0eee0513bb24126347e32dd5f10c7911.ppt
- Количество слайдов: 63
 Implementing Network and Perimeter Security
Implementing Network and Perimeter Security
 Prerequisite Knowledge u u u Understanding of network security essentials Hands-on experience with Windows® 2000 Server or Windows Server™ 2003 Experience with Windows management tools Level 300
Prerequisite Knowledge u u u Understanding of network security essentials Hands-on experience with Windows® 2000 Server or Windows Server™ 2003 Experience with Windows management tools Level 300
 Agenda u u u Introduction Using Perimeter Defenses Using Microsoft® Internet Security and Acceleration (ISA) Server to Protect Perimeters Using Internet Connection Firewall (ICF) to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
Agenda u u u Introduction Using Perimeter Defenses Using Microsoft® Internet Security and Acceleration (ISA) Server to Protect Perimeters Using Internet Connection Firewall (ICF) to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
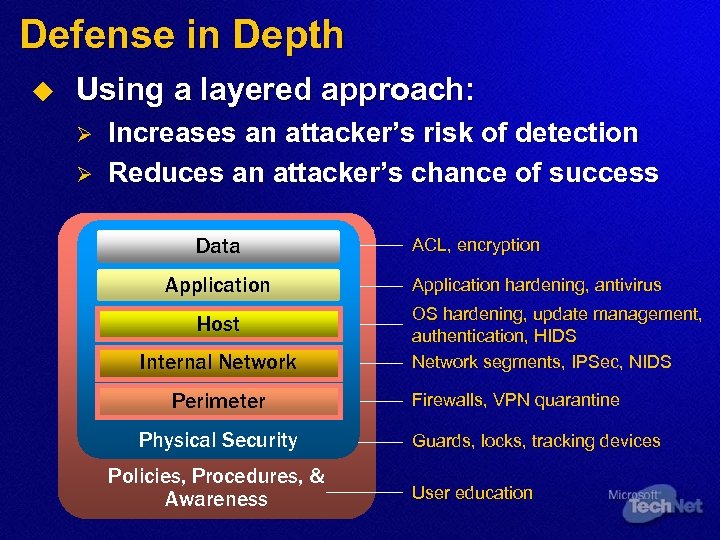 Defense in Depth u Using a layered approach: Ø Ø Increases an attacker’s risk of detection Reduces an attacker’s chance of success Data Application Host Internal Network Perimeter Physical Security Policies, Procedures, & Awareness ACL, encryption Application hardening, antivirus OS hardening, update management, authentication, HIDS Network segments, IPSec, NIDS Firewalls, VPN quarantine Guards, locks, tracking devices User education
Defense in Depth u Using a layered approach: Ø Ø Increases an attacker’s risk of detection Reduces an attacker’s chance of success Data Application Host Internal Network Perimeter Physical Security Policies, Procedures, & Awareness ACL, encryption Application hardening, antivirus OS hardening, update management, authentication, HIDS Network segments, IPSec, NIDS Firewalls, VPN quarantine Guards, locks, tracking devices User education
 Purpose and Limitations of Perimeter Defenses u u u Properly configured firewalls and border routers are the cornerstone for perimeter security The Internet and mobility increase security risks VPNs have softened the perimeter and, along with wireless networking, have essentially caused the disappearance of the traditional concept of network perimeter Traditional packet-filtering firewalls block only network ports and computer addresses Most modern attacks occur at the application layer
Purpose and Limitations of Perimeter Defenses u u u Properly configured firewalls and border routers are the cornerstone for perimeter security The Internet and mobility increase security risks VPNs have softened the perimeter and, along with wireless networking, have essentially caused the disappearance of the traditional concept of network perimeter Traditional packet-filtering firewalls block only network ports and computer addresses Most modern attacks occur at the application layer
 Purpose and Limitations of Client Defenses u u Client defenses block attacks that bypass perimeter defenses or originate on the internal network Client defenses include, among others: u Operating system hardening u Antivirus software u Personal firewalls Client defenses require configuring many computers In unmanaged environments, users may bypass client defenses
Purpose and Limitations of Client Defenses u u Client defenses block attacks that bypass perimeter defenses or originate on the internal network Client defenses include, among others: u Operating system hardening u Antivirus software u Personal firewalls Client defenses require configuring many computers In unmanaged environments, users may bypass client defenses
 Purpose and Limitations of Intrusion Detection u u Detects the pattern of common attacks, records suspicious traffic in event logs, and/or alerts administrators Threats and vulnerabilities are constantly evolving, which leaves systems vulnerable until a new attack is known and a new signature is created and distributed
Purpose and Limitations of Intrusion Detection u u Detects the pattern of common attacks, records suspicious traffic in event logs, and/or alerts administrators Threats and vulnerabilities are constantly evolving, which leaves systems vulnerable until a new attack is known and a new signature is created and distributed
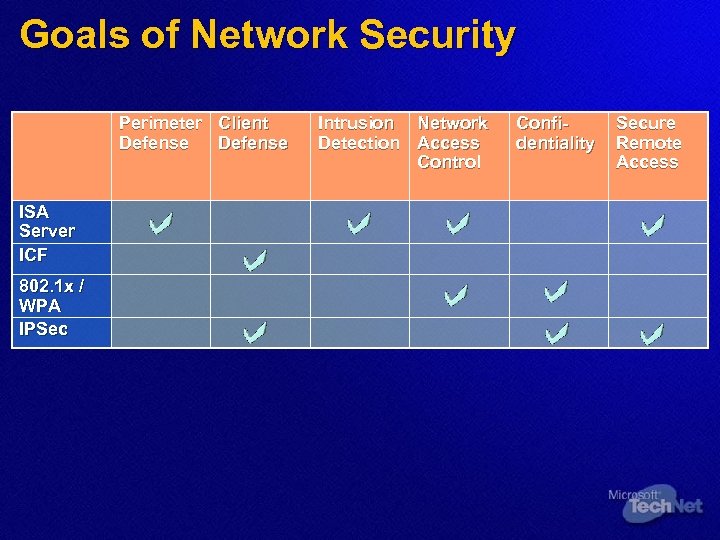 Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Network Detection Access Control Confidentiality Secure Remote Access
Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Network Detection Access Control Confidentiality Secure Remote Access
 Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
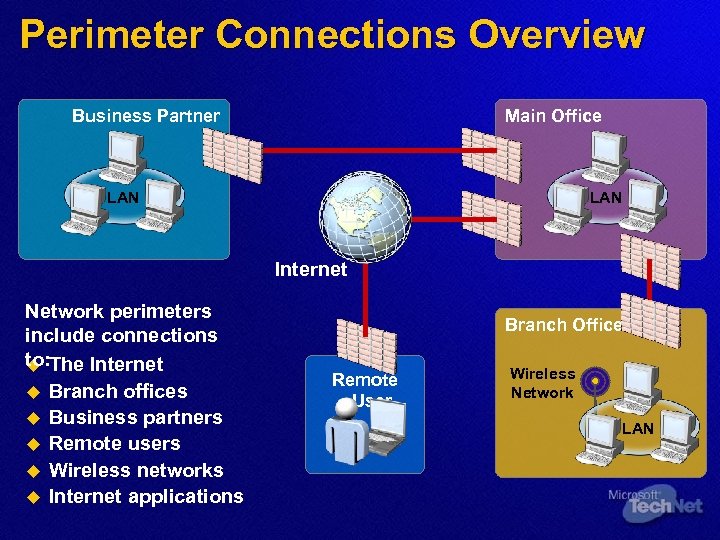 Perimeter Connections Overview Business Partner Main Office LAN Internet Network perimeters include connections to: The Internet u u Branch offices u Business partners u Remote users u Wireless networks u Internet applications Branch Office Remote User Wireless Network LAN
Perimeter Connections Overview Business Partner Main Office LAN Internet Network perimeters include connections to: The Internet u u Branch offices u Business partners u Remote users u Wireless networks u Internet applications Branch Office Remote User Wireless Network LAN
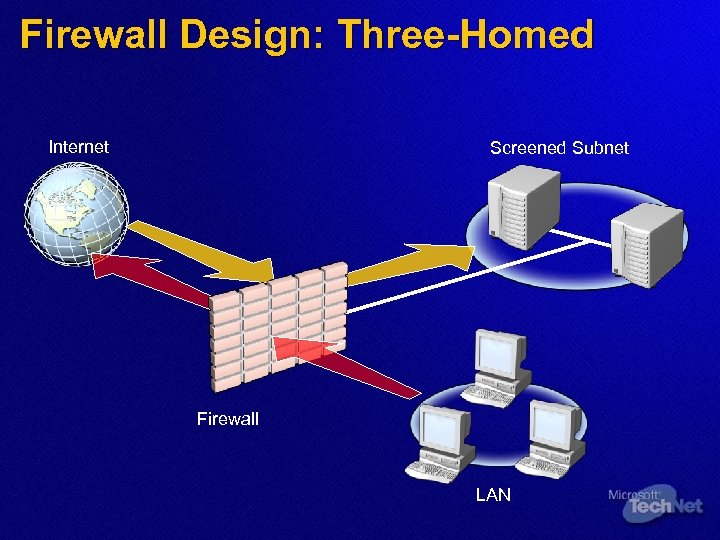 Firewall Design: Three-Homed Internet Screened Subnet Firewall LAN
Firewall Design: Three-Homed Internet Screened Subnet Firewall LAN
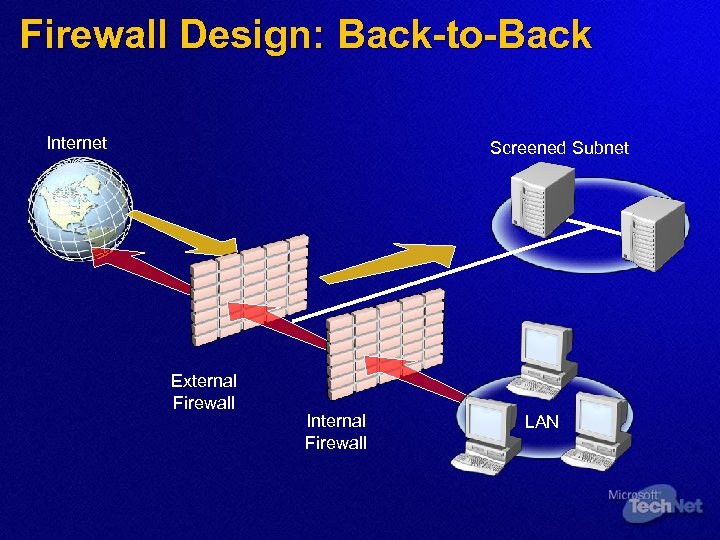 Firewall Design: Back-to-Back Internet Screened Subnet External Firewall Internal Firewall LAN
Firewall Design: Back-to-Back Internet Screened Subnet External Firewall Internal Firewall LAN
 What Firewalls Do NOT Protect Against u u u Malicious traffic that is passed on open ports and not inspected at the application layer by the firewall Any traffic that passes through an encrypted tunnel or session Attacks after a network has been penetrated Traffic that appears legitimate Users and administrators who intentionally or accidentally install viruses Administrators who use weak passwords
What Firewalls Do NOT Protect Against u u u Malicious traffic that is passed on open ports and not inspected at the application layer by the firewall Any traffic that passes through an encrypted tunnel or session Attacks after a network has been penetrated Traffic that appears legitimate Users and administrators who intentionally or accidentally install viruses Administrators who use weak passwords
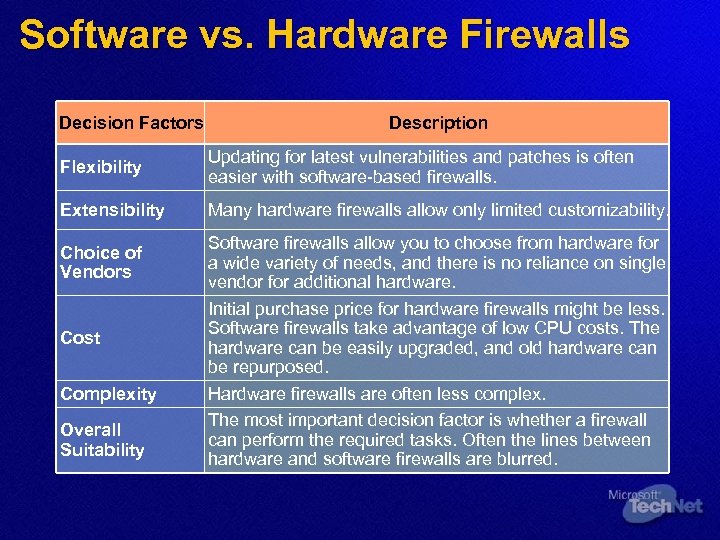 Software vs. Hardware Firewalls Decision Factors Description Flexibility Updating for latest vulnerabilities and patches is often easier with software-based firewalls. Extensibility Many hardware firewalls allow only limited customizability. Choice of Vendors Cost Complexity Overall Suitability Software firewalls allow you to choose from hardware for a wide variety of needs, and there is no reliance on single vendor for additional hardware. Initial purchase price for hardware firewalls might be less. Software firewalls take advantage of low CPU costs. The hardware can be easily upgraded, and old hardware can be repurposed. Hardware firewalls are often less complex. The most important decision factor is whether a firewall can perform the required tasks. Often the lines between hardware and software firewalls are blurred.
Software vs. Hardware Firewalls Decision Factors Description Flexibility Updating for latest vulnerabilities and patches is often easier with software-based firewalls. Extensibility Many hardware firewalls allow only limited customizability. Choice of Vendors Cost Complexity Overall Suitability Software firewalls allow you to choose from hardware for a wide variety of needs, and there is no reliance on single vendor for additional hardware. Initial purchase price for hardware firewalls might be less. Software firewalls take advantage of low CPU costs. The hardware can be easily upgraded, and old hardware can be repurposed. Hardware firewalls are often less complex. The most important decision factor is whether a firewall can perform the required tasks. Often the lines between hardware and software firewalls are blurred.
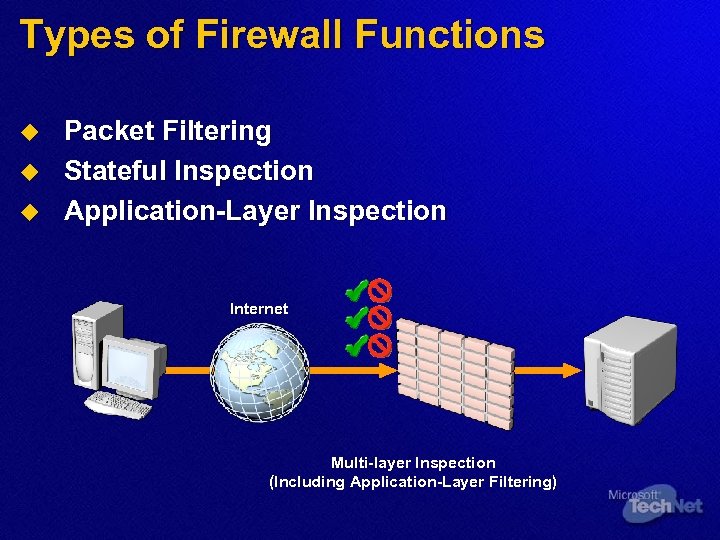 Types of Firewall Functions u u u Packet Filtering Stateful Inspection Application-Layer Inspection Internet Multi-layer Inspection (Including Application-Layer Filtering)
Types of Firewall Functions u u u Packet Filtering Stateful Inspection Application-Layer Inspection Internet Multi-layer Inspection (Including Application-Layer Filtering)
 Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
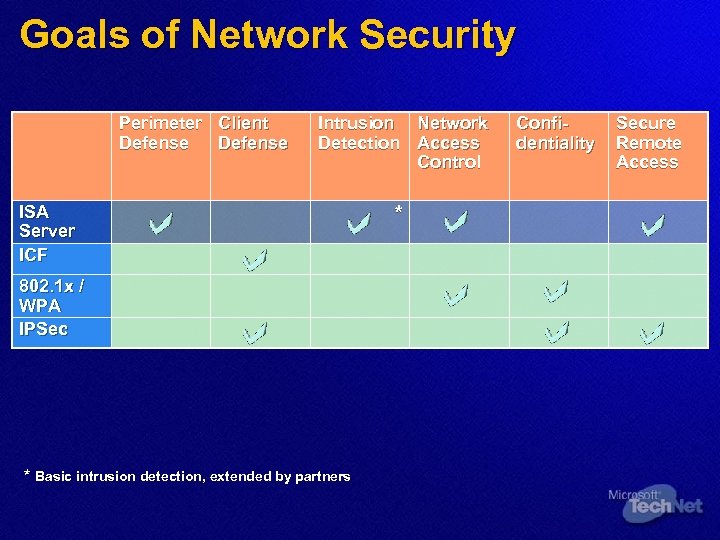 Goals of Network Security Perimeter Client Defense Intrusion Network Detection Access Control ISA Server ICF 802. 1 x / WPA IPSec * Basic intrusion detection, extended by partners * Confidentiality Secure Remote Access
Goals of Network Security Perimeter Client Defense Intrusion Network Detection Access Control ISA Server ICF 802. 1 x / WPA IPSec * Basic intrusion detection, extended by partners * Confidentiality Secure Remote Access
 Protecting Perimeters u ISA Server has full screening capabilities: Ø Ø Ø u u u Packet filtering Stateful inspection Application-level inspection ISA Server blocks all network traffic unless you allow it ISA Server provides secure VPN connectivity ISA Server is ICSA certified and Common Criteria certified
Protecting Perimeters u ISA Server has full screening capabilities: Ø Ø Ø u u u Packet filtering Stateful inspection Application-level inspection ISA Server blocks all network traffic unless you allow it ISA Server provides secure VPN connectivity ISA Server is ICSA certified and Common Criteria certified
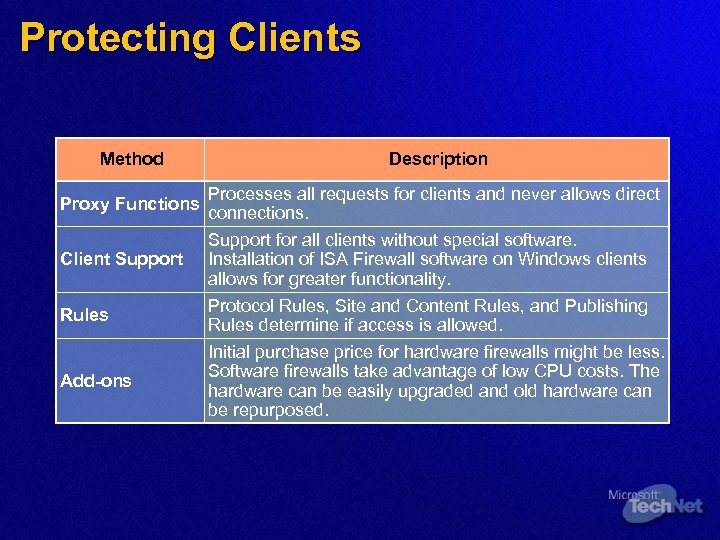 Protecting Clients Method Proxy Functions Client Support Rules Add-ons Description Processes all requests for clients and never allows direct connections. Support for all clients without special software. Installation of ISA Firewall software on Windows clients allows for greater functionality. Protocol Rules, Site and Content Rules, and Publishing Rules determine if access is allowed. Initial purchase price for hardware firewalls might be less. Software firewalls take advantage of low CPU costs. The hardware can be easily upgraded and old hardware can be repurposed.
Protecting Clients Method Proxy Functions Client Support Rules Add-ons Description Processes all requests for clients and never allows direct connections. Support for all clients without special software. Installation of ISA Firewall software on Windows clients allows for greater functionality. Protocol Rules, Site and Content Rules, and Publishing Rules determine if access is allowed. Initial purchase price for hardware firewalls might be less. Software firewalls take advantage of low CPU costs. The hardware can be easily upgraded and old hardware can be repurposed.
 Protecting Web Servers u Web Publishing Rules Ø u Protect Web servers behind the firewall from external attacks by inspecting HTTP traffic and ensuring that it is properly formatted and complies with standards Inspection of Secure Socket Layer (SSL) traffic Ø Ø Decrypts and inspects incoming encrypted Web requests for proper formatting and standards compliance Will optionally re-encrypt the traffic before sending them to your Web server
Protecting Web Servers u Web Publishing Rules Ø u Protect Web servers behind the firewall from external attacks by inspecting HTTP traffic and ensuring that it is properly formatted and complies with standards Inspection of Secure Socket Layer (SSL) traffic Ø Ø Decrypts and inspects incoming encrypted Web requests for proper formatting and standards compliance Will optionally re-encrypt the traffic before sending them to your Web server
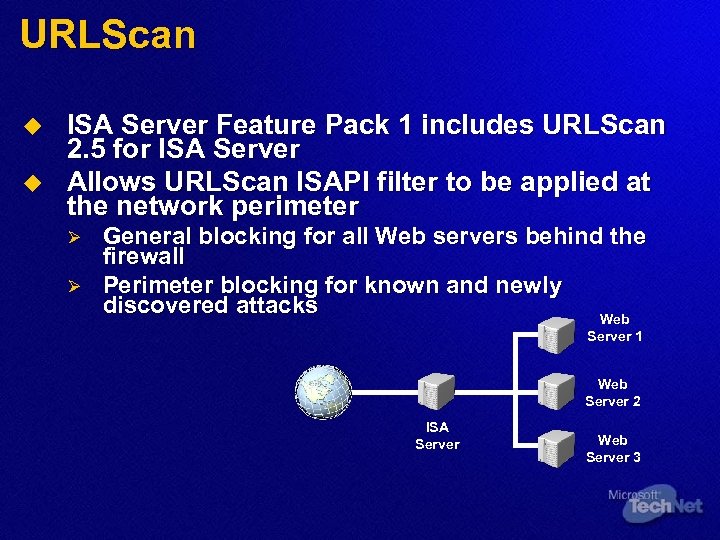 URLScan u u ISA Server Feature Pack 1 includes URLScan 2. 5 for ISA Server Allows URLScan ISAPI filter to be applied at the network perimeter Ø Ø General blocking for all Web servers behind the firewall Perimeter blocking for known and newly discovered attacks Web Server 1 Web Server 2 ISA Server Web Server 3
URLScan u u ISA Server Feature Pack 1 includes URLScan 2. 5 for ISA Server Allows URLScan ISAPI filter to be applied at the network perimeter Ø Ø General blocking for all Web servers behind the firewall Perimeter blocking for known and newly discovered attacks Web Server 1 Web Server 2 ISA Server Web Server 3
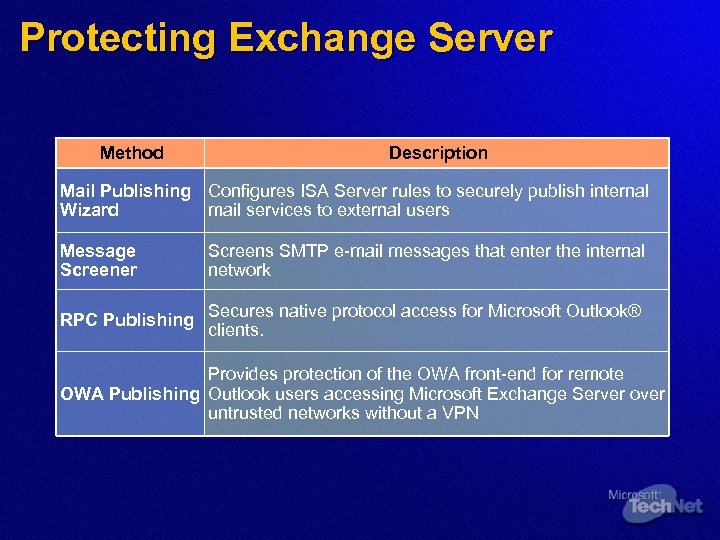 Protecting Exchange Server Method Description Mail Publishing Configures ISA Server rules to securely publish internal Wizard mail services to external users Message Screener Screens SMTP e-mail messages that enter the internal network RPC Publishing Secures native protocol access for Microsoft Outlook® clients. Provides protection of the OWA front-end for remote OWA Publishing Outlook users accessing Microsoft Exchange Server over untrusted networks without a VPN
Protecting Exchange Server Method Description Mail Publishing Configures ISA Server rules to securely publish internal Wizard mail services to external users Message Screener Screens SMTP e-mail messages that enter the internal network RPC Publishing Secures native protocol access for Microsoft Outlook® clients. Provides protection of the OWA front-end for remote OWA Publishing Outlook users accessing Microsoft Exchange Server over untrusted networks without a VPN
 Traffic That Bypasses Firewall Inspection u u u SSL tunnels through traditional firewalls because it is encrypted, which allows viruses and worms to pass through undetected and infect internal servers VPN traffic is encrypted and cannot be inspected Instant Messenger (IM) traffic often is not inspected and might be used to transfer files
Traffic That Bypasses Firewall Inspection u u u SSL tunnels through traditional firewalls because it is encrypted, which allows viruses and worms to pass through undetected and infect internal servers VPN traffic is encrypted and cannot be inspected Instant Messenger (IM) traffic often is not inspected and might be used to transfer files
 Inspecting All Traffic u Use intrusion detection and other mechanisms to inspect VPN traffic after it has been decrypted Ø u u Remember: Defense in Depth Use a firewall that can inspect SSL traffic Expand inspection capabilities of your firewall Ø Use firewall add-ons to inspect IM traffic
Inspecting All Traffic u Use intrusion detection and other mechanisms to inspect VPN traffic after it has been decrypted Ø u u Remember: Defense in Depth Use a firewall that can inspect SSL traffic Expand inspection capabilities of your firewall Ø Use firewall add-ons to inspect IM traffic
 SSL Inspection u u SSL tunnels through traditional firewalls because it is encrypted, which allows viruses and worms to pass through undetected and infect internal servers. ISA Server can decrypt and inspect SSL traffic. Inspected traffic can be sent to the internal server re-encrypted or in the clear.
SSL Inspection u u SSL tunnels through traditional firewalls because it is encrypted, which allows viruses and worms to pass through undetected and infect internal servers. ISA Server can decrypt and inspect SSL traffic. Inspected traffic can be sent to the internal server re-encrypted or in the clear.
 ISA Server Hardening u u Harden the network stack Disable unnecessary network protocols on the external network interface: Ø Ø Ø Client for Microsoft Networks File and Printer Sharing for Microsoft Networks Net. BIOS over TCP/IP
ISA Server Hardening u u Harden the network stack Disable unnecessary network protocols on the external network interface: Ø Ø Ø Client for Microsoft Networks File and Printer Sharing for Microsoft Networks Net. BIOS over TCP/IP
 Best Practices u u Use access rules that only allow requests that are specifically allowed Use ISA Server’s authentication capabilities to restrict and log Internet access Configure Web publishing rules only for specific destination sets Use SSL Inspection to inspect encrypted data that is entering your network
Best Practices u u Use access rules that only allow requests that are specifically allowed Use ISA Server’s authentication capabilities to restrict and log Internet access Configure Web publishing rules only for specific destination sets Use SSL Inspection to inspect encrypted data that is entering your network
 Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
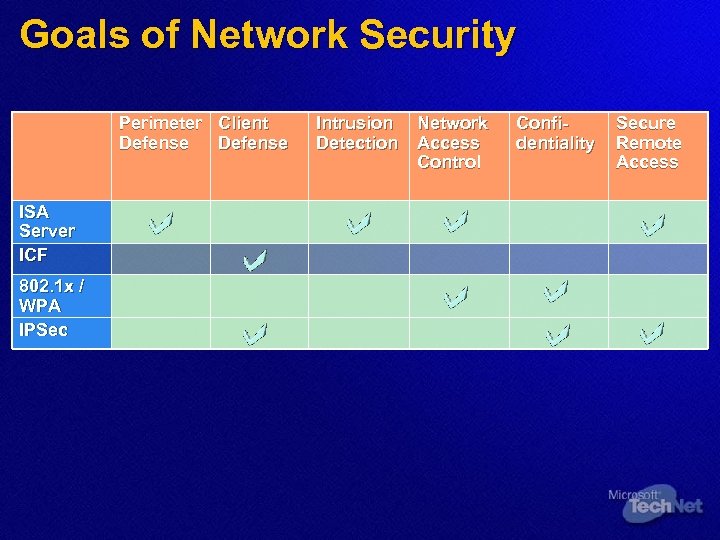 Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Detection Network Access Control Confidentiality Secure Remote Access
Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Detection Network Access Control Confidentiality Secure Remote Access
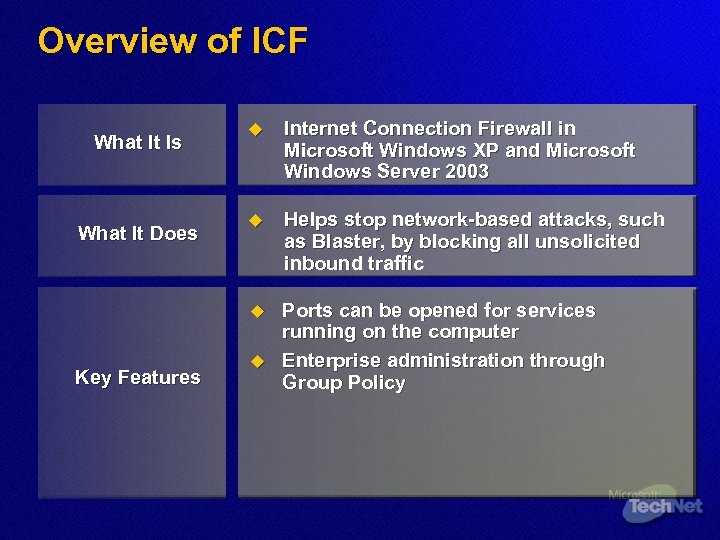 Overview of ICF What It Does Key Features Internet Connection Firewall in Microsoft Windows XP and Microsoft Windows Server 2003 u Helps stop network-based attacks, such as Blaster, by blocking all unsolicited inbound traffic u What It Is u Ports can be opened for services running on the computer Enterprise administration through Group Policy u
Overview of ICF What It Does Key Features Internet Connection Firewall in Microsoft Windows XP and Microsoft Windows Server 2003 u Helps stop network-based attacks, such as Blaster, by blocking all unsolicited inbound traffic u What It Is u Ports can be opened for services running on the computer Enterprise administration through Group Policy u
 Enabling ICF u u Enabled by: Ø Selecting one check box Ø Network Setup Wizard Ø New Connection Wizard Enabled separately for each network connection
Enabling ICF u u Enabled by: Ø Selecting one check box Ø Network Setup Wizard Ø New Connection Wizard Enabled separately for each network connection
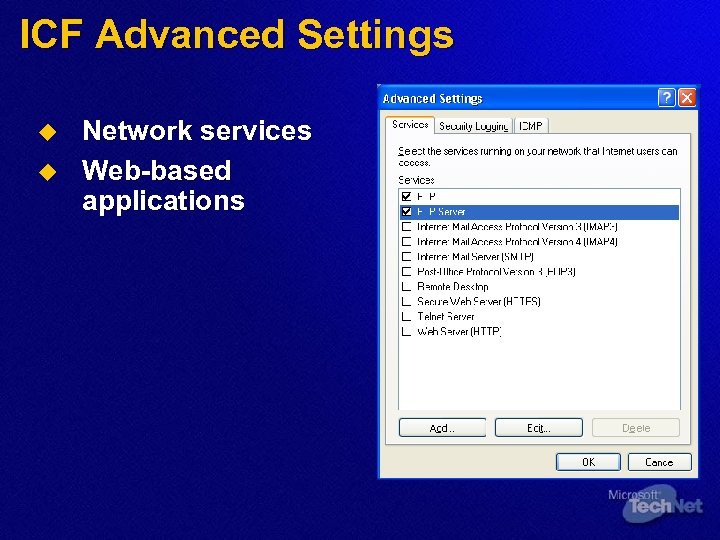 ICF Advanced Settings u u Network services Web-based applications
ICF Advanced Settings u u Network services Web-based applications
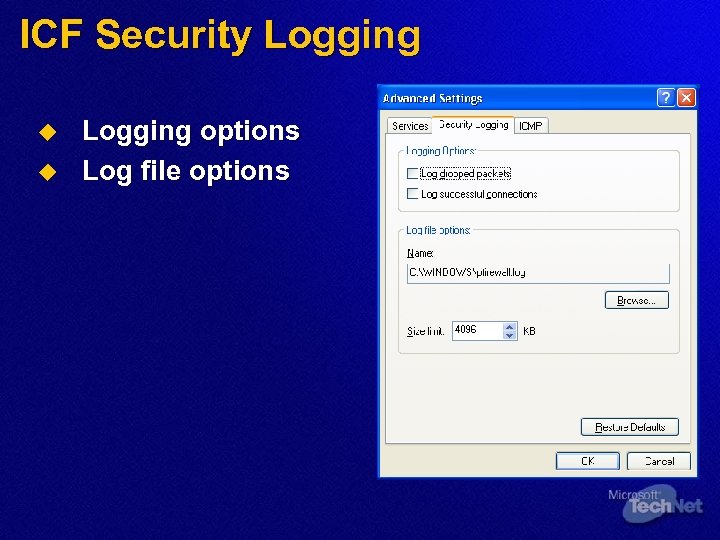 ICF Security Logging u u Logging options Log file options
ICF Security Logging u u Logging options Log file options
 ICF in the Enterprise u u Configure ICF by using Group Policy Combine ICF with Network Access Quarantine Control
ICF in the Enterprise u u Configure ICF by using Group Policy Combine ICF with Network Access Quarantine Control
 Best Practices u u Use ICF for home offices and small business to provide protection for computers directly connected to the Internet Do not turn on ICF for a VPN connection (but do enable ICF for the underlying LAN or dial-up connection Configure service definitions for each ICF connection through which you want the service to work Set the size of the security log to 16 megabytes to prevent an overflow that might be caused by denial-of-service attacks
Best Practices u u Use ICF for home offices and small business to provide protection for computers directly connected to the Internet Do not turn on ICF for a VPN connection (but do enable ICF for the underlying LAN or dial-up connection Configure service definitions for each ICF connection through which you want the service to work Set the size of the security log to 16 megabytes to prevent an overflow that might be caused by denial-of-service attacks
 Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
Agenda u u u Introduction Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
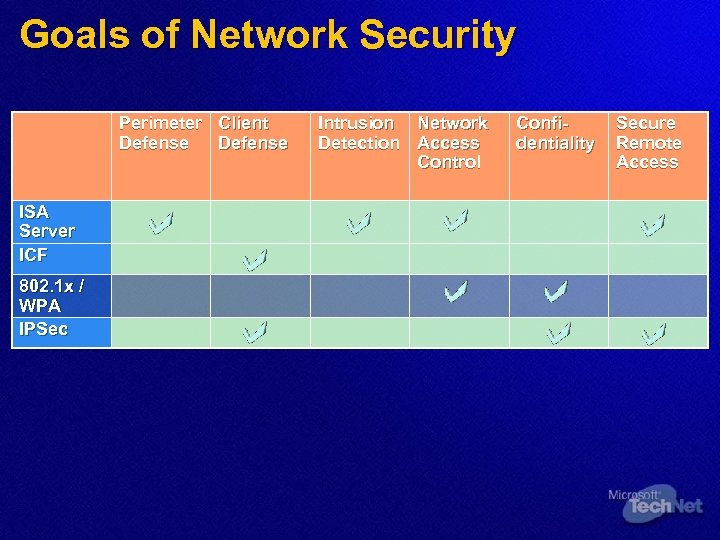 Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Network Detection Access Control Confidentiality Secure Remote Access
Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Network Detection Access Control Confidentiality Secure Remote Access
 Wireless Security Issues u Limitations of Wired Equivalent Privacy (WEP) Ø Ø Ø u Static WEP keys are not dynamically changed and therefore are vulnerable to attack. There is no standard method for provisioning static WEP keys to clients. Scalability: Compromise of a static WEP key by anyone exposes everyone. Limitations of MAC Address Filtering Ø Attacker could spoof an allowed MAC address.
Wireless Security Issues u Limitations of Wired Equivalent Privacy (WEP) Ø Ø Ø u Static WEP keys are not dynamically changed and therefore are vulnerable to attack. There is no standard method for provisioning static WEP keys to clients. Scalability: Compromise of a static WEP key by anyone exposes everyone. Limitations of MAC Address Filtering Ø Attacker could spoof an allowed MAC address.
 Possible Solutions u Password-based Layer 2 Authentication Ø u Certificate-based Layer 2 Authentication Ø u IEEE 802. 1 x PEAP/MSCHAP v 2 IEEE 802. 1 x EAP-TLS Other Options Ø VPN Connectivity Ø Ø Ø L 2 TP/IPsec (preferred) or PPTP Does not allow for roaming Useful when using public wireless hotspots No computer authentication or processing of computer settings in Group Policy IPSec Ø Interoperability issues
Possible Solutions u Password-based Layer 2 Authentication Ø u Certificate-based Layer 2 Authentication Ø u IEEE 802. 1 x PEAP/MSCHAP v 2 IEEE 802. 1 x EAP-TLS Other Options Ø VPN Connectivity Ø Ø Ø L 2 TP/IPsec (preferred) or PPTP Does not allow for roaming Useful when using public wireless hotspots No computer authentication or processing of computer settings in Group Policy IPSec Ø Interoperability issues
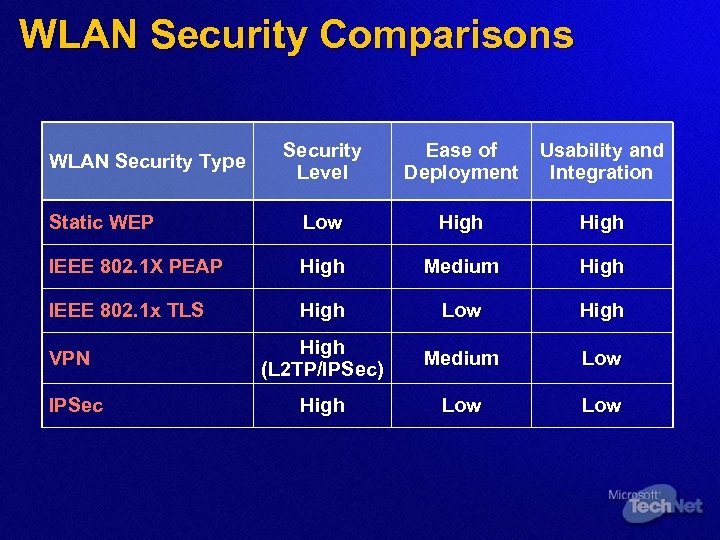 WLAN Security Comparisons Security Level Ease of Deployment Usability and Integration Static WEP Low High IEEE 802. 1 X PEAP High Medium High IEEE 802. 1 x TLS High Low High (L 2 TP/IPSec) Medium Low High Low WLAN Security Type VPN IPSec
WLAN Security Comparisons Security Level Ease of Deployment Usability and Integration Static WEP Low High IEEE 802. 1 X PEAP High Medium High IEEE 802. 1 x TLS High Low High (L 2 TP/IPSec) Medium Low High Low WLAN Security Type VPN IPSec
 802. 1 x u Defines port-based access control mechanism Ø Ø u Allows choice of authentication methods using Extensible Authentication Protocol (EAP) Ø Ø u Works on anything, wired or wireless No special encryption key requirements Chosen by peers at authentication time Access point doesn’t care about EAP methods Manages keys automatically Ø No need to preprogram wireless encryption keys
802. 1 x u Defines port-based access control mechanism Ø Ø u Allows choice of authentication methods using Extensible Authentication Protocol (EAP) Ø Ø u Works on anything, wired or wireless No special encryption key requirements Chosen by peers at authentication time Access point doesn’t care about EAP methods Manages keys automatically Ø No need to preprogram wireless encryption keys
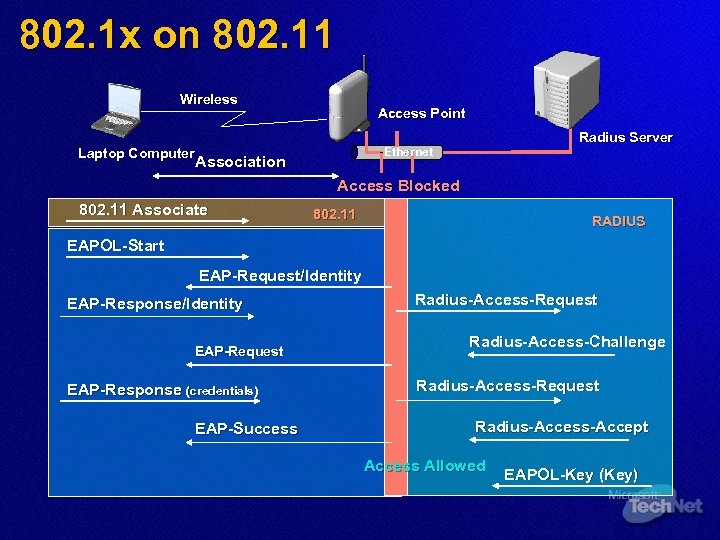 802. 1 x on 802. 11 Wireless Access Point Radius Server Ethernet Laptop Computer Association Access Blocked 802. 11 Associate 802. 11 RADIUS EAPOL-Start EAP-Request/Identity EAP-Response/Identity EAP-Request EAP-Response (credentials) EAP-Success Radius-Access-Request Radius-Access-Challenge Radius-Access-Request Radius-Access-Accept Access Allowed EAPOL-Key (Key)
802. 1 x on 802. 11 Wireless Access Point Radius Server Ethernet Laptop Computer Association Access Blocked 802. 11 Associate 802. 11 RADIUS EAPOL-Start EAP-Request/Identity EAP-Response/Identity EAP-Request EAP-Response (credentials) EAP-Success Radius-Access-Request Radius-Access-Challenge Radius-Access-Request Radius-Access-Accept Access Allowed EAPOL-Key (Key)
 System Requirements for 802. 1 x u u Client: Windows XP Server: Windows Server 2003 IAS Ø Ø u Internet Authentication Service—our RADIUS server Certificate on IAS computer 802. 1 x on Windows 2000 Ø Ø Client and IAS must have SP 3 See KB article 313664 No zero-configuration support in the client Supports only EAP-TLS and MS-CHAPv 2 Ø Future EAP methods in Windows XP and Windows Server 2003 might not be backported
System Requirements for 802. 1 x u u Client: Windows XP Server: Windows Server 2003 IAS Ø Ø u Internet Authentication Service—our RADIUS server Certificate on IAS computer 802. 1 x on Windows 2000 Ø Ø Client and IAS must have SP 3 See KB article 313664 No zero-configuration support in the client Supports only EAP-TLS and MS-CHAPv 2 Ø Future EAP methods in Windows XP and Windows Server 2003 might not be backported
 802. 1 x Setup 1. 2. 3. 4. 5. 6. 7. 8. 9. Configure Windows Server 2003 with IAS Join a domain Enroll computer certificate Register IAS in Active Directory Configure RADIUS logging Add AP as RADIUS client Configure AP for RADIUS and 802. 1 x Create wireless client access policy Configure clients Ø Don’t forget to import the root certificate
802. 1 x Setup 1. 2. 3. 4. 5. 6. 7. 8. 9. Configure Windows Server 2003 with IAS Join a domain Enroll computer certificate Register IAS in Active Directory Configure RADIUS logging Add AP as RADIUS client Configure AP for RADIUS and 802. 1 x Create wireless client access policy Configure clients Ø Don’t forget to import the root certificate
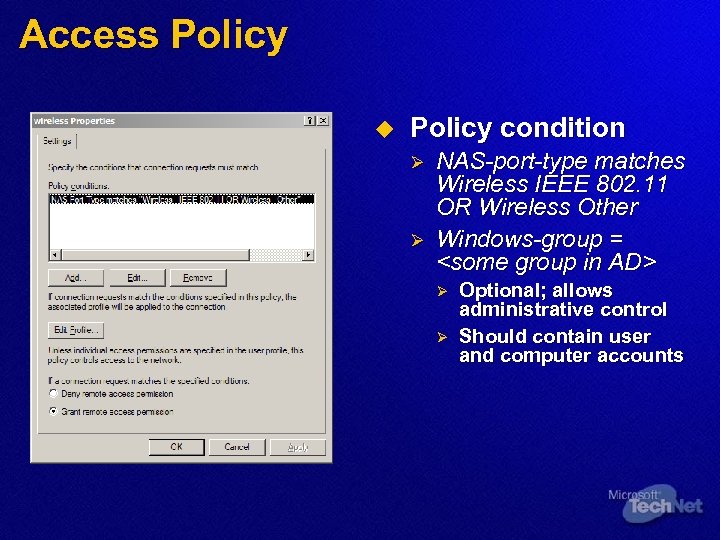 Access Policy u Policy condition Ø Ø NAS-port-type matches Wireless IEEE 802. 11 OR Wireless Other Windows-group =
Access Policy u Policy condition Ø Ø NAS-port-type matches Wireless IEEE 802. 11 OR Wireless Other Windows-group =
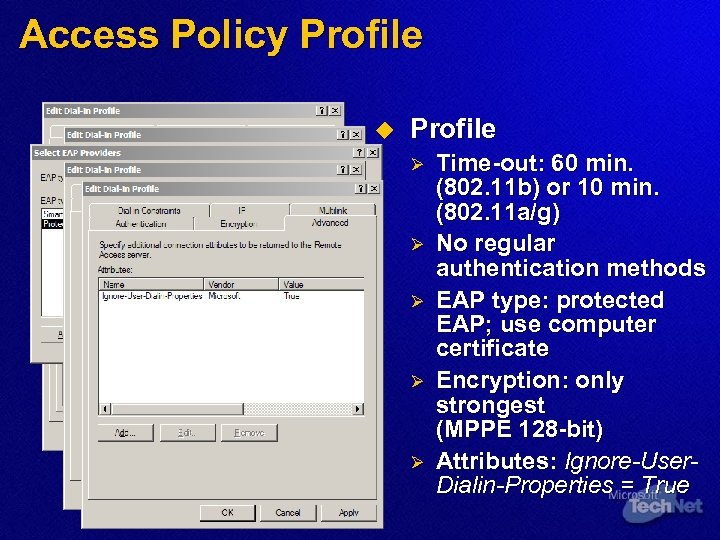 Access Policy Profile u Profile Ø Ø Ø Time-out: 60 min. (802. 11 b) or 10 min. (802. 11 a/g) No regular authentication methods EAP type: protected EAP; use computer certificate Encryption: only strongest (MPPE 128 -bit) Attributes: Ignore-User. Dialin-Properties = True
Access Policy Profile u Profile Ø Ø Ø Time-out: 60 min. (802. 11 b) or 10 min. (802. 11 a/g) No regular authentication methods EAP type: protected EAP; use computer certificate Encryption: only strongest (MPPE 128 -bit) Attributes: Ignore-User. Dialin-Properties = True
 Wireless Protected Access (WPA) u A specification of standards-based, interoperable security enhancements that strongly increase the level of data protection and access control for existing and future wireless LAN systems WPA Requires 802. 1 x authentication for network access u Goals u Ø Ø u Enhanced data encryption Provide user authentication Be forward compatible with 802. 11 i Provide non-RADIUS solution for Small/Home offices Wi-Fi Alliance began certification testing for interoperability on WPA products in February 2003
Wireless Protected Access (WPA) u A specification of standards-based, interoperable security enhancements that strongly increase the level of data protection and access control for existing and future wireless LAN systems WPA Requires 802. 1 x authentication for network access u Goals u Ø Ø u Enhanced data encryption Provide user authentication Be forward compatible with 802. 11 i Provide non-RADIUS solution for Small/Home offices Wi-Fi Alliance began certification testing for interoperability on WPA products in February 2003
 Use 802. 1 x authentication u Organize wireless users and computers into groups u Apply wireless access policies using Group Policy Best Practices u Use EAP-TLS for certificate-based authentication and PEAP for password-based authentication u Configure your remote access policy to support user authentication as well as machine authentication u Develop a method to deal with rogue access points, such as LAN-based 802. 1 x authentication, site surveys, network monitoring, and user education u
Use 802. 1 x authentication u Organize wireless users and computers into groups u Apply wireless access policies using Group Policy Best Practices u Use EAP-TLS for certificate-based authentication and PEAP for password-based authentication u Configure your remote access policy to support user authentication as well as machine authentication u Develop a method to deal with rogue access points, such as LAN-based 802. 1 x authentication, site surveys, network monitoring, and user education u
 Agenda u u u Introduction/Defense in Depth Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
Agenda u u u Introduction/Defense in Depth Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Communications by Using IPSec
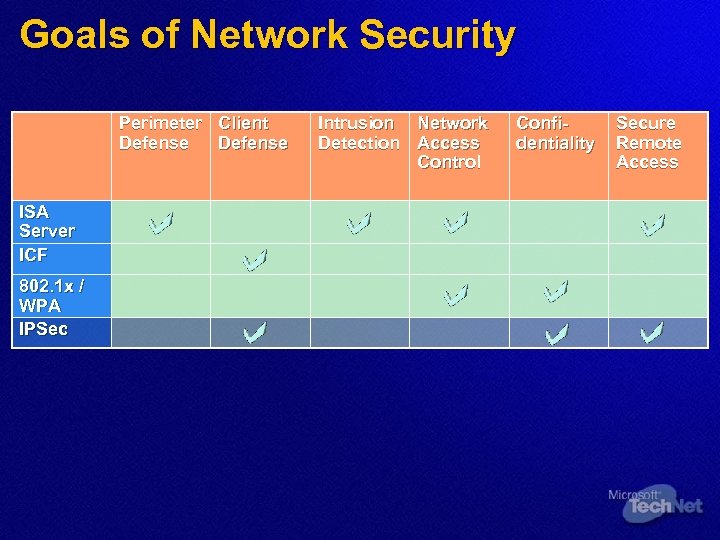 Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Network Detection Access Control Confidentiality Secure Remote Access
Goals of Network Security Perimeter Client Defense ISA Server ICF 802. 1 x / WPA IPSec Intrusion Network Detection Access Control Confidentiality Secure Remote Access
 Overview of IPSec u What is IP Security (IPSec)? Ø Ø u A method to secure IP traffic Framework of open standards developed by the Internet Engineering Task Force (IETF) Why use IPSec? Ø Ø To ensure encrypted and authenticated communications at the IP layer To provide transport security that is independent of applications or application-layer protocols
Overview of IPSec u What is IP Security (IPSec)? Ø Ø u A method to secure IP traffic Framework of open standards developed by the Internet Engineering Task Force (IETF) Why use IPSec? Ø Ø To ensure encrypted and authenticated communications at the IP layer To provide transport security that is independent of applications or application-layer protocols
 IPSec Scenarios u u Basic permit/block packet filtering Secure internal LAN communications Domain replication through firewalls VPN across untrusted media
IPSec Scenarios u u Basic permit/block packet filtering Secure internal LAN communications Domain replication through firewalls VPN across untrusted media
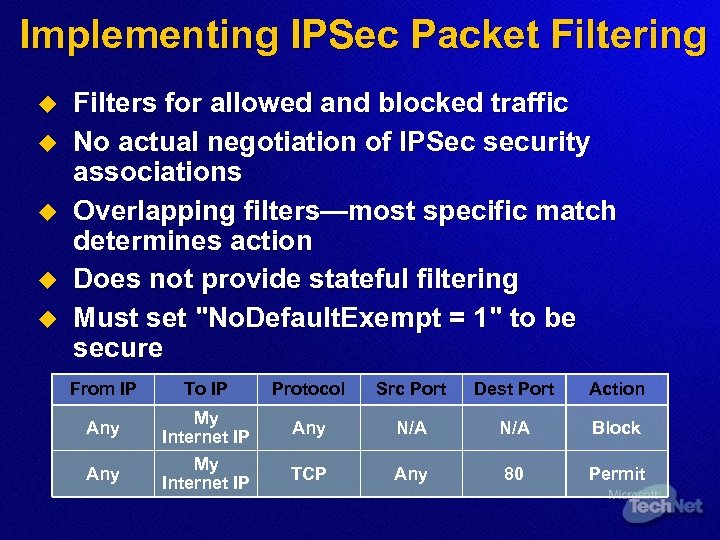 Implementing IPSec Packet Filtering u u u Filters for allowed and blocked traffic No actual negotiation of IPSec security associations Overlapping filters—most specific match determines action Does not provide stateful filtering Must set "No. Default. Exempt = 1" to be secure From IP Any To IP My Internet IP Protocol Src Port Dest Port Action Any N/A Block TCP Any 80 Permit
Implementing IPSec Packet Filtering u u u Filters for allowed and blocked traffic No actual negotiation of IPSec security associations Overlapping filters—most specific match determines action Does not provide stateful filtering Must set "No. Default. Exempt = 1" to be secure From IP Any To IP My Internet IP Protocol Src Port Dest Port Action Any N/A Block TCP Any 80 Permit
 Packet Filtering Is Not Sufficient to Protect Server u u u Spoofed IP packets containing queries or malicious content can still reach open ports through firewalls IPSec does not provide stateful inspection Many hacker tools use source ports 80, 88, 135, and so on, to connect to any destination port
Packet Filtering Is Not Sufficient to Protect Server u u u Spoofed IP packets containing queries or malicious content can still reach open ports through firewalls IPSec does not provide stateful inspection Many hacker tools use source ports 80, 88, 135, and so on, to connect to any destination port
 Traffic Not Filtered by IPSec u IP broadcast addresses Ø u Multicast addresses Ø u Kerberos is a secure protocol, which the Internet Key Exchange (IKE) negotiation service may use for authentication of other computers in a domain IKE—UDP destination port 500 Ø u From 224. 0. 0. 0 through 239. 255 Kerberos—UDP source or destination port 88 Ø u Cannot secure to multiple receivers Required to allow IKE to negotiate parameters for IPSec security Windows Server 2003 configures only IKE default exemption
Traffic Not Filtered by IPSec u IP broadcast addresses Ø u Multicast addresses Ø u Kerberos is a secure protocol, which the Internet Key Exchange (IKE) negotiation service may use for authentication of other computers in a domain IKE—UDP destination port 500 Ø u From 224. 0. 0. 0 through 239. 255 Kerberos—UDP source or destination port 88 Ø u Cannot secure to multiple receivers Required to allow IKE to negotiate parameters for IPSec security Windows Server 2003 configures only IKE default exemption
 Secure Internal Communications u Use IPSec to provide mutual device authentication Ø Ø u Use Authentication Header (AH) to ensure packet integrity Ø Ø u AH provides packet integrity AH does not encrypt, allowing for network intrusion detection Use Encapsulation Security Payload (ESP) to encrypt sensitive traffic Ø Ø u Use certificates or Kerberos Preshared key suitable for testing only ESP provides packet integrity and confidentiality Encryption prevents packet inspection Carefully plan which traffic should be secured
Secure Internal Communications u Use IPSec to provide mutual device authentication Ø Ø u Use Authentication Header (AH) to ensure packet integrity Ø Ø u AH provides packet integrity AH does not encrypt, allowing for network intrusion detection Use Encapsulation Security Payload (ESP) to encrypt sensitive traffic Ø Ø u Use certificates or Kerberos Preshared key suitable for testing only ESP provides packet integrity and confidentiality Encryption prevents packet inspection Carefully plan which traffic should be secured
 IPSec for Domain Replication u Use IPSec for replication through firewalls Ø u u On each domain controller, create an IPSec policy to secure all traffic to the other domain controller’s IP address Use ESP 3 DES for encryption Allow traffic through the firewall: Ø Ø UDP Port 500 (IKE) IP protocol 50 (ESP)
IPSec for Domain Replication u Use IPSec for replication through firewalls Ø u u On each domain controller, create an IPSec policy to secure all traffic to the other domain controller’s IP address Use ESP 3 DES for encryption Allow traffic through the firewall: Ø Ø UDP Port 500 (IKE) IP protocol 50 (ESP)
 VPN Across Untrusted Media u Client VPN Ø u Use L 2 TP/IPSec Branch Office VPN Ø Ø Ø Between Windows 2000 or Windows Server, running RRAS: Use L 2 TP/IPSec tunnel (easy to configure, appears as routable interface) To third-party gateway: Use L 2 TP/ISec or pure IPSec tunnel mode To Microsoft Windows NT® 4 RRAS Gateway: Use PPTP (IPSec not available)
VPN Across Untrusted Media u Client VPN Ø u Use L 2 TP/IPSec Branch Office VPN Ø Ø Ø Between Windows 2000 or Windows Server, running RRAS: Use L 2 TP/IPSec tunnel (easy to configure, appears as routable interface) To third-party gateway: Use L 2 TP/ISec or pure IPSec tunnel mode To Microsoft Windows NT® 4 RRAS Gateway: Use PPTP (IPSec not available)
 IPSec Performance u IPSec processing has some performance impact Ø IKE negotiation time—about 2– 5 seconds initially Ø Ø Ø u 5 round trips Authentication—Kerberos or certificates Cryptographic key generation and encrypted messages Done once per 8 hours by default, settable Session rekey is fast—<1– 2 seconds, 2 round trips, once per hour, settable Encryption of packets How to improve? Ø Ø Offloading NICs do IPSec almost at wire speed Using faster CPUs
IPSec Performance u IPSec processing has some performance impact Ø IKE negotiation time—about 2– 5 seconds initially Ø Ø Ø u 5 round trips Authentication—Kerberos or certificates Cryptographic key generation and encrypted messages Done once per 8 hours by default, settable Session rekey is fast—<1– 2 seconds, 2 round trips, once per hour, settable Encryption of packets How to improve? Ø Ø Offloading NICs do IPSec almost at wire speed Using faster CPUs
 Best Practices u u u u Plan your IPSec implementation carefully Choose between AH and ESP Use Group Policy to implement IPSec Policies Consider the use of IPSec NICs Never use Shared Key authentication outside your test lab Choose between certificates and Kerberos authentication Use care when requiring IPSec for communications with domain controllers and other infrastructure servers
Best Practices u u u u Plan your IPSec implementation carefully Choose between AH and ESP Use Group Policy to implement IPSec Policies Consider the use of IPSec NICs Never use Shared Key authentication outside your test lab Choose between certificates and Kerberos authentication Use care when requiring IPSec for communications with domain controllers and other infrastructure servers
 Session Summary u u u Introduction/Defense in Depth Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Networks by Using IPSec
Session Summary u u u Introduction/Defense in Depth Using Perimeter Defenses Using ISA Server to Protect Perimeters Using ICF to Protect Clients Protecting Wireless Networks Protecting Networks by Using IPSec
 Next Steps u u Stay informed and Sign up for security bulletins. Get the latest Microsoft security guidance. Get further Security Training. Get expert help with a Microsoft® Certified Partner. Microsoft Security Site (all audiences) Ø http: //www. microsoft. com/uk/security Tech. Net Security Site (IT professionals) Ø http: //www. microsoft. com/uk/technet/ MSDN Security Site (developers) Ø http: //www. microsoft. com/uk/msdn/
Next Steps u u Stay informed and Sign up for security bulletins. Get the latest Microsoft security guidance. Get further Security Training. Get expert help with a Microsoft® Certified Partner. Microsoft Security Site (all audiences) Ø http: //www. microsoft. com/uk/security Tech. Net Security Site (IT professionals) Ø http: //www. microsoft. com/uk/technet/ MSDN Security Site (developers) Ø http: //www. microsoft. com/uk/msdn/



