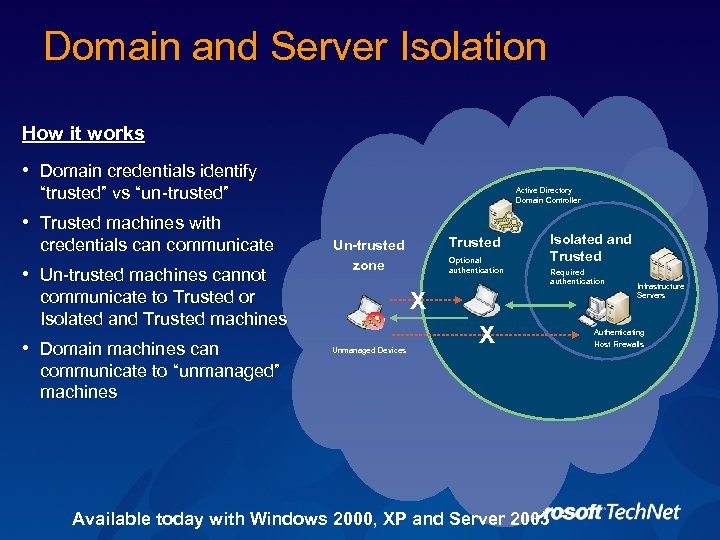 Domain and Server Isolation How it works • Domain credentials identify “trusted” vs “un-trusted” Active Directory Domain Controller • Trusted machines with credentials can communicate • Un-trusted machines cannot communicate to Trusted or Isolated and Trusted machines • Domain machines can Trusted Un-trusted zone Optional authentication Isolated and Trusted Required authentication X Unmanaged Devices X communicate to “unmanaged” machines Available today with Windows 2000, XP and Server 2003 Infrastructure Servers Authenticating Host Firewalls
Domain and Server Isolation How it works • Domain credentials identify “trusted” vs “un-trusted” Active Directory Domain Controller • Trusted machines with credentials can communicate • Un-trusted machines cannot communicate to Trusted or Isolated and Trusted machines • Domain machines can Trusted Un-trusted zone Optional authentication Isolated and Trusted Required authentication X Unmanaged Devices X communicate to “unmanaged” machines Available today with Windows 2000, XP and Server 2003 Infrastructure Servers Authenticating Host Firewalls
 Threats That IPsec Mitigates: Tampering with data in transit Unauthenticated access to trusted systems Including worm propagation from untrusted systems Man-in-the-middle attacks Spoofing Eavesdropping on network traffic And others….
Threats That IPsec Mitigates: Tampering with data in transit Unauthenticated access to trusted systems Including worm propagation from untrusted systems Man-in-the-middle attacks Spoofing Eavesdropping on network traffic And others….
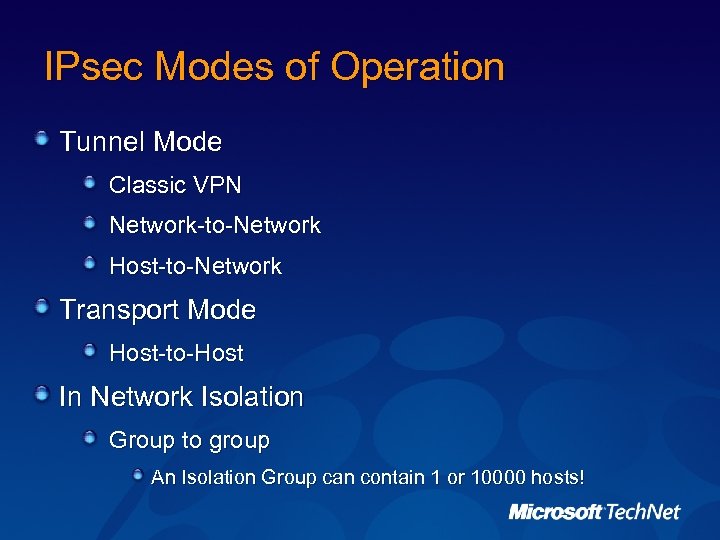 IPsec Modes of Operation Tunnel Mode Classic VPN Network-to-Network Host-to-Network Transport Mode Host-to-Host In Network Isolation Group to group An Isolation Group can contain 1 or 10000 hosts!
IPsec Modes of Operation Tunnel Mode Classic VPN Network-to-Network Host-to-Network Transport Mode Host-to-Host In Network Isolation Group to group An Isolation Group can contain 1 or 10000 hosts!
 Methods for IPsec Protection AH Mutual authentication of endpoints End-to-end IP header integrity Will not traverse a NAT device ESP Mutual authentication of endpoints Option to use encryption Will traverse a NAT device
Methods for IPsec Protection AH Mutual authentication of endpoints End-to-end IP header integrity Will not traverse a NAT device ESP Mutual authentication of endpoints Option to use encryption Will traverse a NAT device
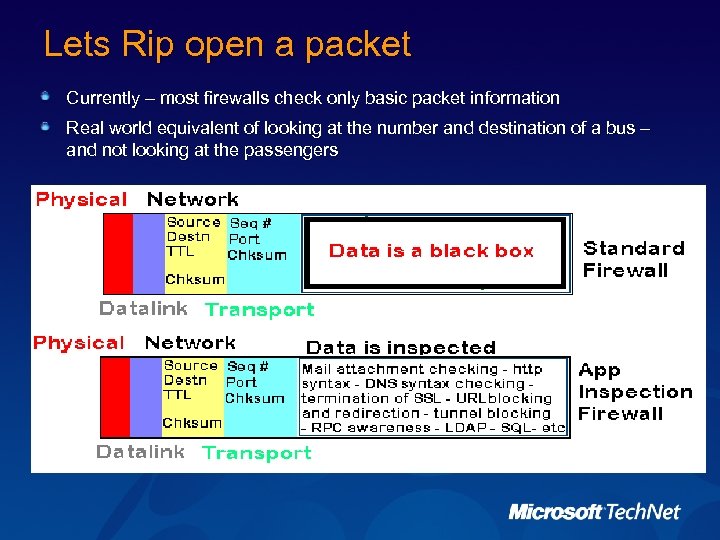 Lets Rip open a packet Currently – most firewalls check only basic packet information Real world equivalent of looking at the number and destination of a bus – and not looking at the passengers
Lets Rip open a packet Currently – most firewalls check only basic packet information Real world equivalent of looking at the number and destination of a bus – and not looking at the passengers
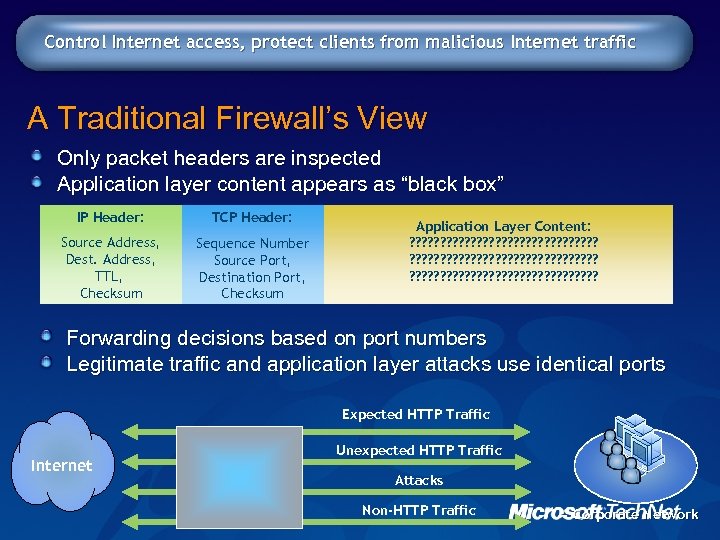 Control Internet access, protect clients from malicious Internet traffic A Traditional Firewall’s View Only packet headers are inspected Application layer content appears as “black box” IP Header: TCP Header: Source Address, Dest. Address, TTL, Checksum Sequence Number Source Port, Destination Port, Checksum Application Layer Content: ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? Forwarding decisions based on port numbers Legitimate traffic and application layer attacks use identical ports Expected HTTP Traffic Internet Unexpected HTTP Traffic Attacks Non-HTTP Traffic Corporate Network
Control Internet access, protect clients from malicious Internet traffic A Traditional Firewall’s View Only packet headers are inspected Application layer content appears as “black box” IP Header: TCP Header: Source Address, Dest. Address, TTL, Checksum Sequence Number Source Port, Destination Port, Checksum Application Layer Content: ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? Forwarding decisions based on port numbers Legitimate traffic and application layer attacks use identical ports Expected HTTP Traffic Internet Unexpected HTTP Traffic Attacks Non-HTTP Traffic Corporate Network
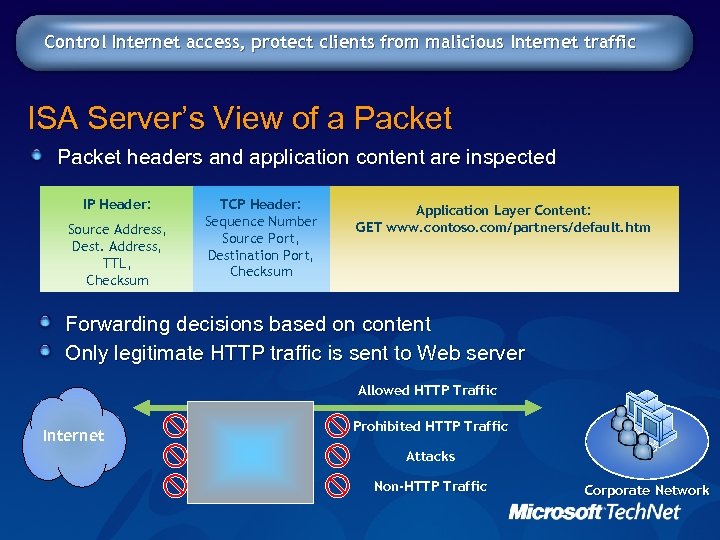 Control Internet access, protect clients from malicious Internet traffic ISA Server’s View of a Packet headers and application content are inspected IP Header: Source Address, Dest. Address, TTL, Checksum TCP Header: Sequence Number Source Port, Destination Port, Checksum Application Layer Content: GET www. contoso. com/partners/default. htm Forwarding decisions based on content Only legitimate HTTP traffic is sent to Web server Allowed HTTP Traffic Internet Prohibited HTTP Traffic Attacks Non-HTTP Traffic Corporate Network
Control Internet access, protect clients from malicious Internet traffic ISA Server’s View of a Packet headers and application content are inspected IP Header: Source Address, Dest. Address, TTL, Checksum TCP Header: Sequence Number Source Port, Destination Port, Checksum Application Layer Content: GET www. contoso. com/partners/default. htm Forwarding decisions based on content Only legitimate HTTP traffic is sent to Web server Allowed HTTP Traffic Internet Prohibited HTTP Traffic Attacks Non-HTTP Traffic Corporate Network
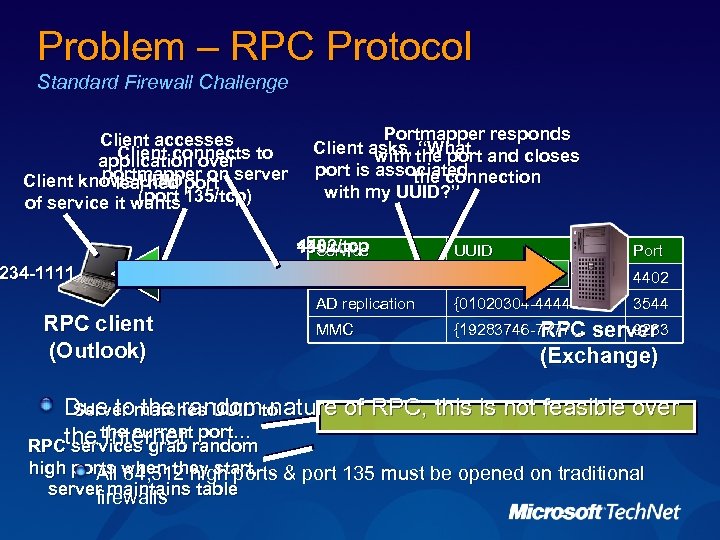 Problem – RPC Protocol Standard Firewall Challenge Client accesses Client connects application over to portmapper on Client knows UUID port server learned (port of service it wants 135/tcp) Portmapper responds Client asks, the port and closes with “What port is associated the connection with my UUID? ” 4402/tcp 135/tcp Service 234 -1111…} RPC client (Outlook) UUID Port Exchange 4402/tcp {1234 -1111… 4402 AD replication {01020304 -4444… 3544 MMC {19283746 -7777… server 9233 RPC (Exchange) Due tomatches UUID to Server the random nature of RPC, this is not feasible over the currentrandom Internet port… RPC services grab high ports when they start, & port 135 must be opened on traditional All 64, 512 high ports server maintains table firewalls
Problem – RPC Protocol Standard Firewall Challenge Client accesses Client connects application over to portmapper on Client knows UUID port server learned (port of service it wants 135/tcp) Portmapper responds Client asks, the port and closes with “What port is associated the connection with my UUID? ” 4402/tcp 135/tcp Service 234 -1111…} RPC client (Outlook) UUID Port Exchange 4402/tcp {1234 -1111… 4402 AD replication {01020304 -4444… 3544 MMC {19283746 -7777… server 9233 RPC (Exchange) Due tomatches UUID to Server the random nature of RPC, this is not feasible over the currentrandom Internet port… RPC services grab high ports when they start, & port 135 must be opened on traditional All 64, 512 high ports server maintains table firewalls
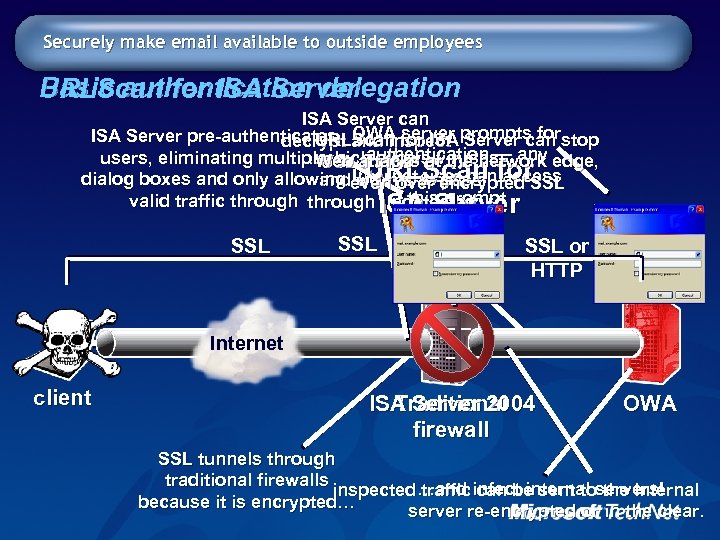 Securely make email available to outside employees Basic authentication delegation URLScan for ISA Server can ISA Server pre-authenticates and inspect prompts forstop URLScan server decrypt OWA for ISA Server can authentication — users, eliminating multiple …which allows viruses any edge, Web attacks at the network SSL traffic URLScan dialog boxes and only allowing even over encrypted SSL and Internet to pass for worms user can access this prompt valid traffic through ISA Server undetected… SSL SSL or HTTP Internet client Traditional ISA Server 2004 firewall OWA SSL tunnels through traditional firewalls inspected …and infect internal servers! traffic can be sent to the internal because it is encrypted… server re-encrypted or in the clear.
Securely make email available to outside employees Basic authentication delegation URLScan for ISA Server can ISA Server pre-authenticates and inspect prompts forstop URLScan server decrypt OWA for ISA Server can authentication — users, eliminating multiple …which allows viruses any edge, Web attacks at the network SSL traffic URLScan dialog boxes and only allowing even over encrypted SSL and Internet to pass for worms user can access this prompt valid traffic through ISA Server undetected… SSL SSL or HTTP Internet client Traditional ISA Server 2004 firewall OWA SSL tunnels through traditional firewalls inspected …and infect internal servers! traffic can be sent to the internal because it is encrypted… server re-encrypted or in the clear.
 Event Information What’s Next? Technical Roadshow Post Event Website www. microsoft. com/uk/techroadshow/postevents Available from Monday 18 th April Please complete your Evaluation Forms
Event Information What’s Next? Technical Roadshow Post Event Website www. microsoft. com/uk/techroadshow/postevents Available from Monday 18 th April Please complete your Evaluation Forms
 © 2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.
© 2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.


