c878bbfe1d4e5adf3aaf5031114b48c4.ppt
- Количество слайдов: 21
 Implementing ACLs in Linux Jesse Dyer, Dennis Lu, and Erik Welsh Comp 527 – Fall 2001
Implementing ACLs in Linux Jesse Dyer, Dennis Lu, and Erik Welsh Comp 527 – Fall 2001
 Overview o o o o Why ACLs? Solaris ACLs NT ACLs Our ACLs VFS Our Implementation Some Examples Problems and Future Work
Overview o o o o Why ACLs? Solaris ACLs NT ACLs Our ACLs VFS Our Implementation Some Examples Problems and Future Work
 In case you were sleeping… o What is an ACL? n o What is an ACE? n o Access Control List: collection of Access Control Entries (ACEs) associated with a file. A structure specifying permission for a user, group, or other entity. What is an inode? n A structure containing metadata about files and directories.
In case you were sleeping… o What is an ACL? n o What is an ACE? n o Access Control List: collection of Access Control Entries (ACEs) associated with a file. A structure specifying permission for a user, group, or other entity. What is an inode? n A structure containing metadata about files and directories.
 Why ACLs? o o Traditional rwx for ugo not fine grained enough File owner controls all permissions Can allow group, but admin controls groups, creates administrative headache Want to give specific user or group ability to access to files and directories
Why ACLs? o o Traditional rwx for ugo not fine grained enough File owner controls all permissions Can allow group, but admin controls groups, creates administrative headache Want to give specific user or group ability to access to files and directories
 For Example – CVS on owlnet o o o Must give world rwx permissions! Allows ANY malicious user or accident to mess up your project files Preferably give access to certain directories to certain people
For Example – CVS on owlnet o o o Must give world rwx permissions! Allows ANY malicious user or accident to mess up your project files Preferably give access to certain directories to certain people
 Solaris ACLs o o Standard ACL implementation Can give specific and multiple users and groups rwx permission on a file Has mask entry Almost POSIX compliant
Solaris ACLs o o Standard ACL implementation Can give specific and multiple users and groups rwx permission on a file Has mask entry Almost POSIX compliant
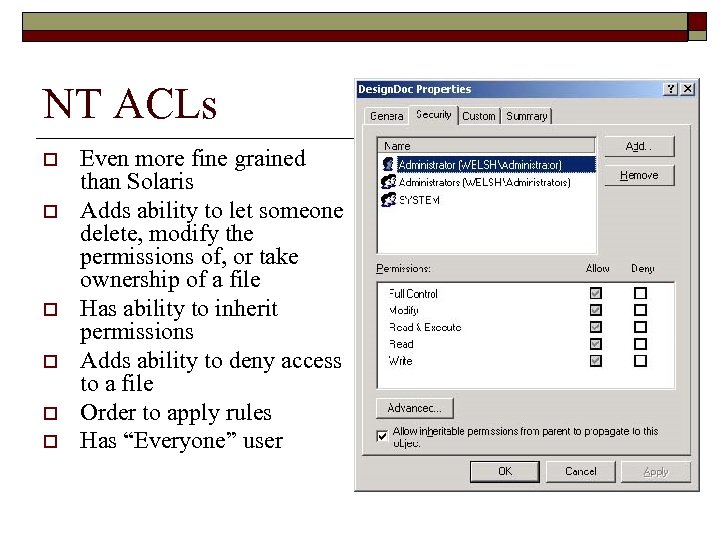 NT ACLs o o o Even more fine grained than Solaris Adds ability to let someone delete, modify the permissions of, or take ownership of a file Has ability to inherit permissions Adds ability to deny access to a file Order to apply rules Has “Everyone” user
NT ACLs o o o Even more fine grained than Solaris Adds ability to let someone delete, modify the permissions of, or take ownership of a file Has ability to inherit permissions Adds ability to deny access to a file Order to apply rules Has “Everyone” user
 Our ACLs o o o Combination of Solaris and NT ACLs Have traditional rwx for multiple users and groups Added p (permission) Added inheritance Added ability to deny Rules applies in order
Our ACLs o o o Combination of Solaris and NT ACLs Have traditional rwx for multiple users and groups Added p (permission) Added inheritance Added ability to deny Rules applies in order
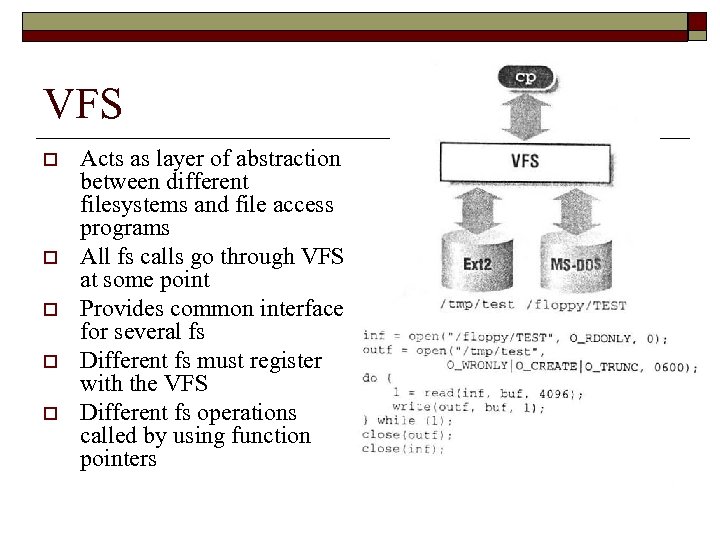 VFS o o o Acts as layer of abstraction between different filesystems and file access programs All fs calls go through VFS at some point Provides common interface for several fs Different fs must register with the VFS Different fs operations called by using function pointers
VFS o o o Acts as layer of abstraction between different filesystems and file access programs All fs calls go through VFS at some point Provides common interface for several fs Different fs must register with the VFS Different fs operations called by using function pointers
 ext 2 o o o o Default Linux file system Allows for variable size blocks to minimize fragmentation Variable number of inodes to maximize usable space Block preallocation for files to reduce fragmentation Disk blocks partitioned into groups Robust crash recovery Designed to be extensible (ACLs, encryption, etc…)
ext 2 o o o o Default Linux file system Allows for variable size blocks to minimize fragmentation Variable number of inodes to maximize usable space Block preallocation for files to reduce fragmentation Disk blocks partitioned into groups Robust crash recovery Designed to be extensible (ACLs, encryption, etc…)
 Our Implementation o o o Modified version of ext 2 on Mandrake Kept ACL information in the inode, not in blocks Max users = 32 Compiled as kernel module Modified mke 2 fs to setup our fs and ext 2 fsck to not demolish our ACLs
Our Implementation o o o Modified version of ext 2 on Mandrake Kept ACL information in the inode, not in blocks Max users = 32 Compiled as kernel module Modified mke 2 fs to setup our fs and ext 2 fsck to not demolish our ACLs
 Permission Checking o o o If no ACL present, reverts to traditional file permissions Search for any deny, then allow Support for new modify permission functionality
Permission Checking o o o If no ACL present, reverts to traditional file permissions Search for any deny, then allow Support for new modify permission functionality
 setfacl o o o User command utility to set, modify, or delete ACLs on a file Can be ran by file owner or anyone given permission to modify permissions Sample commands: n n setfacl –s –m –u –d u: alice: +rx: i my. File o: : drwx my. File u: alice my. File
setfacl o o o User command utility to set, modify, or delete ACLs on a file Can be ran by file owner or anyone given permission to modify permissions Sample commands: n n setfacl –s –m –u –d u: alice: +rx: i my. File o: : drwx my. File u: alice my. File
 getfacl o o o User utility to examine the ACL on a particular file Examines a file’s inode to detemine what permissions are set Sample: n getfacl my. File
getfacl o o o User utility to examine the ACL on a particular file Examines a file’s inode to detemine what permissions are set Sample: n getfacl my. File
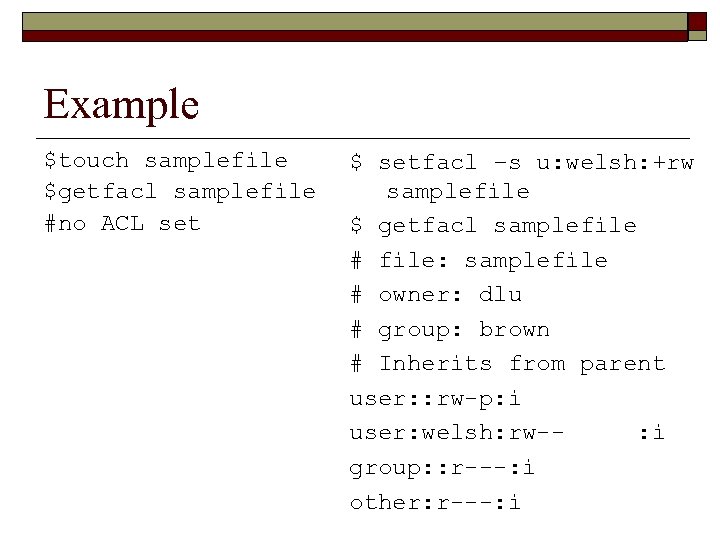 Example $touch samplefile $getfacl samplefile #no ACL set $ setfacl –s u: welsh: +rw samplefile $ getfacl samplefile # file: samplefile # owner: dlu # group: brown # Inherits from parent user: : rw-p: i user: welsh: rw-: i group: : r---: i other: r---: i
Example $touch samplefile $getfacl samplefile #no ACL set $ setfacl –s u: welsh: +rw samplefile $ getfacl samplefile # file: samplefile # owner: dlu # group: brown # Inherits from parent user: : rw-p: i user: welsh: rw-: i group: : r---: i other: r---: i
: i group: : r---: i other: r---: i 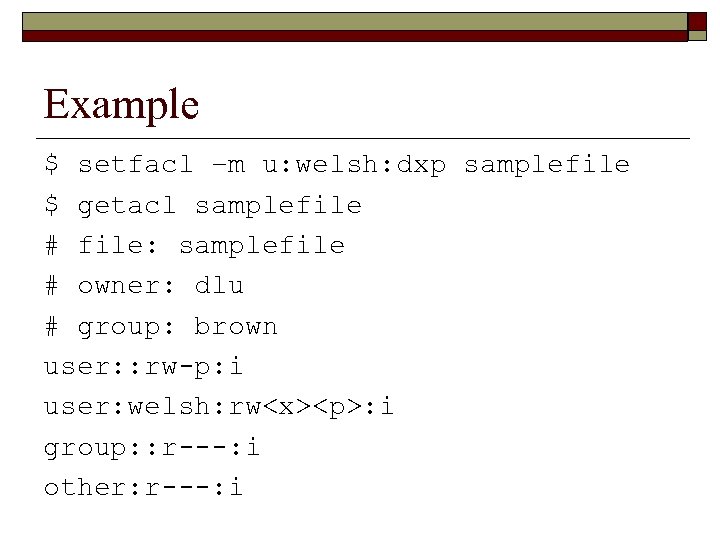 Example $ setfacl –m u: welsh: dxp samplefile $ getacl samplefile # file: samplefile # owner: dlu # group: brown user: : rw-p: i user: welsh: rw
Example $ setfacl –m u: welsh: dxp samplefile $ getacl samplefile # file: samplefile # owner: dlu # group: brown user: : rw-p: i user: welsh: rw
 Example – permission partitions Development QA Marketing
Example – permission partitions Development QA Marketing
 Problems o Open Source code is inconsistently documented o Communication between kernel and user programs is confusing o Testing is a pain
Problems o Open Source code is inconsistently documented o Communication between kernel and user programs is confusing o Testing is a pain
 Future Work o o Make it as a patch to the current linux distribution Determine the optimum number of ACLs to be kept Caching effective ACLs minimizes performance hit from inheritance Graphical User Interface
Future Work o o Make it as a patch to the current linux distribution Determine the optimum number of ACLs to be kept Caching effective ACLs minimizes performance hit from inheritance Graphical User Interface
 The Ideal ACL o o Deny and allow have equal importance, based on their location in the ACL. I. e. Order matters. Example n n n User Chuck member of: everyone, losers. ACL: allow Chuck; deny losers; allow everyone Chuck is given access. Existing implementation Chuck is denied access
The Ideal ACL o o Deny and allow have equal importance, based on their location in the ACL. I. e. Order matters. Example n n n User Chuck member of: everyone, losers. ACL: allow Chuck; deny losers; allow everyone Chuck is given access. Existing implementation Chuck is denied access
 References o o o Bovet and Cesati, Understanding the Linux Kernel, O’Reilly, 2001 Anderson, Security Engineering, Wiley, 2001 Linux Documentation Project Algis Dan
References o o o Bovet and Cesati, Understanding the Linux Kernel, O’Reilly, 2001 Anderson, Security Engineering, Wiley, 2001 Linux Documentation Project Algis Dan


